Fifty-nine percent of people admit to using the same password everywhere—and our analysis shows that Fortune 1000 employees are no different.
Password reuse matters because of how often login credentials are exposed in data breaches. An employee who reuses their corporate credentials as personal logins puts their employer’s security in the hands of third-party site operators. When some of those sites are inevitably breached, the corporate passwords become available to attackers.
Cybercriminals inevitably test breached credentials against a variety of other logins, taking over any other accounts protected by the same username and password. If those stolen credentials contain a corporate email domain, criminals have an obvious clue that they could provide access to valuable enterprise systems, customer data, and intellectual property.
In addition to corporate credentials, data breaches expose a wealth of personal information that can enable cybercriminals to bypass security measures, take over accounts, and compromise enterprise networks. Employees, trusted partners, and suppliers with privileged access can all be vulnerable to account takeover and business email compromise.
To provide a snapshot of the breach exposure affecting major enterprises, we examined SpyCloud’s database of nearly 100 billion breach assets to see what breach data we could tie to companies in the Fortune 1000. To do so, we searched for breach records containing Fortune 1000 corporate email domains, excluding “freemail” domains that are available to consumers. For example, if a Fortune 1000 employee signed up for a breached third-party site using their corporate email address, example@employer.com, we were able to tie the resulting breach record to their employer.
We were able to tie over 412 million breach assets within our dataset to employees within the Fortune 1000. Within this analysis, we have broken that number down by data type and sector (as defined by Fortune) to reveal the scope of the breach exposure facing different sectors.
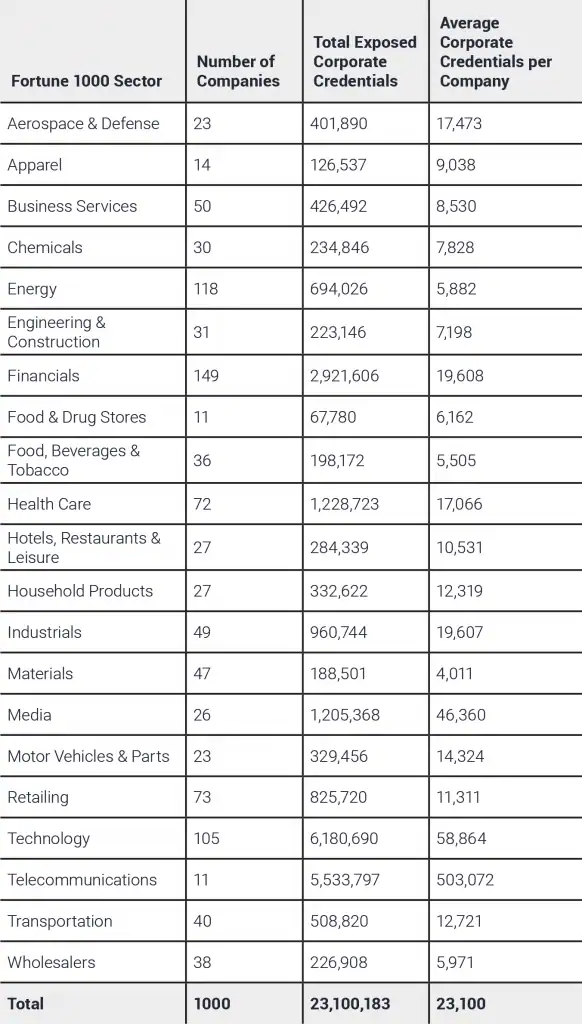
Over 23M plaintext credentials tied to Fortune 1000 employees are available to cybercriminals
Across the SpyCloud dataset, we discovered 23 million pairs of credentials containing Fortune 1000 corporate email addresses and plaintext passwords. While not every credential pair will match corporate login details, the ones that do match represent substantial risk for these enterprises—and their customers and partners.
By sector, here’s how that breaks down:
Figure 1: Chart Showing Fortune 1000 Credential Exposure by Sector
In theory, corporate passwords should be strong given the importance of the assets they protect and the robust guidance often provided by corporate security teams. In practice, many employees practice bad password hygiene at work. That’s why the latest guidance from the National Institute of Standards and Technology (NIST) calls for organizations to proactively check for “commonly-used, expected, or compromised” user passwords to effectively mitigate the risk posed by human behavior.
Across those exposed credentials, Fortune 1000 employees reused passwords at a rate of 76.5%.
Within our dataset of Fortune 1000 corporate breach exposures, we calculated password reuse rates by determining how many employees with more than one exposed login have reused the same password or a close variation across multiple sites, then assigned a Password Reuse Index to each industry. The higher the percentage, the greater the rate of employee password reuse. By sector, password reuse rates ranged from 53% (Retailing) to 85% (Media), with an overall average of 76.5%.
Employees with multiple reused passwords in our dataset may or may not reuse passwords at work—we can’t tell for sure without checking their actual work passwords. However, password reuse across personal accounts does provide an indication of employees’ overall password hygiene.
Interested in your own organization’s match rate? Contact us to request a data test
The credentials of 127,083 C-level Fortune 1000 executives are available on the criminal underground.
Exposed executive credentials present prime targets for business email compromise (BEC), which can be extremely costly. According to the 2019 Internet Crime Report released by the FBI’s Internet Crime Complaint Center (IC3), complaints related to BEC led to over $1.7 billion in losses in 2019 alone.
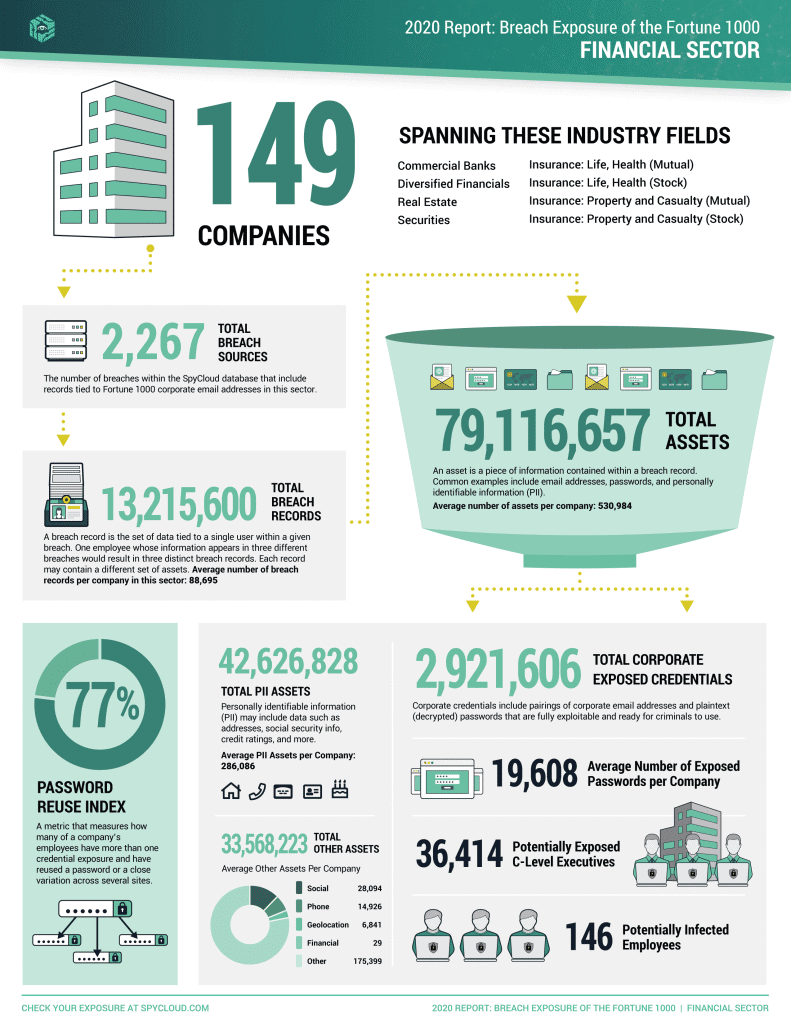
On average, companies in the Hotels, Restaurants & Leisure sector have the most exposed C-level executives, with an average of 260 per company (7,021 exposed executives across 27 companies). The Financial sector comes in second, with an average of 244 exposed C-level executives per company (36,414 executives across 149 companies).
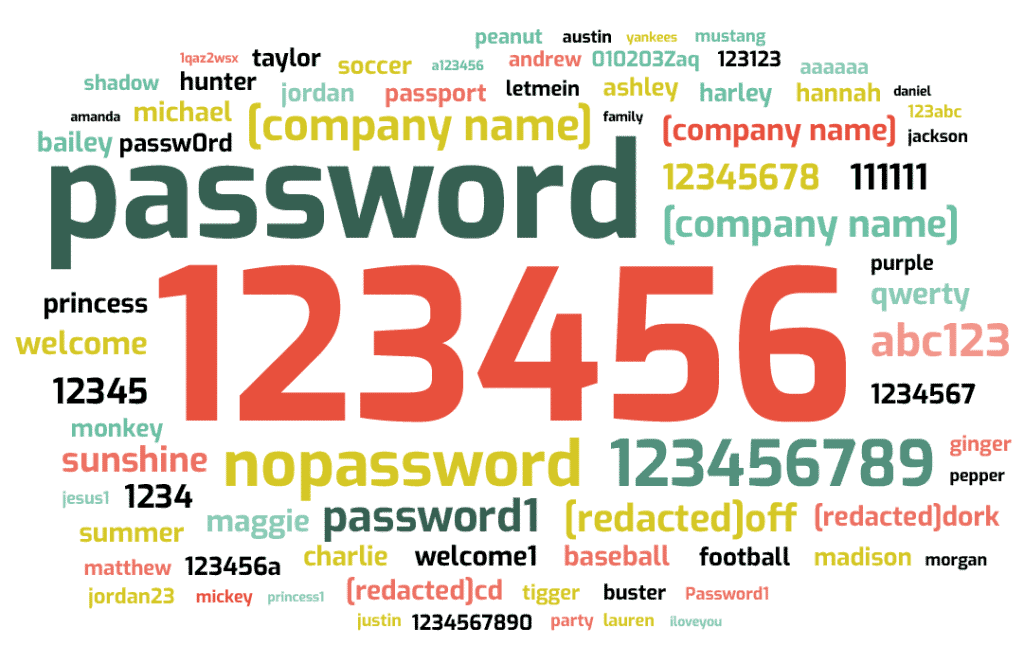
Favorite passwords of the Fortune 1000 include: 123456, password, and 123456789. (Also, plenty of expletives.)
Certain passwords in our dataset appeared thousands of times; for example, the most popular password on the list, 123456, appeared 14,252 times within the dataset.
Certain themes dominated the list. Passwords that appear to be names (maggie, bailey, michael) accounted for 32 of the top 100 passwords, appearing over 24 thousand times. Strings of digits (123456789) and easy-to-type combinations of letters and numbers (abc123, qwerty) accounted for another 19 of the top passwords.
You can see more of the top 100 passwords below. For anonymity, we have redacted passwords containing company names or expletives.
Figure 2: Top 100 Passwords of the Fortune 1000
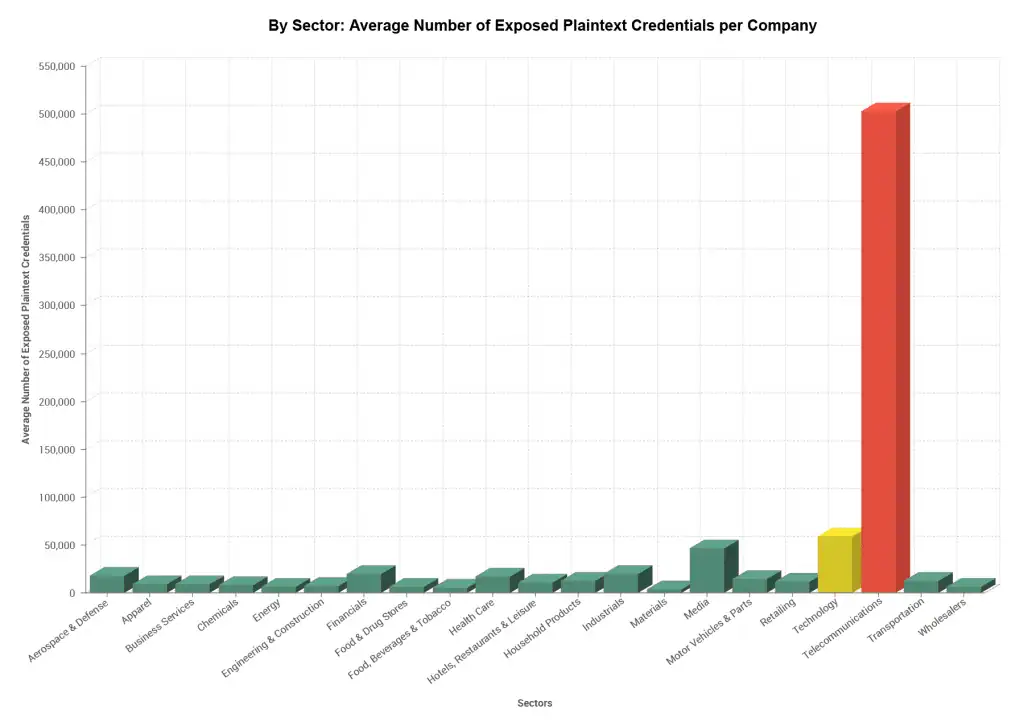
The Telecommunications sector is the worst offender—by far.
The Telecommunications sector’s employee breach exposure dominated every other sector we examined. Although the companies within this sector are large, with an average of about 74,000 employees per company, employee totals do not account for the disparity. The Telecommunications sector’s ratio of exposed credentials to total employees is still the highest out of every sector.
It’s possible that employee tenure could have something to do with the sector’s high exposure levels. Employees who have owned their corporate email accounts for many years would have had plenty of opportunities to use them on third-party sites. Conversely, high levels of churn could also potentially play a part, with many short-term employees racking up a few exposures each before moving on.
The full report includes a comparison of exposure by sector, as well as a full-page infographic for each of the Fortune 1000’s 21 sectors.
Figure 3: Bar Chart Showing Fortune 1000 Credential Exposure by Sector
Technology comes in second place—and has the highest number of potentially infected employees.
We recovered credentials from 1,022 Technology sector employees whose corporate or personal systems appear to be infected with keylogging malware. Given the breadth of data revealed in these records, these exposures represent significant risk for affected organizations. Whether the keyloggers are installed on corporate or personal systems, criminals can collect a wealth of data that can be used against these users’ employers.
Credential exposure is just the beginning.
Beyond exposed passwords and potentially compromised users, bad actors have access to a wealth of compromised PII that can be used in targeted attacks—over 200M PII assets tied to Fortune 1000 employees are available to cybercriminals.
While stolen credentials provide an obvious entrypoint for malicious actors, other types of breach assets—such as phone numbers, addresses, social security numbers, and credit ratings—can provide tremendous value to cybercriminals, whether for consumer fraud or as a means of gaining access to enterprise networks, data, intellectual property, and funds.
Criminals may engage in highly-targeted, manual attacks against victims with privileged access to corporate resources, such as C-suite leaders, senior executives, system administrators, and developers. Given the potential payoff associated with these targets, it’s no wonder malicious actors are willing to invest substantial effort and creativity to take over their accounts.
Your Plan of Action
SpyCloud’s analysis of Fortune 1000 companies’ exposure as a result of third-party breaches has revealed more than 412 million breach assets in criminals’ hands, 4 million of which are plaintext passwords tied to Fortune 1000 company employees. Combined with high rates of password reuse, these exposures represent significant account takeover risks for these organizations and the companies that do business with them. Attackers actively test stolen credentials against different accounts to exploit bad password habits and gain access to corporate systems and data. Even worse, stolen PII and account data make it easy for criminals to craft highly targeted, creative attacks that cause great harm and are difficult to detect. Enterprises must be able to trust the identities of the employees, consumers, and suppliers logging into their networks—and safeguard the corporate assets and IP behind those logins. The answer is to build early detection and remediation of exposed credentials into their cybersecurity strategy, and the best method, simply put, is to use SpyCloud.Interested in learning how SpyCloud can help your enterprise combat employee account takeover? Request a demo
Figure 4: Infographic Showing Financial Sector Breach Exposure
Download the full 2020 report to see an infographic for each of the 21 sectors in the Fortune 1000.