Infostealers are not a new topic for us on our blog. In the past, we’ve covered how actors use them to steal sensitive information, and how it’s increasingly easy for criminals to leverage that stolen data to create havoc for individuals and businesses alike. Lately, we’ve also covered some of the enablement services used in conjunction with stealers, like install brokers, to spread malware at an alarming scale.
SpyCloud Labs monitors the infostealer malware space so closely because it’s been a growing factor in cybercrime since the widespread adoption of malware-as-a-service (MaaS) in 2018 and 2019, which exploded in use during the pandemic. Our latest research highlights this growth: on average, each internet user has around a 20% chance of having already been the victim of an infostealer infection. In addition, recent infostealers come with more features than their ancestors, including the ability to defeat or circumvent multi-factor authentication (MFA), steal users’ files, and snag financial information.
To that end, we’ve added three new Windows infostealer families to our recaptured data repository over the past few months:
Here’s what you should know about each of them.
Xehook
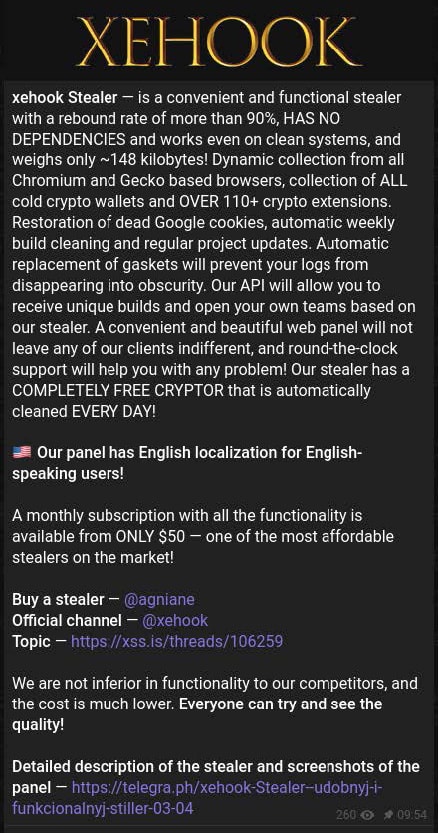
A Xehook stealer sales post on Telegram.
The Xehook Stealer is an emerging threat that targets financial information, focused on stealing banking credentials, cryptocurrency private keys, and other personal information. Xehook shares some of its codebase with the open-source MaaS Cinoshi, and other researchers have speculated that it may be operated by the same team behind the Agniane Stealer. As a new stealer that was discovered in January 2024, Xehook may be benefiting from a lack of detection capabilities, enabling it to bypass anti-malware software.
Xehook is notably cheaper than many of its competitors, advertising a monthly rate of only $50 compared to competitors that charge upwards of $150 or $200 for a monthly subscription.
First introduced by the developer of LummaC2, Xehook claims to ship with the ability to regenerate Google authentication cookies and supports other common functions including autofill and saved credit card theft. SpyCloud Labs has observed Xehook being delivered in small but consistent numbers through install brokers.
Meduza

A Telegram post by the operator(s) of Meduza showcasing new features in an April 1 release of the malware.
With the rising popularity of online gaming, cybercriminals have found a lucrative niche to exploit. The Meduza Stealer is another new infostealer that has been observed by SpyCloud Labs as targeting online gaming platforms. Meduza popped up on the scene in the summer of 2023 with several campaigns leveraging gaming-related lures, capturing login credentials and in-game purchases, which are then sold on the dark web.
Based on SpyCloud Labs’ analysis of recent logs, Meduza appears to be commonly delivered through cheats, online skins, and cracked versions of popular games including Counter Strike 2 and Fortnite. Meduza’s official distribution channels are actively maintained, with several recent updates to the malware released in recent weeks. This may suggest a longer life for Meduza than other stealers because malware that receive frequent updates tend to be preferred by criminals as they are more likely to stay apace of new techniques.
Meduza is sold via Telegram as well as several Russian-language hacker forums like XSS and Exploit, and offers plans ranging from $199 for a one-month subscription, to $1,199 for lifetime access, as of the time of writing.
Elusive
True to its name, the Elusive Stealer is a stealthy threat that has proven challenging to detect and mitigate. This infostealer uses advanced encryption techniques to shield its activities, making it difficult for traditional security measures to spot.
Notably, Elusive also includes functions for stealing photos from an infected device, an unusual choice for a stealer due to the size of photos as well as the lack of easily monetizable information contained therein. Novelty aside, infostealers targeting a user’s photos present an additional risk of exposure to the victim given the often personal nature of photos saved to a user’s device.
Of the three, Elusive is the least active new stealer detected by SpyCloud Labs, and it remains to be seen whether Elusive will gain traction in the MaaS community or fizzle out like dozens of other short-lived stealers, such as 420Stealer, Collector Project, or Coronarecovery.
Reduce risk with these infostealer malware countermeasures
As infostealers continue to evolve and pose significant risks, it’s crucial to reinforce the cybersecurity measures you have in place to safeguard devices, digital identities, and sensitive information. Here are some countermeasures we recommend implementing to prevent and remediate malware exposures that will protect your organization from follow-on attacks like session hijacking and ransomware:
- Implement a good antivirus program
- Enforce advanced authentication through MFA and passkeys
- Implement cookie expiration and invalidation policies
- Make sure you have comprehensive management over your devices and networks, including a strict bring-your-own-device (BYOD) policy
- Continuously monitor for malware exposures in the criminal underground
- When a malware exposure is detected, be sure to isolate, image, and wipe the device, if accessible, and:
- Reset passwords and usernames for affected applications
- Invalidate the user’s web sessions to prevent session hijacking
- Review all activity and access logs for the user within affected applications to confirm that detected activity is coming from expected IP address ranges and geographies and that all behavior fits the expected profile of the user
SpyCloud Labs keeps a tight pulse on the criminal underground and adds new malware families to our daily ingests as they surface.



