In the last couple of weeks, two different threat actor groups presenting themselves as “furry hacktivists” have released headline-grabbing breaches.
Cybercriminals may attempt to leverage stolen data from these breaches to target individuals in account takeover attacks, phishing campaigns, and other scams.
In this blog, we’ll dive into these two notable breaches and summarize what you should know about each of them:
- SiegedSec’s data breach of The Heritage Foundation
- NullBulge’s breach of Disney’s internal Slack data
Keep reading for an analysis of each threat actor group, the breaches, and SpyCloud’s progress ingesting the stolen data to keep affected individuals and organizations safe from follow-on attacks.
About the “SiegedSec” hacker group
- NATO
- Anti-LGBTQ+ organizations in support of the LGBTQ+ community
- Israeli organizations in support of Palestine
- Idaho National Laboratory
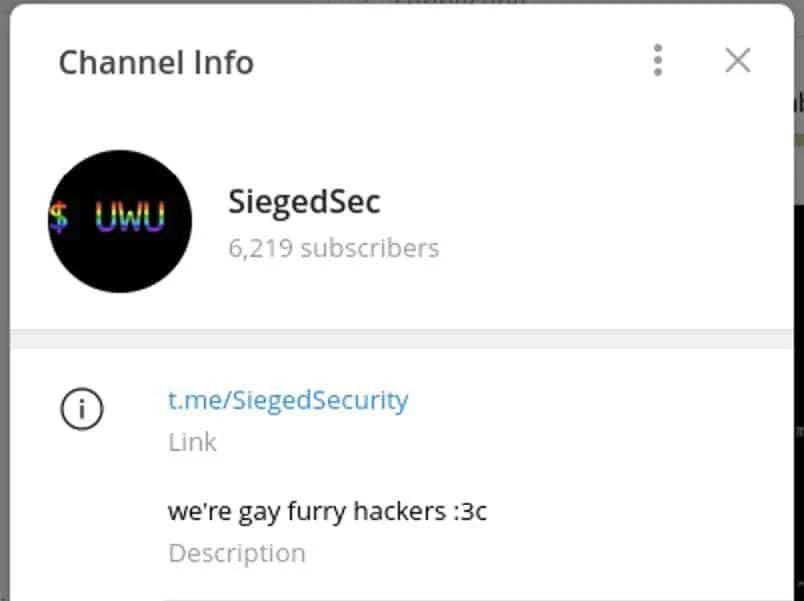
Screenshot of the channel info from SiegedSec’s Telegram Channel. The channel description states “we’re gay furry hackers :3c”

Comment by ‘Vio’ for a Reddit AMA in r/hacking
SiegedSec’s breach of The Heritage Foundation
On July 9, SiegedSec leaked data from The Heritage Foundation, a conservative think tank in the United States. In the post, they state that they were motivated to target The Heritage Foundation because their “Project 2025 threatens the rights of abortion healthcare and LGBTQ+ communities.”
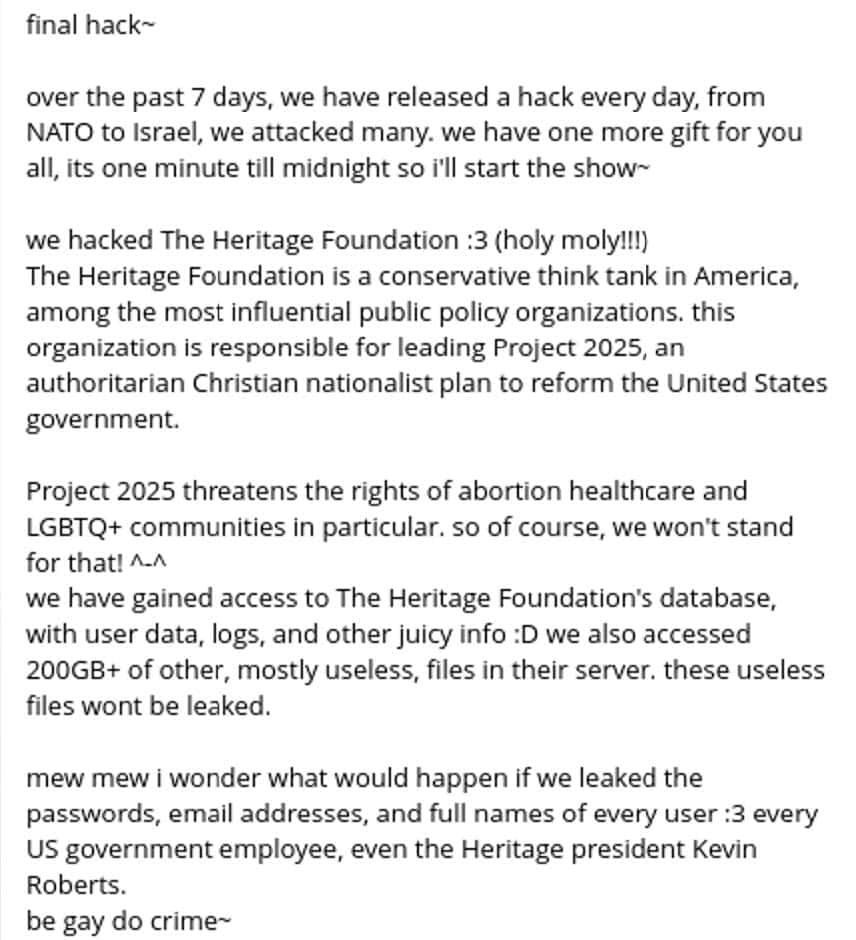
Telegram message from SiegedSec’s Telegram channel claiming that they hacked The Heritage Foundation and explaining their motivation behind leaking the data
This breach appears to be a 1.94 GB SQL dump of “The Daily Signal”, a media website that was created by The Heritage Foundation in 2014, which spun off as an independent entity in June 2024.
The leaked user data contains over 72,000 unique email addresses, including over 900 for users with heritage.org email addresses. In addition to emails, the breach contains user PII such as md5 password hashes, IP addresses, user-agent strings, twitter handles, account metadata such as account signup time, and a limited number of phone numbers and full names. SpyCloud has recaptured 669,031 records from this breach.
The day after this data was posted, SiegedSec posted that they were disbanding, citing “mental health” and a desire to “avoid the eye of the FBI” as reasons behind this decision. On July 11, The Verge published a statement from The Heritage Foundation spokesperson Noah Weinrich claiming that the leaked data was from “a two-year-old archive of The Daily Signal website that was available on a public-facing website owned by a contractor.”
About the “NullBulge” threat actor group
NullBulge is a new threat actor group that has been operating as “NullBulge” since Spring 2024. On their data leak site (DLS) they self-identify as “a hacktivist group protecting artists’ rights” next to a large image of a lion fursona.
While the group self-identifies as hacktivists and has adopted a “furry” aesthetic similarly to SiegedSec, there has been recent coverage from other groups detailing NullBulge’s financially motivated cyber crimes – including deploying ransomware payloads that appear to have been compiled from leaked copies of the leaked LockBit Black builder as well as selling infostealer logs and API keys in criminal marketplaces.

Screenshot from the homepage for NullBulge’s DLS showing their self-description as a “hacktivist group” as well as the lion fursona image that they use on their website and as a profile picture on cybercriminal forums
NullBulge’s breach of Disney’s Internal Slack data
On July 11, NullBulge posted a 1.1 TB leak of data from Disney’s internal Slack. The data appears to be a Slack workspace export, containing message history from 9,985 public and private Slack channels in JSON format as well as zip files containing files shared in those Slack channels. Overall, this data breach is structured similarly to many ransomware data breaches – it has a huge amount of files, some of which contain sensitive information, but it requires significant digging to find valuable data.
Based on timestamps in the message history files, the data appears to span the time period from October 30, 2013 until July 3, 2024. The oldest channels all appear to be Hulu-related, suggesting that they were migrated over from Hulu at some point, as Disney has only controlled Hulu since 2019. This would make Hulu one of Slack’s earliest adopters, as they announced their preview release in August 2013.
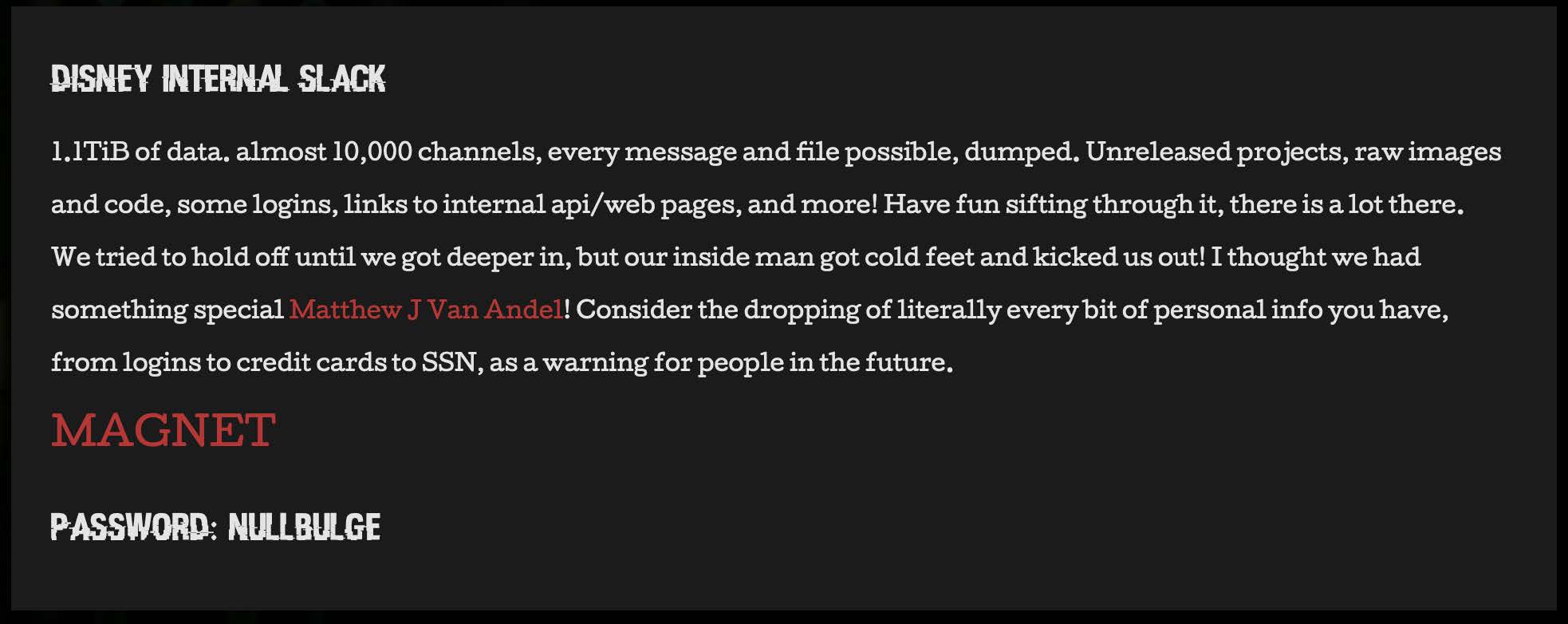
A screenshot of NullBulge’s post to their DLS entitled ‘Disney Internal Slack’
The files are named with the relevant Slack channel ID, which start with a capital C followed by a string of letters and numbers or, for private channels created before March 2021, a capital G followed by a string of letters and numbers. Within the zip files, the file attachment names all include their file ID, which start with a capital F, allowing the files to be correlated with the messages in which they were shared.
The message history files only appear to contain channel and message data. According to Slack documentation, these message history files can only be exported by Workspace Owner and Admin accounts, meaning NullBulge had to gain access to an Admin account to access the data. Messages are associated with a user ID (or bot ID) for the user (or bot) that authored the message. However, the leak does not appear to contain a file correlating those user IDs with user data like email addresses and Slack display names. Some older messages – like those in the migrated Hulu channels – have first and last names in the “username” field within the message history, but the majority of messages don’t appear alongside any meaningful user identity data.
These message history JSON files do appear to contain sensitive information and PII, but it is generally unstructured and buried within the “text” field of messages. Without the ability to tie many of the message authors’ user IDs to their human identities, this message data also loses some of its potential usefulness to threat actors. However, a portion of the vast array of file attachments shared in those Slack channels appear to contain sensitive, structured information that appears much more potentially useful.
For example, the message history file for the #peloton_riders Slack channel contains messages where Disney employees chat and share their Peloton usernames. The file attachments for that channel, however, contain a file named ‘F01FQK7R44E-Disney_Peloton_Roster’ containing an organized list of 111 Disney employees full names and leaderboard handles. At the time of publication, SpyCloud Labs is actively analyzing these attachment files to identify additional PII, identity data, and financial data suitable for recapture into SpyCloud’s Cybercrime Analytics Engine.
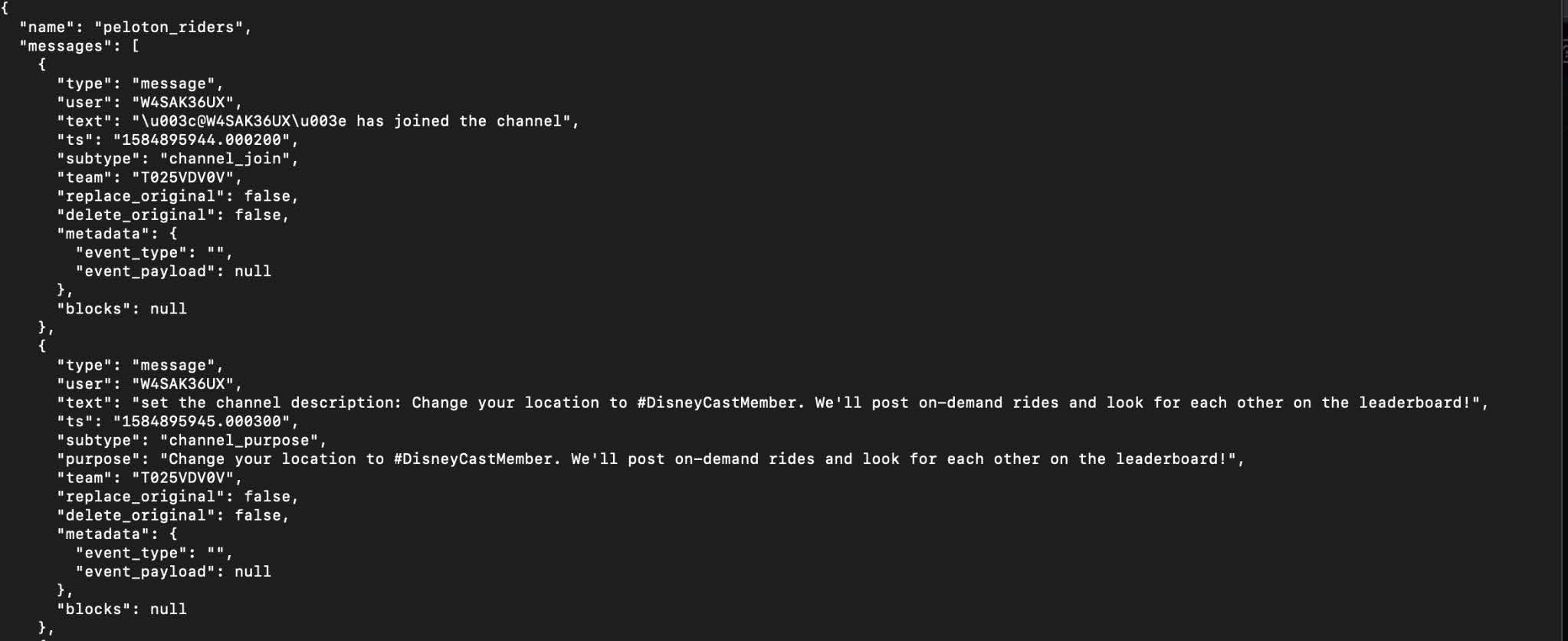
Channel metadata from the #peloton_riders Slack channel
Additionally, each of the zip files appear to contain a ‘readme.txt’ file with NullBulge ASCII art. These readme files do not have the same naming convention of Slack File ID–Filename as all of the other files, suggesting that they were likely added after the files were exported from Slack and were never posted to Disney’s Slack channels.
NullBulge readme.txt files with ASCII art
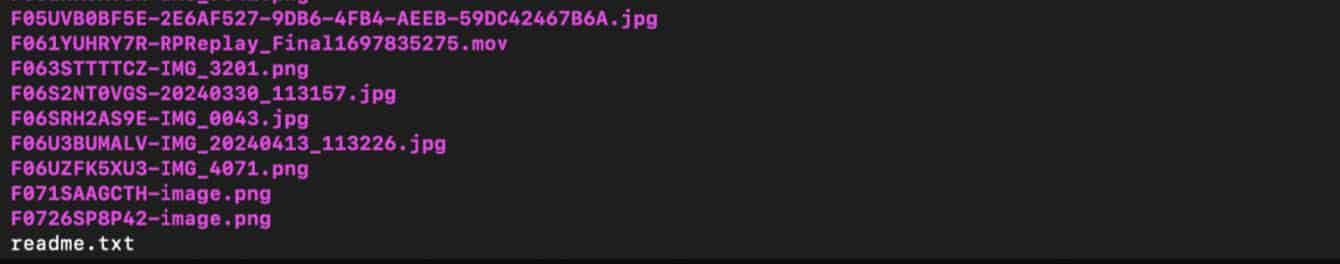
Screenshot of unpacked file names illustrating the differences in naming conventions between the readme.txt files and the other files that appear to have been exported from Slack
Key takeaways from these recent data breaches
Two self-described hacktivist groups with “Furry” aesthetics, SiegedSec and NullBulge, released headline-grabbing data breaches in July 2024:
- SiegedSec released a 1.94GB SQL dump of “The Daily Signal” website including email addresses, md5 password hashes, IP addresses, user-agent strings, twitter handles, account metadata such as account signup time, phone numbers, and full names.
- NullBulged released a 1.1TB dump of Slack channel message data and Slack file attachments from Disney. The data appears to go back to 2013 and contains messages from as recently as July 3, 2024.
SpyCloud Labs has ingested the ‘The Daily Signal’ breach into our existing data repository of more than 600 billion assets so it’s accessible by SpyCloud customers and can be used to remediate exposure risk. Our team is also actively analyzing the Disney breach to identify additional PII, identity data, and financial data suitable for recapture into SpyCloud’s Cybercrime Analytics Engine.
If you’re a SpyCloud customer, please reach out to your customer success manager with questions about these breaches.



