If you had to guess the industry most vulnerable to cyber criminals, you might think about something like retail, where there are millions of consumers making online transactions every day, or banking and finance, where all those transactions get processed and where the money ends up.
You would be wrong.
While those industries are certainly vulnerable, the industry with the highest risk is telecommunications. Like retail and banking, telecom companies are rich in data and have huge numbers of customers, both of which make them valuable targets for the bad guys. But not only are they valuable, they are also exposed.
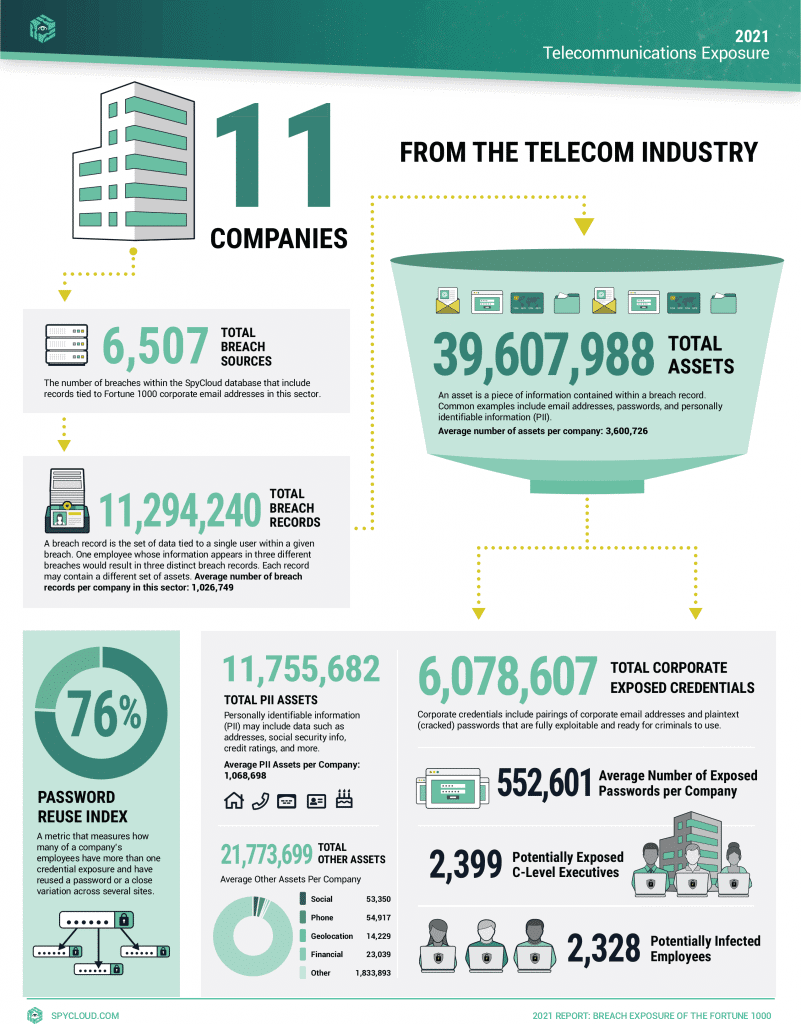
My colleagues at SpyCloud analyzed our database of over 100 billion assets collected from data breaches to examine the exposure of Fortune 1000 companies, and they found 543 million breach assets tied to employees at those companies – up 29% from last year.
For the 11 Fortune 1000 telcos specifically, the researchers found 6 million exposed credentials, including 2,399 exposed C-level executives, and 2,328 employees infected with credential-stealing malware. While technology companies had more total exposed credentials, when averaged out per company, telcos were the worst with an average of 552,601 exposed credentials and 212 infected employees per company. That works out to eight exposures, on average, per employee.
In fact, when averaged by company, telcos led all industries in the Fortune 1000 with the most exposed employee phone numbers and personally identifiable information (account secrets, financial details, and social media handles) on the criminal underground.
This year’s analysis found a big spike in phone numbers exposed in data breaches. That is particularly troubling because phone numbers can be used to bypass multi-factor authentication, which many companies rely on to bolster their login process. Criminals can combine a phone number with some light social engineering to divert a victim’s phone service to their own device. Once they have control of someone’s number, they receive all SMS-based authentication messages and can easily log into sensitive accounts undetected.
Unfortunately, the problem doesn’t end with telecom employees. SpyCloud also identified 59,669 potentially infected consumers of their services. These are users of the telecoms’ consumer-facing sites, where keylogger malware is harvesting the usernames and passwords (along with other personal and system information) for bad actors. The true number is likely higher because the analysis excluded many consumer-only domains from the analysis. It also removed credentials with usernames instead of email addresses because it’s unclear whether they are employee or consumer records. However, each one of these is at extremely high risk of account takeover, identity theft and online fraud, which can result in substantial losses for individuals and brand damage for affected businesses.
A big reason for the telecom industry’s vulnerability is its high rate of password reuse. The report found that 76% of employees have reused passwords, or close variations, across several sites. The use of weak or compromised passwords is the leading cause of account takeovers. Once a cyber criminal knows the password for one account, they will test it on other accounts, and if the account owner has reused the password, the criminal has easy access. If the stolen credential includes a company email domain, the bad guys have a pretty good idea of where they might be able to access a corporate network and potentially valuable enterprise systems, customer data or intellectual property.
That makes it extremely important for companies to identify vulnerable accounts early so they can lock them down and force password changes before they can be compromised. Cybersecurity teams should train employees about preventative measures such as multi-factor authentication, use of password managers, and recognizing phishing attempts, but they should also leverage proactive monitoring services that send alerts when employee information is found in a data breach.
With so many employees and customers, telcos will continue to be a target for criminals, but taking preventative steps can go a long way to thwarting attackers and protecting company assets.