PRODUCT: ENDPOINT THREAT PROTECTION
Remediate
Malware-Infected Users & Applications
Infostealer malware silently exfiltrates authentication artifacts from infected devices – and your enterprise inherits the risk. SpyCloud delivers definitive post-infection evidence for SOC teams to act on immediately – shutting down follow-on identity attacks like account takeover, lateral movement, and ransomware before they escalate.
HOW IT WORKS
Where EDRs fall short, Endpoint Threat Protection fills the gap
SpyCloud Endpoint Threat Protection solves the overlooked problem of remediating data stolen by infostealer malware – especially critical when endpoint protection tools miss two-thirds of infections. Give your SOC critical visibility into the attack surface: the exact malware-exfiltrated credentials, session tokens, and application access artifacts tied to infected users, across managed and unmanaged endpoints.
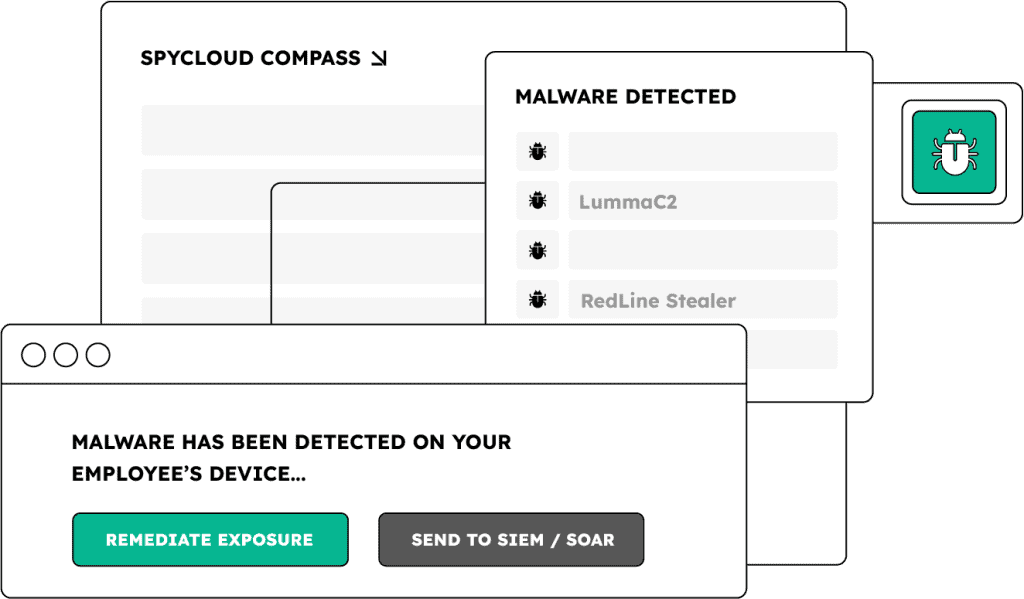
Expose malware-infected users & devices
Detect infections on managed and unmanaged endpoints – including BYOD laptops and remote contractor devices – before attackers escalate
Reveal stolen access for critical applications
Understand your risk from exposed SSO logins and business-critical apps that house sensitive data and IP, as well as shadow IT apps accessed with a corporate email address
Automate malware post-infection playbooks
Trigger password resets, invalidate sessions, and review access using context-rich identity exposure data for post-infection remediation
PRODUCT DEMO
Explore how SpyCloud's continuous endpoint threat protection works
Built for the stack you already run
SpyCloud Endpoint Threat Protection integrates into your EDR, SIEM, and SOAR tools – enriching the workflows your SOC already uses to detect and contain identity threats without extra lift.
EDR integrations
Reveal infections missed by EDRs – especially from unmanaged or bring-your-own devices

SIEM integrations
Add malware exposure intelligence to enrich alerts and correlate with endpoint and authentication activity
SOAR integrations
Automate high-confidence responses like credential resets and user lockdowns, directly from verified exposure data


You can’t really put a number on what was saved by just having this information.
EXPLORE OTHER PRODUCTS
Protect more than logins
Compass works alongside other SpyCloud products to deliver holistic identity threat protection.
Next steps
Don’t let malware-exfiltrated data lead to a full-blown incident. Get a demo today.