Combolists are often thought to contain a gratuitous amount of fake or engineered data, or otherwise ineffectual at their claimed purpose, and, thus, frequently disregarded by security researchers and defenders alike. However, initial research by SpyCloud suggests the way that new combolists are being generated may challenge those assumptions.
SpyCloud’s security researchers have discovered that some combolists have shockingly high validity rates, and many prove to have a significant match to credentials sourced from malware records.
What is a combolist?
Combolists are created when criminals compile lists of previously breached credentials for websites or applications. Targeted combolists may be tested by the creator using automated account checkers to “verify” them as being valid for a specific website or service. For most, the usefulness of combolists is found in credential stuffing attacks, where credentials from a data leak/breach on one service are used to attempt to log into other services (which can be a related or unrelated service).
History of combolists
Combolists have a high percentage of duplicate records as they are commonly crafted from past data leaks or breaches. Sometimes their content may even be duplicates of other combolists themselves – duplicates of older breach data. However, we can’t completely discredit old passwords. When people use old passwords or variants of them, it makes it that much easier for the criminal to execute account takeovers, especially with massive combolists that were published years prior and with websites or services that lack multi-factor authentication protection.
In the past, collections of combolists containing billions of email addresses and passwords have been shared via the hosting service “MEGA,” which offers low-cost and free file storage. Additionally, in 2020, due to the migration of almost everything in the cloud, combolists-as-a-service (CaaS) became a subscription model for cybercriminals. With this service, buyers pay a monthly membership to access a vast array of stolen credentials. As such, they can be used in credential stuffing or account takeover attacks.
Validity of combolists
From a security standpoint, combolists were usually not highly sought after. They’ve been more of an afterthought with, at best, questionable credibility. Not only do they have high levels of duplicate records, but they also have a low percentage of validity, potentially due in part to shoddy, incomplete, or completely missing validation protocols on the part of the maker or seller.
The validity of combolists can be determined by the source they came from. SpyCloud researchers hypothesized that a significant contributor to validity would be stealer logs, acquired from malware running on infected devices. Malware can be very stealthy and generate stealer logs, which include critical data for executing cybercrime, such as the login credentials, device and cookies, auto-fill data, extensive information about the device/OS and so much more that is exfiltrated directly from the infected machine. Therefore, combolists are evidently valid if they are made from these stealer logs, which can be seen in their quantifiable collision rate, or match rate (which shows a percentage of (exact) matching data from one set to another log) to the various types of stealer logs.
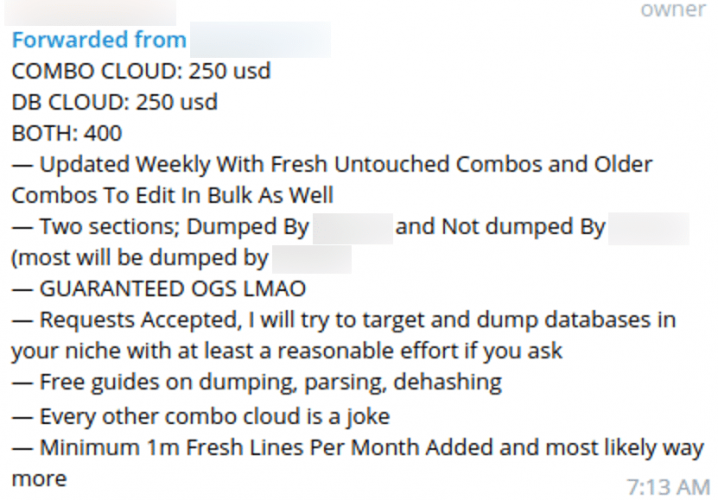
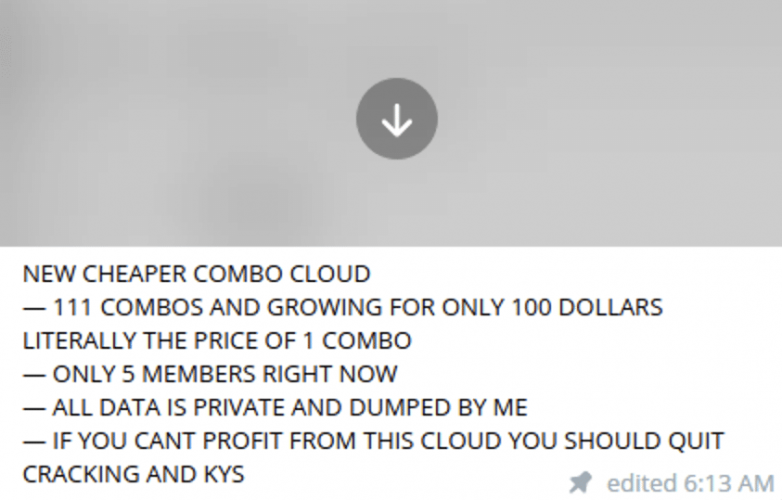
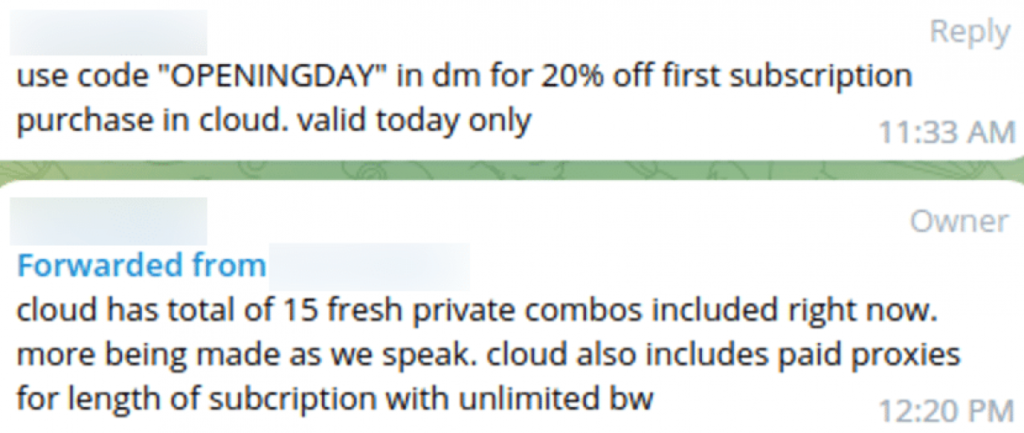
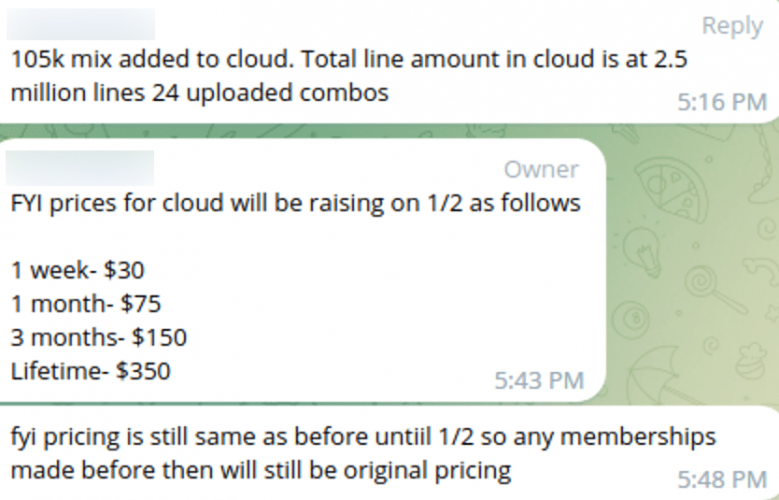
The following screenshots represent combolist posts from actors alongside SpyCloud’s analysis of match rates to stealer logs in our database:
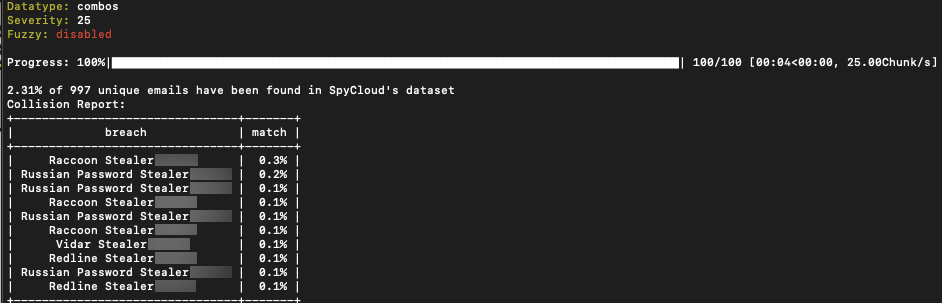
Threat actor LeakBase from BreachedForums posts 99k HQ Combolist with a low 2.3% match to stealer logs
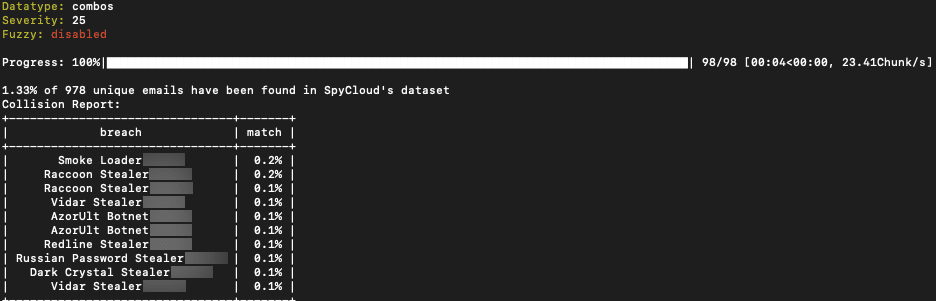
Threat actor HqComboSpace from BreachedForums posts 884K HQ Crypto Target Combolist with a low 1.3% match to stealer logs
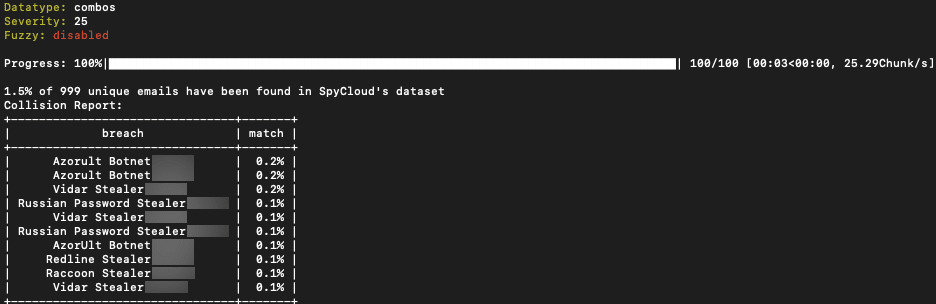
Threat actor nestor from BreachedForums posts 100k Email:Pass Combolist with a low 1.5% match to stealer logs
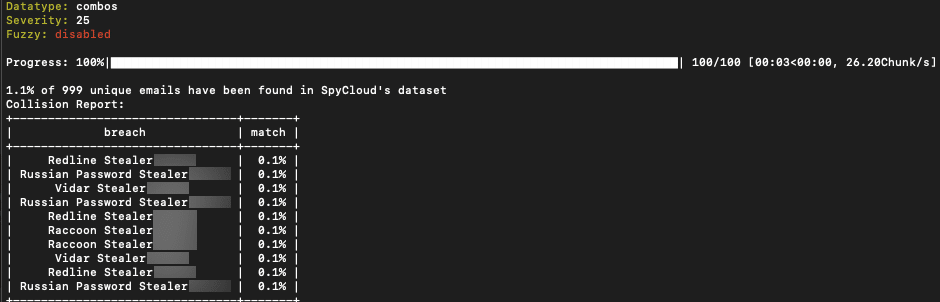
Threat actor NoDebt from NulledForums posts 450k Combolist with also a low 1% match to stealer logs
Combolist correlation to stealer logs
SpyCloud security researchers have begun discovering increased data repetition between stealer logs and combolists. This redundancy significantly increases the danger of combolists because stealer logs are not the typical data leak or breach that you see publicly disclosed by a company. Instead, stealer logs come from infostealer malware, which can be installed on a victim’s device without their awareness. Infostealers extract a variety of authentication information from infected computers which often includes usernames, email addresses, passwords, browser cookies, and autofill data. Our research shows a percentage of 5%-98% match of stealer logs in combolists ranging from 2,000 credentials all the way to 44 million credentials.
Since we first published this blog, we’ve continued to track the evolution of combolists. See our newest research on combolists and their overlap with stealer logs here >
Threats of valid combolists
Combolists have never been the main weapon in a cybercriminals’ arsenal. Combolists have been around for a long time, but utilizing stealer log data to craft them is the up-and-coming way for cybercriminals to not only monetize the stolen data, but also use them in credential stuffing, account takeover or other targeted campaigns. With this new combolist crafting method, they are more dangerous than ever before. Here are a few examples that explain why:
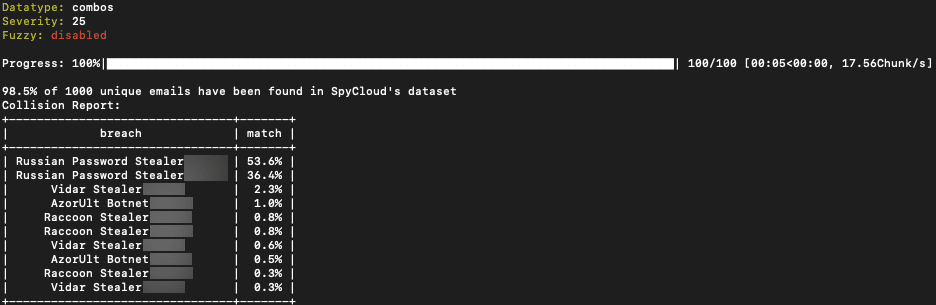
Threat actor from BreachedForums posts 100k Combolist Collected from logs with a high 98.5% match to stealer logs
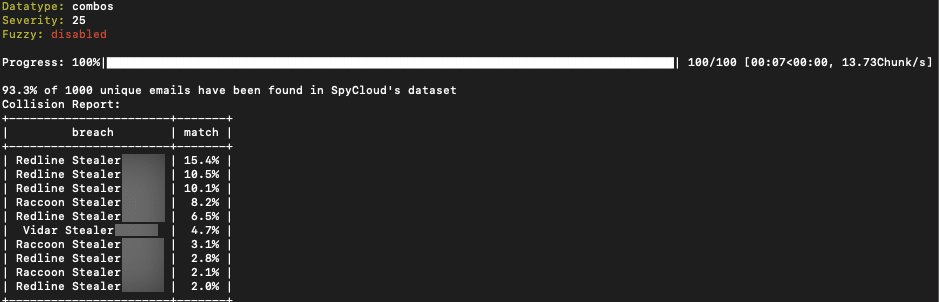
Threat actor from BreachedForums posts 100k Fresh Email_Pass with a 93% match to stealer logs
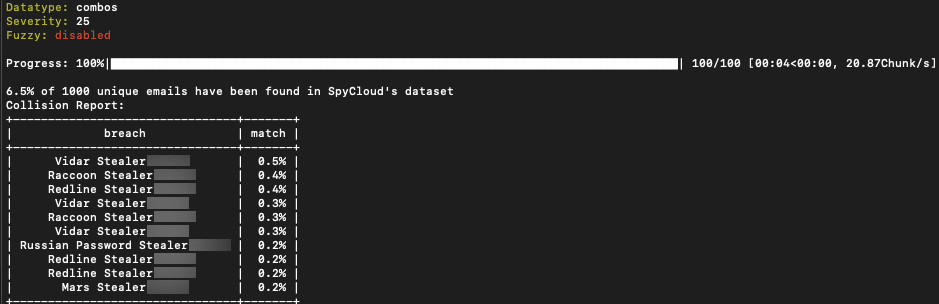
Threat actor MegaCloud from BreachedForums posts a 50k Fresh Combolist with a 6.5% match to stealer logs
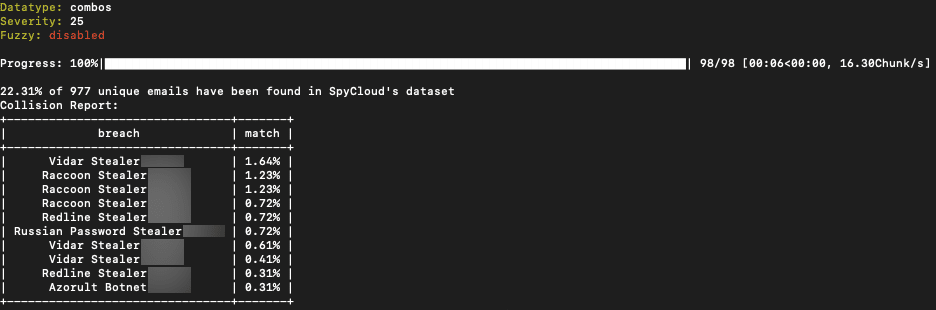
Threat actor from BreachedForums and Telegram posts 80k UHQ Combolist with a 22% match to stealer logs
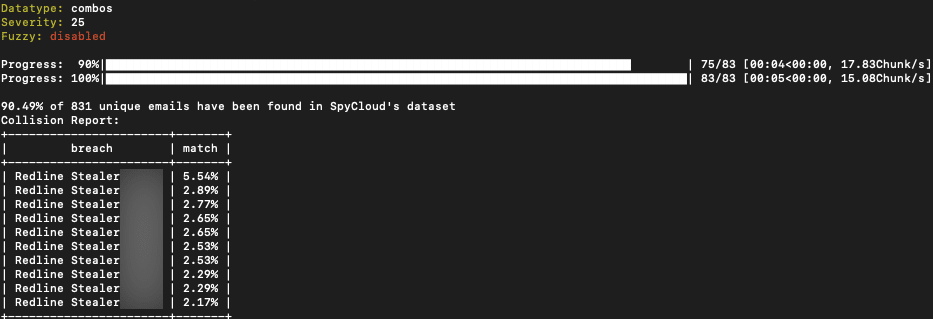
Threat actor from BreachedForums posts 9k Combolist from RatLogs that has a 90% match to stealer logs
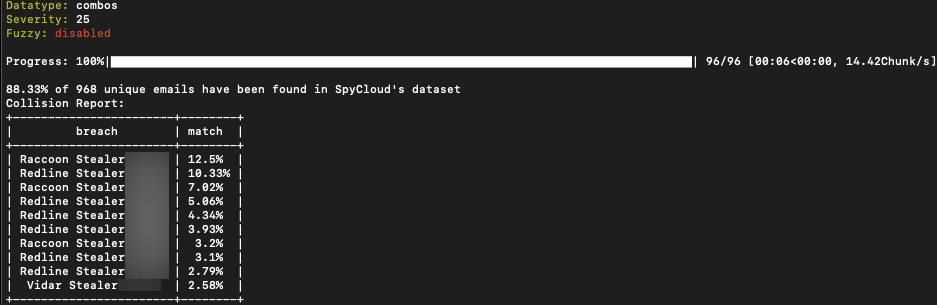
Threat actor from BreachedForums posts UHQ 316k Combolist that has a 88% match to stealer logs
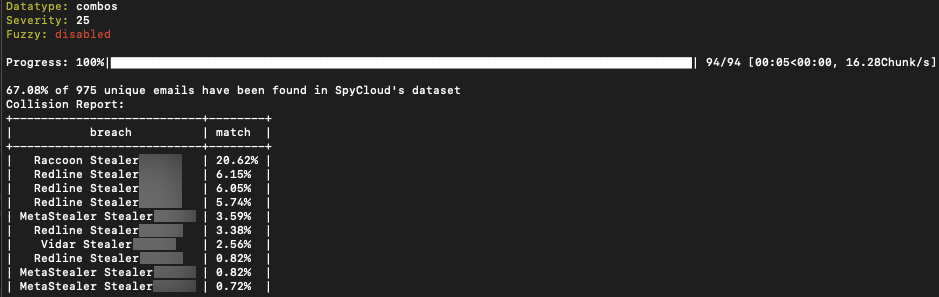
Threat actor from NulledForums posts 72k Combolist with a 67% match to stealer logs
Combolists of the future, powered by infostealer malware
Not all combolists are made the same, nor are they all valid. Combolists have long been an afterthought due to their questionable credibility, until recently. In the past, combolists were commonly generated by cybercriminals through past breaches and can even be fake, engineered data for the purpose of notoriety. Credentials from these sources are often old and invalid, especially if the company that has been breached has required their users to change their passwords.
Today, researchers from SpyCloud have noticed a new trend of combolists being generated from stealer logs. Such combolists have a tendency to be of high quality, as the credentials are harvested fresh out of stealer logs. Stealer log data comes from malware and seizes the latest, valid, and critical personal information directly from an infected machine’s browser and autofill data – the home of login credentials for a plethora of websites.
Combolists generated from stealer logs are out there and they are now undeniably a threat. It’s an alarming plot twist, but one that shouldn’t surprise us. Criminals are always innovating – but it’s our job to keep pace, and this discovery could be the all-important denouement.



