As we reported in a previous post about China-based threat actor TTPs, Chinese-language criminal actors have unique methods of data collection and aggregation that can give them extremely detailed pictures of individual targets. These actors offer data collection as a service, and then sell the exfiltrated data to competitors, hackers, data vendors, and the black market for further exfiltration and cyberattacks.
In this blog, we’ll take a deeper dive into the techniques China-based threat actors refer to as SDK and DPI, which they use to primarily target the mobile application supply chain and collect “fresh” data directly from the source. Additionally, we’ll take a closer look at SGKs, which house the exfiltrated data from the SDK and DPI collection methods as well as other hacked databases and can be queried to find detailed information about Chinese residents.
How Chinese-language actors advertise illicit data collection services
In our research, we have uncovered a range of different keywords that these actors use to advertise their data collection services on X, Telegram, and clearnet websites.
Terms used synonymously with SDK, DPI, and SGK
| English Terms | Chinese Characters |
| First-hand data | 一手数据 |
| Primary data/First-hand data resources | 一手数据资源 |
| Fresh data | 新鲜数据 |
| Accurate data | 精准数据 |
| Real-time data | 实时数据 |
| Operator data | 运营商数据 |
| Operator big data | 运营商大数据 |
| Big data customer acquisition | 大数据获客 |
| Three network data | 三网数据 |
| Industry-wide data | 全行业数据 |
| Domestic data | 国内数据 |
| Online shopping data | 网购数据 |
| Human Flesh Search | 查人 人肉搜索 |
These terms are used by China-based actors to sell breached data and hacking services, such as Distributed Denial-of-Service (DDoS) attacks, SMS hijacking, and DNS hijacking.
Vendors that advertise operator-related data services also appear to include marketing services that operate in a gray area, between legitimate services authorized by statute and those which would be best described as criminal in nature. These ‘marketing services’ that engage in illicit data collection in Chinese-speaking criminal communities share some similarities with Western pay-per-install (PPI) networks, which are popular services for malware distribution.
Breaking down the top Chinese-language actor TTPs
Let’s dive into the technical analysis of these TTPs:
SDK data collection method
In our last blog on Chinese cybercrime, we provided an overview of how Chinese actors are using Software Development Kits (SDKs) to steal massive amounts of user data that they can resell in criminal marketplaces.
A quick recap on SDKs
- SDKs are legitimate packages of software tools that are bundled together to be used by app developers.
- China-based criminal actors trojanize existing SDKs or create new malware ones that inject malicious code into applications. We primarily observe SDKs being used by actors to target mobile apps.
- Trojanized SDKs are advertised as optimized code with the aim of saving time and effort for development over the vanilla SDK versions.
- Malware SDKs are advertised to unsavory developers as “invasive application creation kits” that allow developers to exfiltrate data from users of their applications.
- Both trojanized and malware SDKs contain malicious vectors in the form of excessive permissions, backdoors, or both. Often application end users cannot fully access the compromised app without agreeing to the excessive permissions on installation.
- These excessive permissions effectively give actors root-level access to Android and iOS devices that have installed apps created with the malicious SDKs.
- Both SDK types allow for the threat actors to directly exfiltrate user data, sometimes with or without the developers knowledge.
The data collected and exfiltrated through the SDK method are mainly domestic (to China) personally identifiable information (PII) that includes full names, phone numbers, genders, ages, and location information. However, it varies based on the type of app, its intended audience, and other factors.
The information collected, extracted, and sold from the SDK exfiltration method may also include online behavior records (such as frequently used apps or visited websites), the users’ contacts, and the user’s personal account information from other applications installed on the mobile device. Criminals use this data for a variety of cyber attacks, especially online shopping and financial fraud.
Threat actors usually post a list of the SDKs they have direct access to, which they refer to as a ‘library.’ For example:
Table 1: Example SDK Library
| Alipay |
| Kuaishou Express |
| China Construction Bank |
| Postal Savings Bank of China |
| Douyin Express |
| Meituan |
| Ping An Guarantee, Personal Loan, Auto Finance |
| WeChat Business Bank |
| Everbright Futures |
| Guangzhou Futures |
| Chongqing Credit Loan |
Table 1 shows a list of applications that China-based threat actors claim to have backend access to.
Based on the sheer breadth of persistent access that these malicious actors claim to have, we assess with moderate confidence that some of these actors are likely tainting and repackaging open source SDKs to add in vulnerable or malicious components. By repackaging popular development tools with their own malicious code, these actors are targeting the mobile application supply chain as a vector to harvest data from mobile end users.
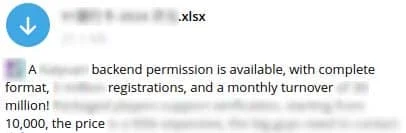
Figure 1: A China-based threat actor providing a data leak file and advertising that backend permissions are available and other high quality data features.[1]
SpyCloud Labs researchers have conducted a static analysis of applications and have observed excessive permissions as shown below in Figures 2, 3, and 4.
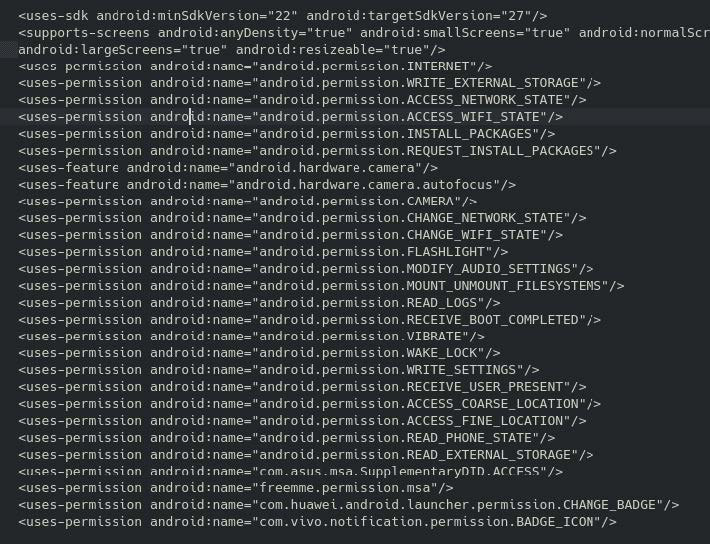
Figure 2
In this instance, an application that is mainly used for venue and activity management is requesting excessive permissions, as noted in the manifest file.
These permissions include:
- [ACCESS_NETWORK_STATE] Allows the application to check if the device is connected to a network and the type of network connection. This permission could be used to monitor when the device is online and track user activity based on the network status.
- [CHANGE_NETWORK_STATE] Allows the application to change the device’s network. This could be used maliciously to disable the internet or switch networks without the users’ knowledge, such as enabling insecure or compromised connections.
- [ACCESS_WIFI_STATE] Allows the application to view current WiFi connections, the list of WiFi networks, and the connection state. This may be used for WiFi tracking.
- [CHANGE_WIFI_STATE] Allows the application to enable/disable the WiFi connection, which could be exploited by malicious actors by forcing the device to connect to untrusted or malicious networks.
- [INSTALL_PACKAGES] Allows the application to install other APKs on the device without user interaction. Malicious actors could install other apps or even malware on the device.
- [REQUEST_INSTALL_PACKAGES] Allows the application to request the user’s permission to install packages. However, a malicious application could repeatedly prompt users to install malware.
- [READ_LOGS] Allows the application to read system and application log files. System logs can contain sensitive user information, app states, and errors that could be exploited by a malicious application to gather data about the device or user.
- [RECEIVE_BOOT_COMPLETED] Allows the application to automatically start running when the device finishes booting. A malicious application could use this to start itself every time the phone reboots, which allows it to run covertly without user interaction and survive reboots.
- [WAKE_LOCK] Allows the application to prevent the device from going to sleep or turning off the screen. As such, malicious applications could prevent the device from entering sleep mode, potentially enabling unauthorized activities such as data collection.
- [WRITE_SETTINGS] Allows the application to modify system settings. A malicious application could use this for system manipulation and change critical settings such as disabling security features, modifying network settings, or enable insecure settings such as turning off encryption or screen lock protections.
- [RECEIVE_USER_PRESENT] Allows the application to detect when the user unlocks the device. A malicious application could track when and how often the user interacts with the device, leading to user behavioral profiling. Additionally, it could use this permission to trigger malicious activities and execute tasks such as data exfiltration the moment a device is unlocked.
The same threat actor also shared data derived from an application made with this APK code, showing they were able to extract user information such as username, mobile information, login IP address, and registration IP address.
While these permissions may be essential for specific functionalities of the application and may be used individually based on the application’s purpose, when combined, they can pose significant security risks.
The excessive permissions shown in Figure 3 and Figure 4 below are derived from an APK template shared between threat actors on a China-based hacker channel. The purpose of this APK is to provide pre-written base malicious code to hackers to embed in SDKs they develop.
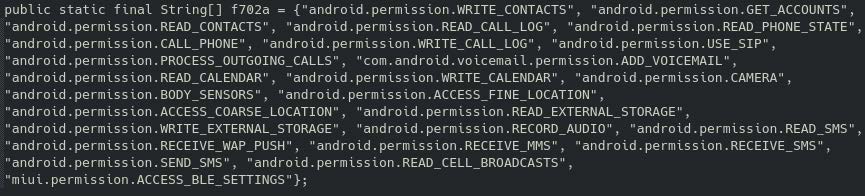
Figure 3: A sample of pre-written code designed to be embedded in SDKs to extract user data.
The code in Figure 3 includes excessive permissions, as it provides access to:
- [GET_ACCOUNTS]: Allows the application to retrieve a list of accounts stored on the device, in which malicious apps could collect the list to conduct phishing and fraudulent attacks and it can also access account information
- [READ_PHONE_STATE]: Allows the application to access the phone number, network information, ongoing calls, and the SIM status; this can lead to unwanted tracking of the user and targeted attacks using personal device information
- [CALL_PHONE]: Allows the application to initiate phone calls without user interaction, which can be used to place unwanted calls, especially to numbers that may compromise the user’s privacy and security
- [WRITE_CALL_LOG]: Allows the app to modify or delete entries in the call log, which could be exploited to hide evidence of unwanted phone calls
- [READ_EXTERNAL_STORAGE]: Allows the application to read files from external storage such as photos, videos, files, and documents. With this type of access, such data files can be exfiltrated without the users’ knowledge
- [WRITE_EXTERNAL_STORAGE]: Grants the application the ability to write and modify files on the external storage in which a malicious application could modify or delete important files or even replace them with malicious ones
- [RECORD_AUDIO]: Allows the application to capture audio on the device’s microphone; however, malicious applications could record audio without the users’ knowledge and could capture private information
- [READ_SMS]: Grants the application access to read text messages stored on the device. Malicious applications can have access to read One-Time Passwords (OTPs) for Two-Factor Authentication (2FA), which can lead to Account Takeover (ATO).
- [SEND_SMS]: Grants the application permission to send text messages on the user’s behalf. With this permission, malicious actors can send unauthorized messages without the user’s consent which can lead to cyber attacks.
- [ACCESSIBILITY_SETTINGS]: Allows the application to access and modify the device’s accessibility settings, such as screen readers and magnification. However, a malicious application could exploit this permission to enable features such as screen reading or tap simulation. These features would allow it to capture user input or interact with other applications, without the user’s knowledge or consent, potentially leading to keylogging or account takeover.
Many of the permissions outlined in this template grant access to sensitive user data. When integrated into an application, these permissions could be used to collect and exfiltrate this information.
Moreover, access to personal data such as text messages, call logs, and contacts could be exploited by threat actors to track users, create and maintain highly accurate user profiles with behavioral data, and conduct phishing or other cyberattacks targeting the user’s friends and family.
As previously mentioned, China-based threat actors claim that in China some applications require users to grant all requested permissions and those who decline are unable to use the application completely. Some companies justify this by claiming they may need the information in the future, even if it’s not currently necessary. However, it’s crucial to remember that excessive permissions can pose significant security risks, increasing the potential for data collection, further exfiltration, and cyberattacks.
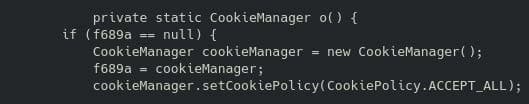
Figure 4: A sample of pre-written code designed to automatically accept all cookies on behalf of a user.
This code above sets the cookie policy of an application to accept all cookies. This raises security and privacy concerns, such as session hijacking, cross-site scripting, and data exfiltration:
- Session hijacking can occur if an application accepts all cookies indiscriminately. Injecting malicious cookies can lead to this type of cyberattack.
- Cross-site scripting can occur if an application accepts cookies without proper validation; a threat actor can inject malicious scripts to steal cookies and potentially exfiltrate data.
DPI (三网数据) data collection method
For China-based actors, DPI refers to more than just deep packet inspection – instead, it refers to a collaborative data collection method between China’s telecommunication operators, marketing companies, and malicious cyber threat actors and hackers.
DPI for these individuals and groups combines data aggregation, data enrichment, and data mining. This appears to take place through two main methods, which differ depending on whether or not the owners of a website or application consent to having this data collected from their users.
1. DPI data collection with user consent:
Some companies legally allow telecom companies to insert crawlers on their websites and capture visitor data for data collection and analysis. When this happens, marketing companies create user profiles (name, birthday, gender, region/location) for end users based on the IMEI and phone number they receive from the telecom operator.
User profiles generally include a person’s full name, date of birth, gender, email address, phone number, location, financial information, and internet behavior, such as frequently visited apps and websites. These profiles are made from behavioral modeling of a user’s online behavior.
2. DPI data collection without user consent:
When companies do not allow telecom operators to crawl their website, a more sophisticated and nefarious tactic is at play. Threat actors use insider access to telecommunications provider infrastructure to track when users visit certain webpages. When a customer approaches a criminal data seller to request data about users of an application or website that is not already listed on the TA’s SDK/DPI library, the actor will ask the customer to find the exact target URLs that they want to buy data for.
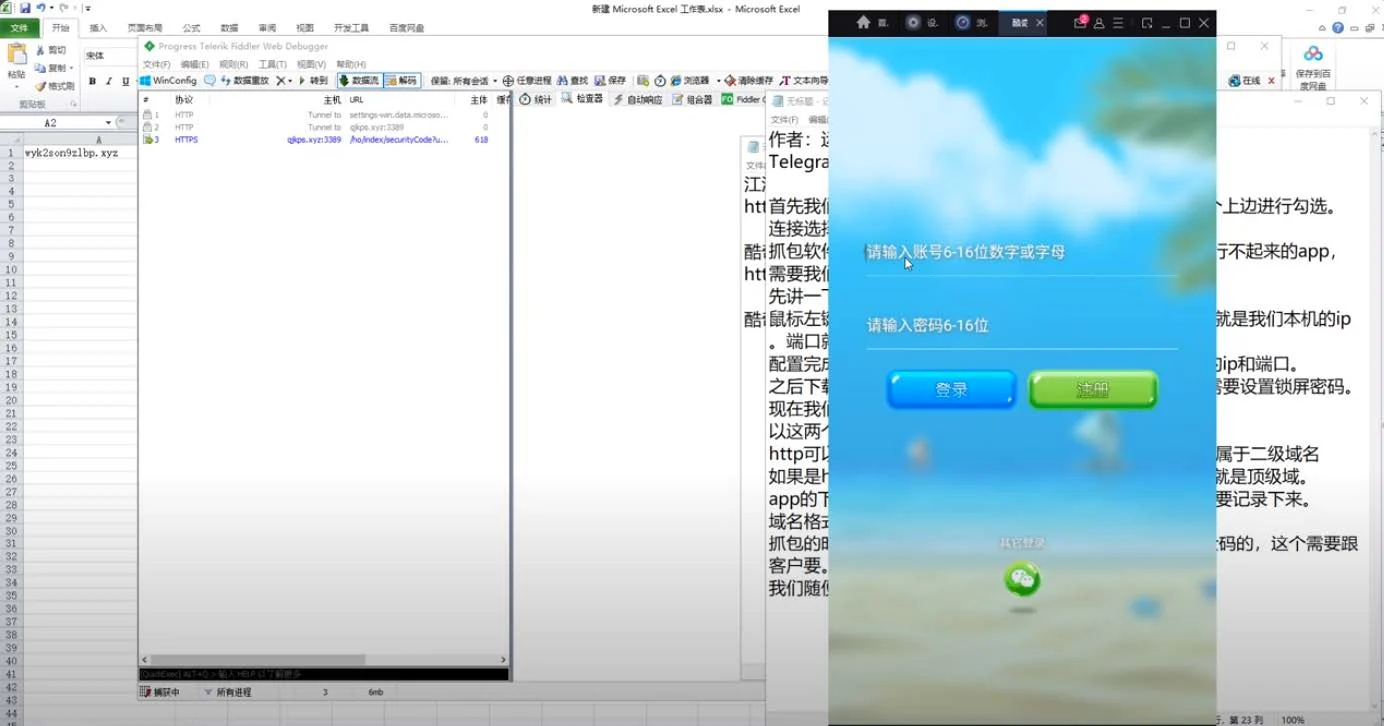
In our research into these groups, we found a step-by-step tutorial for these customers to show them how to extract their desired target URLs for mobile application traffic, as seen on Figure 5. In this tutorial, they use the Telerik Fiddler debugging tool for mobile applications to capture application web traffic and generate the exact URLs of the account creation and login pages of the targeted application. The malicious actors provide their customers with a Bill of Lading form that includes the target URLs, quantity of records, gender, location, and other fields to filter the data if desired by the customer. After this form is submitted to the sales agent, it is then submitted to the insider agent, who claims to have access to view the data traffic through network monitoring methods. The direct translation of how they refer to this traffic monitoring is inside the “screening” or “computer” room.
When the insider agents who allegedly work for telecom operators are informed of the target URLs, they proceed to collect visitor traffic on the URLs. However, they may be limited to observing the IMEI of the mobile phone number(s) that belong to their telecom company. The telecom companies are able to match IMEIs with user profiles of customers and their network IP addresses when they are accessing the internet.
For example, let’s say a Chinese citizen named Zhang Wei (张伟) who has a phone with the IMEI number XXXX is visiting example[.]com on September XX, 2024. The telecom operator can see that Zhang is visiting this website on their network traffic logs. To obtain additional information such as a user profile on Zhang, they are able to match the IMEI number to the associated mobile phone number. Marketing companies can then match the mobile phone number to a comprehensive user profile. Some data brokers also allegedly claim to have assistance from insiders for some mobile phone manufacturers. This assistance may come in the form of providing IMEI numbers and also having pre-installed and trojanized applications.
In short, mobile phone users’ traffic is monitored by telecom companies. The telecom operators then communicate with marketing and third-party services to enrich the collected data based on a user’s IMEI to build a more robust user portrait. If all other methods fail, malicious actors also offer their “penetration services” against targeted apps or websites.
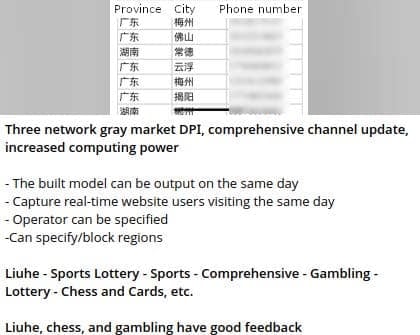
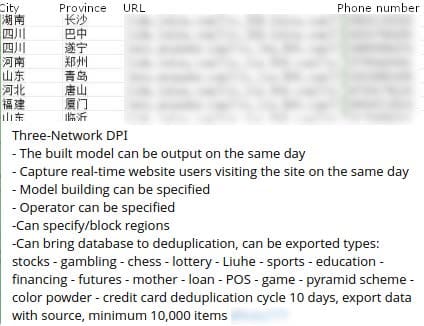
These data brokers market their services to potential customers by claiming that if they don’t give their sales staff highly detailed data on their clients, they are sending them into battle without equipping them with “swords to fight.” [A] According to one data seller, “the integration of the three networks [China’s telecom operators] and operator big data [marketing companies] will make it easier, cheaper, and more accurate to acquire customers, thereby increasing a company’s sales.” [B] Additionally, they flaunt that they are “always adding onto their data models,” meaning that they are always adding more sources to their SDK/DPI ‘libraries’. These data brokers will “establish models on the behaviors of users accessing or registering on websites, apps, receiving verification codes, and calling 400 numbers[2],” allowing their customers – both businesses marketing their products and social engineers trying to defraud users – to meet their goals.
The DPI data exfil method is referred to as highly timely, as orders can be processed the same day or by the next day and is also highly accurate because the data is collected via direct monitoring of users.
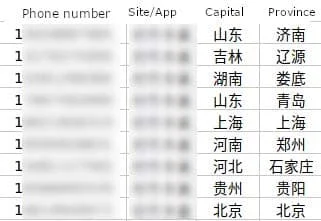
Figure 7 shows a China-based Telegram actor’s data leak channel advertising DPI data for sale with high quality features of data extraction.[3]
Figure 8 shows a China-based Telegram actor’s data leak channel advertising DPI data for sale with high quality features of data extraction, deduplication, and industries that data can be extracted from. [3]
Recruiting techniques:
SpyCloud Labs analysts have also observed Chinese-language cybercriminal actors post public recruitment ads for ‘internal cooperation’ personnel as shown on Figure 9 and 10.
In one of these posts, an actor states that, their “most profitable projects include those with access to bank statements, judicial freezing, room sharing, WeChat, QQ, call records, those in the Public Security Bureau, and those who work in public banks,” as seen on Figure 10. They claim to operate under a “professional gray monetization service, and distribute commissions earned from inquiries [orders] through virtual currency.” They also promise to coach new ‘internal cooperation personnel’ through how to avoid risks of being caught as well as how to mix and withdraw virtual currency.

Figure 9 shows a China-based Telegram channel recruiting agents for the cybercrime industry.[3]
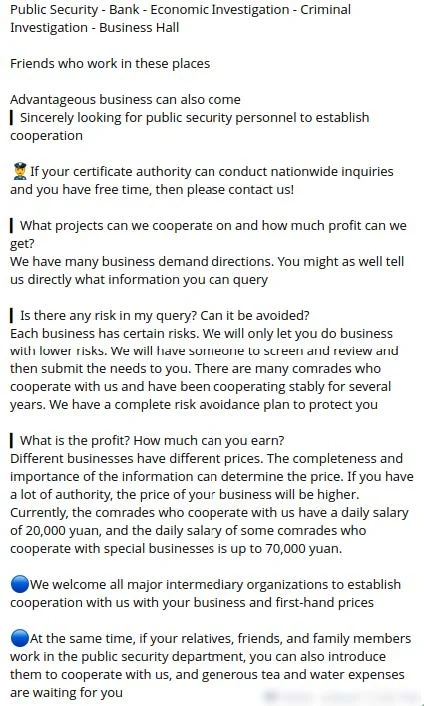
Figure 10 shows a China-based Telegram channel recruiting agents for the cybercrime industry. [3]

Figure 11 shows A China-based Telegram channel recruiting agents for the cybercrime industry. [3]
Social Work Library (SGK 社工库)
Social Work Library is referred to as SGK because the translation of the term is ‘Shègōng kù.’ It is also commonly referred to as a social engineering database, social worker database, and human flesh search.
This database is a repository of leaked PII, created by Chinese-language threat actors that compile hacked and leaked databases. Some are fully public, while others require engaging with an actor to gain access.
These libraries generally contain basic information on individuals such as their name, national ID number, and photo, and they may also contain additional PII like place(s) of residence, place(s) of work, business trips (past and future), place(s) of travel, income level, shopping habits, movies watched, restaurants visited, purchases made, and other behavioral data.
SGK libraries can paint a highly accurate “user portrait” for malicious actors, which enable them to create profiles on targets. These types of libraries are referred to as “social engineering” databases by threat actors because with the amount of fine detail found in these libraries, actors can more convincingly use social engineering methods to commit fraud, phishing, and other forms of cyberattacks targeting individuals and their employers.
The China-based actors host SGK libraries on clearnet websites and Telegram channels, and the data that can be found therein include, general PII, banking or other financial information, social media data, residency information, and travel and lodging information.
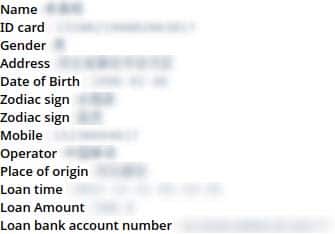
Figure 14 shows a China-based SGK query with detailed PII results. [3]
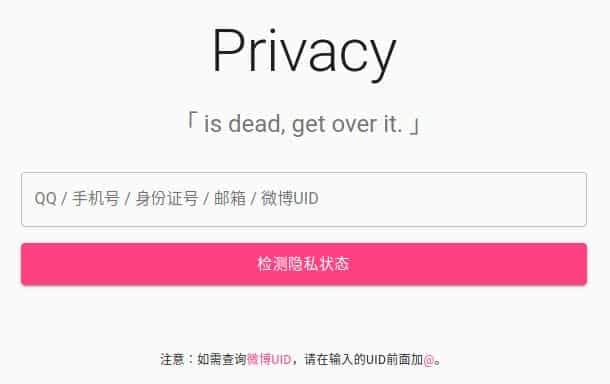
Figure 12 shows an SGK clearnet website that can be queried through QQ numbers, mobile phone number, national ID number, email address, or Weibo ID.
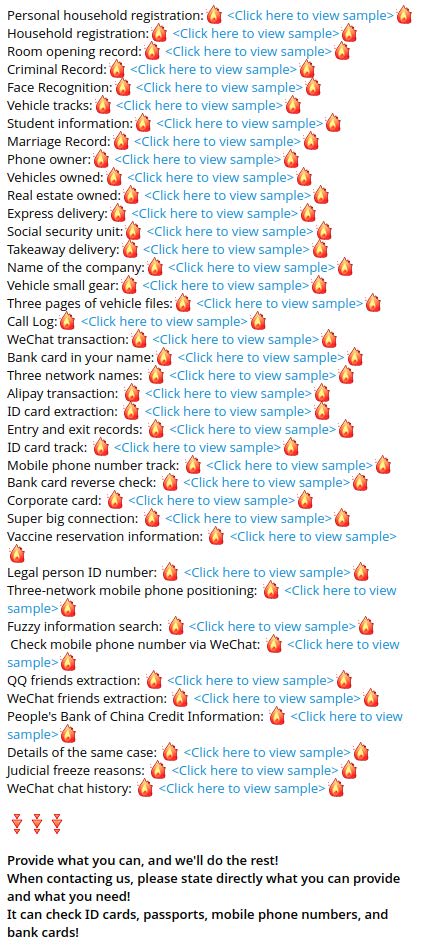
Figure 13 shows an SGK Telegram channel that describes the detailed information that can be found in SGK libraries [3]
Summary of research findings
The intricacy of Chinese cybercrime TTPs is both unique and highly effective for threat actors. Here are some of the things that set it apart and that should be kept on the security community’s radar:
- China-based threat actors are targeting the mobile application supply chain. SpyCloud Labs researchers have observed excessive permissions in SDK applications being used to exfiltrate user data. These actors have constant uploads of library lists of SDKs they claim to have backend access to.
- DPI is a collaborative data collection method involving several players. It combines the access of China’s telecommunication providers with marketing companies and malicious cyber actors to collect, aggregate, and enrich PII data.
- Chinese-language cyber actors are recruiting insiders. They are constantly seeking to collaborate with and leverage the access of personnel from the Public Security Bureau and Public Banks for profitable projects in the gray/black market industry.
- Stolen user profiles are highly accurate and can be queried through SGKs. Due to the constant data collection through SDK and DPI methods, user profiles contain more than PII- they contain behavioral records that are perpetually updated and can be used by malicious actors to create profiles on their targets.
Our team at SpyCloud Labs continues to monitor the Chinese-language threat actor community and will provide new research as we uncover it in additional blogs.
Read more from SpyCloud Labs
Sources:
[A] https[://]www[.]bilibili[.]com[/]read[/]cv27089075
[B] https[://]www[.]sohu[.]com[/]a[/]457256002_121005322
[1] The text in this figure was translated to English using the Telegram Premium translation feature.
[2] A 400 number is a toll-free number in China, mainly used by businesses.
[3] The text in this figure was translated to English using the Telegram Premium translation feature.