In the middle of the 20th century, a purchaser of a new car could be fairly certain that most of the components of their new car were stamped with the logo that adorned its exterior. Even with the advent of new automation technologies, internal components were still predominantly manufactured by the vehicle manufacturer in-house or nearby and assembled into a finished car.
The car that is rolling off the assembly line today has emerged from a complicated ecosystem of intertwined supply chains representing thousands of individual companies and suppliers of components as small as a single plastic clip or computer chip.
Where once there existed massive divisions focusing on the production of specialty parts within large car brands, these components now often originate from companies few have heard of, in cities and states far afield of the car manufacturer’s assembly lines, making their way to their final place of assembly through a complicated dance of specialists and partnerships.
What does this have to do with cybercrime, you ask? This journey from relatively unitary manufacturing to a complicated process involving increased specialization is a convenient metaphor for the changes that have taken place within the cybercriminal ecosystem over the prior decade.
Keep reading as we dig into the intricate world of cybercrime enablement services.
Alternatively, you can listen to our team talk about this same topic on the Cyberwire Daily Industry Insights podcast.
Listen now: Cyberwire Industry Insights Podcast
The evolution of the cybercrime ecosystem
Historically, cybercriminals had to be highly-skilled in a number of areas. For many years, “sophistication” was used as a byword for success when discussing specific actors or groups, and for good reason. Lacking a defined ecosystem of products and services, actors had to figure out how to do almost everything themselves in order to be successful – from authoring and distributing malware, to figuring out ways to avoid detection, to scaling their distribution efforts with the hopes of getting lucky and seeing some profit.
Now, however, as the cybercrime industry grows into a reported $9 trillion global industry, the average Joe doesn’t have to be a super cybercriminal to collect and take advantage of stolen data. And while members of the cybersecurity community still talk in terms of sophistication, it means far less to the overall efficacy or risk posed by a specific actor or threat than it once did.
Today, we see specialists for each step of the cybercrime process. Anything a criminal doesn’t want to do – or can’t do – themselves, they can simply buy as a service. True to their opportunist nature, bad actors are taking every shortcut they can to outsource and gain efficiency.
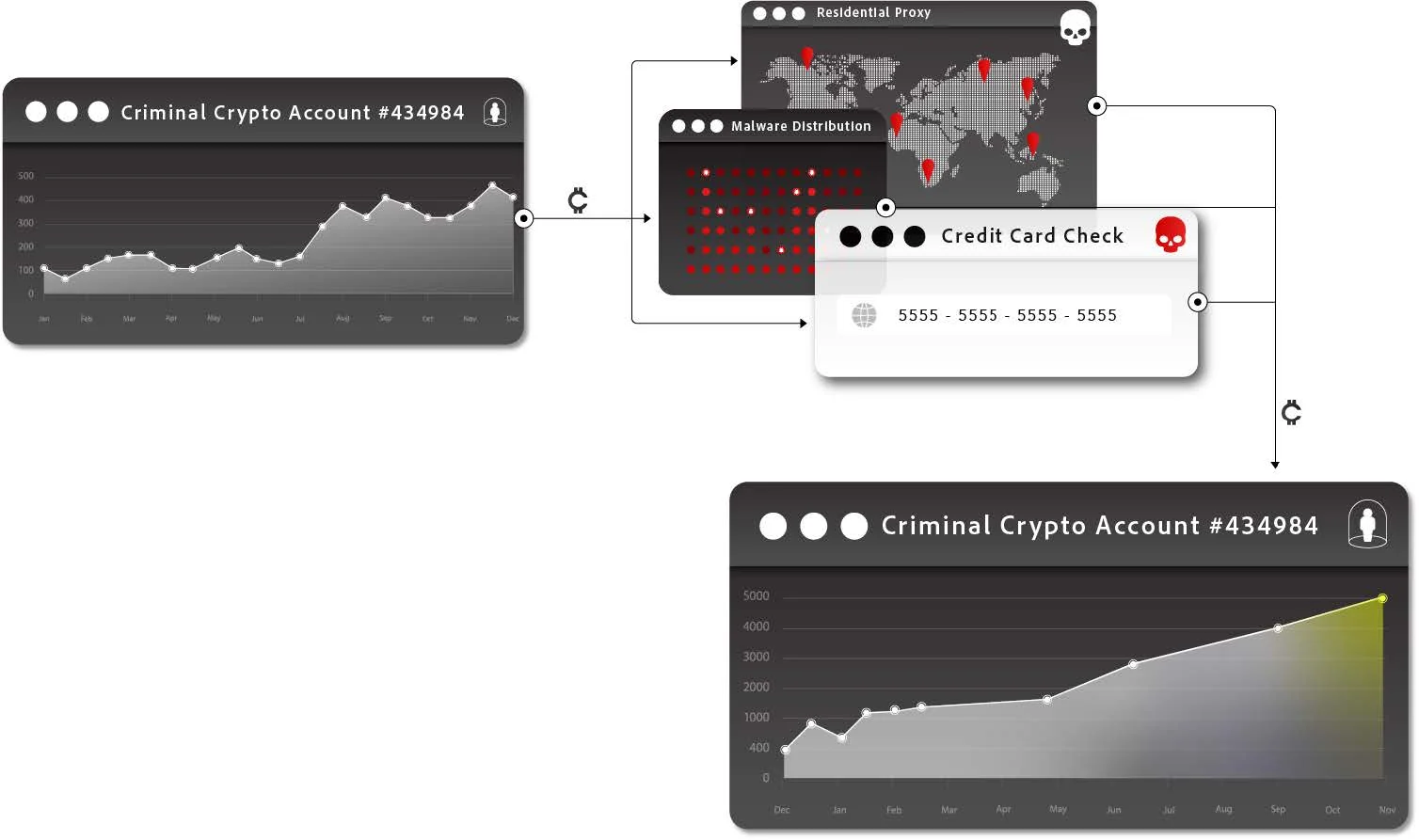
For example, the average cybercriminal with just a few hundred dollars in cryptocurrency can simply buy cybercrime services and start profiting in very little time with very little effort.
(Some of) the components of cybercrime enablement services
Let’s talk about some specific examples of cybercrime enablement services and how they contribute to the overall criminal ecosystem.
Malware-as-a-Service (MaaS)
MaaS enables low-skill cybercriminals to gain access to polished malware that can be almost immediately used to steal information from victims. The current ecosystem is largely focused on infostealers, but also includes things like loaders that can act as an initial foothold on a device that then pulls down other malware.
This off-the-shelf (OTS) model means that a criminal with a few hundred dollars in a cryptocurrency and basic knowledge of the ecosystem can gain access to high-quality malware that often comes with a ready pipeline to steal data. The most centralized stealers, like RisePro, come with a web-based panel for interacting with stolen data, and many stealers allow users to exfiltrate logs to a service like Telegram – completely obviating the need to establish Command and Control (C2) infrastructure of their own.
The rise of MaaS has been attributed to a similar rise in the availability of stolen data, referred to as “logs.” These logs are themselves a commodity, being offered for $10 or less through markets like Russian Market, and for far less when purchased in bulk or in direct transactions.
Malware crypters/packers
Malware crypters are specially-designed tools used primarily for evasion of antivirus software. A malware developer, or purchaser of MaaS, may buy access to one or more crypting services to obfuscate their malware prior to delivering it to a victim.
Many MaaS sellers explicitly require the use of a crypter prior to distribution of their malware, and threaten users with license suspension and bans on future purchases should they attempt to distribute their malware without crypting, or by uploading it to a malware repository like VirusTotal.
Some enterprising MaaS sellers even bundle crypting services with access to their malware, or advertise a specific crypting service alongside their own MaaS. While SpyCloud cannot independently confirm any financial relationship between MaaS sellers and purveyors of crypting services, bundled services and in-panel advertisements suggest more than a coincidental relationship.
“Packing,” often used interchangeably with crypting or crypters, can also describe intentional obfuscation of legitimate software. However, instead of modifying the code in order to evade detection by antivirus software, in this context “packing” is typically done for Digital Rights Management (DRM) purposes so that modification or theft of proprietary software is less likely. Nonetheless, packers who market their services to large software companies like video game developers have nonetheless been used by malware developers for the same reasons many turn to an illicit crypting service: to avoid detection and increase their success rate.
Install brokers
Install brokers, alternatively known as “install services,” “ad brokers,” or “pay-per-install (PPI) services,” are specialized organizations or individuals that maintain a network of websites and advertisements that facilitate the distribution of malware at scale.
These entities sell the service of installing malicious software on target devices, which in turn dramatically simplifies the process for cybercriminals and increases the reach of malware distribution.
Our research and reporting on malware install brokers like InstallBank and SpaxMedia demonstrates how affordable and effective this type of service is for bad actors looking to distribute and monetize a variety of different malware families.
Residential proxies
I once heard someone say, “residential proxies do more damage than ransomware” and I don’t think they’re wrong.
While some proxies serve legitimate purposes, many are intertwined with malware, enabling criminals to mimic trusted IP addresses from victims’ home locations to bypass location authentication measures. And even those which are wholly distinct from malware still often come with functionality that is highly sought after by those seeking to commit crimes, especially fraud, by obfuscating their identity and location.
This is a byproduct of many industries adopting device fingerprinting, which is an online tracking method based on identifying and tracking devices using unique data points, such as an OS, web browsers, IP address or even screen resolution.
As part of this approach, companies often use “geobounding” or “geofencing” to look at a user’s IP address and establish a pattern of behavior, or normalcy, to be able to identify anomalous activity. So if something outside a normal pattern pings – say you typically log into your bank account from Austin, TX but all of a sudden your log-in pops from the middle of Russia – that’s a pretty good sign it may not be the legitimate user trying to log in.
These types of “resnet” proxies are especially dangerous when combined with the proceeds of a successful infostealer infection. Since most infostealers exfiltrate system- or device-level information, such as the operating system, language settings, and networking details, a criminal – armed with a resnet proxy – is able to not only transit their internet traffic through a compromised device geographically close to their target, but also emulate many of the same system details specifically queried by even advanced device fingerprinting.
The 911 S5 botnet: Residential proxy as a service
A great example of the power and scale of criminals taking advantage of residential proxies is the 911 S5 botnet, which after its recent takedown is being labeled as likely “the world’s largest” botnet operation.
The botnet administrator, YunHe Wang, distributed malware through VPN programs and pay-per-install services to millions of residential Windows computers worldwide. He then set up and managed at least 150 dedicated servers to control the infected devices and sell access to proxied IP addresses for cybercriminals, enabling them to commit various offenses, including large-scale financial fraud, identity theft, and child exploitation, resulting in billions of dollars in damages. Wang’s operation is alleged to have scored him $99 million in illicit profits.
Antidetect browsers
Like other entries on this list, antidetect browsers are not themselves inherently malicious. Indeed, it is conceivable – easy, even – to believe that an individual wary of the degree to which certain online services collect information on users would turn to an anonymity-focused browser like Linken Sphere or Multilogin to further obfuscate their online activity.
Nonetheless, these browsers are often common tools within the cybercriminals toolbelt, and are often paired with infostealer logs and resnet proxies to bypass device fingerprinting and commit fraud at an alarming scale. A common feature of these browsers is the ability to load cookies from a local file, thus, taking on the browser identity of another user or device. Combined with a geographically-similar proxy and some device information (which is also importable directly into these browsers), bypassing MFA or other secondary authentication methods can be comically easy.
Checkers
In the cybercriminal lexicon, a “checker” is a lightweight tool to extract monetizable information from data exfiltrated after a successful infostealer infection. By virtue of the scale at which infostealers are used, many criminals and traffer teams have thousands of “logs” to parse through in order to identify information that can be monetized.
Using checker software, a criminal can “test” logins, validate stolen session cookies to use for session hijacking, extract financial information, and perform advanced log analysis – often without writing any code themselves.
What all of this means for the state of cybercrime
This isn’t a comprehensive list of the scope of cybercrime enablement services available to cybercriminals today, but hopefully it gives you a feel for the scale and capabilities of the ecosystem. Unbeknownst to many, it’s way more affordable than it’s ever been, and way easier for criminals to capitalize on stolen data than ever before.
By professionalizing and standardizing what were once ad-hoc criminal activities, even the most novice cybercriminals can carry out sophisticated attacks. The implications for all of us are huge, and recent high-profile attacks including the likes of the ransomware of Medibank, which has been publicly attributed to a commodity MaaS, are evidence that the problem is only becoming more significant.
While state-sponsored cyber actors with names that evoke zoo animals capture much of the media attention when they target a critical infrastructure provider or federal agency, individual cybercriminal actors with only a Telegram handle and username on an obscure Russian-language hacker forum are much more likely to impact the lives of the average consumer or enterprise.
Cybercrime countermeasures and key takeaways
To best defend against the modern cybercriminal, you have to know what stolen data they have at their disposal to potentially use against you or your organization. At SpyCloud, we focus on giving this power back to security, identity, and fraud teams via cybercrime analytics so that you can:
- Protect employee and customer digital identities
- Prevent targeted cyberattacks like ATO, session hijacking, ransomware, and fraud
- Accelerate cybercrime investigations and attribute threat actors