PRODUCT: CONSUMER THREAT PROTECTION
Stop Consumer Account Takeovers Before They Start
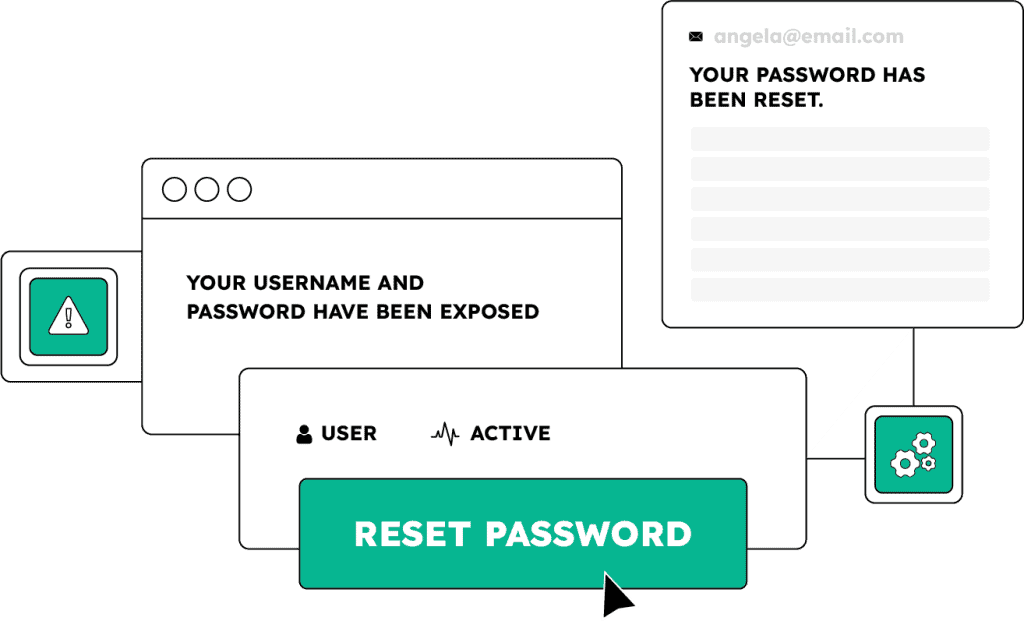
Account takeovers don’t just happen from reused passwords. Empower your fraud and security teams with timely identity intelligence to detect compromised users and intervene before unauthorized access, fraud, or brand damage occurs.
Disrupt cybercriminals' ability to profit
Today’s cybercriminals exploit the full spectrum of a user’s exposed identity – from malware-exfiltrated session cookies to stolen credentials and PII. SpyCloud operationalizes the world’s largest recaptured identity data repository – including breach, malware, and phished data – to help you detect exposed credential data, automate step-up authentication or password reset, and support your overall consumer ATO prevention strategy.
Prevent criminals from making fraudulent purchases, siphoning rewards points, stealing personal information, and locking legitimate users out of their own accounts
Reset passwords or choose an appropriate step-up authentication path for affected users without adding unnecessary friction to the user experience
From account creation to digital transactions – safeguard your consumers’ digital experiences to ensure brand loyalty and trust
Flexible APIs for your workflows & use cases
Identify exact-match identity exposures tied to users across breaches, malware, and phishing – based off username or email address
Check whether a password has ever been exposed to prevent risky, reused credentials
Go beyond basic credential checks to reveal additional exposure signals tied to your consumers, helping you make better-informed decisions about account security
Since SpyCloud recaptures credentials directly from the criminal underground, we now have a level playing field with fraudsters – with the same data, we can easily identify compromised consumers and be more proactive in protecting them.
EXPLORE MORE PRODUCTS
Shut down other entry points
Layer SpyCloud’s additional products to tackle fraud at every entry point.
Session Identity Protection
Stop session hijacking by detecting stolen authentication cookies that could lead to customer account takeover
Cybercrime Investigations
Next steps
Fraud moves fast – you move faster with SpyCloud
Your consumers expect security. Give it to them, before attackers act.