There are dangers ahead for many businesses and individuals dealing with the global panic surrounding the COVID-19 virus. Unfortunately, as people search for information and guidance about what to do, it’s clear that cybercriminals are taking advantage of their anxiety and fear.
Ordinary criminals and state-sponsored actors alike are adapting existing attack methods to align with and capitalize off of global concerns about coronavirus. By tapping into strong emotions, attackers can lure people into taking risky actions without considering the consequences.
As security professionals, we need to ensure users are informed about the risks. Responding to coronavirus and the associated fallout will be enough of a challenge without the added strain of a security incident. Sadly, we’ve already seen this type of situation arise; the University Hospital Brno in the Czech Republic, which houses coronavirus testing facilities, experienced a disruptive cyberattack on March 11th.
On that note, here are a few of the ways attackers are taking advantage of COVID-19 panic.
1. Posing as Official Government Agencies
With so many people searching for official answers, this is one of the most prevalent tactics we’ve noticed. Users are more likely to open, trust, and forward messages that appear to come from official sources. Unfortunately, attackers are using the promise of official information about the pandemic to lure users into downloading malware, handing over login credentials, and “donating” to fraudulent causes.
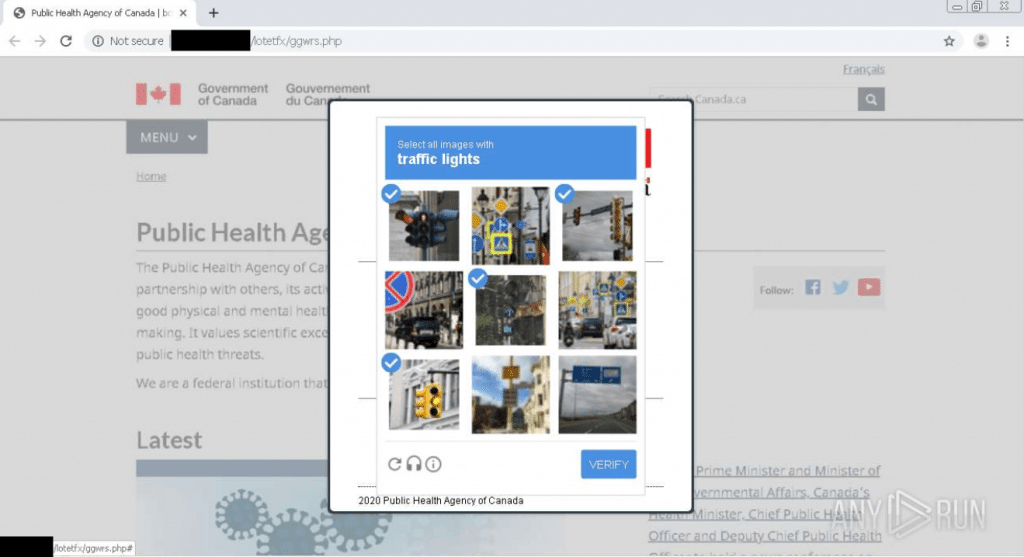
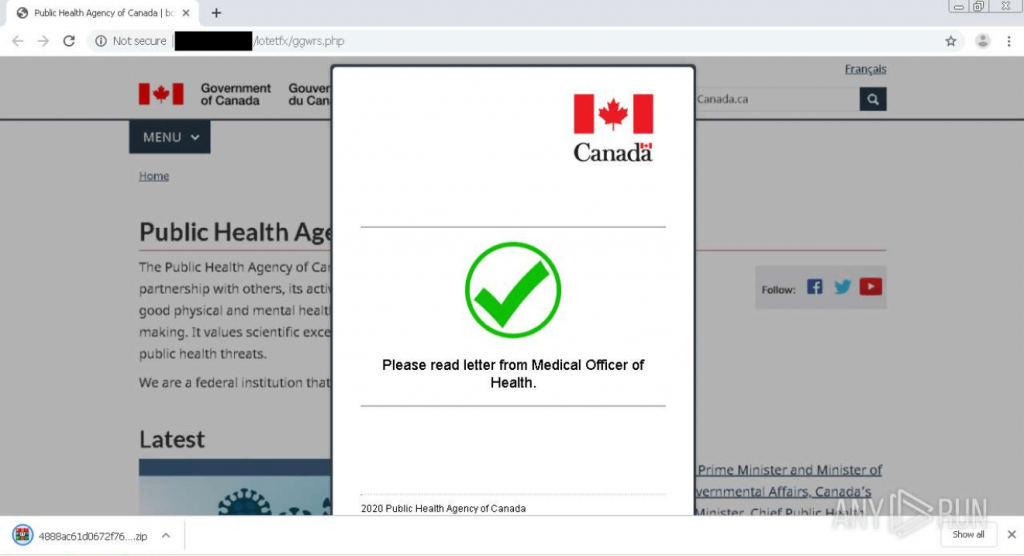
SpyCloud researchers encountered one case in which a threat actor created a fake site masquerading as the Public Health Agency of Canada. The actor even went so far as to create a fake captcha to make the site feel legitimate and put victims at ease.
Figure 1: A scammer’s fake version of the Public Health Agency of Canada website, with a fake “captcha” challenge.
When a victim completes the captcha, the website invites them to download a letter from a “Medical Officer of Health” on COVID-19.
Figure 2: The website directs victims to download a file: “Please read letter from Medical Officer of Health.”
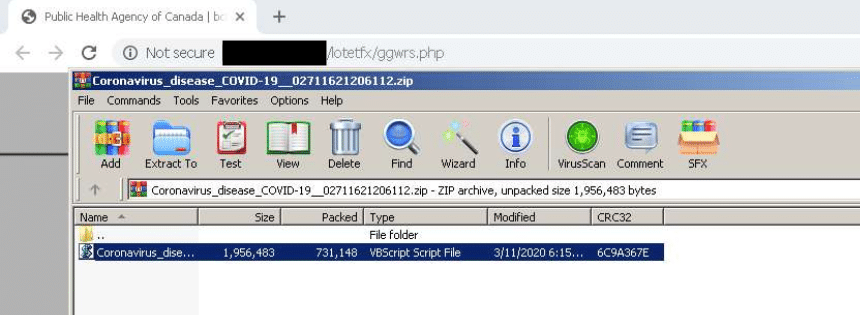
Instead of official medical guidance, the website downloads a nested zip file. At the end of this nested zip file, an obfuscated vbscript acts as a loader for Ursnif stealer. Researchers and security teams can reference the VirusTotal page for this malware here.
Figure 3: Malware downloaded by the fraudulent website.
Scams like this one are extremely common, with a variety of different twists. The World Health Organization, which threat actors frequently reference to add a sense of legitimacy, has released an announcement acknowledging phishing attempts that may claim to have an affiliation with WHO and urging users to beware of malicious impersonators. In one example, researchers at Sophos reported a phishing scam that sends users to a simple webpage mirroring the WHO website, with an important twist. A pop-up on the page prompts users to enter their email username and password in order to proceed, which of course goes directly to malicious actors. SophosLabs also noted a spam campaign in Italy that includes a Word document with a malicious macro that distributes Trickbot malware, drawing on content from WHO to convince users to download the file.
Criminals have also been observed impersonating the US Center for Disease Control (reported by Codefense), the Center for Public Health of the Ministry of Health of Ukraine (reported by RedDripTeam and MalwareHunterTeam), the Vietnamese Prime Minister (reported by VinCSS), the Mongolian Ministry of Foreign Affairs (reported by Check Point), a disability welfare service provider in Japan (reported by IBM X-Force), and many others.
2. Offering Up Malicious Coronavirus-Related Maps
Many legitimate charts and maps are circulating as people struggle to understand the scope of the pandemic. Attackers are tagging onto the trend, which allows them to blend in with legitimate sources and offer visually-appealing sources of information to lure in victims.
One fake ‘Corona Virus Map’ application that has been going around makes use of a legitimate map created and maintained by Johns Hopkins, making it difficult for victims to determine that it is malicious. The map is interactive, resizeable, works on all Windows machines, and requires any version of Java. Unfortunately, the compelling download contains Azorult malware, designed to steal victims’ credentials.
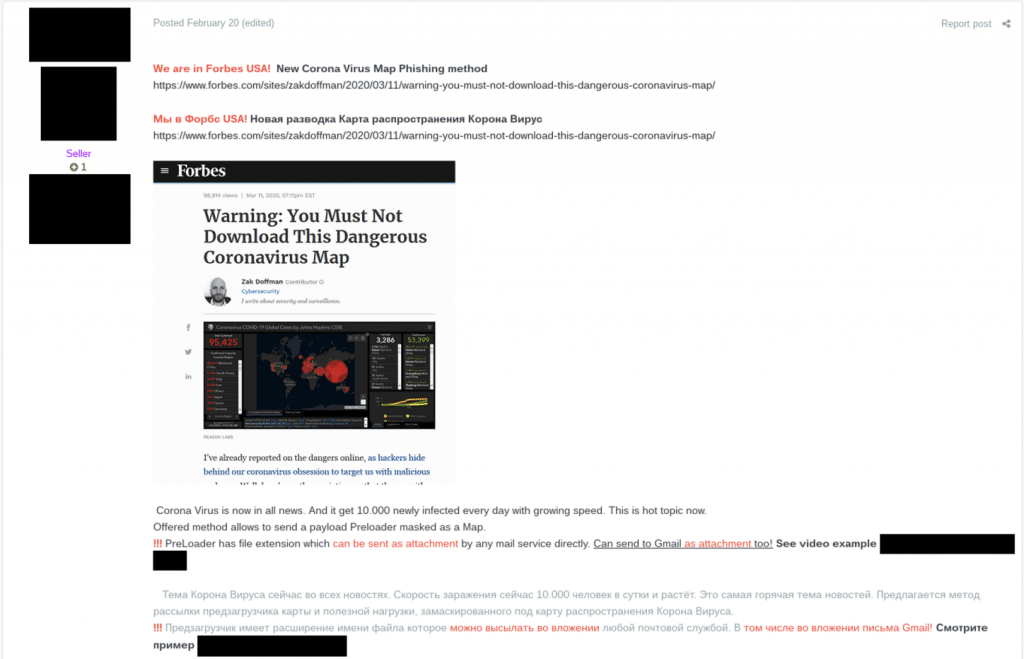
SpyCloud researchers have observed advertisements for this malware on criminal forums. The threat actor touts recent press coverage from Forbes, offers a how-to video to help prospective criminals get started, and lists prices at $300 (without Java CodeSign cert or $700 with Java CodeSign cert).
Figure 4: Screenshot of an advertisement for “Corona Virus Map Phishing Method” on a popular criminal forum.
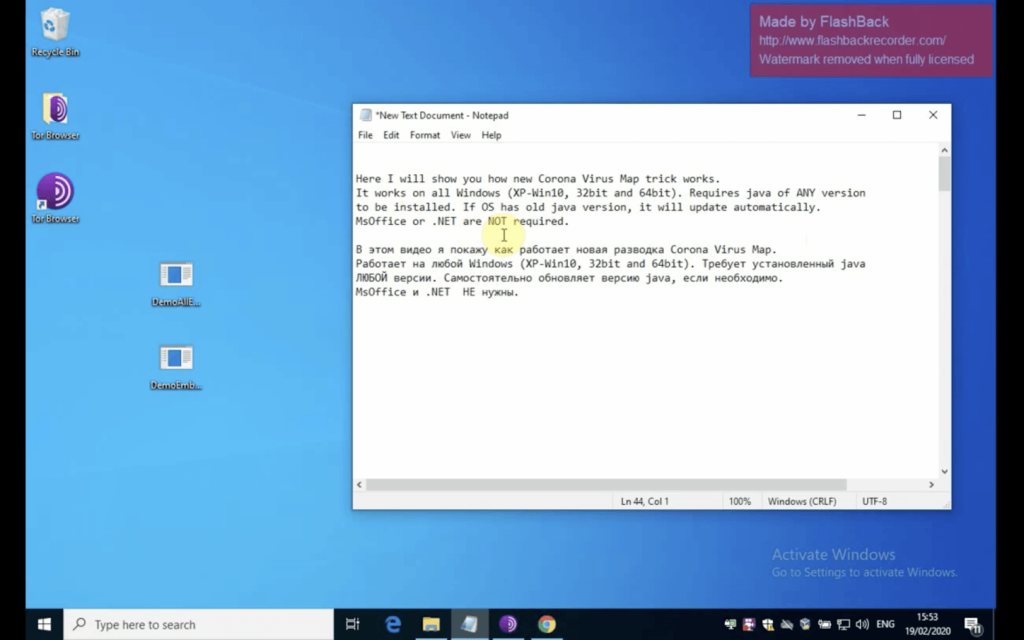
The threat actor’s detailed video tutorial (which has over 400 views to date) provides step-by-step instructions in both English and Russian. Later in the video, the actor demonstrates that the download does not trigger Windows Defender or get picked up by a variety of common antivirus software programs.
Figure 5: Screenshot of the threat actor’s detailed video tutorial for getting started with the malicious map.
The campaign appears to be working. On March 12, a researcher shared a report from the command and control server used by the Fake Corona Virus Map actor, showing that their campaign has been relatively successful. At the time the report was captured, most infections were located in the United States, with Canada coming in second.
3. Developing ‘Convenient’ Mobile Apps to Track COVID-19
In several cases, threat actors have created malicious mobile applications, particularly for Android phones. So many examples have emerged that researcher Lukas Stefanko has created a dedicated page to track Android malware samples related to coronavirus.
In one interesting example, DomainTools researchers have reported a COVID-19 Tracker App, which promises victims access to a map that tracks the spread of the virus. Instead, the application distributes an Android lock-screen ransomware that DomainTools have called “CovidLock.” Victims are faced with a $100 fee, to be paid in bitcoin, to restore access to their data and prevent it from being leaked. (To protect themselves against this lock-screen attack, users should ensure that they have updated to Android Nougat and established a phone password.)
4. Targeting Food Delivery Accounts via Credential Stuffing
As people attempt to practice social distancing, shelter in place, or quarantine themselves to prevent the spread of coronavirus, food access is a source of concern for many people. Some people don’t want (or can’t) go to crowded stores to pick up food, plus many grocery stores are running through their merchandise ahead of schedule as people stock up on large quantities of groceries at once.
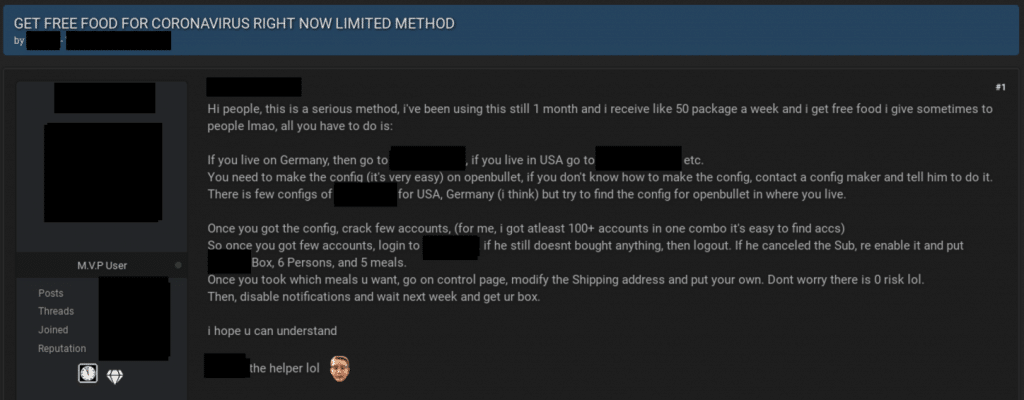
SpyCloud researchers recently observed a threat actor sharing instructions for cracking and taking over meal-kit delivery accounts on a popular criminal forum. Food delivery providers with online or mobile ordering applications can expect to see an uptick in credential stuffing attempts as attackers try to get free groceries delivered to avoid going outside during the pandemic.
Figure 6: Screenshot of a popular criminal forum showing a threat actor sharing instructions for taking over meal-kit delivery accounts.
In this second example, another criminal offers to sell meal-kit delivery codes to people stuck at home. The seller helpfully explains, “If you need food and you don’t want to go out for the next couple weeks (corona virus), you can buy some [redacted] codes from me!”
Figure 7: Screenshot of a criminal advertisement for meal-kit delivery codes in a post titled, “[Food] Stay Fed and Safe!”
5. Recruiting Desperate Laid-off Workers as Money Mules
Coronavirus has disrupted regular life around the world and led to a slew of layoffs, gig cancellations, and other hardships that will leave many people in desperate positions. Sadly, this provides yet another way for threat actors to capitalize from the suffering of others: recruiting mules.
Money mules are individuals who are recruited to help threat actors transfer money to disguise fraudulent transactions. A criminal who drains a stolen bank account typically won’t take the money directly; instead, they first transfer it to the “mule,” who then passes the cash along to the criminal in exchange for a small cut. Mules may or may not know the role they play in laundering money, but they carry a much higher risk of being identified by law enforcement than the criminals who hire them.
Brian Krebs reports that a fake charitable organization called “Vasty Health Care Foundation” has been using job postings related to helping coronavirus patients to recruit money mules. New hires are given a series of busywork tasks, both to identify who is willing to follow through on work and to make the recruit feel useful. Finally, the new hire is asked to process a donation, which of course entails transferring stolen money for the cybercriminals.
6. Advertising Coronavirus Services, Products, and Discounts to Other Cybercriminals
Like the threat actor advertising the coronavirus tracking map described above, many threat actors are pivoting their existing products and services to focus on coronavirus lures.
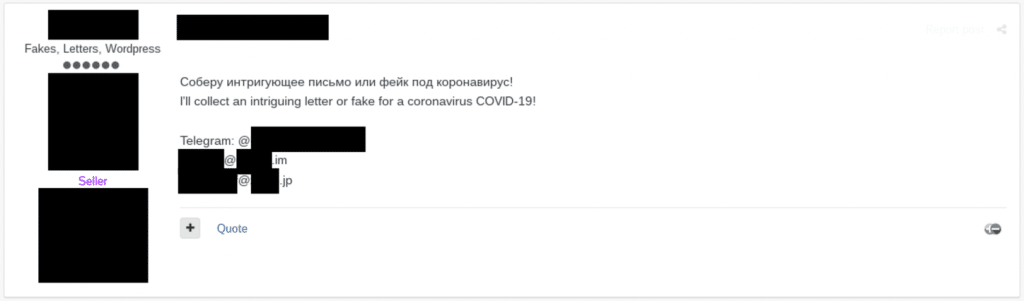
In this example, SpyCloud researchers observed a threat actor advertising a service in which they craft coronavirus-focused scam letters and scam sites for customers. Although this threat actor has been operating since at least 2017, the coronavirus spin has been added recently.
Figure 8: Screenshot of a popular criminal forum showing an advertisement for coronavirus scam letters and sites.
The scam letters are priced from $20 to $100. Scam WordPress sites cost $300 to $500. This particular actor’s work looks fairly professional and seems to be somewhat popular. Based on the “Scams” listing, SpyCloud researchers speculate that the actor has the ability to spin up scam shops for items related to coronavirus prevention, such as masks, but we have not seen proof of that.
Figure 9: Screenshot showing the same threat actor’s pricing.
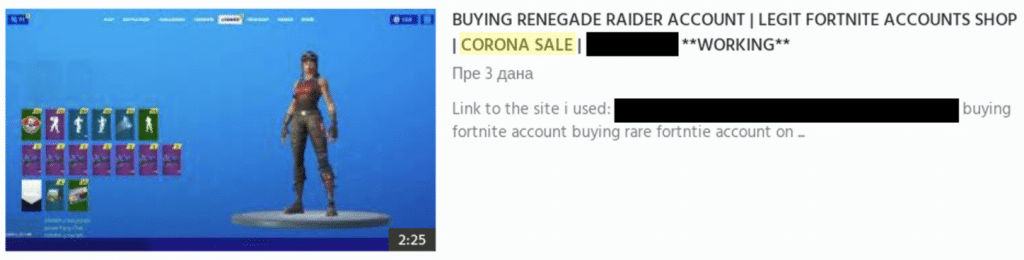
Another threat actor has advertised a “CORONA SALE” for stolen Fortnite accounts. We expect to see an uptick in the popularity of stolen accounts that can be used to occupy people during social isolation and quarantines, such as streaming services.
Figure 10: Screenshot showing an advertisement for Fortnite accounts with “CORONA SALE” in the description.
7. Malvertising on Coronavirus News Stories
Coronavirus news has been spreading like wildfire. Every news outlet has at least some coverage of COVID-19, and (speaking from experience) users are checking obsessively for new updates. Unsurprisingly, Proofpoint researchers report that malvertising campaigns featuring coronavirus have become prevalent.
8. Playing into Conspiracy Theories and Fears
Conspiracy theories always pop up during a crisis, particularly when official sources lack satisfying answers.
Proofpoint researchers have observed coronavirus campaigns driving clicks via conspiracy theories, such as one that promises access to a “Confidential Cure Solution” that has been developed by a “secret medical scientist team.” When victims click to gain access to the purported cure, they are instead directed to a fraudulent DocuSign login page that collects their login credentials.
In another example, Cofense has observed a phishing campaign, supposedly sent by the US Center for Disease Control (CDC), that claims the coronavirus has reached the local region and is now more contagious than ever. The subject line reads: “COVID 19 – Now Airborne, Increased Community Transmission.” While these claims are untrue, they play into people’s fears about the virus and make them more likely to click the malicious link within the message and enter their login credentials.
9. Fostering Panic via Disinformation
In Ukraine, a disinformation campaign went viral and supposedly led to violent riots, according to Buzzfeed News. The campaign, which appears to have involved emails and social media posts, spread incorrect information about the number of new cases in the country and led people to protest the arrival of evacuees arriving from China. According to ZDNet, the campaign was the product of the Hades group operating out of Russia.
In the United States, Bloomberg has reported that an attack on the US Health and Human Services Department on March 13th may be related to the spread of text messages containing rumors that the government was going to institute a national quarantine. The National Security Council addressed these rumors in a tweet.
Conclusion: Be Vigilant
As the global pandemic continues, we can expect that threat actors will continue to use world news for criminal gain. Infosec teams should educate their users about these types of threats and provide them with guidelines for practicing good security hygiene.
For example, to avoid common coronavirus scams, users should:
- Think critically about sources that promise coronavirus news
- Review WHO guidelines for avoiding phishing scams
- Stick to trusted sources for the latest updates
While also applicable to avoid specific coronavirus scams, users should ALWAYS keep the following best practices in mind:
- Don’t click suspicious links
- Don’t download attachments from unknown or untrusted sources
- Do not “Enable Content” in unknown Word documents
- Use a unique password for every online login
- Be careful not to share login credentials with unknown or suspicious providers (there is NEVER a legitimate reason for a third-party to require your login credentials)
- Check all of your devices for software or firmware updates
![Screenshot of a criminal advertisement for meal-kit delivery codes in a post titled, “[Food] Stay Fed and Safe!” The post highlights how cybercriminals may change their account takeover targets due to coronavirus.](https://spycloud.com/wp-content/uploads/2020/03/corona-blog-figure-7-1024x517.png)