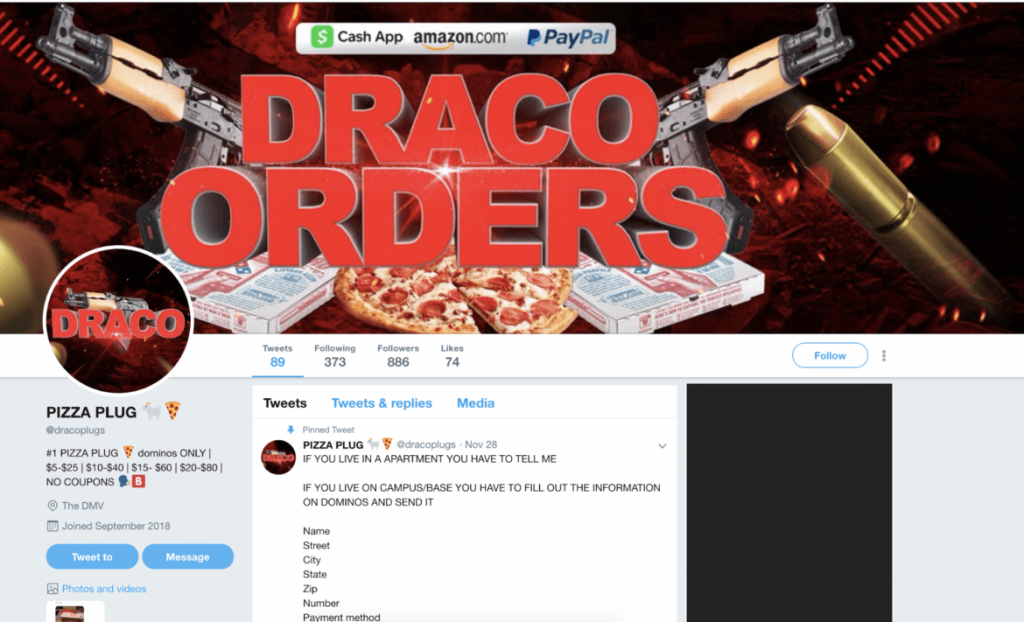
Lower-tier criminals are taking over fast food accounts to reap hot and fresh rewards–on your dime.
By now you’ve probably heard us talk at length about the importance of using passwords that are easy to remember but hard to guess. We’ve cautioned against password reuse, highlighted the importance of utilizing password managers, and reviewed why NIST’s updated password guidelines for 2017 are so important for everyone to understand. The new guidance contains critical updates on how to more securely store and protect our information. It still wasn’t enough to prevent any of the several massive data breaches of 2018, at least those that happened before 2017.
In 2018, the U.S. suffered 1,244 breaches with over 446 million records exposed according to Statista figures on cyber crime. However, our own data suggests these numbers are even higher with 2,882 breached data breaches and over 3.5 billion records exposed. The last month of the year brought a few of the year’s most sobering data breaches. Some breaches included information that members may not want to be publicly linked to their email addresses and real names. The Quora “question-and-answer” site included victims’ names, email addresses, encrypted passwords, and users’ “public questions and answers.” The site was breached in November 2018.
The Facebook breach, which occurred between July 2017 and September 2018, included users’ relationship statuses, contact information, location details, and even devices used to log in and the victims’ recent searches. The methods used to compromise this type of data was often more sophisticated. Not much is publicly known about the methods employed by the “malicious third-party” responsible for the Quora breach and Facebook was breached several times both through vulnerabilities through its code and through third-party apps. It’s important to note that organizations such as these are not soft targets. Breaching them successfully can reap massive rewards for sophisticated criminals as long as they are not caught. But what about softer targets? Unsurprisingly, basic guidance on security hygiene and passwords strength applies to preventing these as well.
The low-hanging “food”
To be fair, sites using weak encryption algorithms and committing embarrassing security transgressions, such as storing passwords in plain text, are largely to blame for some of the most high-profile breaches. If services such as Facebook and Quora are so easily breached and manipulated, then what about softer targets? Fraudsters dealing in food delivery apps represent a prime example. These services, and the methods used to defraud them, are common topics of conversation among the script kiddie (“skid”) population. In our blog post, “Criminals Are Using These Tools to “Crack” Your Website”, we talked about some of the old-school credential stuffing tools, such as Sentry MBA, that are often used by lower-tier offenders to take over accounts.
These custom-built “cracking” tools make it easy for freshly-minted cyber criminals to automate credential stuffing. Credential stuffing ( or password spraying) is the act of testing large sets of stolen credentials against a targeted interface. Criminals load lists of breached credentials into these tools to test them at large scale against targeted web or mobile authentication interfaces.
In our research, we’ve seen many popular fast-food services being targeted by criminals who are looking to cash out quickly. Some of these criminals are taking over accounts at major food retailers and monetizing them by offering these same services at cheaper prices. According to Dunkin’ Donuts, there has been a rise in attacks in the food industry, as pointed out in a recent report of Dunkin’ Donuts experiencing ATO activity.
Tools for cracking Dunkin’ Donuts accounts specifically have been around since at least 2017. The screenshot below shows a custom Dunkin Donuts account checker that was posted to an online cracking forum on October 2017. Just as there are well-known credential stuffing tools, such as Sentry MBA and Vertex, there also exists custom application-specific account checking tools which employ similar tactics. Some of these tools act as account checkers only for specific targeted services while others are designed to grab credentials from paste sites. This Dunkin Donuts account checker needs to run from a U.S.-based IP address in order to work.
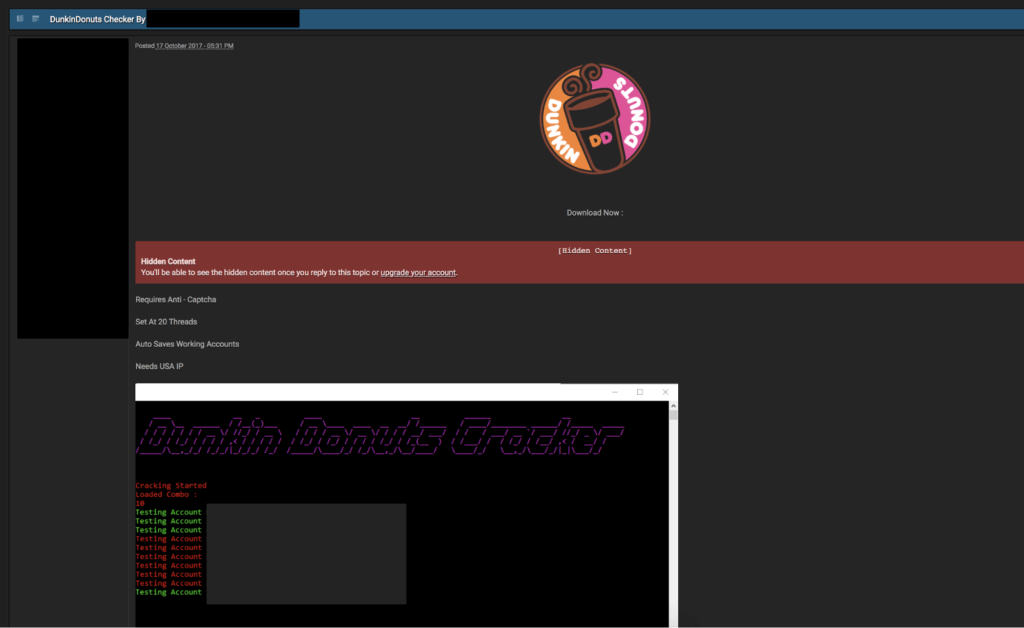
Screenshot of an actor’s advertisement of a custom cracking tool to a popular cracking forum.
Of course, donuts are not their only option. Such custom account checkers exist for several types of food-delivery services. The screenshot below shows a similar checker designed to target the Domino’s pizza delivery app.
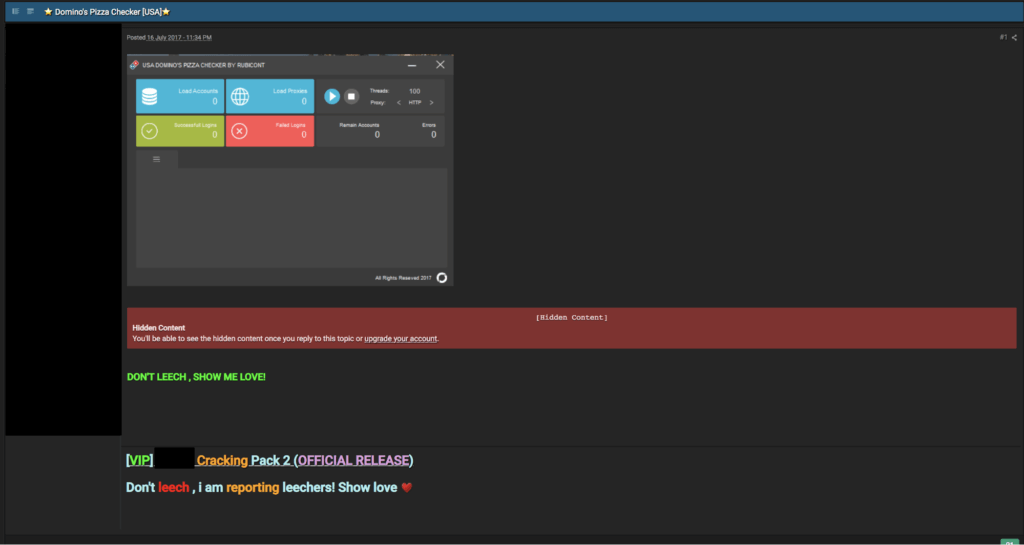
Screenshot of member of a cracking forum advertising a custom account checker for Dominos Pizza.
Although these tools are rudimentary, they represent a relatively safe and unsophisticated way of taking over accounts when compared to more involved methods. By running these tools through a proxy, criminals need only to push a button and wait until there is a hit in one of their combo lists. Given that the victim hasn’t likely enabled multi-factor authentication in their pizza delivery app account, they could be buying pizza for someone they never knew.
Beyond Credential Stuffing
The methods employed by many of these relatively unsophisticated criminals have grown beyond credential stuffing. Some of these services, such as so-called pizza “plugs”, rely more on social engineering and credit card fraud than the brute-force blasting of credential stuffing tools.
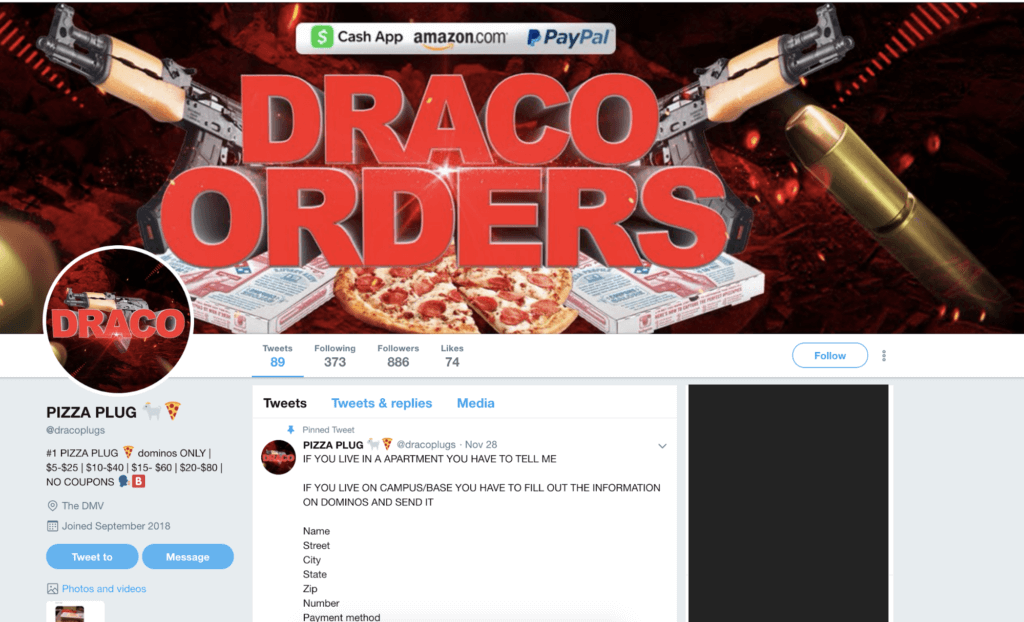
Screenshot of an advertisement for a pizza plug service on Twitter
These services are likely more trouble than they’re worth. Twitter accounts are advertising “cheaper” than normal food service and are operated by criminals affiliated with account takeover campaigns. These types of pizza “plug” operations allow hungry customers to spend a few bucks on a pizza order rather than pay full price. Some of the most vulnerable populations, such as college students, have fallen victim to scams which resulted in unintended consequences. Faced with a raid of police officers dressed as pizza delivery men, one student learned the hard way that these schemes are operated by criminals.
When someone indulges one of these pizza plugs, those behind the scheme use the victim’s personal information to place a pizza order in their name, using a stolen credit card. We’ve talked about fullz here before, especially in terms of how important they are to credit card fraud operations. Credit card fraudsters and data resellers use it to refer to “full” packages of a victim’s personal information. These packages usually contain a victim’s birth date, social security number, physical address, mother’s maiden name, and any other data that can be used to verify the victim’s identity. This information is combined with fraudulent raw credit card data (which is read from a credit card’s magnetic strip by point of sale (PoS) terminals) to initiate transactions. Therefore, when a pizza plug’s victim receives his “deal,” he may also be met with allegations of credit card fraud and a court order. Is this risk worth saving a few dollars on pizza?
Not The Smartest Game
There appears to be a healthy ecosystem centered around pizza plugs. But for criminals, the pizza plug game can be risky. Although those fraudsters who produce the logs may evade detection, it is the actual plug themselves who may get caught thanks to notifications sent to the holder of the original account.
In terms of the pizza plug business, it appears that in new ecosystems such as these, the first point of contact is the wholesaler. These are the sellers you see in twitter posts advertising themselves as pizza plugs and are effectively functioning as the middleman. The actual criminal who supplies the logs appears to be doing so using account checking tools and account cracking tools, such as Sentry MBA.
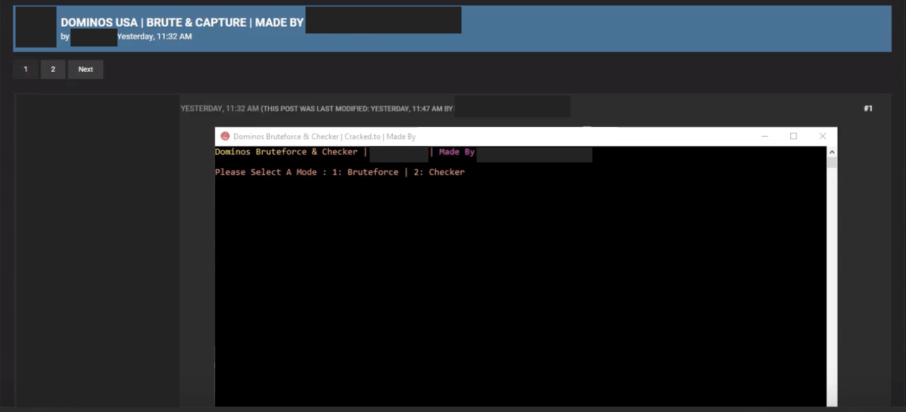
Screenshot of a custom brute forcing tool for the Dominos app on a cracking forum.
These fraudsters also appear to be using custom cracking tools as well. Although it’s not completely clear where the resellers are acquiring compromised accounts, it appears that some are leveraging them directly.
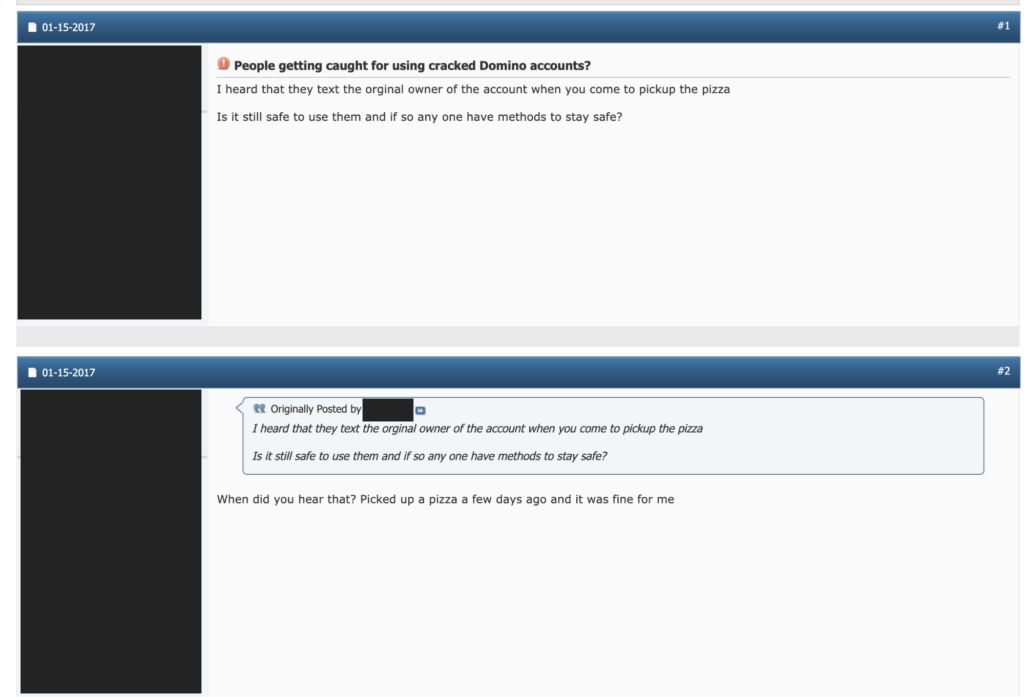
In the screenshot above that was taken from a cracking forum, one user expresses fears that the “original owner” of the cracked account will receive a text message when the pizza is delivered to the wrong person. The user appears to be afraid that using the app with cracked account may be unsafe. Another user assured him that, in his case, this had never been a problem. Still, some victims are catching on. One victim of a pizza plug in British Columbia posted to Reddit about the situation, complaining that someone had stolen their Domino’s Pizza Points and effectively cashed out their account after account takeover.
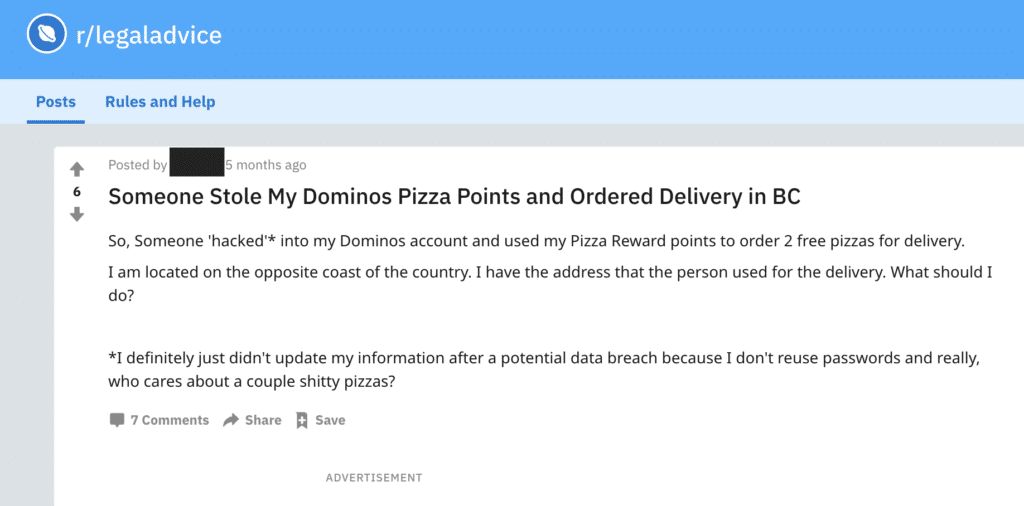
Victim of a pizza plug seeks recourse after finding out that their account has been used fraudulently.
“So someone ‘hacked into my Dominos account and used my Pizza Reward points to order 2 free pizza for delivery,” they wrote. “I am located on the opposite coast of the country. I have the address that the person used for delivery. What should I do?”
Unfortunately for criminals, if the victim has the proof via a notification that pizzas were ordered to a different address in their name, that may be all the evidence they need. Whether or not the order was for the customer of a pizza plug or the fraudster themselves, it may no longer be relevant when police show up at the door.
Still, some customers of pizza plugs are trying to remedy the problem of scammer pizza plugs vigilante-style. They have little recourse given that they know the scheme itself is fraudulent. One such vigilante runs a Twitter account called “Pizza Plug Exposer.” The job of this individual isn’t to expose pizza plugs, rather, to expose those who scam customers out of orders for pizza that never get delivered.
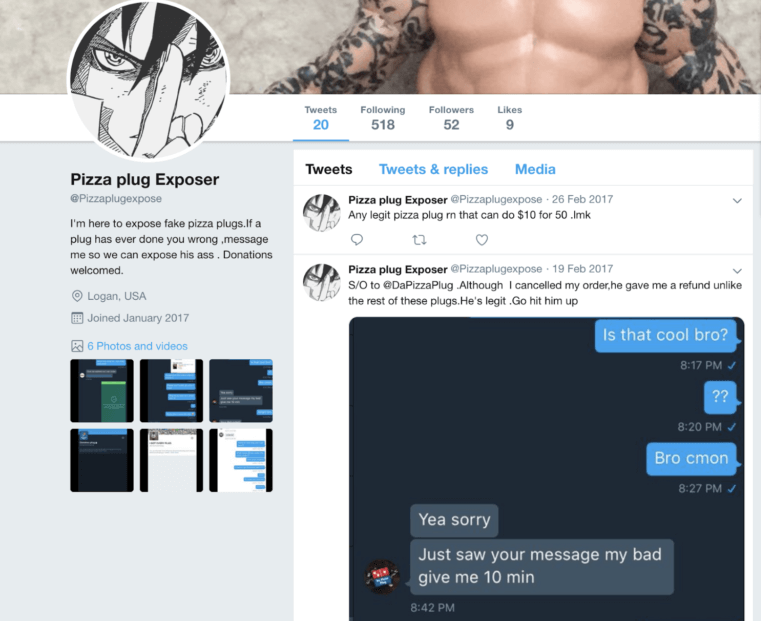
Screenshot of the Pizza Plug Exposer page
“I’m here to expose fake pizza plugs,” the page reads. “If a plug has ever done you wrong, message me so we can expose [him]. Donations welcomed.”
Conclusion
Although there appears to have been a healthy ecosystem of fraud orbiting around pizza delivery, the opportunity window may be closing. Normally, either a fraudster would supply a pizza plug with logs who would then bear the risk of ordering the fraudulent pizza, or a fraudster would function as the plug himself. Now that law enforcement has caught wind of the scheme and pizza plug exposers have done their work revealing scammers, the scheme appears to be dwindling.
It’s no secret there is no honor among thieves. It appears that pizza fraudsters, pizza plugs and their customers are no exception. If you truly want a great deal on pizza we recommend asking your favorite pizza place if they have any specials. Saving a few dollars using cracked account may not be worth the risk.