Our mission at SpyCloud is to disrupt cybercrime, so we spend a lot of time tracking and analyzing the TTPs bad actors are exploiting to enable all sorts of cyber threats. Infostealer malware is one that’s been on an upward trend the last couple of years, and we’ve kept a concentrated focus on this emerging threat, tracking and analyzing existing and new malware families like LummaC2, which frequently gets beefed up with significant upgrades.
However, it’s also worth noting that many older malware families, especially RedLine Stealer, remain juggernauts in the cybercrime ecosystem. Originally identified in 2020, RedLine steadily gained market share, in part due to the law enforcement takedown of Raccoon, and up until the announcement of Operation Magnus, remained a consistent threat.
About Operation Magnus & the RedLine disruption
On October 28, 2024 the Dutch National Police announced that they had disrupted the infrastructure of the RedLine and Meta infostealers. The disruption was conducted as part of international law enforcement Operation Magnus. To announce the disruption, the Dutch National Police shared an Operation Magnus website with a tongue-and-cheek video announcing the “final update” to the stealers, a link to an Operation Magnus Telegram account where individuals can contact the law enforcement teams working on this operation, and a countdown clock to another announcement.
On October 29, the US Department of Justice followed up with an announcement of their participation and partnership with other international counterparts on the “seizing of domains, servers, and Telegram accounts used by the RedLine and Meta administrators to disrupt the operations of the infostealers.”
In conjunction with the disruption effort, the DoJ unsealed charges against Maxim Rudometov, one of the developers and administrators of RedLine Infostealer. Rudometov is charged with regularly accessing and managing the infrastructure of RedLine Infostealer, being associated with various cryptocurrency accounts used to receive and launder payments, and being in possession of RedLine malware.
“RedLine was – by nearly any metric – the most prolific infostealer malware in history, resulting in substantially more infections than any other comparable malware to date. The actions taken by law enforcement during Operation Magnus represent a significant disruption to the RedLine and Meta network and will likely cause ripple effects throughout the entire cybercriminal ecosystem.
While we are seeing some initial volatility for RedLine since the announcement of this global takedown, it will continue to be interesting to monitor the prevalence of this infostealer family and the evolution or creation of others as bad actors work quickly for alternatives to keep momentum and productivity.“
Legacy malware infections by the (staggering) numbers
We analyzed data from the last 30 days as well as ‘all time’ (since SpyCloud began collecting infostealer malware in 2016) and compiled counts of unique infections by malware family. Notably, while SpyCloud tracks more than 60 individual families of malware, we scoped this analysis to the top 10 most prevalent infostealers within each time frame.
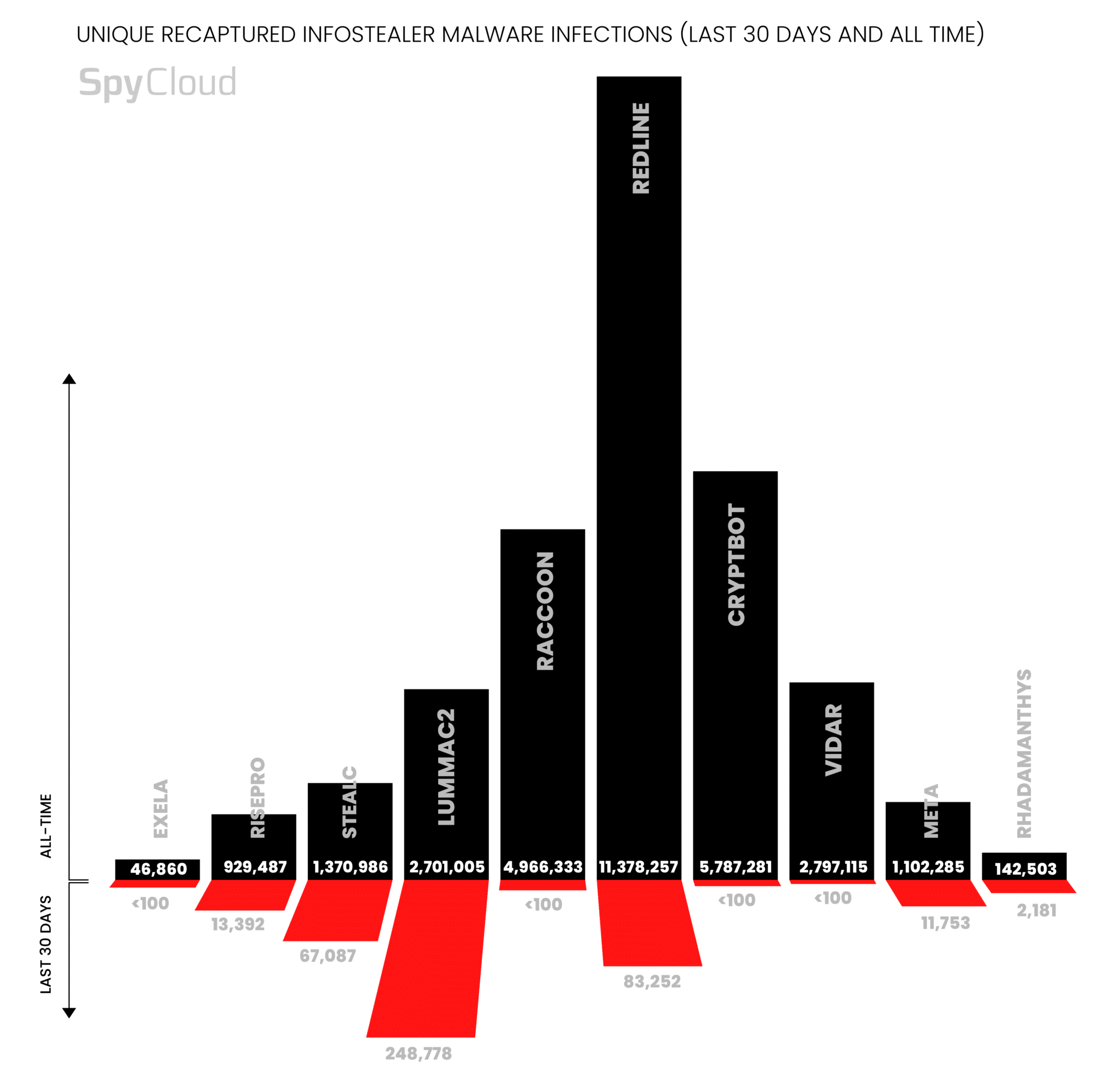
While graphs can help us understand the scope and trends of these threats, it’s worth noting that each individual infection shown above contained a host of information that landed in the hands of bad actors. And while some of these families have indeed diminished in recent years, others have remained consistent, and the sheer volume of stolen data is staggering.
How malware-exfiltrated data fuels the cybercrime ecosystem
The data exfiltrated from these infections – ranging from credentials, plaintext passwords, and PII to session cookies and files saved on the device – is then entered into a sprawling criminal marketplace where criminals can continue to sell and trade the stolen data to perpetrate fraud, identity theft, account takeover, and even ransomware.
Our analysis of digital identity exposure shows that the average digital identity is found in at least 9 breaches and has a 1 in 5 chance of already being the victim of an infostealer infection. Of the almost 4,000 breaches we analyzed for our Annual Identity Exposure Report, a majority of them (61%) were malware-related.
These numbers demonstrate that cybercriminals have a range of opportunities for gaining access to accounts, applications, and organizations overall from non-persistent threats like infostealer malware – and helps explain why the digital identity has become a top attack vector.
How to combat infostealer malware threats
There are actionable steps to prevent data stolen via malware infections from plaguing you and your company.
For organizations, it’s important to augment your malware incident response playbooks with a more robust post-infection remediation process. The benefits of automatically negating the value of data that has been stolen from employees, contractors, and suppliers before it can be used against your business cannot be overstated. We consider it a vital step in protecting your organization from cyberattacks.
And for individuals, if you are concerned about whether you have exposed data circulating on the dark web from breaches of sites you use, or from malware on a device you’ve logged into personal or work applications from, visit checkyourexposure.com. Enter your email(s) to receive a free exposure report detailing what information criminals have in hand and learn what you can do to protect yourself.



