The World Turns to Zoom
As we deal with the ramifications of the global pandemic, from avoiding COVID-19-themed scams and malware to social distancing and working from home, millions of us have turned to collaboration and communication tools to maintain work and personal connections. Due to its ease of use, ability to run on multiple platforms, and low price point, Zoom has quickly become the video meeting service of choice: daily meeting participants on the platform surged from 10 million in December to 200 million in March, and 300 million in April.
Software and services that reach mass adoption usually attract the attention of attackers as well. The more popular they are, the more attractive targets they make. In this case, Zoom was not actually breached, yet credentials that were stolen in third-party breaches are being used against them, promoted as “leaked Zoom credentials.” Criminals are capitalizing on the name recognition, which helps them better monetize the compromised data – though price wars on underground sites have driven the cost of a Zoom account down below $0.01 (and in some cases they are given away for free).
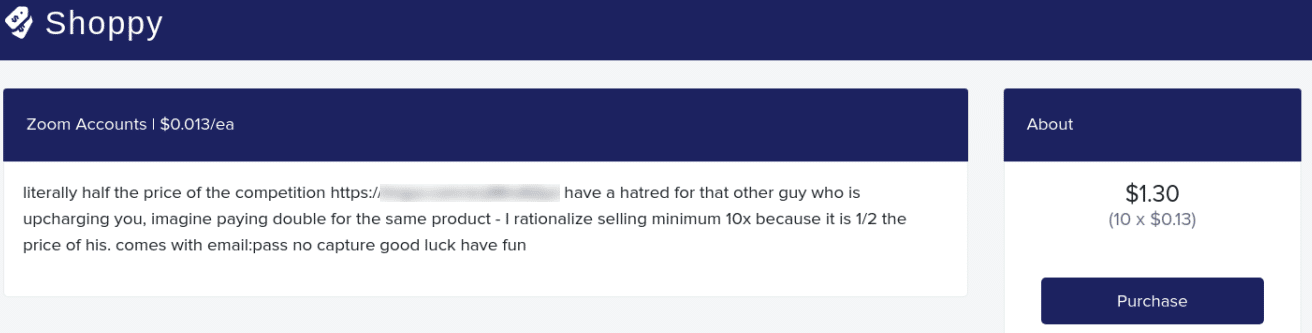
Figure 1: A post offering Zoom accounts for “literally half the price of the competition”
due to a “hatred for that other guy who is upcharging you.”
It doesn’t appear that bad actors are looking to sell Zoom credentials so their community can enjoy the service at a lower cost (as is the case with the likes of Spotify and Disney+, where for a one-time cost of under $2, one can illegally obtain credentials for what would normally cost $9.99/mo+).
For sellers, offering the stolen creds from a well-known service fuels the growth of their darknet market customer base. But for buyers? The motivation is probably one of three things:
-
The potential ability to eavesdrop on meetings and potentially obtain corporate secrets.
-
Fuel for other account takeovers; the hope that users have reused their Zoom passwords on their corporate and personal email accounts (given that 59% of people admit to reusing passwords, it’s not a stretch), enabling them to easily break into those accounts and perpetrate fraud, IP theft, and businesses email compromise.
-
Simply put: the lulz; the amusement gained, for example, from “zoombombing” meetings and disrupting school classes.
The story of “Zoom credentials for sale” has attracted a lot of attention from major press outlets, and though they have started to acknowledge the likelihood that most (if not all) of the exposed passwords are old, the plethora of articles has likely damaged Zoom’s reputation, and the company has been forced to communicate more publicly about security measures than ever before.
In an effort to clear up any confusion about these alleged credential “leaks” of Zoom accounts, SpyCloud offers this summation along with an analysis of credential dumps our research team found on criminal forums, which prove that though they have been enhanced with data that enables Zoom meeting hijacking (host PINs, meeting IDs, etc), the lists were created using textbook credential stuffing attacks and old compromised third-party databases. In other words, though it’s news to media outlets, these credential sets aren’t new to the criminal community, or to SpyCloud.
In response, Richard Farley, Chief Information Security Officer at Zoom, said:
“SpyCloud’s analysis found that threat actors committed credential stuffing attacks using email addresses and passwords obtained in previous breaches of other companies, or through malware infection on their devices. SpyCloud is the authority on account takeover prevention, and we appreciate this important security intelligence. This information has assisted us in identifying Zoom users who may have reused passwords compromised in third-party breaches. We have performed password resets on the accounts, and have provided notification to impacted users. Zoom will continue to work diligently to identify and respond to such issues in the future.”
Are Zoom Accounts Still for Sale on the Dark Web?
On the deep and dark web, it is common practice for criminal marketplaces to advertise sales on illegal wares such as stolen credentials, which criminals can use to take over consumer accounts, steal funds, and siphon rewards points.
A quick clearnet search on April 28 revealed a number of very recent articles from tier-one media outlets about Zoom credentials being shared and sold on the dark web. Cybersecurity firms continue to come out with blog articles and analysis of the leaked credential databases, which likely intend to be in Zoom’s best interest, but in fact only fuel the news cycle.
But is the media attention reflective of what’s currently happening on the dark web?
The short answer is no: SpyCloud researchers are seeing a decrease in Zoom account sharing as criminals seek to avoid the attention of law enforcement. Some forums have taken down Zoom account sales:

Figure 2: A hacking forum mod’s post banning Zoom account sales.
It also appears that changes Zoom has made to its user interface have also interfered with configs we’ve seen in circulation. The changes seem to be disruptive to the criminals trying to gain access to users’ accounts. However, criminals will likely begin to iterate to bypass those new measures. Once the immediate media attention has died down, we expect to see Zoom accounts being traded publicly once again.
Account Takeover: Fueled by Password Reuse
A recent SpyCloud analysis of Fortune 1000 employee breach data gives insight into just how bad the password reuse problem is: on average 76.5% of F1000 employees reuse passwords. It’s not unlikely that a large percentage of Zoom users do the same.
Simply put, password reuse fuels account takeover. Passwords are the easiest entry point for criminals, and they continue to be leaked via third-party breaches, impacting even the most sophisticated users of top technology services.
Once credentials are in hand, taking over accounts is simple and lucrative, resulting in unfettered access to the corporate data, funds, and PII contained within, and wreaking havoc on the lives and finances of victims.
Companies like Zoom, whose user credentials have been exposed by various third-party leaks, experience brand and reputation damage. Zoom has responded quickly with a great deal of transparency and new security features, all helping to alleviate some of the damage; but for users who reuse their compromised Zoom password on other accounts, they may continue to experience the effects of sensitive data being exposed as criminals hop from one account to the next:
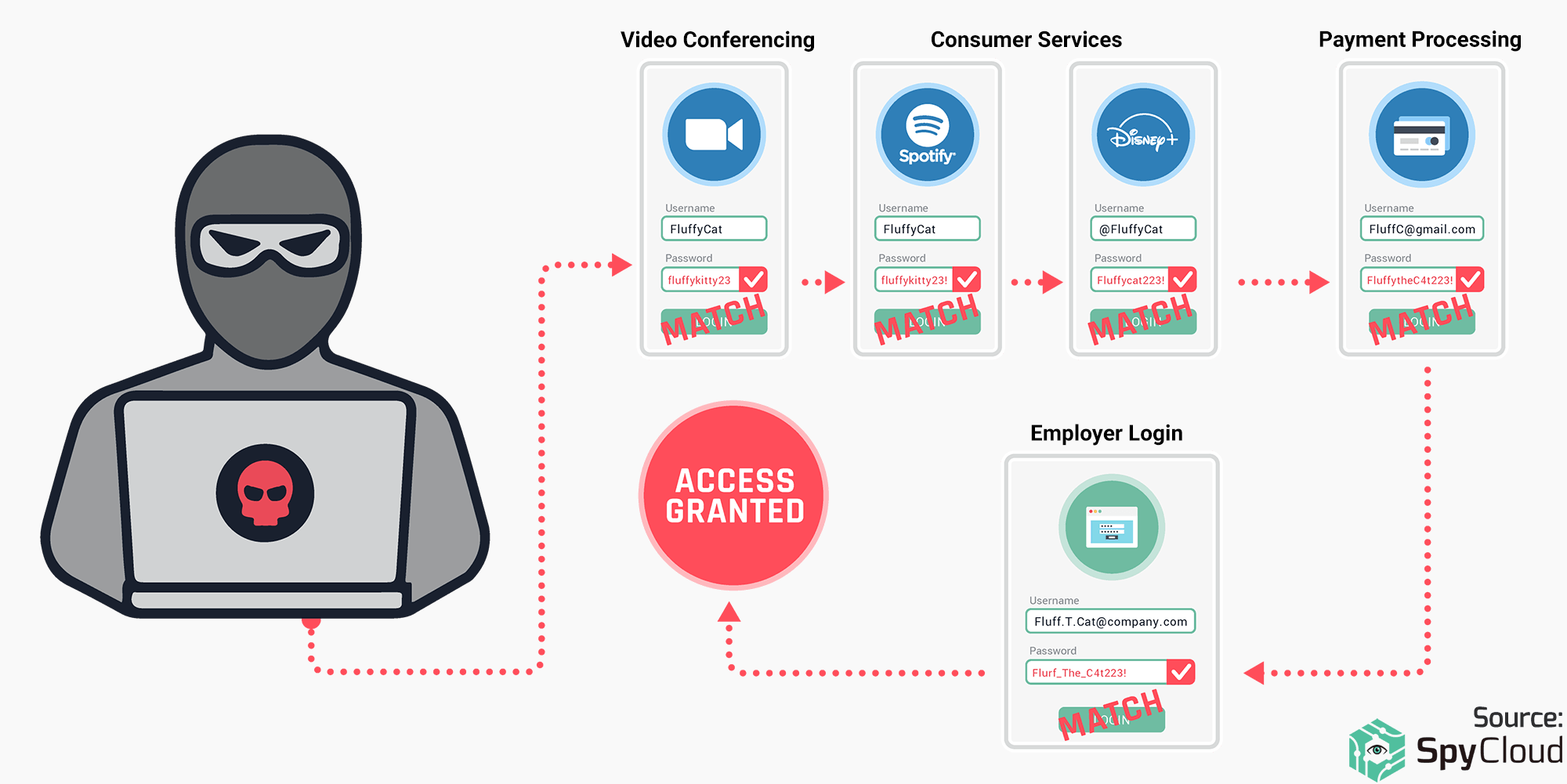
Figure 3: Criminals leverage reused, recycled and fuzzy matches of a user’s password to compromise multiple personal and work accounts.
Credential Stuffing 101
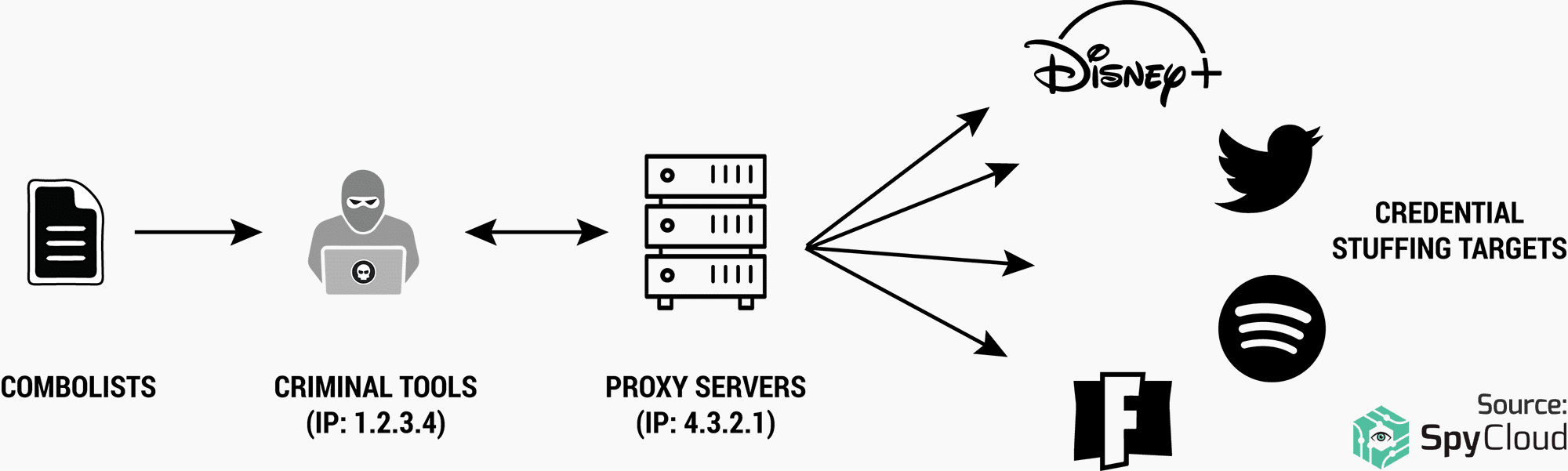
Figure 4: Flow of data when an attacker uses an account checker tool for credential stuffing.
As we stated, criminals take advantage of the lowest hanging fruit, reused passwords, exploiting credentials that have appeared in third-party data breaches to access other accounts. In credential stuffing attacks, criminals automate their account takeover attempts by using account checker tools along with combolists (thousands of credential pairings formatted for use with account checkers) to test thousands of stolen passwords at once. With an impressive success rate, inexpensive credentials and advanced crimeware tools make credential stuffing possible with minimal effort, expense, or expertise – even for unsophisticated criminals.
Most often, attackers begin with a popular account checker such as Sentry MBA, SNIPR, or Openbullet (which is free and bills itself as a legitimate “webtesting suite”) and upload a configuration file, or “config,” to modify it for a specific target. Configs can be purchased privately, from a vendor of account checker software, or downloaded for free from several criminal forums.
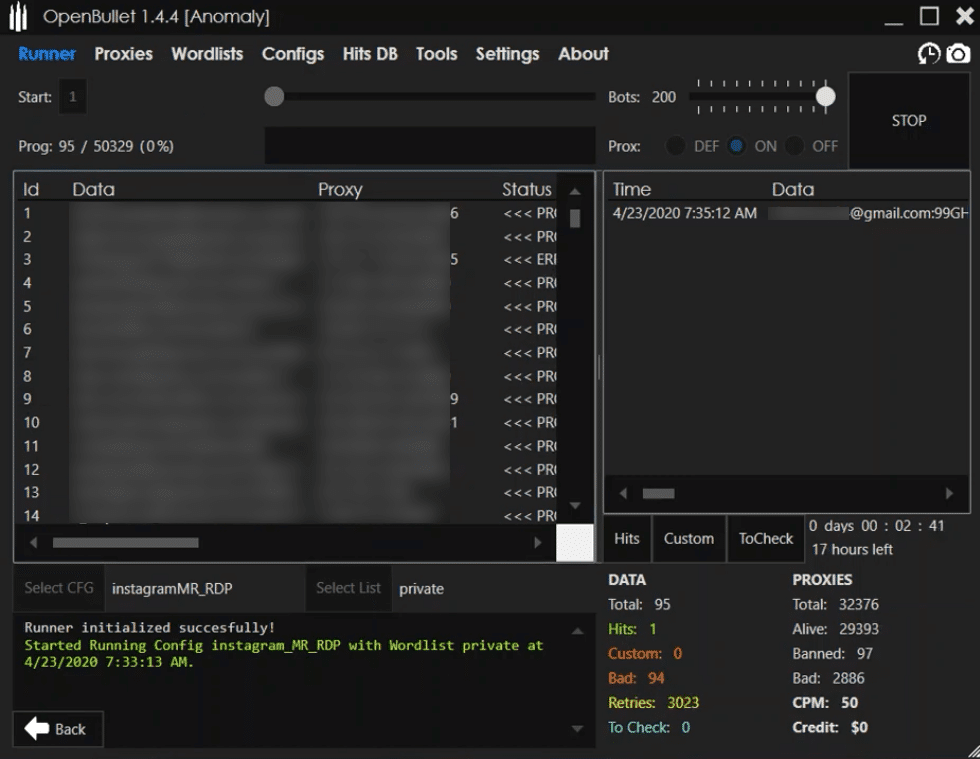
Figure 5: Recent screenshot of OpenBullet with an Instagram config loaded.
SNIPR features innovations that enhance user friendliness and detection evasion. In addition, it comes pre-baked with built-in configurations that are able to target large websites, such that even low-skill criminals can operate the tool without building and uploading configuration files.
Figure 6: Cracked SNIPR Account Checker screenshot showing some locally available configs for various credential stuffing targets.
Unlike Openbullet, SNIPR is not free. Like OpenBullet, the tool has its own open-source development community and supports multiple attack surfaces such as web requests, email (IMAP), and others, allowing apps, games and more. SNIPR also scrapes public proxies dynamically, which lets attackers look for alternating proxies.
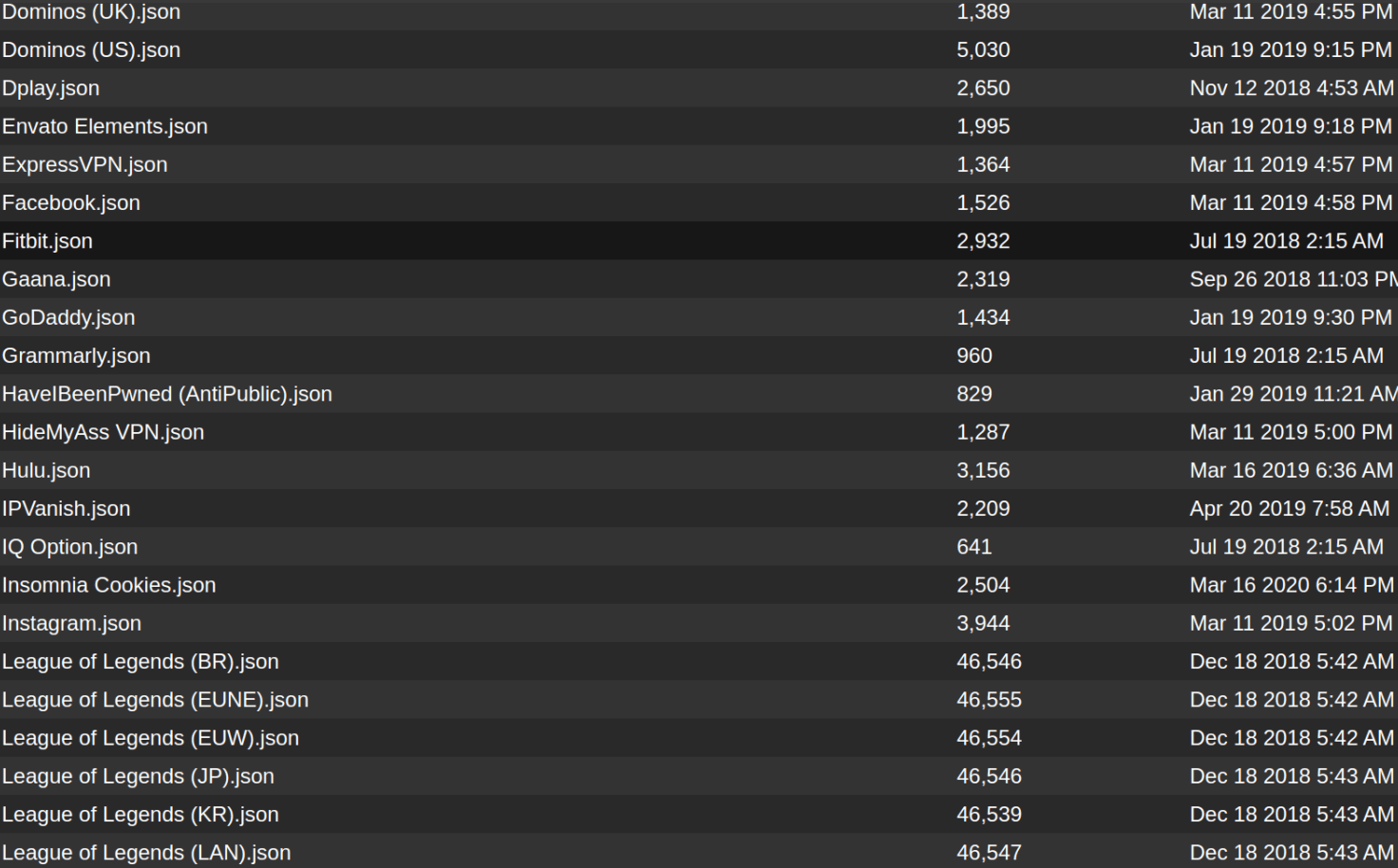
Figure 7: Screenshot from a popular crimeware config repository.
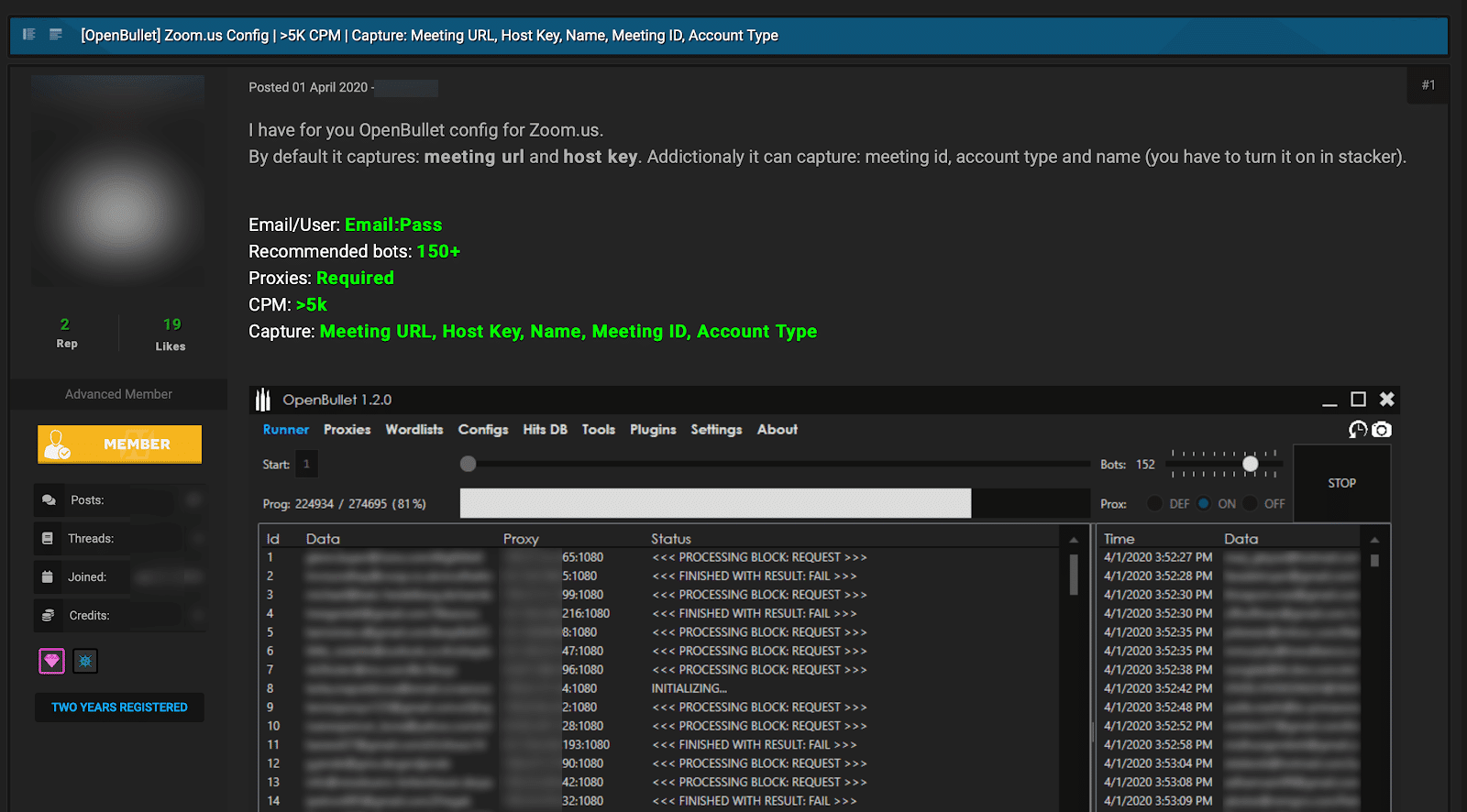
Figure 8: A forum post showing a Zoom OpenBullet config release.
Video: See how accounts are taken over via credential stuffing.
SpyCloud’s Analysis of Zoom “Leaked” Credentials
SpyCloud researchers have obtained multiple databases on several underground forums that contain usernames, passwords, Host PINs, Meeting IDs, and names. An analysis of these databases reveals that they were created using textbook credential stuffing attacks leveraging old compromised databases.
List 1: This list was shared on a forum:
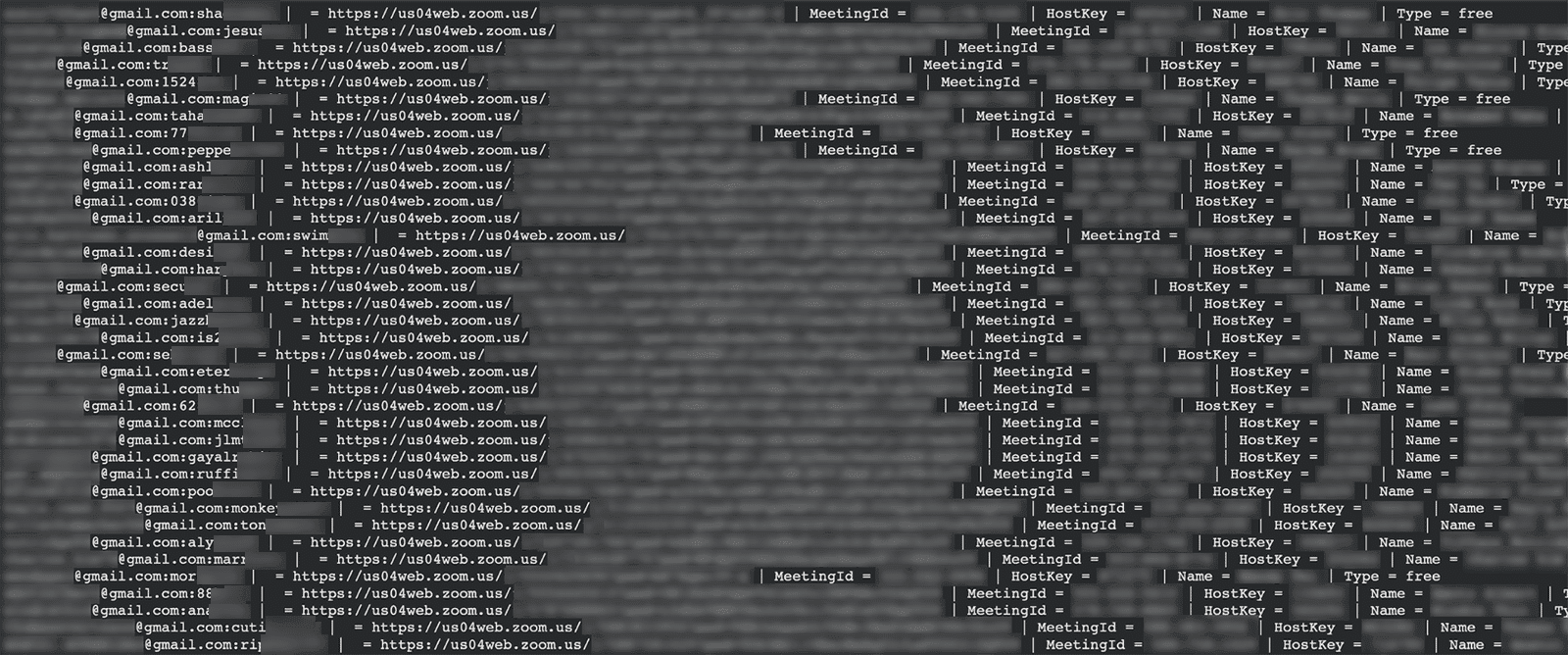
Figure 9: Redacted list of Zoom user logins, meeting links, host keys, full names, and more shared on a forum.
100% of these users were part of previous breaches and accounted for in the SpyCloud database:
Breach Title | SpyCloud Source ID | Impacted Users |
“Collection #1-5” Combolists | · 16573 · 16575 · 16576 · 16577 · 16579 | 100% |
2019 Antipublic Combolist | 16580 | 100% |
AP MYR and Zabugor Combolist | 16581 | 100% |
Sensitive Source | N/A | 100% |
Russian Bitcoin Security Forum Account Dump | 16323 | 100% |
Combolist of 1.4 Billion Credentials | 13305 | 100% |
Gmail Combolist | 3707 | 98.09% |
List 2: A shorter list was discovered by our team which included the seller’s Discord username, advertising sales of Zoom accounts:
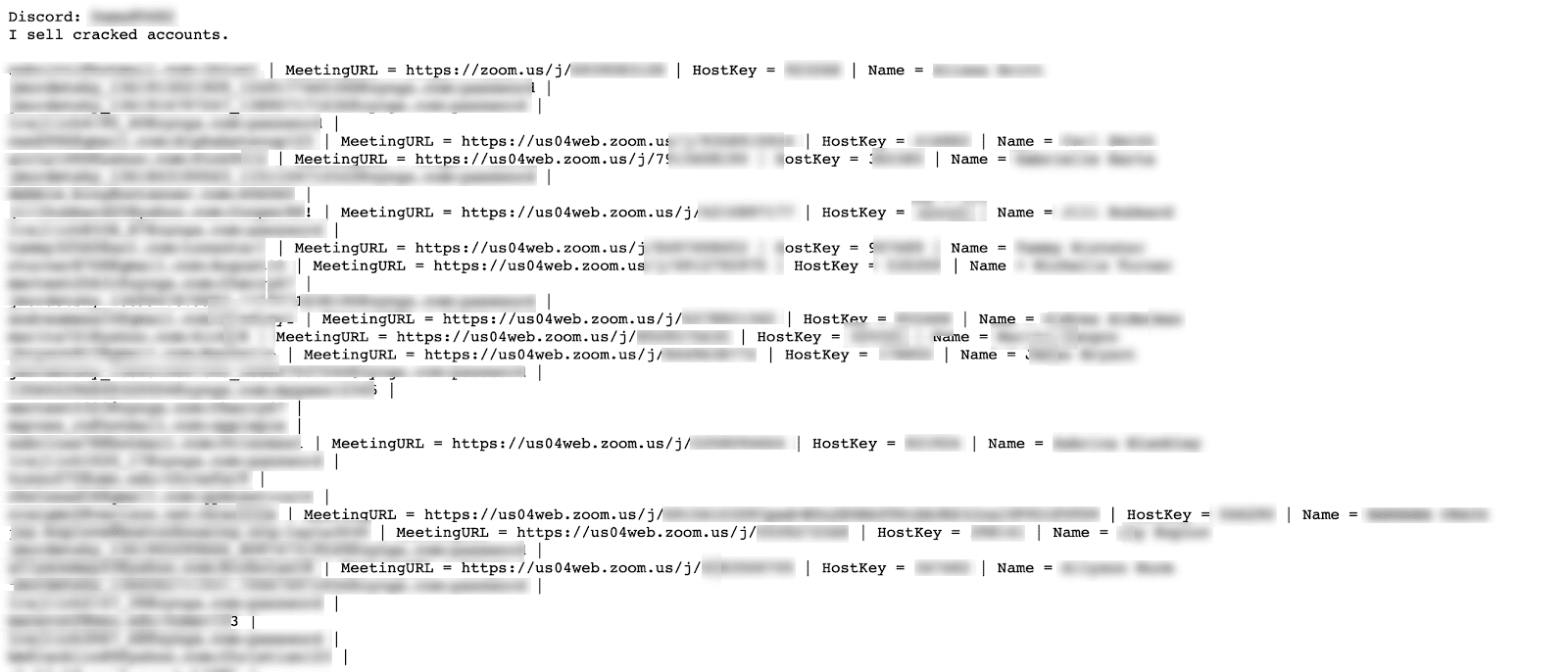
Figure 10: Zoom accounts for sale.
When we ran an analysis of these accounts, we saw similarly that 100% of the credentials were already in SpyCloud’s dataset from previously reused passwords:
Breach Title | SpyCloud Source ID | Impacted Users |
Zynga | 17009 | 100% |
Collection #2 Combolist | 16575 | 25.0% |
MyFitnessPal | 13916 | 22.73% |
Combolist of 1.4 Billion Credentials | 13305 | 21.97% |
Collection #4 Combolist | 16577 | 18.94% |
Collection #1 Combolist | 16573 | 17.42% |
2019 Antipublic Combolist | 16580 | 17.42% |
Sensitive Source | N/A | 15.15% |
2 | 15.15% |
List 3: In late April, the SpyCloud Human Intelligence team acquired a list of several thousand leaked zoom accounts. From our analysis, the majority of the previously reused passwords were sourced from the Chegg (2018), MyFitnessPal (2018), and Poshmark (2019) breaches.
99.2% of the records were part of previous breaches and accounted for in the SpyCloud database:
Breach Title | SpyCloud Source ID | Impacted Users |
Active Combolist | · 16398 · 16359 · 16360 · 16361 · 16362 | 56.73% |
Chegg | 15990 | 43.74% |
Collection #2 Combolist | 16575 | 42.27% |
Collection #4 Combolist | 16577 | 37.54% |
MyFitnessPal | 13916 | 31.03% |
Poshmark | 16844 | 29.80% |
Collection #1 Combolist | 16573 | 30.95% |
2019 Antipublic Combolist | 16580 | 30.71% |
Combolist of 1.4 Billion Credentials | 13305 | 30.19% |
Verifications.io | 16613 | 29.80% |
Next Steps for Zoom & Similar Enterprises
Despite the fact that nearly 100% of known Zoom credential leaks are from older breaches, the attention generated by the media has put the company under the spotlight. As a result, it has implemented many visible feature enhancements related to security. For example, it has:
- Begun educating users on steps they can take to keep their meetings and classrooms safe
- Changed the UI to defeat current Account Checker configs (this is only a stopgap as crimeware will evolve)
- Updated the default screen sharing setting for Education accounts
- Enabled Waiting Rooms so meeting hosts can control which participants join specific meetings and when
- Made security features easier to access by collating them in a new icon on the main meeting interface
What we recommend for all enterprises is:
- Proactively and constantly monitoring accounts for password reuse
- Adding friction to the login process when an account is exposed and the password hasn’t been changed
- Aligning with NIST password guidelines to secure the existing account creation process and password change mechanism, banning the use of commonly used or expected passwords along with those found in previous breach corpuses
- Educating users on what they can do to protect themselves:
- Unique passwords for every online account. If one account’s credentials are exposed in a breach, criminals will test the same username and password combination against other accounts. Using a different password for every account limits the damage criminals can do with a single set of stolen credentials.
- Long, strong passwords. Short, simple passwords are the easiest for criminals to crack and exploit. Long, complex passwords can make it harder for criminals to crack, and many will find it’s not worth the effort.
- Using a password manager, since the average consumer cannot memorize complex, unique passwords for hundreds of online accounts.
- Enabling multi-factor authentication wherever possible. Though not impossible to circumvent, MFA provides criminals with an additional barrier before they can access an account
It is also common for SpyCloud customers to monitor all user credentials on an ongoing basis and check their consumer passwords against our entire database independent of username, preventing consumers from choosing any password that has ever appeared in a data breach. We recommend that after identifying an exposed password, the user should be forced to reset their password, and provided with an explanation of why:
During a routine security check, we found that your login info might have been compromised through a breach unconnected to Zoom. Since a lot of people use the same email and password combinations across multiple sites, we require you to reset your password before your account can be accessed again. We strongly recommend doing the same for any other sites and services where you use the same password, and creating a strong, unique password for each.
(Learn more in our guide to notifying users that their passwords have been exposed in a third-party breach)
Ultimately, account security is the responsibility of the service provider and the user. In the case of Zoom, it can implement all the security features it can dream up, but users won’t take advantage of all of them, and some percentage will likely still reuse an old, recycled, or exposed password until an account takeover prevention solution is in place.
Have questions about our analysis? Contact us.