In an era of escalating identity threats, the 2025 Verizon Data Breach Investigations Report (DBIR) reveals urgent trends no security team can afford to ignore. The 18th annual report once again delivers critical cybersecurity insights and analyses (along with its notoriously quippy footnotes) – but with 100+ pages, it can be a bear to dig through.
At SpyCloud, we combed through the latest findings to pinpoint some big takeaways security teams should know to better defend their organizations from account takeover, ransomware, and other identity-driven attacks.
Here’s what stood out.
TLDR;
- Third-party involvement in breaches doubled year-over-year.
- Stolen credentials are still the most common initial access vector.
- Verizon’s research shows that 30% of compromised systems in infostealer logs were enterprise-licensed devices. Similarly, SpyCloud’s most recent research shows that 66% of malware infections happen on devices with antivirus or endpoint security solutions installed.
- Verizon’s findings also support SpyCloud’s earlier research, which draws an important connection between infostealer infections and subsequent ransomware attacks.
- Ransomware still dominates the threat landscape, but resilience is improving.
- Yes, attackers are using AI, but the more concerning issue for now is that users are accessing GenAI tools with personal emails on corporate devices.
About Verizon’s 2025 Data Breach Investigations Report
Verizon’s newly released report analyzes over 22,000 incidents and 12,195 confirmed breaches – the largest dataset in DBIR history – and highlights the escalating complexity organizations face, especially from third-party risk, ransomware, and identity-based threats. This article highlights key data points from the report.
Top Findings from the 2025 Verizon DBIR
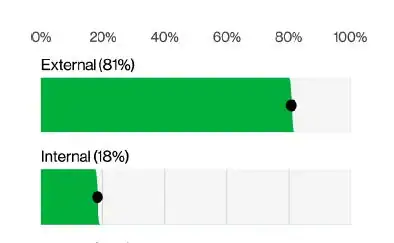
Who's behind the breaches? External and insider threats
When it comes to who’s behind today’s breaches, the data paints a familiar picture: external threat actors are largely responsible, accounting for the majority of incidents by a wide margin.
But that doesn’t mean teams should ignore insider threats – malicious or accidental – which remain a consistent although smaller portion of breaches.
Verizon’s breakdown shows:
- External actors: Leading cause behind System Intrusion, Social Engineering, and Basic Web Application Attacks.
- Internal actors: Primarily responsible for Miscellaneous Errors and Privilege Misuse
Whether credentials are compromised externally via infostealers or internally through misuse, security teams need visibility into identity analytics that illuminate past exposures and aid in investigations.
Third-party risk: A growing contributor to breaches
Third-party involvement in breaches doubled year-over-year, jumping from 15% to 30%. Whether it was software supply chain compromises or weak security practices at service providers, organizations increasingly found themselves impacted by security gaps outside their direct control.
While the vastness of the average supply chain can feel overwhelming, Verizon encourages teams to focus on holding vendors accountable and ramping up transparency and information sharing instead of “lying down on the floor and crying” (Verizon DBIR, pg. 19). SpyCloud offers supply chain exposure monitoring to help with this universal challenge.
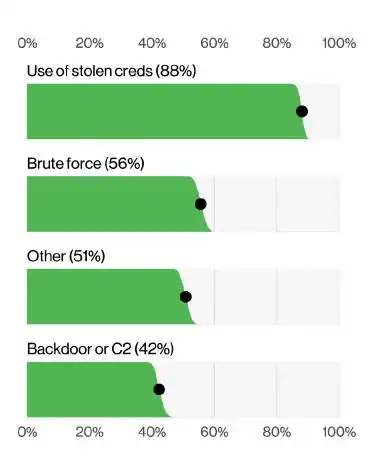
Credential abuse and stolen data remain the foundation for many attacks
Credential-based attacks continue to dominate the threat landscape. Verizon reported that stolen credentials were still the most common initial access vector — used in 22% of breaches. Also notable: 88% of basic web application attacks involved the use of stolen credentials, making it the dominant tactic in this pattern.
SpyCloud’s own research aligns with these findings: infostealer malware infections and successful phishing campaigns fuel the criminal underground’s supply of compromised credentials, enabling account takeover, ransomware deployment, and other attacks.
The proliferation of infostealers, the availability of stolen credentials in access brokers and our own results here in the DBIR that show credential abuse is consistently the top initial access vector can paint a picture that all is lost. ‘Assume compromise,’ some security companies used to say in their marketing materials. We have always thought that was too bleak, and to be honest, a bit paralyzing. Rather than ‘you have already been breached, so stop struggling,’ given the evidence we have presented, we are not blind to the risks. Perhaps a better, more constructive way of thinking of how this impacts your organization is to ‘assume access, ready defenses.
Notably, Verizon found that 54% of ransomware victims had prior credentials exposed in infostealer logs, 40% of which contained corporate email addresses, underscoring how access brokers are fueling ransomware ecosystems.
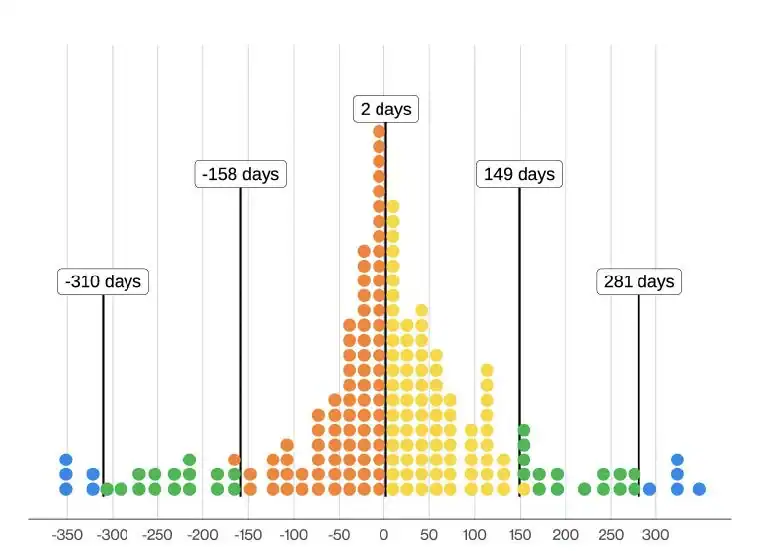
“Distribution of difference in days between ransomware posting and infostealer log discovery (n=503 – each dot is 2.52 ransomware victims)” sourced from page 57, 2025 Verizon DBIR.
Wondering how exposed your organization might be?
Ransomware still dominates, but payments are dropping
Ransomware remains a dominant force, appearing in 44% of breaches, up from 32% last year. However, there’s a glimmer of good news: organizations are becoming more resilient.
- The median ransom payment fell to $115,000, down from $150,000.
- 64% of victim organizations refused to pay ransoms, up significantly from 50% two years ago.
Post-infection remediation, including resetting stolen credentials and invalidating active session cookies, is a key addition to existing workflows to properly remediate the threat of malware-exfiltrated data and stop ransomware operators from reusing stolen access.
Once a human, always a human
The notorious human element – errors, social engineering, and misuse – still played a role in 60% of breaches this past year. Phishing, credential stuffing, and MFA bypass tactics like prompt-bombing remained top techniques.
Encouragingly, organizations investing in regular security training saw a 4x improvement in employee phishing reporting rates, per DBIR data. While education is critical, no one is immune to compromise, and almost everyone has identity data already circulating the criminal underground that can come back to haunt individuals and employers long into the future.
Other gaps in enterprise security
The 2025 DBIR also highlights another blind spot for organizations: the significant security risks posed by unmanaged or BYOD (bring your own device) systems. Infostealer malware infections, in particular, expose a dangerous gap between enterprise control and user behavior.
Verizon’s analysis found:
- 46% of compromised devices with corporate logins were non-managed systems.
- Many of these devices mixed personal and business credentials, offering attackers a clear path to infiltrate corporate networks.
- 30% of compromised systems in infostealer logs were enterprise-licensed devices – meaning even some managed systems aren't immune.

These findings reinforce a major enterprise security challenge: when employees use personal or poorly secured devices for work – especially without visibility or enforcement by IT – it dramatically expands the attack surface.
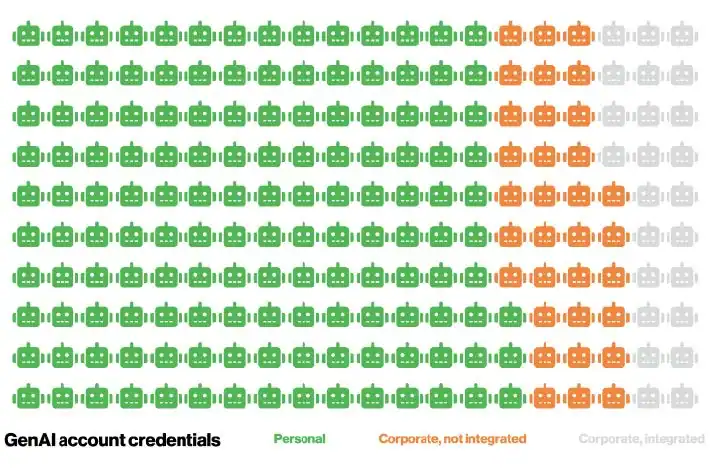
No surprise, but generative AI and data leak risks rise
- 14% of employees were found to be using GenAI tools on corporate devices.
- A concerning 72% of these users accessed GenAI services with personal emails or without an authenticated system in place, rather than secure corporate accounts.
Key takeaways from the latest Verizon DBIR
The 2025 Verizon DBIR makes it clear: today’s cybersecurity battle is identity-centric. Credential theft, third-party risk, and ransomware all stem from vulnerable identities — whether human or digital.
At SpyCloud, we believe in turning the tide against cybercriminals by providing organizations with early, actionable insights into their exposures. By recapturing stolen data from the criminal underground and enabling automated identity threat protection, we help businesses protect their people, customers, and bottom line.
SpyCloud helps enterprises worldwide protect billions of accounts and stop identity-driven attacks before they start. To see insights on your organization’s exposed data, check your exposure now.