Stop Telecommunications Fraud & Mobile Account Takeover
Telecom providers share the daunting task of securing a high number of subscriber and employee accounts against account takeover, and unmasking the fraudsters perpetrating these crimes.
Not only has the use of stolen credentials and SIM swapping grown as ways to compromise subscriber accounts, but criminals are also going after your employees and third parties, too. To steal valuable consumer data, criminals are taking over their accounts and perpetrating business email compromise scams. The risk that these crimes present to personal and corporate assets is huge.
For mobile network operators (MNOs), managed service providers, and even cable companies and ISPs, SpyCloud simplifies account security, and empowers investigators to quickly resolve fraud cases. Both use cases leverage the largest collection of recaptured data in the world. With more than 400B assets from data breaches and malware-infected devices made actionable, SpyCloud enables telcos to protect themselves, their employees, and their subscribers from cyberattacks.
These days, your customers’ credentials are stolen and instantly used.
It’s time we fight back.
Protect Mobile Subscribers From ATO
Mobile subscribers are extremely vulnerable to account takeover. Weak and reused passwords across mobile accounts and apps provide easy access to the subscriber’s financial details (stored credit cards, for example, that can be used to make fraudulent purchases). Phone numbers are targeted because many platforms rely on a one-time PIN sent via text or phone call to authenticate their customers.
Knowing only the customer’s mobile network operator, criminals can perpetrate a SIM swap attack – an increasingly common targeted attack that enables criminals to take control of a subscriber’s phone number and send and receive calls and texts as if they were the customer, making it easy to bypass multi-factor authentication and get into many other accounts owned by the victim.
SpyCloud secures the mobile experience and helps operators stay ahead of SIM swapping by checking subscribers’ passwords at the point of login against billions of credentials that SpyCloud researchers have recovered from data breaches. MNOs can offer account takeover prevention and dark web monitoring to their subscriber base, which can go a long way in rebuilding the eroded trust that many subscribers have in their providers.
Special Report: Telecommunications Industry Credential Exposure
Prevent ATO of Telecom Employee Accounts
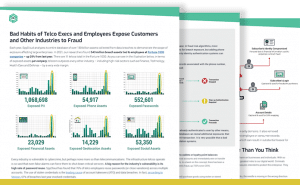
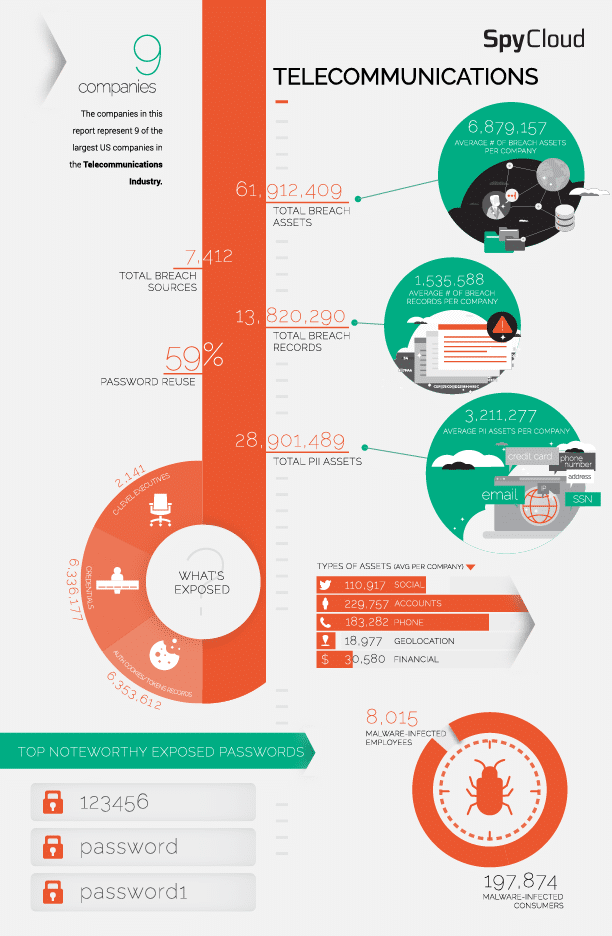
Recent SpyCloud research reveals that more than 6 million pairs of corporate email address + plaintext password pairs tied to Fortune 1000 telecommunications employees are available to cybercriminals. These can be easily used to gain access to corporate systems containing customer data, funds, and PII, perpetrate business email compromise, and then exploit reused passwords to gain entry into personal accounts.
For the last four years, the use of weak or stolen passwords is the #1 hacking technique aiding bad actors in taking over accounts. However, if breach data is recovered and quickly reported right after it is stolen, passwords can be reset before criminals have the chance to exploit them.
SpyCloud helps you secure employee accounts against ATO and BEC through proactive compromised credential monitoring. You know immediately when employee data is found in a breach – within days – so you can force password resets. Our team of researchers embedded across the dark web continuously uncover compromised credentials and employee PII before criminals have the chance to take action.
Managed Service Providers Protecting the Enterprise
Enterprise organizations often sign up with a mobile operator MSP to manage everything from thousands of computers and devices to databases in the cloud and security services. These large organizations are susceptible to ATO attacks for all the same reasons consumers are vulnerable, and the damage can be exponential.
With SpyCloud’s solutions, MSPs can warn enterprises when their data is exposed on the dark web and provide an immediate solution for preventing account takeover.


Investigating Fraud in Telecommunications Organizations
Most telecom operators have investigative teams in place tasked with identifying bad actors and the origins of fraudulent activity, including mobile ATO, subscription fraud, and BEC. Drawing on billions of records SpyCloud has recovered from third-party breaches, investigators can piece together decades-worth of criminals’ digital breadcrumbs to unmask the identities of cybercriminals engaging in fraud. SpyCloud has provided invaluable evidence to law enforcement teams and investigators around the world, helping them track down bad actors and bring them to justice.