What is account takeover attacks (ATO)
In general, the account takeover definition is the success of a malicious third-party attacker gaining access to a user’s account via stolen credentials for the purpose of fraud. This happens when a bad actor acquires another person’s login credentials, most often by leveraging reused or similar passwords from previously breached sites, and gains access to existing accounts – which may unlock corporate data, sensitive PII, funds, loyalty points and more. Criminals use those stolen assets to commit fraud, make unauthorized purchases, and perpetrate business email compromise (BEC), among other tactics, then eventually package the credentials for sale on the dark web, perpetuating the profit cycle.
The result can be devastating to the victim and to the organization’s reputation, operations, and bottom line.
What is an account takeover (ATO) attack?
Account takeover or ATO fraud attacks can take many forms, but generally come in one of two flavors:
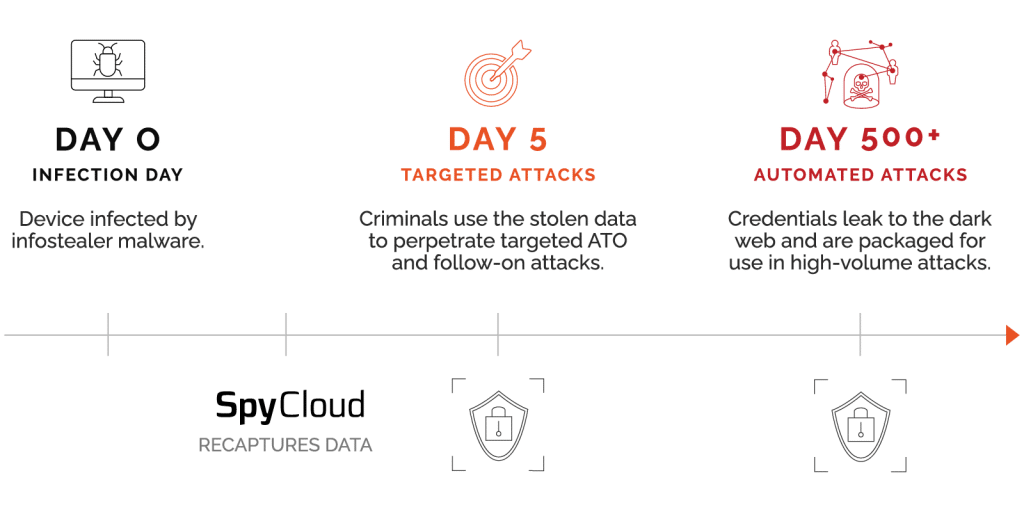
Targeted account takeover attacks
- What: Highly effective, difficult to detect manual attacks like phishing, social engineering, SIM swapping, extortion, blackmail.
- When: Occur early in the breach timeline, usually in the first 18-24 months after the breach. During this time, criminals keep the stolen data within a small group that monetizes the credentials before selling them on the dark web, usually for identity theft purposes.
- Result: Huge potential losses. SpyCloud customers report 80% of their losses stemming from targeted ATO attacks.
Automated credential stuffing attacks
- What: High-volume attacks that use thousands of credential pairings to attempt to login to websites and even exposed endpoints on corporate networks.
- When: Occur long after the breach, when older stolen credentials have been packaged for sale and trade on the dark web.
- Result: A high enough success rate that it remains a popular attack type for even unsophisticated criminals. SpyCloud customers report 20% of their losses stemming from these attacks.
Types of account takeover fraud
The use of stolen credentials is the #1 ATO attack technique. But it’s not just credentials that are leaked in breaches; personally identifiable information is up for grabs and is used for account takeover fraud. In fact, SpyCloud recovered nearly 9B pieces of PII in 2022 alone, which speaks to just how much data is in the hands of criminals via third-party breaches. The account takeover fraud definition is when bad actors gain unauthorized access to online accounts to perpetrate fraud.
What is account takeover fraud and what do criminals do with all that stolen data? Some examples include:
- Drain financial accounts, crypto wallets or loyalty point balances
…where criminals will immediately wire or transfer the balance from victims’ accounts. - Make fraudulent purchases
…where criminals purchase goods using stolen or stored credit card or gift card data. - Create synthetic identities
…where criminals create a new identity with a combination of fake and legitimate (usually stolen) data. Often deployed in long-term scams to obtain lines of credit. - Break into victims’ work accounts
…where criminals will try to locate and steal corporate IP and deploy business email compromise scams, which resulted in $2.4B in losses in 2021 alone. - SIM swap victims to bypass MFA
…where criminals transfer a victim’s phone number to their own SIM card in order to bypass multi-factor authentication and take over sensitive accounts.
How do I know I’ve been a victim of an ATO attack?
One day, you might be suddenly locked out of your account because a bad actor has taken it over and changed the credentials. Or you may notice a strange transaction on a credit card statement – a purchase you didn’t get an email confirmation for because the criminal changed the email address associated with the account to stop you from receiving notifications. These are just some examples of account takeover identity theft.
You might receive an email from your bank or credit card company that says your information has been exposed in a breach. But often, this is months or years after your data has been in criminals’ hands.
The truth is, even the most sophisticated companies and cybersecurity teams may not realize for a long time that they have been breached, putting users’ data at risk. Early detection and continuous monitoring for compromised credentials is key.
Check if your email has been compromised & sign up for free breach monitoring
How to prevent account takeover
Preventing account takeover can’t be done with behavior-based technologies, like bot mitigation, alone. Those solutions are only meant to stop automated account takeover attacks that occur years after the breach takes place using old lists of previously stolen credentials (called “combo lists”).
Truly stopping ATO/account takeover requires identifying compromised accounts early, before criminals have time to use the stolen credentials, test them against other accounts, or sell them on the dark web. The only way to do that is to have access to a comprehensive, constantly updated, real-time database of breach data.