Password Spraying Is One of the Top Types of Password Attacks
There are many types of password attacks, meaning cyber attacks that exploit weak and reused passwords to take over user accounts, whether to take advantage of the stolen accounts directly or sell access to them on underground markets. The most common types of password attacks are often brute force attacks:
- Password spraying
- Credential stuffing
- Phishing
- Dictionary attacks
- Keylogger attacks
- Exhaustive key search
- Reverse brute-force attack
SpyCloud helps organizations combat brute force attacks like password spraying by detecting when users’ passwords are available on the criminal underground, heading off attacks that leverage weak or stolen credentials.
Password Spraying Exploits Users’ Bad Password Habits
Password spraying is a type of password attack where a cybercriminal uses a list of usernames and common passwords like “password” and “qwerty” to try to gain access to a particular site. Once they get a match, the criminal may test that same username and password combination against as many accounts as possible.
Password spraying is a successful brute force attack because so many people use the same common passwords across multiple accounts, including consumer and professional logins. With SpyCloud, you can combat password spraying by detecting when your users’ passwords have appeared in a data breach.
Protect Your Users from Password Spraying with SpyCloud
Attacks like password spraying work when users’ passwords are weak or have been exposed in a previous data breach. While strong password guidelines can encourage users to choose better passwords, policies that make passwords harder for users to remember can backfire, encouraging password reuse across accounts that’s harder for IT teams to detect or prevent.
SpyCloud helps enterprises take a proactive approach to password spraying by checking users’ passwords against the largest repository of recaptured darknet data in the world, with over 350 billion recaptured assets from third-party data breaches and malware victim logs – and growing every month. If a user’s credentials appear in the SpyCloud dataset, IT security teams can take action to validate their identity and protect their account from attack.
Reduce Online Fraud by Securing Consumer Accounts
Password spraying and brute force attacks against your consumer accounts takeover can result in fraudulent credit card purchases, warranty fraud, and stolen loyalty points. For your enterprise, consequences can include the costs of financial fraud, increased support demands, and damaged reputation.
SpyCloud helps enterprises protect consumers from account takeover fraud by detecting when consumer passwords have been exposed so enterprises can validate their identities through step-up authentication measures and reset compromised passwords.
Protect Your Enterprise from a Data Breach
When criminals take over victims’ corporate accounts, attackers can gain entry into business email accounts, proprietary databases, and restricted financial applications. The majority of corporate data breaches are a result of an employee’s compromised account exploited through weak or stolen passwords, often accessed using methods like password spraying.
To protect employee accounts from password spraying, SpyCloud enables security teams to detect and reset exposed passwords swiftly to prevent attackers from exploiting them.
Featured Products
Our award-winning products enable you to proactively protect your users’ accounts and thwart online fraud.
Consumer ATO Prevention
Protect your users from account takeover fraud and unauthorized purchases.
Employee ATO Prevention
Protect your organization from breaches and BEC due to password reuse.
Featured Resources
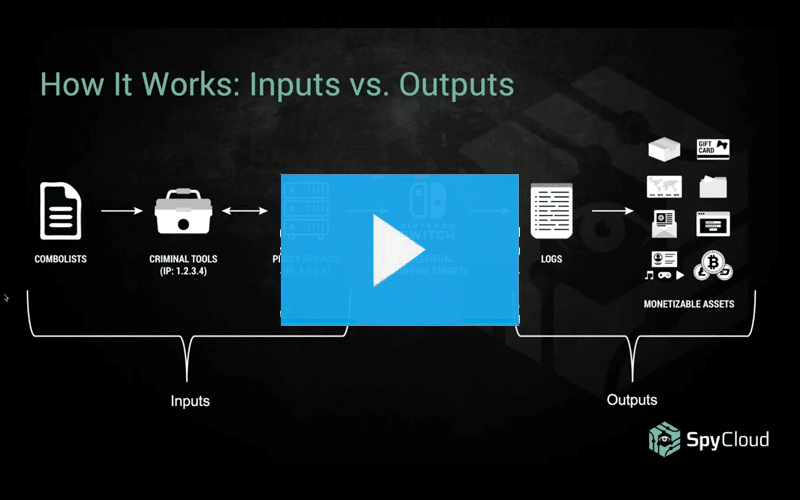
How Credential Stuffing Tools Are Made
Learn how credential stuffing works and get insights into the tools of the trade (including some very sophisticated custom Nintendo crimeware). Discover why stolen accounts that don’t have obvious monetary value can be profitable for cybercriminals.

Credential Stuffing 101
We tap our expertise in helping organizations recover exposed credentials to help you understand the anatomy of credential stuffing attacks, why they persist, and what you can do to prevent them.
