We’re back with more infostealer updates – and a little twist: keyloggers are (sort of) back on the scene!
As malware usage shifts in the criminal underground, so too does our product offering here at SpyCloud. SpyCloud Labs keeps a firm pulse on how cybercriminals are using infostealers – and which they’re favoring – so we can recapture the data and provide critical exposure insights to customers. As of the publishing of this blog, we’re actively recapturing nearly 60 different infostealer malware variants.
What's new: Stealers & keyloggers we're tracking
Several new malware families have popped onto our radar recently:
- Kemicat Infostealer
- Mephedrone Infostealer
- Prometheus Infostealer
- WorldWind Infostealer
And a little surprisingly, we’ve also observed a comeback in keylogger records in the criminal underground, including:
- Snake Keylogger
- [Unnamed Keylogger], which we’re calling “Artemis”
Kemicat Stealer
SpyCloud Labs recently observed a new stealer billing itself as the Kemicat Stealer. While no public reporting was available on the stealer as of the publish date, the stealer appears to heavily target gamers. Based on logs collected by SpyCloud, Kemicat steals the Steam library (not new or novel in itself, but Kemicat actually makes a whole folder called “_gaming” for gaming-related theft) and Discord. In addition to these categories, Kemicat also steals form fill data, browser bookmarks, internet history, and saved credit cards.
Interestingly, unlike many other infostealers that produce folders only if a specific asset is found on the infected device (for example, saved credit card data), Kemicat creates the same folder structure regardless of the data that is actually exfiltrated from the infected host.
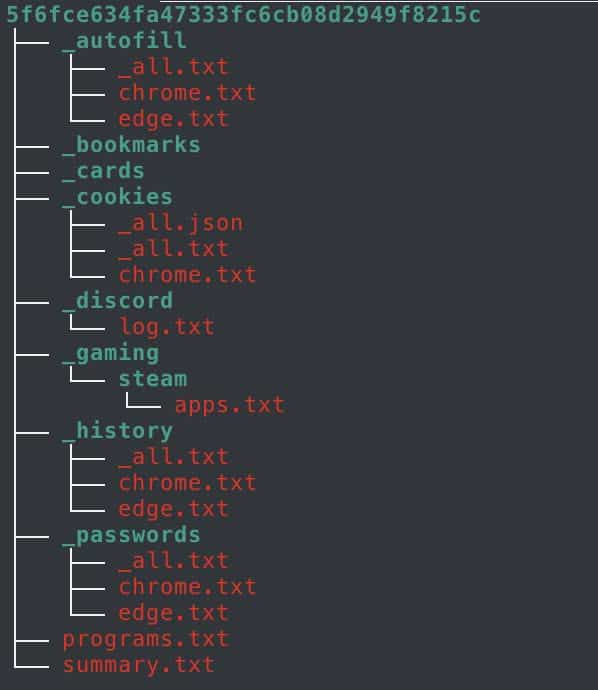
Notice that the folders “_bookmarks” and “_cards” both exist in the log even though neither folder has been populated with stolen data.
Mephedrone/Phemedrone Stealer
The Mephedrone Stealer appears to be a slightly modified variant of the Phemedrone stealer, based on our comparison of log outputs from the two malware variants. In fact, many of the error files that are generated by Mephedrone actually state “Phemedrone” in them, supporting this connection.
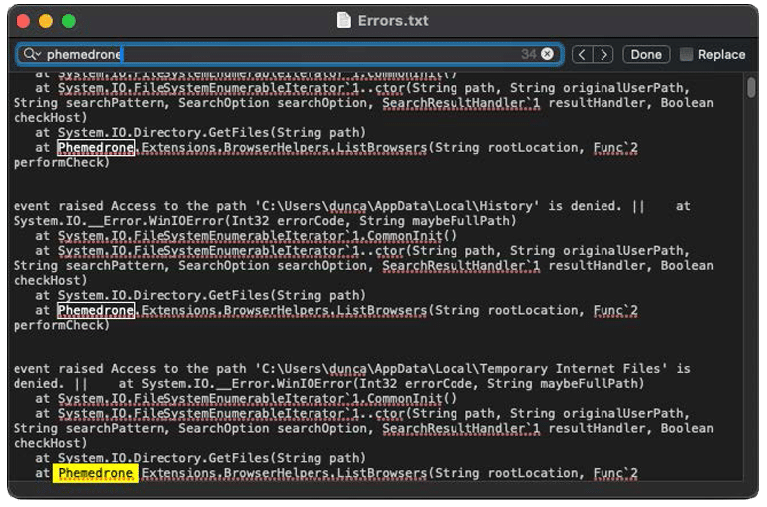
Example of a Mephedrone log where Phemedrone appears multiple times.
The Mephedrone variant appears to be largely similar to Phemdrone, with slightly modified log. “Phemedrone” in the stealer log outputs have been replaced with “Mephedrone” and there are some other minor log changes.
Phemedrone is an open source stealer written in C# that targets Windows computers and steals from browsers like Chrome, Firefox, Edge, as well as applications such as crypto wallets, Steam, Telegram, and some VPNs. Additionally, Phemedrone allows threat actors to choose to send logs to a C2, or over Telegram, with Telegram having an optional RSA encryption (which is not implemented in released versions of Phemedrone). As this bot is open source and C#, presumably groups that run it can and will easily modify the code for use, as is the case with Mephedrone.
Prometheus Stealer
Prometheus is an open source stealer available on GitHub and is written in Python. Similar to other infostealers which have risen in popularity recently, Prometheus allows exfiltrated logs to be streamed directly to Discord or Telegram, reducing the infrastructure requirements for an actor seeking to deploy the stealer.
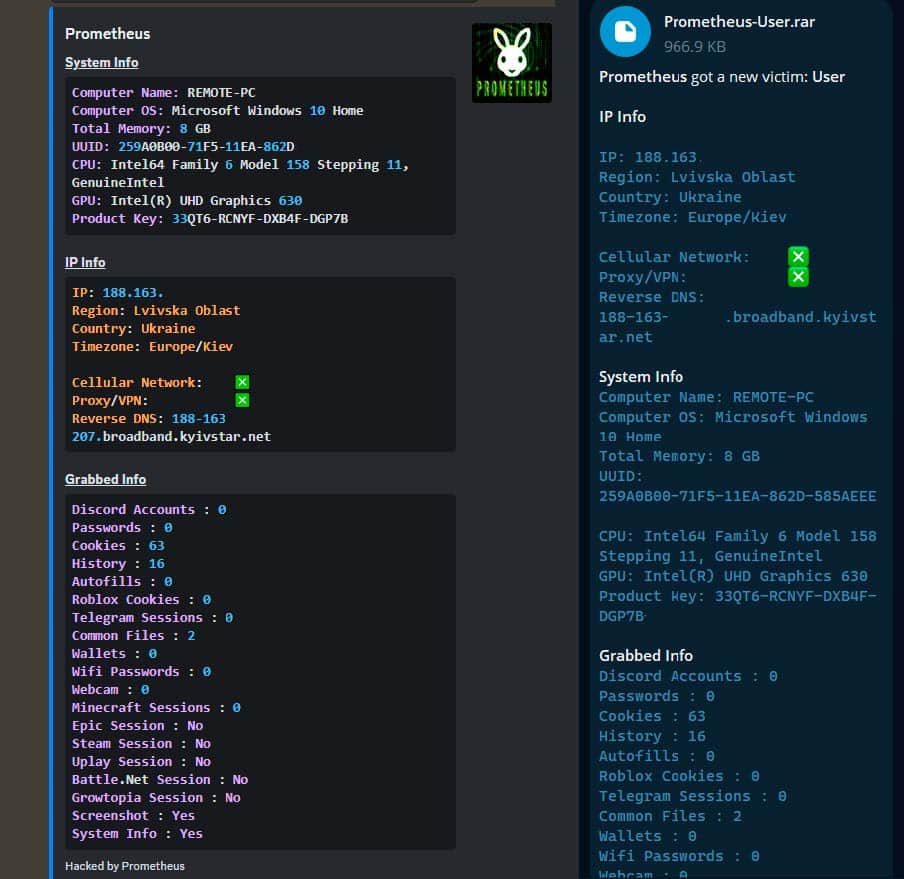
Information about Prometheus as shown on the corresponding GitHub page.
One notable feature of Prometheus is the ability to steal WiFi network credentials (SSID and password), as well as capturing a full file tree of the following Windows folders, if found:
- Desktop
- Documents
- Downloads
- Pictures
- Music
- Videos
WorldWind Stealer
WorldWind is not a new infostealer (having been originally released for sale in 2022 as Prynt Stealer), but it’s seeing something of a renaissance in 2024.
Offering data delivery exclusively through Telegram, WorldWind has broad data theft capabilities, including the ability to steal browser information – form data, cookies, bookmarks, history files, and more – as well as files from directories on the infected host. WorldWind constructs a similar file tree-like output as Prometheus (detailed above), and also includes a function that can steal the Windows product key from the infected host machine.
WorldWind lacks many configuration options available from more advanced stealers like LummaC2 or RisePro, however, the simplistic builder has been lauded by criminals as easy to use and highly effective.
The resurgence of keyloggers
Keyloggers are not a new type of malware, and they never really went away. Nonetheless, SpyCloud Labs has seen a marked increase in the amount of keylogger-exfiltrated data that is being shared among cybercriminals, particularly on the messaging platform Telegram, in the past few months.
Snake Keylogger
Snake is a keylogger that was released as early as 2021 and has seen sporadic attention over the past few years. Originally supporting exfiltration by email, newer versions of Snake use Telegram as their primary means of retrieving logged data. As we’ve made clear in other parts of this blog, we feel this is notable as it means that new users of Snake have far less set-up to do before being able to deliver the malware and receive stolen data.
Snake’s capabilities include theft of saved credential data, copying text from the clipboard, recording keystrokes, and collecting credentials from email clients including Outlook. Notably, these capabilities lack some of the more sought-after data assets available from infostealers, especially cookie data.
As we’ve discussed in other blogs, cookie data is highly prized by threat actors and used to bypass authentication, especially when the targeted service employs MFA as a means of further securing the login process.
Agent Tesla
The second keylogger that has appeared in SpyCloud’s recaptured data collection is the Agent Tesla, which saves its output within a single HTML file. Like Snake, this keylogger exfiltrates these logs via Telegram, and in addition to stealing clipboard contents and tracking keystrokes, also extracts limited host information such as the Windows user name, local hostname, CPU and RAM configuration, and Windows version.
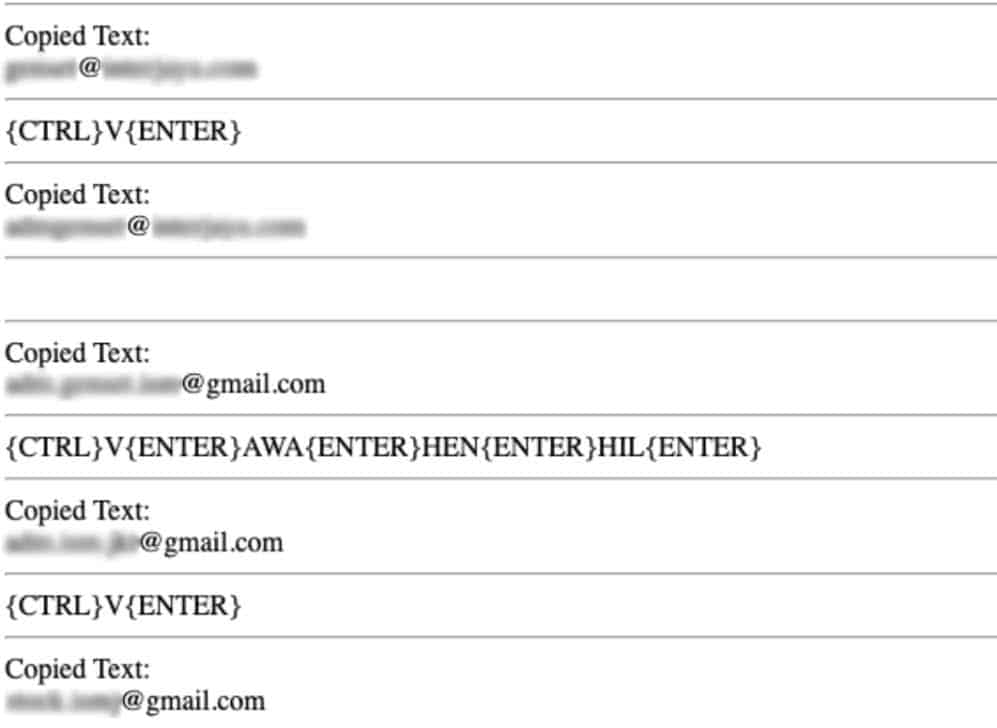
Screenshot of an “Artemis” log file showing the clipboard theft and keystroke logging capabilities. Emails have been blurred to protect victim privacy.
Interestingly, many of the Artemis logs SpyCloud Labs has collected appear to have been created from infections of Windows devices in the Asia-Pacific (APAC) region, with a preponderance appearing to use a version of Chinese. It is not currently known whether this is a coincidence, an artifact of SpyCloud’s collection methods, or active targeting of the APAC region.
How to reduce enterprise risk stemming from infostealer malware & keylogger infections
We recommend implementing industry best practices to prevent and remediate infostealer malware and keylogger exposures to keep your organization best protected from follow-on attacks like account takeover, session hijacking, and ransomware:
- Implement a solid antivirus program
- Enforce advanced authentication through MFA and passkeys
- Implement cookie expiration and invalidation policies
- Make sure you have comprehensive management over your devices and networks, including a strict bring-your-own-device (BYOD) policy
- Continuously monitor for malware exposures in the criminal underground
- When a malware exposure is detected, be sure to isolate, image, and wipe the device, if accessible, and:
- Reset passwords and usernames for affected applications
- Invalidate the user’s web sessions to prevent session hijacking
- Review all activity and access logs for the user within affected applications to confirm that detected activity is coming from expected IP address ranges and geographies and that all behavior fits the expected profile of the user
SpyCloud Labs keeps a tight pulse on the criminal underground and adds new malware families to our daily ingests as they surface. See other infostealer families we’ve recently added to our collection here.



