Simplify NIST Password Standards with SpyCloud
The latest password guidelines from the National Institute of Standards and Technology (NIST) lighten requirements for users—and increase the burden on security teams, who now need to identify and reset passwords that have been exposed in third-party data breaches.
At SpyCloud, we take the legwork out of aligning with NIST password standards. SpyCloud enables you to check your consumer and employee passwords against the largest repository of stolen credentials in the world, reducing the effort required to comply with NIST and keep your users secure.
Understand the Latest NIST Password Guidelines
Breaking away from strict requirements that encourage bad password habits, the most recent NIST password standards strike a balance between human-friendly policies that encourage users to choose strong passwords and strategies to help enterprises mitigate risk.
To get a full picture of why and how the latest NIST guidelines have changed, download our whitepaper.
Read the Whitepaper: Understanding the Latest NIST Password Guidelines
- Previous Breach Exposures
- Less than 8 Characters
- Context-specific Words
- Dictionary Words
- Repetitive Characters
- Password Hints
Align with NIST to Protect Your Users from Account Takeover
When users take shortcuts, criminals benefit. That’s why NIST password standards call for businesses to check for “commonly-used, expected, or compromised” passwords, which make it easy for criminals to take over accounts and commit fraud, drain accounts, and steal sensitive data.
With SpyCloud, security teams can prevent users from setting bad passwords and detect newly-exposed credentials by checking them against billions of plaintext passwords our research team has recovered from data breaches and botnet infections.
Read the Guide: Best Practices for Implementing NIST Password Guidelines
Easily Detect Weak or Compromised Passwords
Following NIST’s guidance to monitor user passwords poses a challenge for security teams. SpyCloud reduces that burden by making it easy to operationalize the billions of passwords in SpyCloud’s breach database.
To protect consumer accounts from online fraud, SpyCloud Consumer ATO Prevention enables enterprises to not only screen passwords at the time of creation in alignment with NIST, but also monitor users for new exposures over time.
For employee accounts, SpyCloud offers an even greater degree of automation. SpyCloud Active Directory Guardian enables you to prevent employees from creating passwords that NIST considers weak or compromised, and then scan employee credentials on an ongoing basis to detect and reset:
- Exact employee credentials exposed in a third-party breach
- “Fuzzy” credential matches, meaning a compromised password that has been reused with trivial changes
- Any password that has appeared in the SpyCloud breach database, regardless of username
- Dictionary words
- Repetitive characters
- Context-specific terms
Respond to Bad Password Hygiene
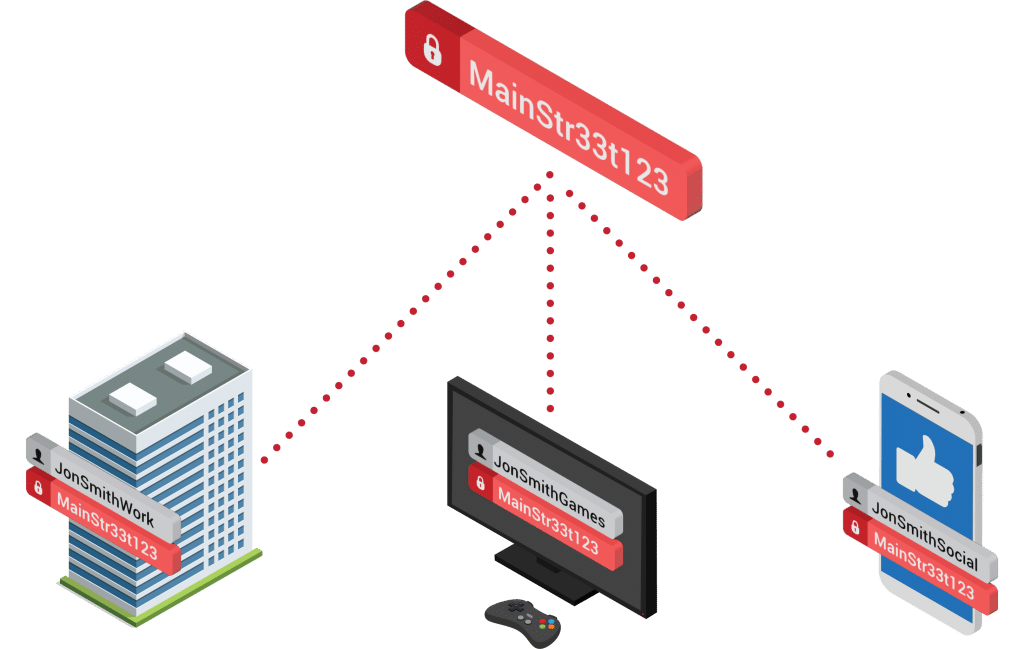
With hundreds of online accounts to keep track of, it’s no wonder users resort to bad habits like choosing weak passwords or reusing the same password across every account. For security teams, it’s challenging to detect this type of behavior at scale, especially when users recycle their work password with personal usernames and email addresses.
SpyCloud helps by enabling you to check user passwords against our entire repository of stolen credentials, so you can tell if a password has ever appeared in a breach—whether or not your user was involved. When a user chooses a password that has already appeared in our database, like the name of a popular sports team, you can block them from creating the password or, in the case of an existing password, take action to reset it.
Identify Stolen Passwords Before Criminals Can Use Them
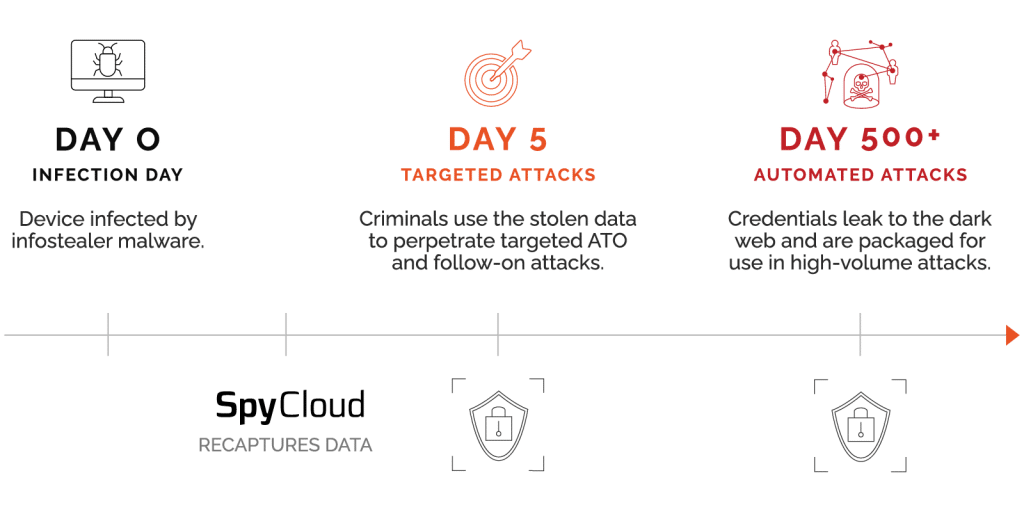
Following NIST guidelines can help organizations mitigate the risk of account takeover—but getting access to exposed passwords early is key. Immediately after a breach, criminals contain stolen credentials within a select group of trusted advisors while they crack passwords and systematically monetize the information. After extracting as much value as possible over the course of 18 to 24 months, they finally allow breach data to leak to the deep and dark web where it can be picked up by mainstream sources. By that point, the worst damage has already been done.
SpyCloud helps you stay ahead of criminals and align with NIST password standards by gaining access to stolen credentials early in the breach timeline. Unlike scraping and scanning tools that collect data only once it becomes widely available, SpyCloud researchers use proprietary tradecraft to get you access to stolen data as soon as possible after a breach occurs.
Reduce Your Team’s Workload with Automation
Some of NIST’s password guidelines can be enforced easily using built-in features of most directory services. Others create substantial work for IT teams. But busy teams don’t have time to research new breaches as they emerge, make that data actionable, compare it to user credentials, and reset compromised passwords at scale.
SpyCloud makes it easy for you to automate even the most challenging aspects of NIST password standards. Read our guide to learn best practices for enforcing NIST requirements, including step-by-step instructions for setting up Active Directory policies.
Read the Solution Brief: Simplify NIST Password Guidelines with SpyCloud

Featured Resources

Understanding the Latest NIST Password Guidelines
Over the years, security professionals have learned surprising lessons about how password policies affect user behavior.

Simplify NIST Password Guidelines with SpyCloud Active Directory Guardian
Read this solution brief to understand the benefits of using SpyCloud to align with NIST password guidelines.

Best Practices for Implementing NIST Password Guidelines
Aligning your enterprise’s password policy with the latest guidelines from NIST can help encourage better password habits and reduce the risk of account takeover.
