Ransomware attacks begin in the criminal underground, where an expansive cybercrime enablement infrastructure arms both aspiring and seasoned cybercriminals with tools to wreak havoc and inflict damage.
With infostealers and other tools in hand, bad actors can quickly gain momentum and launch any number of cyberattacks – with ransomware as an often desirable choice.
The same underground ecosystem that enables malware and ransomware cybercrimes creates endless challenges for defenders across all industries.
In line with our mission to disrupt cybercrime, each year, SpyCloud surveys teams on the frontlines and combines their responses with our own research and analytics to bring you new insights about malware and ransomware trends. So without further ado, let’s recap our findings from the 2024 SpyCloud Malware and Ransomware Defense Report.
Cybercrime trends that are setting the scene
We start our journey with two major trends that have converged over the past 18 months, and which are playing a large role in shaping the landscape we find ourselves in today:
- Cybercriminals shifted to next-generation tactics, using data exfiltrated by information-stealing malware (infostealers) to gain initial access for follow-on attacks like ransomware, and
- Ransomware saw a resurgence as a frequent and damaging attack method
Against this backdrop, this year’s report shows that security teams are doubling-down and looking for ways to boost their defenses. The good news is that they are recognizing that identity-related threats fueled by malware infections create a high risk of ransomware attacks. And they’re starting to embrace next-generation mitigation strategies.
About this year’s malware and ransomware survey
For the fourth consecutive year, we surveyed security leaders and practitioners about the state of malware and ransomware in their organizations. More than 500 individuals – from security analysts and engineers to CISOs – shared their perspective. We supplemented this data with our own original research, including ransomware prediction modeling, to get a more complete understanding of what teams are facing – and what shifts may be needed.
01
KEY FINDING: Malware exposure creates universal concerns about ransomware risks
This year’s survey respondents rank ransomware as their biggest threat, and 75% report that their organization has been affected by it more than once in the past year – up from last year’s 61%.
Virtually all – 99.8% – are concerned that identity, session cookies, and other data exfiltrated from malware-infected devices may be used for ransomware and other follow-on attacks.
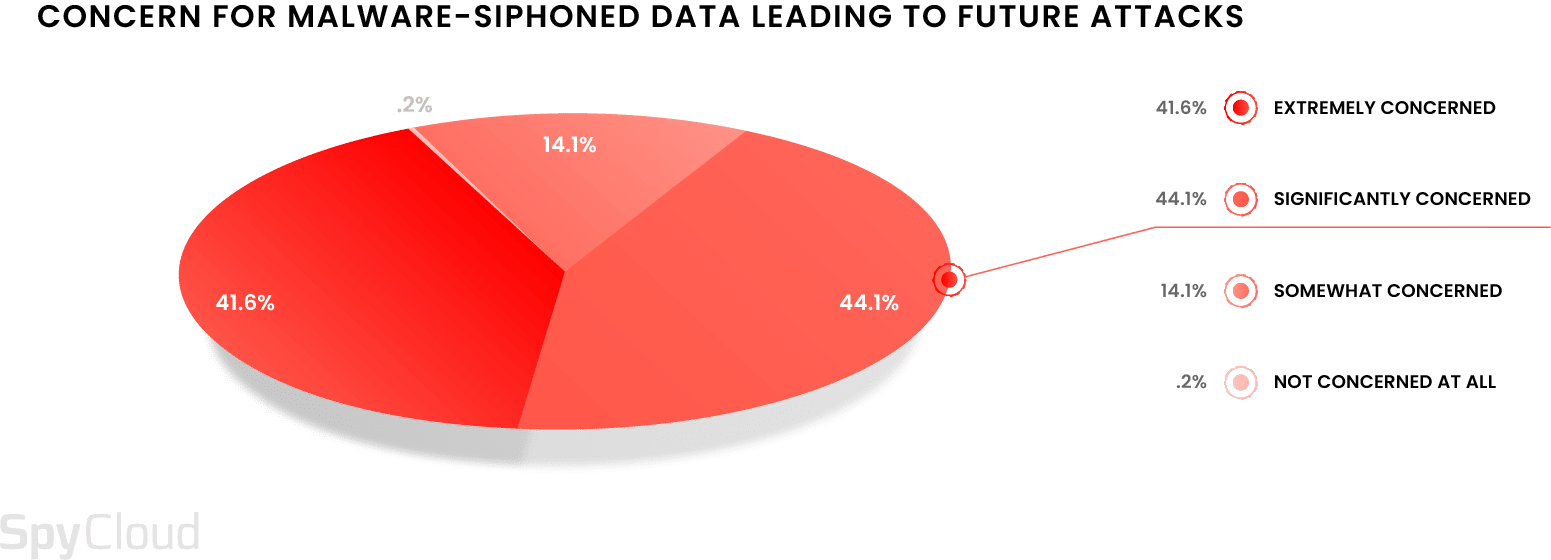
Our independent research validates these concerns. SpyCloud’s supplemental analysis of data recaptured from the criminal underground shows that:
- 61% of breaches last year were related to malware, as well as responsible for 343.78 million stolen credentials.
- Nearly a third of organizations that experienced a ransomware attack last year had at least one infostealer infection in the months leading up to the attack – indicating a correlation between infostealer malware and the likelihood of the organization experiencing a ransomware attack in the near future.
02
KEY FINDING: Perceived threats and priorities vary across industry sectors
Security professionals from each sector rank ransomware as their biggest threat and risk. But there are differences in how various sectors were affected, as well as their priorities and capabilities. Worthy of note:
- Only three sectors – manufacturing, retail, and technology – rate improved ransomware prevention capabilities among their two main priorities in the next 12 to 18 months
- Retail organizations rank their ability to identify exposed business applications as their top capability when it comes to malware response.
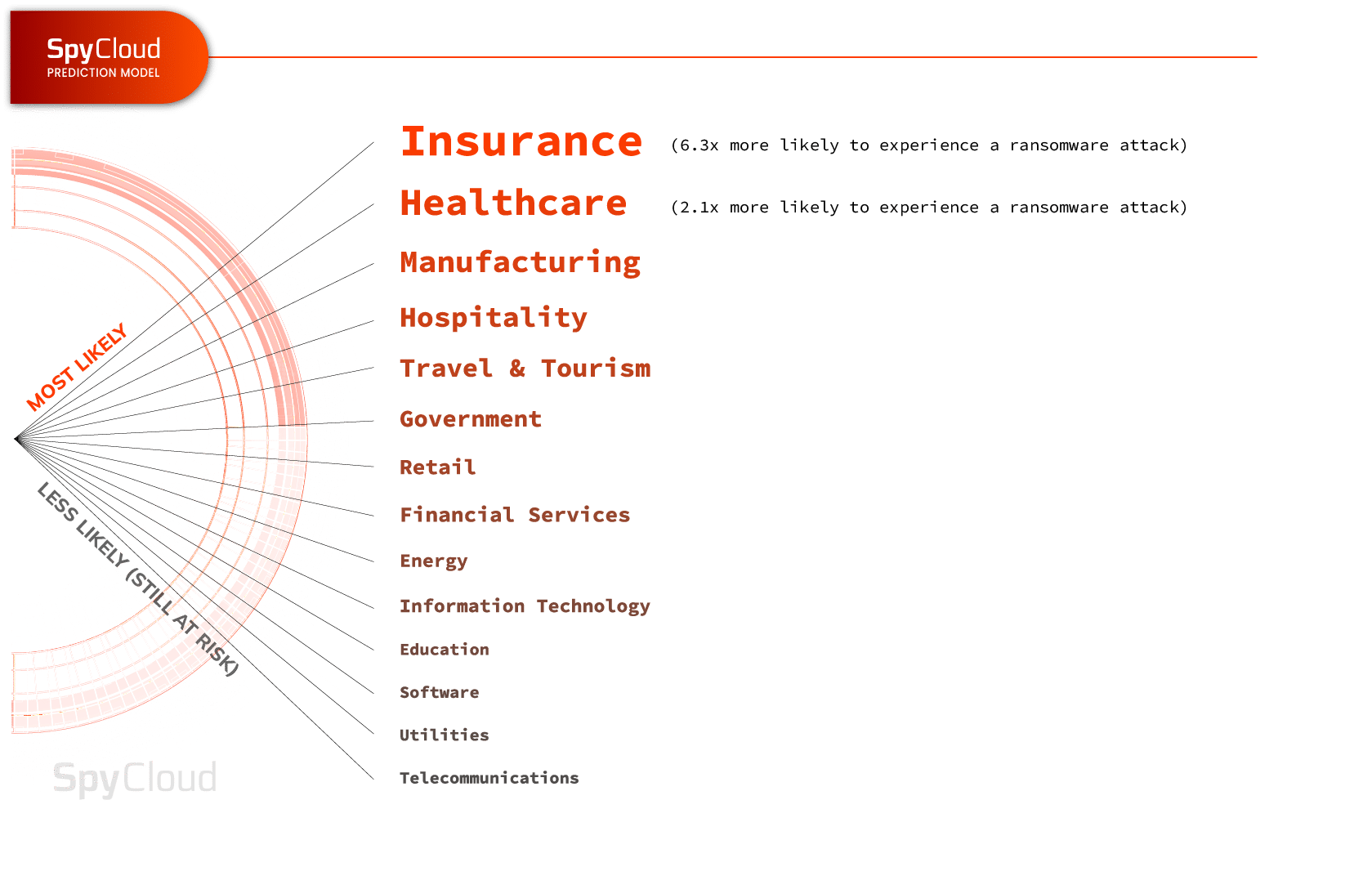
- Somewhat surprisingly, 17% of healthcare respondents reported not being affected at all by ransomware last year. But based on our prediction modeling, healthcare is one of the industries with the greatest risk of future ransomware events in 2024, being 2.1x more likely to experience a ransomware attack. The sector we found to be most at risk is insurance: this industry is 6.3x more likely to experience a ransomware attack in the remainder of the year.
03
KEY FINDING: MFA bypass via session hijacking is a prominent new attack vector
For the first time this year, we asked organizations to identify the entry points that led to initial access in attempted or successful ransomware events. Among the organizations that were affected by ransomware in the past year, stolen cookies that enabled session hijacking ranked as the third most common entry point.
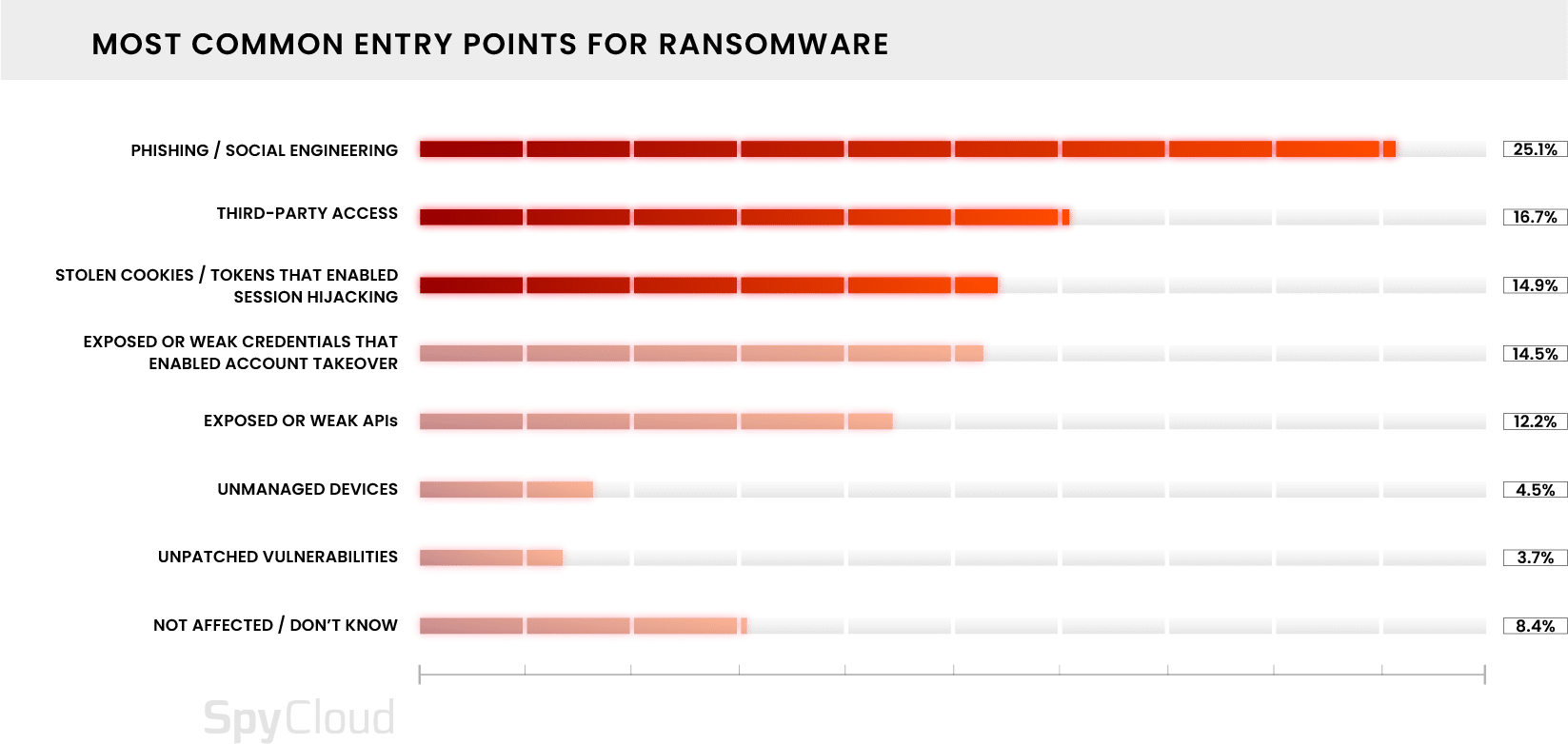
This finding emphasizes that traditional defenses such as MFA and antivirus fall short in the new era of next-generation attacks. In fact, our recent research shows that in the first six months of 2024, at least 54% of devices infected by infostealers had an antivirus or endpoint detection and response (EDR) solution in place at the time of infection.
There is some hope: security teams’ second biggest priority for the next 12-18 months is to improve visibility and remediation for compromised credentials and data siphoned by malware. As further proof of a heightened awareness about this risk, 57.5% also say they currently invalidate or terminate open session cookies in response to a malware infection on a managed device.

04
KEY FINDING: Third parties give an advantage to the adversary
SpyCloud’s recaptured data analysis shows that each malware infection exposes an average of 10 to 25 third-party business application credentials. And it appears our survey participants are feeling the pressure of this third-party exposure.
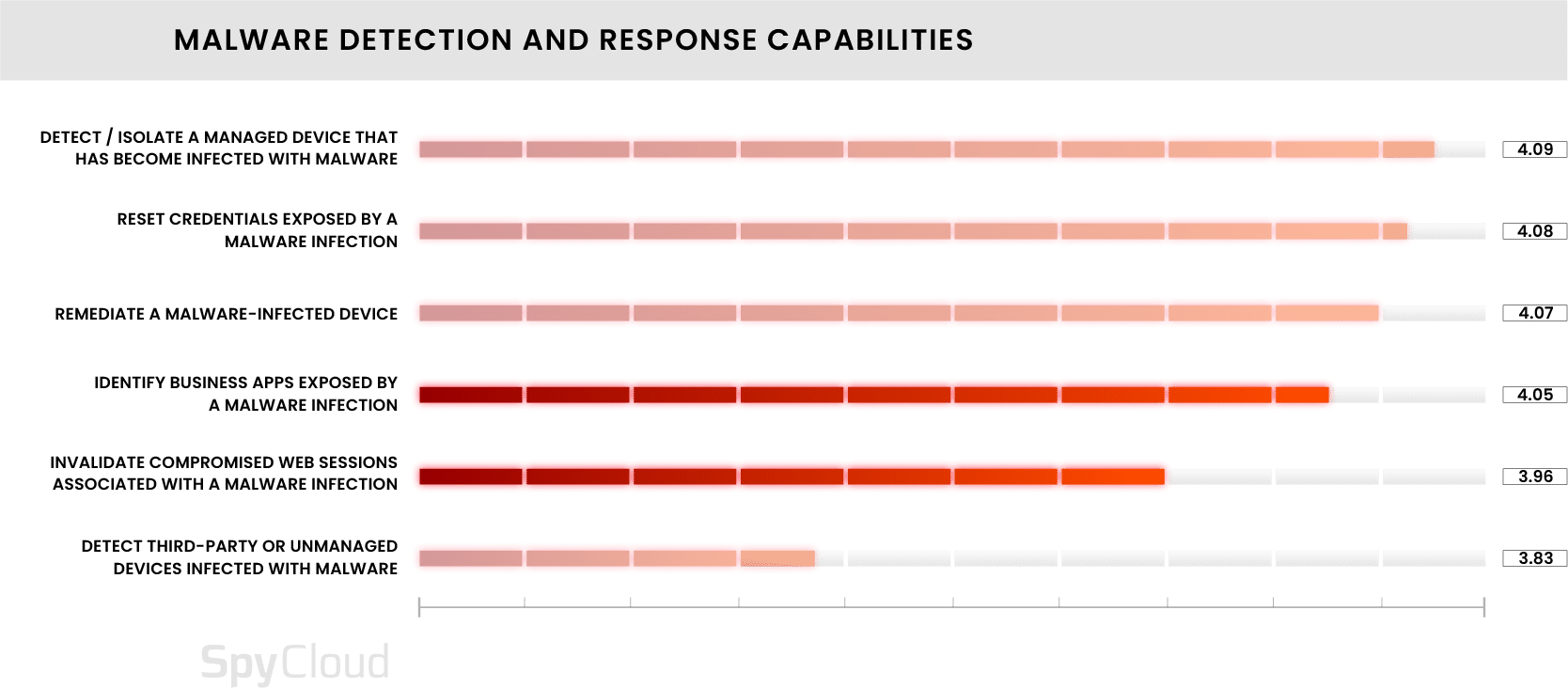
Almost 100% of those surveyed worry about the risks stemming from third-party accounts that are compromised by malware. They also rank third-party access as the second most common ransomware entry point. Yet unfortunately, teams rank their ability to detect third-party or unmanaged devices infected with malware lowest compared to other capabilities.
Identity and access management (IAM) teams are the most concerned about malware-infected users and risks from third-party exposure. This gives us hope because IAM teams are at the frontlines of protecting their organizations from identity-driven cybercrimes like account takeover and ransomware attacks.
But there’s a big gap in perceptions between IAM professionals – as well as security practitioners in general – and security leaders.
Among those surveyed, 91% of CIOS, CISOs, and IT security executives are confident about their organization’s ability to prevent a full-blown ransomware attack, compared to 71% of IAM professionals and 54% of security operators, analysts, and incident responders. There’s no better time than now for the two sides to join forces and bridge this disconnect, especially since they’re on the same team.
How to rewrite the ransomware narrative
- More teams strongly agree they need visibility into malware-exfiltrated data.
- There’s an uptick in the number of respondents reporting they proactively reset passwords for exposed applications.
- Organizations are adopting practices like resetting application credentials and invalidating compromised session cookies to prevent session hijacking.
Security teams can use the same underground data cybercriminals use to strengthen their defenses.
By gaining visibility into malware exposure across users, devices, and applications, they can implement next-generation strategies such as post-infection remediation – and start gaining the upper hand.
The fight against malware and ransomware is extremely challenging, but not unsurmountable. These recent insights tell us that organizations are paving a path to gaining higher ground. With the right resources, defenders can tip the scales – and write a better ending.



