Protect Against Credential Stuffing and Account Takeover with SpyCloud
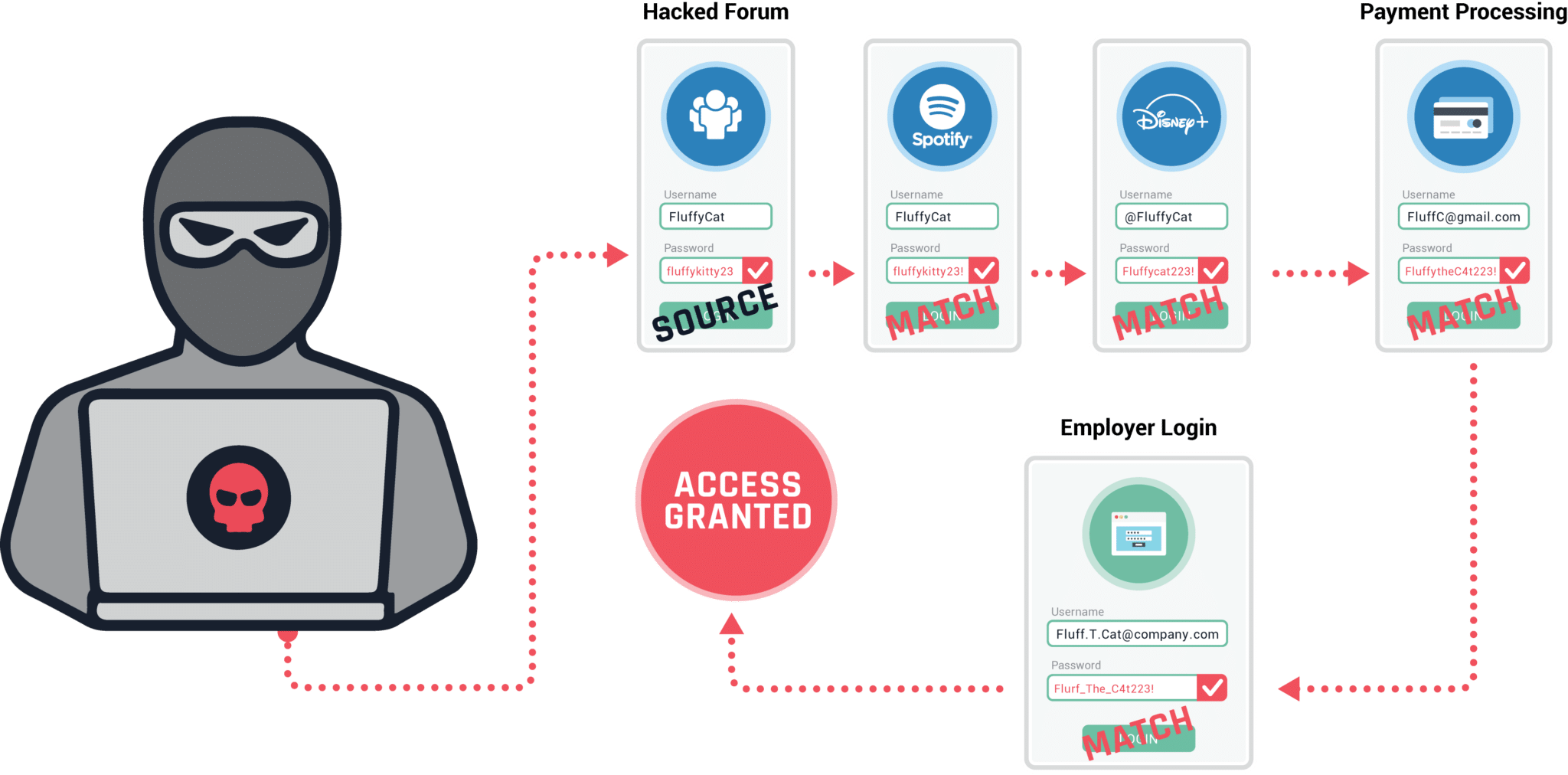
Criminals frequently take advantage of reused passwords, exploiting credentials that have appeared in third-party data breaches to access corporate and consumer accounts. In credential stuffing attacks, criminals automate their account takeover attempts by using account checker tools to test thousands of stolen passwords at once.
SpyCloud helps organizations combat not only automated credential stuffing attacks, but also the high-cost, specialized attacks that happen well before breach data becomes available to a broad criminal audience on the deep and dark web.
How Credential Stuffing Works
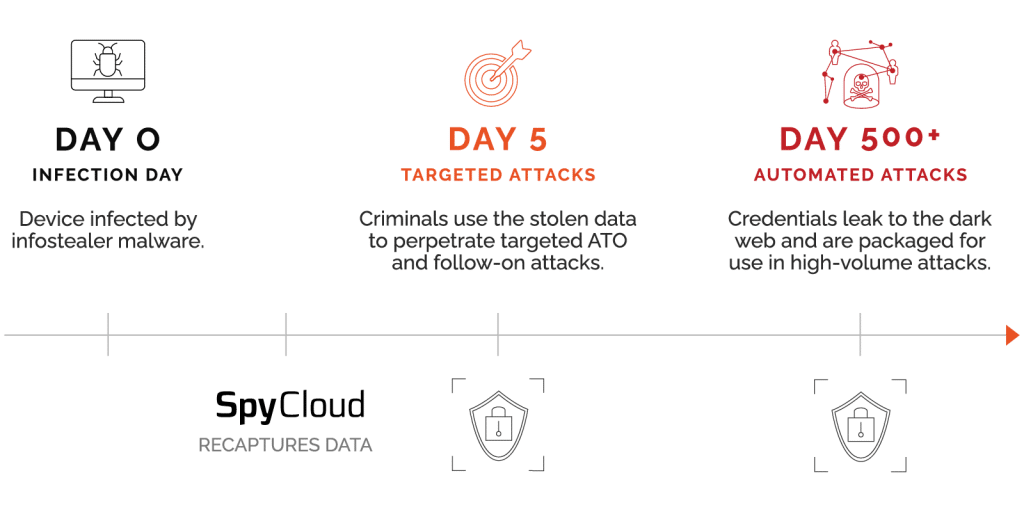
After a data breach, attackers typically keep stolen information contained within their trusted network until they’ve fully monetized the data. The attacker may engage trusted advisors to help them parse the data and crack passwords. At this stage, they may identify exceptionally wealthy or high-profile victims who should be treated differently than the rest, and get creative in targeting them with sophisticated, manual account takeover attacks.
Once the accounts have been thoroughly monetized, the credentials are packaged for sale or trade as combolists, which are credential lists that have been formatted for use with automated account checker tools. These automated tools, which can be used even more efficiently in combination with bots, use thousands of credential pairings to attempt to login to websites and even exposed endpoints on corporate networks. With up a two percent success rate, inexpensive credentials and advanced crimeware tools make credential stuffing possible with minimal effort, expense, or expertise – even for unsophisticated criminals.
Combat Both Targeted Account Takeover and Credential Stuffing
80 Percent of Losses Come from Just 10 Percent of Attacks
Many enterprises think their bot firewall, used to block credential stuffing attacks, keeps employees and consumers safe from account takeover (ATO). Bot firewalls do a good job of blocking automated attacks, but these attacks generally come later in the timeline of a breach. Sophisticated, focused attacks by human actors come earlier, aimed at the highest value targets.
While targeted attacks are less common, the costs are exponentially higher: SpyCloud customers report that 80 percent of losses result from targeted attacks that account for just 10 percent of account takeover attempts. SpyCloud helps thwart both types of attacks by enabling enterprises to detect and reset compromised credentials early in the breach timeline, protecting affected accounts and rendering stolen passwords useless to criminals.
Detect and Reset Compromised Passwords Before Criminals Can Use Them
Leverage the Largest Database of Recaptured Breach Assets in the World
Both targeted account takeover and credential stuffing attacks rely on stolen login credentials, whether they’re being entered by a human or an automated account checker tool. Early detection shortens the window for attackers to use stolen logins successfully; however, the worst damage happens while criminals are still trading the data privately, often for a period of 18 to 24 months before the data becomes available on the deep and dark web.
SpyCloud researchers infiltrate criminal communities to gain early access to breached data, helping enterprises reset passwords as early as possible to shut out attackers and prevent account takeover. With over 500 billion recaptured assets, SpyCloud maintains the largest database of underground data in the world.
Featured Products
Our award-winning products enable you to proactively protect your users’ accounts and thwart online fraud.
Consumer ATO Prevention
Protect your users from account takeover fraud and unauthorized purchases.
Employee ATO Prevention
Protect your organization from breaches and BEC due to password reuse.
Featured Resources

Credential Stuffing 101
We tap our expertise in helping organizations recover exposed credentials to help you understand the anatomy of credential stuffing attacks, why they persist, and what you can do to prevent them.
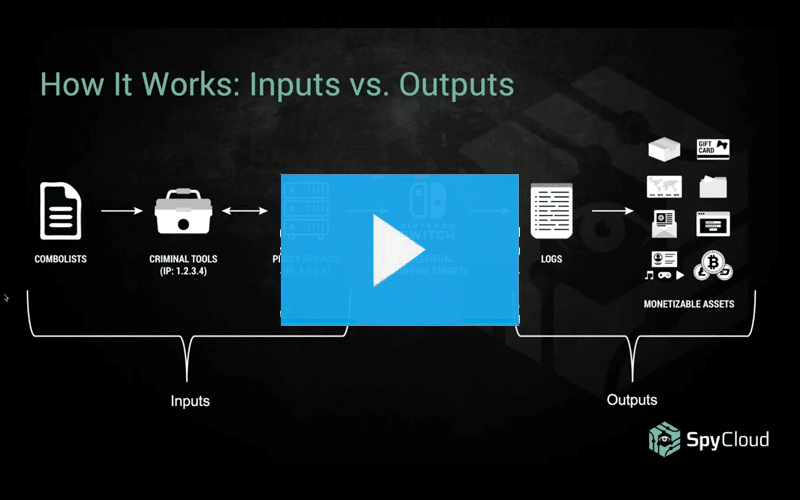
How Credential Stuffing Tools Are Made
Learn how credential stuffing works and get insights into the tools of the trade (including some very sophisticated custom Nintendo crimeware). Discover why stolen accounts that don’t have obvious monetary value can be profitable for cybercriminals.
