On May 2, 2024, the website for The Post Millennial, a Canadian news outlet, was defaced by threat actors. The defacement consisted of a fake message from the news outlet’s editor, Andy Ngo, and leaked three databases which allegedly included all of their mailing lists, their subscriber database, and personal details on their writers and editors.
This data has continued to circulate since the defacement, and was posted to BreachForums (prior to the site being seized by the FBI on May 15, 2024).
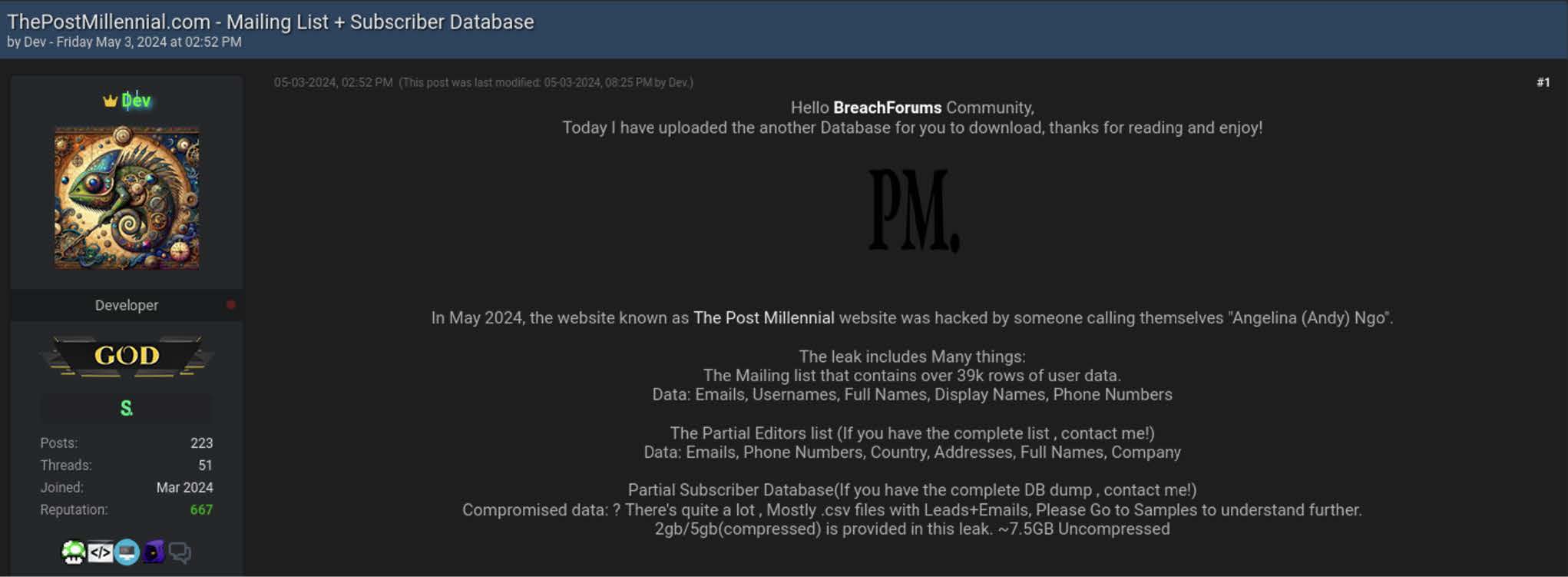
The data was re-posted to BreachForums the day after it was originally published to the defaced website.
SpyCloud Labs’ analysis of the leak
SpyCloud Labs parsed and analyzed the data from these three databases and ingested over 87 million records, including data related to over 57 million distinct email addresses and over 39,000 passwords. Here’s a summary of our analysis of the stolen data – which includes notes on its usefulness to cybercriminals as fuel for follow-on attacks.
Subscribers database
The subscribers database contains over 39,000 records and includes names, usernames, email addresses, plaintext passwords, account information, gender, and payment information apparently for subscribers to The Post Millennial.
Individuals whose data was leaked in this database should be on the lookout for account takeover attempts against accounts sharing the same email and password combination. Many subscribers in this database appear to use work-related email addresses, with some emails in the data leak even associated with US government agencies and law enforcement organizations. Because most people re-use their passwords across multiple accounts, this combination of work emails and plaintext passwords also creates an enterprise risk for bad actors to target workplace accounts using the leaked credentials.
Writers and editors database
The writers and editors database contains 761 records for writers and editors of The Post Millennial including names, usernames, addresses, IP addresses, emails, phone numbers, and account information.
While some of this data appears accurate and directly correlated with contributors to the news outlet, other records appear to be populated with some amount of placeholder or fake data. For example, 540 out of 761 records list the country of the user as “Zimbabwe.”
Mailing lists database
The mailing lists database is by far the largest database included in the data leak. While there appears to be some limited password information in these files, the vast majority of data appears to be names and email addresses organized into different mailing lists and marketing campaigns.
The data also includes information such as party affiliation, gender, donation amounts, job titles, social media handles, data detailing political views of individuals (such as “Pro-Life” and “Pro-Guns”), and even what appears to be sales notes from call center employees.
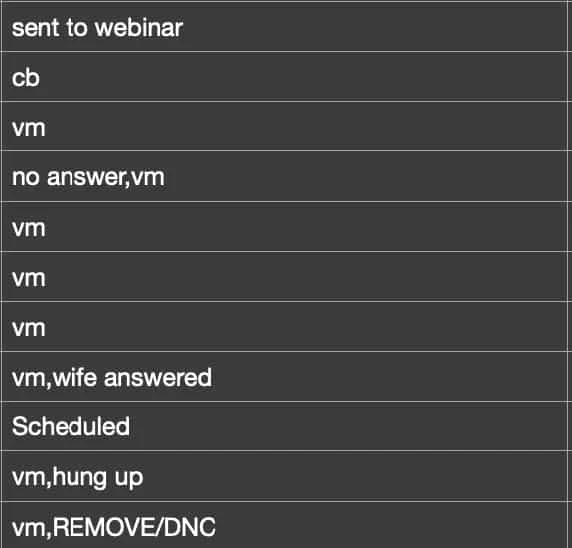
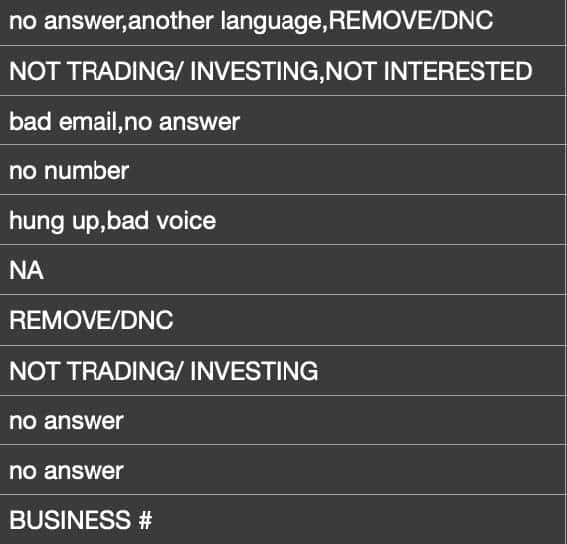
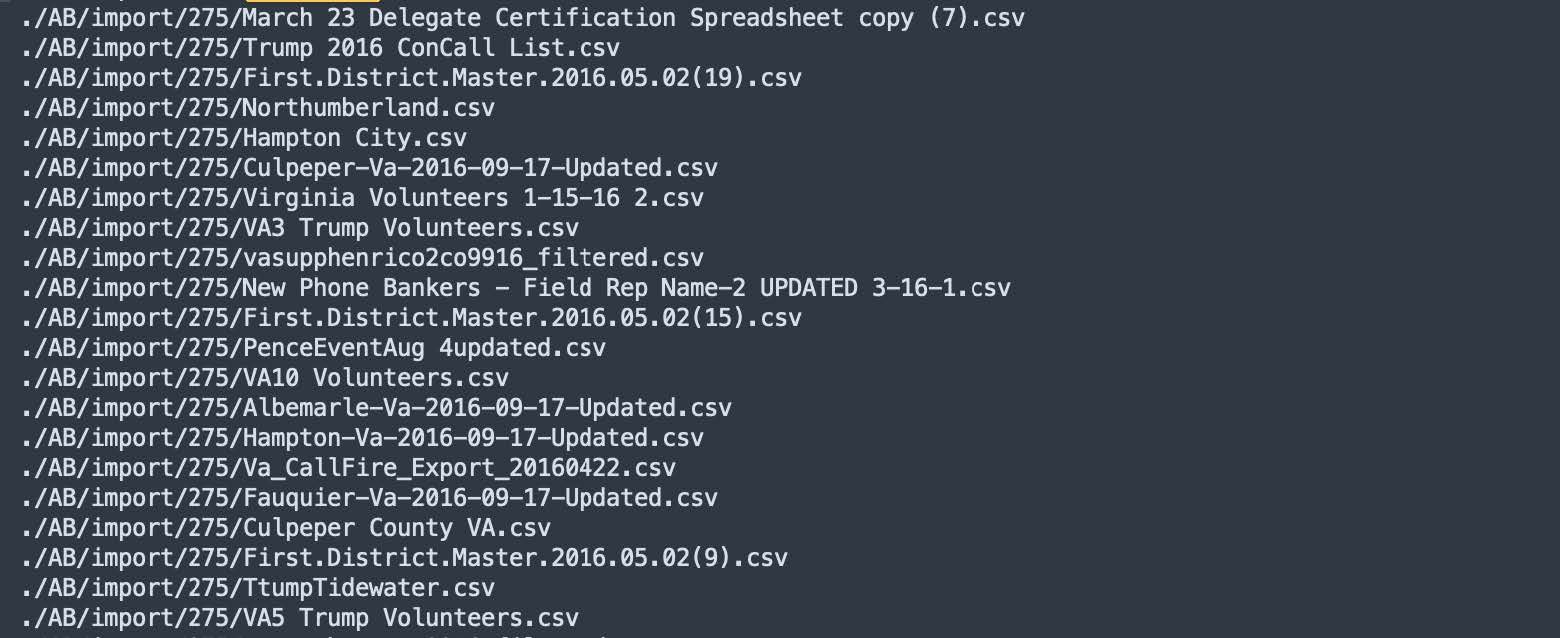
This mailing lists data consists of over 7,900 differently formatted files, making it much more challenging to parse than the other databases. Some of the files have particularly detailed filenames referring to things such as signatories to political petitions, political candidate supporters, election phone bank volunteers, and political donors for different causes.
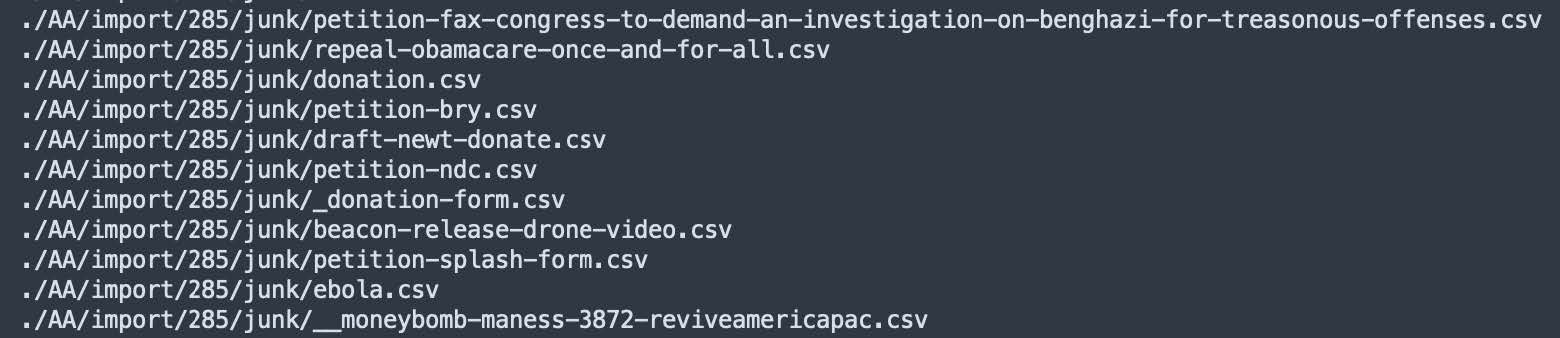
Filenames from the ‘Mailing Lists’ database showing signatories to political petitions and political donors.
Additionally, the database contains files that appear to be associated with other media outlets including what appears to be data related to the Washington Examiner, the Epoch Times, the Weekly Standard, and the National Review.
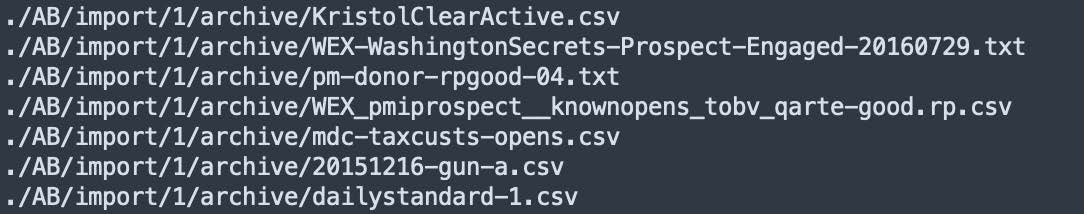
Filenames from the ‘Mailing Lists’ database showing references to other media outlets.
This rich, qualitative data about individuals – such as their political party affiliation, political viewpoints, industry of employment, net worth, and social media presence – makes it easier for threat actors to craft effective targeted phishing campaigns.
Individuals who had their emails exposed in this breach should be on the lookout for any targeted phishing attempts that appeal to specific political viewpoints or reference media outlets.
Comprehensive summary of data exposed in The Post Millennial data breach
In total, SpyCloud Labs ingested 87,797,094 records containing 332,205,826 data assets across 44 different data asset types from The Post Millennial breach, which are broken out in the table below.
Many data breaches, as is true with this breach, contain significantly more data than just email addresses and passwords, and SpyCloud parses and normalizes a wide variety of data asset types from every single breach that we collect. With dozens or hundreds of data types to pull from, cybercriminals can piece together digital user identities to carry out a range of successful follow-on attacks.
| Data Asset Type | Total Number of Assets |
| “email” | 86,936,220 |
| “first_name” | 38,305,118 |
| “last_name” | 36,155,528 |
| “country” | 4,509,334 |
| “account_last_activity_time” | 6,266,803 |
| “full_name” | 38,409,902 |
| “country_code” | 4,507,451 |
| “postal_code” | 25,311,511 |
| “phone” | 7,503,767 |
| “address_1” | 11,606,468 |
| “city”: | 17,892,299 |
| “political_affiliation” | 7,484,354 |
| “state” | 22,236,544 |
| “account_title” | 1,322,340 |
| “company_name” | 1,008,481 |
| “account_signup_time” | 4,274,367 |
| “address_2” | 175,870 |
| “ip_addresses” | 3,313,124 |
| “timezone” | 1,188,882 |
| “geolocation” | 1,246,467 |
| “job_title” | 1,578,983 |
| “gender” | 3,345,758 |
| “dob” | 346,572 |
| “age” | 1,981,041 |
| “voter_id” | 537,633 |
| “birth_year” | 346,572 |
| “middle_name” | 180,177 |
| “county” | 776,411 |
| “username” | 141,238 |
| “user_agent” | 593,959 |
| “net_worth” | 43,417 |
| “homepage” | 503,986 |
| “account_notes” | 767,524 |
| “social_twitter” | 357,641 |
| “social_linkedin” | 309,243 |
| “social_facebook” | 24,406 |
| “fax” | 70,771 |
| “company_address” | 7,633 |
| “password” | 39,502 |
| “account_nickname” | 39,733 |
| “account_image_url” | 39,806 |
| “api_token” | 5 |
| “industry” | 268,586 |
| “social_skype” | 250,399 |
Table showing the total number of data assets that SpyCloud ingested from The Post Millennial breach.
Recommendations to minimize risk following The Post Millennial leak
As mentioned above, cybercriminals may attempt to leverage stolen data from this breach to target individuals in account takeover attacks, phishing campaigns, and other scams. Our team has ingested this breach into our existing data repository of 560+ billion assets so it’s accessible by SpyCloud customers and can be used to remediate exposure risk. If you’re a SpyCloud customer, please reach out to your customer success manager with questions.
If you aren’t yet a SpyCloud customer, you can use our free tool to check your domain’s exposure to this and other recent leaks, as well as your personalized risk stemming from malware infections.



