Proactive ransomware prevention
Enterprise-ready ransomware protection with automated detection and remediation of breach and malware exposures to thwart targeted attacks
The modern approach to combating ransomware
As cybercriminals evolve their methods of attack and become more sophisticated, it’s critical for enterprise to secure the perimeter – but traditional, static defenses are not enough. Keep your organization safe from data loss and the implications of ransomware with an automated ransomware prevention solution powered by Cybercrime Analytics.
Complete
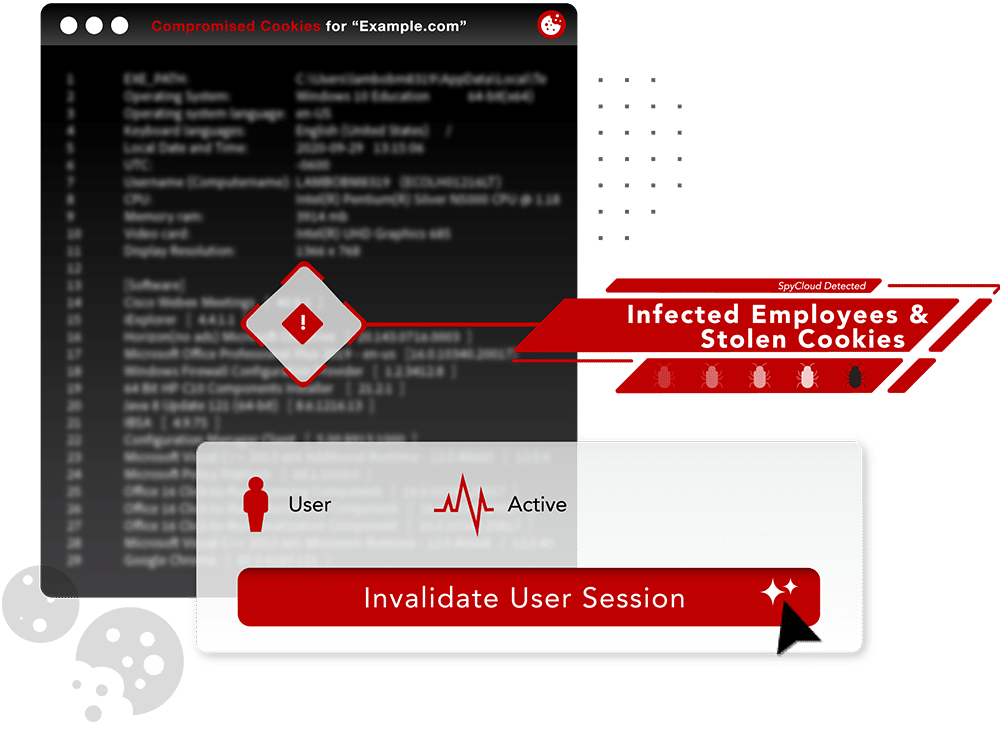
exposure visibility
From unmanaged devices to undermanaged devices – automate workflows to reset passwords and block access to data siphoned by malware-infected devices
Exposed application remediation
Go beyond the device and mitigate access to exposed applications that put corporate data at risk – ghost IT, shadow IT, stale user accounts, personal accounts, and more
Security gap
elimination
Identity-centric remediation that helps close the gaps in existing ransomware prevention measures – from MFA to EDR
Typical incident response plans often focus on the later stages of ransomware attacks because that’s when it’s evident that criminals have gotten into your enterprise. It’s typically only then that you may realize that your current detection measures weren’t enough.
To truly understand ransomware attacks, you must understand how criminals can get in the first place – particularly the ways that fall through the cracks of traditional ransomware prevention solutions.
High fidelity alerts
SpyCloud delivers alerts that you actually want more of. With actionable insights and dynamic alert prioritization that reduces the burden for security teams, you're empowered to make informed decisions, with confidence.
Unmatched intelligence
Leverage the world's largest and deepest collection of recaptured data, with 25+ billion assets analyzed and ingested monthly. No other provider offers this scale of high-quality data that is curated and enriched, with a flexible and scalable API – enabling action on evidence of compromise.
Contextualized at scale
With SpyCloud, identity-centric context and correlation goes beyond the device – enabling swift remediation of compromised credentials across devices, applications, and users for a proactive approach to ransomware prevention.
Enterprise-grade automation
Get infinitely actionable analytics on compromised identities – with seamless integration into SIEMs, SOARs, and directory services, SpyCloud provides only the most relevant data to power automation of security workflows in the SOC, and beyond.
Our ability to identify infected users was really beneficial because [our stakeholder's] cyber capabilities didn’t detect that their system was subject to a cyber attack.
Learn how SpyCloud’s malware insights help EUROCONTROL prevent ransomware attacks



SpyCloud offers out-of-the-box API integrations with top technology vendors across SIEM, SOAR, XDR, TIPs and more – delivering Cybercrime Analytics at scale for analysis, detection, remediation and automated workflows.
Learn more about our extended support of vendors
Explore SpyCloud
Enterprise Protection
Reduce your risk of ransomware and other critical attacks – acting on known points of compromise
Learn more
Consumer Risk Protection
Take a proactive approach to combating account takeover and stop high-risk attacks tied to malware
Learn more
Investigations
Efficiently piece together criminals’ digital breadcrumbs to reveal the identities of specific adversaries engaging in cybercrime
Learn more
Data Partnerships
Access comprehensive breach and malware data to add value to security and fraud detection products and services
Learn more
SecOps
Efficiently secure employee identities and safeguard corporate data and critical IP from cyberattacks.
Learn more
Threat intel teams
Investigate and stop threats with insights well beyond raw data and IOCs
Learn more
Cybercrime Analytics
Learn about the new way to disrupt cybercrime with automated analytics that drive action
Learn more
Test our data
We’re confident you’ll get more matches with SpyCloud – let’s do a match rate test
Learn more
Check your exposure
Uncover threats to your organization like malware-infected employees, stolen session cookies, and recency of breach exposures
See your results
Ransomware Prevention FAQs
Sometimes, attacks are purely opportunistic. An attacker may choose to infect a vulnerable organization because they encounter convenient credentials or have other potential access into their network. In other circumstances, the bad actors may go through various stages that follow a more complex attack pattern.
1. Research + Reconnaissance
In this stage, the attacker researches the company, including pulling job postings, social media posts, blog comments, press releases, company reports and may even make a list of employees mentioned on the company website and crawl the internet searching for their email addresses. The more they know about a victim, the better they can execute social engineering tactics, such as crafting believable phishing emails to lure them into clicking on a malicious link or opening a dangerous attachment. Criminals use this information to build a dossier on the organization, which may also include third-party contractors, suppliers and other vendors associated with the target company.
2. Identify Entry Point
Determining how to best gain access to a particular target without being detected is where IABs play a critical role. Often, these actors work directly on behalf of the ransomware gangs to find vulnerable systems or perform spear phishing campaigns or simply collect harvested credentials and databases from forums and resell them to ransomware gangs.
3. Gain Access
Once access has been obtained, the next goal is to penetrate the network and establish a foothold. A common entry point is through a public-facing Remote Desktop Protocol (RDP) portal, a Citrix server, or a VNC portal. During this phase (sometimes outsourced, other times performed by ransomware operators themselves), the attacker executes malicious code on one or more systems. This often occurs through credential-based social engineering, most often spear phishing via email or internal messaging services, or by exploiting a software vulnerability. The attacker needs to ensure continued control over a newly compromised system. Typically, they establish a foothold by installing a backdoor or delivering malware to the victim.
4. Escalate Privileges
Attackers often escalate their privileges through software vulnerabilities or credential exploits, such as password cracking. In many cases, passwords stored on a network have essentially been converted into sets of cryptographic hashes, which, when obtained by criminals, are long strings of scrambled characters that look nothing like the original password. Using various methods, the threat actors can either crack the passwords or use pass-the-hash attacks to obtain cleartext passwords. In an ideal scenario, threat actors will then be armed with a systems administrator’s credentials, giving them freedom to move laterally around the network without arousing suspicion.
5. Network Propagation
Some malware includes self-propagating features, automatically infecting multiple systems in a network without any extra effort from the criminal actor. In other cases, the attacker may use their initial access to move from system to system within the compromised environment, scanning files to find exposed secrets, additional credentials or configurations. One of the key acts is to develop and deploy a backdoor to slip in and out of during the attack and, in some cases, return to the scene post-attack to inflict more damage. This could happen over a period of months.
6. Destruction + Encryption
Once the attackers have completed their theft, the ransomware will be deployed and encryption begins. This is often the point when organizations realize they’re under attack. What are the signs your system may have been infected by ransomware? Filenames will change to show that they have been encrypted. You’ll see a mysterious ransom note file on your desktop called openme.txt or something similar, with instructions for how to communicate with the ransomware gang.
7. Negotiation
Criminals have turned to extortion tactics in recent years, such as threatening to leak victim names or expose potentially damaging information to the public or to competitors. The question for organizations remains the same: how much risk can you tolerate? If you’re a company losing millions of dollars per day or if lives are at stake, you are going to pay. You may be more likely to pay if you’ve got a cyber insurance policy that reimburses you, at least partly, for the payment. But even after paying the ransom, there is no guarantee your files will be returned.
8. Aftermath
The ransomware recovery process is costly and time-consuming. While costs vary, organizations can expect to pay for legal fees, lost business, customer outreach, and overall interruption of traditional business operations. Regardless of financial losses, it’s rare that organizations fully recover from a successful attack.
There is no one-size-fits-all when it comes to ransomware attack prevention, it is necessary to have a layered defense focused on quick remediation of exposed credentials and stolen cookies (we call it Post-Infection Remediation).
Steps to prevent ransomware should include:
- Continuously monitor and remediate compromised credentials and stolen cookies
- Implement multi-factor authentication (MFA)
- Educate workforce on cybersecurity best practices
- Detect malware infections and stop the bleed with Post-Infection Remediation
Once stolen data gets siphoned by malware, it doesn’t just go away. Data from malware infections gets traded on the criminal underground by Initial Access Brokers. And it remains valuable to criminals as long as the credentials and cookies remain active and in-use.
Learn more about proactive ransomware prevention
Watch the webinar
Benchmark your ransomware preparedness & discover proactive strategies to solve your defense blindspots.
See the statistics
Updated stats on the prevalence and cost of common cyberattacks including ATO and ransomware.
Read the report
Our annual Ransomware Defense Report covers the costly impacts of ineffective countermeasures and organizations’ plans to improve defenses.