Threat actors are leveraging infostealer malware like LummaC2 to dramatically increase and improve their tactics. To better understand the scope of its capabilities, our analysts at SpyCloud Labs reverse-engineered the latest LummaC2 malware and observed some notable changes to its code between June and November 2023.
Some of the noteworthy observations were:
- Changes to LummaC2’s theft capabilities to allow for email client theft
- Changes to LummaC2’s theft capabilities to allow for theft of 2FA secrets
- Changes to LummaC2 to allow the download and execution of remotely hosted files (.ps1, .exe, or .dll)
With the addition of dynamic config acquisition, these changes give customers of LummaC2 further customizability with their campaigns.
Keep reading to dig into its latest capabilities.
LummaC2 Forum Ads
As observed here, LummaC2 offers a monthly pricing scheme of Experienced ($250/month), Professional ($500/month), and Corporate ($1000/month), with a variety of features offered for each tier.
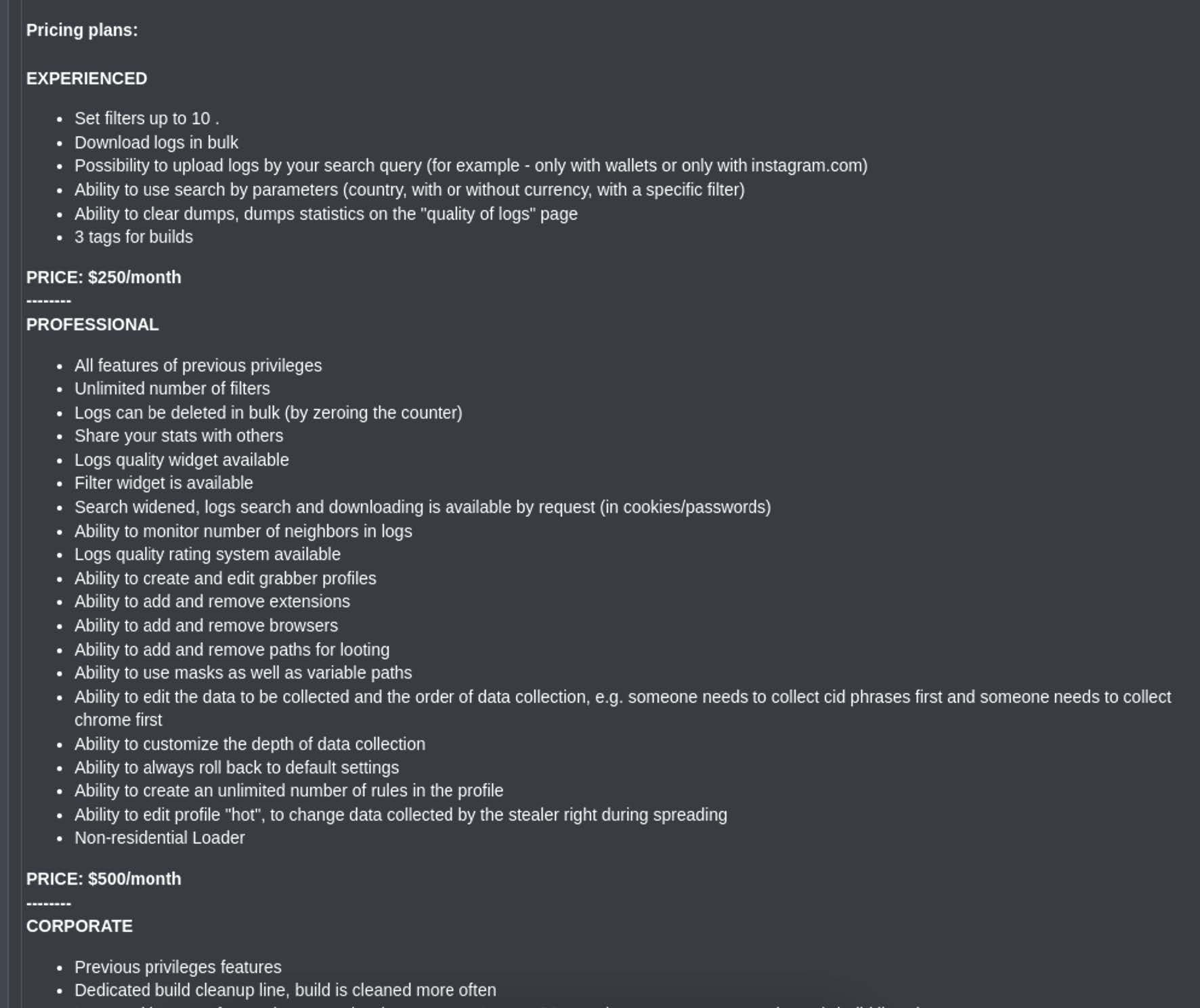
LummaC2 pricing tiers
With LummaC2’s operating model, while the bot steals credentials and account information, it doesn’t do a whole lot of parsing on the victim’s machine. Instead it does most of the log parsing on the C2. Recent updates show that the developers are continually adding new features to the log parsing, now allowing for the extraction of credit card information, and valid Google accounts, as observed below.
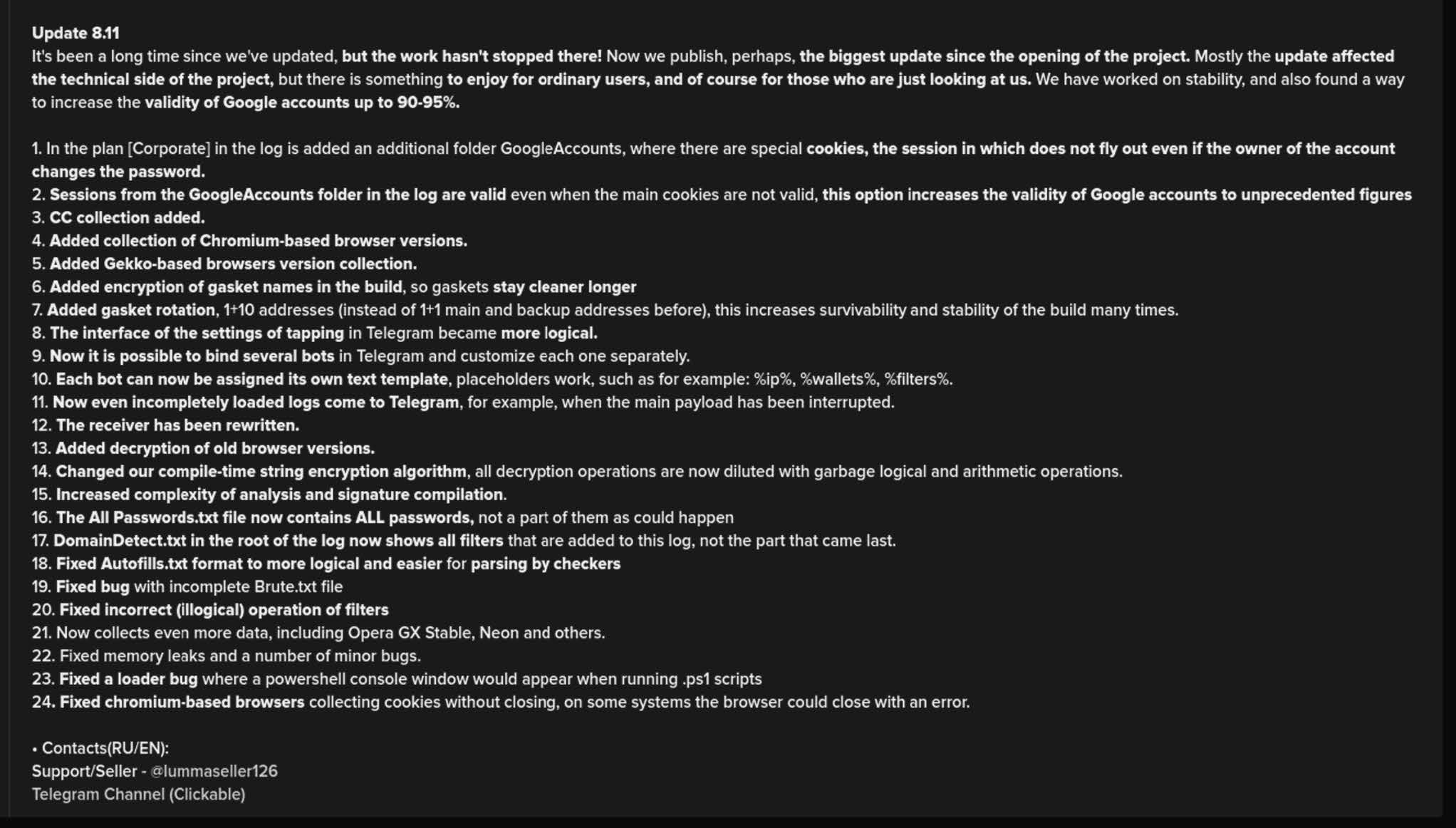
LummaC2 Config Analysis
LummaC2’s config, pulled from the C2 during check-in, has gone through a slight refactoring in order to change how some of the entries are handled by the LummaC2 bot. Target extensions to steal from have been moved to their own json entry of “ex”, which allows the bot to easily transport the extension list from Chromium application to Chromium application. The full list of extensions targeted by LummaC2 is as follows:
Full list of extensions
Extension name | Extension address |
MetaMask | ejbalbakoplchlghecdalmeeeajnimhm |
MetaMask | nkbihfbeogaeaoehlefnkodbefgpgknn |
Trust Wallet | egjidjbpglichdcondbcbdnbeeppgdph |
TronLink | ibnejdfjmmkpcnlpebklmnkoeoihofec |
Ronin Wallet | fnjhmkhhmkbjkkabndcnnogagogbneec |
Binance Chain Wallet | fhbohimaelbohpjbbldcngcnapndodjp |
Yoroi | ffnbelfdoeiohenkjibnmadjiehjhajb |
Nifty | jbdaocneiiinmjbjlgalhcelgbejmnid |
Math | afbcbjpbpfadlkmhmclhkeeodmamcflc |
Coinbase | hnfanknocfeofbddgcijnmhnfnkdnaad |
Guarda | hpglfhgfnhbgpjdenjgmdgoeiappafln |
EQUA | blnieiiffboillknjnepogjhkgnoapac |
Jaxx Liberty | cjelfplplebdjjenllpjcblmjkfcffne |
BitApp | fihkakfobkmkjojpchpfgcmhfjnmnfpi |
iWlt | kncchdigobghenbbaddojjnnaogfppfj |
EnKrypt | kkpllkodjeloidieedojogacfhpaihoh |
Wombat | amkmjjmmflddogmhpjloimipbofnfjih |
MEW CX | nlbmnnijcnlegkjjpcfjclmcfggfefdm |
Guild | nanjmdknhkinifnkgdcggcfnhdaammmj |
Saturn | nkddgncdjgjfcddamfgcmfnlhccnimig |
NeoLine | cphhlgmgameodnhkjdmkpanlelnlohao |
Clover | nhnkbkgjikgcigadomkphalanndcapjk |
Rabby | acmacodkjbdgmoleebolmdjonilkdbch |
Pontem | phkbamefinggmakgklpkljjmgibohnba |
Martian | efbglgofoippbgcjepnhiblaibcnclgk |
Bitwarden | nngceckbapebfimnlniiiahkandclblb |
Nami | lpfcbjknijpeeillifnkikgncikgfhdo |
Petra | ejjladinnckdgjemekebdpeokbikhfci |
Sui | opcgpfmipidbgpenhmajoajpbobppdil |
ExodusWeb3 | aholpfdialjgjfhomihkjbmgjidlcdno |
BinanceWallet | fhbohimaelbohpjbbldcngcnapndodjp |
Sub | onhogfjeacnfoofkfgppdlbmlmnplgbn |
PolkadotJS | mopnmbcafieddcagagdcbnhejhlodfdd |
Talisman | fijngjgcjhjmmpcmkeiomlglpeiijkld |
MewCX | nlbmnnijcnlegkjjpcfjclmcfggfefdm |
CryptoCom | hifafgmccdpekplomjjkcfgodnhcellj |
Liquality | kpfopkelmapcoipemfendmdcghnegimn |
Terra Station | aiifbnbfobpmeekipheeijimdpnlpgpp |
Keplr | dmkamcknogkgcdfhhbddcghachkejeap |
Sollet | fhmfendgdocmcbmfikdcogofphimnkno |
Auro | cnmamaachppnkjgnildpdmkaakejnhae |
Polymesh | jojhfeoedkpkglbfimdfabpdfjaoolaf |
ICONex | flpiciilemghbmfalicajoolhkkenfe |
Nabox | nknhiehlklippafakaeklbeglecifhad |
KHC | hcflpincpppdclinealmandijcmnkbgn |
Temple | ookjlbkiijinhpmnjffcofjonbfbgaoc |
TezBox | mnfifefkajgofkcjkemidiaecocnkjeh |
DAppPlay | lodccjjbdhfakaekdiahmedfbieldgik |
BitClip | ijmpgkjfkbfhoebgogflfebnmejmfbm |
Steem Keychain | lkcjlnjfpbikmcmbachjpdbijejflpcm |
Nash Extension | onofpnbbkehpmmoabgpcpmigafmmnjh |
Hycon Lite Client | bcopgchhojmggmffilplmbdicgaihlkp |
ZilPay | klnaejjgbibmhlephnhpmaofohgkpgkd |
Coin98 | aeachknmefphepccionboohckonoeemg |
Authenticator | bhghoamapcdpbohphigoooaddinpkbai |
Cyano | dkdedlpgdmmkkfjabffeganieamfklkm |
Byone | nlgbhdfgdhgbiamfdfmbikcdghidoadd |
OneKey | infeboajgfhgbjpjbeppbkgnabfdkdaf |
Leaf | cihmoadaighcejopammfbmddcmdekcje |
Authy | gaedmjdfmmahhbjefcbgaolhhanlaolb |
EOS Authenticator | oeljdldpnmdbchonielidgobddfffla |
GAuth Authenticator | ilgcnhelpchnceeipipijaljkblbcob |
Trezor Password Manager | imloifkgjagghnncjkhggdhalmcnfklk |
Phantom | bfnaelmomeimhlpmgjnjophhpkkoljpa |
UniSat | ppbibelpcjmhbdihakflkdcoccbgbkpo |
Applications targeted for theft by LummaC2 are still stored in the “c” entry of the config, or what we are calling the “command” list. These “commands” are stored in json dictionaries and instruct the malware on how to steal applications stored in “p”, using the command opcode in “t”. The following table can be used for command opcode translations:
Opcode | Command Name | Command Description | Example json |
0 | Steal_Clients | Using directory listed in “p”, steal file extensions listed in “m” and save application to “z”. FS is max file size. | { “t”: 0, “p”: “%appdata%\\Exodus\\exodus.wallet”, “m”: [“*”], “z”: “Wallets/Exodus”, “d”: 2, “fs”: 20971520 } |
1 | Steal_Chromium_data | Using directory listed in “p”, steal chromium browser data from sqlite3 databases. Additionally steal extensions. Save to “z”. | { “t”: 1, “p”: “%localappdata%\\Google\\Chrome Beta\\User Data”, “z”: “Chrome Beta” } |
2 | Steal_Mozilla_data | Using directory listed in “p”, steal mozilla browser data from sqlite databases. Save to “z” | { “t”: 2, “p”: “%appdata%\\Mozilla\\Firefox\\Profiles”, “z”: “Mozilla Firefox” } |
3 | NULL | ||
4 | Drop_File | Download file stored at “u” and drop, using ft to determine type of file. 0 = .exe, 1 = .dll, 2 = .ps1 | { “t”: 4, “u”: “https://localhost/test.exe”, “ft”: 0, “e”: 0 } |
Steal_Clients
LummaC2’s Steal_Clients function allows the malware to steal data from a variety of clients/software on a victim’s machine. With the changes to LummaC2’s config, theoretically, customers of LummaC2 could easily add other software to be stolen from by LummaC2; they just need to supply:
-
The path to steal from
○ In the “p” field in the config -
The file extensions to steal
○ In the “m” field in the config -
The output directory to store stolen data in the log
○ In the “z” field in the config -
The depth of recursiveness
○ In the “d” field in the config -
The maximum file size to steal
○ In the “fs” field in the config
The following clients/software were observed as targets in configs analyzed by SpyCloud Labs:
Client name | Path | Files stolen | Output path |
Electrum | %appdata%\\Electrum\\wallets | * | Wallets/Electrum |
Ethereum | %appdata%\\Ethereum | keystore | Wallets/Ethereum |
Exodus | %appdata%\\Exodus\\exodus.wallet | * | Wallets/Exodus |
Ledger Live | %appdata%\\Ledger Live | * | Wallets/Ledger Live |
Atomic | %appdata%\\atomic\\Local Storage\\leveldb | * | Wallets/Atomic |
Coinomi | %localappdata%\\Coinomi\\Coinomi\\wallets | * | Wallets/Coinomi |
Authy Desktop | %appdata%\\Authy Desktop\\Local Storage\\leveldb | * | Wallets/Authy Desktop |
Bitcoin core | %appdata%\\Bitcoin\\wallets | * | Wallets/Bitcoin core |
Binance | “%appdata%\\Binance” | “app-store.json”, “.finger-print.fp”, “simple-storage.json” | Wallets/Binance |
JAXX | %appdata%\\com.liberty.jaxx\\IndexedDB | *.leveldb | Wallets/JAXX New Version |
AnyDesk | %appdata%\\AnyDesk | *.conf | Applications/AnyDesk |
FileZilla | %appdata%\\FileZilla | “recentservers.xml” “sitemanager.xml” | Applications/FileZilla |
KeePass | “%userprofile%” | *.kbdx | Applications/KeePass |
Steam | %programfiles%\\Steam | ssfn* | Applications/Steam |
Steam | %programfiles%\\Steam\\config | * | Applications/Steam/config |
Telegram | %appdata%\\Telegram Desktop | *s | Applications/Telegram |
Important Files | %userprofile% | “*seed*.txt”, “*pass*.txt”, “*ledger*.txt”, “*trezor*.txt”, “*metamask*.txt”, *bitcoin*.txt”, “*words*”, “*wallet*.txt” | Important Files/Profile |
TheBat | %appdata%\\The Bat! | “*.TBB”, “*.TBN”, “*.MSG”, “*.EML”, “*.MSB”, “*.mbox”, “*.ABD”, “*.FLX”, “*.TBK”, “*.HBI”, “*.txt” | Mail Clients/TheBat |
Pegasus | C:\\PMAIL | “*.CNM”, “*.PMF”, “*.PMN”, “*.PML”, “*CACHE.PM”, “*.WPM”, “*.PM”, “*.USR” | Mail Clients/Pegasus |
Mailbird | %localappdata%\\Mailbird\\Store | *.db | Mail Clients/Mailbird |
EmClient | %appdata%\\eM Client | “*.dat”, “*.dat-shm”, “*.dat-wal”, “*.eml” | Mail Clients/EmClient |
Steal_Chromium_data
LummaC2’s Chromium browser theft function takes an input directory in config field “p” and a log output directory in config field “z”. Using the directory in “p”, it enumerates profiles for Chromium browsers, and then locates the Chromium browser-specific sqlite3 db that contains all of the victim’s stored passwords, cookies, autofill, and history. It also locates and decrypts the victim’s OS encryption key, created by Chromium browsers and used to decrypt many values in the sqlite3 dbs. It steals the key and the entire db, and zips them up in the output directory specified by “z”. It also attempts to steal all extensions using the above extension list stored in the config. These are all zipped up and sent back to the C2 for further log parsing. Just like with the steal clients command, this command is highly configurable and depends entirely on what is supplied to it from the downloaded config, so new browsers could theoretically be added by customers of LummaC2.
Here are the following browsers targeted currently as observed in configs analyzed by SpyCloud Labs:
Browser name | Path | Output path |
Google Chrome | %localappdata%\\Google\\Chrome\\User Data | Chrome/ |
Google Chrome Beta | %localappdata%\\Google\\Chrome Beta\\User Data | Chrome Beta/ |
Opera | %appdata%\\Opera Software\\Opera Stable | Opera/ |
Opera Neon | %localappdata%\\Opera Software\\Opera Neon\\User Data | Opera Neon/ |
Opera GX Stable | %appdata%\\Opera Software\\Opera GX Stable | Opera GX Stable/ |
Microsoft Edge | %localappdata%\\Microsoft\\Edge\\User Data | Edge/ |
Brave Browser | %localappdata%\\BraveSoftware\\Brave-Browser\\User Data | Brave/ |
Epic Privacy Browser | %localappdata%\\Epic Privacy Browser\\User Data | EpicPrivacyBrowser/ |
Vivaldi | %localappdata%\\Vivaldi\\User Data | Vivaldi/ |
360Browser | %localappdata%\\360Browser\\Browser\\User Data | 360Browser/ |
CocCoc | %localappdata%\\CocCoc\\Browser\\User Data | CocCoc/ |
Steal_Mozilla_data
Lumma’s Steal Mozilla function is very similar to the Chromium browser theft functionality, however it targets the Mozilla-specific sqlite dbs, instead of the Chromium specific ones. In the config, this function is only used for Mozilla Firefox, but could theoretically be modified for any other Mozilla-based browser/client.
Drop_File
While this function was not observed in the configs analyzed by SpyCloud Labs, our analysts were able to reverse this command and determine the requirements of each entry in the json dictionary, and their purpose.
This command currently only opens a connection to the url pointed to by “u”, and then pulls down a file, saving it to a randomly named file stored in %TEMP%. This file is given an extension based on values in “ft” and executed, as observed in the following table:
“ft” value | extension | execution routine |
0 | .exe | File is dropped and executed with CreateProcessW. |
1 | .dll | File is dropped and loaded |
2 | .ps1 | File is dropped and executed using powershell -exec bypass \”%s\” |
The “e” field in the json dictionary determines the execution behavior. Only a few options exist currently (for .DLLs):
-
Execute with LoadLibraryW
○ “e” = 0 -
Execute with rundll32.exe
○ “e” = 1
As LummaC2 is still under active development, more execution options will surely be developed.
Take_Screenshot
This function allows LummaC2 to take a screenshot of the victim screen using internal Windows API calls. This capability is tied to the config entry “se” and is only triggered when “se” is set to “True”.
Delete_Self
This function allows LummaC2 a way to delete itself from victims once it has finished stealing data and exfilling it back to its C2, however it doesn’t run on all infections. The deletion function is tied to the config entry “ad”, and is only triggered when “ad” is set to “True”.
LummaC2 deletes itself by running the following cmd.exe command:
- cmd.exe /c timeout /nobreak /t 3 & fsutil file setZeroData offset=0 length=%lu “%s” & erase “%s” & exit
Language_Check
This function gives LummaC2 a language checker in order to determine if it’s running in a banned region. This checker looks for the following languages on a victim’s system and terminates if found:
- Russian
- Uzbek
- Azerbaijani
Interestingly, this function is tied to the config value “az” and only runs if this value is set to “True”. If the value is not found or set to False, this function will not run, which theoretically would allow LummaC2 to run in those regions.
Theft Upgrades
Mail Theft
LummaC2 now has a multi-part email theft added into the bot. The first part comes from the inclusion of Email clients in LummaC2’s Steal_Clients command. This inclusion of Email clients and extensions commonly used by these clients allows LummaC2 to systematically steal data from basic Email clients that exist on the system. Based on config and log analysis, SpyCloud analysts have seen the following clients targeted by LummaC2’s config-based Email client theft:
Client | Targeted extensions | Log output directory |
emClient | *.dat”, “*.dat-shm”, “*.dat-wal”, “*.eml” | Mail Clients/EmClient |
The Bat | “*.TBB”, “*.TBN”, “*.MSG”, “*.EML”, “*.MSB”, “*.mbox”, “*.ABD”, “*.FLX”, “*.TBK”, “*.HBI”, “*.txt” | Mail Clients/TheBat |
Pegasus | “*.CNM”, “*.PMF”, “*.PMN”, “*.PML”, “*CACHE.PM”, “*.WPM”, “*.PM”, “*.USR” | Mail Clients/Pegasus |
Mailbird | “*.db” | Mail Clients/Mailbird |
Additionally, as observed in the screenshot below, LummaC2’s next part of email theft consists of a hardcoded section of code that targets Thunderbird and attempts to perform a “Steal_Mozilla_data” on the Thunderbird directory, allowing LummaC2 to steal Thunderbird data.
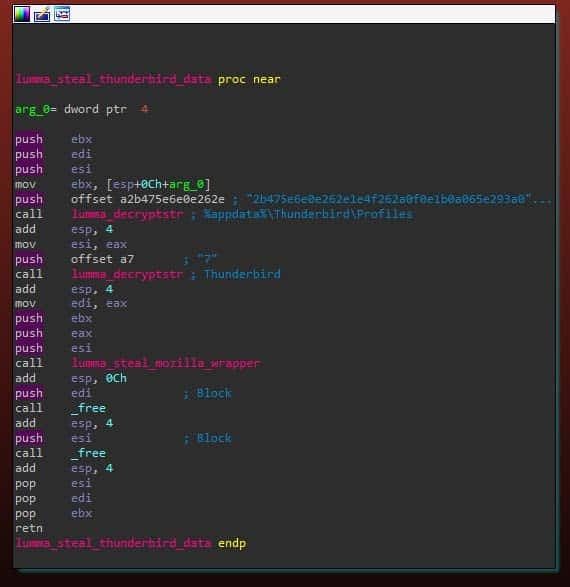
Additionally, LummaC2 steals from Windows Mail’s default storage location and alternative storage location, using the Steal_Clients command, targeting “*.eml” files:
- %localappdata%\Microsoft\Windows Mail\Local Folders
- %localappdata%\Packages\microsoft.windowscommunicationsapps*
Based on analyses of logs collected by our analysts, we can confirm that these capabilities not only work, but also are able to steal emails, IMAP/SMTP session tokens, credentials, and attachments, and even entire email databases (which may contain additional forensic information/emails).
2FA Theft Updates
With the inclusion of Authy’s %appdata% directory in the Steal_Clients function, LummaC2 is now able to properly steal two-factor authentication (2FA) secrets from Authy on victim systems. These can be leveraged by attackers during account takeover to gain access to a victim’s machine. While the only 2FA manager stolen from is Authy in LummaC2 default configs, as the config is highly configurable, attackers could theoretically add more 2FA programs, so long as they find where their storage directories are on systems.
C2 Uptime Updates
In the period around late October to early November, LummaC2 began introducing changes to their bot in order to guarantee a longer-lasting uptime on embedded C2s. These changes include the addition of more C2s in the binary (increasing the buffer from a main and a backup, to at least 3 C2s), as well as a CloudFlare anti-phishing block awareness catch and bypass. SpyCloud Labs reversed the bypass used by LummaC2 and have developed a POC that has been sent to CloudFlare so that CloudFlare can harden their anti-phishing blocked page.
Log Analysis
Through analysis of obtained victim logs, we can begin to lend some clarity to LummaC2’s current operations.
Percentage of logs with stolen browsers
Checking our logs for the past 30 days, we can see that 83.04% of victim logs contained stolen data for Chrome, while 82.27% of victim logs contained stolen data for Edge, and 25.23% of victim logs contained stolen data for Firefox. While these folders are not mutually exclusive, meaning one victim log could have all three or any combination of the three, it does give a good snapshot into one of the more common theft routines of LummaC2.
Percentage of logs with a screenshot
Checking our logs for the past 30 days, we can see that only 24.84% of victim logs contained a screenshot inside of them. As screenshots are triggered by the “se” field in the config, this means that most configs that are used by the log sources we pull from do not set the “se” field and so do not take a screenshot of the victim machine.
Logs with Stolen Mail Clients
Compared with presence (or lack thereof) of screenshots, the numbers for Stolen Mail Clients seem very low, however any mail client theft should be treated as a high priority as there is a large amount of sensitive information that can be stolen. For the past 30 days, 0.2% of LummaC2 victim logs contained stolen mail clients like emClient or Windows Mail and 1.0% of victim logs contained Thunderbird client info. The stolen mail client info consisted of entire mail databases.
Logs with Stolen Authenticators
As LummaC2 can now successfully steal 2FA secrets from a victim’s machine, we decided to look at our collection of victim logs to determine how often 2FA secrets are actually found and stolen. In the past 30 days, only 0.08% of victim logs contained exfiltrated 2FA secrets, however from checking those logs, the 2FA secrets were properly exfiltrated and are theoretically usable.
LummaC2 also attempts to steal “.kbdx” files from a victim’s system for Keepass, as that is the extension used for Keepass password manager database files. However, this theft method is not as precise as someone might expect from checking logs, as CAD software also uses the “.kbdx” extension for entirely unrelated files.
Final thoughts
We’ll continue monitoring developments of Lumma’s capabilities and reviewing recaptured logs to better understand exfiltration trends. Keep an eye out for more reverse-engineering analyses from our team at SpyCloud Labs in the coming months.
Samples
hash |
ecabbeae6218b373f2d3a473d9f6add4ba5482ea3b97851c931197fb8993f8ef |
b14a6b1df2c111796586dd3694b2a5d9c9785453eecd00f292321dff41767c10 |
3e8b6d837b5bbf71883c127ab03f1cb95503223fb3fbb31f6bb8de16b77c7c96 |
2e5e802bdb6e3ffcaeacebb80ffb4312ab072f82fdd9a72f0206eb388d8e9cfb |
7bf4febec4be45f052ed028afe51f4e89de90b4d0b85ef26eb812b68a611456f |
a5007c2a62b3ed572f0b424bd4f1ab8b7833d24cea0338f1b5c599e39778d9ff |
9ee1188bfa814e0ae8dccba22ead8ed250915807d8750a48120b514f24e762b2 |
507fb71ea7fa80c8d01ed8ef5388953389cb930ec5337286a84bbe31d6921f07 |
0052e15271e436c6c1e4c332a147120edf944ab5c6807b86132c04c325911575 |
acd61fac3ce6b535dfa80708de6a0f266d6cd204457ea84afb8195b89523a884 |
721b92974da0c27672f987d6d905df86a666d3526a39948b24f22f62ab89a15b |
09ac4880051d17a4f2528a7054ff97d5f812af440d0bab7e779bcf830a90bebb |
bfff24ea90ade6dc230d693c9244567afff5656795dd68779e053ea8ace5d9f1 |
0cc5f44a21bdc293bb2f0a3aaae38fd584166460ff03cb9c1789bff5fbe0107c |
2a32c5f765120aa040cf6f02b423fc6c808f0a801cfc929d600def72c6aa9626 |
783d50aa5c7f35ca4a39fd9e4cce7aa5d6acad51ff60f0539abaf0b96a9b82c8 |
cf051d7958626831278710ce0c75850b6d999efebf013083f91db8eef635e2f9 |
1e8f3a9eea737e1a5d74f838f3e3a9c337ad963c29b0d6784897dc16f16c5bd7 |
2cf4ec770b12b991a11f0005488a1ea713e8935b91445de7b6cec32691cca602 |
99bba4b98096259772dc0c12f0ebb3b3ff275f4babf75caa380e94e3dbed90c9 |
a9760807ff1e50509224d2998a2a7ab3bed3d2857aa5964f7f58e6403ac63699 |
9b44d71415ede559d3f35a2c2eb67deb57e0565cd6de18bace4b2fbd7037f16e |
5b50828e8628ef7fa69741d4ac8e8f082d9e0dc62141e80402530f263b27e6b1 |
513b4bcf6c6b1ac9f4444fb4ecf3cc461dba87c7367ebf44ae750da394e27c40 |
6eeca105c170605cdf94b58a253d5c21f41212aadb00a9d89626e57546d4e91b |
56a4dc64bfecac9f9d88558ebf5ffcdc4f7e14af9074c3f8b6a41e3ab2915c79 |
543c9b343d5cf44cbecd7e1087e99d2a9d0528e6b25ee987ff6e66d878609d78 |
b7878591d918196b67c9111f6e90a77fd0c35635b2e04fd98f8f279eb4b1095b |
e8698d602b5ed94f3ad99848e0be68f8a59f66bb79f9b958dcca7d715c82df5a |
ec0fedf719f70faf4bdc56f277d630e7b9ae3521c895aefe4ad67b351a15666c |
437f7c5f886a657a87f6b578e3c31eba6c92bc90d04034e34bddf0b95a11f521 |
aed9659e8123816a0436aa58bb3ac978beb9fd7f9490b9c68d781409b1eca669 |
2e619bc930202b5b7c6a0cebb51d6debbf1b1c97317e3da92db2864c4b96e799 |
1292e664ae63e7b30b891f21dbcc21d9d0574516277a2b80e84638e7757c99a7 |
03767208d85bbdf1514508f176b779fab0805c7ede0c03328cbe4054d8b14e15 |
3baa42f89607ff21e7cdf7b18631d8610ebe8d3463ebf53e68ab488a60ce0b01 |
33974d7d1f9012095c74678b6204f736e59e733cafbb9f9f19fae94373ccf49a |
a1af0ce4c68f665285084e8edd7bc41ae93b44e06a460cc0b2204b5e98c84d3c |
0b809064ce20fcd07cc04b1124f54461d5cc420b065011b983aa1dce0dd939b6 |
4a5e8b0102136a2cb4f8c748751a88fa55801008b7832c9442b8c1eb97cd787f |
b0d090e1c5d6b484797c7be499b4be366e215f05a89aa5a56b4c20760ccd880b |
1640cd03f53e2de56aa866c72a9a3f6eaa7ba036b52e38f97a4a190b9c8cd083 |
e138c56b6f9c968e96e0a614353a9b984139159e68abcbd3f69cdcf4f1419792 |
b24c5de730bfc545634e80c241041702ffcc996a925e63e22ad40854916e95fd |
9fa6240c173ba6a9c5a31fdd294ac4c70a16ca9ac19b858608129f39d95e4321 |
742d37231ce24ff392e0239a29c7dbf1f3ca1556f9117ffe75c412154da32dfe |
6ad05f367c13ed6b095473ab67a1a8311e5ebf7172c2b543a402196ebbac8b84 |
e2b5ebd2b923cd351663c3acd2025cf6bb802a31f09c65c39fb2f4a54d9f6e93 |
3a07c8a902f158d099a860ed844026c35a204d2e304187ccc90112953e8c4f6b |
9e87484d77eff6a2e8b85b64d759e07a166f7994a9069e04d7a2aed93a0b5186 |
cb3dd6269e47e341a3cba362d7bb76f15e9653b698c9d3bae13413a70b166c55 |
6cd3e5c4e5bcd9e604e5c894b5b64cc766e6e3e81582ac259039ee4bd125905e |



