Account Takeover by the Numbers
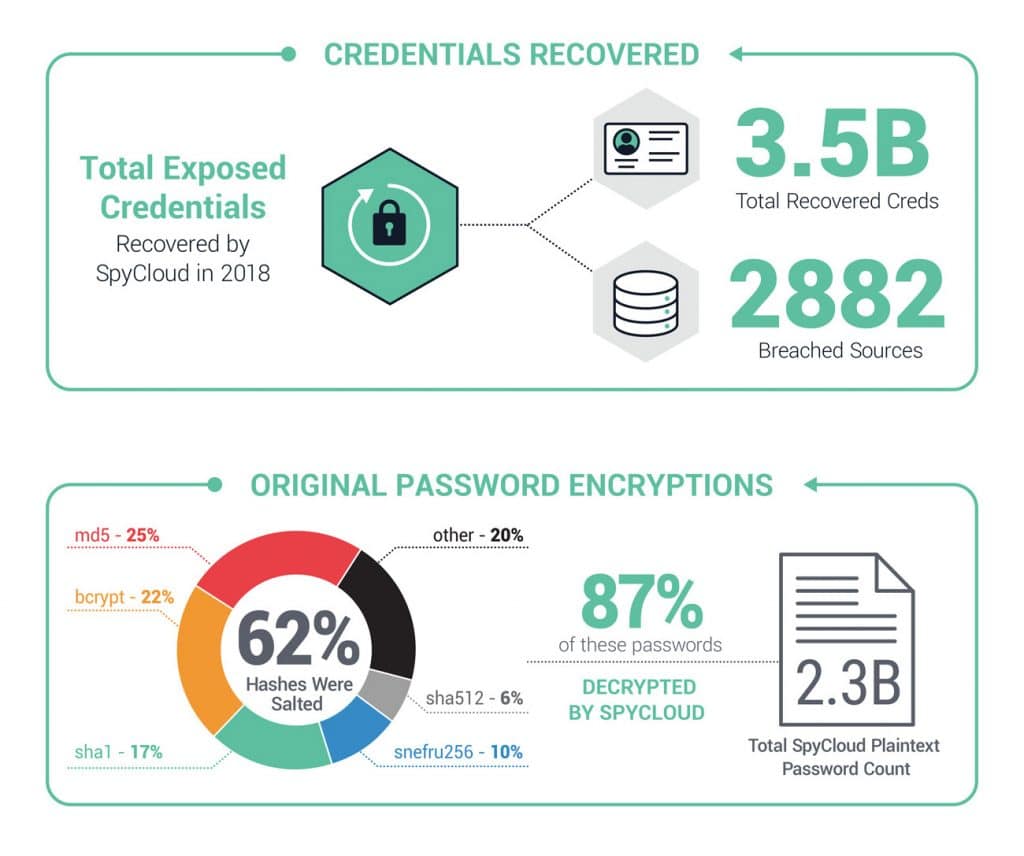
 In account takeover (ATO) attacks, threat actors exploit compromised customer accounts on underground markets for financial gain. ATO attacks can do more than drain accounts of funds; they can exploit sensitive data and damage brand reputations. Once again, the annual SpyCloud Credential Exposure Report found password reuse remains a main culprit for ATO. Of the 3.5 billion exposed credentials SpyCloud recovered in 2018, 24 percent can be directly attributed to reused passwords, 90 percent of which were exact matches.
These passwords are easier to crack than most people realize. Cyber criminals use sophisticated software, much of which requires only basic knowledge to find, to discover and leverage vulnerable credentials at scale. In only minutes, they can aggregate massive amounts of data and dump them into online databases they then sell to fellow hackers and underground communities. Once credentials are on the market, they rarely disappear. Unless those passwords are never used again by the user, fraudsters will abuse the stolen credentials for as long as they continue to reap any benefits.
In account takeover (ATO) attacks, threat actors exploit compromised customer accounts on underground markets for financial gain. ATO attacks can do more than drain accounts of funds; they can exploit sensitive data and damage brand reputations. Once again, the annual SpyCloud Credential Exposure Report found password reuse remains a main culprit for ATO. Of the 3.5 billion exposed credentials SpyCloud recovered in 2018, 24 percent can be directly attributed to reused passwords, 90 percent of which were exact matches.
These passwords are easier to crack than most people realize. Cyber criminals use sophisticated software, much of which requires only basic knowledge to find, to discover and leverage vulnerable credentials at scale. In only minutes, they can aggregate massive amounts of data and dump them into online databases they then sell to fellow hackers and underground communities. Once credentials are on the market, they rarely disappear. Unless those passwords are never used again by the user, fraudsters will abuse the stolen credentials for as long as they continue to reap any benefits.
Data Breaches in 2018

Related: The 2020 Credential Exposure Report
By the time the owners of these hacked accounts and the general public get wind of such breaches, the damage has already been done. The key is to discover vulnerable and exposed accounts before the criminals have time to sell the information in the underground. The SpyCloud team uses a proprietary process to gather breached records in the earliest stage of an ATO attack to prevent ATO altogether. SpyCloud is the only security company in the world to incorporate both automated technologies and human intelligence to go deeper into the web to uncover data otherwise undetectable. Our database of exposed credentials is the largest in the industry, giving our clients a better opportunity to protect user accounts.The Weak Link in Password Encryption
Many companies who offer customer web applications believe that by storing a hash of user passwords, that is, an encrypted form of the user password, they are protecting user accounts from being cracked. Unfortunately, most hashing algorithms use weaker algorithms, such as unsalted md5 and sha1, that provide only a weak barrier for criminals. Most fraudsters have become quite savvy in deciphering these basic hashes, using software to quickly convert hashed passwords into readable passwords that can be used to fuel ATO attacks.Password encryption types
(discounting combolists)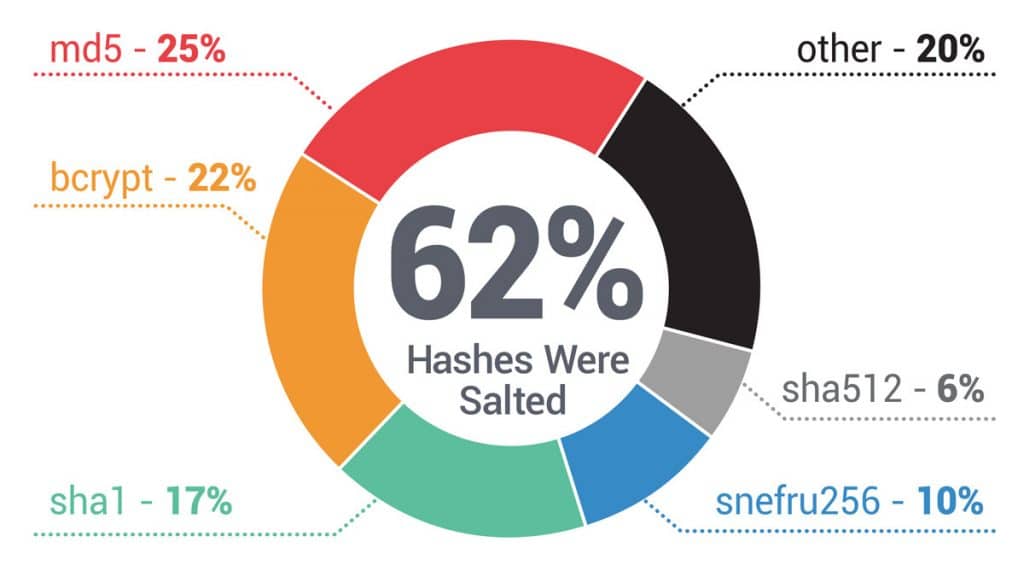
Personal Identifiable Information Is For Sale
Personal Identifiable Information (PII) is information about an individual that can be used to identify that person’s identity. PII combines a person’s first and last name with various pieces of personal data, such as social security number, driver’s license number, passport number, credit card numbers, medical records and much more. Because we live in a culture of information and most of it is stored in vulnerable systems, this personal data is not as private as we would all hope. Just as usernames and passwords bring value in underground markets, so too does PII. In 2018, SpyCloud discovered an eye-opening number of exposed PII data.The PII Recovered by SpyCloud in 2018
Names: 856M Address: 612M DOB: 315M Gender: 301M Phone Numbers: 240M Religion: 234M Ethnicity: 216M Occupation: 212M Estimated Income: 207M Net Worth: 203M Marital Status: 197M Credit Rating: 188M Social Media URL: 134M Job Title: 123M Voter ID: 70M Political Affiliation: 72M2018 Top Leaked Passwords Per Country
Once again, “123456” remains at the top of the most widely used plaintext passwords, just ahead of “password” and “qwerty”. Even while these are mainstays, password trends vary depending on the country of origin. It is an interesting dive into which passwords are most common by region of the globe. SpyCloud filtered out the 100 most popular passwords to not only gain a glimpse into the zeitgeist of the region but to illustrate how prevalent weak passwords are across the world. Passwords need to be unique and difficult to guess, according to the latest NIST guidelines. However, our research shows many passwords are surprisingly common and, therefore, the most leaked. Keeping with the sporting theme, “liverpool”,”arsenal”, and “chelsea” are the most popular passwords in Ireland and the U.K. where soccer reigns. Not surprisingly, “baseball”, “basketball” and “soccer” top the list in the U.S. and Canada. South American countries follow suit with “flemengo”, “nacional”, “riverplate” and “alianza” for Brazil, Columbia, Argentina and Peru, respectively. Even less unique are when the name of the country or a country’s most populous cities are used. SpyCloud found “australia”, “venezuela”, “bolivia” and “norway” were the most popular passwords in their respective countries, along with the biggest cities within those countries. Hover over the map to see the most leaked passwords from your country. Cyber criminals will continue to leverage the technology that promises only to evolve and become more capable. Companies must take a proactive approach to prevent breaches and account takeover. These attacks will no doubt escalate in their sophistication and combating them will require more than basic security measures. Now, more than ever, organizations must look to companies like SpyCloud to equip them with a modern defense. Only by using proven methodologies and cutting-edge technologies will companies be able to protect their users, their data and their reputations. Feel Free to Share our Infographic on your Site