We have plenty to cover in this edition of our cybercrime update, so refill your coffee and settle in as we recap some of the top news as well as our own research findings from the month, including:
- What we found when we looked closer at LummaC2’s collaboration with the GhostSocks residential proxy
- How malware infection logs can be used to identify fraudulent North Korean IT workers
- Cybercriminal arrests and indictments
- Why you and everyone you know is getting smishing texts about toll roads and missing packages
TL;DR of new SpyCloud Labs research
In our ongoing research into LummaC2, we came across a collaboration between the stealer family and GhostSocks, a residential proxy plugin. The collab gives bad actors a backconnect proxy into their infected victim’s machines – which is pretty much as bad as it sounds. We dug deeper to untangle what GhostSocks is capable of doing from an infected device. See what we found.
Cybercriminals are humans too, which means they’re also subject to being victimized by infostealer malware. In the case of the highly publicized North Korean hiring fraud scams, our team was able to analyze malware infection logs from infected fraudulent workers’ workstations to uncover some of their TTPs and identify organizations they have targeted with their scheme. Dig in with us.
Major cybercrime events this month
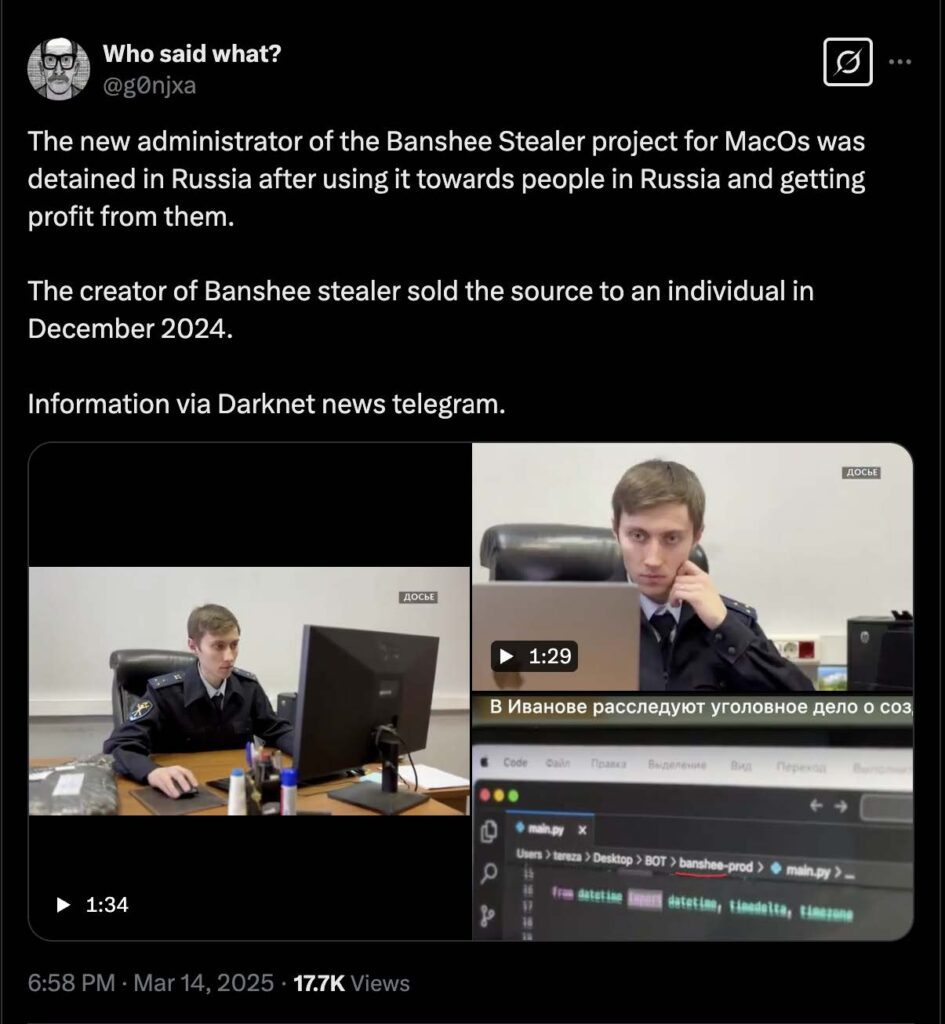
Russian cybercriminal connected to Banshee infostealer arrested
Researchers have identified a man arrested by Russian law enforcement earlier this month for targeting Russian citizens with computer crimes as an administrator of the Banshee infostealer. Independent security researcher g0njxa reposted a Russian news video that showed a Russian Ministry of Internal Affairs (MVD) officer describing their arrest of a hacker suspected of crimes including targeting Russian residents with malware to steal their data and infecting routers to use as proxies for web traffic.
In the video, the officer states that they seized the individual’s computer, and B-roll footage depicts the officer scrolling through banshee-prod source code on his computer. In the video clips of the code, the officer appears to be looking at code written in Python within a banshee-prod folder. The visible snippets of the code appear to be related to creating, editing, and querying a database and administering a Telegram bot (including loading a TG_TOKEN config and loading bot-related modules like bot.database.database and bot.database.structure).
As many cybercrime researchers have noted in the past, Russia generally turns a blind eye to cybercriminals operating within their borders under the norm that those criminals do not target any domestic victims. Criminal malware often includes hardcoded functions to avoid installing or executing malicious functionality on computers in Russia and post-Soviet countries by checking for certain keyboard languages. However, when cybercriminals break these norms, Russian authorities will enforce computer crime laws.
Banshee is an infostealer that targets MacOS devices. It is designed to exfiltrate passwords, cookies, autofill data, and cryptocurrency wallets while evading detection. There is a historical misconception that criminal malware only targets Windows devices, but malware targeting MacOS is increasingly prevalent. As Apple devices steadily capture more market share with individuals and within corporate environments, macOS malware like Banshee becomes progressively more worthwhile for criminals to create and deploy.
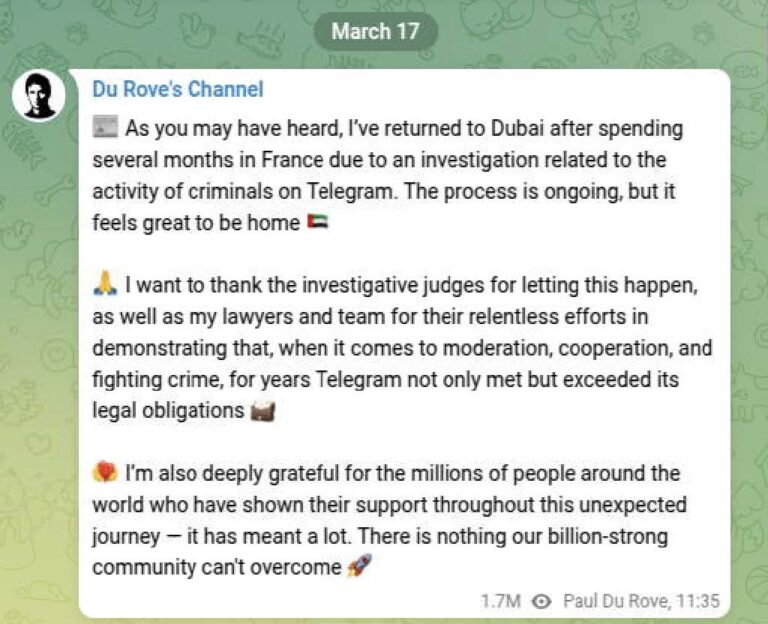
Telegram’s Durov back in Dubai
Bloomberg News reported that French authorities had temporarily suspended their mandate that Durov remain in France between March 15 and April 7, 2025, allowing Durov to leave the country.
Last Fall, after Durov’s initial arrest, he made claims that Telegram would be amping up their content moderation efforts. While SpyCloud did observe an initial increase in enforcement actions after this announcement, we are still yet to see a migration of criminal activity off of the platform.
As we noted last December, Telegram does appear to have made some changes to their search feature, making it more difficult to search for public Telegram channels using crime-related keywords. Despite this change, Telegram still remains a central hub for discussions of cybercrime and digital fraud.
i-Soon employees indicted
On March 5, the DOJ announced their indictment of eight individuals employed by the Chinese government contracting firm i-Soon (aka Anxun) for conducting state-sponsored cyber espionage, as well as two Chinese Ministry of Public Security (MPS) officers who directed the hacking operations. The charges allege that i-Soon conducted hacking of Western targets at the direction of MPS and the Ministry of State Security (MSS). It also states that they conducted self-directed hacking operations and then attempted to sell the stolen data to various different Chinese government entities, charging “between approximately $10,000 and $75,000 for each email inbox it successfully exploited.”
In February 2024, a trove of internal documents and chat logs from i-Soon were posted to a GitHub repository, and subsequently translated and analyzed by cybersecurity researchers. The i-Soon data leak shined a light on the Chinese hacking-for-hire industry, giving an in-depth look into the day-to-day operations of one of the many Chinese private-sector hacking firms. In particular, SpyCloud Labs researchers were interested in the i-Soon employees’ discussions of criminal side-ventures selling sensitive data on the darknet. Employees discussed reselling data that they obtained through their jobs at i-Soon and building social engineering databases (SGKs), databases of stolen PII sold by Chinese cybercriminals.
Current & forthcoming cybercrime research
Gone smishing: Chinese-developed phish kits targeting users via text messages
No, it’s not just you – there’s been a sharp uptick in smishing, or text-message based phishing (literally, phishing over SMS), lately, and they are primarily being served to phone users in two flavors:
The “missing package” message:
In this lure, the phishing message masquerades as being from a postal service or shipping company. These messages state that the message recipient’s package has been delayed, held, or otherwise waylaid in transit, and the user needs to click on the link to confirm their information so that their package can be properly delivered
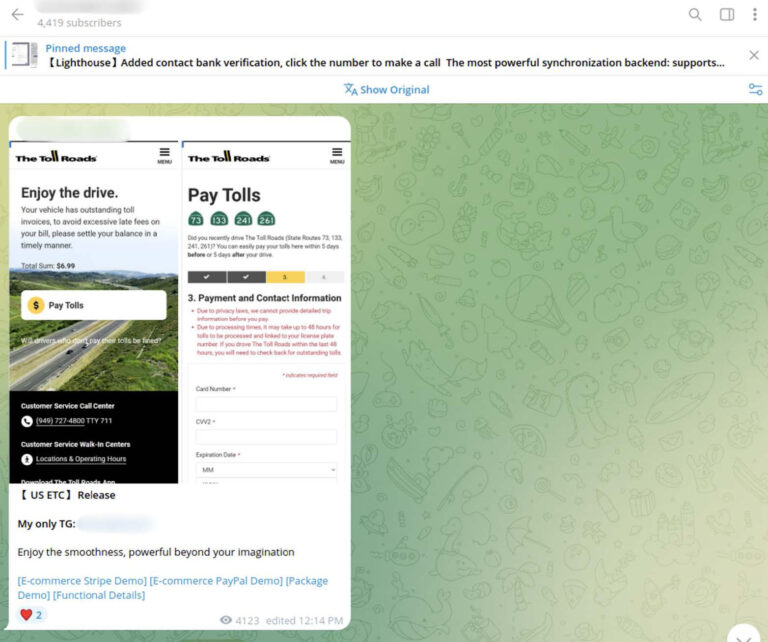
The “toll violation” message:
These phishing lures are geographically targeted, with different lures for different state and regional toll road authorities. The FBI has been publicly warning people about these toll road scams in particular, stating that they received more than 60,000 complaints reporting the unpaid toll scam in 2024.
There are likely a few different factors driving the rise in smishing, including:
- According to digital marketing data, the click through rate for links shared via text messaging is significantly higher than the click through rate for links shared via email
- Phishing-as-a-Service (PhaaS) developers have evolved their tactics to take advantage of the features of more advanced text messaging protocols like Rich Communication Services (RCS) and iMessage
- These protocols also allow phishing operators to bypass SMS spam filters
About the threat actors behind these phishing kits
Chinese-speaking PhaaS developers and phishing operators appear to be distributing sophisticated phishing kits that make it easy for phishing scam operators to send out convincing targeted smishing messages en masse (including “missing package” and “toll violation” messages), collect sensitive financial data, and cash out using stolen credit card details.
One group, that goes by XinXin (鑫鑫), operates large smishing campaigns to harvest credit card details. As Prodaft noted in a recent report on the group, XinXin appears to primarily users in the United States and United Kingdom and appears to operate large rigs of mobile phones used for bulk messaging of victims.
Another group, Lighthouse (灯塔), distributes a phishing kit with various localized fake toll violation lures. The use of iMessage and RCS also allows them to bypass traditional SMS spam filtering mechanisms.
Chinese-speaking PhaaS developers and phishing operators appear to be distributing sophisticated phishing kits that make it easy for phishing scam operators to send out convincing targeted smishing messages en masse (including “missing package” and “toll violation” messages), collect sensitive financial data, and cash out using stolen credit card details.
One group, that goes by XinXin (鑫鑫), operates large smishing campaigns to harvest credit card details. As Prodaft noted in a recent report on the group, XinXin appears to primarily users in the United States and United Kingdom and appears to operate large rigs of mobile phones used for bulk messaging of victims.
Another group, Lighthouse (灯塔), distributes a phishing kit with various localized fake toll violation lures. The use of iMessage and RCS also allows them to bypass traditional SMS spam filtering mechanisms.
How phishing operators are cashing out
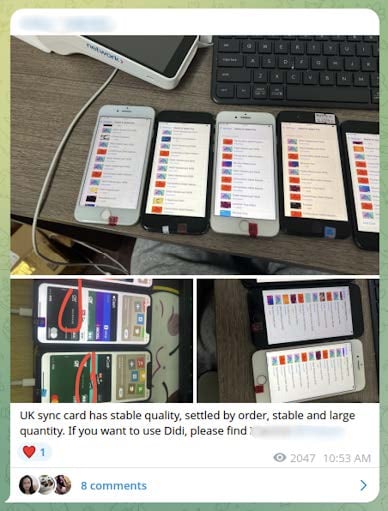
A popular cash out method for these scams is loading stolen cards into digital wallets and cashing out through NFC payments. Many of the groups involved in these scams have been observed posting photos of dozens of phones with stolen credit cards loaded into mobile wallets applications, which can be used to pay with a digital version of a credit card at point-of-sale (POS) terminals.
These screenshots hint at a popular cash-out method for these smishing campaigns, loading stolen card details into mobile wallets and using tap-to-pay payments in cash out schemes. For example, KrebsonSecurity reported that eleven Chinese nationals were arrested earlier this month in Tennessee and charged with “buying tens of thousands of dollars worth of gift cards at local retailers with mobile wallets created through online phishing scams.”
Mobile phones can be loaded with cards virtually using NFC relay applications in a method dubbed “Ghost Tap” by researchers. In other cases, criminals cash out by opening fake vendor accounts with a payment processor and cashing out by making fraudulent transactions using a physical POS terminal.
SpyCloud’s recaptured data collection numbers for March
March monthly total
Total New Recaptured Data Records for March
2,282,082,475
New third-party breach data this month
Third-Party Breaches Parsed and Ingested:
320
New Data Records from Third-Party Breaches:
1,795,104,797
New infostealer malware data this month
Stealer Logs Parsed and Ingested:
4,610,348
New Data Records from Stealer Infections:
12,275,538
New Stolen Cookie Records:
474,702,140
New stealer families added
Nova Blight: Nova Blight is a rebranding of the Nova Sentinel infostealer, a Malware-as-a-Service (MaaS) offering targeting Windows devices.
Mint Stealer: We have observed a recent surge in popularity for Mint Stealer, a Python-based infostealer with a browser-based C2 panel.
Stay in the Loop
Sign up to get the latest cybercrime research, insights, and best practices in your inbox





