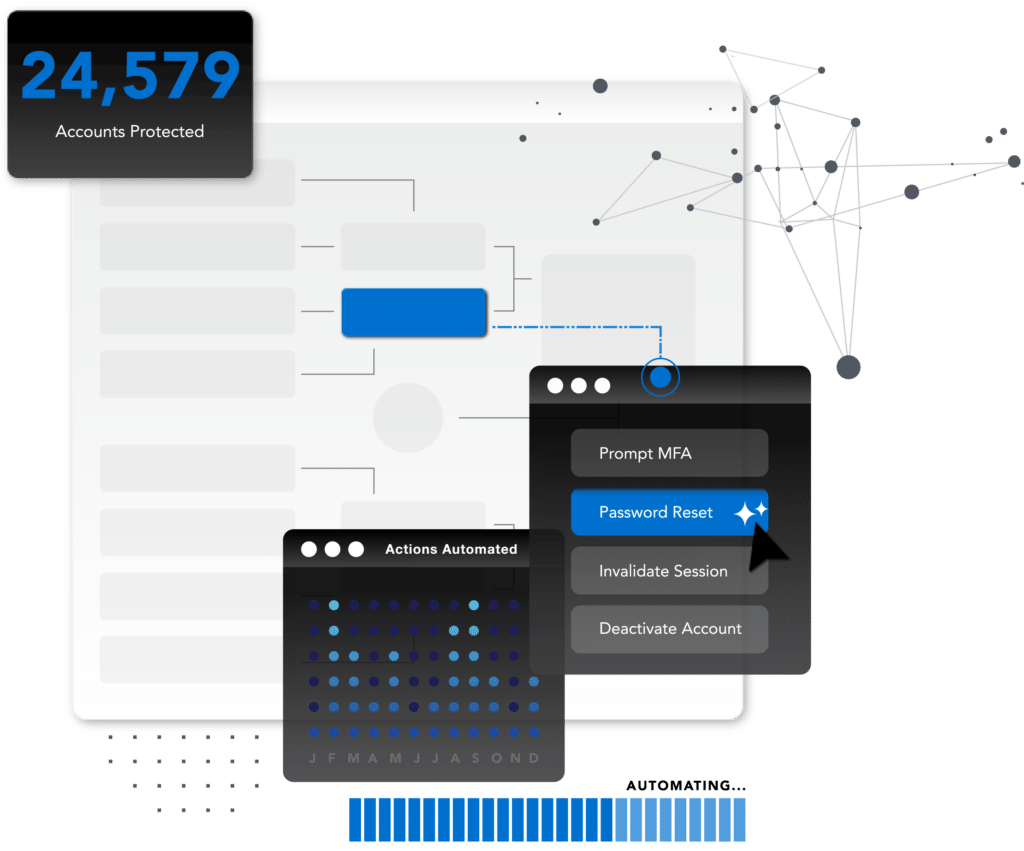
Automated ATO Prevention
SpyCloud researchers recapture data early in the breach and malware infection timeline, enabling you to stay ahead of both targeted and automated account takeover attempts. Our automated solutions plug into existing workflows and integrate with common directory services and SOARs to make ATO prevention seamless for busy teams.
Next-generation ATO prevention for the modern enterprise
To prevent account takeover attacks, organizations must find ways to detect and reset compromised credentials. However, each of these only addresses one aspect of the problem. SpyCloud delivers the next generation of account takeover prevention, which focuses on not only addressing ATO via stolen credentials, but also malware-stolen session cookies as criminals evolve their tactics to include hijacking web sessions.
High-volume darknet data
Data collection at the scale you need to stay on top of threats is impossible for most enterprises – with actionable insights from the lower and core layers of the darknet, where high-value data is traded and sold
Malware insights
Visibility into employees’ managed and unmanaged malware-infected devices accessing your network so compromised passwords can be reset and stolen web sessions can be invalidated, thus locking out bad actors
Enriched analytics
Data enrichment that offers contextual insights, including the source, breach description, and the actual breached plaintext password to increase its actionability – with access to cracked passwords
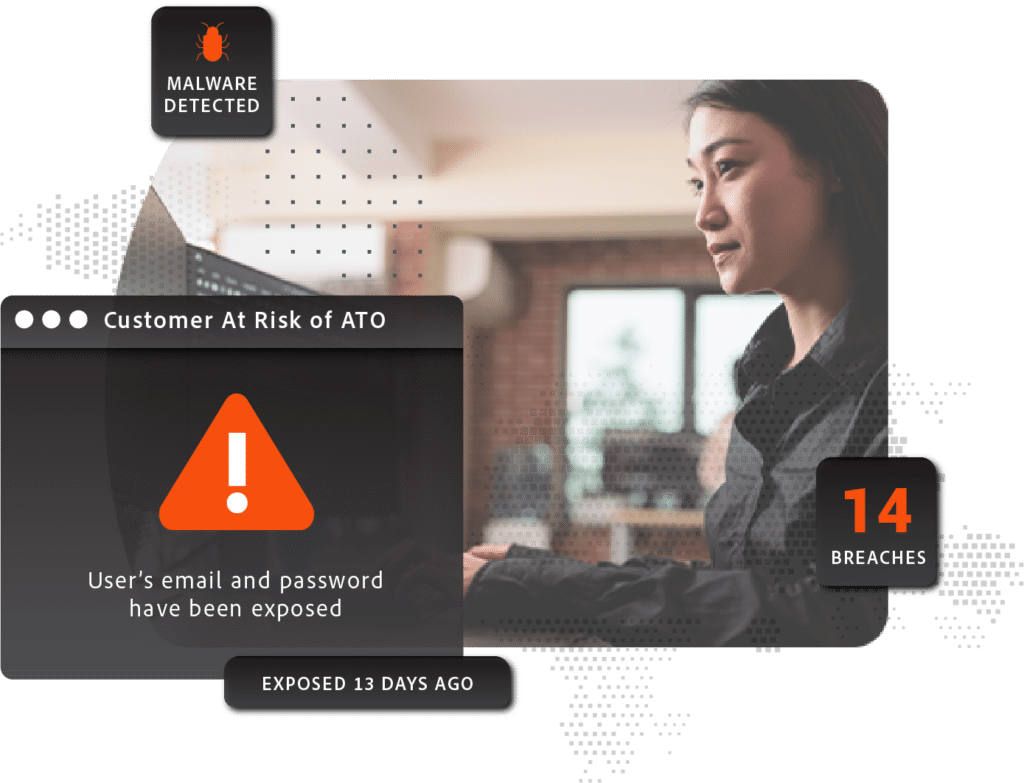
Corporate account takeover poses a substantial risk to enterprises. With access to one employee’s account, an attacker can easily move laterally within a corporate network or gain access to sensitive consumer data, intellectual property, competitive information, or funds.
Reduce data breach risk
SpyCloud’s Employee ATO Prevention reduces your risk by alerting you when your employees’ credentials appear on the criminal underground so you can take immediate action.
Shorten exposure window
When an employee’s credentials appear in a newly-ingested data breach, you can act quickly to validate their identity and reset their password before it's used to cause harm.
Continous credential monitoring
Leave the burden of scouring the darknet for exposures relevant to your users to SpyCloud. Our solutions enable automatic and continuous monitoring of your employees’ credentials and authentication cookies against the largest repository of compromised data in the industry so you can focus on more value-added activities.
Automated prevention
Seamless integrations into existing workflows and applications, including popular directory services, SIEMs, and SOARs, allow enterprises to automate password resets and make sure the right teams are armed to remediate malware-infected devices, users, and applications effectively.
“The SpyCloud API was super easy to integrate. It took a day and a half for our engineers, and then it was just up and running. We’ve had the integration in place for a year now and had zero issues, zero downtime. On the technology side, it’s an enterprise-grade API for us.”
– Global Fintech Company
Read case study
Explore SpyCloud
Enterprise Protection
Reduce your risk of ransomware and other critical attacks – acting on known points of compromise
Learn more
Consumer Risk Protection
Take a proactive approach to combating account takeover and stop high-risk attacks tied to malware
Learn more
Investigations
Efficiently piece together criminals’ digital breadcrumbs to reveal the identities of specific adversaries engaging in cybercrime
Learn more
Data Partnerships
Access comprehensive breach and malware data to add value to security and fraud detection products and services
Learn more
SecOps
Efficiently secure employee identities and safeguard corporate data and critical IP from cyberattacks.
Learn more
Threat intel teams
Investigate and stop threats with insights well beyond raw data and IOCs
Learn more
Cybercrime Analytics
Learn about the new way to disrupt cybercrime with automated analytics that drive action
Learn more
Test our data
We’re confident you’ll get more matches with SpyCloud – let’s do a match rate test
Learn more
Check your exposure
Uncover threats to your organization like malware-infected employees, stolen session cookies, and recency of breach exposures
See your results
SpyCloud offers out-of-the-box API integrations with top technology vendors across SIEM, SOAR, XDR, TIPs and more – delivering Cybercrime Analytics at scale for analysis, detection, remediation and automated workflows.
Automated ATO Prevention FAQs
In an account takeover attack, criminals use another person’s login credentials, most often by leveraging reused or similar passwords from previously breached sites, to gain access to existing accounts. Once inside, they make unauthorized transactions, siphon funds, and steal corporate data or personally identifiable information (PII) to use for other purposes, or simply to sell to other attackers on the dark web.
We Choose Weak, Common Passwords
Regardless of all the advice out there about the importance of strong passwords, users will choose sequential numbers and dictionary words or add a ! or 1 to the end of their password (especially when prompted to change passwords every 90 days by corporate IT). Memorable passwords may seem unique to users – but they often aren’t. Among the millions of passwords SpyCloud recovered from breaches last year alone, “123456789” was found over 35 million times. “querty123” was found over 13 million times, “iloveyou” 3 million times, and “football” 1 million times. Unless these passwords are banned and password complexity requirements put in place, some users will always select easy-to-remember passwords.
We Reuse Passwords Across Multiple Accounts
In a Google study, 66% of people admitted to reusing the same password across one or more accounts. SpyCloud’s own research shows that even employees at some of the world’s largest and most innovative companies share this bad habit; 62% of Fortune 1000 employees are reusing passwords across work and personal accounts. When one site is breached, cybercriminals can access any other accounts that are protected by the same credentials. Using a password manager is a way to kick this habit, but only some flag compromised passwords and stop users from choosing them.
We Click Links & Download Attachments from Unfamiliar Sources
To the dismay of security teams everywhere, users habitually click any link or file that lands in their inbox, whether they recognize the sender or not. Inevitably, this leads to users’ machines becoming infected; 94% of malware is delivered by email! Some malware can harvest usernames and passwords, browser cookies, autofill data, and more – putting those users at extremely high risk of ATO.
If it was, we’d be seeing less of an account takeover problem as businesses adopt MFA. Requiring users to provide something they know (a password) plus something they are (biometrics) or something they have (smartphone token), is an important layer of protection and will deter some cyber attacks. Some – not all. It is still possible via many avenues to bypass MFA. Even still, MFA causes friction between the user and the service. Most of us will buck at pulling out our phones to tap ‘approve’ on a login multiple times a day and may turn MFA off at the first opportunity.
Password managers can help, but even when companies mandate their use, most employees don’t use password managers at home or for personal services. This wouldn’t be such a problem if password reuse wasn’t so rampant and the lines between personal and employee accounts and devices weren’t already blurred. Confusing BYOD policies and the use of employee accounts on personal devices only make the situation worse.
Password rotation policies actually benefit threat actors more than the users. Criminals test stolen credentials on a regular basis knowing that eventually, the user will think they’re safe and reset their password to one that has already been compromised. This blog on password rotation summarizes our point of view well.
It's time for next-gen ATO prevention
Get the buyer's guide
Check out key considerations for choosing an enterprise ATO prevention solution.
Account takeover 101
Access a plain-English primer on the latest attack methods and strategies for prevention.
Get a demo
Experience how SpyCloud can automate account takeover prevention across your entire enterprise.