On April 24th, Nintendo confirmed that attackers have been able to access 160,000 Nintendo accounts since early April. SpyCloud researchers have identified source code for an account checker tool that we believe cybercriminals have used in credential stuffing attacks against the compromised accounts.
How do attacks like this happen? What’s unique about this particular account checker tool? And what can users and enterprises do to protect themselves from similar account takeovers?
In this post, we’ll explore answers to those questions as we break down this account checker’s source code and examine how some of the crimeware developer’s design choices mimic those found in legitimate applications.
Background: Understanding Credential Stuffing
Some news outlets have begun referring to this incident as a “hack” or “breach,” implying that the accounts were accessed via a data breach of Nintendo itself. Instead, we believe that attackers used a combination of crimeware and older breach data to identify and take over accounts with vulnerable logins.
In a typical credential stuffing attack, criminals use account checker tools to rapidly check lists of stolen credentials against online logins, typically using credential pairs that were made available to attackers through previous data breaches. When a user’s credentials match those found in a previous breach, the attacker is able to take over the account for the purpose of monetizing it, whether by exploiting account access themselves or by reselling access to other criminals.
Affected Nintendo accounts were vulnerable because users had chosen passwords that had been exposed in previous data breaches. Given that 59 percent of people admit to reusing passwords, it’s unsurprising that so many accounts were vulnerable to this type of attack.
Breaking Down “Nintendo Checker” Source Code
Account checker tools typically fall into one of two categories: generic or custom. Most often, attackers begin with a popular, generic checker such as Sentry MBA and upload a configuration file, or “config,” to modify it for a specific target. Less frequently, criminal developers create custom cracking applications for target organizations. Custom software is easier for the attacker to sell as a proprietary product, whereas configs are highly likely to leak to other criminals and lose value quickly. This is because configs generally consist of raw text files, which are easy to copy, paste, and share. In contrast, cracking and leaking custom software requires a higher level of skill.
In the case of this particular account checker tool, which we will call “Nintendo Checker” to avoid providing the tool’s author with publicity, the developer chose to write custom code specific to Nintendo rather than relying on a config. This is one of many decisions indicating that it was created for resale to other criminals, as configs are easier to leak or resell. Many design decisions mirror those of a traditional software developer, such as using a licensing server and anti-debugging features to control the user experience, further indicating that the intention for writing this software was monetary.
By accessing the source code for this Nintendo account checker, SpyCloud researchers were able to gain insight into how these tools are designed for targeting specific industries or companies.
Notable Features:
- A kill switch in the source code makes it possible to remotely disable the checker for everyone who purchased it
- Users authenticate using a license key, as with traditional software products
- The checker also leverages users’ hardware ID for additional authentication, which is a unique identifier associated with their computer that cannot be easily spoofed, preventing unauthorized sharing
- The checker has anti-debugging capabilities built in to make reverse engineering challenging for security researchers or anyone attempting to crack and resell it
- The application is written in C#, a programming language for Windows
Execution Path
This graphic describes each step of the program’s execution path, showing at what point the kill switch is used and at what point anti-debugging features come into play.
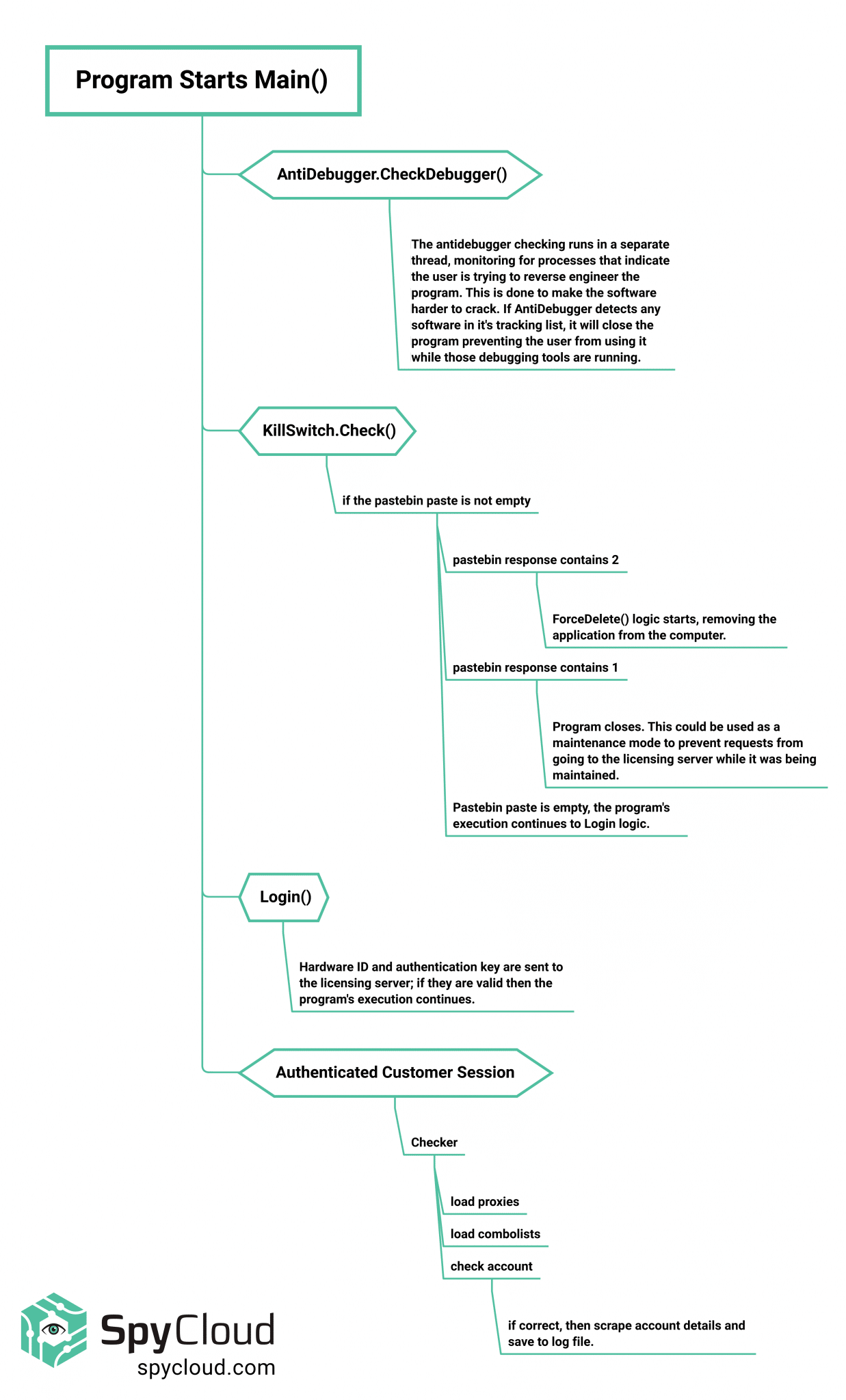
Figure 1: Execution path of the account checker program.
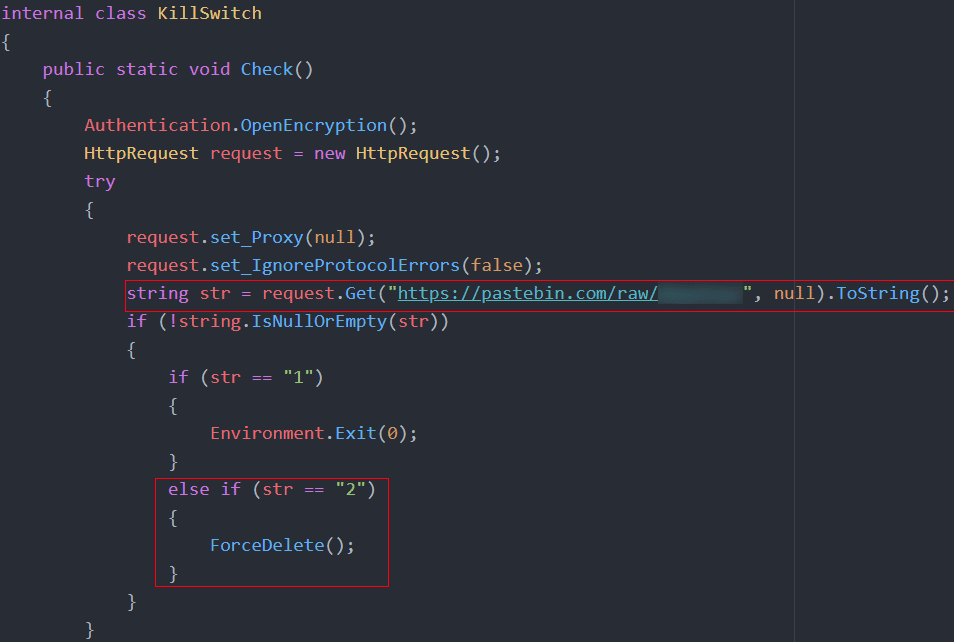
Remote Kill Switch
As soon as a user opens the application, the software runs “kill switch” logic to determine if the user may proceed. Essentially, the kill switch code provides the attacker with remote control over the application, including the ability to put the program into maintenance mode for all “customers” or even wipe it from all users’ systems.
Figure 2: Remote kill switch code in Nintendo Checker.
As you can see in the screenshot above, the kill switch code goes out and hits a pastebin link belonging to the developer. Choosing pastebin to store this value would be an unusual, rudimentary approach for a traditional software product, but provides the developer with remote control. One reason this approach would be strange for most use cases is that antivirus software typically flags any software that reaches out to pastebin as potentially malicious activity. This is a risk for the developer as the criminal community could claim that the checker contains malware, which could damage their reputation. Given the importance of reputation in criminal communities, this could hinder their ability to monetize their products.
The program’s path of execution depends on the string stored in the pastebin paste. If the string is not empty, the code continues. If the string is greater than or equal to one, the program closes. This option is what we believe to be the maintenance mode, enabling the developer to perform maintenance on the licensing API.
On the other hand, if the paste is equal to 2, the program executes a method called ForceDelete. This method writes a script to a .bat file (a batch processing file for Windows), and executes it. This batch script will terminate the running program, and will remove all files and folders where the program was running. If this code is executed, the program is completely removed from the user’s machine.
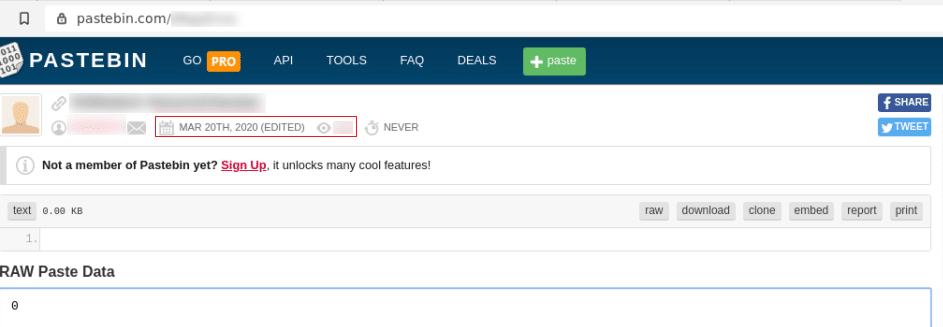
Interestingly, the pastebin page was last edited on March 20th, the day Animal Crossing: New Horizons became available for the Nintendo Switch, suggesting that this checker tool has been available since at least that date.
Figure 3: Screenshot of the developer’s pastebin paste, showing the date it was last edited.
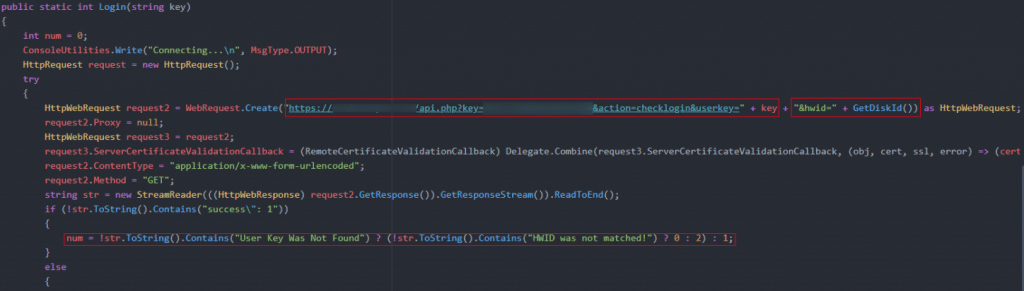
Licensing
After running the remote kill switch code, Nintendo Checker runs “Auth class” code for user authentication. As you might see in a traditional software product, Nintendo Checker authenticates users using a license key via PHP API. Users receive a license key when they purchase the product, which they can enter within the product to access its functionality.
Figure 4: Nintendo Checker authenticates users by checking for a license key and hardware ID.
On its own, a license key could be reused by multiple people. To reduce the risk of users sharing their license key with others, the software also checks the user’s hardware ID – the serial number of the user’s harddrive, which cannot be easily changed – as an additional form of authentication. If these authentication steps fail, the software will display an error message: “User Key Was Not Found” or “HWID was not matched!”, depending on the issue.
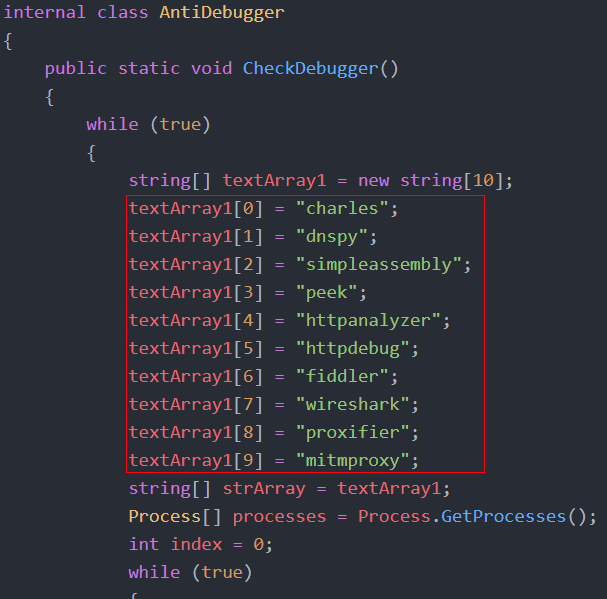
Anti-Debugging Features
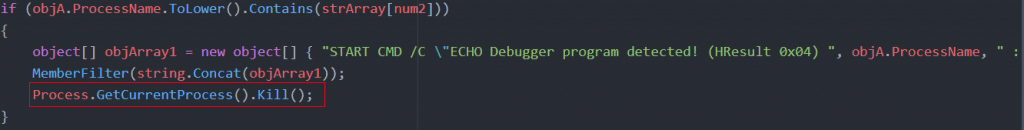
The Nintendo Checker software includes anti-debugging capabilities to discourage reverse engineering. Specifically, the application’s code checks for open processes looking for the account checker. For example, it detects Wireshark, an application used to analyze network traffic. If found, it triggers the kill switch and removes the software from the system.
Figure 5: Anti-debugging capabilities within Nintendo Checker.
Figure 6: Steps the program takes if debugging tools are detected.
In addition to identifying debugging tools, the authentication code checks the user’s public key fingerprint to make sure it matches the original certificate used by that host. This step, called certificate pinning, guarantees that someone can’t spoof or man-in-the-middle the SSL traffic. If the program detects that someone is tampering with SSL to view traffic, it triggers the kill switch.
The purpose of this type of anti-debugging feature is to discourage security researchers or other criminals attempting to crack and resell the product as their own. Having the source code meant that SpyCloud researchers didn’t need to spend time attempting to find ways to defeat these features. However, we did encounter a forum post by a criminal who had cracked the account checker despite these features and offered to share the application with others.
Account Checker Functionality
Having satisfied Nintendo Checker’s authentication measures, users can access the checker’s functionality. The software’s capabilities are very typical for an account checker tool.
To get started, users load their own proxies into the account checker. Proxies are devices that make it possible to obfuscate the origin of someone’s internet traffic. Feeding traffic through a proxy makes it appear to come from the proxy’s IP address, which can be helpful for both malicious and legitimate purposes. When used with an account checker tool, proxies help the checker’s malicious traffic blend in with normal user-behavior, making it harder for security tools to detect.
Users also need to load their own combolists, which are “combination” lists of stolen or leaked usernames and plaintext passwords that are formatted for use with account checker tools. Stolen credentials are typically sourced from previous data breaches; however, by the time the breach data leaks from the initial threat actors to a broader criminal audience and is repackaged into combolists for high-volume credential stuffing attacks, the data may be years old; for example, the Collection Combolists that made headlines in early 2019 contained some credential pairs sourced from the 2012 LinkedIn breach. However, people continue to reuse favorite passwords, giving criminals a reliable success rate even with older lists.
With both proxies and combolists loaded, criminals can start using Nintendo Checker to rapidly stuff Nintendo logins using their stolen credential pairs. If a Nintendo user’s login credentials have appeared in a previous breach and appear in the attacker’s combolist, Nintendo Checker attacker gains access to their Nintendo account.
To learn more about the timeline of a breach and what types of attacks happen during each stage of the breach lifecycle, watch our webinar: Targeted Attacks: How Sophisticated Criminals Bypass Enterprise Security Measures
Log Files
After Nintendo Checker gets a successful login request, it parses the response from Nintendo and produces logs containing the following account and billing information, depending on the method of payment associated with the account:
- Gold Points balance (points that allow you to buy Nintendo Switch digital games)
- Nintendo Store or Nintendo eShop balance
- Paypal subscription ID
- Card Type (Visa, Mastercard, etc)
- Card expiration
- Currency denomination
- First 6 digits of credit card number
- Last 4 digits of credit card number
Conclusion: Don’t reuse passwords because they might “turnip” on the dark web
The design patterns chosen by the author of Nintendo Checker share uncanny similarities to those used in legitimate software products. Still, despite the anti-debugging measures built into the tool, other criminals were still able to crack the tool, showing the persistence and competition that characterize criminal communities.
Currently, Nintendo Checker’s functionality is broken due to changes Nintendo made in response to the influx of account takeover attempts they experienced after the release of Animal Crossing. When Nintendo saw a spike in ATO activity, they took responsible action by notifying their users, resetting affected passwords, and urging users to enable multi-factor authentication and avoid password reuse. However, Nintendo configs are already circulating on criminal marketplaces and forums, which means that the criminals will continue to iterate and come back with new tactics to crack Nintendo customer accounts.
For enterprises like Nintendo, protecting users from account takeover poses a unique challenge. Inevitably, some portion of users will reuse passwords, putting their accounts at risk. To protect users from account takeover, enterprises need to secure their human attack surface by proactively monitoring user logins for credential reuse and resetting compromised passwords — before criminals have the chance to use them.
What enterprises can do to combat account takeover:
- Educate users about security hygiene, including password security
- Align with password security guidelines from the National Institute of Standards and Technology (NIST)
- Constantly monitor user credentials for weak or stolen passwords (including employees, consumers, and third parties)
- Force the use of multi-factor authentication (MFA) everywhere
What individuals can do to protect themselves from account takeover:
- Create a unique password for every online account
- Choose long, strong passwords
- Use a secure password manager to keep track of passwords
- Enable multi-factor authentication wherever possible
Are your users at risk of account takeover? Check your corporate exposure and contact SpyCloud to set up a data test.