PLATFORM
Protect Customer
Accounts & Stop Fraud with
Consumer Protection
Accounts & Stop Fraud with
Cybercriminals exploit more than just passwords — they weaponize session cookies, stolen credentials, and PII from malware, phishing, and breaches.
SpyCloud Consumer Risk Protection delivers deep, proactive intelligence to detect and stop identity threats before they lead to account takeover, fraud, or churn.
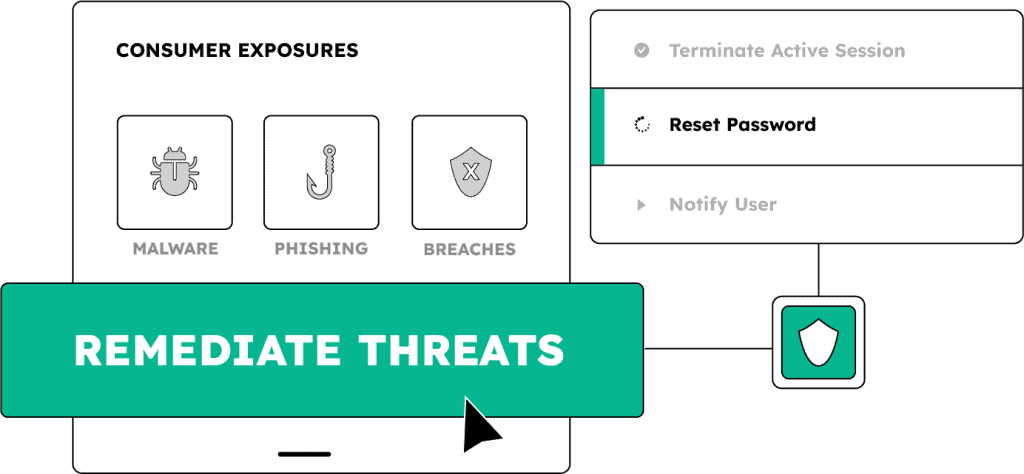
Protect the person, not just the password
Unlike traditional solutions focused solely on login credentials, SpyCloud protects the full digital identity – including exposed session cookies and stolen device fingerprints – giving you an early warning system for targeted fraud.
Detect compromised customers whose exposed identity attributes – stolen from breaches, malware infections, and successful phishes – pose an active fraud risk to your business
Identify when an attacker has the means to hijack an authenticated session and bypass MFA – and take decisive action to invalidate the session, require reauthentication, or apply risk-based controls
Use SpyCloud’s enriched dark web identity data to uncover vulnerable users, detect risky behavior patterns, and take proactive steps to prevent fraud – before transactions occur or customer trust is compromised
WHEN TO USE SPYCLOUD
Deploy SpyCloud for added consumer protection – without unnecessary friction
Enterprises typically implement and call the SpyCloud APIs at three points in a customer authentication flow. These approaches are not mutually exclusive and can be used together for coverage across the entire customer lifecycle.
Prevent consumers from selecting bad passwords by checking them against SpyCloud’s database during account creation, password change, and password reset
Check credentials in real-time as users log into your application – in parallel with a step-up authentication procedures for high-risk users
Check your entire database of credentials on a regular basis to detect new exposures – regardless if your users have been active during that time
EXPLORE PRODUCTS
SpyCloud Consumer Protection Products
Secure your consumers’ digital identities with breach, malware, and phished data insights from the criminal underground, integrated directly into your application or workflows.
Get early warning of malware-compromised cookies to protect authenticated sessions
Remediate stolen payment card data before it’s monetized by bad actors
Maintain persistent visibility into evolving exposures of customer credentials, PII, and other data
Our customers are everything to us. We have a core value around protecting them at all costs. So by adding Session Identity Protection to the rest of our SpyCloud instance, we basically get rid of the threat of account takeover, whatever the source – which means our customers and their data are safe.
EXPLORE WHO USES SPYCLOUD
Defenders
we help
THREAT INTELLIGENCE
Track breaches involving consumer data and triage high-severity threats to consumer identities