The move to a passwordless future is a positive development. A day when everyone’s accounts are less vulnerable to criminal activity? That’s a huge step forward in SpyCloud’s vision for making the internet a safer place. Unfortunately, that day is still a long way off. Passkeys, while a valiant step in the right direction, are simply an improvement on a per-application password methodology and present many of the same challenges when it comes to maintaining the security of user accounts.
In response to improvements in passwordless technologies, criminal ecosystems are rapidly adapting by:

Moving their focus from account credentials to account recovery methods

Developing ways to steal passkeys

Working around passkeys and other passwordless authentication methods with session hijacking attacks
At SpyCloud, we have a concentrated focus on recapturing breach and malware-exfiltrated data at scale, while researching and recovering new forms of data bad actors find valuable for their criminal intentions to help enterprises quickly react – invalidating stolen authentication data to keep their users and their business protected. Passkeys, along with other technologies that will be developed in the future, are part of that mission.
The Current Landscape of Passwordless Authentication
As technology transitions, it would be ignorant to assume that any new solutions are immune to cyber compromise. This is true in the case of the transition from passwords to passwordless.
Since passwords are a simple, cost-effective, and ubiquitous security measure that is easy to implement and has virtually no learning curve for the average user, they are likely to be around for some time. But in the meantime, let’s review the options for passwordless authentication that exist now.
Passwordless authentication is a security control concept designed to replace traditional passwords. And for decades, new methods of augmented authentication have approached spanning categories of hard tokens and soft tokens. Most commonly used are:
HARD TOKENS
YubiKey
Proprietary hardware-based authentication device that enables secure access to computers, networks, and online services through the use of one-time passwords – developed by the FIDO Alliance.
Biometrics
Uses unique personal identifiers, like a retina scan, facial recognition, or fingerprint that delivers access through integration directly with the hardware or application.
SOFT TOKENS
Time-based One Time Passwords (TOTP)
A type of two-factor authentication (2FA) where unique, time-based numerical passwords are created. Offering an additional layer of account security through a seamless and easy to use process that is also available offline.
Passkeys
Designed in accordance with FIDO, a passkey is a digital credential that is uniquely tied to a website or application that enables authentication without the need for a username, password, or even additional authentication factor.
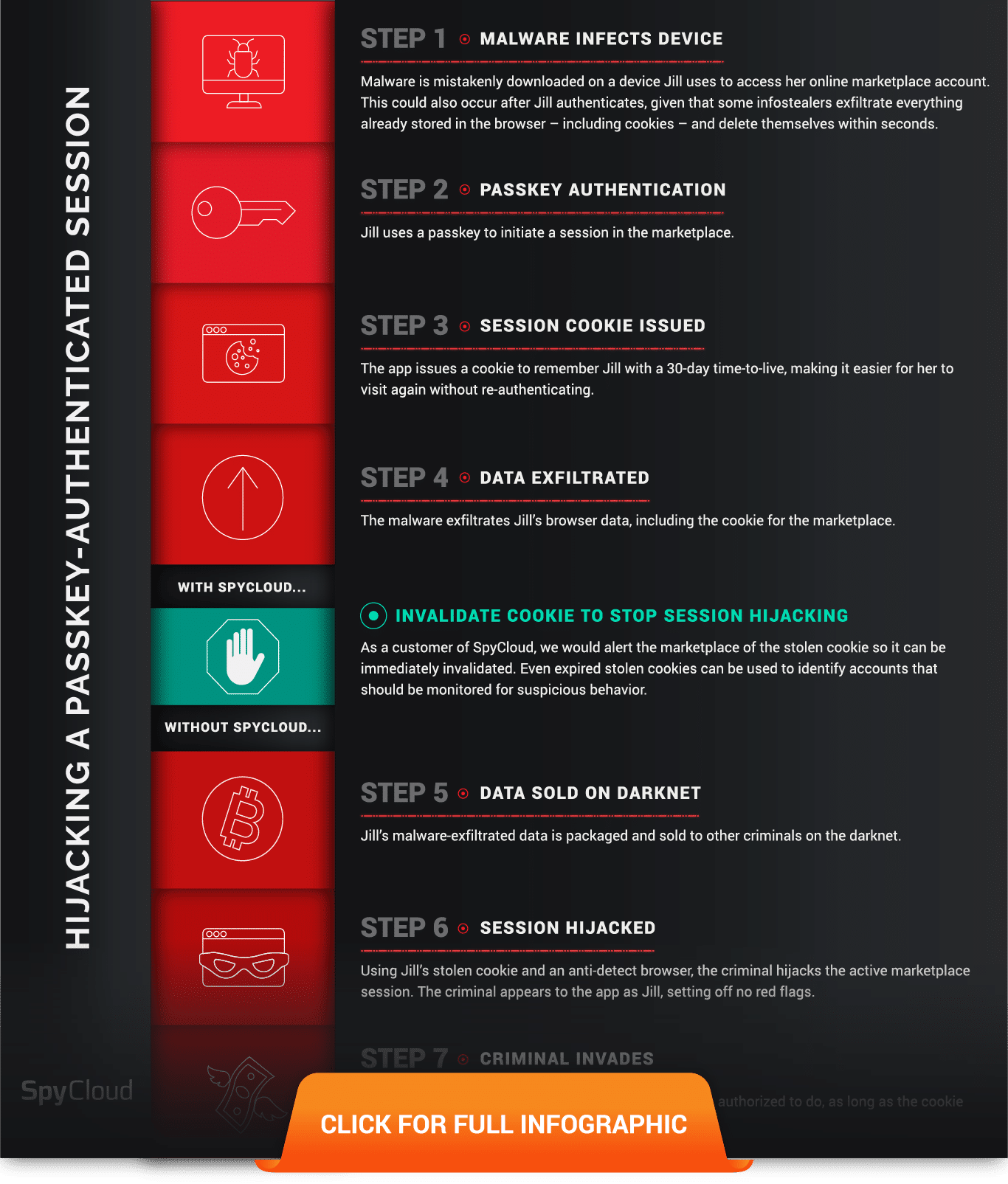
Account Takeover in the Passkey Era: Session Hijacking
While they are the next iteration of passwordless technology – and one generating a lot of excitement and news – passkeys are not immune to compromise. They are more secure than some authentication methods, and definitely less prone to poor hygiene practices, and in terms of usability, significantly easier to keep track of access to everything across our digital footprint.
That said, any one layer of authentication is never going to fully block a bad actor from getting in.
SpyCloud solutions evolve as criminals evolve, as we aim to keep customers agile in responding to ever-changing criminal tactics. Over the last 12-18 months, we’ve begun seeing criminals go beyond stolen passwords to perpetrate account takeover. They’ve moved on to what we call next generation ATO: session hijacking.
With the high volume of malware-exfiltrated session cookies available on the darknet, this attack is becoming more and more popular. Infostealers siphon everything contained within an infected user’s browser, including session cookies. These cookies are sold (and sometimes given away) on darknet marketplaces and enable an attack that only takes a few seconds, allowing a criminal to impersonate the legitimate user without raising red flags.
Session hijacking requires no credentials and bypasses MFA – and renders passkeys irrelevant.
All it takes is a stolen cookie for an active session and an anti-detect browser for a criminal to perpetrate session hijacking. These attacks bypass any strong authentication mechanisms that are in place. It doesn’t matter if the user logged in with a username and password, completed an MFA challenge, or used a passkey. And if the stolen cookie is tied to an active SSO session, that could open the door for a cybercriminal to 200+ applications for the average large enterprise.
Whether a session was originally authenticated with a password or a passkey, every site and application assigns a cookie/token – a string of characters that the site or server uses to remember visitors and make it easier to visit the site again without authenticating. These cookies vary in terms of “time to live,” but you’d be surprised how many of them remain valid for weeks, months, or even longer.
If you’re asking yourself, ‘how many of these cookies are really out there for criminals to use?’ Last year alone, SpyCloud recaptured over 20 billion session cookies stolen by infostealers.
If you’re asking yourself, ‘can we do away with cookies if they present such a huge risk?’ Frankly, no. Cookies are fundamental to the way the internet works.
Needless to say, there is enormous opportunity for criminals when it comes to session hijacking, which will remain a critical threat even as passkeys grow in popularity.
Interested in exploring session hijacking prevention?
Learn more about SpyCloud Session Identity Protection.