USE CASE: AUTOMATED ATO PREVENTION
Protect Employees & Consumers from
ACCOUNT TAKEOVER
Preventing account takeover attacks requires fast detection and remediation of exposed identity data beyond just stolen credentials. SpyCloud’s holistic approach illuminates dark web exposures well beyond what your current toolset finds and eliminates ATO threats automatically – so you can finally get ahead of criminals targeting your employees and customers.
The SpyCloud approach
Credentials are only part of the story. Identity data is dynamic, interconnected, and often exploited in ways most tools can’t see.
SpyCloud extends a holistic identity lens across personal, corporate, and crossover exposures with actionable data tied to real users and real threat vectors – with automation that solves the problem, not just notifies you about it.
Treating accounts as standalone perimeters and assuming device wipes solve the problem.
Viewing identities as interconnected data points that criminals exploit for unlimited access.
Users’ work, personal, current and past exposures matter to your business.
You don’t need more feeds – you need the right identity data that illuminates the scope of threats to your users right now.
Automating the remediation of stolen identity data (passwords, cookies) so you actually stop attacks before they happen.
Get ahead of account takeover – for every identity you manage
EXPLORE MORE PRODUCTS
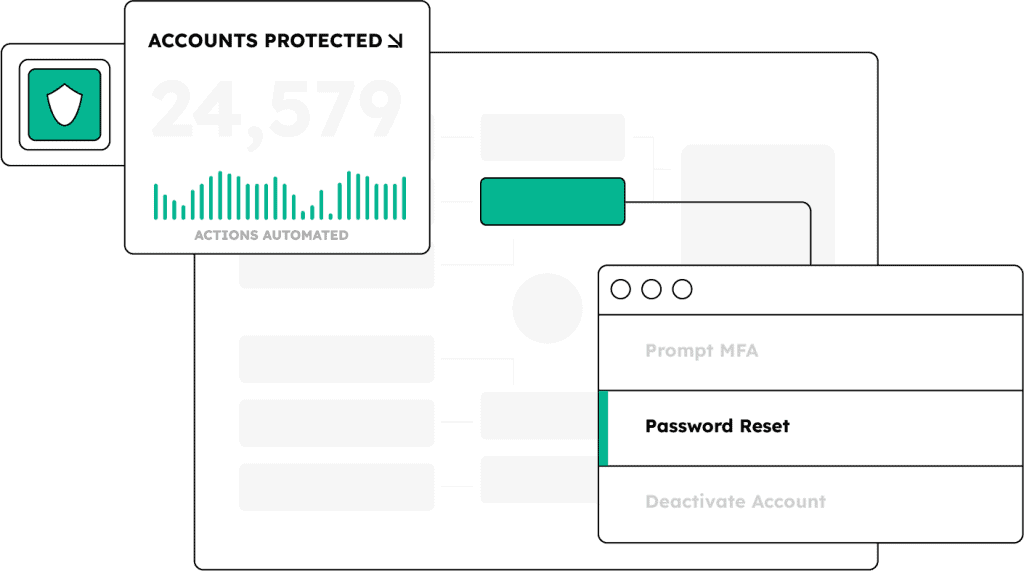
Stop account takeover with identity threat protection
Automate credential remediation within minutes of discovery in Active Directory, Entra ID, and Okta
EXPLORE WHO USES SPYCLOUD
Defenders
we help
SECURITY OPERATIONS
Automatically detect exposed workforce credentials and respond across identity infrastructure
Integrations






Next steps
Catch dark web identity exposures before attackers log in