Spoiler alert: If any password is exposed on the dark web, your employees and customers shouldn’t be using it.
Passwords remain a weak link in enterprise security defenses – and cybercriminals know it. From automated credential stuffing to malware that silently captures logins, attackers have built an entire economy around password-based access. And as account takeover (ATO) incidents continue to rise, organizations need more than just policies to protect themselves – they need real-time visibility into the identity threats targeting their workforce and customers.
To help organizations address these challenges, the National Institute of Standards and Technology (NIST) has updated its password guidelines in Special Publication 800-63-4, shifting toward usability without sacrificing security. Let’s break down what’s new — and how SpyCloud makes it possible to implement these recommendations at scale.
A modern approach to password security
NIST’s latest password guidance reflects a simple truth: complexity doesn’t equal security. Long gone are the days of requiring uppercase-lowercase-symbol combos that lead to predictable password variations (like “Summer2025!”). Instead, NIST recommends:
- Longer passwords (15+ characters) over complexity
- No required character mixing or password hints
- Eliminating routine password expiration
- Screening passwords against blocklists of commonly used or compromised credentials
- Supporting multifactor authentication (MFA) with appropriate secondary factors
Critically, NIST calls for organizations to prevent the use of known-exposed passwords, including those from data breaches, malware infections, and successful phishing attacks.
The problem: Most enterprises can’t keep up with password exposures
Password exposures happen constantly. In the past year alone, SpyCloud recaptured over 3.1 billion passwords from the criminal underground. And our research shows that 70% of users reuse passwords, often across both personal and corporate accounts.
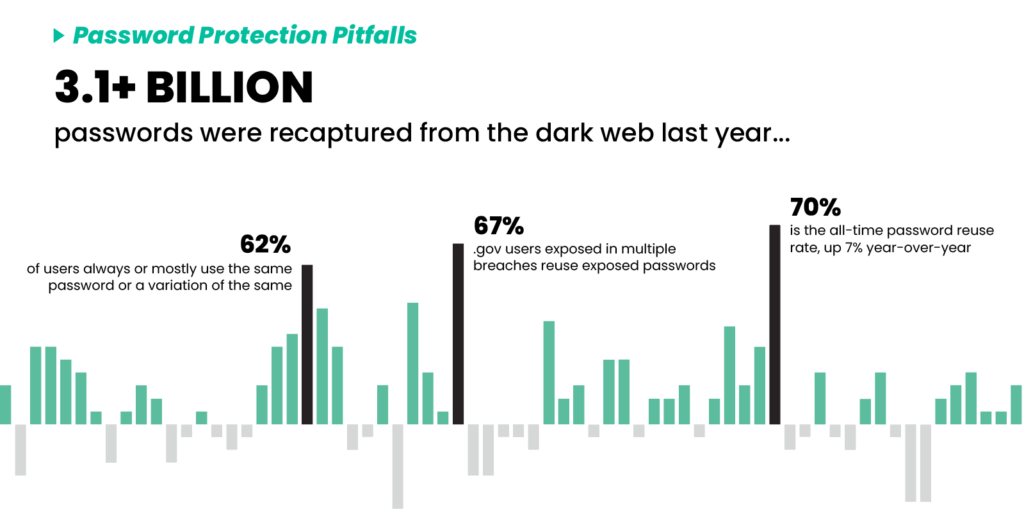
Even with MFA and SSO in place, just one exposed password can enable lateral movement, business email compromise, or worse. Manual checks against breach lists and third-party tools aren’t enough — especially when exposures can happen at any time, from any source.
The solution for employee password protection: Automated remediation with SpyCloud Active Directory Guardian
SpyCloud’s Active Directory Guardian makes NIST password compliance easy – and scalable – by preventing weak password creation and automatically remediating exposed ones.
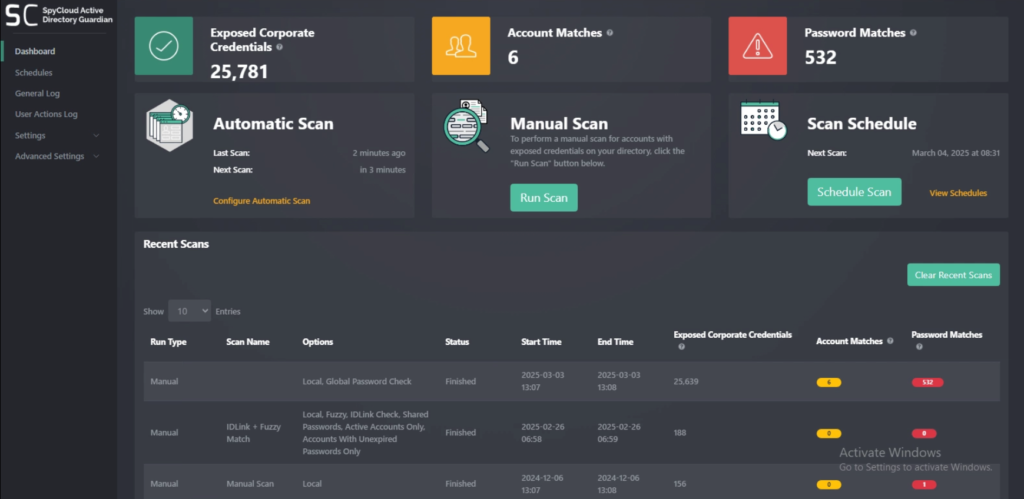
Here’s what it does:
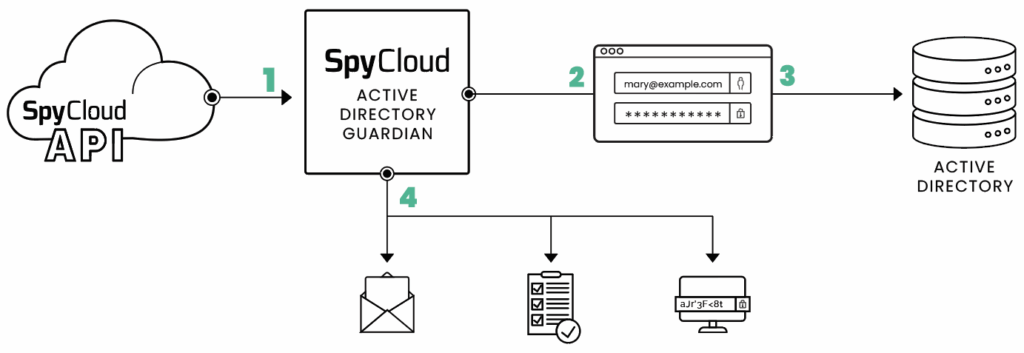
Block weak and exposed passwords at the source
Active Directory Guardian prevents employees from selecting passwords that are too short, too simple, or found in breach datasets. Every time a password is created or changed, Active Directory Guardian checks it against the largest repository of recaptured identity data – more than 30 billion credentials and counting.
Monitor continuously
Active Directory Guardian scans for exposed passwords around the clock, comparing Active Directory credentials to recaptured data from the criminal underground. Whether it’s a reused password from an old account or a personal password tied to a professional email, we find it.
Automate remediation
If a password is exposed, Active Directory Guardian can automatically reset it – within five minutes of discovery – or notify admins to take action. No more waiting for third-party alerts or sifting through dark web monitoring reports.
Provide executive-level reporting
Gain insights into your organization’s password hygiene with detailed reports that show password reuse trends, remediation metrics, and the impact of your policies over time.
The solution for consumer account protection: SpyCloud Password Exposure API
SpyCloud also addresses password hygiene for consumer accounts. SpyCloud Password Exposure API reduces the risk of account takeover attacks by checking for credential exposures at account creation, login, or overnight for quick remediation – mitigating potential financial losses for both the customer and your organization.
By implementing SpyCloud’s API into existing workflows, when users create new passwords, you can check them against SpyCloud’s entire database to find out if the new password has ever been exposed before. To securely check password-only matches, SpyCloud’s Password Exposure API uses k-anonymity to send only the first five characters of each password hash over the network — never the user’s plaintext password.
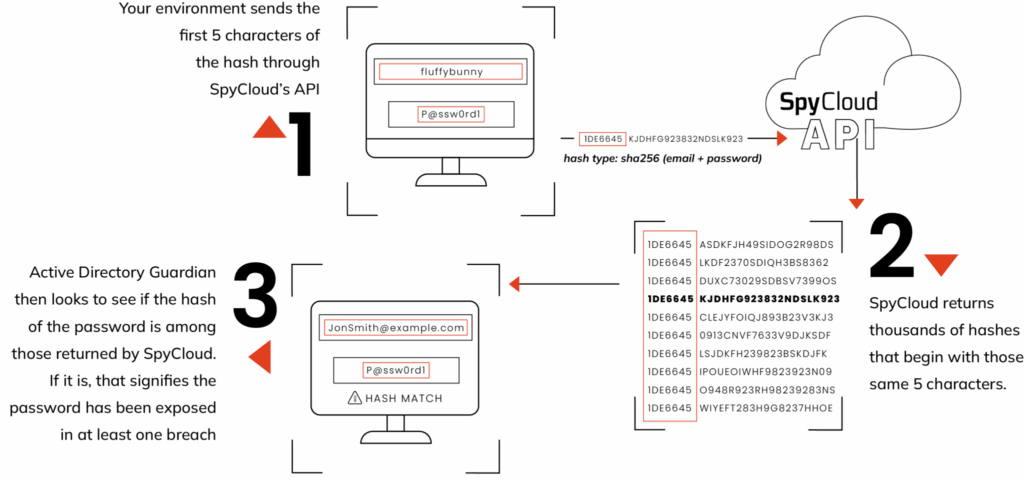
SpyCloud can also alert you when credentials tied to your consumers appear in a new data breach, malware-infected device, or successful phishing attack, enabling you to reset passwords or choose an appropriate step-up authentication path for affected users without adding unnecessary friction.
By addressing vulnerable accounts early, you can protect your consumers from hard-to-detect targeted attacks that occur early in the breach timeline.
Final thoughts: If it’s exposed, it’s off limits
The latest NIST password guidelines reinforce what security leaders have long suspected: outdated password policies aren’t keeping up with today’s threats. If a password has been exposed – even just once – it’s compromised. Full stop.
SpyCloud gives you the tools to act decisively. With continuous detection and automated remediation, you can shut down the use of stolen passwords and stop identity-based threats before they escalate.
Want to see how exposed your organization really is?
Try our free darknet exposure check or request a demo of SpyCloud Active Directory Guardian.
Additional information
Here are key NIST resources to reference and incorporate into your cybersecurity strategy:
- NIST Digital Identity Guidelines
- SP 800-63A: Digital Identity Guidelines – Enrollment and Identity Proofing
- NIST SP 800-63B: Digital Identity Guidelines – Authentication and Lifecycle Management
- SP 800-63C: Digital Identity Guidelines – Federation and Assertion
Regularly revisiting these materials is important for compliance, and gives you a leg up to fortify your defenses. Establish a routine for policy reviews and updates in line with NIST’s evolving recommendations to maintain alignment with best practices and stay prepared for emerging threats.



