Another year, another breakdown of incidents and breaches in the 16th annual Verizon 2023 Data Breach Investigations Report (DBIR). This year they took us back to basics in their analysis of 5,199 data breaches taking place between November 2021 and Oct 2022 and the actions leading to them. In many ways, this year’s report bubbled up similar headlines as in years past: credentials are king, ransomware is consistent, and human error continues to prevail.
Let’s dig into key takeaways from the report, including the usual suspects and a conspicuous miss, in our opinion. Plus we shed a little light on things we’re still curious about after the full 89-page report.
No Surprises Here: Credentials are a Criminal’s Best Friend
We said it last year in our analysis of the DBIR and we could just as easily say it again this year: “The more things change, the more they stay the same.” The use of stolen credentials remains the #1 way criminals gain access to organizations – continuing its reign as the top action variety in 44.7% of breaches. And when it comes to basic web application attacks, which make up 25% of breaches, unsurprisingly 86% of those involved the use of stolen credentials.
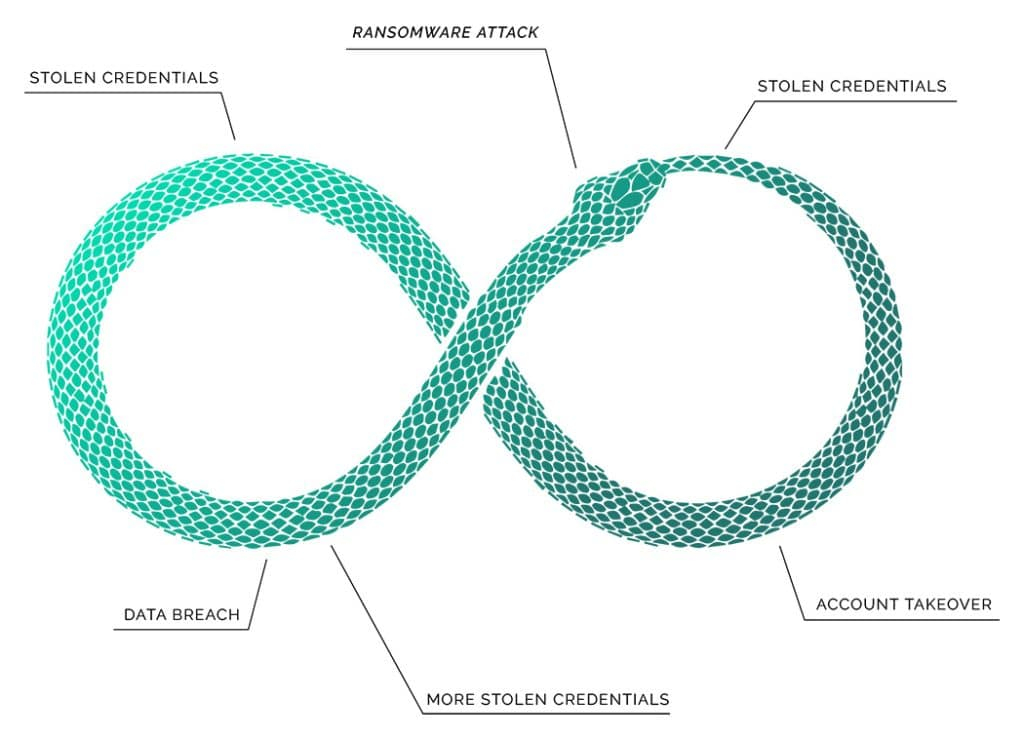
Credentials fuel account takeover (ATO) attacks, which serve as a precursor to breaches and ransomware attacks, which expose credentials that fuel further attacks, and on and on.
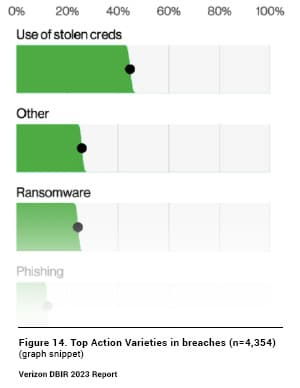
Source: Verizon 2023 Data Breach Investigations Report, pg. 14
The vicious cycle of stolen credentials is that even if a cybercriminal has only one, they can leverage that for ongoing cyberattacks to gain more credentials, creating an infinite, dangerous exposure of data and access that feeds itself.
But our own research has shown a shift in how bad actors are stealing credentials these days. Last year alone, SpyCloud recaptured 721 million credentials from the criminal underground, 48.5% of which were initially exfiltrated from infostealer-infected devices. Infostealer malware is playing a more prominent role in criminal activities than ever before. This malware quickly steals authentication data including usernames and passwords combos as well as session cookies for websites the victim has visited, along with system and device data that enables easy impersonation. Username/password combos (aka traditional credentials) are still a hot commodity on criminal forums, but many consider authentication cookies the ultimate prize. Attackers can import valid stolen cookies into readily available anti-detect browsers to hijack a session – bypassing the need for credentials altogether, including multi-factor authentication (MFA).
With the rise in passwordless authentication methods like passkeys, we see a corresponding rise in the use of stolen cookies to circumvent these methods. We were surprised that cookies and session hijacking didn’t have more prominence in the Verizon report, but perhaps there will be more on this front next year.
Ransomware Looms, and Persists
Last year’s report revealed a shocking ransomware statistic: in 2022, Verizon reported an almost 13% increase in ransomware, with it being present in 25% of breaches – a jump as big as the previous five years combined. This year, however, ransomware appeared to stay statistically steady, involved in just under a quarter (24%) of breaches. And, at risk of sounding like a broken record, the report reiterates that no organization is immune to ransomware, no matter the size, industry, or geographic location. Email continues to remain a top delivery method for ransomware/malware, as shown in Figure 30 from the report.
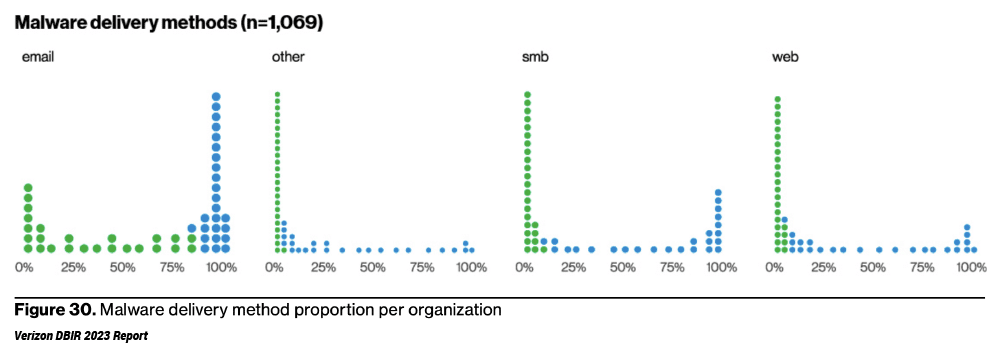
Source: Verizon 2023 Data Breach Investigations Report, pg. 26
The ransomware and compromised credential connection remains the same: ransomware only succeeds when bad actors gain access to your systems, and the easiest way to gain unauthorized access is to use stolen login credentials – or as we said above, stolen cookies. Typically, the ransomware operator obtains these credentials through an initial access broker, who purchased or stole them, and provides guaranteed access to the operator for a fee. As ransomware continues to wreak havoc on organizations, the sources of stolen authentication data cannot be ignored.
The Tangled Web We Weave
Organizations depend on cloud and web-based applications to conduct business, including email and office applications, SSO, hosting environments, customer relationship managers, payroll apps, video conference platforms, and the list goes on. According to the report, web applications are the top asset affected in breaches (affected in 60% of breaches). Since these apps are necessary for doing business, enterprises should take all precautions to secure them because they are clearly so valuable to attackers.
This information piqued our interest, as our recent analysis of the darknet exposure of Fortune 1000 companies included a new data point: the number of exposed credentials from corporate web applications associated with Fortune 1000 employees. We recaptured a total of 223,098 exposed credential sets facilitating access to 56,006 cloud-based applications used by Fortune 1000 employees. These app exposures are typically a blind spot for security teams but when exposed, create yet another entry point into the organization.
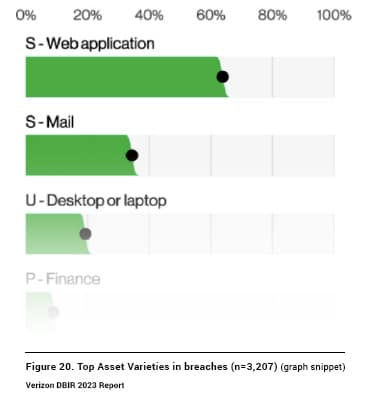
Source: Verizon 2023 Data Breach Investigations Report, pg. 18
When Private Information Goes Public
Verizon observed personally identifiable information (PII) as the top confidential data type found in breaches. While credentials comes in a close second on this chart, we’d be remiss if we didn’t pay attention to the impacts of exposed PII.
SpyCloud is no stranger to PII and how it is used to perpetrate online fraud. We recaptured 8.6 billion PII assets last year, including names, birthdates, addresses, phone numbers, national identification numbers, bank account information, and credit cards – all information leaked in breaches that enables fraudsters to find new, creative ways of monetizing the stolen data. One such way is creating synthetic identities by piecing together personal information from multiple sources, with which fraudsters open new accounts, apply for credit, make big purchases, or do anything else that might establish these identities as real people.
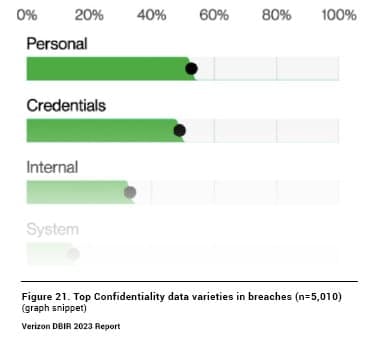
Source: Verizon 2023 Data Breach Investigations Report, pg. 19
My (Not So) Favorite Mistake: The Impact of Human Error on Breaches
This year, the human element made a significant impact on breaches: “74% of all breaches include the human element, with people being involved either via Error, Privilege Misuse, Use of stolen credentials or Social Engineering.” More specifically, Social Engineering incidents including phishing and pretexting were on the rise, accounting for 17% of breaches, with email the top method for criminals trick victims.
One social engineering tactic that is prevalent but not always as prominent in the spotlight is Business Email Compromise (BEC). However, BEC has been making headlines again recently with the most recent FBI IC3 report showing an uptick in BEC-related complaints and losses – 21,832 complaints received, totaling $2.7 billion in losses in 2022. The DBIR featured some intriguing statistics on this social engineering attack as well.
According to Verizon, BEC incidents have almost doubled in Verizon’s entire incident dataset, with pretexting overtaking phishing as the most prevalent social engineering tactic this year.
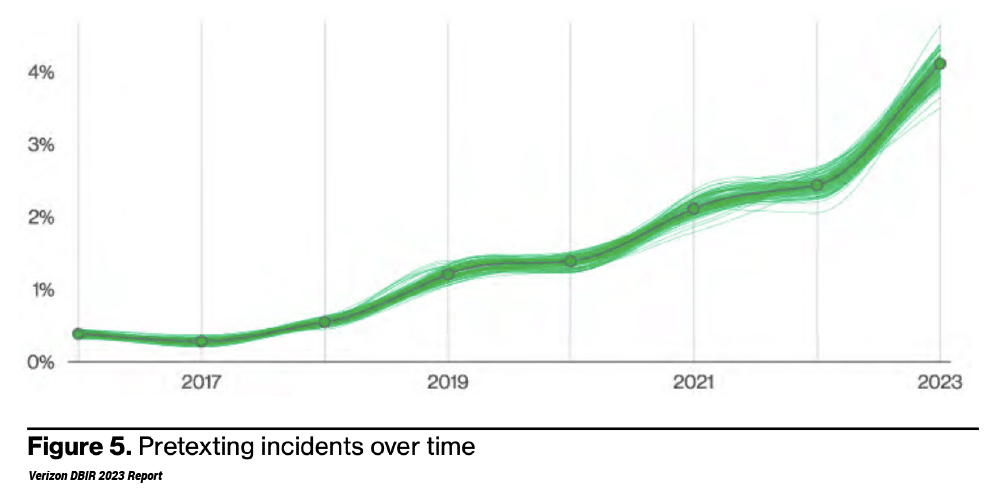
Source: Verizon 2023 Data Breach Investigations Report, pg. 8
These types of incidents take advantage of human behavior and create a false sense of urgency for the victim. And as with other attack vectors, SpyCloud has observed criminals are getting more sophisticated in how they evade detection via BEC: buying residential IP addresses exfiltrated by infostealer malware to make their origin attempts appear legitimate, which could be a contributing factor to the increase in BEC incidents reported by Verizon.
Say It Louder for Those in the Back: MFA is Not Infallible
While the report included several nods to MFA as a deterrent, we do want to reiterate the report’s point that MFA is not a silver bullet. Of course it adds a layer of defense to further enhance account security, but MFA prompt bombing is just one example of how it can be defeated by persistent attackers.
Verizon discussed MFA bypass in the report and even updated their Vocabulary for Event Recording and Incident Sharing (VERIS) framework to capture attacks that bypass MFA. On our minds is how the report may morph next year to include session hijacking as a method of MFA bypass and potentially an action variety leading to breaches.
Focus on the Future: Evolve the Definition of Credentials as Criminals Evolve Breach Tactics
If you read our 2024 Annual Identity Exposure Report, you know our stance that credentials in the traditional username + password sense aren’t the only way criminals gain access to organizations. With the abundance of malware-exfiltrated authentication cookies available on the darknet (we recaptured 22 billion last year alone), criminals are leaning into session hijacking as a way to get around the need for passwords, and even passkeys. Yes, the passwordless authentication method du jour is vulnerable to attack. Malware-exfiltrated data is highly accurate and very effective in enabling cybercriminals to hijack web sessions and impersonate an individual online, allowing bad actors to masquerade as a legitimate user with readily available tools like anti-detect browsers.
While the report offers a valuable lookback, we’re interested to see what’s to come. We expect next year’s Verizon report to delve into authentication cookies as a credential type. Frankly, a credential is a catch-all for the possible authentication entry points into a given account, and though this year’s report focuses on passwords, next year we may be talking about cookies and even passkeys. As criminals take to next-generation ways to breach organizations via session hijacking and using stolen passkeys (malware variants are already stealing passkeys) as a way in, we’re curious to see what next year’s analysis presents.
Find out what cybercriminals know about your business.
Use SpyCloud’s Check Your Exposure tool to get insights on your corporate darknet exposure, including exposed credentials and stolen web session cookies that can be used to launch cyber attacks on your organization.