2023 SpyCloud Ransomware Report Finds Outdated Defenses Not Keeping Up Against Infostealer Malware
Over the past few years, organizations have embraced the new reality of hybrid workplaces, where employees can conveniently collaborate and work from anywhere. Cybercriminals have also adapted to this digital- and cloud-first environment, pivoting to next-generation tactics.
Security operations (SecOps) teams, however, haven’t fully kept up with preventing ransomware according to our new SpyCloud Ransomware Defense Report 2023.
What you’ll find in this year’s ransomware report
For the third year in a row, we sought insights from more than 300 cybersecurity practitioners and leaders about their ransomware defense practices and capabilities. Our goal with these surveys is to assess the year-over-year impact of ransomware on organizations, and to learn how security teams are adapting their defenses to address rising threats like malware-exfiltrated identity and authentication data. This year, we combined the survey results with an analysis conducted using original research from our own database and ransomware victim data from ecrime.ch to paint the full picture of the ransomware challenge teams face today.
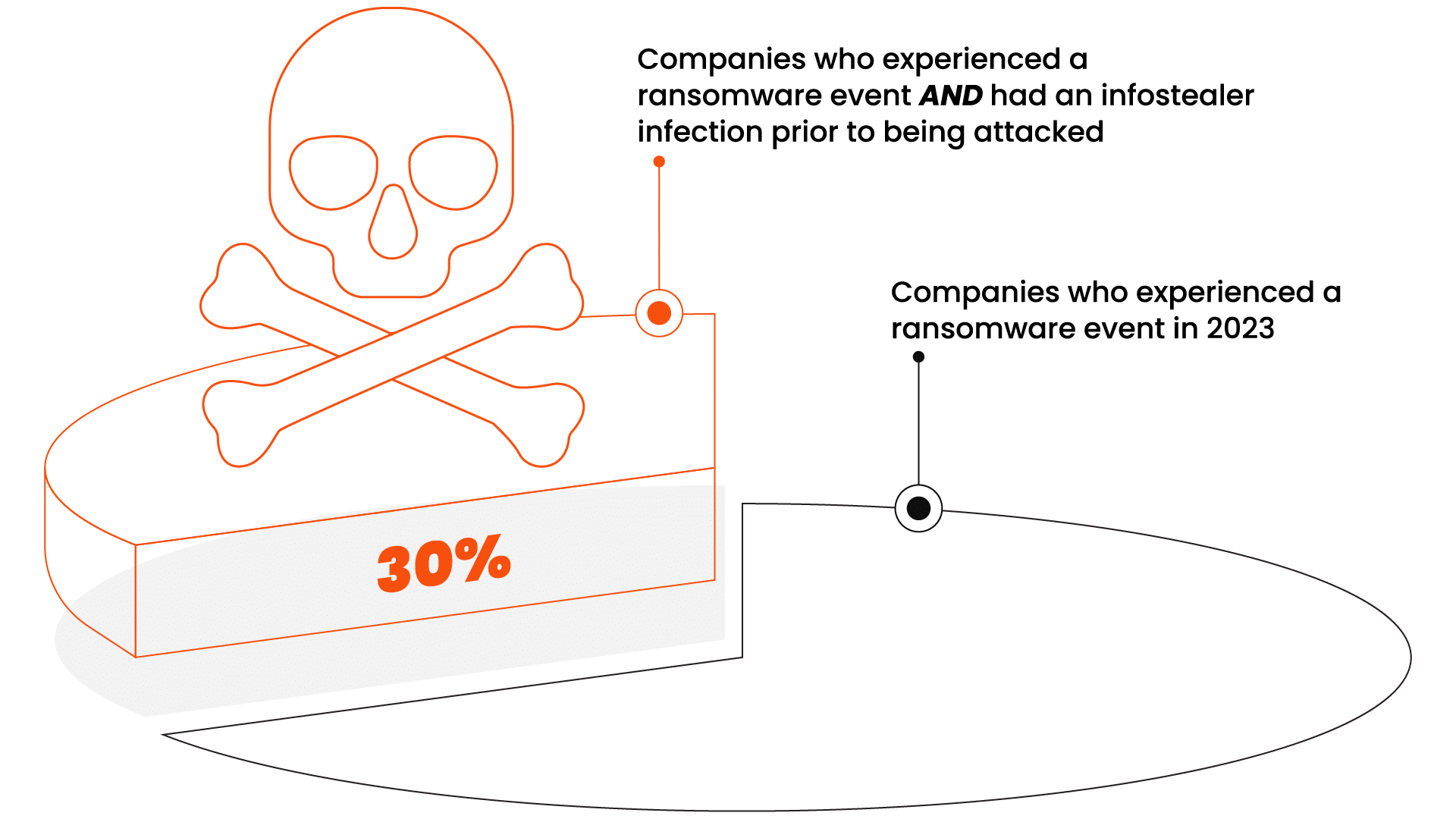
What we found is a critical gap in current ransomware defense practices: comprehensive malware remediation. The rapidly growing threat of infostealer malware is critical to the discussion about ransomware defense because – as shared in this report for the first time – research now shows that the presence of certain infostealers can be the precursor to a ransomware attack. Of 2,613 North American and European companies known to have experienced a ransomware event in 2023, nearly one-third (30%) had at least one infostealer infection prior to being attacked.
Other highlights in the report include:
81%
of surveyed organizations were affected in some way by ransomware at least once in the past 12 months – showing that ransomware continues to be a top threat for the majority of organizations.
98%
of those surveyed agreed that better visibility of malware-exfiltrated data and automated remediation workflows would improve their ability to combat ransomware and improve security posture – however, these beliefs were not reflected in their prevailing security practices and planned improvements.
60%
of organizations identified ransomware prevention as their top priority in the next 12 months – underscoring the importance of taking complete Post-Infection Remediation steps to negate the impact of infostealer-siphoned data.
This year’s report is packed with additional insights, including benchmark data that teams can use to see how their defense mechanisms stack up against peers. Before you dig into the full report, here are a few more topics you’ll find details on inside.
Contrary to popular belief, ransomware impacts organizations regardless of size
Fewer than 12% of our surveyed organizations that were hit by ransomware described their cumulative costs over 12 months as negligible, and 39% spent more than $1 million. These numbers likely don’t account for the harder-to-measure costs such as reputational damage, the impact on operations, and the drain on resources.
And we found that ransomware remains a huge problem regardless of the size of the organization, busting the myth that larger organizations are in a better defensive position because of bigger budgets and more resources. Although organizations with fewer than 1,000 employees weathered the worst impact (with 90% affected), we found that large enterprises with 10,000 or more employees were impacted at the same scale as mid-sized ones (with at least 70% affected).
Organizations are overly optimistic about ransomware defense capabilities
The majority of those surveyed (a whopping 79%) felt confident about their ability to prevent a full-scale ransomware attack, although SecOps practitioners were much less confident than executives (71% of practitioners agreed vs. 91% of execs). However, given the high numbers of organizations that suffered an incident and the gaps in their defenses, this confidence may be misplaced.
One reason behind the high level of self-assurance may be the temporary slowdown in ransomware activity toward the end of 2022. Some researchers found that the number of attacks leveled off and others even noted a decrease in both threat activity and ransomware revenue. But this lull didn’t last long. The number of attacks skyrocketed during the second quarter of 2023 while ransom payouts were headed toward record numbers.
Although it’s common for organizations to judge their defense capabilities based on the current state, this is a dangerous approach. Criminals are innovating fast – and even countermeasures that are adequate today will not keep up with the pace of that innovation. Our survey proved this to be the case, showing that SecOps teams are relying largely on traditional countermeasures like data backup and endpoint protection for prevention.
This approach is inadequate in the new era of cyberattacks, where authentication data is the new currency. Cybercriminals have shifted to using malware-exfiltrated data like stolen session cookies to hijack sessions and seamlessly impersonate employees – bypassing authentication layers from multi-factor authentication to passkeys. Incident response in this evolved environment needs to move beyond conventional device-centric methodology to identity-centric malware remediation in order to prevent follow-on ransomware attacks stemming from the use of data stolen from infected devices.
The human factor may be impossible to solve
Phishing and social engineering ranked as the riskiest entry points for ransomware attacks in this year’s survey, which is far from surprising, since it’s well-known that human behavior and poor cyber hygiene are major contributors to cyber incidents. Verizon’s 2023 Data Breach and Incident Report, for example, found that 74% of all confirmed breaches include the human element – and this number has remained consistently high over the years.
User awareness aimed at changing behavior has long been the mainstay for trying to solve human-driven risk. But organizations are now recognizing that this risk is inevitable, especially with the proliferation of unmanaged and third-party devices. Our survey found that SecOps teams are shifting their focus from user awareness and training to technology-driven countermeasures.
While this is a positive change, it does cause concern because earlier SpyCloud research found that organizations don’t have complete visibility and control across all users, applications, and devices connecting to the network and accessing sensitive data. Without this visibility, the effectiveness of any technology-base controls will be limited.
Ransomware prevention starts with robust malware remediation
With ransomware prevention as the top priority, it’s important to understand that ransomware, at its core, is a malware problem. And the attack surface today includes not just devices but also users and applications.
Incident response must take into consideration that threat actors are exploiting infected systems to exfiltrate authentication data, as well as identify potential entry points to corporate resources and deliver executable files. But conventional response doesn’t address the risk of data stolen from an infected device.
For example, only 19% of those surveyed said that improved visibility and remediation for exposed credentials and malware-exfiltrated data is a priority in the next 12 months. And while automation was viewed as a high priority overall, automated workflows to remediate compromised session cookies/tokens and automated workflows to remediate exposed passwords were among the bottom three authentication priorities.
To succeed in the fight against ransomware, SecOps teams must embrace the paradigm shift of Post Infection Remediation – moving from machine-centric response to an identity-centric one. This next-gen approach goes beyond clearing an infected device, taking additional steps such as resetting stolen credentials and invalidating exposed applications’ active web sessions.
These extra malware remediation steps are necessary for protecting an organization from a ransomware attack – but they’re missing in most incident response playbooks. Until SecOps teams update their playbooks with next-gen tactics, cybercriminals will remain several paces ahead.
Get the report
To get your copy of the new findings, download the SpyCloud Ransomware Defense Report 2023 or watch Ransomware Reality Check: The New Landscape, where SpyCloud researchers break down the top data insights.