It’s been another busy month in the security world. In case you missed the buzz, we’re breaking down the latest happenings – from hot topics like Telegram, Operation Magnus, LockBit, and the arrest of USDoD (the actor behind the National Public Data Breach) – to new research from our in-house team of security researchers, SpyCloud Labs.
Some of it’s uplifting (Operation Magnus!), some of it’s slightly depressing (the MC2 breach), and some of it’s just good to know.
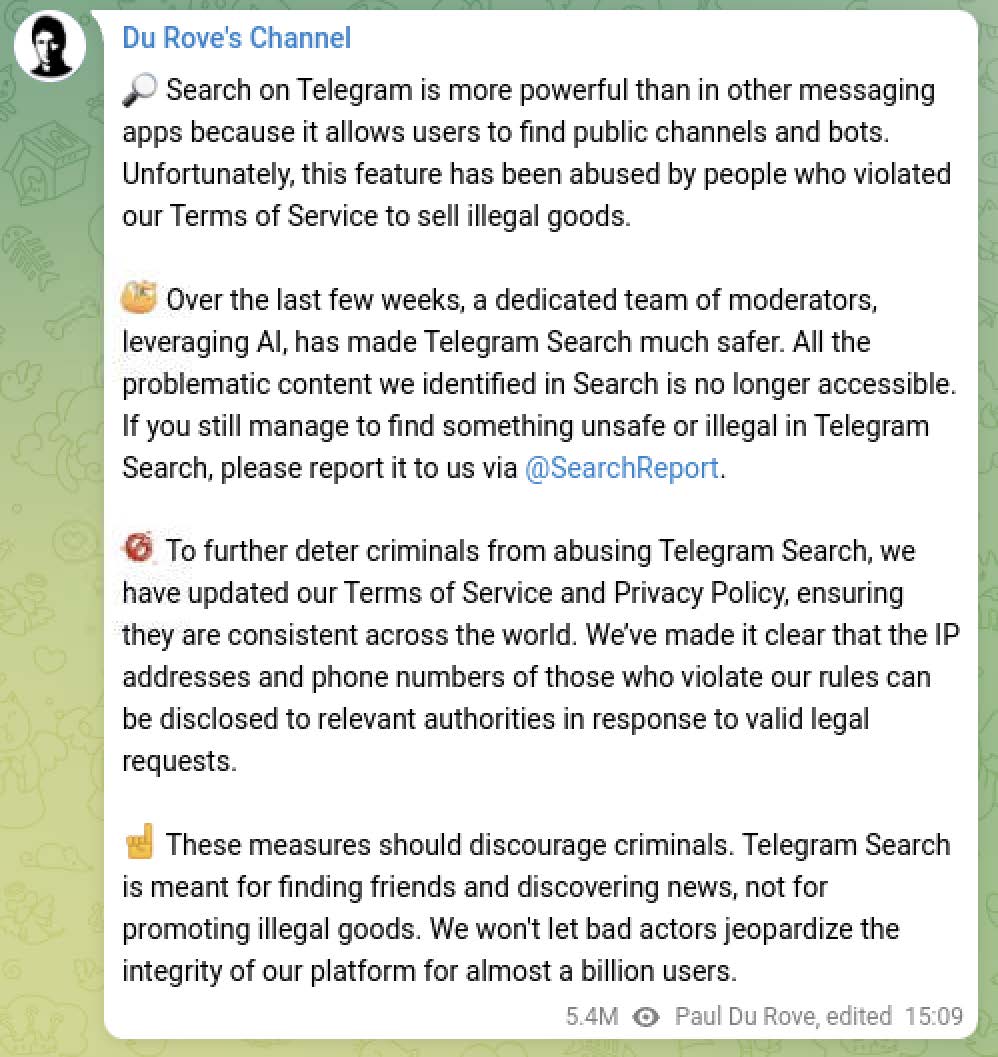
Pavel Durov’s Telegram “crackdown”
In late August, Pavel Durov, the CEO of Telegram, was arrested in Paris for allegedly allowing criminal activity on his platform and not complying with data requests from French law enforcement. In September, Durov announced new measures to increase content moderation of illegal activity on the Telegram platform, ostensibly to appease French authorities.
SpyCloud Labs actively monitors thousands of cybercriminal channels and groups on Telegram, and we have observed an increase in criminal channels and groups being deleted. However, there is still a massive amount of active illicit activity on the platform and Telegram’s “crackdown” still doesn’t appear to be significant enough to push most of the activity that we track to other platforms.
Some observations about this alleged crackdown:
- SpyCloud Labs observed a threefold increase in Telegram’s takedown rate of illicit channels following Durov’s arrest. We compared the average number of Telegram channels actively monitored by SpyCloud that were taken down per day in 2024 before August 24, to the average number that were taken down per day from August 24 to date and observed an 312% increase in the rate of channel deletion.
- In particular, a large number of the illicit channels we have observed being removed from Telegram over the past couple of months appear to center around credit card theft, including channels named with keywords such as: CVV, CC, scrapper, and carder. Other trends for topics that we noticed in the names of recently banned channels include sim swapping and credential combolists.
- We have observed actors discussing contingency plans for moving off of the Telegram platform, but are yet to see a concerted migration off the platform. Some alternatives that we have observed threat actors discussing include Signal, TamTam, Discord, and Meta’s Threads (see more below).
- In a few instances, we have observed cybercriminal Telegram channels with a large number of followers that have created Signal chats and encouraged their Telegram followers to migrate. However, in each of these cases, only a tiny fraction of the Telegram followers appear to have joined these new Signal channels. Channel administrators have continued to post primarily to Telegram and not their newly created Signal channels, which have become effectively dead.
- On October 8, the Russian government blocked the instant messaging platform Discord, making it marginally more difficult for the expansive Russian cybercriminal community to potentially migrate activity from Telegram to Discord.
While Telegram does appear to be slightly ramping up their content moderation of illegal activity in the wake of Durov’s arrest, it will likely require a much more concerted effort to drive most illegal activity off of their platform. Telegram’s extensive features for channel administration, easy-to-use bot features, general reputation as a safe haven for illicit activity, and large existing user community of fraudsters and cyber threat actors continue to make it an attractive platform for cybercriminals. Unless Telegram undertakes a much more concerted effort to crack down on this activity, we anticipate that there will not be a mass migration of these groups off of the platform.
Operation Magnus disrupts RedLine and Meta infostealers
On October 28, the Dutch National Police announced that they had disrupted the infrastructure of the RedLine and Meta infostealers. The disruption was conducted as part of international law enforcement Operation Magnus. To announce the disruption, the Dutch National Police created an Operation Magnus website with a video about the operation humorously announcing the “final update” to the stealers, a link to an Operation Magnus Telegram account where individuals can contact the law enforcement teams working on this operation, and a countdown clock to another announcement.
RedLine continues to be the most prolific stealer malware that we track; we have ingested data from over 11 million RedLine infections since SpyCloud began collecting infostealer malware data almost a decade ago. MetaStealer is a newer and improved version of RedLine that was created and sold by the same threat actors starting in 2022. It remains to be seen how these actions will affect the overall ecosystem for RedLine and MetaStealer, however this appears – at least initially – to have dealt a blow to their current operations.
Anonymous Sudan indicted
On October 16, the DOJ announced charges against two Sudanese nationals, Ahmed Salah Yousif Omer and Alaa Salah Yusuuf Omer, who led Anonymous Sudan, a cybercriminal group that conducted DDoS attacks against a range of targets in the US and internationally. They also developed a DDoS tool which was sold to other criminal actors to use in their own attacks. These attacks caused significant disruptions to the availability of thousands of websites including the websites of critical infrastructure entities, government agencies, and hospitals.
SpyCloud was thanked by the DOJ in their announcement, along with other private sector companies, for our assistance to Operation PowerOFF, an ongoing international law enforcement effort to dismantle criminal DDoS-for-hire infrastructure.
USDoD arrested in Brazil
The individual behind the screen name USDoD was arrested by Brazilian authorities on October 16. USDoD, the online persona of 33-year old Brazilian man Luan BG, was best known for leaking data from the FBI’s Infragard data-sharing program as well as publishing the National Public Data breach which exposed the personal information and social security numbers of millions of US persons earlier this year.
USDoD was a prolific poster to BreachForums, a popular English-language data leak website and the successor to RaidForums. The FBI and international law enforcement partners have taken multiple actions to shut down BreachForums since it was started in 2022. Last year, they arrested the site’s original creator Conor Brian Fitzpatrick (a.k.a. pompompurin), and they seized the website in 2023 and again in May 2024. While the forum has gone through a few different iterations and administrators since 2022, BreachForums continues to operate as a central forum for sharing and selling breached data.
Operation Cronos continues & Evil Corp sanctioned:
On October 1, Europol announced additional actions taken against LockBit operators and infrastructure as part of the ongoing international law enforcement campaign against LockBit – Operation Cronos. Four individuals were arrested including:
- A LockBit developer who was arrested by French authorities while vacationing outside of Russia,
- Two LockBit affiliates in the UK, and
- The administrator of a bulletproof hosting service used by LockBit who was arrested along with the seizure of nine servers.
That same day, the US, UK, and Australia jointly announced a series of new sanctions against various members of the Russian cybercrime syndicate Evil Corp. The US DOJ also unsealed charges against Aleksandr Ryzhenkov, one of the individuals affiliated with Evil Corp, for his use of the BitPaymer ransomware variant to attack and extort US companies. Evil Corp has been active since at least 2009 in a variety of cybercriminal schemes including:
- The development of the Zeus and Dridex malware variants, which started as banking trojans and evolved into having additional capabilities over time such as loader and stealer components
- The development and use of multiple ransomware variants including Macaw, Phoenix, Hades, WastedLocker, and DoppelPaymer; researchers believe that the frequent rebranding of their ransomware offerings was likely in an attempt to confuse authorities and avoid the sanctions on Evil Corp
- The development of the Zeus and Dridex malware variants, which started as banking trojans and evolved into having additional capabilities over time such as loader and stealer components
- The development and use of multiple ransomware variants including Macaw, Phoenix, Hades, WastedLocker, and DoppelPaymer; researchers believe that the frequent rebranding of their ransomware offerings was likely in an attempt to confuse authorities and avoid the sanctions on Evil Corp
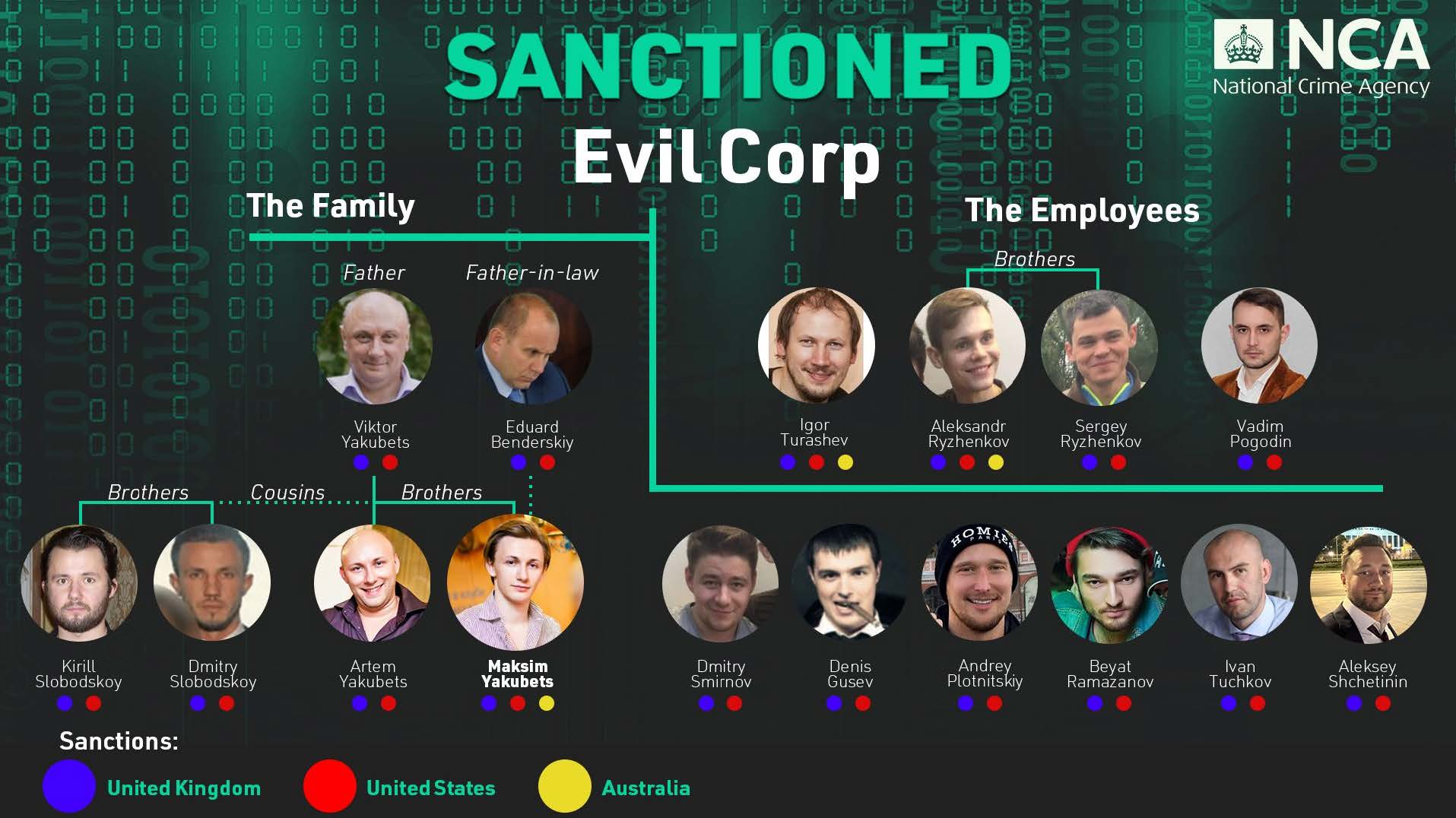
Graphic from the NCA showing down the familial relationships between sanctioned members of the Evil Corp cybercrime syndicate. The diagram also breaks down which individuals were sanctioned by which countries.
TL;DR of new SpyCloud Labs research
Google rolled out Application-Bound Encryption in July to limit access to encrypted browser cookie data on Windows to just the Chrome application. While the feature release temporarily resulted in several stealer families stopping their distribution, SpyCloud soon saw actors claiming they had bypassed the new Chrome security feature.
On October 2, we published research based on reverse-engineering the bypass deployed in Phemedrone, an open-source infostealer, which showed that infostealer developers could bypass App-Bound Encryption by using Chrome’s internal API – intended for remote management and testing. After enabling remote debugging over a specified port, an authenticated user is able to dump all cookies in plaintext.
While we have not specifically examined the means by which other malware families have bypassed the new App-Bound Encryption feature, based on our review of the remote management API, it is likely that other malware is making use of the same method. Notably, all major infostealer families have announced a bypass capability as of October 2024.
On September 25, news outlets reported a large data breach affecting MC2 Data, a company that offers background check services. SpyCloud Labs recaptured and analyzed the data, which included both user account data from customers of MC2’s services, as well as public records data on US persons who were looked up through one of MC2’s services.
The user account data includes customer names, email addresses, hashed passwords, phone numbers, IP addresses, device and browser information, and payment information. The public records data on individual US persons looked up using MC2’s services is even more extensive, and includes data on individuals ranging from basic PII like names and birthdates to in-depth background information like criminal history, financial records, and information on family members and known associates. Interestingly, we noticed that at least a portion of the public records data in the breach appears to have been obtained through a third party data intelligence provider Enformion using one of their APIs.
The MC2 data breach also came about a month after a similar data leak from another background check surface, National Public Data, was posted publicly to BreachForums. Both breaches affected background check companies that stored data on US persons, many of whom never directly interacted with NPD or MC2, but whose data was stored by these companies in the service of supplying data for background checks and people lookups.
While the MC2 leak contains fewer total records than the NPD breach, those records – particularly the data on individuals investigated through the service – contain a significantly greater level of detail and variety of data asset types.
SpyCloud Labs is continually researching Chinese-language criminal hacking communities and dark marketplaces for breached and leaked data. This month, we published our second deep dive into this topic, which takes a closer look at three Chinese crime TTPs:
- SDKs: China-based criminal actors trojanize existing SDKs or create new malware ones that inject malicious code into applications. When app developers use these SDKs, threat actors are able to directly exfiltrate user data, sometimes with or without the developers knowledge.
- DPI (三网数据) data collection method: Threat actors use insider access to telecommunications provider infrastructure at the big three Chinese telecommunications companies to monitor user browsing behavior. They then resell this information in gray and dark marketplaces.
- Social Work Library (SGK 社工库): This database is a repository of leaked PII, created by Chinese-language threat actors that compile hacked and leaked databases. These libraries generally contain basic information on individuals, but may also contain additional PII like places of residence, places of work, business trips, places of travel, income level, and other behavioral data.
In an analysis of stealer logs from the past thirty days, we found the highest number of logs for LummaC2, a stealer and loader malware variant that has increasingly caused trouble since 2022. But when we ran a comparison of the past thirty days of data against our entire dataset, we found that – overall – legacy malware families still lead by a large margin when it comes to infection counts. RedLine Stealer is responsible for the highest number of unique infection logs by far, with 11+ million total RedLine logs in our recaptured data lake.
Current and forthcoming cybercrime research
Recapturing phishing data
Earlier this year, SpyCloud Labs expanded our efforts to recapture breached, leaked, and stolen data by collecting data from phishing pages and phishing kits. This month, we ingested records from two related phishing-as-a-service (PhaaS) platforms: Caffeine and ONNX.
Phishing kit analysis: Caffeine & ONNX PhaaS Data
Caffeine was a PhaaS platform that was active beginning in 2022. It offered a user-friendly dashboard and a full suite of tools to conduct phishing campaigns, including more advanced features like dynamically generated pages with pre-populated victim information. As Mandiant reported at the time, Caffeine was “somewhat unique in that it [featured] an entirely open registration process, allowing just about anyone with an email to register for their services” instead of requiring direct outreach to the admin or a vouch from an existing customer. This made it extremely easy to procure, set up, and use.
In 2024, researchers discovered that Caffeine had been revised and rebranded as ONNX, which is operated by the same persona: MRxC0DER. ONNX offers many of the same features, as well as some exciting new ones, like a feature to distribute malicious links through QR codes embedded in PDF documents, a feature to capture and test 2FA codes in real time, and the use of Cloudflare anti-bot CAPTCHA to delay the detection and takedown of phishing pages. The ONNX store has gone dark for the past few months, potentially as a result of researchers revealing the identity of MRxC0DER in June as an Egyptian man named Abanoub Nady. Using SpyCloud Investigations, we can independently reproduce the pivots that Dark Atlas made to link the MRxC0DER identity to Abanoub Nady.
SpyCloud has recaptured over 1.7 million phished records between ONNX and Caffeine, and continues to monitor developments in similar PhaaS platforms.
Screenshot of an initial phishing landing page crafted with ONNX. It shows the use of Cloudflare’s legitimate anti-bot CAPTCHA service. It also contains a Microsoft logo and the Outlook blue envelope logo, indicating that this page is intended to phish Microsoft Outlook account credentials from victims.
Stolen credit card data on Threads
In early September, SpyCloud Labs discovered some accounts on Meta’s Threads platform posting full stolen credit card data. While scrolling through the newsfeed on their personal Threads account, a SpyCloud Labs researcher saw a post from an account they didn’t follow containing what appeared to be someone’s full stolen credit card information. After clicking on this post, their feed became filled with similar posts containing stolen card information.
We continued to dig into this phenomenon and have since found dozens of large Threads accounts, some with as many as 12,000 followers, posting full stolen credit and debit card data along with other PII.
These posts include things like:
- Card holder full names
- Full and partial credit card numbers
- SSNs
- CVVs
- Bin numbers
- Pin numbers
- Addresses
- Birth dates
- Associated bank name and/or credit card lender names
- Credit card amounts
- Expiration dates
- IP addresses
- Phone numbers
- Email addresses
- Passwords
In some instances, we found posts using Threads’ poll feature to drive engagement and crowdsource whether or not card details are valid. For example, an actor might post the details of a stolen credit card, along with two poll options so users can give feedback on whether or not the card details worked for them such as “Worked fine” for a successful transaction or account opening or “Declined | Post more” to prompt the account to post more cards.
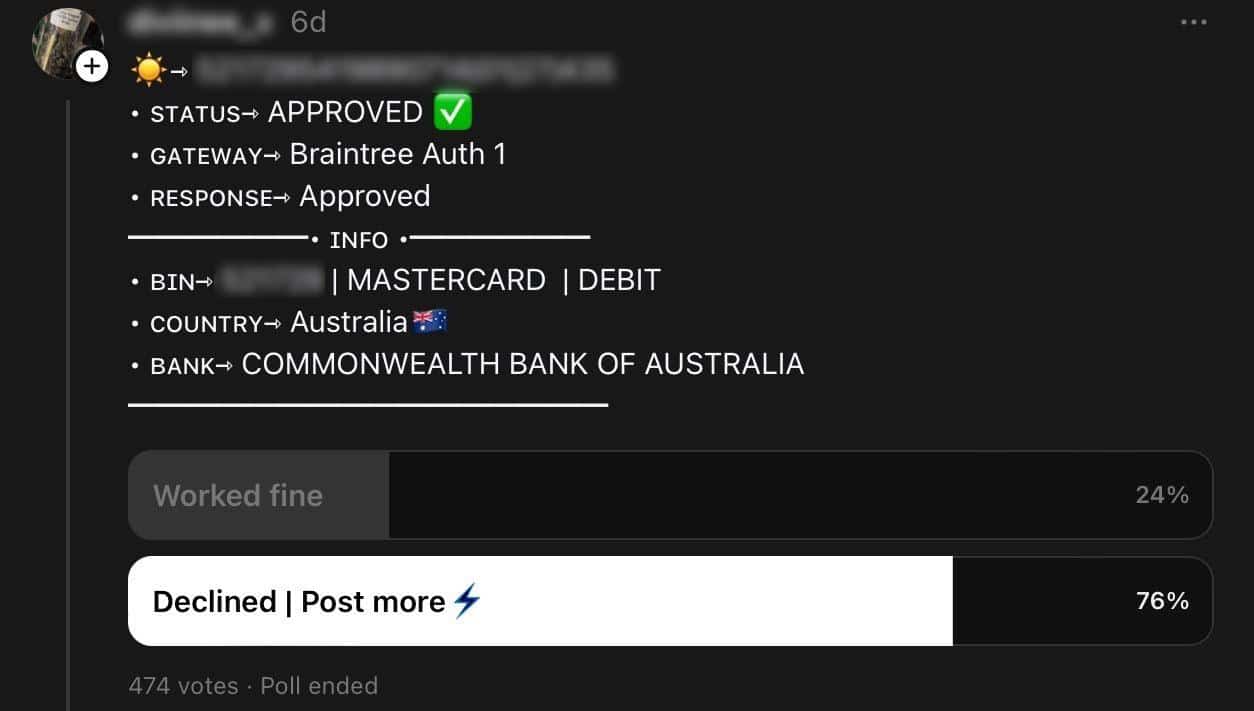
Screenshot of a Threads post containing stolen card information along with a poll prompting users to select whether the associated debit card details worked for them. The account user appears to be using the Threads poll feature to crowdsource whether or not stolen card details are still working. Engagement with the poll likely also boosts the post’s visibility to other users. The poll has over 400 responses at the time of observation.
Additionally, we have come across anecdotes of other people stumbling upon this data without seeking it out – and even (as you can see in the screenshot on this Reddit post) without visiting the Threads platform. In the Reddit post linked above, the poster explains that they saw multiple stolen credit cards Threads posts served to them in their Instagram feed via the Threads integration with Instagram.
We also found some other Reddit posts (like this one and this one) from people who downloaded Threads for the first time and immediately started seeing posts with stolen cards in their feeds without seeking them out. Stolen credit card data doesn’t only exist on the Threads platform, it appears to be heavily promoted by the Threads algorithm.
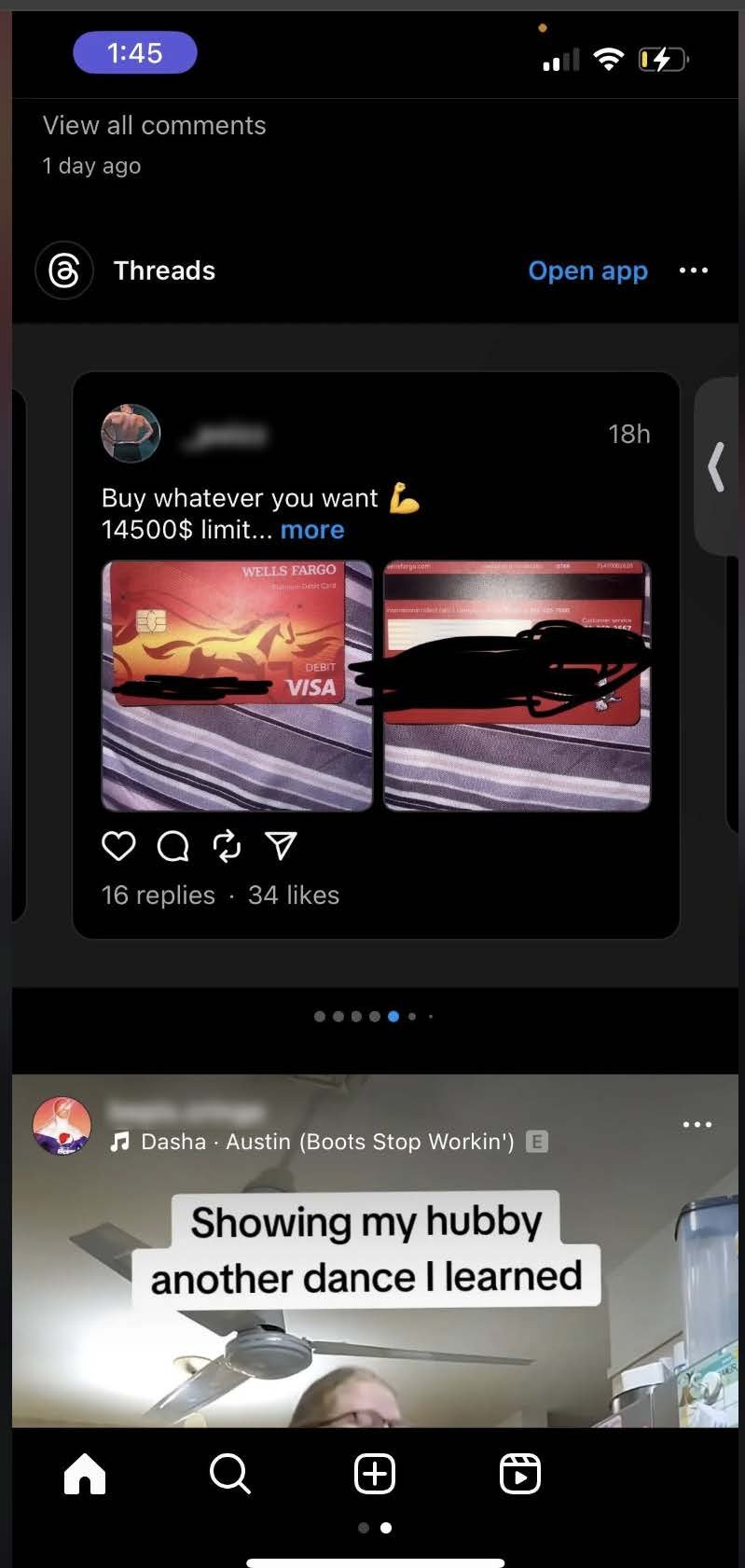
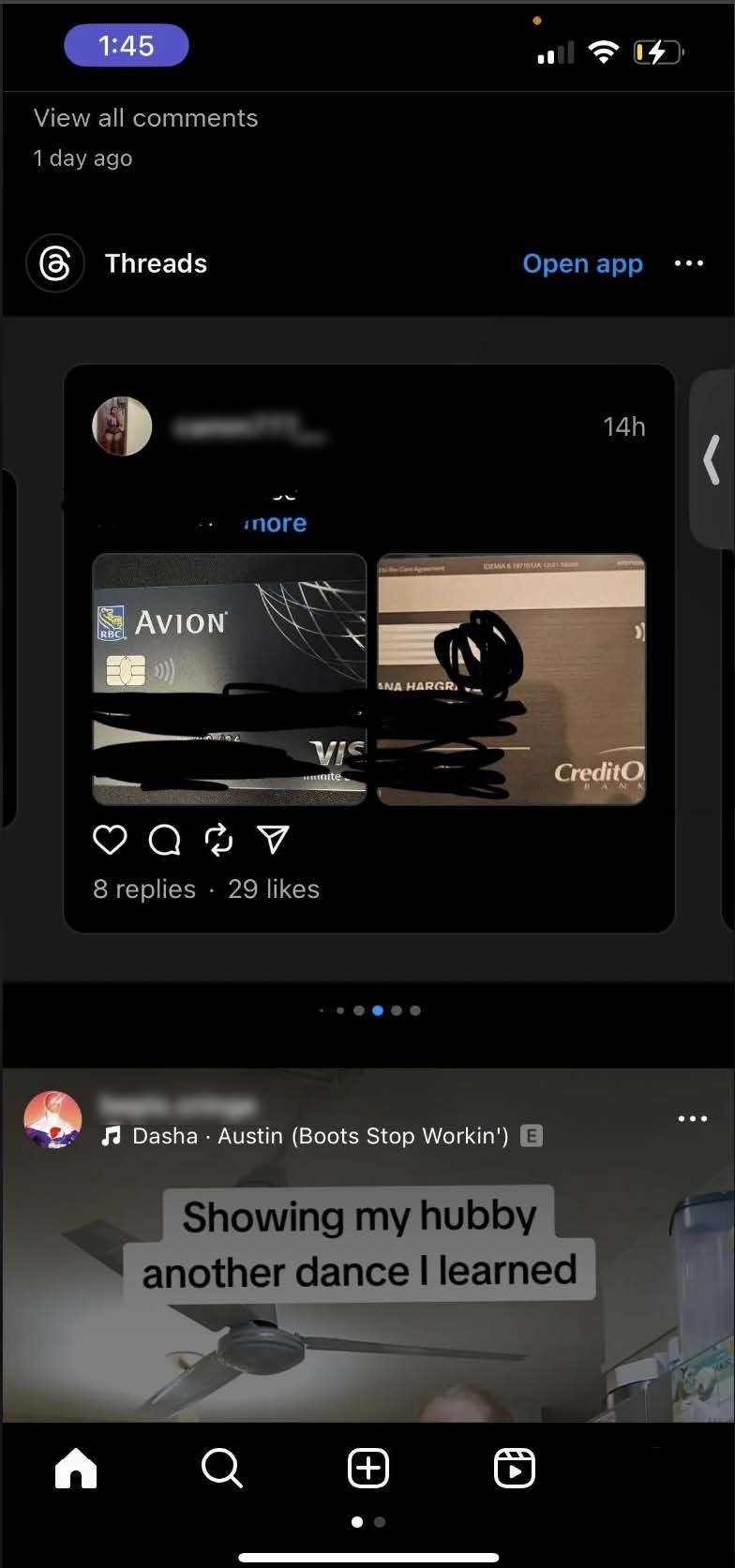
Screenshots from a Reddit user showing Threads posts containing photos of stolen credit cards served to them in their Instagram feed.
As a note: Many of the accounts we discovered have creation dates in late September and early October, but already have large followings. One particularly large account that we are tracking has 12.4K followers; the account’s bio contains a link back to a Telegram channel with an even larger number of members. This Threads account was created on September 28, five days after Pavel Durov’s post stating that his team had “made Telegram Search much safer” by removing content from users trying to “sell illegal goods.”
We can’t draw a direct correlation between this activity and the increased scrutiny on illicit activity on Telegram following Pavel Durov’s arrest. However, it is certainly interesting that we stumbled upon this activity on Threads in September, right around the time of Durov’s announcements that they would be increasing Telegram’s content moderation efforts and cooperation with law enforcement requests. If Telegram continues to crack down on illegal activity on their platform, more actors might turn to Threads to advertise their stolen credit card offerings.
SpyCloud’s recaptured data collection numbers
SpyCloud detects when employee and customer credentials, cookies, PII, and other critical stolen assets are in the hands of cybercriminals and so you can reduce your risk of cyberattacks.
We rigorously cleanse and parse billions of stolen data assets every month from data breaches, malware-infected devices, and successful phishes – then crack passwords, further enrich the data, and correlate it to individual user identities so you can see and stop threats to your enterprise.
October Monthly Total
Note: Each recaptured record corresponds to an average of approximately seven data assets.
Total New Recaptured Data Records for October:
1,028,774,011
New Third-Party Breach Data this Month
Third-Party Breaches Parsed and Ingested:
319
New Data Records from Third-Party Breaches:
72,234,559
New Infostealer Malware Data this Month
Stealer Logs Parsed and Ingested:
360,330
New Data Records from Stealer Infections:
17,967,556
New Stolen Cookie Records
938,571,896
New Stealer Families: This month, SpyCloud began monitoring a new infostealer being discussed by threat actors: Vega Stealer. We also identified apparent source code for Vega Stealer on GitHub, written in Python. As of the time of this writing, we have yet to see Vega logs being shared or sold, but will continue to monitor for stolen data obtained through Vega Stealer infections. Note: There was a different stealer called Vega Stealer which was observed back in 2018, however this ‘old’ Vega was written in .NET and doesn’t appear to bear strong similarities to the new Vega Stealer.
Get the latest research
Sign up to receive regular updates from SpyCloud, including new cybercrime research, product update and security resources.