Criminals are using tools old and new for credential stuffing and account takeover. Here’s what you need to know about popular cracking tools including Vertex, Sentry MBA, SNIPR, and OpenBullet, along with custom and target-specific account checkers – plus how you can protect your users and yourself from these attacks.
Want to jump right to a section?
Automating Account Takeover
Three years ago (!), in our blog post Criminals are Using These Tools to Crack Your Website, we talked about some of the custom-built “cracking” tools that criminals use to automate credential stuffing. Our analysis included older credential stuffing tools like Sentry MBA, Vertex and Apex – all of which are still widely used.
Credential stuffing refers to the act of testing large sets of stolen credentials against targeted applications or web interfaces. Compromised credentials yielded from breaches are used to build “dictionaries” or “combolists.” These credentials are traded and sold within criminal networks and then used for credential stuffing operations. In effect, as long as companies keep getting breached, the lists keep getting better.
As criminals have become both more adept and more vigilant, so too have their tools. According to our research, newer versions of old cracking tools and next-generation account checkers are better at evading detection, cracking targeted applications, and bypassing countermeasures like captcha challenges. Since our last post, some of these credential stuffing tools have been “modded” by members of online cracking communities. Although these are not new, bonafide versions of the original tools have improved (with updates made by their original developers), and criminals are enjoying their new functionalities.
New and improved credential stuffing tools have options for more targeting. These tools have been developed as standalone custom account checkers built to target specific services. Some of these tools are foreign and target services in different languages. VirusTotal scans for many of these tools come out clean, but some of them may leave behind tell-tale signatures – user agent strings that give them away.
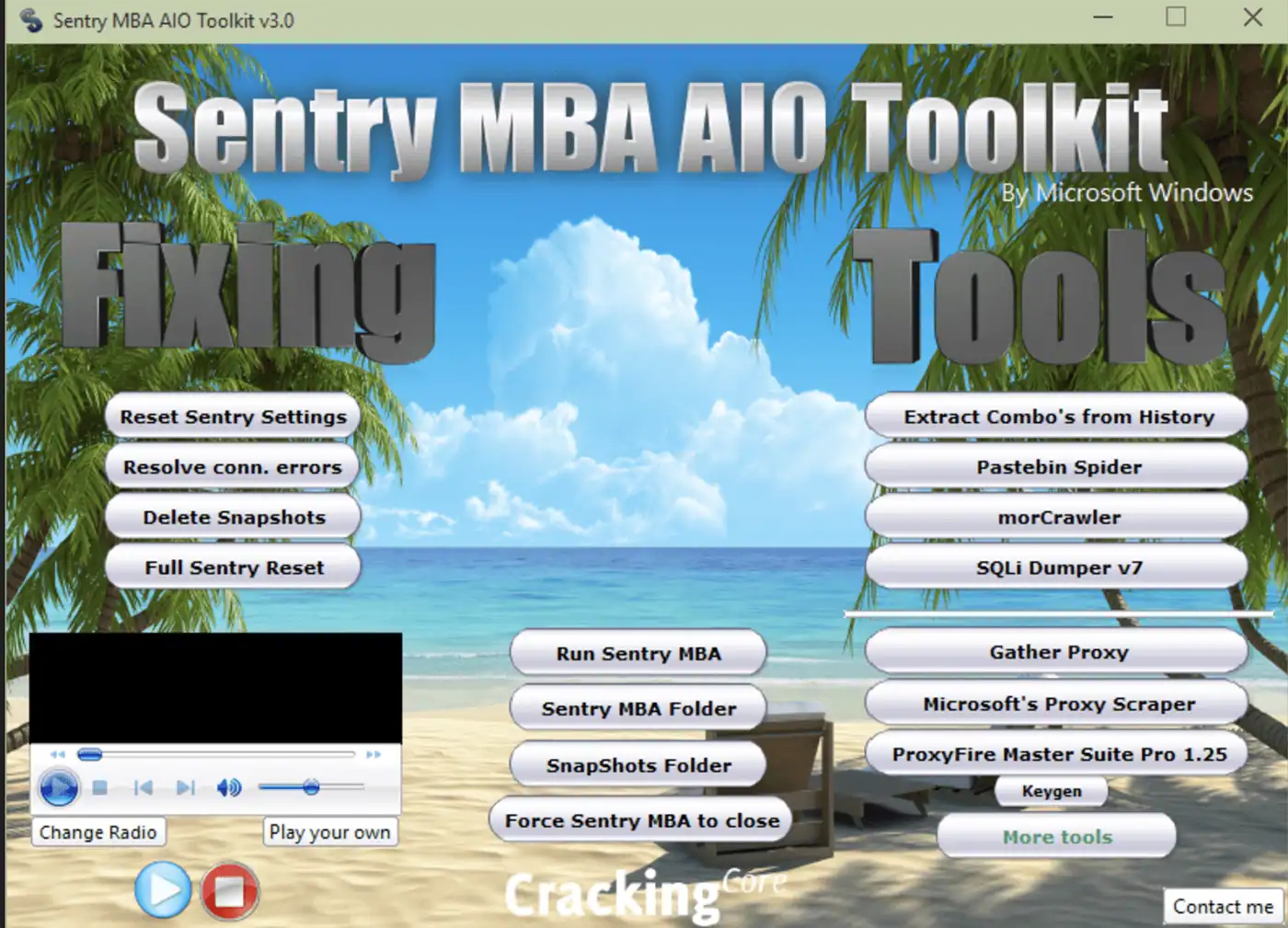
Figure 1: CrackingCore’s “Sentry MBA AIO” Toolkit includes add-on functionalities for sentry MBA to help bypass common user issues. The tool works with the custom Sentry MBA 1.5.0 (which is not a bonafide Sentry MBA version, but a custom mode – more on that later). It features tools to get proxies and combolists, extract user history, troubleshoot issues, and even radio support “to make cracking more enjoyable.” The tool is obviously not “by Microsoft Windows,” despite the claim on the interface.
Criminals load lists of breached credentials into these tools to test them at scale against targeted web interfaces or mobile applications. Thanks to the ubiquity of password reuse, it’s inevitable that they eventually find a match, and subsequently “crack” somebody’s account. For accounts unprotected by multi-factor authentication (MFA), operators of credential stuffing tools can log in to these accounts themselves.
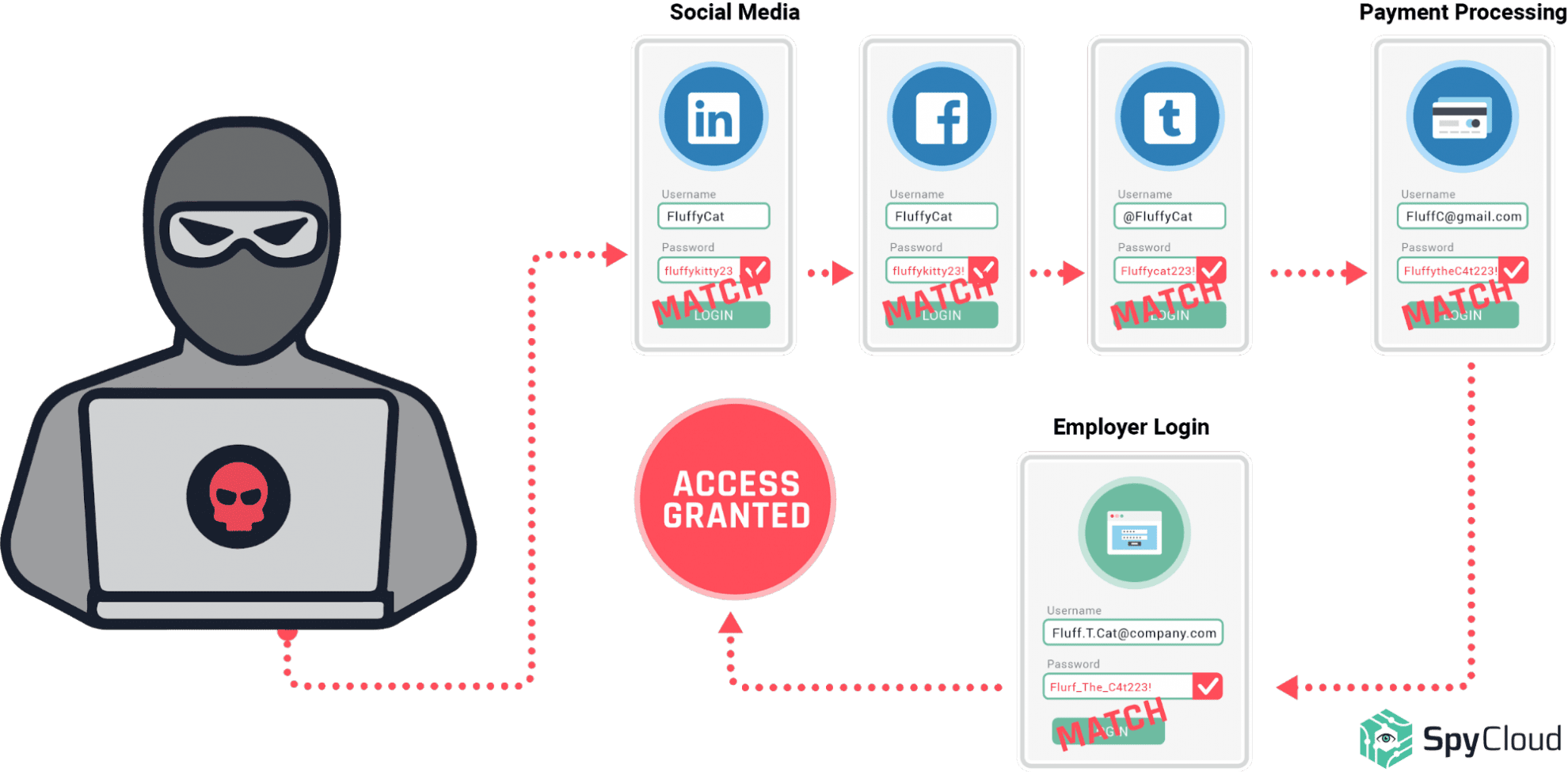
Figure 2: Credential stuffing 101
We wrote specifically about a fraud scheme particular to pizza delivery services in our blog post These Fraudsters Are Hungry for Account Takeover.
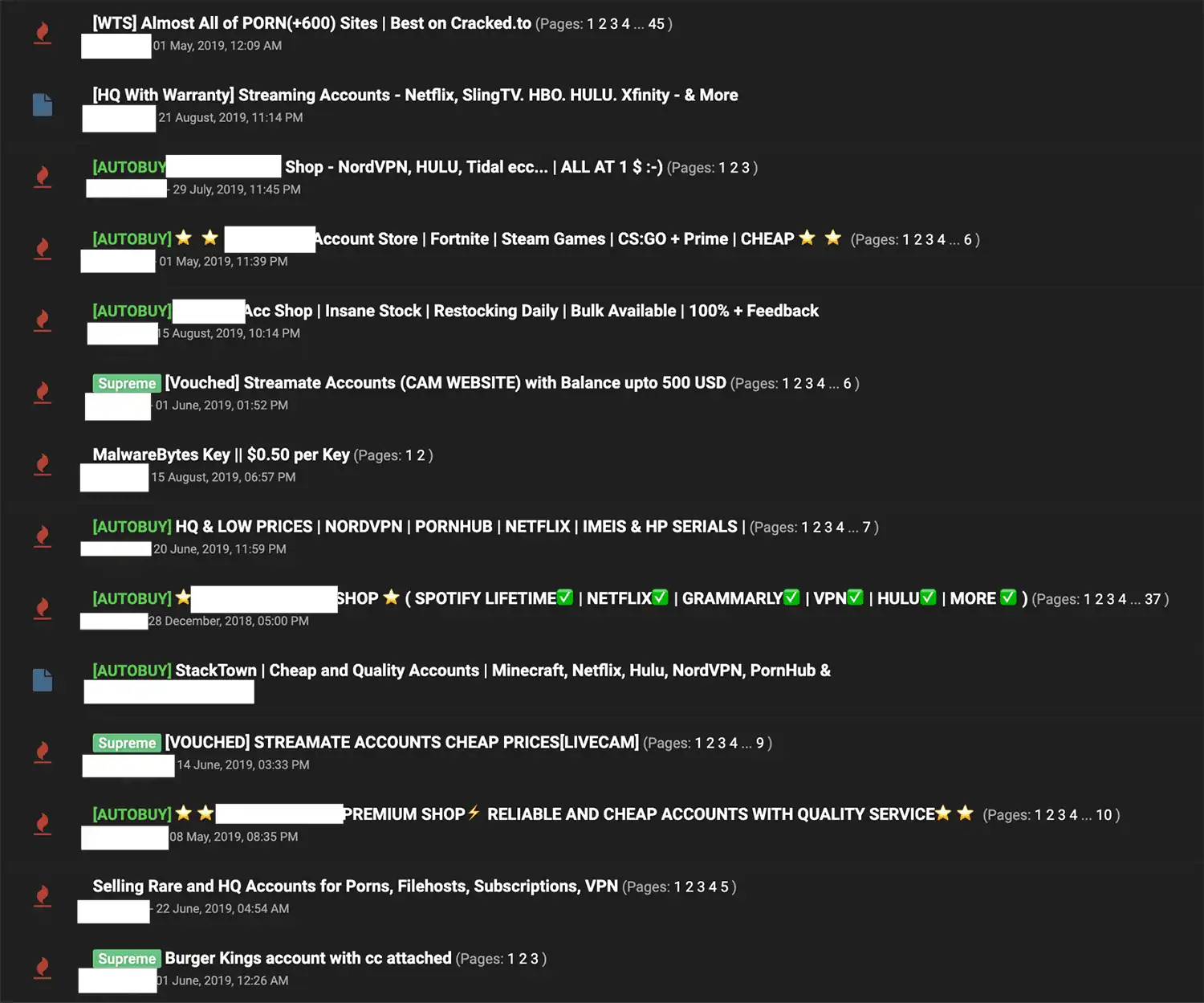
Figure 3: Various types of cracked accounts listed for sale on a popular cracking forum.
New Games, New Playgrounds
In addition to popular cracking communities on both the darknet and clearnet, there exists a burgeoning community for cracking services on the video game chat app Discord. This influx of cracking activity makes sense as many displaced dark web communities have also found a home there. In addition to serving as a platform for criminals to hawk stolen credentials, advertise doxxing services, and conduct other activities, Discord now offers access to several cracking communities. Security researchers have discovered OpenBullet’s source code for sale on Discord, as well as configuration files for the tool.
There are several Discord servers that host discussions relating to cracking. Some Discord servers serve as official channels attached to online cracking communities such as Nulled or even as a spillover community for darknet market users. Many of these servers host discussions related to broader hacking topics, including cracking, while some are specific to them. Many of these communities serve as a platform for vendors to sell custom configs, combolists, and tools for the purpose of account takeover.
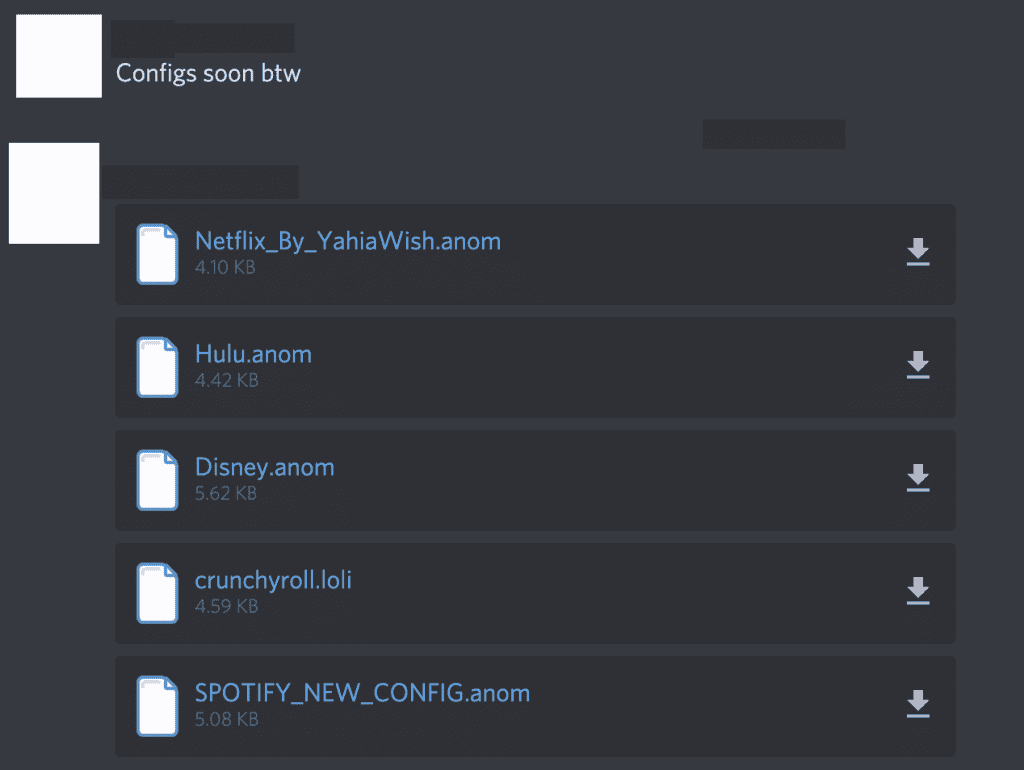
Figure 4: Screenshot of a channel from a hacking Discord server. This channel is used to sell custom configs.
It’s important to note that these servers often do not stay online for long periods of time as they are frequently reported for being in violation of Discord’s user guidelines.
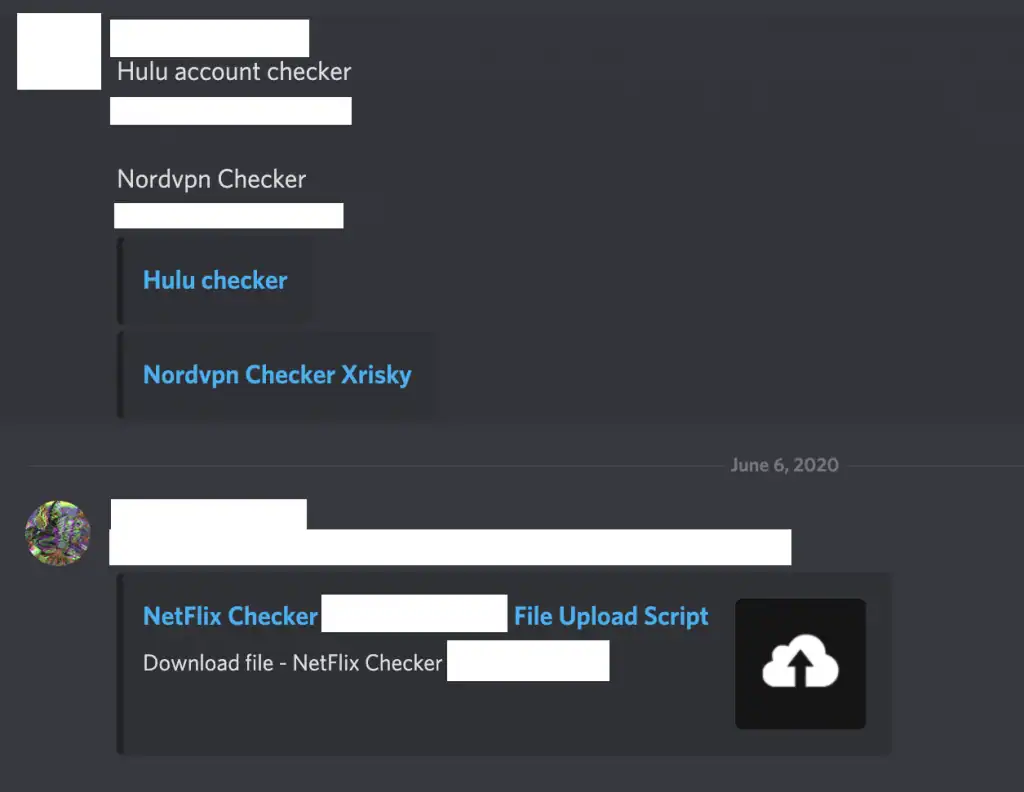
Figure 5: A user sharing custom account checkers for Hulu, NordVPN, and Netflix on a cracking Discord server.
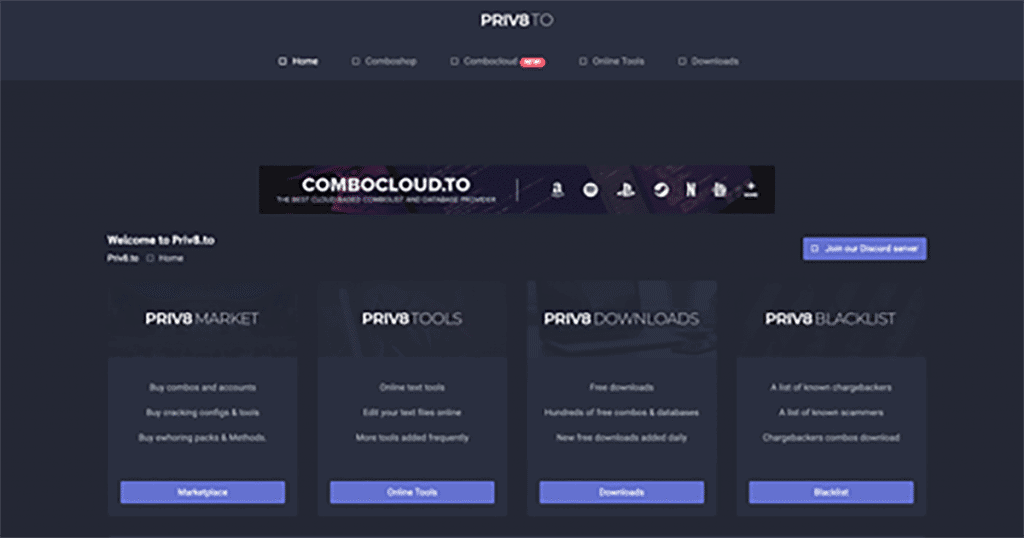
Many newer credential stuffing “shops” such as “PRIV8TO” that trade in combolists, tools, and configuration files now have their own Discord servers, as shown below.
How Cracking Tools Have Evolved
The sale of taken-over accounts is a popular and lucrative game. The tools, methods, and means used to achieve credential stuffing have evolved significantly in the last couple of years. But we also see criminals using older tools that still work well. For example, ever-popular credential stuffing tool Sentry MBA includes features such as OCR (optical character recognition) functionality to bypass captcha challenges.
We’ve recently seen updates to the functionalities, features, and ease of use in updates to older tools. Just as developers in the real world seek to constantly debug and improve their products, so too do criminals.
Next-generation tools take cracking a step further. These tools leverage the power of botnets and outsourced computing power. This can be achieved via a variety of means, such as through cloud computing services and even IoT devices. Less-sophisticated botnets are easier to block on the network edge. That’s because they may use the same IP address and user agent. If you see a large set of automated and unsuccessful login attempts in your logs, you may be dealing with a less-sophisticated botnet. These are easier for organizations to deal with because network administrators can block those IPs as user-agents using rules. Other botnets are just as noticeable, but harder to deal with.
So how can you tell where credential stuffing attacks are coming from? Although they can be masked, many tools (like Sentry MBA and Vertex) have default user agent strings that may be left in your web server logs. Credential stuffing attacks that originate from a device controlled by the less-sophisticated botnet herder themselves may also leave the same user agent string at least most of the time. Botnets that attack from tens of thousands of different proxies and use a plethora of different user agents will still attack en masse in a manner that makes it a dead giveaway. But blocking these attempts requires more sophisticated, heuristics-based tools designed to recognize not only signatures, but behaviors.
New Takes on Old Tools
Some of the tools we discussed last time included earlier credential stuffing tools such as Vertex Sentry MBA, and Apex. These “old but good” tools still work well, but newer mods have yielded significant improvements. Although there are newer alternatives, cracking tools such as these are still in use.
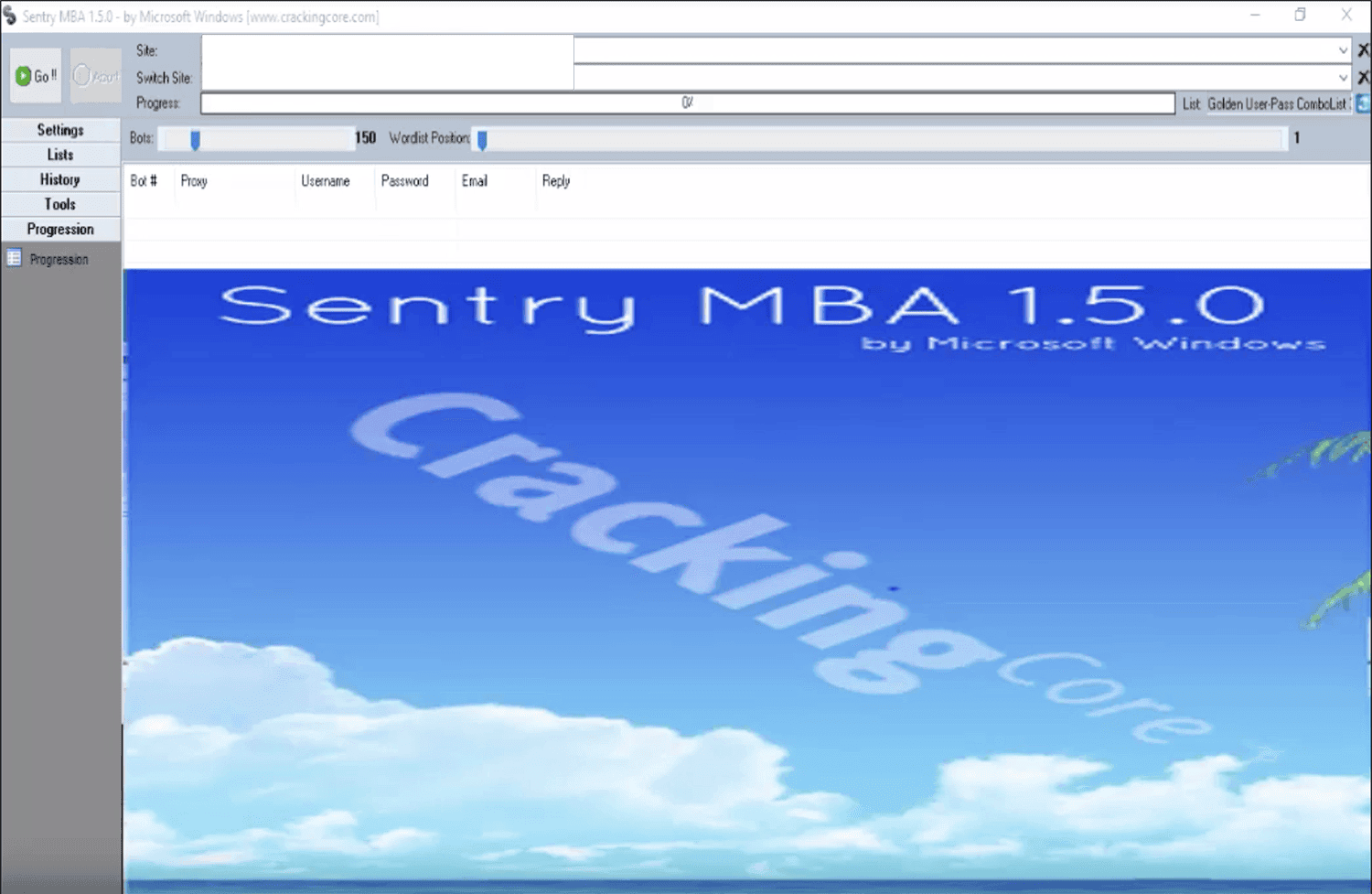
Vertex 1.0.4
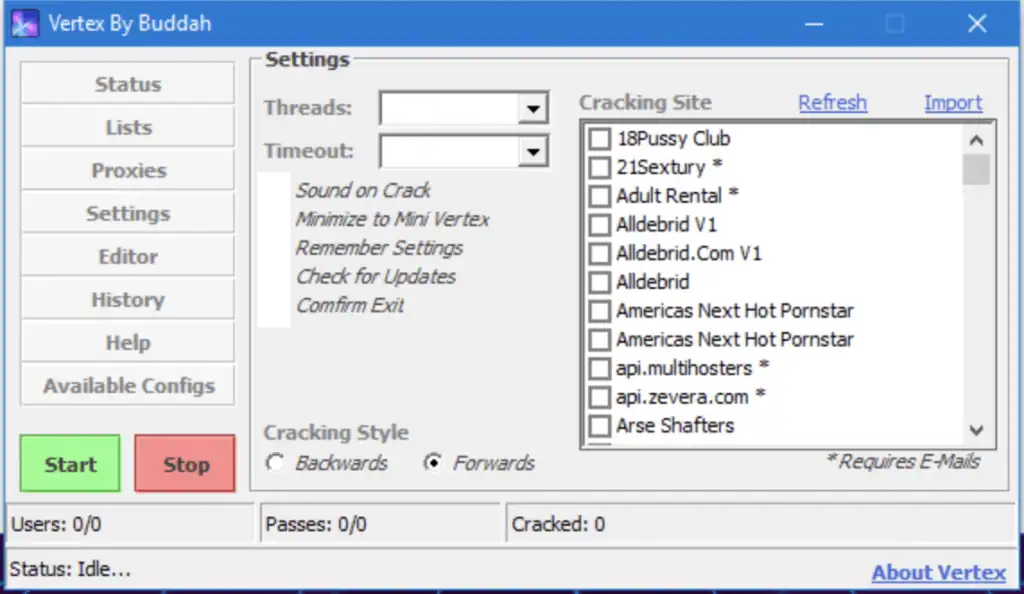
Figure 7: Screenshot of Vertex 1.0.4 posted by Buddah. Version 1.0.4 of this earlier cracking tool was reportedly developed by the same author of Sentry MBA, though that author also goes by “Sentinel.” A download link to this version was posted to a popular cracking forum in October 2018. According to VirusTotal this version was last modified on October 11, 2018.
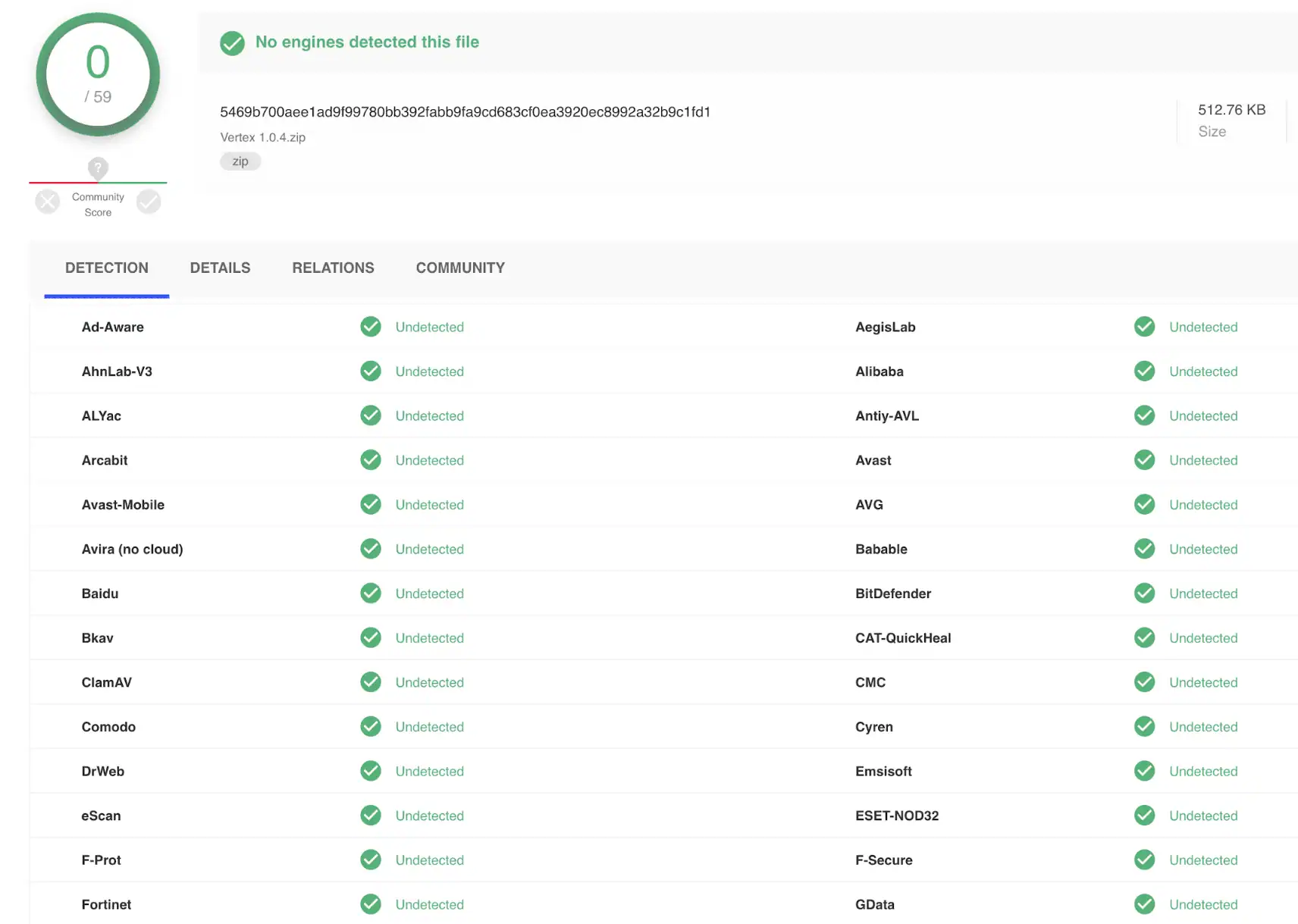
Figure 8: VirusTotal results for the latest version of the Vertex credential stuffing tool.
Like Sentry MBA, Vertex requires a configuration file, which includes inputs for user agent, POST data, HTTP headers, and other connection settings depending upon the targeted application. Full HTTP headers can’t be configured in Vertex, however, making it easier to identify its attack signatures than other tools such as Sentry MBA. The default user agent string for Vertex is:
Mozilla/5.0 (Windows NT 6.1; rv: 17.0) Gecko/20100101 Firefox/17.0
For anyone who is concerned about potential attacks via Vertex, it’s important to know that because attackers cannot change this string within the application. Because of this, you may see this user agent string within your SIEM logs if your organization has been attacked.
Sentry MBA Mods
Last time we talked about Sentry MBA, we left off with version 1.4.1. However, more recent versions–or spinoffs–of the credential stuffing tool have new features. The first version of the Windows brute-forcing application, “Sentry 2.0,” was originally developed by someone going by “Sentinel” in underground communities. The tool was later modified by “Astaris” according to Sentry MBA’s opening interface, and renamed “Sentry MBA.”
Sentry MBA requires the following inputs in order to run against a targeted mobile or web application:
- Configuration file: This file helps Sentry MBA navigate the unique characteristics of the site being targeted. The URL for the targeted website’s login page, for example, is specified in the config (configuration) file. These files are in .ini format, and help Sentry MBA determine what it needs to interact with on a targeted site.
- Proxy file: A list of IP addresses (usually compromised endpoints and botnets) to route traffic through, so that the set of login attempts appears to be coming from a large variety of sources (resembling organic traffic) rather than from a single attacker.
- Combolist: A database of username/password pairs to be tested against the target site; these lists are typically obtained from the breaches on other websites that can also be sold or traded on certain markets.
There are countless underground forums on both the dark web and clearnet dedicated to the sale and trade of Sentry MBA config files, combolists and proxy files (although sometimes config files are advertised as “proxyless”). Members who use config files (which are often pasted as text files) without giving back to the community are often banned for “leeching.” Many of these communities use reputation scoring for members and enforce disciplinary measures for breaking rules, or for “leeching” too much. Rather than acting as marketplaces, these forums allow members to manufacture, test, and post access to config files, combolists, tutorials, and extra tools for free. This honor system has helped create self-sustaining micro-markets for the creation and trade Sentry MBA config files and combolists.
There are also marketplaces dedicated solely to the sale of Sentry MBA inputs – config files and combolists. These often require a bitcoin wallet or other cryptocurrency to purchase inputs. Users can buy “gold” as a currency on one site using a bitcoin wallet and must use this to purchase configs that have been uploaded by various users.
Since our last cracking tools article, Sentry[.]mba has been down a few times, but as of now it has been upgraded and back online. On the site, the “current” version of Sentry MBA for download is still 1.4.1. However, updated versions of Sentry MBA claiming to be the “latest version” have been turning up in cracking communities and in YouTube cracking tutorials.

Figure 9: Screenshot of a post introducing Sentry MBA 1.4.1 “crackingcore” edition, modded to be less “ugly.”
The screenshot above shows the interface of a purported Sentry MBA 1.4.1 “cracking core” edition. This version apparently doesn’t have any new features or functionalities in comparison with the earlier version, but it does have a new interface. The screenshot above shows a post on a cracking forum by a user who claimed to have “modded” Sentry MBA 1.4.1, claiming that his version isn’t as “ugly.” It doesn’t appear that this edition offers any advanced functionalities.
The same user also modded Sentry MBA to produce a “Sentry MBA 1.5.0” mod. This is not technically a new version of the original Sentry MBA, which was produced by “Astaris.” Several YouTube tutorials exist detailing the use of version 1.5.0 of Sentry MBA. However, it appears that neither Sentinel nor Astaris were involved in the making of this mod.
Next Gen Tools
SNIPR
A newer account checker, called SNIPR has become more popular within the credential stuffing community. SNIPR is a stand-alone tool that is not a mod of a more popular tool like Sentry MBA. SNIPR represents a new, more sophisticated generation of credential stuffing tools.
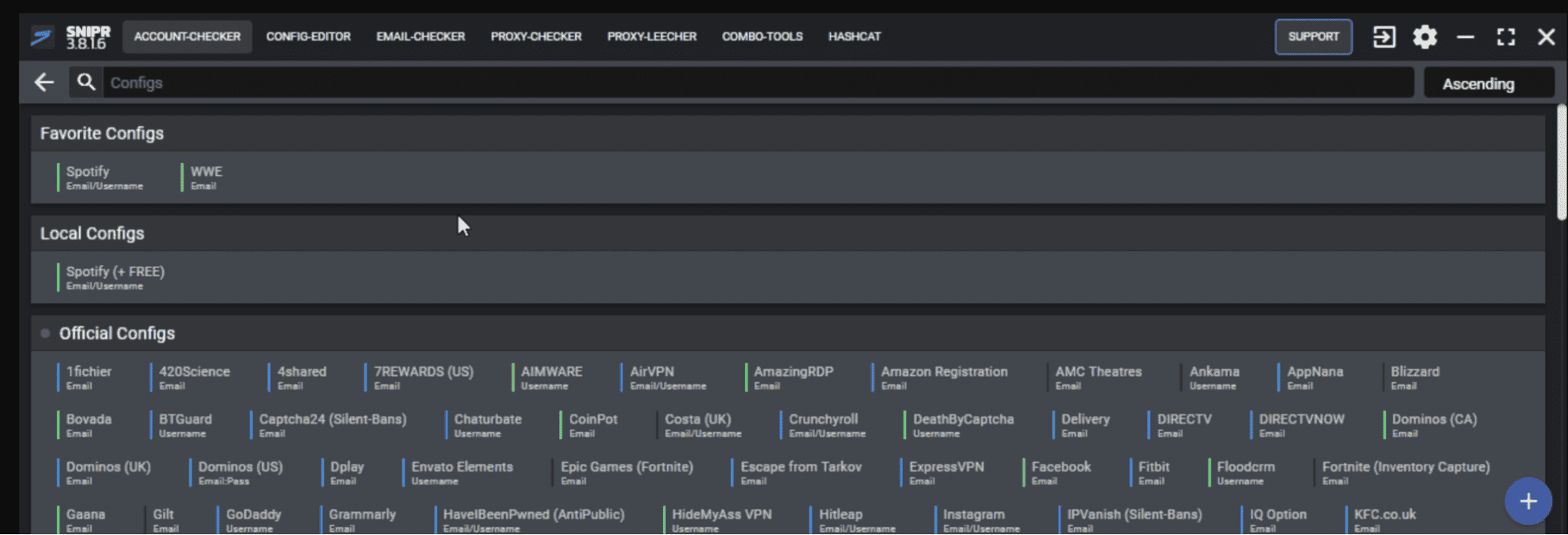
Figure 11: Screenshot of the SNIPR interface.
SNIPR features innovations that enhance user friendliness and detection evasion. In addition, it comes pre-baked with built-in configurations that are able to target popular websites, such that even low-skill criminals can operate the tool without building and uploading configuration files required for tools such as Sentry MBA. Users can still do this of course, but configs for many popular targets are built-in. These files typically include information such as target URL, user agent, and additional information required for targeting. SNIPR works both online and offline credential stuffing attacks.
Unlike Sentry MBA, SNIPR is not free. Users can purchase the tool for $20.00 using Amazon Pay or Bitcoin on the tool’s official Shoppy site. The tool has its own open-source development community, and supports multiple attack surfaces such as web requests, email (imap), and others. SNIPR also scrapes public proxies dynamically, which lets attackers look for alternating proxies. The tool was originally developed by an actor going by “PRAGMA” in threat actor communities.
In February, Dunkin’ Donuts issued a warning to users of their DD Perks app that their accounts may have been taken over via credential stuffing, giving criminals access to account information, including the account holder’s first and last names, their email address, and the 16-digit DD Perks account number and QR code. Although many configuration files exist for Dunkin’ Donuts belonging to a variety of tools, one of these, custom for SNIPR, was highlighted as relevant to these early 2020 attacks.
OpenBullet
OpenBullet is a relatively new credential stuffing tool that, like SentryMBA, Vertex, and others, performs multiple tests against a targeted application. The tool can also be used for scraping, parsing, and penetration testing besides its use as an account checker.
OpenBullet’s use case as a cracking tool is well known within online cracking communities. The tool was originally released in May 2019 on Github as a pen-testing tool intended for security researchers. However, it was modded by those with less noble intentions to operate as a standalone credential stuffing tool, and can now be found used for various account cracking purposes across various targeted industries.
OpenBullet has its own dedicated forum, which offers the latest version of the tool for download but cautions that it is not a cracking forum. There are several cracking tutorials on YouTube, cracking communities, and other hacking forums that instruct users on how to use the tool for the purpose of unauthorized account takeover.
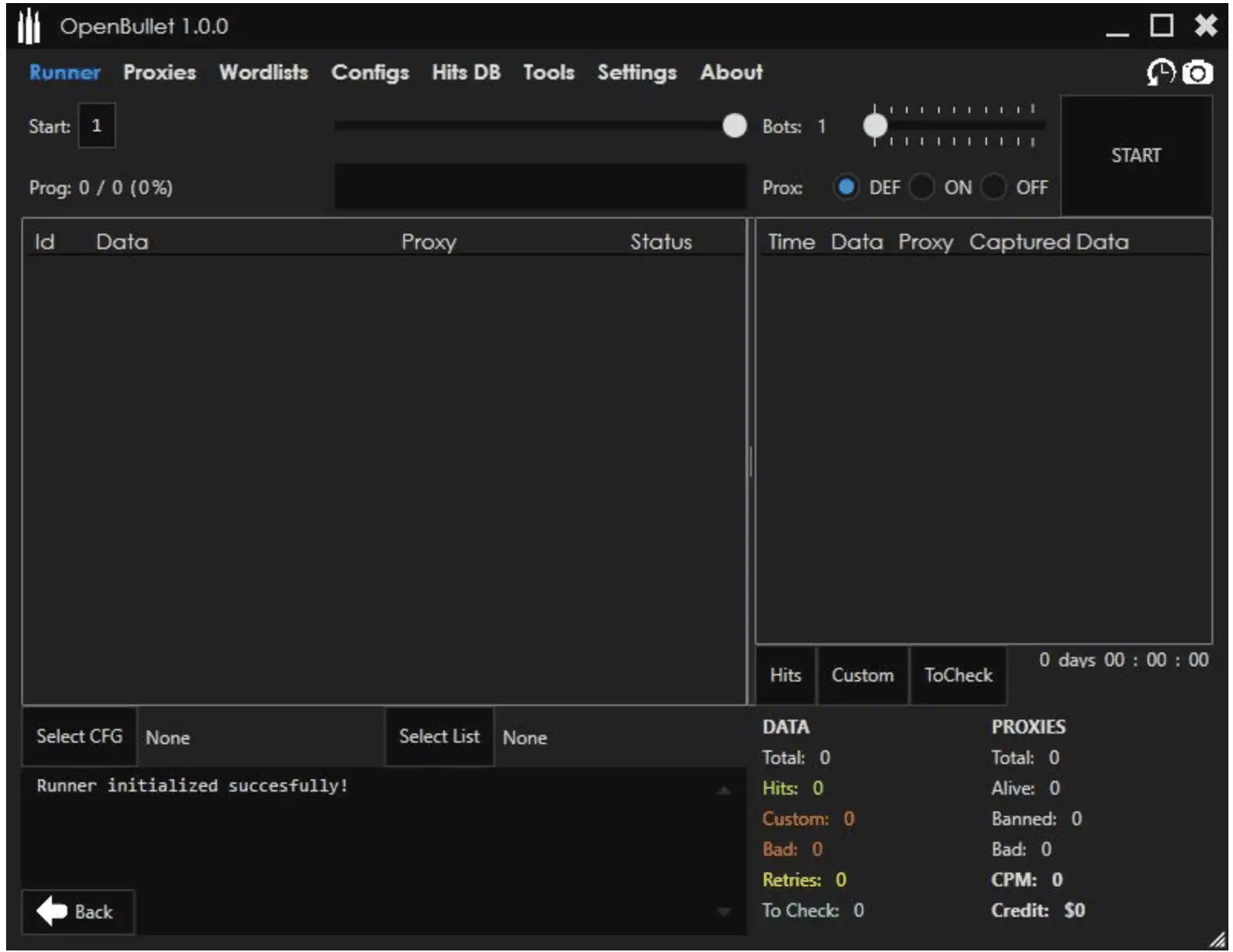
Figure 12: Screenshot of OpenBullet’s user interface.
Like many other credential stuffing tools, OpenBullet requires certain inputs to operate and test a targeted web or mobile application, such as a configuration file, wordlist, and target URL. And, like other tools, its success relies upon the ubiquity of password reuse. But OpenBullet, as some in cracking communities have commented, may be “better” than SentryMBA. Part of this may be an effect of not only threat actor innovations, but of the cyber crime community “growing up.”
In one cracking community, a user commented that OpenBullet is better than Sentry MBA and SNIPR because their configuration files are outdated, and that few make configuration files for these tools anymore. While configs for Sentry MBA, SNIPR, and other well-known tools can still be found within cracking communities, there is a new and noticeable trend for OpenBullet configs as well. OpenBullet configs for services such as Netflix, Microsoft Azure, IMVU, Scribd and other services are for sale on cracking forums.
Private Keeper
Private Keeper is a newer brute forcing tool that appears to have originated from within Russian-language cracking and hacking communities. According to our research, Private Keeper appears to be more feature-rich compared to other account checkers on the market, especially in comparison to Sentry MBA or OpenBullet. And because it’s more modular and scriptable than other account checkers, it can more easily improved upon to fulfill specific needs not offered by the original tool.
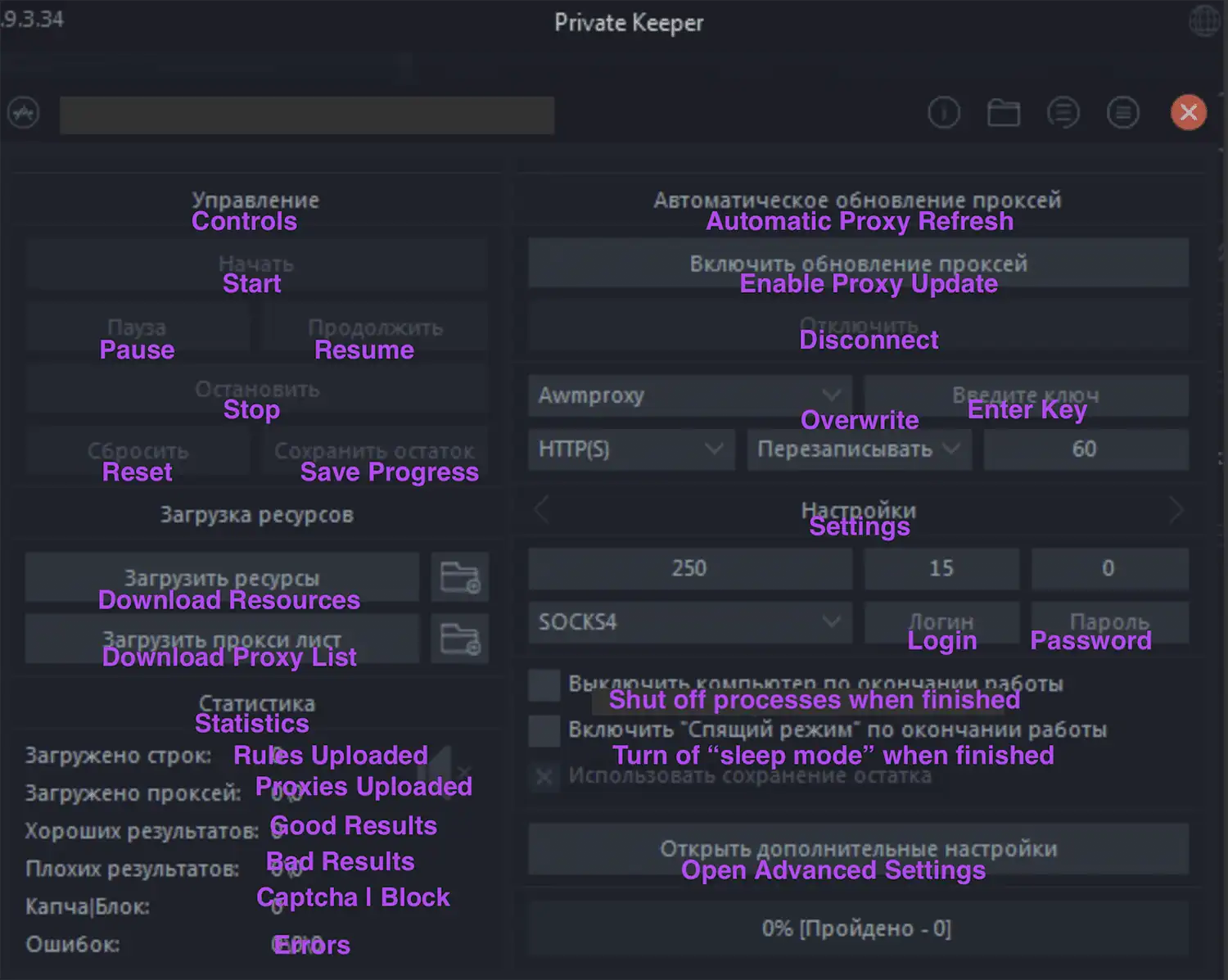
Figure 13: Screenshot and translation of the Private Keeper brute forcing tool. We have added English translations of the tool’s features in purple.
Custom and Target-Specific Account Checkers
Several custom standalone account checkers exist that have been distributed throughout various underground forums. Tools like these exist in multiple languages and may target specific services, or focus on certain features such as usability or evasion detection.
The cracking tool below, called “Brute and Checker PSN 1.0” originated from a Russian-language hacking forum. We translated the various functions into English to show how similar it is to the custom cracking tools we are used to seeing in the English-language cracking communities.
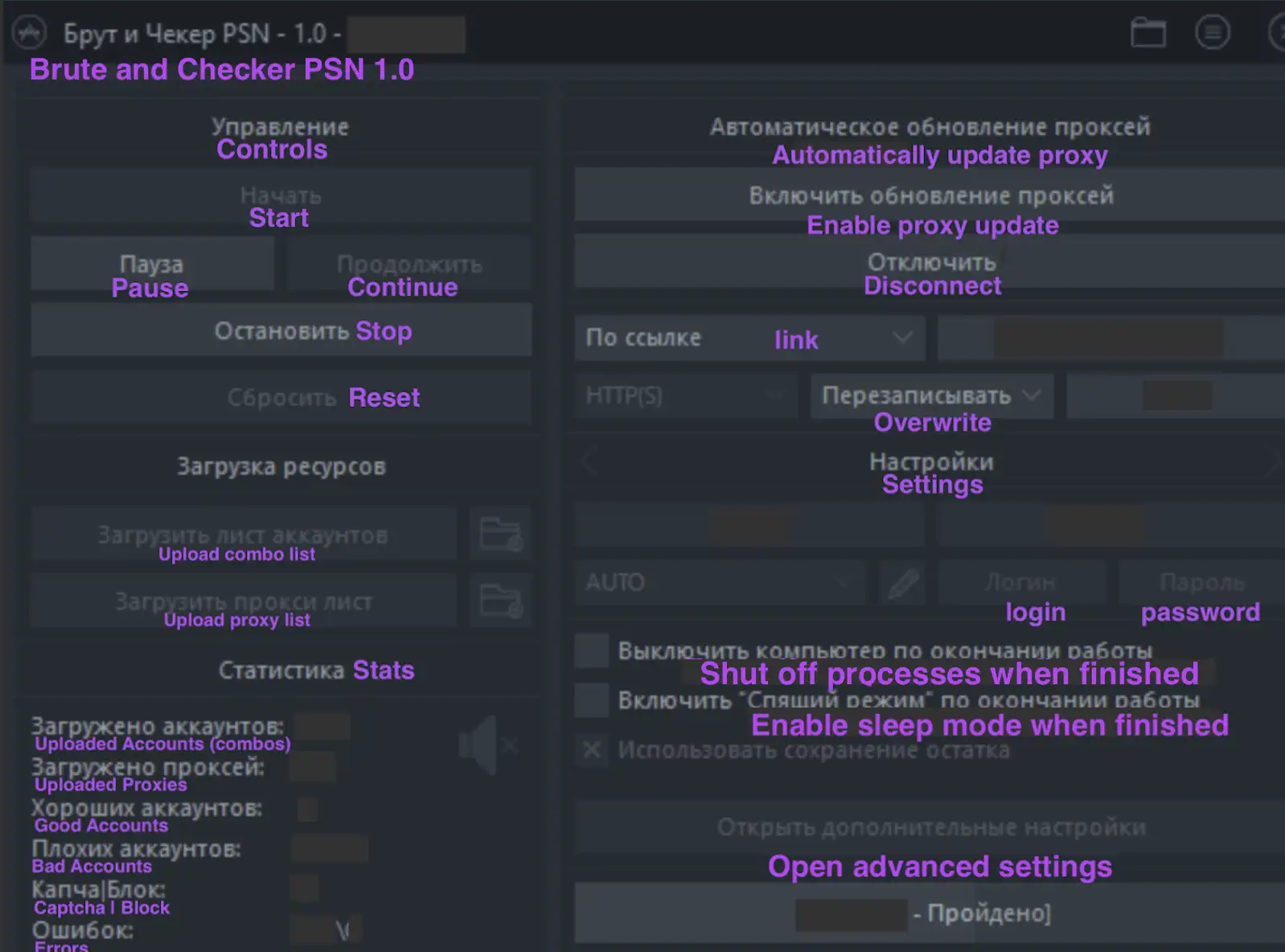
Figure 14: Russian-language “Brute and Checker” credential stuffing tool. We have added English translations of the tool’s features in purple.
We see the familiar functionalities to upload combolists and proxies. A statistics bar shows the statistics of ongoing attacks, including errors, uploaded proxies, uploaded accounts, good accounts, bad accounts, captchas and errors.
The Russian-language account checker below, called Chase Bruteforce, appears to be target-specific to Chase financial applications.
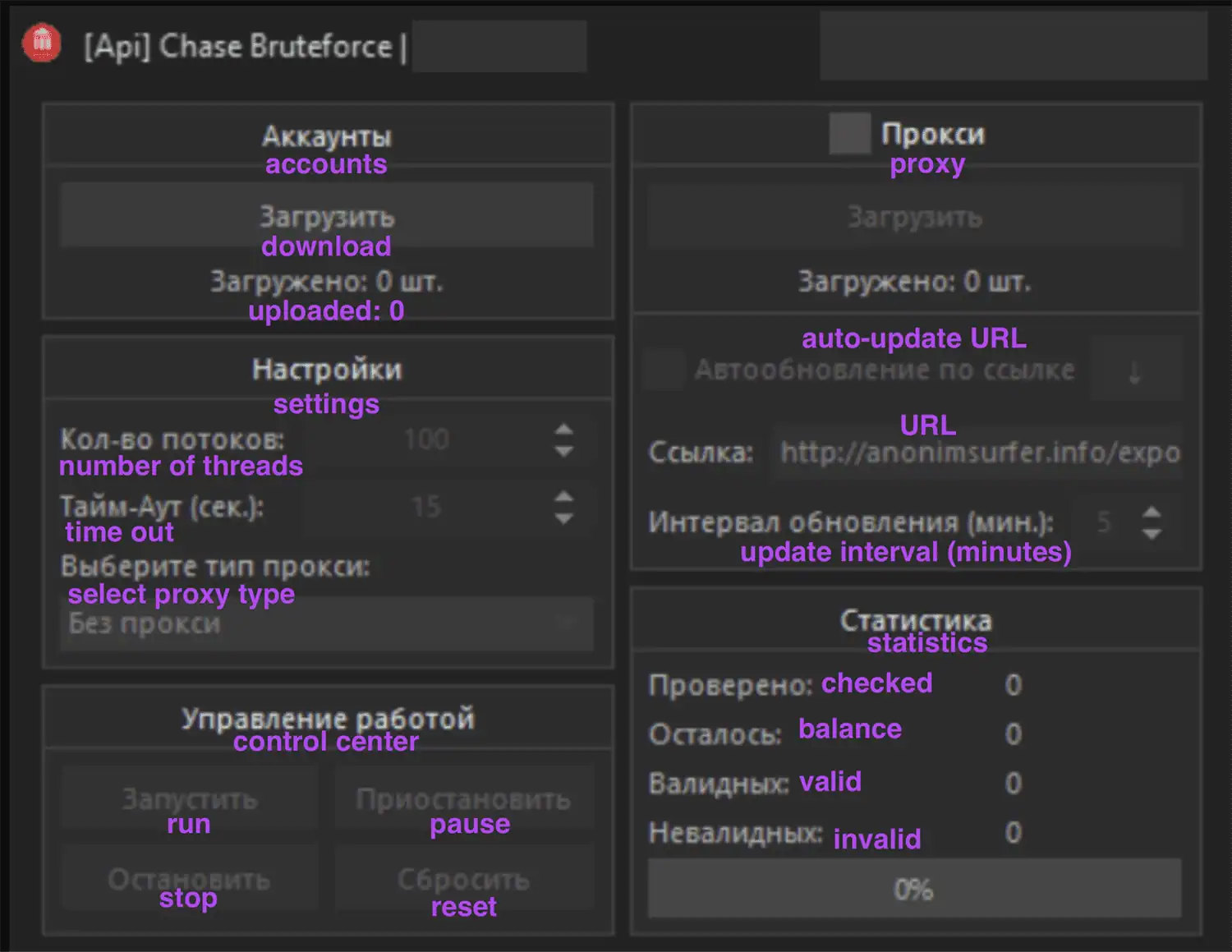
Figure 15: Translation of a Russian brute forcing tool built to target Chase customers. We have added English translations of the tool’s features in purple.
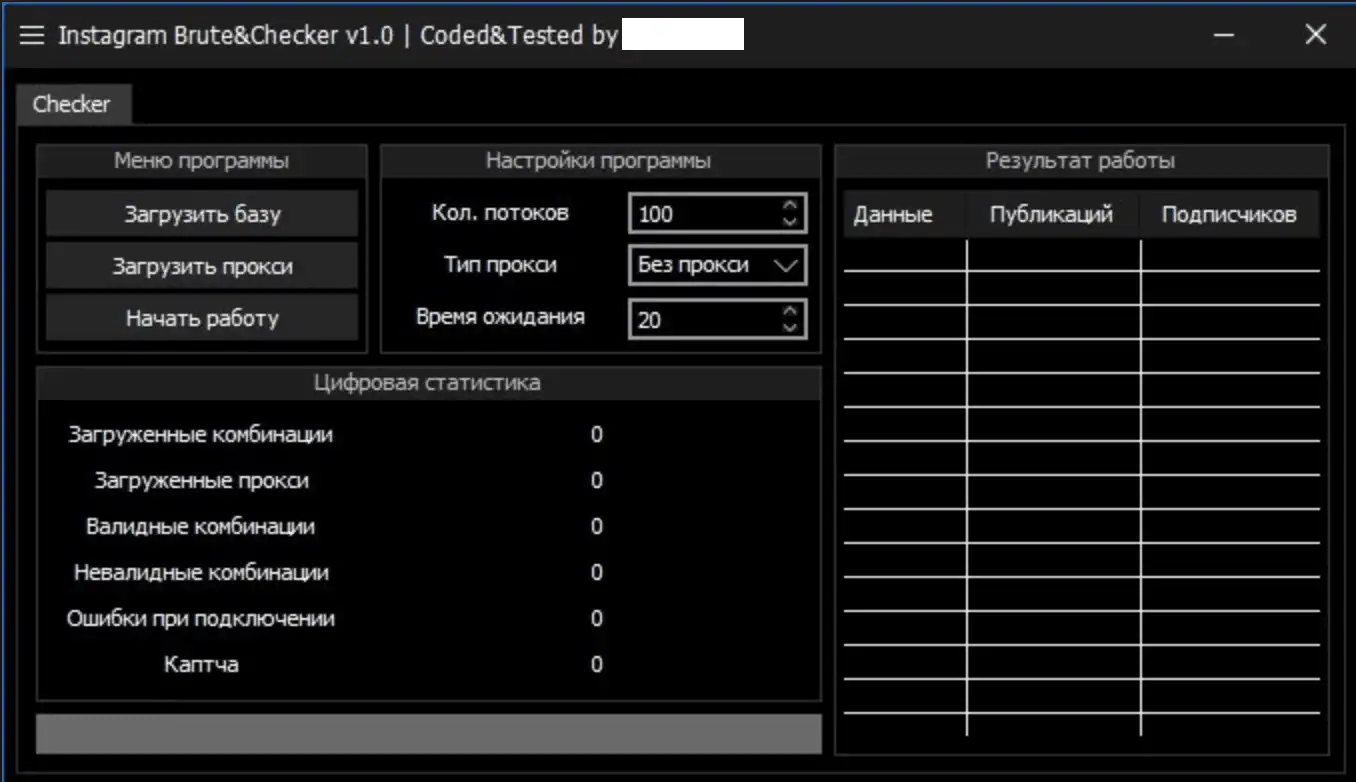
Figure 16: Russian “Instagram Bruteforcing Tool and Checker.”
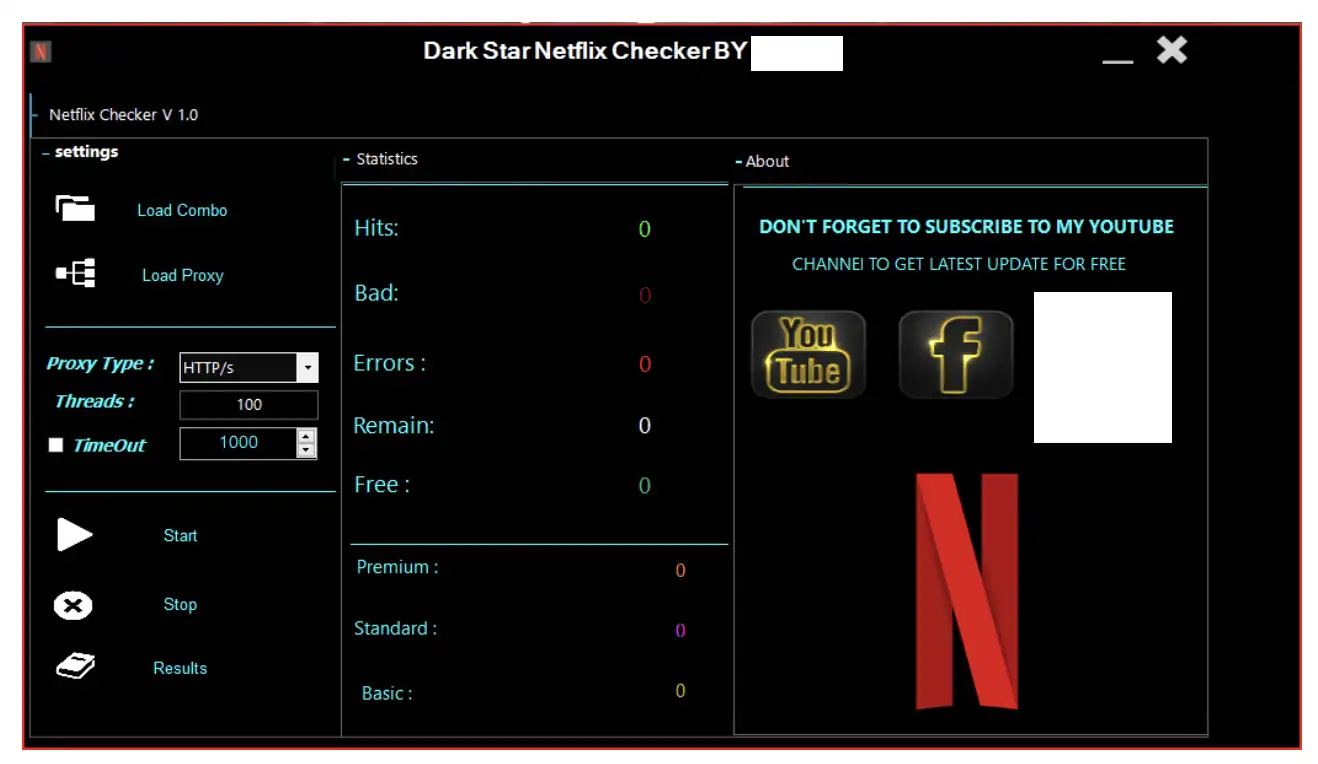
Figure 17: Screenshot of a custom-built Netflix account checker.
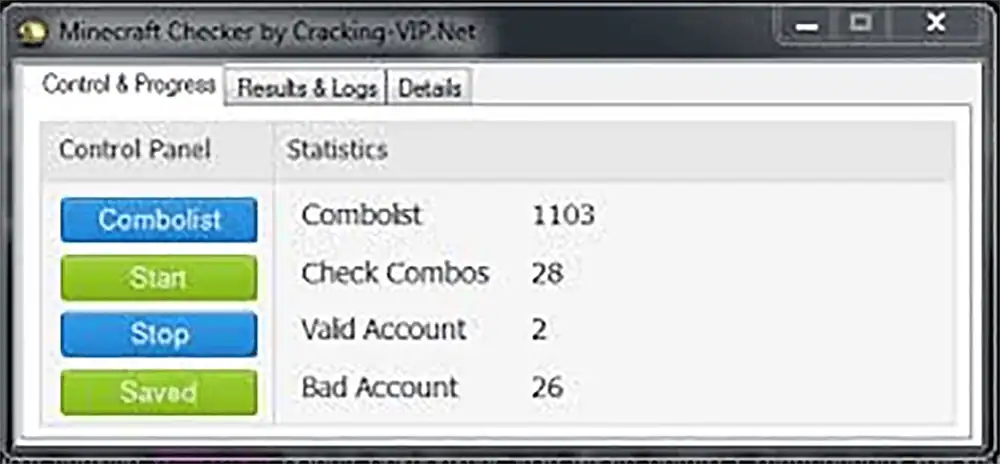
Figure 18: Screenshot of a custom Minecraft checker from an online cracking community.
Protecting Your Users & Yourself
Old reliable tools such as Sentry MBA have been modded while new, custom account checkers targeting specific services are constantly released. These innovations, however, operate upon a single vulnerability. The ubiquity of password reuse is the primary reason that these types of fraud vectors exist. The truest conclusion is that new cracking tools will continue to be developed, and older tools will be improved upon over time – modded to include new features enhancing the effectiveness, speed, and stealth of account cracking.
The best defense is a long, strong, randomly-generated password unique to each account (with the help of a password manager). We did some testing ourselves and found out what makes a password “slowest to crack” in our post How long would it take to crack your password? Strong passwords have random letters, numbers, characters, and are at least 16 characters in length. According to our testing, passwords such as these would require centuries to crack.
Ultimately, as we saw earlier in 2020 when “leaked Zoom accounts” hit the news – and turned out to be lists of credentials formed by textbook credential stuffing attacks aided by reused, previously compromised passwords – the services we use every day are increasingly targeted. While users need to take proper action to protect themselves, it cuts both ways: services themselves have a responsibility to do what they can to protect their users, too.
We recommend:
- Preventing account takeover with proactive and continuous monitoring for compromised credentials – frankly, this is why SpyCloud exists. Don’t let users choose passwords that have ever appeared in a data breach. That is possible – and easy – by checking passwords against our entire database, independent of username / email. Want to learn more? Contact us for a demo.
- In addition to encouraging users to select unique, complex passwords, we also recommend encouraging them to turn on MFA. It increases the difficulty for criminals to access cracked accounts and the sensitive data therein. Criminals already have a wealth of tools at their disposal to take over accounts. Why make it any easier for them?
Get an alert when your email address appears in a breach, putting you at risk for account takeover: sign up for free exposure monitoring.