What is Malware?
When it comes to a malware definition, these days malware isn’t just one thing. Broadly, speaking, malware is malicious software that can steal information, damage files and networks, or gain unauthorized access to organizations.
Malware gains access to systems in a variety of ways. From being executed through a phishing attempt in which a bad actor poses as someone else and gets a victim to click a malicious link or download a file, to being distributed through websites and vulnerabilities in software – the threat of malware is growing since the payoff is high.
Infostealer Malware
There are many types of malware, including trojans, viruses, and worms – as well as ransomware, which is a costly and even “game-ending” form of malware for some organizations. But one form of malware we see growing in prevalence is infostealer malware.
An infostealer is part of a malware toolkit that can be easily purchased and enables cybercriminals to exfiltrate target URLs, login credentials, authentication cookies or tokens, autofill data, crypto wallet details, files with specific extensions, chat history, lists of installed programs and running processes, the machine’s globally unique identifier (GUID), and much more from infected devices.
Infostealer malware is typically delivered through phishing emails, malicious websites, and other deceptive tactics. As malware becomes more sophisticated, some forms of malware are able to execute, steal data, and auto-delete in mere seconds.
RedLine, MetaStealer, Raccoon Stealer, and Vidar are just a few popular types of infostealer malware families SpyCloud has observed on the darknet recently.
What is a Malware Log?
When malware exfiltrates data, it creates a log of all the files and information stolen from the infected device. But what is a malware log and what does it include? Malware logs are typically text files that contain everything bad actors need to launch attacks themselves or sell on the darknet for others to use.
Infected user data includes but is not limited to:
Infected machine information
This is a robust set of data about the victim’s device, including the operating system, processing power, processes running, and installed software.
Credentials
Modern infostealers come equipped with modules that are capable of reading the databases used by browsers to store URLs and associated login credentials (username + password combo).
Cookies/tokens
An authentication cookie or token authenticates a session on a given website for a period of time. A still-valid stolen cookie lets a bad actor masquerade as the legitimate user via session hijacking, which enables them to bypass all forms of authentication including multi-factor authentication (MFA) and even passwordless technologies like passkeys without setting off any red flags.
Dangers of Malware
Malware often serves as a precursor to follow-on cyberattacks. Using data exfiltrated by infostealer malware, bad actors can launch attacks including account takeover (ATO), session hijacking, and ransomware on your organization.
The risk of malware affects employees and consumers alike, siphoning authentication data and all forms of personally identifiable information (PII) that bad actors can use to perpetrate online fraud.
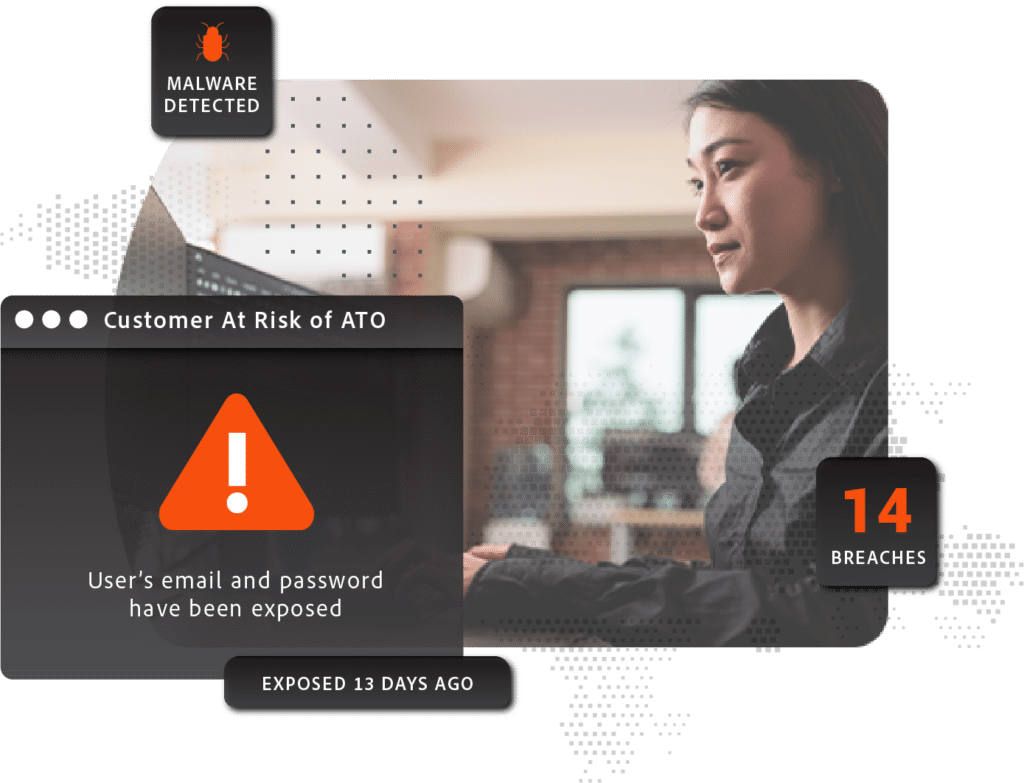
Account Takeover
Account takeover happens when a criminal uses another person’s login credentials to gain access to one of their existing accounts. With plaintext credentials stolen from a malware-infected device, a criminal doesn’t need to do much at all to attempt an account takeover. Once inside the account they can make unauthorized transactions, siphon funds, and steal corporate data or PII to use for other purposes, or simply to sell to other attackers.
Learn more about account takeover.
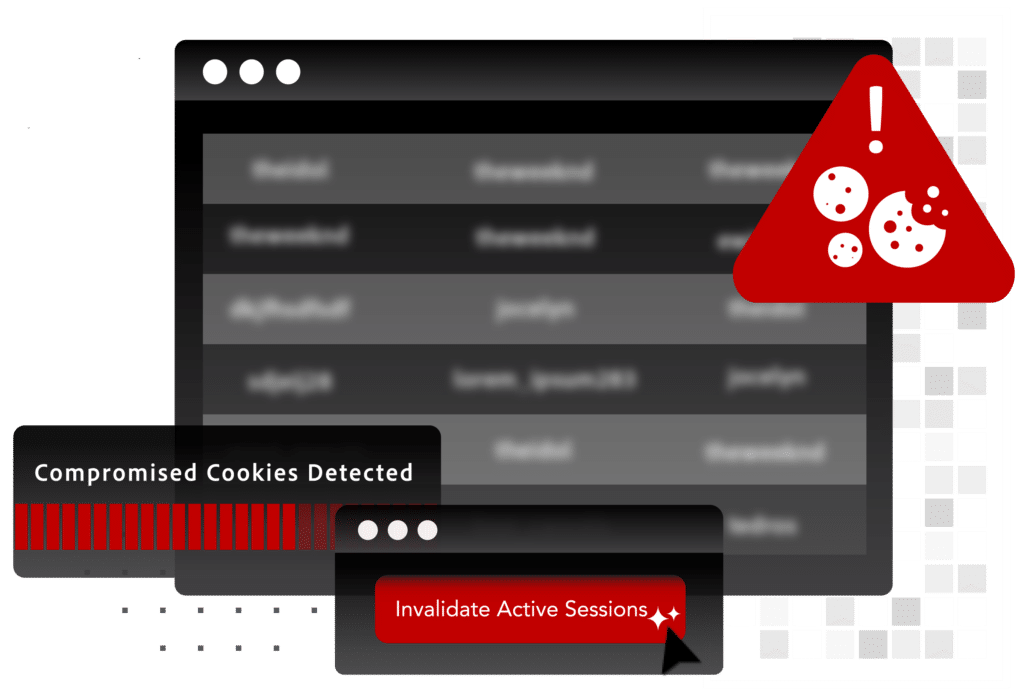
Session Hijacking
Session hijacking or next-generation account takeover occurs when a bad actor accesses a user’s web session using a valid stolen authentication cookie in an anti-detect browser.
This attack enables a criminal to bypass even the most robust authentication measures (passkeys, you are not immune!) to gain access to your network, masquerading as a trusted user. Once inside a corporate account, it’s possible for the actor to escalate privileges, move laterally within the network, and launch ransomware.
We consider these attacks “next-generation account takeover” because they rely on cookies – not traditional login credentials (username + password) – and are the way criminals are bypassing MFA and passwordless authentication. While widely considered safer than passwords, these forms of authentication are not infallible as long as the internet relies on cookies.
Learn more about session hijacking.
Ransomware
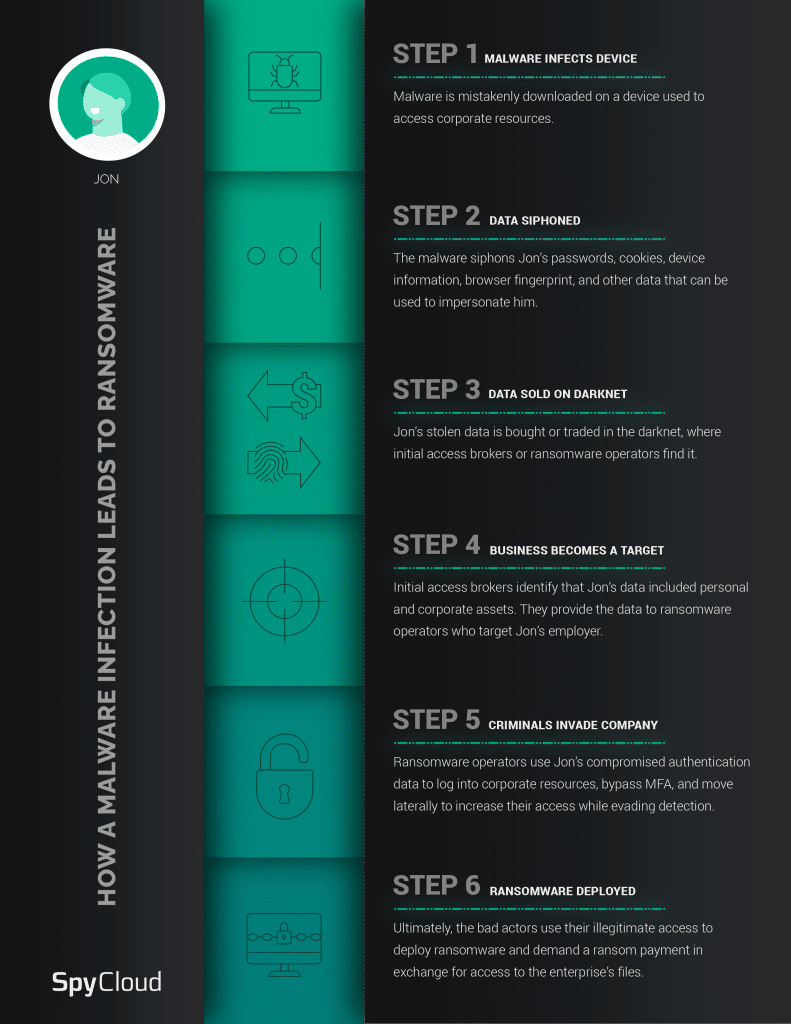
Ransomware remains a top security threat and concern for organizations around the world, with 92% reporting that they were impacted by a ransomware attack last year. One of the easiest ways for bad actors to gain access to your organization and launch ransomware attacks is with login credentials stolen from a malware-infected device. But as we mentioned, criminals are also moving beyond credentials to leverage other forms of access as their new currency. Authentication cookies have opened new doors for bad actors and we’re seeing a shift to malware-exfiltrated data over traditional breach data.
The path from a malware infection to a full-blown ransomware attack is short. Once malware infects a device, the data from that device is siphoned and then quickly used and/or bought or traded on the darknet from initial access brokers to ransomware operators as a form of guaranteed access.
Learn more about ransomware.
Gaps in Malware Infection Response
When understanding “what’s malware” and “what does malware do?”, it’s important to be aware of all the possible ways that malware can exploit gaps in your layered security defenses.
Browser-Based Sync Functionality
Web browsers offer synchronization features that allow users to keep their bookmarks, browser sessions, and passwords available across multiple devices. This user convenience creates a security risk if one of the devices has an infostealer malware infection and is also used to access corporate business applications; the malware can siphon all forms of authentication for all types of accounts, whether personal or work-related.
Unmanaged/Personal Devices
As organizations embrace hybrid and remote-friendly work environments, the lines between business and personal have become blurred – with employees using personal devices to access business applications.
Not all personal devices follow the same security standards that enterprises have in place, which can lead to exposed entry points when employees use these devices to access corporate applications like work email, a sales CRM, or chat programs. Unmanaged or personal device use can quickly expand the attack surface for an organization far beyond their sphere of control.
Under-Managed Devices
Despite increasingly stringent corporate security policies, 40% of employees don’t believe it is their responsibility to update their work device. Corporate devices that are out-of-date for security patches or software updates put the entire enterprise at risk for security incidents.
Furthermore, employees often allow family members to use their work devices for personal matters, and there’s no guarantee that someone will heed warnings about downloading bad files or clicking malicious links while they game, shop, or stream from a corporate device.
Third-Party Vendors and Contractors
Organizations typically depend on a variety of third-party vendors and contractors to do business. However, these businesses might not necessarily employ the same level of security measures and pose a potential risk to those they work with. In fact, 59% of surveyed organizations reported experiencing a breach or cyberattack that originated from a third party.
Third-Party Applications
Businesses run on a variety of tools and applications, spanning password managers, security tools, collaboration apps, CRM and marketing automation platforms, chat, ticketing systems, learning platforms, HR and payroll systems. While these critical applications are necessary for businesses to operate, they also pose a significant risk if accessed by a device infected with infostealer malware. And, if these applications are housed in an SSO instance, one malware infection could expose multiple applications. In fact, according to SpyCloud research, every malware infection exposes an average of 26 third-party applications, creating compounding windows of exposure for an organization.
Shadow IT
In an effort to work more efficiently, employees often use tools or applications that fall outside of corporate security oversight. Using such “shadow IT” tools generates “shadow data” that contributes to the growing attack surface and isn’t managed by regular corporate controls. Credentials and cookies siphoned from these apps by infostealer malware can go undetected, yet they still pose a significant risk despite teams not having visibility that they’re even in use.
Benefits of Automated Malware Protection
Protecting against malicious software in the form of anti-virus programs and endpoint protection is one thing, but reducing the risk that results from a malware infection can’t be ignored. As cybercrime continues to be a lucrative business, malware campaigns against businesses create quick wins for cybercriminals and security teams need to assume malware infections will happen (for all of the above reasons) and have a plan to mitigate the damage from malware-stolen authentication data.
Close Blind Spots in Your Malware Infection Response
Protecting against malicious software in the form of anti-virus programs and endpoint protection is one thing, but reducing the risk that results from a malware infection can’t be ignored. As cybercrime continues to be a lucrative business, malware campaigns against businesses create quick wins for cybercriminals and security teams need to assume malware infections will happen (for all of the above reasons) and have a plan to mitigate the damage from malware-stolen authentication data.
Empower Your SecOps Teams with Actionable Insights
While your SecOps teams work to keep pace with the evolving threat landscape, they are inundated with alerts, some of which are more pressing than others. When it comes to threats like malware infections, your team requires visibility into the attack surface across the entire technology ecosystem to act on malware-compromised devices, users, and applications. Automated solutions that enable action on the highest priority exposures from malware help teams address the most critical issues and free up time and resources to focus on other priorities.
Prevent Cyberattacks on Your Organization
With account takeover, session hijacking, and ransomware all potential threats to your organization, the common denominator is stolen data – whether from data breaches or malware-infected devices. Knowing the risks associated with malware infections and taking swift action to properly and comprehensively remediate the complete scope of an infection can help protect your enterprise from criminals trying to harm your business.
How to Prevent Malware Incidents
A malware attack can be the tip of the iceberg with its potential to turn into a full-blow security incident or cyberattack. Malware prevention and protection is the responsibility of the user and the security team, in partnership. Ensuring that your organization has solid security processes and protocols in place to prevent malware, that your employees and users are maturing in their cyber practices and hygiene, and properly mitigating malware infections is critical to your ability to protect your organization.
Install Anti-Virus Software
Anti-virus software is an obvious way that organizations can prevent malicious software from infecting your network – but it’s not foolproof. While ensuring all employee devices are equipped with anti-virus software is a proactive preventative measure against malware, similar to having MFA in place, anti-virus software is not a silver bullet. In fact, in the first half of 2024, SpyCloud researchers found that at least 54% of malware-infected devices had an antivirus program installed at the time of successful malware execution. Not only did these solutions not prevent the attack, they also lack the automated ability to protect against any stolen data that can be used in the aftermath. So while there is great value, a more layered defense approach is a must for greater risk mitigation.
Keep Operating Systems Up-to-Date
Old versions of operating systems often lack the most current security protocols and can create an entry point into your organization. Making sure all updates are complete and current can help protect against cyber threats like malware.
Beware of Suspicious Emails and Links
Even the most vigilant employees can be overwhelmed and busy, and bad actors are poised to take advantage of this typical human behavior with phishing attempts. Posing as high-level executives, HR or security teams, criminals disseminate malicious links and attachments to unsuspecting victims that can launch malware and wreak havoc on your organization.
Be wary of emails that come from unknown senders. And always validate the origin of a request for a download or a seemingly innocuous web link.
Know Your Darknet Exposure
Awareness of your organization’s exposure on the darknet may be a lesser-known consideration in the prevention of attacks that stem from malware infections. When your corporate data is exposed on the darknet, criminals target your business as an opportunity for cyberattacks.
Check your exposure using SpyCloud’s free tool now to identify threats to your organization like malware-infected employees and stolen cookies.
How to Reduce Risk from Data Exposed by Malware
Typical malware response involves a machine-centric approach focused on the device in which isolating and wiping the device clean is perceived as proper remediation.
In a recent SpyCloud survey of security leaders and practitioners on malware readiness and defense, respondents reported being confident in their abilities to respond at this stage of malware infection response. However, when it comes to ensuring any malware-exfiltrated data such as credentials or active web session cookies are addressed, survey respondents said they were less confident in their capabilities.
An identity-centric approach called Post-Infection Remediation provides a framework that gives SecOps teams the full picture of a malware infection, including the exposed credentials and authentication cookies for business applications that need to be reset and invalidated, respectively.
When a malware infection is detected, the usual steps around isolating the device, identifying the details, creating an image, and removing the malware are necessary – but remediation can’t stop there.
To fully remediate a malware infection, you must define malware response in a more holistic way. In addition to wiping the malware infection from the device, security teams need to also address exposed identity-related components by resetting credentials, invalidating web sessions, and reviewing application integrity to ensure all aspects of an infection are properly handled.
Taking these additional, more comprehensive steps and mitigating exposures related to the identity of the victim slams the door on criminals who are trying to harm your business and negates opportunities for ransomware attacks that can result from data exfiltrated by infostealer malware.
Go Beyond Traditional Threat Intelligence with Advanced Malware Protection
The growing threat of malware reached a fever-pitch last year, with more than 4 billion malware attempts observed last year. Our own research validates the threat: of the thousands of breaches that we recaptured from the darknet last year, 61% came from malware logs.
To truly reduce the risk of data exfiltrated by malware-infected devices, Compass Malware Exposure Remediation gives enterprises full visibility into a malware infection including compromised assets like exposed credentials and authentication cookies that lead to future ransomware attacks.
Compass Malware Exposure Remediation is powered by SpyCloud’s Cybercrime Analytics Engine, which transforms darknet data into actionable insights to proactively mitigate the threat posed by malware infections. This information helps organizations protect themselves before criminals can leverage their stolen data for account takeover, session hijacking, and ransomware.
SpyCloud goes beyond the threat intelligence we know today by enabling enterprises to drive action to protect their business. Our massive repository of billions of recaptured data assets from the darknet has gone through a rigorous process of collection, curation, enrichment, and analysis to surface actionable insights and fuel automated solutions to shut down cyberattacks.
This new way of fighting cybercrime turns the tables on criminals by alerting enterprises of what cybercriminals know about their business and customers and automate remediation to stop bad actors from profiting off of your stolen data.
Let SpyCloud Protect Your Enterprise from the Threat of Malware
Organizations of all sizes are at risk of cyber attacks, and no industry is immune. Preventing attacks that result from malware infections is a critical component of a complete security framework.
Empowered by the knowledge of what criminals know about your business, you can use that information to your advantage. With most of that data coming from breaches and malware-infected devices that ends up on the darknet, taking action to prevent attacks that result from malware infections can help proactively prevent cyber attacks.
However, traditional threat intelligence isn’t enough. As criminals evolve their tactics, enterprises require a new approach to protecting against the threat of malware that leads to account takeover, session hijacking, and ransomware.
The SpyCloud Difference
It’s time for a new way to fight cybercrime – a way that makes darknet data work for you, instead of against you. By incorporating darknet data and insights into your security framework, you can effectively turn the tables on criminals by detecting what data is exposed on the darknet and employing automated solutions to remediate those exposures.
Our customers, including more than half of the Fortune 10, use our solutions every day to disrupt cybercrime and protect their businesses. Organizations from government agencies, financial institutions, ecommerce, technology and security companies trust SpyCloud to partner in protecting their employees, consumers, and bottom line from the impact and dangers of cybercrime.
When it comes to Post-Infection Remediation, only SpyCloud can reveal what bad actors already know about your enterprise from a malware attack and deliver the critical insights you need to take action.
Ready to disrupt cybercrime? Contact us today or request a free demo to see SpyCloud in action.