Industry: Cryptocurrency ExchangeS
Safeguard cryptocurrency accounts from cybercrime
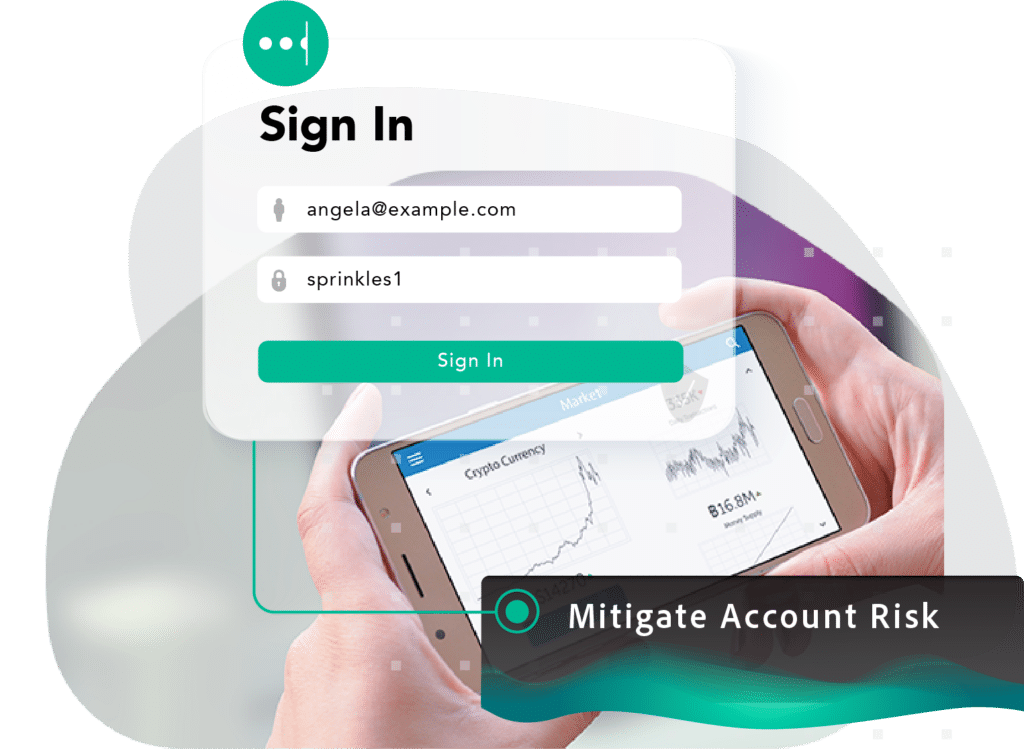
Crypto exchange accounts represent lucrative targets for cybercriminals, putting consumers at high risk of account takeover and online fraud. Crypto balances are the first priority for criminals when a third-party breach or infostealer infection exposes a consumer’s credentials or authentication cookies.
Award-winning solutions from SpyCloud help leading cryptocurrency exchanges secure users’ accounts by proactively checking user credentials for breach and malware exposures that can lead to ATO. In addition, SpyCloud solutions empower analysts to investigate and attribute online fraud to specific threat actors.
WHO USES SPYCLOUD?
Comprehensive consumer protection powered by Cybercrime Analytics
Empowering crypto exchange security teams to act on what matters to reduce losses from account takeover and online fraud
Prevent ATO
Re-secure malware-infected users to strengthen defense mechanisms against emerging ATO techniques like session hijacking
Combat online fraud
Leverage darknet data to prevent fraudulent account creation and ensure account integrity throughout the digital lifecycle
Speed up investigations
Get a full picture of adversaries with robust recaptured data – enabling teams to swiftly unmask threat actors and attribute crimes
Thwart financial crimes with SpyCloud
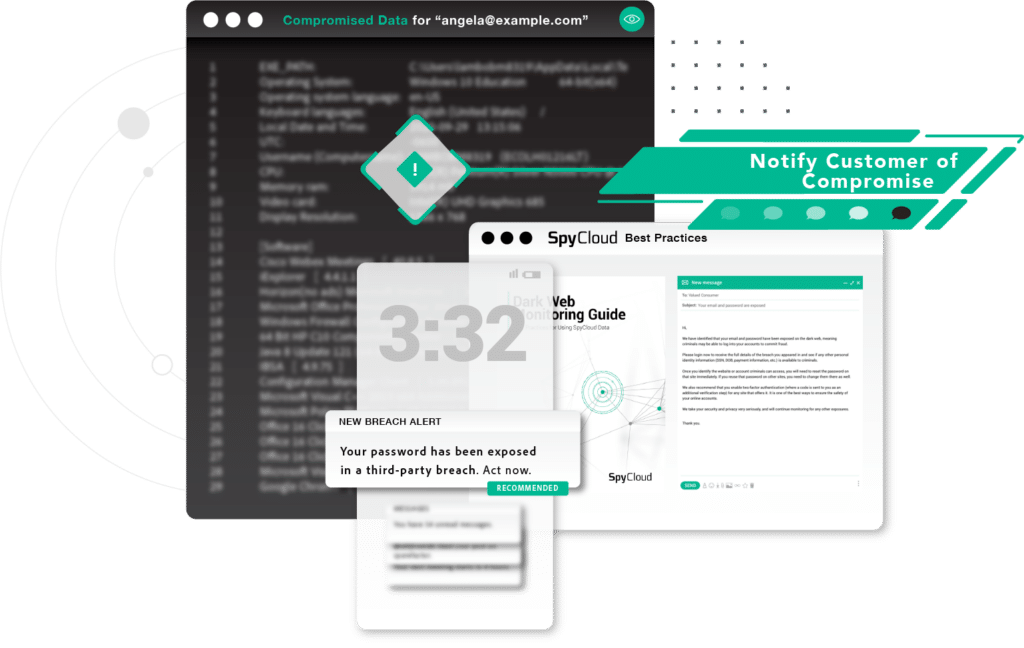
The world’s leading financial institutions, including top crypto exchanges, rely on SpyCloud to safeguard their users’ accounts with proactive, ongoing detection and automated remediation of darknet exposures.
Combat online fraud and ATO
Stay ahead of targeted ATO attacks by checking consumers’ authentication data against the largest collection of recaptured data in the industry – illuminating exposures of passwords and cookies before attackers defraud users.
Flag the riskiest users
Identify malware-infected consumers at high risk of account takeover and fraud, and take action accordingly – with step-up authentication, password reset, or even customer service outreach.
Detect fraud, without friction
Tailor the customer’s journey, allowing users with little to no exposures to interact friction-free, while implementing the appropriate measures for compromised accounts – even blocking transactions for the highest risk users.
Investigate cryptocurrency crimes
Arm analysts with with the investigative power of billions of recaptured data assets – the digital exhaust from criminals exposed in breaches themselves – to de-anonymize cybercriminal personas.
The new way to fight cybercrime
SpyCloud turns the tables by making darknet data work for you. We detect when your employee and customer credentials, cookies, PII and other critical stolen assets are in the hands of cybercriminals and automate remediation to reduce your risk of cyberattacks.
Assets
Breaches
Assets Ingested Monthly
Malware
Families
What else can I do with SpyCloud?
Ensure compliance
Take a proactive approach by identifying and remediating security and compliance risks
Flexible APIs
SpyCloud provides custom, high-volume APIs with simple configuration to help you integrate our Cybercrime Analytics with your current tech ecosystem
Next steps with SpyCloud
Read case study
See how a leading cryptocurrency exchange defends users from ATO and fraud tied to malware.
Read whitepaper
Learn how to protect your customers from targeted and automated ATO attacks.
