The 2025 Report is live!
IBM’s 2025 Cost of A Data Breach Report has been published.
Get new insights from the latest report here >
IBM’s 2024 breach report is out – and as we’ve come to expect, has some great context into the state of data breach incidents as reported by more than 3,500 security practitioners and leaders across the globe. This year’s report is particularly timely given the recent spike in breach events and related coverage, so let’s recap some of the highlights and key points.
What’s inside IBM's Cost of a Data Breach Report 2024
There’s both good and bad news. IBM and the Ponemon Institute report that security teams have improved their detection and containment of breaches, particularly through the use of automation and AI, but the news is less positive when looking at costs, resources, and implications.
Interesting stats from the 2024 report
01
The average cost of data breaches goes up by 10%
The global average cost of a data breach increased by 10%, reaching USD $4.88 million – the highest jump since the pandemic. This jump was primarily driven by the resulting business disruption and post-breach response activities. The US leads the pack as the country with the highest average breach cost ($9.36 million).
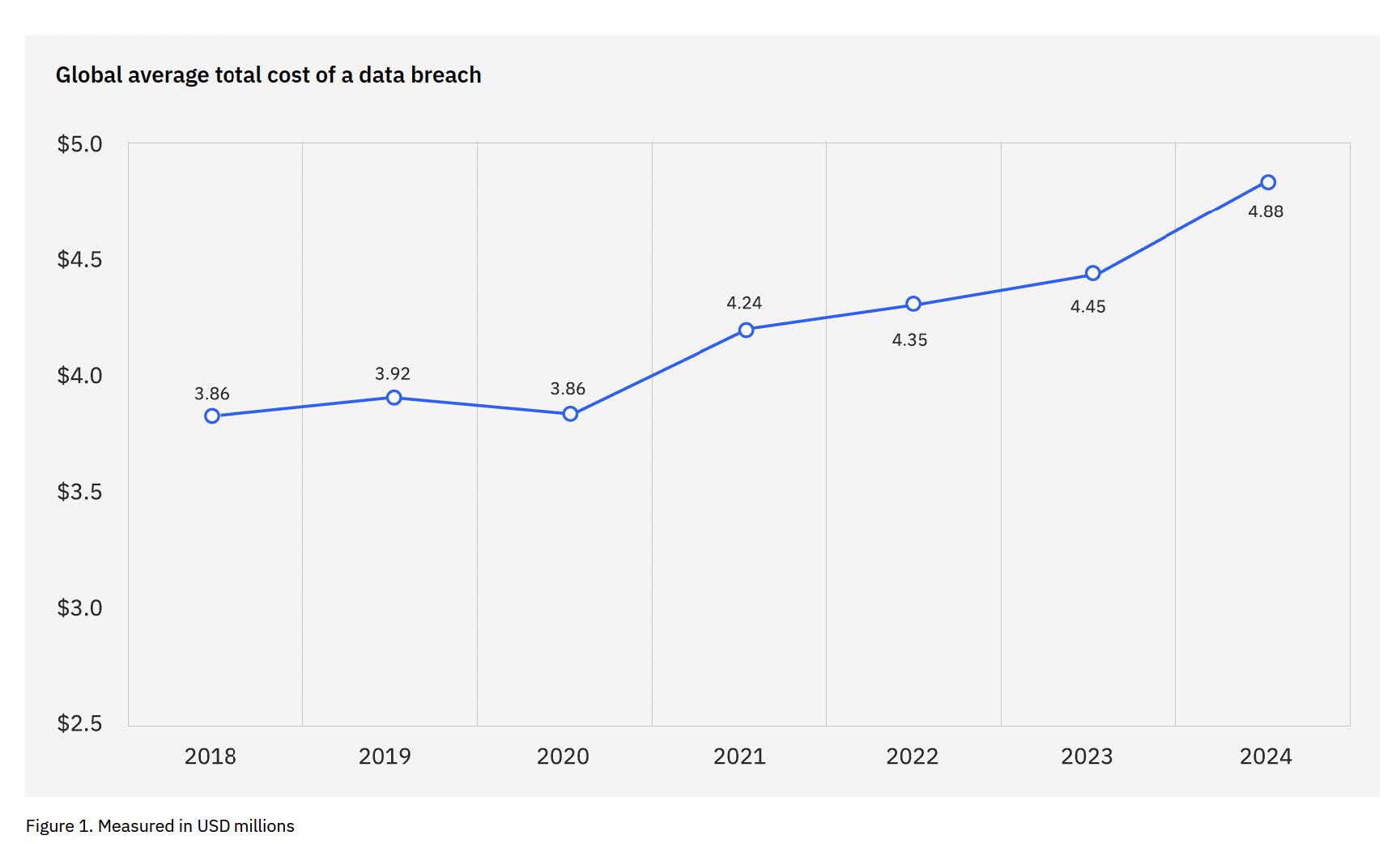
Cost of the average data breach from March 2023 – February 2024, sourced from IBM’s Cost of a Data Breach 2024, page 8.
02
Automation and AI relieve strapped security teams
Organizations using security AI and automation reported significantly lower breach costs, averaging USD $3.84 million, compared to USD $5.72 million for those not using those technologies. The use of AI and automation not only reduced costs but also accelerated the time it took teams to identify and contain breaches.
03
Organizations feel the impact of the cybersecurity skills gap
The report highlighted the shortage of skilled security personnel, with more than half of breached organizations stunted by this issue. The skills gap was associated with higher breach costs, averaging USD $5.74 million for those with high-level shortages compared to USD $3.98 million for those with low-level shortages.
04
Customer PII is the most targeted by cybercriminals
Customer personally identifiable information (PII) was the most commonly compromised data this year, accounting for 46% of breaches. Breaches involving PII were particularly costly for impacted organizations, highlighting the financial impact of losing sensitive customer data.
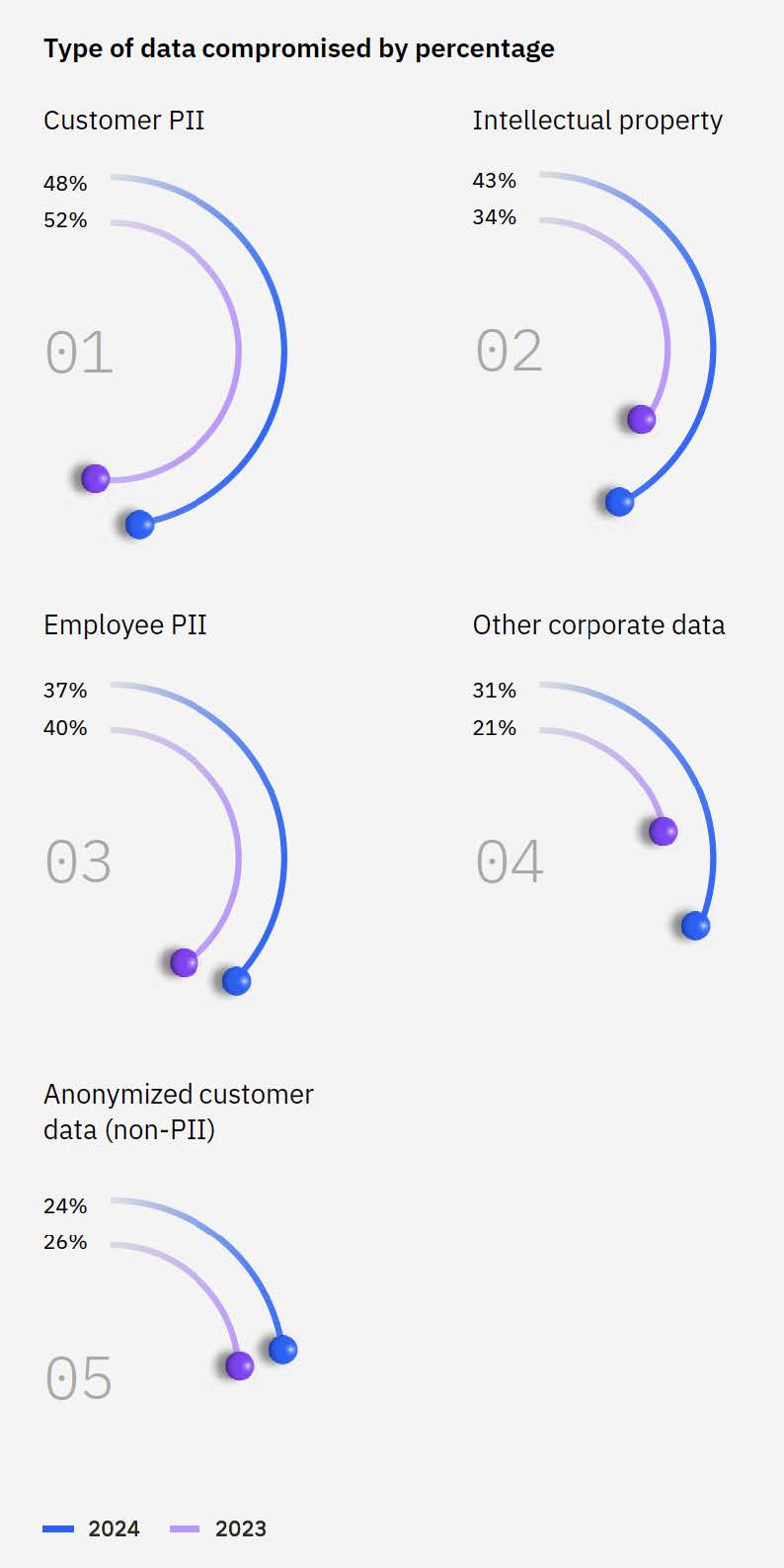
Year-over-year comparison of the types of data reported to be compromised in data breaches. Sourced from IBM’s Cost of a Data Breach 2024, page 12.
05
The most common initial attack vector was the use of compromised credentials
The research in this year’s report showed compromised credentials as the most common attack vector in reported data breaches, representing 16% of all breaches and overtaking the place of phishing, which held the number one spot last year.
Compromised credential attacks also packed a reported $4.81 million in related costs per breach and took the longest to identify and contain (292 days). Phishing, BEC, and malicious insiders rounded out as the other most costly vectors.
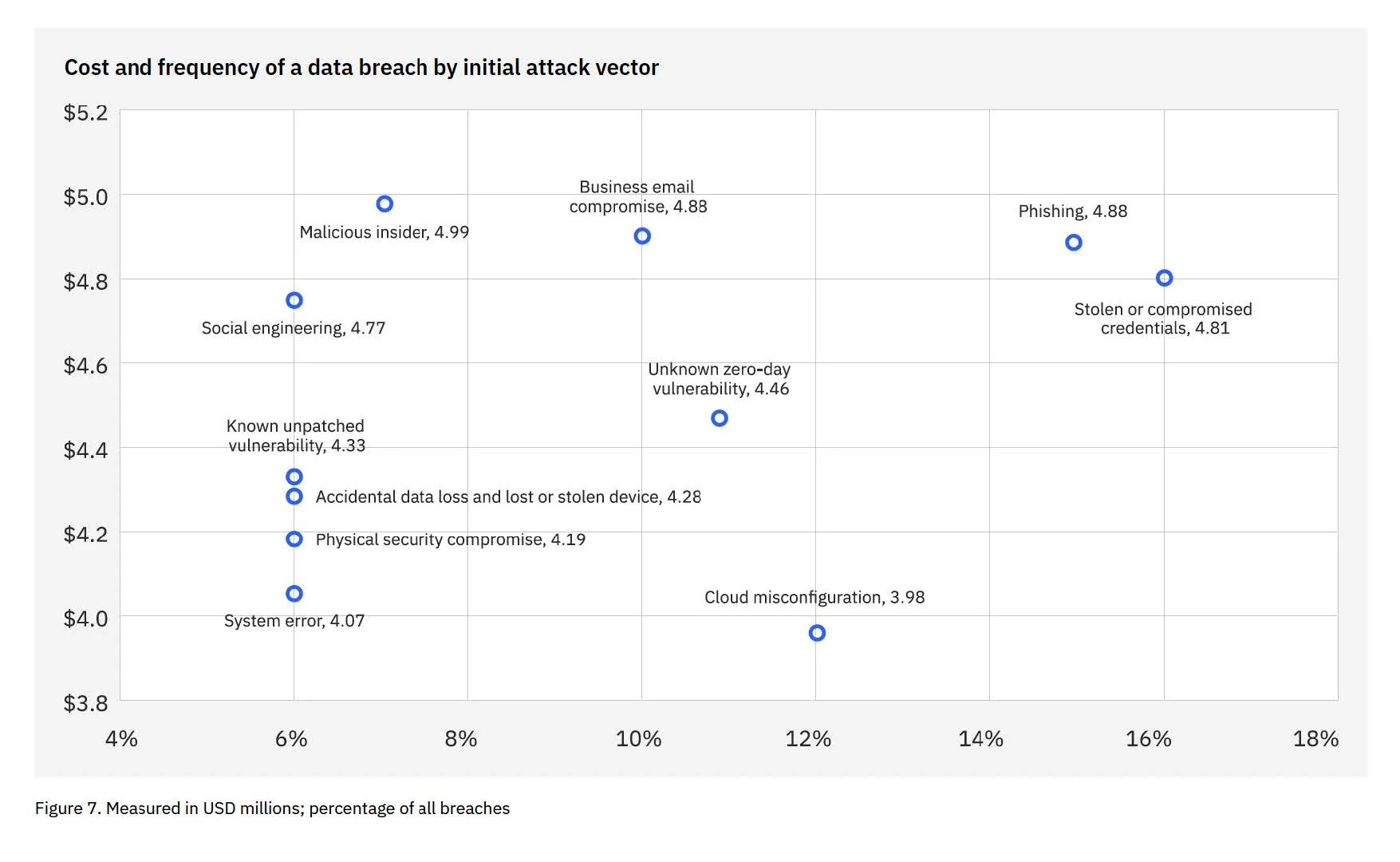
Cost and frequency of a data breach by initial attack vector. Sourced from IBM’s Cost of a Data Breach 2024, page 13.
To keep in mind – prevention is key
If you have the time, we always recommend giving the full report a read.
At SpyCloud, we relentlessly focus on recapturing stolen data like compromised credentials and PII because we know how dangerous it can be in the hands of bad actors. IBM’s report shows that costs from lost business and post-breach response increased almost 11% this year – so prevention really is key.
By prioritizing early detection of compromised authentication data and leveraging automated remediation, your organization can substantially reduce the risk of breaches and other follow-on attacks.