Enterprise fraud teams and CISOs face increasing threats as criminals shift to new platforms where stolen data is shared more openly than ever. Threads, Meta’s Twitter/X competitor, has quickly become a new haven for cybercriminals looking to buy, sell, and distribute stolen credit card information – creating serious implications for businesses trying to prevent financial fraud and downstream identity abuse.
In what may be correlated to the increased scrutiny of Telegram following Pavel Durov’s arrest, SpyCloud security researchers have observed and documented several instances of newly created Meta Threads accounts posting full stolen credit card numbers and other sensitive personally identifiable information (PII).
Starting on September 12, 2024, SpyCloud security researchers noticed new accounts – some with upwards of over 12,000 followers – posting credit card details and even photos of physical credit cards and debit cards.
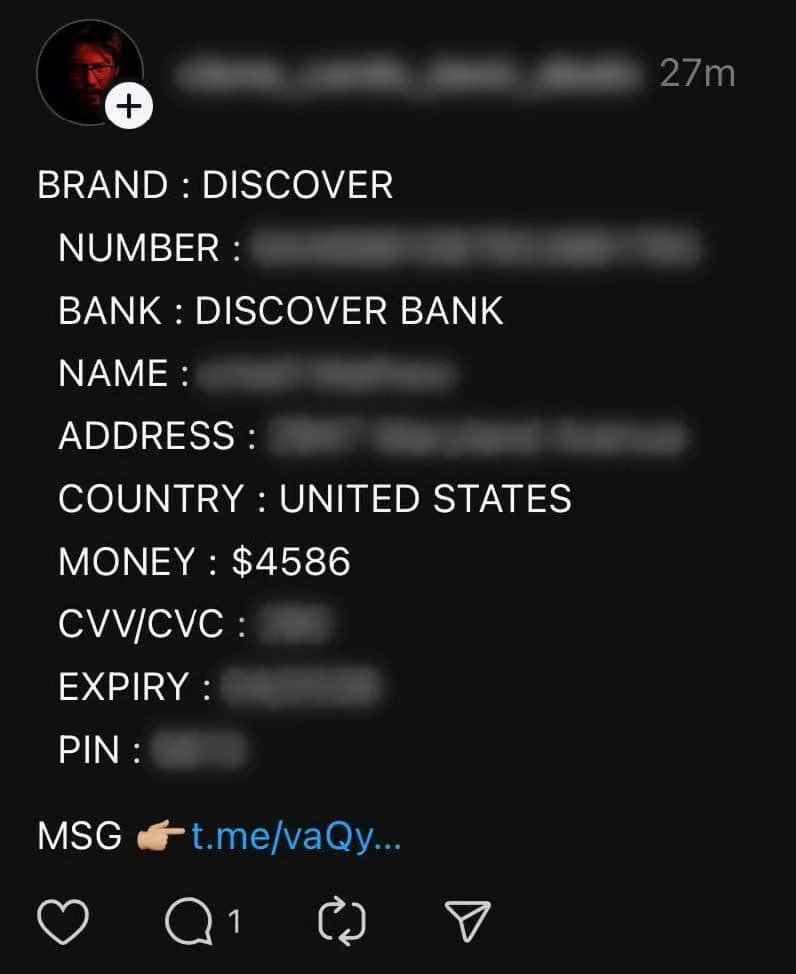
Threads post containing detailed financial card information, including what appears to be an account balance or credit limit.
Many of the observed posts contain sufficient data for bad actors to use to commit financial fraud as well as other targeted attacks (also known as “fullz”), including:
| Cardholder full names |
| Full and partial credit card numbers |
| SSNs |
| CVVs |
| Bin numbers |
| Pin numbers |
| Addresses |
| Associated bank name and/or credit card lender name |
| Credit card amounts |
| Expiration dates |
| IP addresses |
| Birth dates |
| Phone numbers |
| Email addresses |
| Passwords |
Analysis of how Threads became a new marketplace for stolen financial data
You may be wondering why threat actors would post full credit card details for free, but it’s actually a fairly common criminal advertising tactic.
In most cases, actors post the details of a limited number of stolen cards as a way to advertise that they have a larger and constant stream of fresh cards available for purchase. A prospective customer of their illicit wares might test the most recent cards they posted, see that the cards are valid, and contact them to buy more premium offerings like subscriptions to feeds of stolen payment data.
In some cases, we observed sample “fullz” posted on Threads with a critical piece of information (such as the CVV) omitted to drive interested parties to a website, Telegram channel, or direct messages on another platform. There are also scammers that advertise using stolen cards recycled from other sources, entice people to buy a fake premium offering, take their money, and then never deliver any additional data.
Breakdown of the Threads features being leveraged by cybercriminals
Threads is a feature-rich platform, and threat actors are clearly using Threads’ features and functionality, including taking advantage of suggested content, polls, and trending social tags to promote stolen financial data.
-
Recommended content: SpyCloud researchers initially came across these findings after being served suggested content with credit card data via their Threads feed. After clicking the post, Threads then recommended many other posts from accounts advertising stolen credit card data.
Additionally, we’ve observed anecdotes of other individuals stumbling upon this same scenario without seeking it out – and even (as you can see in the screenshot on this Reddit post) – being served the suggested content on Instagram without even accessing the Threads platform.
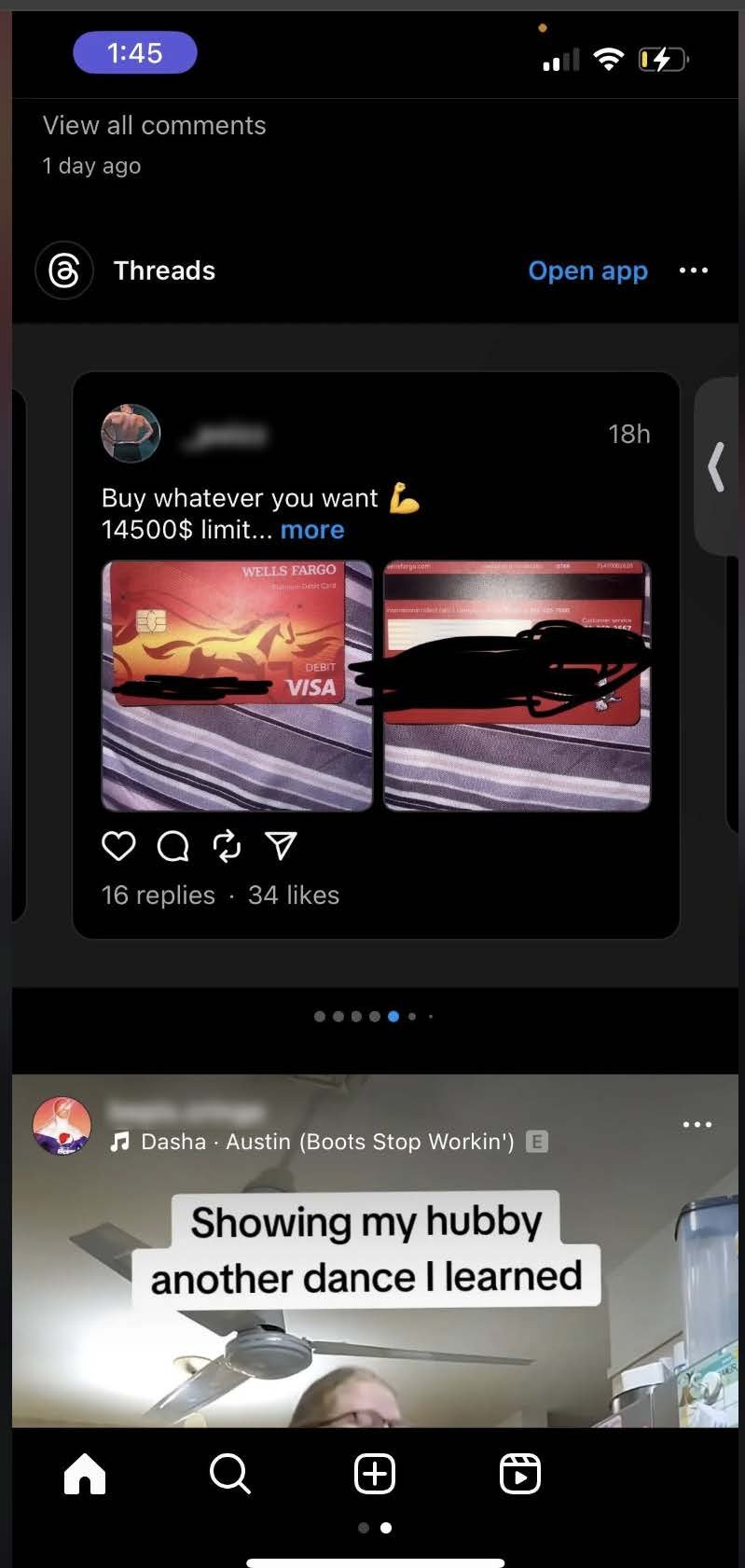
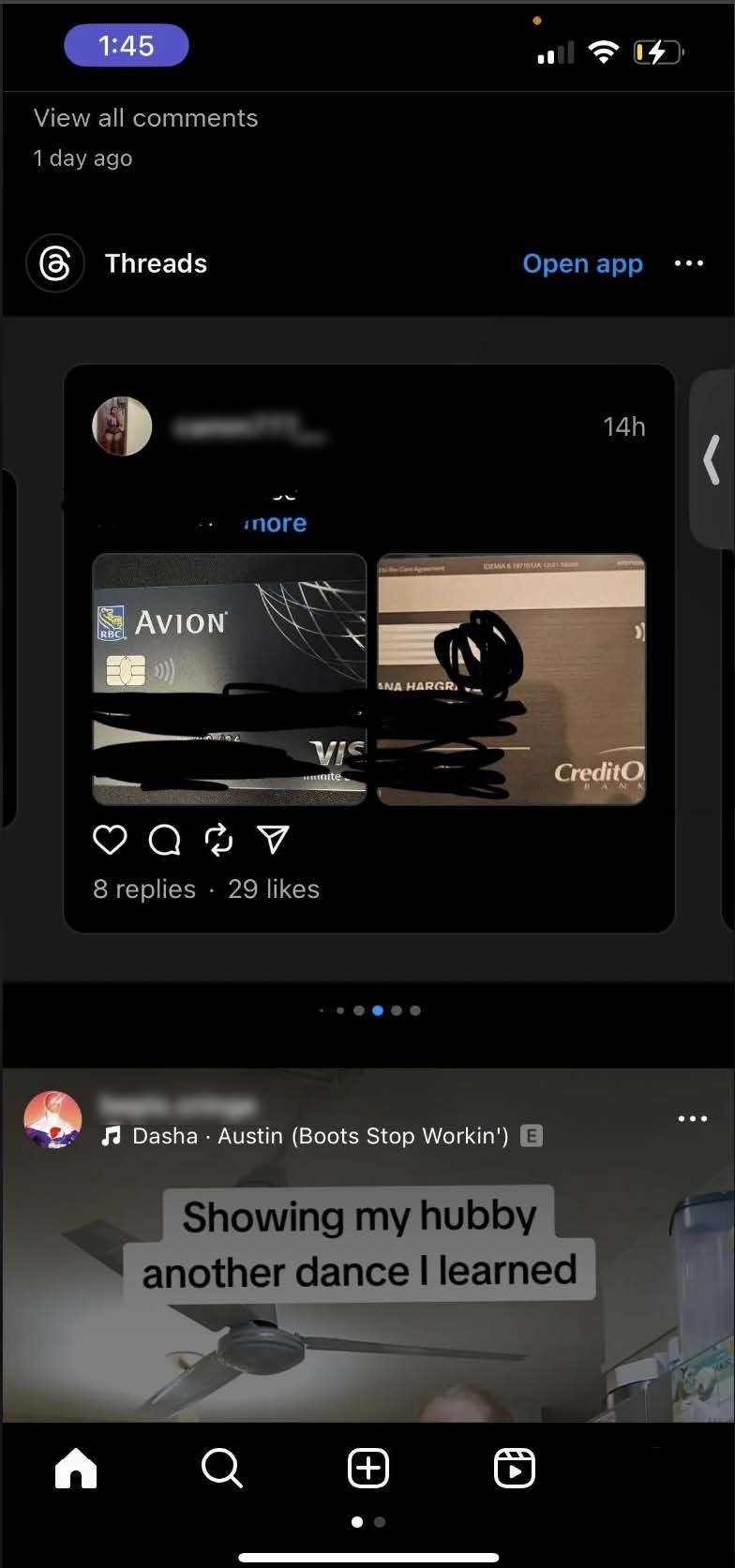
-
Polls: SpyCloud researchers found posts using the Threads’ poll feature in what looks like an attempt to drive engagement with the post, as well as to crowdsource verification of whether or not posted credit card details are valid.
In one example, an actor posted the details of a stolen credit card along with two poll options, giving other users the opportunity to provide feedback on whether or not the card details worked for them. Engagement with the poll likely also boosted the post’s visibility to other users, and at the time of observation, the poll had over 400 responses.

Screenshot of a Threads post containing stolen card information along with a poll prompting users to select whether the associated debit card details worked for them, with the options “Worked fine” for a successful transaction or account opening or “Declined | Post more” for failed transactions.
- Trending tags: Additionally, we have observed some threat actors tagging posts with “fyp”, which stands for “For You Page,” This tag is more heavily used on TikTok, where the fyp originated, but Instagram and Threads now also have similar “for you” features. If you search this tag on Threads, several posts with financial card information show up in the search results.

Screenshot of a post with stolen credit card information that contains “fyp,” an abbreviation of “For You Page.”
At the time of this writing, stolen credit card data and other sensitive PII found in these posts appear to not only exist on the Threads platform, but unfortunately appear to be heavily promoted by the Threads algorithm in some cases. We also found additional anecdotes on Reddit (here and here) where people had similar experiences creating brand new Threads accounts and finding recommended posts with stolen card information as the first thing that popped up in their feeds.
Timing and Telegram’s crackdown
Many of the Threads accounts we discovered have creation dates in late September and early October, but already have large followings. One particularly large account that we are tracking has 12.4K followers; the account’s bio contains a link back to a Telegram channel with an even larger number of members. This Threads account was created on September 28, five days after Pavel Durov’s post stating that his team had “made Telegram Search much safer” by removing content from users trying to “sell illegal goods.”
We can’t prove a direct correlation between this activity on Threads and the increased content moderation on Telegram following Pavel Durov’s arrest by French authorities in August. However, it is certainly interesting that we stumbled upon this activity on Threads in September, right around the time of Durov’s announcements that they would be increasing Telegram’s content moderation efforts and cooperation with law enforcement requests.
Notable Telegram moderation trends
We actively monitor Telegram and were able to independently confirm what appears to be increased content moderation in the form of removing or deactivating channels used to discuss fraud and cybercrime.
On October 31, we observed the deactivation rate of channels we actively track – measured as the number of channels deactivated on a single day as a proportion of all channels that have been deactivated year to date – rise to approximately 20%, indicating that substantially more channels were removed on that day than on previous days. A review of the channels deactivated on this date revealed that the overwhelming majority involved the distribution or discussion of infostealer malware logs.
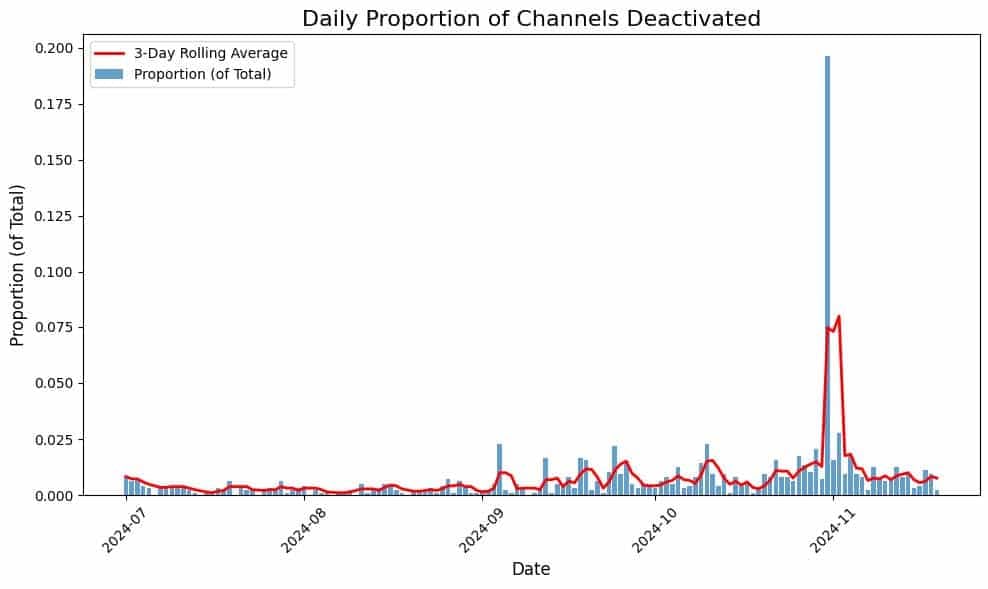
Telegram began cracking down on illicit channels in September of 2024, with a significant spike in channel deactivations occurring on Halloween. This chart shows the proportion of channels deactivated by day, measured based on the total number of channels deactivated year-to-date.
While we have seen an increase in deactivations of Telegram channels discussing illicit topics, the vast majority of channels discussing fraud, scams, malware, hacking, and cybercrime that we track continue to exist on the platform.
However, we have also noticed that some search terms related to these topics appear to be shadow-banned by Telegram. Users now need an exact channel name or link to surface some of these channels, instead of being able to search key fraud-related terms and return all of the public channels with those terms in their names and descriptions.
Some of the accounts we found on Threads appear to be linking back to Telegram channels in their posts or account bios. This is likely a strategy to circumvent the apparent shadow ban on specific search terms that is preventing potential customers from finding their channels using Telegram search.
This concerted content moderation effort by Telegram to remove channels and search terms related to criminal activity, together with newly observed stolen credit card posts on Threads, could indicate a larger trend of criminals navigating to other platforms to advertise or obtain stolen data.
Recommendations for how to combat stolen financial data
Our team at SpyCloud Labs will continue to actively monitor Threads for posts containing sensitive stolen financial data and other PII.
As we observe posts about stolen information shifting from Telegram to other more public-facing platforms like Threads, there is also the potential for more people to interact with and become interested in scams and financial fraud. Criminals are abusing mainstream social media applications to advertise stolen data, in this case by brazenly posting full stolen credit card data to the Threads app.
To stay protected from the risks posed by stolen financial data, we recommend:
Organizations:
The risk exposed consumer data poses for your business can impact your organization’s bottom line just as much as if the threat were to come from inside the house via an exposed employee or vendor. It’s imperative you have visibility into the stolen data being used to potentially create fraudulent accounts or transactions.
- SpyCloud’s Consumer Risk Protection solution helps you identify your customers’ darknet exposures and stop high-risk attacks like account takeover.
- SpyCloud’s Compromised Credit Card API lets your business query its own BIN(s) to proactively scan issued cards for dark web compromise, so you can remediate exposures before criminals can act.
- You can also enter your company’s domain into SpyCloud’s Check Your Exposure tool and get a free report on the company and consumer risk for your organization.
The more you know about what criminals know about your employees and customers, the better you can prepare for and prevent costly cyberattacks like account takeover and fraud from occurring.
Individuals
If you are concerned about whether you have exposed financial or other identity data circulating on the dark web visit checkyourexposure.com. Enter your email(s) to receive a free exposure report detailing what information criminals have in hand and learn what you can do to protect yourself.
Check for exposed customer data
Identify exposed customer data that could be putting your business at risk.