Identity Access Management Solutions Protect Your Valuable Data
Long before remote work gained traction, few security functions were as essential to organizational health as Identity Access Management (IAM). The proliferation of new user accounts has led to a proliferation of poor password hygiene, making it among the most stubborn security measures to enforce.
It has also led to a heightened awareness of gaps left wide open for criminal exploitation.
Regardless of strong password policies, 70% of users continue to reuse passwords across multiple accounts. With more than 80% of data breaches resulting from stolen and/or weak passwords, password security plays an increasingly critical role in protecting the modern enterprise. Using SpyCloud as a key component of enterprise IAM programs, IT and security teams can ensure that users logging in – whether employees, consumers, or suppliers – are who they say they are, and not bad actors leveraging stolen credentials.
How Account Takeover Makes Identities Vulnerable
One of IT’s most important functions is identity and access management (IAM) to define and manage the roles of various users and the circumstances when they are granted or denied access to different parts of the network. Those users could be customers, employees, partners, vendors or other third parties.
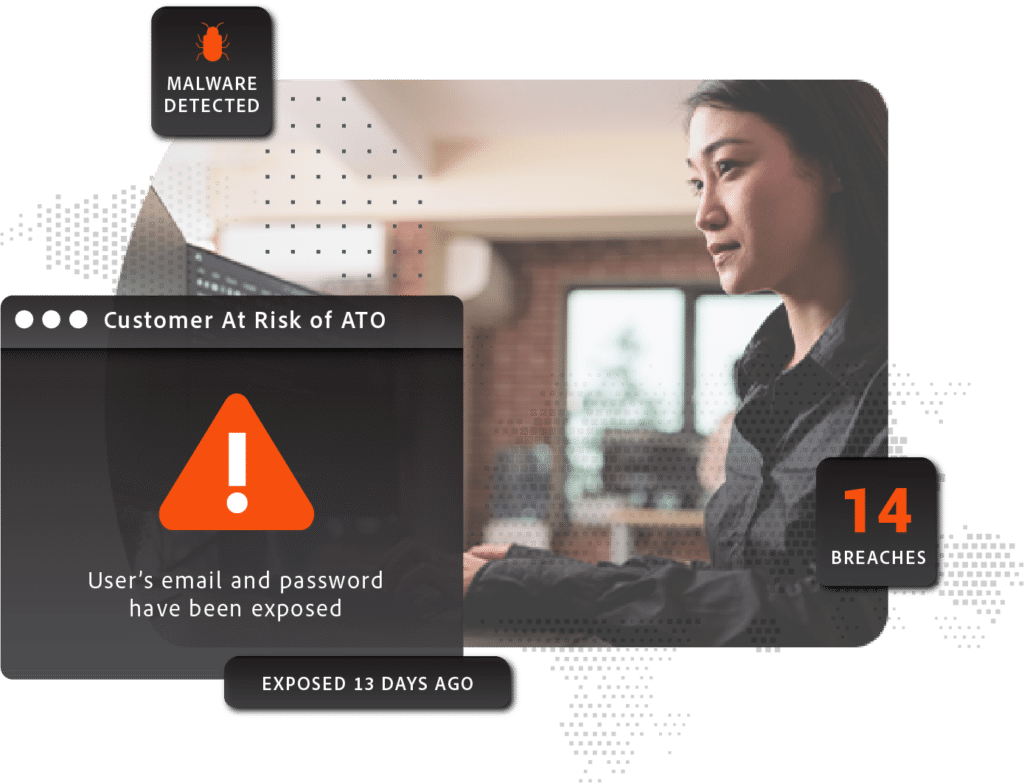
As strict as an organization’s IAM policies might be, they are only as secure as the user’s identity. If the user’s credentials are compromised, the wrong person can pose as them and access everything they can.
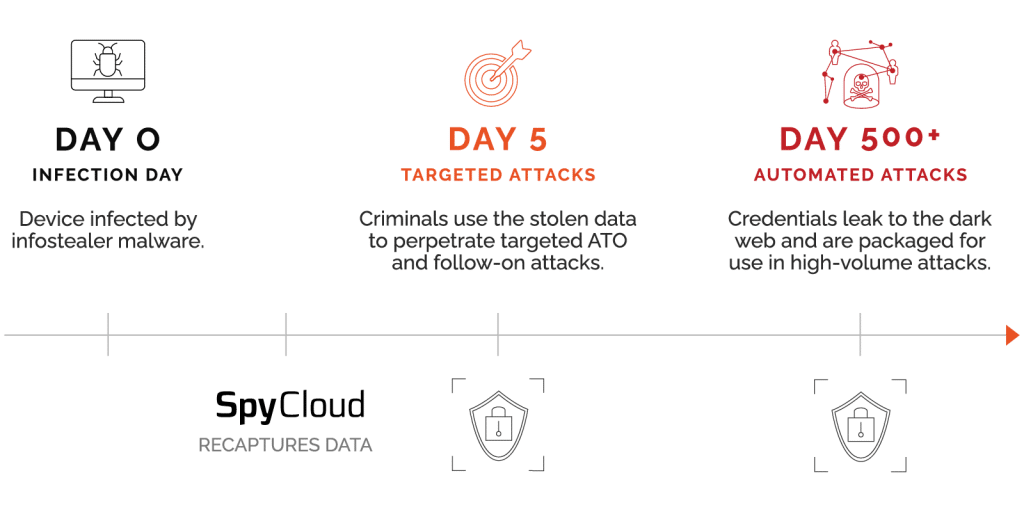
Billions of logins and passwords have been exposed through various data breaches and infostealer malware infections, and they are circulating among criminals who use them for account takeover. Most people have hundreds of online accounts, and they tend to reuse the same usernames and passwords on multiple accounts. Unfortunately, when a data breach or malware infection exposes those passwords to criminals, every account that shares the same login information becomes vulnerable to account takeover.
If a criminal takes over one of your employees’ accounts, suddenly the criminal has access to your enterprise network. And criminals aren’t stupid. They often target executives and other specific users who are more likely to have access to the most sensitive and valuable parts of the network.
Take an Innovative Approach to Protecting Identity
Because new threat vectors emerge and constantly evolve, enterprises need new solutions and approaches to protect identities – solutions that help you stay ahead of threats.
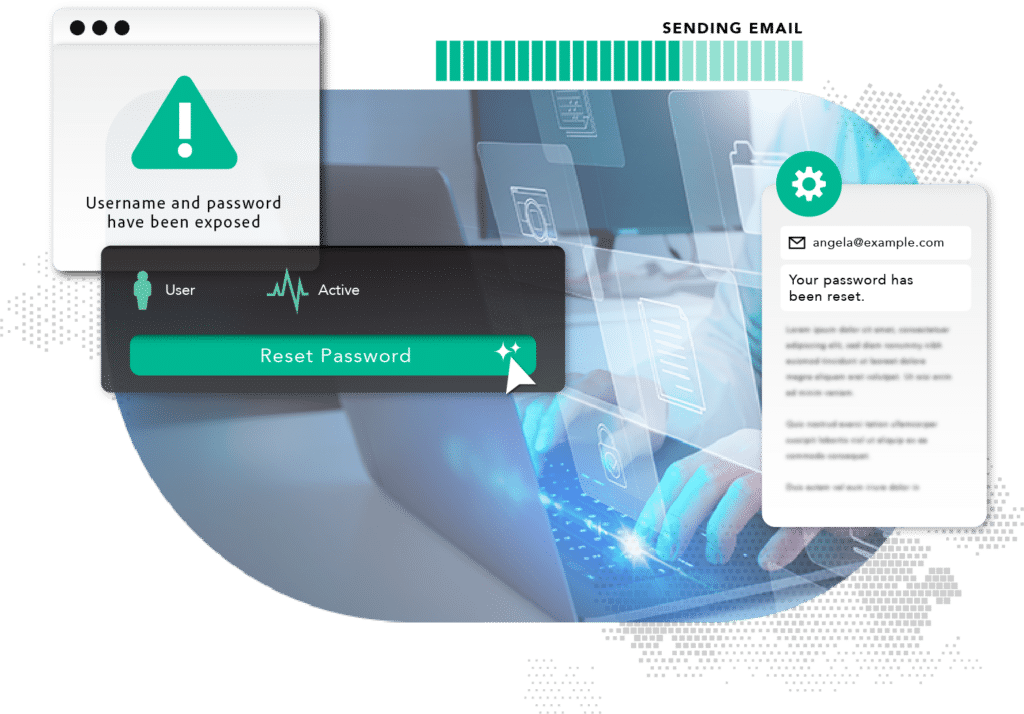
SpyCloud uses human intelligence to recapture breached information and maintains the world’s largest and freshest collection of data from breaches, malware-infected devices, and other underground sources. SpyCloud customers can check their user accounts against this data to see whether the credentials have been compromised. If they have, SpyCloud automatically handles the remediation of the exposed password, or you have the option to additional account authentication or take other steps to verify the identity of the user before granting access.
How many of your users are potentially compromised?
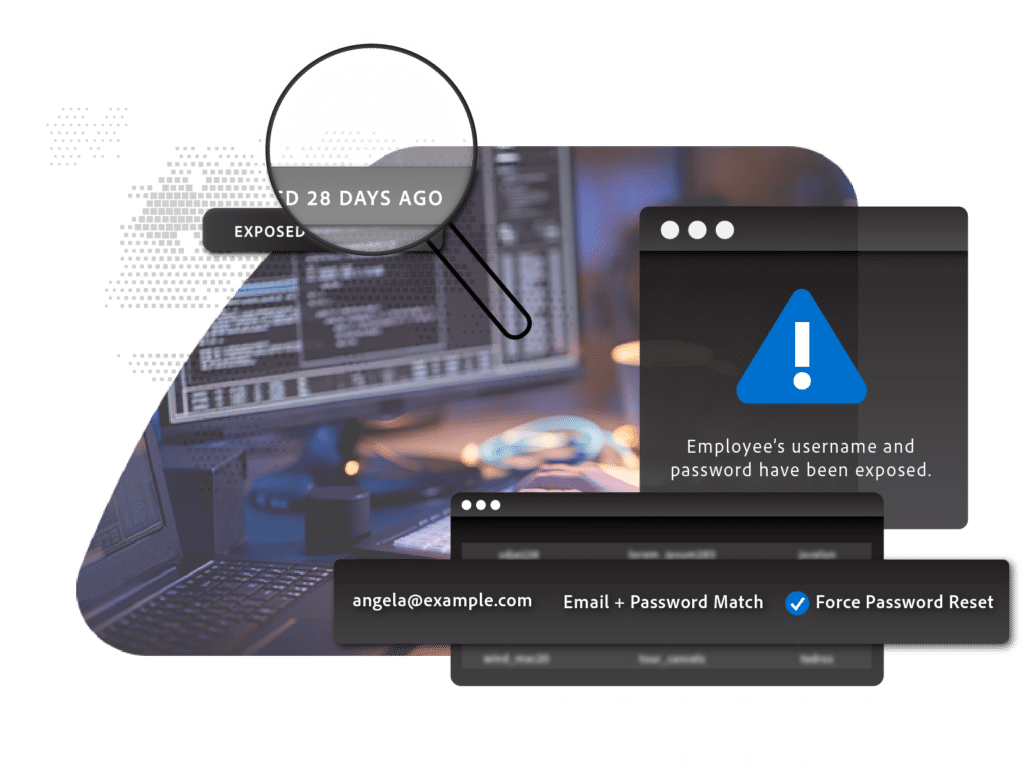
Business Emails Increasingly Targeted
Global losses for compromised business email accounts totaled more than $26 billion over the last two years, according to the FBI. Just one attack carries an average cost of $93,000.
Threat actors use phishing attacks, social engineering or reused credentials to access business accounts and bypass traditional IAM safeguards.
To protect your enterprise from business email compromise, SpyCloud provides continuous password monitoring and early detection of breach exposures, which stop ATO before it happens.
SpyCloud Helps Enterprises Safeguard Identities
Current and truly actionable recaptured data is the backbone of SpyCloud’s solutions, built by a combination of human intelligence and automated dark web scanning. The speed with which we recover, clean, and enrich the data to make it actionable is unmatched in the industry.
At SpyCloud, we are distinctly different in our approach to identity and access management. We are proud to protect billions of employees and consumers around the world.
Featured Products
Our award-winning products enable you to proactively protect your users’ accounts and thwart online fraud.
Consumer ATO Prevention
Protect your users from account takeover fraud and unauthorized purchases.
Employee ATO Prevention
Protect your organization from breaches and BEC due to password reuse.
Featured Resources
SpyCloud Connect
SpyCloud Connect is a hosted custom automation solution that enables rapid remediation of compromised identities
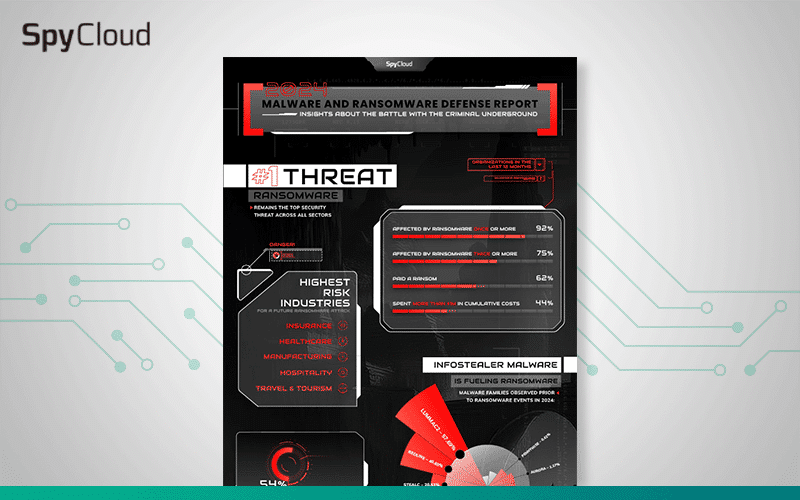
2024 Malware & Ransomware Insights
See the latest malware and ransomware trends, including top infostealers and industries most at risk of ransomware attacks.

2024 SpyCloud Malware and Ransomware Defense Report
The 2024 SpyCloud report uncovers today’s malware and ransomware resurgence. See top threats and what security teams are prioritizing to prevent attacks.

