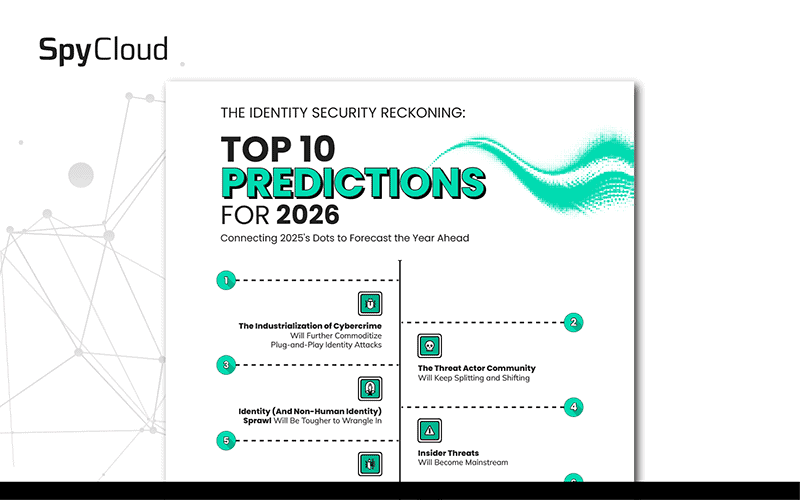
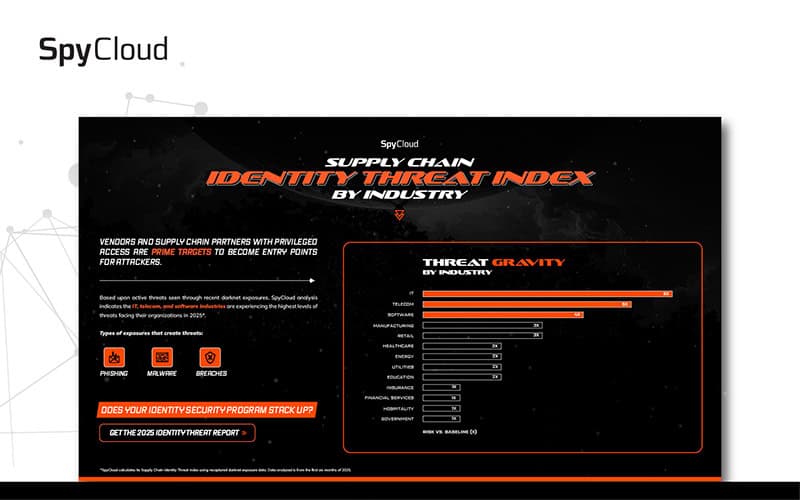
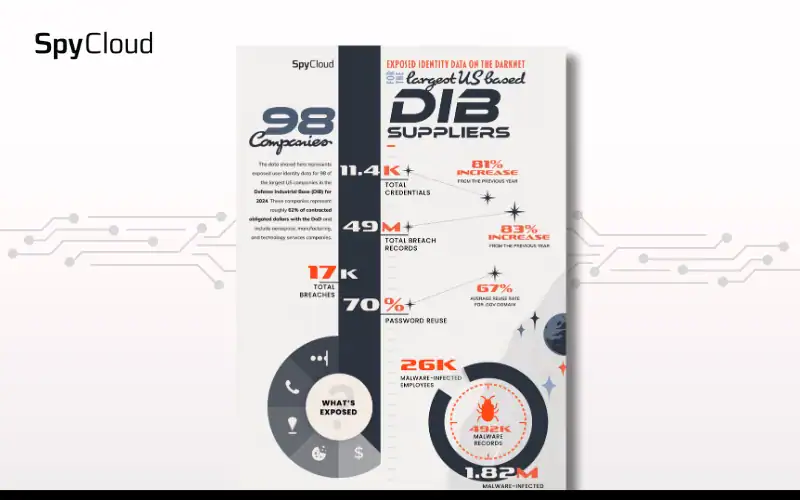
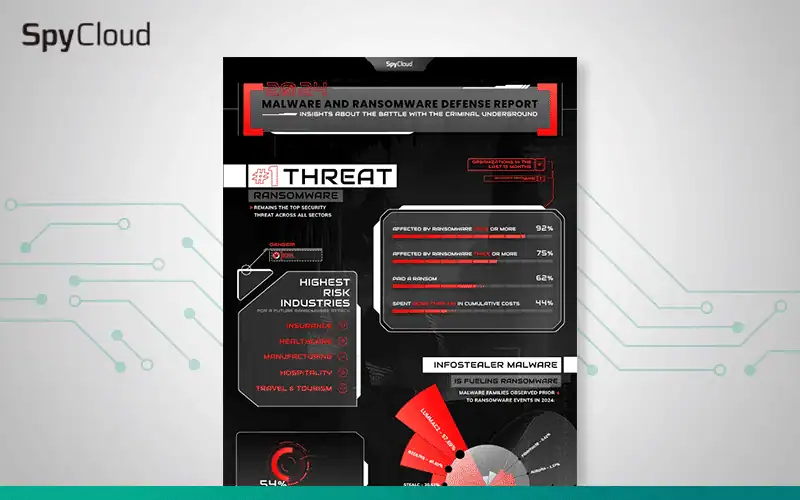
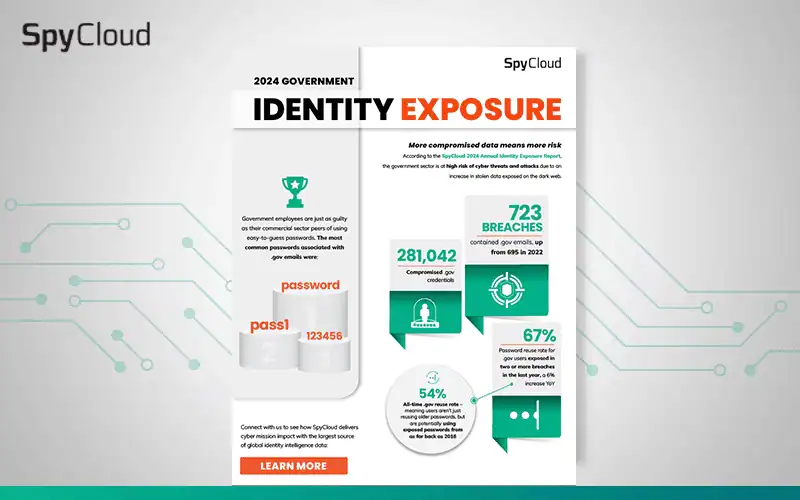
SPYCLOUD RESOURCES
Insights from the criminal underground that help you get ahead of the latest threats
- Tools
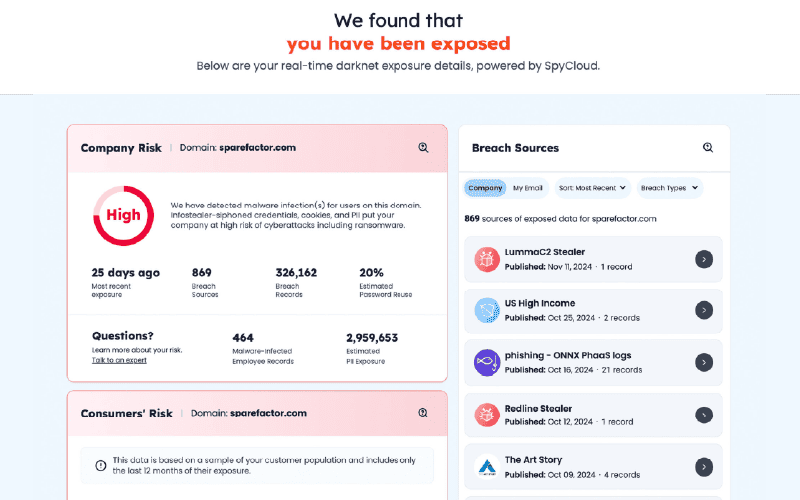
Darknet Exposure Check
Identify threats to your organization including third-party breach exposures, malware-infected employees and consumers, password reuse, and more.
- Tools
Password Exposure Check
Test any password to see how many times it has appeared on the darknet, meaning it’s unsafe to use.
Webinar Videos
Okay. Great. We see a lot of participants. So, let's go ahead and get started. Thanks for joining today. Today, we have a live event all about minding the malware gap, about identity threat protection beyond the endpoint. Our hosts today are Damon Fleury, the chief product officer at SpyCloud, and Joe Russin, director of security research. Joe is over twenty years in various IT roles, but is now focused on cybersecurity and leads our whole security research arm. He's all about collecting all the breach and malware and fish data that we'll talk about today, and he's actively collecting data as we speak. So, a little Zoom etiquette today. Please post your question in q and a in Zoom. We'll have time at the end to address it, or we'll have live q and a depending on on how the conversation goes. But please add it to q and a. We'll make sure we answer your question on this call or afterwards. So today is all about malware. We're gonna give a brief overview of the malware landscape and what's changed the past few years. Joe will talk a bit more about what SpyCloud Labs has learned from, looking at trends malware and analyzing some of the top stealer families out there. Dane will talk a bit more about the malware kill chain and the attack life cycle we're seeing from, bad actors, but then we'll go beyond the the endpoint with spy cloud, show a bit more about how our solutions could help you, including a live demo. And then Joe will give some tips for how you can protect your workforce identities today. Thanks, Taylor. So before we get into the conversation around exactly what is going on with malware, Just wanted to give a brief overview of the kinds of data that spy cloud does collect. And so spy cloud really focuses on information that is flowing through the dark net. Like in this image, you know, we have all these data points flowing through the dark net that is on its way to actors, With those actors, you're using this information and this identity related information in order to attack your enterprise at the end of the day for account takeover, for online fraud, for ransomware, for a variety of other types of attacks. And when we are looking for data, when SpyCloud is looking for data that becomes the basis of our products, we're really looking for three forms of data. What we're known the most for is this box in the middle here for breached data that we've been collecting since the beginning of the company, and we have more than forty thousand distinct third party breaches. We're adjusting hundreds of new breaches that we find throughout the globe every single week. So we have a lot of data that comes from third party breaches. We also have data that comes from successful fishes. So when you when one of your employees or an individual clicks on that link and just just falls prey to that trick once again, and they actually give up their data, I mean, the the actors are using that information for their own for their own agenda. We are collecting that data, and we'll have some webinars on how that works coming up. But what we wanna talk most about today is another core element of what we collect, and that's malware victim logs. So when individuals do accidentally install malware or somehow malware does get installed on that system, then those bad actors are collecting as much as they can from that system as quickly as possible, funneling that into the dark net, and that's where SpyCloud picks up that data. So just wanted to set the stage for these are the different types of data. So when you're a SpyCloud customer, you gain access to all of these. But we know a lot of lot of customers and a lot of folks are interested in what's going on with respect to malware data specifically, and how that can be used to help protect your enterprise, the data that we find. So with that, I wanna turn this over to Joe to talk much more about the malware landscape. Thanks, Damon. Good morning, everybody. Two thousand twenty four was a great year for collections in Spy Cloud Labs. We have, nearly eight billion third party records ingested, and those are the breaches that Damon was talking about or the breach data assets. And we also have, five hundred and forty eight million malware records that were ingested. This is actually what we're talking about today, and that's across sixty four malware families. We also had a good one point five million, Telegram messages collected, and those might include things like combo lists or phishing data or even sometimes the third party records that we were talking about earlier and even some malware records for, stinger logs. So these things are actually something that we're looking to leverage more in the future and hopefully be able to have quite a bit more data as we increase our assets. But we also had, speaking of assets, a good, fifty four billion or so, new assets ingested. So that's quite the number. We're we also have a pretty decent, report, if I must say so. The two thousand twenty five spike cloud identity report, you should check it out if you haven't already online. I thought it was extremely well written, and there's a lot of good little tidbits of information. We have basically a couple things here that we want to go over that's related to this particular, scenario today, which is, ninety one percent of orgs reported some sort of identity threat in the last year. And then stolen credentials were actually part of eighty percent of the breaches, that we basically saw that were related to malware, in malware or combo list. And, honestly, with combo list and what we call, URL login and password or U LPs, those basically all kind of our source from combo or excuse me, from malware. The stealers that are actually involved, basically, are usually parsed out by the threat actors, and they make up these specific type lists where we can basically then, where they target certain organizations or certain vertical sectors. The other thing that we wanted to mention here is that the Infostealer malware, basically had been involved in fifty percent of corporate user infections. So as you see here in in this slide, we had quite a bit of red line in two thousand twenty four, and you also will see Rizepro and, Steel Seed, Meta, and LUMA kinda at the bottom. But here's the big thing that changed, basically, in this, near New Year. Basically, as of two thousand twenty five, even in the first quarter so far, we have seen Luma really take off. Base if if you could see here, the increase is huge compared to what we had in the past. You're looking at a twelve thousand, eight hundred or excuse me, twelve thousand eighty three percent, or twelve hundred eighty three percent, excuse me, year over year luma increase. And as you could see also, the other Steelers kind of all kind of, fell by the wayside. We think that this particular issue or what we see here is because of red line's takedown with Operation Magnus in October twenty, excuse me, October twenty ninth two thousand twenty four. This basically led to LUMA kind of taking over the underground and being the stealer of choice or the commodity malware of choice. So, going back to the heyday of monolithic botnets and kinda going back to two thousand seventeen or even earlier, in the past, what we saw was a single owner, that were a group of owners that had a modular code base. We're talking about botnets like Quackbot, Emotet, Trickbot, these types of things. The way that the malware kind of, worked at that time, it was pretty centralized, and it actually had trite infection vectors. You probably have all seen it in the past where you get an email, it's a phishing email, and it tries to get you to execute some sort of macro code on your machine. The technology basically is now or excuse me, has was at that time more centralized and and susceptible to LE action. And law enforcement agencies actually executed takedowns of Emotet in two thousand twenty one, and also in two thousand twenty two, and then Quietbot in two thousand twenty three. And then we saw, operation endgame, which took down Iced ID, Bumblebee, Peekabot in two thousand twenty four. All of these things kinda had a very heavy weight on the, underground infrastructure for criminals. They, were no longer able to utilize these things for the initial access brokerage. So, essentially, the attack chain also was expensive to, maintain. They had to do every angle or every part of the whole attack chain themselves or somehow package it within their c two infrastructure. Social engineering also was the main thing that was getting them, access or their lures in Microsoft, as we mentioned earlier, had basically macros, that we're allowing by automatic or default, executions on local machines. It was pretty easy for users to click one box and infect themselves. That changed in July two thousand twenty two, and we basically had the new infection vectors, that they tried to use afterwards. Not so effective. Things like l n k's or ISOs or JavaScript where they were fifteen some different steps you had to do, and it was unlikely that users were basically going to do the whole chain of events in order to infect themselves. So what we have today is, as a result of that law enforcement action in bad actors having to adapt, They started to look towards things like commoditized malware and taking things off the shelf. Things like info stealers were already on the rise. They were basically coming up and becoming more sophisticated, but this actually really accelerated that. What really mattered to the endpoint actors, in order for them to be able to install some sort of ransomware or to extract things is just the access. That's all they care about. They need to basically get those different victims listed so they can actually attack them. So one of the ways that the teams or the people that do the actual initial access, brokerage for them was they started to use malvertising. And this is where you have common apps that you might have on the Internet where people look and try to find some sort of a download for maybe Zoom or Slack. And these types of things were leveraged by threat actors to create fake ads, and the ads always show up at the top of the list when you do a search. And since end users are accustomed to searching for things, they just pick the first thing. And that way, the actors can set up a fake website, essentially, that is a mirror of a real download website for Slack or Zoom, and then they have their malware that's actually injected as part of the process. The technology was essentially no longer as centralized as it was, with the old take downs of the past. So for the most part, they were more resilient to being able to be taken down, although we still seen some action to it. They also, are leveraging a mature ecosystem of criminal services. There's best of recode. There's a whole criminal infrastructure that essentially is, partners or a web of partnerships where people trade services. So this leverages that. Speaking of those services, some of the independent services that were out there, like Ghostox, have had some very, burgeoning partnerships with modules for the info stealers. So the impact is basically we have, an expanded and diversified malware economy. It broadens the threat actors, community access with common tooling, which is very important because then people can move from team to team in order and have the actual exact same tools that they're accustomed to using. In the users, actually, as we mentioned, infect themselves because they're searching for apps to install. And when they go to install the app, actually, it does, in a lot of cases, install it, but it is also putting some malware in there for along the ride. So here we have basically an example of the one of the partnerships. Ghostox has been working with Luma, and we had created a blog on this that we'll send out to you afterwards. But, the main idea here is that LUMA has a second punch now where most of the cases in the past, Infostealers would run once, and they'd be done after ex exfiltrating all the data from your system. In this particular instance, the threat actor can, from the c two panel, actually decide to install Ghostox on a particular victim, and then that victim has a persistent backdoor on their machine. What will happen then is that the threat actor can essentially run commands and browse through that, SOX proxy. That SOX proxy, could be used to do spam or fraud, or they will sell that access to somebody else. And then that basically is just another issue for your environment. Here's an example of basically some of the law enforcement take downs and how it's leveraged, essentially by large ransomware type groups. Bypass, you probably heard about, had a issue recently where they their chats were released, and, we took some time to announce do some analysis on the the chats. We found that, basically, when operation Duck Hunt took down Quackbot, which was in August two thousand twenty nine, of two thousand twenty three excuse me. Basically, we had, essentially, the threat actors have a, oh, crap moment because they didn't have any of those initial access vectors coming in anymore. They had to find something other than quackbot in order to get their foot in the door. So as you could tell with the listing of the different chat topics here, this is a map of what the chat topics were over a period of time in with September first being after the takedown. As you could see with the Steelers, it actually starts to increase over time. Eventually, Black Vesta decided to move more towards brute forcing, but this is from another blog that's gonna be coming up soon. So look out for that, which gives you a more in-depth, sort of overview. But Black Vesta did have in their panel a Steeler module. So what's in a Steeler log? Why are these such an issue? Well, you can kinda see, what we have here in this page is at the bottom, we have a a, atomic stealer. Basically, the log that shows you the key chain access, and the key chain access for your macOS is essentially where you save all your passwords. Also, you could see there's autofills in there. There's some brute force ideas. Sometimes there's more than zero bytes in there. That one just happens to be empty. But, you can also see cookies. You could see things like desktop files inside of this or browsing history or even desktop screen captures of what you were doing when you installed the malware. The, really critical thing too is from a financial perspective, it also will pull out credit cards from the browsers or it'll pull out cryptocurrency wallets from different apps. It will also, basically look at different common application installs to see what may be saved for credentials. So the really important thing and something to think about how you could pivot or very easily get into a corporate system if if a user at home installs essentially, a malware that is an info stealer that pulls data from their remote desktop application, whether that's VNC or something else. They can then basically get the access to that remote system. So if they use that in order to remote into their workplace or their enterprise, you could see how that would be a big problem. Some of the common apps you can see on the right, there is AnyDesk, Telegram, TypeVNC that are listed at the top there. That actually is a Luma c two, log that's shown. So let's meet the, top malware, Essentially, inside of our, our top list, I guess you could say, on the Windows side, you see Lumacy two. By far, it's the most common sealer infection we've seen in two thousand twenty five. We expect this to continue. LumaC two has seen some constant, development. There's been a lot of, things where different browser, creators will try to lock down things like cookies or stuff like that with encryption, but then matter of days, this developer from Lumacy two comes back and has a workaround for it and still has access to it. The it's essentially a cat and mouse game with detection. We have we we have quite a few different pieces of the ecosystem where the actors are able to take their malware, send it to a particular encryptor or a loader service. And from that point, it has a whole new attack vector and is able to get in quite easily. The as we already mentioned, we pull unique configs on the configuration with Luma c two, and we also have that GOSOX partnership we already talked about. So if we have, essentially, Max, are we okay? Well, not so much. If you take a look at what we also have in the ecosystem, we have Atomic Steeler. And what we've noticed so far is that this is growing and is increasing in size in the amount of, atomic steeler logs that we're able to collect in the dark net. And this is probably one of the fastest growing even though Luma is growing so fast from what I see. The same type of malvertising is used for, basically, these third party, apps vectors, where if you're trying to install, for instance, a particular Mac OS application, they will be out there mirroring those download sites and doing malvertising to get you to choose them first, and then they come along for the ride. One thing to that's really important to note with the malvertising is, just to touch on it again, we see basically some of these packages that they put together installs this info stealer, but it also installs the real app. So the end user doesn't realize something has actually happened. Logs are also including the keychain info, as I mentioned earlier, which is pretty critical. And now I'm gonna send it over to Damon. Thanks, Joe. And I see there's a question, in the q and a that actually segues perfectly into the next part of our conversation. And that question is how good are EDRs at preventing malvertising from being successful, and can they bypass EDRs? And I think the unfortunate reality is even though EDRs are fantastic and critical parts of your protective mechanism, you absolutely we do absolutely have issues where some of these different technologies and malware are bypassing the EDR. And, you know, this number on the screen is specifically talking to that. In the first quarter of this year, we discovered we pulled in from our dark net sources ten point seven million infections of systems, and sixty six percent of those had an endpoint security product of some kind, an AV or an EDR, deployed on that device at the time of infection. And so the unfortunate reality is that there isn't a silver bullet in stopping malware. There isn't there isn't something that could stop every single case. And we'll talk a little bit more about what some of those what some of the reasons might be for this. But our reality as as individuals that wanna protect enterprises is that we, you know, we have EDR. We have to have it. It's a critical piece of that solution, but we have to realize that some things will get passed. And are there ways for us to understand, and what can we do in those scenarios? And so I wanna talk for a little bit about this kind of larger ecosystem of of malware. You know, I think Joe just gave us a great, bit of insight into what we're seeing, particularly in the info stealer part of malware. But I think it's easy to get kinda lost in. Well, we talked about all these different variants. I think we'd last year, we had sixty four variants of of Infosys we are tracking. We're up to seventy five different variants already this year. How does all that fit into when an actor is trying to target an enterprise or trying to to gain access and find a way to make money off of one of our companies. Like, what's going on, and where does LUMA c two or any of these infrastillers fit into that? And how can SpyCloud get this data, and what can you do about it when that happens? And so, so all, you know, all endpoints, endpoint security solutions, and really all kind of malware detection solutions are trying to find any place in the attack cycle that an actor is trying to take advantage of a weakness, and you wanna detect that and you wanna stop it. And so when you think about the attack life cycle, many forms of malware may play a role, and the things Joe just talked about are just one of those bits of malware. So if you think about somebody trying to attack an organization, it always starts with the entry to that organization. You see in this first column on the left, they could get in through a phish. They could get in just with stolen identity and credentials, which is something that we we see quite a bit from spy cloud's perspective or social engineering. There's a variety of ways to get entry to a system, and that typically happens very quickly. And once they gain entry to a system, they immediately move into what I like to think of as the recon phase. They're trying to establish some level of control so they can run more malware or some level of connectivity. It's often automated. There's there's sometimes not, you know, any additional steps. And then they're trying to figure out where are they? What have they gained access to? Running an info stealer has become the primary way of getting an inventory about that computer and about the rest of the system. They wanna know things like, are they on a domain? What kinds of applications are installed? What do these users have access to? Do these look like administrators? Like, where have they landed? Right? And they at at the beginning, they don't know. And an infostealer is a really well established set of infrastructure that allows an actor to run this tool really quickly. It goes up to a command and control or to a panel, and then they can gain access to that data right away. They'll also run other tools to do network mapping or to to run domain enumeration. So they're trying to figure out where have they landed, and that infostillers a key piece of it in most of these attack scenarios. Then they move to the entrenchment phase. Right? And so they know a little about where they are, and they now wanna move laterally within that organization or they wanna disable security apps. They wanna figure out, can they get to privilege escalation? They form a back door back to their command and control. You know, I'm not gonna read all of the boxes, but there's a lot of steps that they'll take to entrench themselves within that organization and to make sure that they can then move to the next step. A lot of times, once they've entrenched themselves, that's the point that they might sell access to another actor. That's a point at which they might, you know, go to an initial access broker, sell it, and then a ransomware gang might purchase that access, or there's a variety of ways that access can then be distributed. And then they move to the the disruption or the monetization phase, right, where they've got access to that organization. They wanna steal something they can sell through IP theft, or they want to, lock you out or, you know, domain lockout, admin lockout, data theft, data encryption. All of these core components are what often make up a ransomware attack right at the end of the day, usually with many forms of malware. And so we're talking about how do we understand this entire life cycle. And what Joe was talking about is, you know, we've been able to, with our interaction with the actors, gain a lot of access to this info stealer part. And if we can detect and see that info stealer event, it can help us to know that the controls haven't stopped them from getting this far. And can we then take the take steps to get ahead of the entrenchment and the disruption phase? And the sooner in this life cycle that we can stop the threat, the the cheaper it is for us to fix it. And so endpoint security is an absolutely critical part of this. Right? You know, regardless of of whether spy cloud sees that info stealer, you need this endpoint security solution to help you try to detect the entry, detect the reconnaissance phase, detect the entrenchment phase, and then stop a ransomware. I know we have a lot of endpoint security products and EDR products now. They have tools to stop the actual encryption activities. All those things are critical. And like I said earlier, the sooner that you can detect it, if you can detect it at entry and stop that phish from being successful, well, you're stopping the rest of this life cycle. You're protecting your business from that damage. So all of that is really important. But, nonetheless, no security solution is foolproof. Right? There are mechanisms. It's a as as Joe said, it's a cat mouse game. The actors are always working against us. They are always they themselves are installing the popular EDRs. They are finding ways to get around them or to suspend them. I know when I spent a lot of time in incident response, the first thing we would see with these these, these attacks would be that they would go after immediately whatever the EDR was and take steps to disable those processes or to find that registry configuration that would make it so that, signatures got turned off or they would take whatever steps they could to somehow limit that that that technology, and that game is only escalating. It's not it's not getting simpler. And so what can we do with the kinds of things we've been talking about today? Where can we apply knowledge of an info stealer event? And so in that recon phase, you know, as you see on your picture here, so we have the attack entry. In that recon phase, if a successful info stealer, successful from the actor standpoint, does run and gather that data, that data gets sent to the criminal underground. And then often within minutes, Spy Cloud can gather that information and feed it to our product that we call Compass, which provides malware protection. As soon as we get that data, often within five minutes, we could deliver that to, to our customers through our integrations. And then we have integrations with popular endpoint detection or response platforms such as CrowdStrike, such as Defender. We can immediately take that information, either make your SOC aware, or if configured, we can quarantine that device. And the goal is to take the knowledge that an info stealer did run, run it through the spy cloud compass product, get it to your EDR, give you the ability to take steps before it can reach the entrenchment phase or before it can reach the disruption phase. And the sooner we can figure that out, the more we can protect you from that that eventual disruption. And so why why is this happening? Right? This is a pretty common question of, you know, I I've invested in a very strong EDR solution. I know it's blocking things. I'm getting the alerts. You know, how is this still happening? And the reality is this is happening to all EDR vendors. Like, we we have the data. We can see what's installed on those systems because the logs tell us that no vendor is immune to, you know, to these types of events that that do slip through at times. Why could it happen? We certainly see issues in systems management such as an out of date endpoint software, failure to install security updates, systems sporadically online, or sometimes policy management issues. This is way more common than you might think where something is being interfered with by the endpoint security solution or at least you think it is, and an administrator might turn it off for a little while and then just never get a chance to go back and to reconcile that particular issue, leaving that system vulnerable. That's a very common scenario. I know when I did a lot of IR, that was way too often what was actually happening. But then there's also just the reality that, those actors are always working against the endpoint security solutions. Zero day exploits, do exist. Unpatched vulnerabilities are out there. There are there are always innovations in malware such as memory only malware or specifically EDR targeting malware or polymorphic malware. And I think Joe talked to some of the things. Luma c two has made a business, to finding ways to get around these detection mechanisms. And so all of that fits into a a spy cloud architecture that includes Compass. So the Compass feature set allow us to gain access to these the malware logs that can be connected directly to your domain, and it that information about the infected user along the top can then be used directly to respond to your employee systems or to, other people that have access to your network. That could be directly integrated into your active directory guardian where, sorry, to your Active Directory system through our product called Active Directory Guardian that can automatically take action to reset passwords that are found that that are found through these malware logs that could be used against your enterprise. It can also be integrated with your SIM and your SOAR so that you could take automated actions that are unique to your enterprise. And then on the bottom of the screen, we have this integration with the endpoint detection response system, which we're gonna talk a little more about of how this information can be fed directly into the EDR so that you can then take immediate action in order to protect your enterprise. And so using the Compass product, you can detect unseen infections. We provide you conclusive evidence that there was a malware infection. And it's important to realize that, these infections occur on on enterprise system or enterprise controlled or managed devices that are managed by EDR. But we also often discover infections that occur on unmanaged devices. Maybe an employee went home and had to log in from home due to some critical issue. Well and they didn't realize that their kid's computer was also used to install mods for Minecraft or Fortnite, which provided that opportunity that Joe mentioned for someone to accidentally to you know, not accidentally at all. For Mowers to maliciously put, some type of insert into that package. This is way too common of a case that we see. Your favorite skins on Fortnite are, you know, the thing that cost you your corporate credentials. And then you have things like, you know, password sharing that can make passwords move between people's computers when you log in from multiple places. So all of those things lead to information that ends up getting shared, and those come through unmanaged devices. We cannot resolve those with the EDR because you don't most companies don't have policies that re that require the installation of that EDR on their home computers. But you can at least detect those, and you have conclusive evidence of whether it's an unmanaged device or whether it's a managed device. When it is a managed device, you can also take advantage of automating your response to make sure that that corporate device is protected. And then your goal in all of this is to block that entrenchment phase as early as possible and hopefully to stop ever reaching the disruption phase. And so let me show you what that looks like, when it comes to, our you know, how you can see it in the spy cloud interfaces. And so what I'm showing you here is the spy cloud enterprise protection portal, and, you know, there's a wide variety of features that we could walk through. But today, we're just gonna focus on the Compass set of features where we have this little section here, the Compass compromised device list. And what you'll see when you look at your set of compromised devices is each of these represents an infected computer, that, that gives us information about an infection that happened and all the information that was stolen by whatever that infection is. And let me also say at the get go here that what I'm showing you is sample data. This is data that we create for the purposes of showing how the product works. We're not showing you any sensitive data. If you wanted to specifically see how this could impact your organization, we would love to set up a demo for you. Feel free to reach out. But as we're looking at this sample data, wanna walk through just a quick example of here's a place where we see a computer that was infected that has a name that looks like something I might see in my enterprise. So if I click on that specific one, I can see the types of data that was stolen by this. And let me just just continue to reiterate here. We have no access at all to this computer desktop eighteen ninety six. What we have is access to the information that the bad actors stole about this computer. So we know the system name. We have a little bit of data about the system owner. We can tell it looks like it could be a work computer because it's a Windows ten device. I can then say, well, what's the likelihood that this was actually, you know, fits within my world? And I could see when it was infected, and I could see additional details about the country that it's likely to be in. And down below, I can see the list of applications that that login details were stolen from when they stole the data off of this specific computer. So if I go back to that just to show you another way to view this same type of information, you can also look at this in a graphical form, and this just gives you another way to view that we have a computer that was infected, and we have access to, the list of applications that were accessed by that computer. And you can see often there's there's things that are interesting. The fact that the one login credentials were were, stolen. This hopefully, multifactor authentication was deployed for this enterprise. But even if it was, you just went down to one factor, and, you know, you're depending on that MFA step, to protect you. So you would love to reset those password credentials, which you could do in an automated fashion. And then, you know, you could see the other list of applications. You could see that this user also had a GitHub account. Gives you an opportunity to make sure that all of your applications are in fact managed by your SSO and that you don't have, you know, some credentials slipping out for some type of shadow IT or or access that you may not be aware of. And so this is just a view into we have a computer. It's desktop eighteen ninety six. It does, in fact, appear to be infected or experience an infection moment. And so then you can also see how that would integrate into your endpoint detection. So we offer, as I mentioned before, very straightforward integrations today with CrowdStrike and Defender with more to come. And what you're looking at is the configuration page for our integration with a CrowdStrike deployment that is managing this sample data, the sample environment we call spare factor dot com. And here you can see beyond just basic configuration, the types of things that we can do is that when you have this this configuration enabled, we are always running. We are responding to the detection of new malware events. When we see those, we have the ability to send a daily report to to folks that need to see it. We can also, configure to send notifications at the moment of detection so that what you're really getting is a check between I see a spy cloud event. Does it match to a CrowdStrike managed device? If so, send an email or open a ticket. You can see we support sending tickets into Jira or ServiceNow with more to come. We'd love your feedback on what else we need to add. And then if we see that match, we know there was an infection of that that that could impact or did impact a managed device. We also support automatically isolating those devices when they appear. This is an option that some of our customers are interested in. Many are not quite ready to do that isolation depending on the impact that it has, but that is an option should you need it. And, of course, if you want that, you have to you make you go through a few steps to make sure that we do understand you. You understand the implications of automatically quarantining devices, and most of you have EDRs. You're familiar with this, you know, this conversation. And just to show you what this data could look like, moving to the part where we can show you what is matching between what the spy cloud data looks like and what the CrowdStrike access has. In this part of our configuration, we show you these are the latest compass matches, the data coming from spy cloud. And then down here in this table, we'll show you which ones do map directly to crouch to endpoints that are managed by CrowdStrike. We can see here that desktop eighteen ninety six we were just looking at with a specific username was in fact matched as a managed device. And then I can, you know, I can understand that. A notification would have already been sent. But if I wanted to, I could come in here. I could click that option, and I could say confirm. Please do quarantine that device, and I've now taken a manual step. Of course, you could have done that through CrowdStrike as well if that was your if that was your preference, but we wanted to give you one place to understand it and to respond as quickly as possible. And so at the end of the day, it's a straightforward connection between the data that we have and the ability to respond to it within your own EDR. So I'll stop sharing, turn it back to Joe. Thanks, Damon. Yeah. That's really cool how that works. I'm really impressed with the integration between that and, you know, CrowdStrike. Awesome. Yeah. I wanted to do a little slide here just to kinda go over some things to basically help you with, these threats even if you don't buy our products. This is something we wanted to do just to help everybody. So enterprise tips basically that I have for you are, an advertising threat is quite the the vector here. And it seems like, you know, we had this happen in the past where you had, essentially, maybe in two thousand, you know, eight or so, there was malvertising injected from, you know, ads in ad brokers. But now we've kind of evolved where the actors are stealing, like, AdWords accounts for Google or Bing advertisement accounts, and they are very often putting it in those search bar, essentially searches where they're the top thing for the install of a particular app. And from that standpoint, you definitely want to try to use some sort of ad blocker, and that seems to be like the primary thing that I found in in environments in the last decade or so that really help on this. Also, you definitely want to have your users know where to go to install their applications. They should be basically going to their corporate app store, especially on their corporate machine. They shouldn't be allowed to install random things, just from things that they download from the Internet. Endpoint management solutions can obviously help with this, but, having that known place where where to go or be able to push apps to or official approved apps is very critical because that cuts this off from being an issue. Obviously, as well, if they don't have that particular app in the App Store, they might go and find a pirated version of it. That is also very bad. That's like the number one vector, basically, for these things to get installed for an Infostealers to come along for the ride. And, again, with Infostealers, they just upload that data to a c two. And a lot of times, they don't leave anything behind, and you won't really know that you're infected, especially if they have been ingenious with their deployment where it actually installs something at that same time. It looks like it worked to the end user. The other thing is the holistic identity lens. Basically, if you can have, visibility or as much visibility as possible into their an end user's past, present work, or personal data, this actually helps you. We have a product called, investigations that gives you a deeper dive access into a particular person and what they might use for passwords and things like that. That often is something I found even in my years of do being a sysadmin that comes back to haunt them where they use the same type of password. It's always their dog's name or whatever, and that actually could be used to attack the enterprise. Password hygiene, speaking of which, ensure passwords are not reused and similar with across the enterprise. This is something I keep seeing where, uniqueness is not necessarily enforced at a level where people are having to make a really unique password, and they could just depend different characters onto it. So make sure you do those password policies. And then, of course, MFA. MFA is basically the biggest issue. Security is an onion. You need these layers. Not no single layer is going to solve the issue, but having that extra layer there, I can't tell you how many times I've seen it save people. And then we wanna talk about some of the end user devices and personal devices. Again, pirating is really bad. This is something that I would definitely give education to your users that installing pirated software is almost always going to give you some sort of thing along for the ride. Otherwise, what's the incentive for actors to basically put this stuff together and send it out there? It's basically the number one thing. And, again, installing the ads or through ads is a bad idea. Please try to train users or remember, to understand that in if you search for something in the search bar, because everybody goes and types something, I wanna I want Zoom. Right? Go to the search bar and I type that in. Boom. You get an ad for Zoom install. Well, why not go to the real Zoom site or just type Zoom dot com in? Because that actually is the right way to usually define things. And then, again, as Damon was already talking about, like, skins for different software or rather games or cheats for games. I've seen in YouTube where different actors have actually put very intricate sort of, sort of, I guess, you could say promotional videos for their malware, where you have the ability to get a cool skin or essentially a cheat for a game, and then they go have you download from, what they call their deployment site or their install site. And, essentially, it's just, again, another malware thing. And then also separating personal and work, don't mix passwords. Once again, I think it's a good hygiene thing for everybody to get kind of in the habit of. Password managers are also pretty good. That's basically something that I usually recommend for everybody from a Hoho user. And, again, ad blockers are very good. Going back and keep driving on that one, I think that even though you do get blocked when you go to certain sites, remember, when people come back and say, oh, I I don't use that because I can't read my news articles. Well, you can make exceptions for that news article site, so don't forget that part of it. And then finally, MFA forever ever. If you can do MFA, do it. It's that extra layer that usually saves you. Wonderful. Okay. But we have some time for some live q and a. A few questions came in. There were some issues we're seeing in the demo on the Zoom video. So we'll make sure to send out a recording of the sessions so I can see the spy cloud demo in action with Compass and the endpoint protection integration. So go ahead and please ask your q and a. We have time with Joe and Damon, but there's two that came in. And the first one be for you, Joe. More about the evolution of info stealers and this cat and mouse paradigm. So how would that impact future prevention strategies if the technology is always evolving? So the Infosteeler, community or the these particular types of criminal ecosystems are usually trading secrets amongst themselves in order to get around any endpoints like Damon was referencing. So you really need a layered solution, and you need basically an idea that you will catch certain things at certain times, but you want to also be able to monitor and actually do your own recon instead of them doing recon on you. And, essentially, that's where we try to position ourselves to layer in there to be that check to prevent, those unique things that they basically come up with in the back end or trade amongst themselves from actually making it successful into your environment. This way, if they do get in, now we can actually tell you about it, and and you'd probably be able to go back and figure out why and then plug the hole. A few more live questions are coming in for Damon and Joe. More about infostealers. Any more tips for enhancing prevention and early detection? And then, some information about how to actually triage when you get an alert from your EDR that an infostealer is present. So as far as tips for best practices, I'm interested in your thoughts too, Joe. I mean, I think the reality is enabling your EDR to be as draconian and strict as possible, the less likely you will be to install malware. I mean, we all live in a in a company, and we all, you know, face the restrictions where the companies won't let us install software packages or run macros and those types of things. The more you can, you know, constrain what they're allowed to install, the better. And, you know, sir well, the better from that perspective. I can't, you know, I can't comment on the complaints you're going to get from, you know, from your users because we all face that too. You're also you know, the more that you can, kinda make sure that you're keeping up with the the updates and that you're responding very critically to any alerts from your centralized control that a system has been taken out of band. Right? I mean, I've I've I know from my experiences, I mentioned I've done a little IR. There was usually an alert that system x y z stopped responding to heartbeats from the centralized control of the EDR, and there wasn't necessarily a playbook to to deal with that, right, or to understand how to manage that. So things like that, really give you an opportunity to know that something something is amiss. It also means you're responding to a lot of things, like they went to a weird hotel and the Internet CO service sucked. And so, you know, there's a little bit of downside with with those as well. Any other thoughts there, Jim? Yeah. I I think, actually, you're definitely on the right track with everything there because the more you monitor the situation, you kinda get a pulse for things, and you want to use the, basically, the filtering in in your seam or sore in order to essentially get an idea of what really matters and what doesn't. Everything is gonna require tuning, but that's where the expertise comes in, and that's where the humans come in to be able to help with the automation to find the unique things, things that are novel, things that are out of the ordinary, because there's always gonna be what I call confirmation errors. Absolutely. And then to the the second part of that question, what are the best steps to triage and if a stealer threat that's been alerted by, by the EDR? I think we recommend you quarantine immediately. And then I think that usually, the next steps we would recommend are the same next steps that your EDR vendor is going to give you. Quarantine that device, scan for additional malware, look for the things, the indicators. Often, we see an Infos dealer will run and then delete itself, and leave no trace that it was ever there. But, yeah, that's hard to tell the difference between that and a very good maliciously hidden, piece. And so what you'll have to piece of malware. So what you'll have to do is, you know, you'll get to the point where you've run all the tools and you've made sure that there's nothing there. We always we always recommend that you, of course, you have cleaned the system. If you can go to a full fully clean system, that is recommended as well. But then you do need to take the next next steps, which are understanding the things that were stolen by that by that info stealer, making sure you've reset all the related passwords, make sure that if they stole things like Coinbase seed phrases or any other tokens that, yeah, that are that are in there, that you've reset those and that you've also reset session cookies, that could be used to access all of your enterprise accounts as well. So all of those are great steps. There's automation that could be added for many of those, for many of those issues, to help you do that in an auto to do that quickly. Yeah. I I also want to add in. You can also leverage things, like network access control. If you actually have them on your campus, you can follow the OSI model. And what I always do is start at the physical level. If I can, I'll just shut the port off. And that way, I know they're not gonna be talking anymore. But I would also do other things too. Like, if they're outside the network, then I would revoke all their cookies, and all their logins would change and immediately be locked. So there's things like that that you can do, and you can kinda go up the the level depending on what kind of controls you have available. We have a few more questions. Damon, you mentioned cookies, and, this might ask, what are you seeing in terms of the amount of stolen cookies and stolen passwords and how they're being used by bad actors? Yeah. Excellent question. You know, if you just looked at the proportion of the stolen cookies stolen, versus passwords, it's easily ten x the number of cookies are stolen on a on a given device. And I don't have that specific number, but it's way more than ten x. We're getting on a single device, thousands of cookies are stolen that give a lot of information about that user's behavior as well as, often cookies that can be used to bypass multifactor and to bypass all these these great improvements we made in, passwordless technologies. And so, but I still think so I don't have specific numbers for you, so I'll give you an anecdotal, you know, my view of it. And, Joe, you should offer your opinion as well. Right now, we still see passwords are still the number one vector. Right? They still work way too well. And then social engineering to get through MFA if it's in the way, but there's still so many places where MFA is not implemented, not implemented correctly or fully. Passwords are still the key vector. We'd love to say it's not the case, but, I mean, it's very much the case. Now for things like accessing financial systems and for, you know, very high value targets, we do see the the movement of actors to start using cookies. And so we have one customer that, you know, they reset thirty thousand cookies a month, just alone on the on the knowledge that they have active they found active cookies within their, in that case, consumer facing application, but you could do the same for many enterprise applications. And so we see this as a growing vector. We don't have numbers, good numbers to say whether, you know, what the proportion is of cookie usage and session hijacking is versus, versus credential usage. Joe, did you have more thoughts? Yep. I think, the other thing too is if you have control of how the cookies are issued for your internal enterprise apps, set time to live on them. Make sure that you basically make them expire or become invalid quicker. It may be inconvenient for users in some instances, but it also may save you because sometimes it takes time for the actor to actually figure out what they really have and then actually to bang on it. So if you have it expire before it's actually valid, that still is something that's going to save you in the end. And that's also why the passwords are more effective because peep people basically are looking at the password still as the first thing because it doesn't have that time based sort of thing where it has a time to live. Yeah. And the next couple of questions, Joe, are about, recommended ad blockers. I don't have specific recommendations here. I haven't looked at enough. I just had the one that I use. Do you have specific recommendations? Yep. MuBlock, light origins, is what I tend to use in a lot of cases. And what I do is I turn it up, to the max amount that they have for the support or add other, different lists to it. But pretty much the list that come with the default are pretty good. The only thing that's bad about the the light version of it is that it comes at a lower sort of level. So you there's like a slider where you can turn it up as you click on the icon as you for your extension. And that slider, if you turn it up to the top, it does a really good job, but it starts at, like, the second rung, and that's kinda, and so I I think that, there's a lot of, back and forth with the different, advertisers out there where they're trying to push back on, you know, not being, able to have these sort of things. So, again, you can always click on it, make an exception for that website, and get past it from that. But, definitely, MEW block origins lite is where I bet. Alright. Okay. Wonderful. Well, thanks for joining, Damon and Joe. We appreciate all the knowledge about malware and endpoint protection. We'll send out a recording of the session if you wanna see a bit more about the topics or watch the demo again. But, again, please reach out if you have any more questions about everything we covered today, or you wanna schedule a personalized spy cloud demo that talks more about your organization's data and your own domains. But, otherwise, we're running a a offer for the next few months. So anybody who wants to go ahead and purchase our enterprise protection solution that includes the Compass product that Damon demoed, we're eligible for discount before the end of June. So please reach out with more questions, and thank you both for joining. Thanks, everyone. Appreciate the Thank you. Appreciate your time.
- Video
Minding the Malware Gap – Identity Threat Protection Beyond The Endpoint
This webinar explores the latest malware trends uncovered by our SpyCloud Labs team, and how these insights help security teams enable proactive measures to secure corporate access.
- Video
Accelerate Cybercrime and Identity Threats Investigations
This demo/webinar shows how SpyCloud Investigations revolutionizes your analyst and investigators impact.
Hi! Thanks for joining us! My name is Alex Ash and I’m the Growth Marketing Manager here at SpyCloud. Today we’ll be joined by SpyCloud Labs researchers, Ashley Allocca and Kyla Cardona to discuss The Illicit Chinese "Pantsless Data" Trade, Uncovering Chinese-language actor TTPs for data access, acquisition, and exfiltration. As a refresher, SpyCloud Labs is a focused research group dedicated to uncovering and analyzing the most intricate cybercrime patterns from the criminal underground. They nerd out on all things breach, malware, and threat actor-related – and are hellbent on making the internet a safer place for all. If you want to learn more about SpyCloud Labs, you can visit our website on our resources page - I will post the exact link at the end of our presentation. Okay - a little bit of background on our amazing speakers: Ashley has a background in cyber threat intelligence and holds an M.S. in Cybersecurity from Fordham University. Here at SpyCloud, her research is focused on emerging threats within cybercriminal and illicit communities, Kyla is a U.S. military veteran from the Air Force, Marines, and Army, and holds a BS in Computer Information Systems and multiple cybersecurity certifications. Kyla is a Staff Security Researcher at SpyCloud, with a focus on cyber threats in China and other cybercrimes occurring within deep/dark web illicit communities. Alright, today we will be covering Chinese cybercrime slang terms and keywords, data leaks perspective: western actors vs. Chinese threat actors, Chinese cybercriminals and their TTPs, Chinese data leaks and finally, everyone’s favorite part - the takeaways. And with that, I will hand it off. Thanks, Alex. My name is Ashley Allocca like Alex mentioned, I’m a Security Staff Researcher here at SpyCloud. And we just wanted to start off by quickly defining a few acronyms that will pop up throughout the presentation. The first is TTPs, which stands for tactic, techniques, and procedures, and we will use this phrase to refer to methods we observed by Chinese cybercriminals. APT refers to advanced persistent threat groups, which encompasses state sponsored groups. This presentation will look at Chinese-language cybercriminals who do not have any obvious ties to state-sponsored groups but we just wanted to define that up front. SDK refers to software development kits, and is a tool in the data exfiltration arsenal of these cybercriminals. DPI refers to deep packet inspection, and is both a holistic and invasive tool used to categorize network traffic between end users and telecom companies. Like SDK, DPI is used in data exfiltration efforts. MD5 is a hash function used to encrypt data. In this presentation it will refer to decryption services offered by Chinese-language cybercriminals. SGK which refers to Social Work Libraries, which are functionally data repositories. And we have a couple of slides that will dive into that later on in this presentation. There are words used to describe different elements of the illicit data trade and are specific to public discussions of and advertisements for data in Chinese Telegram channels. We’ll start here with pantsless data. The phrase “pantsless data'' is commonly used in Chinese cybercriminal communities to refer to hacked databases. The origin of this phrase comes from the Chinese homophone for “library dragging”, which is the term used for hacking sites and exfiltrating their data. Library dragging is pronounced tuwow dong kwoo, and it’s homophone tuhwow duwow koozie, translates to “trouser removal” or “to take off one’s pants.” Trouser removal will often refer to the total compromise of an individual’s data or hacking of an entity. There are other iterations of this phrase that include using the Chinese word for “pants,” which sometimes refers to leaked personal information, or using the word “naked” to identify a hacked entity. Other keywords and phrases that are commonly used in the illicit data trade ecosystem include: “Spinach”, which refers to data originating from online gambling, casinos, and to the “chess” industry. Chess is often used to also refer to the lottery and gambling data sets. It is possible that Chinese actors need to use code words or euphemisms, like spinach, when referring to lottery games or online casinos as gambling is illegal in China. The next phrase is “Angels and Demons” which refer to China’s Public Security Bureau, which is their law enforcement entity, or bank employees or individuals affiliated with banks. This phrase highlights the dichotomy of the public opinion of those affiliated with the police and banks, based on their standing in Chinese society. Individual cybercriminals will use this term to refer to either data belonging to the police or financial entities, sort of based on their experience or where they are from. Next is “Red Hat Hackers” and this refers to hackers and cybercriminals who are loyal to the People’s Republic of China. The use of this phrase does not specifically imply an affiliation with state-sponsored actors. Next is “selling dog meat by hanging a sheep’s head” - it's a colloquialism used to refer to data brokers, referring to their deceptive nature. This term may also be used to describe “second hand” or low-quality data, as it may be being passed off as higher value data. And finally we just wanted to point out the use of the English-language phrase “CVV and POS” which is commonly used to advertise or refer to financial data and financial data theft services. So now we’ll take a look at Chinese actors versus their western counterparts. Comparing data leaks between Chinese cybercriminal communities and their western counterparts can help establish an understanding of the inner workings of this illicit data trade ecosystem. Both Chinese-language and western cybercriminals utilize Telegram to illicitly sell, buy, and trade data. However, Chinese cybercriminals are much less likely to repost a specific file when advertising their offerings. This is due to the high value that’s placed upon “real time” data, which is supported by an actor's ability to maintain persistent access to compromised entities. In some channels, actors will leak data samples daily, and they’ll even name the file with that day’s date to highlight the freshness of that data. More information regarding these methods to exfiltrate this data will be explored on subsequent slides. Conversely, in Western channels, databases are generally shared multiple times between channels and actors, with actors incorrectly claiming that a data set originated from them. There is definitely less of an emphasis on first hand, fresh data compared to Chinese channels. Like I had previously mentioned, Chinese channels put a great deal of importance on “real time” data. Depending on the data type and where it originated from, actors can consistently acquire requested data between one and three days from the day their customer placed an order with them. There does not appear to be a similar market within western cybercriminal communities. Finally, like their Western counterparts, Chinese cybercriminals maintain public and searchable data repositories made up of data from publicized breaches. In Chinese communities, these are generally referred to as social work libraries - often abbreviated as SGK. In the West, sites like Search[.]0t[.]rocks offer similar services by aggregating mostly publicly available leaks, and allowing individuals to search for records by various data types. We’ll explore SGKs further in subsequent slides. I will hand it off now to Kyla. Thanks Ashley. I’m Kyla and let’s dive in to talk all about Chinese threat actors! These actors are primarily Chinese-speaking because they use slang terms to refer to data and data exfiltration methods, as well as use Chinese-language emojis in group chats and engagements. They are also deeply concerned about the recent Chinese New Year holiday, as there was a significant decline in data publishing during this time. Some actors also posted “away” messages claiming that they will take a break and start again in the New Year. These Chinese Actors are found on mostly Telegram channels & X, however they also operate on clearnet forums and underground websites, such as vastdata, datahive, free market, royal city and more. Their X accounts are mainly used to advertise their data theft services, with common keywords and hashtags such as SDK, DPI, SMS Hijacking, penetration services, take pants off data, pants removal data, overseas data, and infiltration. These specific methods of exfiltration will be explained later by Ashley. They may also use marketing and telemarketing to refer to their services to obfuscate their true business motive, which is data theft in the illegal data trading industry. Later, we will show you examples of their X accounts, in which they showcase both SDK/DPI data in spreadsheets with redacted information and tend to refer to their Telegram accounts and channels to find more. Chinese Actors have claimed that they use Telegram for privacy purposes as they believe the “Internet police” as they call it, for domestic Chinese platforms, are heavily monitored and controlled. On Telegram, Chinese Actors use similar keywords in their channel descriptions and group chats as those found in Twitter. Some of the Chinese Actors who publish data refer to themselves as black hat hackers, red hat hackers (which means they are loyal to the People’s Republic of China as Ashley mentioned earlier), and dark web hackers (as these are commonly found in their names and channel descriptions). However, not all Chinese cybercriminals self-identify or claim to be hackers. Some people refer to themselves as salesmen, data brokers, or even reptiles (because they use crawler methods to exfiltrate data) and do not claim to provide the penetration services that hackers do. Chinese Actors operate in many ways: they may work individually, have their own teams, or be a part of a data company. The individual operators may engage in data trade with other hackers and also sell data for their own profits. Those that operate in a team have a “sales” team that take orders, usually through Bill of Lading forms, from customers interested in purchasing stolen PII and credentials. Usually, they have a Bill of Lading template for their orders and also have a minimum order, for example of 5,000-10,000 records. The “tech team” are allegedly the people that manage the data access and are experts on technological tools used for data exfiltration and collection. Some Chinese Actors work for quote unquote “companies” that specialize in data exfiltration, collection, packaging and publishing. Analysts at SpyCloud have used social engineering methods to engage with Chinese-speaking threat actors as well as have done extensive research in finding that these Actors are claiming to have insider access to “first-hand” or “real-time” data as Ashley mentioned earlier. Some Telegram channels publish a library list of apps they claim to have access to. This so-called “insider access” could be in the form of backend permissions to apps or websites or have contacts that have direct access to the data. However, if a customer specifies a target that is not on their library list, some Actors are willing to provide penetration services for the target app or website for upwards of $12K per target. Lastly, the Gray/Black Product Industry is a slang term and another name for the illegal data trading industry or data theft industry, which encompasses the entire Chinese cybercriminal ecosystem of data exfiltration, data collection, data sales, and data trading. Let’s take a look at their Telegram channels. On the left is a screenshot of a Telegram channel ran by a Chinese Actor that publishes and sells infiltration data (also known as penetration data), dpi data, and sdk data in the following industries: spinach, lottery, financing, loans, social security, marriage, students, parents, car owners, medical care, air tickets, and domestic and overseas data. On the right is a screenshot of a Telegram channel ran by a Chinese Actor that publishes and sells “real first-hand” operator sdk/dpi/sms data, this means that they are claiming to have insider access to various types of “fresh” data in the following industries: sports, spinach, games, students, medical care, and online shopping. The keyword of “real first hand” operator data reinforces the importance of the “real-time data” to Chinese cybercriminals that Ashley has mentioned earlier. Chinese actors categorize and organize their data differently from Western Actors. Industry-based data is another way to say data that is organized by sector. Usually, this data contains domestic PII. This term is also used interchangeably with “first-hand,” “fresh,” and “real-time” data because of the short time between data extraction and delivery. Actors organize these “data files” by sector to obfuscate the targeted companies and websites, essentially to make it harder for law enforcement officials to track them down so they can maintain access to the victim entity. Ashley will go more in-depth on industry-based data in subsequent slides. Second/Third hand Data refers to data collection from other methods, such as penetration services or hacking tools. CVV/POS Data is a slang term used to refer to foreign financial or credit card data as mentioned earlier. The targets in the Chinese cybercriminal Telegram channels are usually global users. SGK is another term for social work library, or social engineering database. This so-called “library” or “database” is a collection of leaked databases that a hacker or hacker groups have compiled and made searchable for users. Lastly, combolists are also used by Chinese actors. They usually contain email addresses and passwords. With extensive research and testing, analysts at SpyCloud have found that the combolists released from these channels are mostly derived from Collections #1-5. Collections #1-5 is a Megabreach from January 2019, with billions of email addresses and passwords. It was also known as the “breach of breaches” as it was a collection of credentials from numerous websites. Chinese actors tend to repurpose, repackage, and rename these combolists and sort them by country when they publish them. So let’s take a look at some more screenshots. The first screenshot here is a Chinese actor on X offering “operator” SDK and DPI data quote unquote “directly from the source” which often means they will provide first-hand or real-time data and they have “insider access.” The second screenshot is a Chinese Actor on X masking their data theft services by using the phrase “telemarketing data.” However, they continue to use other similar phrases to Chinese Actors, such as “first-hand accurate data” and also offer SDK, DPI, MD5, and SMS hijacking services. Ashley will take a closer look at these services in the next slide. The third screenshot you see here is a Chinese channel on Telegram who refers to themselves as an “overseas data professional penetration master team” claiming to have “many years of penetration experience.” They also claim to focus on overseas markets, global investors, currency circles, overseas Chinese data, gambling, shopping and all other data resources. The fourth screenshot is a Chinese actor on X offering SDK, DPI, SMS Hijacking, penetration data extraction and various types of “pants removal” which again means for a hacker to invade a target website or app and steal all users’ information and the database. I will now hand it off to Ashley. Thanks Kyla. So we touched on some of these methods of exfiltration already, so now we’ll get a bit more into the weeds. The first method we’re going to take a look at are SMS-focused attacks. SMS-focused attacks can include SMS hijacking, smishing, SMS reply attacks, and SMS sniffing attacks. These attacks are sometimes coupled with various social engineering techniques in order to trick victims into disclosing sensitive information. For example, in SMS sniffing attacks, actors may use pseudo base stations, which are akin to mini cellular towers, but leveraged for malicious purposes, in order to intercept data. These pseudo base stations can also be used to disseminate smishing messages with malicious links that also lead to further data collection. DPI - the next method, like we had mentioned in the beginning of the presentation stands for Deep Packet Inspection, and it’s a legitimately used tool by telecom companies to manage network traffic. DPI is holistic and invasive, like we mentioned, so it can accurately look at network traffic in order to best identify and categorize it. Threat actors who claim to have direct access, sometimes through signed contracts with telecom providers, perform data collection when users access a website/app on the network of a Chinese telecom provider. Details of these alleged signed contracts have not been observed publicly at this time, or have not been made public at this time, so the inner workings of these partnerships are unclear. Leaked DPI databases tend to include sensitive information like phone numbers, location information, IP addresses, and URLs. The third method of data exfiltration we’ll take a look at includes the use of Software Development Kits. Software development kits (SDKs) are legitimate packages of software tools bundled together to be used by app developers. SDKs are often built separately from the applications themselves, leaving room for malicious actors to produce their own SDKs to shop around to developers. These Chinese cybercriminals have been observed advertising their SDK data with “t+1” and “t+2” attributes. These attributes likely indicate the amount of time in days after the initial leak date (t) that the buyer will receive their order of the exfiltrated data via SDK exfiltration methods. SDK is considered one of the least accurate and least timely exfiltration methods. This could in part be due to various reasons like the fact that end users may not opt to share PII with an app at all, or they may knowingly input false information to protect their identity. This will obviously impact the fidelity of the exfiltrated information, which data brokers understand. SDK data also most likely passes through several hands before getting to the end customer, which further dilutes the timeliness and accuracy of this data. Additionally, actors may be poisoning and repackaging open source SDKs with vulnerabile or malicious components, which would allow them to maintain access to the SDK but it could also lead to supply chain attacks, as dev tools do persist as an attack vector with supply chain attacks. SDK data may include phone numbers, genders, ages, and location information, and a lot of SDK data tends to be domestic PII of Chinese citizens. The fourth method of exfiltration is referred to as MD5. Although actors claim to provide already desensitized and unhashed data, they can also provide decryption services if a customer has procured hashed data, ostensibly most likely from another source. This is another way that they can make data available through their de-hashing services. They may also advertise their MD5 services as an add-on to their data exfiltration. And finally: penetration services. Penetration services refer to data that is procured using third-party hacking methods. Actors will target vulnerabilities in applications or websites they do not otherwise have access to. Kyla will cover more on these services later on in this presentation. So here we have two examples of what this exfiltrated data looks like, and these files have all been publicly shared in Chinese-language Telegram channels. So the first screenshot is a file called “Malaysia Loan,” and includes sensitive data like applicant names, email addresses, and gross incomes. This database also includes browser information and IP addresses. Based on the information collected, it is possible that this information was exfiltrated using DPI methods, however this has not been confirmed by the original poster. You can see here under the bank name column that it includes the names of several Malaysian banks so it’s possible that this data was collected while individuals were attempting to connect to the websites of these banks. The second screenshot is from a sample file entitled, “China Bank.” This data includes names, unspecified certificate numbers (which have been obfuscated), genders, birth dates, location information, phone numbers, and card numbers. The original poster of this data did not publicly confirm the exfiltration method, though it appears it could have been collected using SDK methods. This top screen shot is called, “South Korea PII,” so while it appears this is called “South Korea PII,” it appears that the location information is actually based in Singapore, which may indicate that this is data of Singapore-based users, possibly of a South Korean app or website. Like we’ve been mentioning, these files are often named something ambiguous in order for these actors to maintain access to the files. And the final screenshot at the bottom exemplifies what a sample file looks like posted on Telegram. This sample is allegedly of data from China’s Provident Fund. The poster of this sample alleges that they can obtain provident fund data from different regions in China. This data was likely collected using some sort of first-hand exfiltration method. Like Kyla mentioned, actors will target certain industries or entities in order to extract specific data types. While some actors specifically target overseas data, much of the observable targeting results in the exfiltration of domestic Chinese data. So the first screenshot to the left shows a file ambiguously called “advanced units - sample” and contains valuable data types, including full names, phone numbers, national ID numbers, ages, and physical addresses. The second screenshot is a sample file called, “Chinese Orders.” Order and product information are also commonly targeted, as they can include sensitive information like shipping addresses, phone numbers, and shipping numbers. Data brokers and their customers will additionally seek out PII like email addresses, usernames, passwords, messaging app accounts, job titles, salary and company information, device information and location information. Some of the data types may have less value on their own, but become increasingly more valuable combined with other data types. First-hand data is regarded as the most accurate data type among Chinese-language threat actors. First-hand data tends to be broken down by industry and is collected generally via SMS, SDK and DPI methods. Chinese cybercriminals tend to name their samples and breach files by sector, and will also use the phrase “industry data” or “industry base data” when referring to these types of offerings on Telegram These offerings can include: online shopping data, online loan information, insurance information, including medical insurance information from the Chinese Social Security System, education information, including details on students,their parents, teachers, and even exams. Data from China Provident Fund and housing fund, like we saw on the last slide about the China Provident Fund and finally, this can include financial data from banking apps or internal bank employees. This data, as previously mentioned, is often referred to as “angel/demon” data. On the slide is a screenshot of a sample file shared on Telegram. The file is called “vietnam bank loan numbers”, and is representative of how similar data sets are advertised. It might include a location, a sector - it’s pretty vague nonetheless. And I will kick it back over to Kyla. Thanks Ashley. So Chinese actors use the term “penetration services” or “infiltration services,” to describe the data they have exfiltrated using hacking methods. But they also offer it as a service for apps or websites requested by customers that they already don’t have access to. A few penetration tools that these actors claim to use are crawlers, fraudulent (trojanized) applications, scripting tools, SQL injection, and phishing kits. They usually use these terms to describe their method of exfiltration for overseas or foreign data files. After careful observation by analysts at SpyCloud, there are times when the overseas or foreign data is unique to the Chinese Actor’s platform or channel, but there are other times when they are originating from a Western Actors’ platform. This means that they do repost data files from Western actors' platforms, so when this happens, the Chinese actors can repost the file or repost, and reduce them in size, to sell the full file for profit. After extensive research and engagements with Chinese Actors, it is important to note that these Actors find the least amount of confidence in this type of data collection method as they believe the data can be forged and altered, and it is usually not extracted in near real time (such as when compared to their other data collection methods that Ashley mentioned earlier). Additionally, second-hand/third-hand data also refers to data that has been pre-parsed and organized by Chinese actors, as this type of data is not usually found in its raw format. Let’s take a look at the screenshots here a little closer. On the top is a screenshot of a channel run by a Chinese Actor on Telegram, claiming themselves to be a “hacker data vendor” for overseas and domestic data. They are offering data in the following industries: recruitment and job hunting, car owners, high-tech careers, banks, currency circles, corporate companies, overseas Chinese, dating, and other data resources. On the bottom is a screenshot of a channel ran by Chinese Actor on Telegram advertising their various services - domestic data, bank-wide resources, and penetration data in the following industries: finance, medical care, online loans, financial management, credit cards, SMS hijacking and interception, provident fund, state-owned enterprises, teachers, students, online shopping, and SDK/DPI penetration. As you can see, there is a pattern to what these actors are claiming to provide as their service and what data files they all tend to leak. As previously mentioned by Ashley, CVV/POS is a slang term used to refer to foreign financial or credit card data. The targets in these channels are usually unfortunately global users. Most advertisements from these channels highlight the availability of US and Japan credit cards. Threat Actors also have sources for checking if the credit cards are “LIVE.” However, credit cards that have been validated (meaning they have had a small pre-authorization charge run against it) will cost more than the cards that have not been validated. Credit card data is leaked in various ways by Chinese actors; some with just the financial details, while others publish FULLZ information. Fullz data is a slang term for full information, and is used to describe stolen identities and credit card information. This can include full names, full physical addresses, phone numbers, credit card information, expiration code, and the cvv. Now let’s talk about global targets. Domestic financial material is not popular in this data collection method, as Chinese actors claim that this financial data can usually be exfiltrated through the exfiltration methods of SMS/SDK/DPI that Ashley has mentioned earlier. Additionally, they claim that domestic credit cards generally require more information such as payment passwords and SMS verification codes and even banking information for larger purchases. All in all, they’re just saying that it’s harder to use it for domestic citizens. However, Chinese actors claim that for foreign or overseas credit cards, there is no multi-step verification of passwords or sms verification to make a successful purchase or transaction. They believe that in foreign countries, (in most cases) a card number, name, expiration date, cvv, and zip code is enough to make a purchase (but this usually depends on the payment gateway). Their methods of attack for this type of data collection are credit card sniffing and phishing kits. These phishing kits are shared in private platforms. However, they also have public clearnet websites that they use for phishing TTPs such as cvvboy and haocvv. Let’s look at telegram channels next. CVV/POS data can be posted in Telegram as both downloadable files or in the body of messages in the group chat or channel. If we look at the screenshots here, the top two screenshots shows the data found in the body of the messages posted inside the CVV/POS channels, which include: Credit Card Number, CVV, Expiration Date, Full Name, Zip Code, Phone numbers, Email addresses, Card Type (Credit, Debit), IP address, Phone & Browser Information. The third screenshot shows a downloadable file posted in a Chinese Telegram channel. The fourth screenshot shows the same, but the last screenshot shows the credit card data found inside the file titled 2024.2.6 - the file shows credit card numbers, expiration dates, cvv codes, card type, country, and if the card is live (or active), SGK is a Chinese term for social work library, or social engineering database, as mentioned earlier. Chinese actors create their own centralized repositories of leaked PII, therefore, these repositories consist of data they have sold in the past, or data they have found or exchanged with other hackers. An SGK can be owned by one hacker, and other times it is owned by a group of hackers. Another motivation for hackers to publish data for free is for this purpose - to exchange databases and build these platforms. These libraries require users to register with an email address or username and password. Registered users can search through the dataset for various records, as it contains detailed personal information. The searchable fields include: QQIDs, mobile phone number, ID number, email address, Weibo ID, household registration, and more. Most SGKs offer a tiered access system: free users (meaning users who have registered but have not deposited any funds or bitcoin into their account), are able to run search queries but only receive a limited amount of results or obfuscated results. If the user wants more results, they must be willing to pay. It is important to note that SGK platforms are not only another money-making scheme for Chinese actors, but they also enable other Chinese actors to collect relational data to perpetuate other types of fraud and cybercrime, such as doxing, support phishing campaigns, social engineering, malicious marketing, identity theft and financial theft. These SGK libraries can be found on clearnet websites, underground websites, Telegram channels, and Telegram bots. For Telegram, there are two types of channels: the first is an SGK telegram bot where a person run search queries, the second is a channel that contains forwarded search queries from SGK bots, and these channels posts PII in the body of the Telegram messages. Let’s take a closer look at the screenshots of the various SGK platforms. The screenshot on the far left is a SGK telegram channel message that was forwarded from a SGK Telegram bot, The fields in the example post are the following: name, ID number, telephone, mobile phone location and service provider, date of birth, nationality, gender, landline number. As you can see that is very detailed information on individuals. The screenshot with multiple links on the far right is a clearnet SGK platform that leads to various websites for different search queries, such as household registration, delivery information, WeChat and Weibo information The screenshot with the text ‘Privacy is Dead - get over it’ is a clearnet SGK platform with searchable fields such as QQ ID, phone number, ID number, email address, and Weibo IDs. The screenshot on the very bottom is a clearnet SGK platform where you can search using the following fields: QQ ID, mobile phone, password, email address, mobile phone number, ID card, name, Weibo UID, and also specify if it is a comprehensive query or a group relations one. As you can see The Chinese Cybercrime Ecosystem is unique and different from that of the Western ecosystem: Western platforms are missing a substantial amount of data leaks from Chinese platforms, for both domestic Chinese data and overseas/foreign data that Chinese actors have targeted themselves. Chinese Threat Actors use generic names for their data leaks and organize them based on industries. Their purposes for this tactic is 1) to obfuscate the target entities, 2) to make it harder for law enforcement officials to find the data and then track them, and 3) to enable them to maintain access to the data. As Ashley mentioned earlier, Chinese cybercrime actors prefer fresh, first-hand, real-time data extracted from the source, or as close to the source as they can get. This type of data is of higher value and accuracy to Chinese actors, rather than data extracted from penetration services and hacking tools, which they find of low confidence, value, and accuracy. Chinese Actors publish files of all sizes, as “real-time data” can have a small or big range in the number of records, depending on the time of extraction. Some actors purposely reduce the file size and publish sample files as their “proof” or “vouch” that their data theft services are credible, with the ultimate goal of selling the full size data file, Other Chinese actors post full-sized files for data exchange and other malicious purposes. The data that analysts at SpyCloud are recapturing from these public and private Chinese cybercriminal platforms are tangible and actionable. They contain sensitive personal and financial information, not just from individuals residing in China, but also from around the globe. Going to hand it off to Ashley. Thanks Kyla. Before we wrap things up, we wanted to leave you with what we think are a few important takeaways. The first is the threat posed by Chinese illicit data trade, the Chinese cybercriminals access to data and exfiltration of this data extends beyond China. Anybody with a Chinese SIM-card that connects to a telecom provider is vulnerable, so this could extend to tourists in the country who get a Chinese SIM-card to put into their phone to have better connectivity throughout their travels. Additionally anybody that has downloaded an app with a malicious SDK is vulnerable, and the use of second-data and penetration services also extends this threat beyond China. The second point that we’d like to drive home is that illicit data trade occurs beyond Telegram, so while our research for this specific presentation honed in on Telegram and X-based cybercriminals, and their breaches, the Chinese illicit data trade extends to both clearnet and tour-based forums and markets. The third point we’d like to leave you with is whether these Chinese cybercriminals are connected to known APT groups. When people hear about Chinese cybercrime the assumption generally tends to be that a state-sponsored group is involved, however, the long and short of it is that we are not entirely sure whether there is a connection between these Chinese cybercriminals that we’ve discussed in this presentation and APT groups, although there is really no overt indication that these groups are affiliated or connected in any way. Additionally the primary motivation of these Telegram actors appears to be financial, whereas APT groups are primarily motivated by espionage. And finally, is the strong emphasis on real-time data. What is perhaps one of the most material differences between the Chinese illicit data trade and the Western data leak market is the emphasis on real-time data. It exhibits that these cybercriminals have consistent access, seemingly vast amounts of sensitive data, and they prioritize timeliness and accuracy of this data. No such prioritization of this data is as obviously apparent in Western cybercriminal communities so it’s very interesting that there is such a heavy emphasis on this real-time data. And on that note, we’ll conclude our presentation. Awesome, thank you so so much! That was so informative. Thank you for all your hard work and research and thank you for joining us. If you would like to hear more from SpyCloud and SpyCloud Labs, you can email us if you have any questions. You can visit our webpage - as promised, there is the SpyCloud Labs specific webpage. You can sign up for our newsletter - we send it out once a month and it will always include updates and any new SpyCloud Labs research. You can connect with us on X, aka Twitter @spycloudlabs and finally, if you’re curious about what cybercriminals might know about your organization, you can use our free darknet exposure tool at Check Your Exposure, which recently had some updates, so make sure to check that out. And once again, thank you so much for joining us and hopefully we’ll talk soon.
- Video
The Illicit Chinese “Pantsless Data” Trade
Hear from SpyCloud Labs researchers how Chinese cybercriminals are accessing, exfiltrating, and trading vast amounts of PII, with international impact.
Hi, everyone. Welcome to our webinar access granted, the reality of compromised credentials in a passwordless world. Let's get started. Okay. So on this call, we're gonna have Chip Witt, who's our VP of product management, Trevor Hiligloss, our director of security research, and I'm Collette Pameshek, director of product marketing. Today, we're gonna go over what we'll cover. We'll give you some context on who spy cloud is and what our overall mission is focused on. Covering some trends in the password problem, the added layers of authentication, and overall what that path to password list looks like. And then we're gonna go over myth versus reality and go into detail on what you need to know about that landscape, the evolution of passwords, to help you for cyberattacks and essentially fortify your enterprise. So at SpyCloud, we're really focused on solving a big problem. And what it is is that criminals profit from stolen data about your organization, about your customers, and it's a huge problem on a scale that's really hard for teams to digest and manage on a daily basis. Our mission at Spy Cloud is to stop that from happening to really ensure that we equip you and your teams with the information context insights you need to protect your business from malware infections or ransomware attempts and just data breaches by taking our recapture data and turning it around on the criminals. So this enables your teams to act quickly whenever enterprise or customer data is compromised, and you can get ahead of these cyber attacks. And what that looks like, it's really more than just threat intel. With Spy Cloud, what we're looking to do is introduce cybercrime analytics, where all of our products are built around our cyber analytics engine. And it's really there to address the problem set that you encounter when you're trying to use lower or core darkenet data It's not just to learn or gain context, but to really take action and protect your business when it actually matters the most. So our engine here on the left side is where all of that recapture data from all of those layers of the dark matte is collected. It's then curated. It's enriched and analyzed. To drive our products that automate protecting your business so you can take action on that data. And one of the reasons that other vendors don't work with some of that lower or core layer because of its raw data formats. It's overwhelming and it's not even unstructured data. It just comes in a variety of broken databases or broken data structure and often in binary or mixed formats at massive scales. So our engine specializes in figuring out when that raw data is. And how it can be used to protect you, parsing, curating, so then can be ingested into our core data set. So our engine also invests heavily in cracking and analyzing passwords and other PII assets and that results in almost ninety percent of passwords being provided in plain text in our products and access to these data elements allows us to perform analysis and create relational links between those different elements we have producing actionable insights to protect your business. And then if you look on that right side of the slide, This is essentially the output of our engine, the use cases that we enable for enterprises, and our engine is leveraged by our products and the APIs in automated protection use cases. And this includes everything from ransomware protection, account takeover protection, online fraud, and we also support cybercrime investigations with access to our dataset. So overall, Spy Cloud is really focused on leveraging this analytics engine that's built to provide you with the industry's deepest and broadest data set that is collected extremely early in that cycle of crime and that is automated to actively protect your business. So let's dive into the core premise of the webinar. We're gonna kick it off with the past program, which I'm gonna pass over to Chip. Yeah. So the password problem, I I think one of the things that's really interesting about the password problem is it probably more than anything provides really interesting insight into the human condition. One of the things that you see, in terms of this because there's a human portion of it. That's very, very important. There's also the criminal ingenuity focuses on those human weaknesses. Do we talk about when we talk about human weaknesses? Well, first of all, users tend to prioritize ease of use and convenience over security. And so they choose passwords that aren't necessarily the smartest passwords. They're usually linked to things that they know and can remember easily. Even if they have, a recurrent password reset, hoisted upon them as part of, enterprise policy. They tend to pick passwords, and lists of passwords that they can continue to reuse over and over. That's where password reuse comes in is it's not just in the enterprise environment that people tend to reuse those passwords. They have over two hundred online services if they're average people. That they're logging into an authenticating most often, most frequently by way of password. And so remembering passwords, if you change them and make them unique for every distinct site, becomes a problem the headspace can't deal with. Humans aren't don't have that kind of capacity. So you see a seventy two percent password reuse rate is what we saw in breaches over the last year. And that's just because humans typically will reuse passwords across all the sites. My favorite, kinda throwback to remember is the LinkedIn breach. Everybody and their brother got within the LinkedIn breach. They all got the word from LinkedIn to change their passwords, changed their passwords, But what they didn't do is change it on the Facebook, the Twitter, the Instagrams, and all the other services on which they were using that exact same password. Criminals knew this and leveraged it by virtue of just sort of adapting to that particular problem. People also tend to use things that are socially relevant, and that's actually one of the really interesting things. We do a password exposure report every year, and it shows that people use real life events to make commentary on their particular stance on those issues or their favorite sports or entertainers, as part of their password. That's interesting considering that nobody else should know your password. So why would you use that as commentary? But nonetheless, we see this habitually, in human behavior. So very, very important to recognize that password fatigue is inescapable. Because of the pervasiveness of the need for passwords, but for criminals, this this human element is of tremendously high value, and they leverage it at every turn to pull out the low hanging fruit and make good use of that profiting off of that that that particular problem with with people's habits. Okay, guys. So what about password managers? So after hearing that ship, I think that the natural next step is, okay, we'll we'll use a password manager. And just to kinda level set before I can get into this slide, That's fantastic. Password managers are great. Right? With Spike Cloud, big fans, anything that's gonna make it harder for the adversary, impose kind of risk in this case. We'll talk about the consequences later, but that's that's good. Right? Those are good things to start doing. The important thing to note there is it's not foolproof. Right? These these, these things that we come up with to protect our enterprises, to protect ourselves, They're fantastic when used properly, but our research has shown that, a, they're not always used properly. And, b, even when they are used properly. There still are vulnerabilities that exist and need to be managed. So this, you know, up here on the screen, the hundred and eighteen thousand master passwords that we found, couple of things to note. We only looked for eight password managers. There's a lot more than eight password managers out there. So if we had expanded our scope, I expect we would have seen more master passwords. The other thing that this really suggests going back to kind of the human element of this. So you're familiar with how browsers work, right, you you kind of have your in browser password manager, say, you know, you use Google Chrome, use the Google Chrome password manager, or you know, some other application, in its own password manager. And then the the the password managers that we're talking about are the ones that are kinda layered on top of that. So these are these are different companies that reduce, you know, a secured vault, enable you to log in with one password and create randomized passwords for all your different services. The fact that we're seeing those master passwords indicates that there's crossover. Right? So even though people are using these external password managers, that are are themselves quite secure. Recent news might say otherwise, in, in, at least in some cases, but they are secure in in what they do. They do it very well. But once you start overlapping, it almost is like password reuse, right, going back to that last slide. You're using the same master password for, your password manager, but you're also saving that password inside of your browser, or you're using it in your auto or even worse, that master password is something that's used as a regular password for various sites. So the problem that that that that arises is now you're giving the criminals access to that vault. So even if you're doing things like, you know, making randomized passwords, you're using, the the password generation function that's often built into those to generate a different password for each of the logins. If you have that master password as a criminal, that gives me access into that vault, which means it's now even worse. Right? Because even though you're not sharing those passwords across all of those services, they are different. The vault itself is a shared password. Right? By dint of that master password. So by gaining access to that vault, that criminal then has access to basically your entire, you know, online infrastructure. Be that a corporate environment or a or a or a commercial, residential environment. So just because you use password managers, You still have to control for user behavior. And, some of the kind of recommendations there are making sure that that master password is used only as that master password. Right? That shouldn't be anywhere else. The way that I like thinking about this is choose something unique, but complicated. Choose like a sentence or something. Add some special characters in there. So it's a little bit more random, but make it memorable. Then you don't have to write it down. It doesn't have to be something that's used on multiple services. And the other thing is pick one password manager and stick with Right? If you're gonna use a an external password manager, use that. Don't use that and then save your password manager in the browser's built in. Manager. Right? We're crossing different applications. We're widening our risk, vector in doing that. So on that, it feels like password is an issue. Password manager still isn't full proof. So then all those additional added layers that we're looking to either authenticate that identity. Do you guys wanna talk about what that landscape looks like and where it's heading towards passwordless? Yeah. So this is super interesting. And you know, we get questions on this all the time. The the security field is constantly adapting Right. We're we've seen massive changes just over the past five to ten years. And it seems like it it maybe it's even, you know, speeding up in terms of the kinds of that we're coming out with to keep ourselves safe, which is just fantastic. This has kind of caused me to reevaluate the way that I think about this. So now, you know, used to think about credentials as being like a username and a password, right, or maybe your your email address and a password. Authentication now is kind of much more broad, right, authentication, maybe it's like a a time based one time password, right? Everybody's had those sites where you don't really have a password, you just put in your email and it sends you a code and you you log in with that code or, you know, redirects you to a link that's that's time based There's pass there's physical tokens out there. Right? So things that you physically plug into your device and that stores the cryptographic material on that physical token that is used to authenticate. The new thing that has come out recently, and we'll talk about it a little bit in future slides, is fully passwordless. So this uses, like, some combination. So usually, like, biometric fingerprint or a, you know, face ID or something like that, in place of your password. But the the the thing to remember here is it's all on authentication. Right? Regardless of how that session is authenticated. The point from the criminal perspective is that there was a section that has been authenticated. And we'll talk we'll get into kinda why that's really significant now. But, you know, whatever kind of part of of the web that you're looking at on screen here you fall into, just remember that we're talking about authentication, and the and that that access is what's really important here. Okay. So on that note of kind of focusing on the access. That is almost in and of itself a layered experience. Right? So you think about like Let's say I I have a multi factor authentication on my GitHub. Right? So I enter my my username, my password, it prompts me with a multi factor code once I enter all of that, I get a authenticated session. Right? There is a cookie that's created on my device that uniquely identifies that device as having logged into that application, successfully, and that's time bound, and there's importance is there. But you can kind of split that up into multi layers. Right? There's like the the the login attempt itself with that traditional username and password. There's the multi factor attempt. Right, using that, you know, password, multi factor authenticator app or, you know, maybe it's like a a physical token or whatever. And then the last one there is kind of the assignment of that session cookie. Right? And that kinda has the longest life in terms of the actual user activity, even though it's not something you really see, constantly in the background, your browser, every time you you click on a different, you know, link on that website, your browser is constantly communicating with that server. To to verify that it is still authenticated. Otherwise, it's gonna kick you back out to the the login prompt. Right? So the point of that is you know, whether we were talking about the first stage of that, the actual login attempt itself, you know, the the multi factor, whether that can be bypassed or not, the cookie Really, all of this is access, you know, from from from the perspective of the criminal, and and how they talk about this online, you know, they're they're talking about that as a means of So I have access into company x, or I have access into x number of accounts on this service. They don't really care quite honestly what that access is. It might be, an RDP access into a device. Right? It might be an established session that has a very long cookie, a long lived cookie that's going to be active for maybe hours, days, weeks. The point is that that access exists and that it can be used for malicious purposes. And that's really what the criminals are after because that leads to the next phased, whether that next phase is, you know, something malicious, just in and of itself or much more commonly monetization, right, fraud committing, either theft or some other form of, fraud to to gain the criminal money. So if access is how they make profit, what are the odds that with Paskis being another form of access for a user? Criminners are like, wow, that is really complicated. No thanks. I'm good. I have an revenue. What does that look like? Well, yeah, from the beginning of time, that whole access problem, the fundamentals of it haven't changed all that much. What has changed is the mechanics or the technical aspects of it. And so right now, from a a bypass of authentication, there are entire ecosystems that are dedicated to stealing, cookie data. Specific to bypass authentication to, you know, leverage, MFA, trusted device to took and said bypass MFA entirely. That is still a big part of what people are doing all in terms of this, this mechanism. So as we move towards pass key and passwordless, that pro problem doesn't change. There's still going to be cookies that are looking to bypass authentication. So if criminals get access to that, they can Get array rid of the problem entirely and not have to worry about having the the the the token or you having a password or any of that. There's also the the the very real, criminal activity of stealing recovery passwords and, Trevor already spoke a little bit about this is that, a a lot of services home run back to a password to reset that device. So if you lose a device, or you change devices or, something happens that fundamentally breaks or has to be upgraded, you still have a password. Password managers still have a central password. And so that data is still of high value if criminals can find a way to get it. So a lot of those human elements that we were talking about earlier, those bad habits around security hygiene are still leveraged by criminals to get access to probably what could be considered even more sensitive passwords because they unlike to the entire entire castle. And, the third piece here is that, and more in line with what I think Collette was asking just a few ago is as the technology evolves so too do the criminal capabilities, innovation around that, criminals are very smart. They look for low hanging fruit, but as technology changes, that fruit changes. And so they're looking for different things on devices, and we've actually seen evidence of this already, the criminals are beginning to explore ways that they can leverage tokens off of devices and take that information. So actually, rather than me talking about details and high hand wavy motions on this slide, let's go on to the next slide and Trevor, can you give us a little bit more insight into what criminals are actually doing? Yeah. Yeah. And I I think that that last call out is fantastic. Right? In the in the research community, we we we talk a lot about sophistication. That's like a buzzword. Right? The actor sophistication, but it's really I as and I'm guilty of as much as the next guy about talking about sophistication just just to be clear. But but really that's it's kind of a a bit of a logical fallacy. Right? Because while things, you know, we we we on the blue side, we we, build tools, we make it harder for the actors. And you might think kind of just sort of having a have a logical exercise there that it being harder means that only those really sophisticated actors are gonna be able to do But the that's actually wrong because what's gonna happen is the sophisticated actors are going to build tooling that the low sophistication actors are gonna use without having to to to under fully understand it. Right? Just like, you know, we think about cookie bypass. Well, you know, if if I if you were to say like, hey, There's no tools. You need to figure out how to do cookie bypass yourself. I mean, that might be a difficult problem, but that's not the problem. Right? There are, dozens, if not hundreds of open source tools, browser frameworks, you know, that allow you to do that. And it's already built for you you you basically have to have no coding experience whatsoever, just the ability to click a mouse and control v, control c a couple times, control c control v. That's all that it takes. Right? So so reframing this into it's not so much actor sophistication. You know, there is certainly a a a timeline there that maybe that is a bit of lag, but very, very quickly, you know, those actors are going to adopt. What we have, conquer it, and then build tooling for others, to do the same. So I just I just really wanted to touch on that real quick because I think that's an excellent point. The other thing too is it's also an economy. Right? That's that's a fundamental word that I see on this slide. It's not, you know, actors doing things as singletons. They've built an entire economy dedicated to this problem. Totally. Totally. Yeah. Yeah. I mean, the the the cybercrime ecosystem deserves a a a webinar of its own, but know, you you only need to look as far as, like, look at all the mowers of service that we've seen pop over over the past, you know, ten years or so, maybe even closer to nine. But, you know, malware developers that are very good at what they do. Pulling out malware, they're not deploying it. I mean, some of them might be, here and there, but, but really, the the the scheme is that they're some person somewhere is going to build malware and then sell that to other people who are gonna use it. Right? Look at the ransomware affiliate. I mean, there there's so many examples of this It really is the commodification of cybercrime in it. And and it's it is, kind of the, you know, bring it to the masses as as you alluded to. Right? And the same is true really for for the, for this, right, for for kind of going to past scheme limitation. One of my biggest concerns, and again, you just want to stay It's great. Right? It's good that we're doing this. We we need to be introducing these things. This does make it harder for the adversaries. We're not saying don't use pass keys. Right. We're not diminishing the great work that's been done on password list. But it does have some significant issues. And the recovery is one of those significant issues in my opinion. So currently, as it stands today, you know, June of twenty twenty three, this might be different tomorrow. But all of the current implementations still require some use of a password. Right? So whether that's like setting up the account itself, or as the case in what we're talking about here, recovering that passkey. There was a few months ago I listed a podcast where they had the one of the co founders of Ubiqui on. And, the he was asked, I forget his name, but he was asked something along the lines of, you know, So my enterprise has just moved Yubiquis. We've we've bought Yubiquis for all of our employees. What should we do next? Right? And his answer was buy a second Yuboon key. And, you know, obviously, like, there's some bias there clearly. Marketing one zero one. Right. Right. Exactly. Well, the point he was trying to make was, you know, What happens when somebody loses a Yubiquee? I mean, Yubiquee's are fantastic. That's great. But you have to have some means of recovering that authentication. We can't just throw our hands up and say, well, I guess that employee doesn't here anymore. Right? Sorry, Bob. You lost your Yubikey. I hope you have a good luck finding your next job. We still have to find some way to get that person access to their accounts. So what that turns to in a lot of cases is either somebody, some human being, an IT worker that can manually reset, a pass key or maybe they can grant access, using, like, a temporary code or something, or some traditional method of reset. Right? Like, get a code to your email and then respond to an MFA prompt or use your password that you created when you created that account, along with some other function, and then, you know, we'll we'll give you access. We'll we'll renew those tokens. So that itself is a large vulnerability. And again, it goes back to the whole convenience factor. Right? We can't just say, well, Sorry, Bob. Right? We gotta make some way for Bob to get access to his stuff again, and and therein lies the security risk. Is is that kind of fungibility of the security, by by in in in pursuit of convenience. So, the last one here, you know, we've talked about bypassing the authentication altogether. I think we've we've beaten that one to death. Talked about stealing recovery, passwords or, you know, making malicious use of that recovery process altogether. But the physical path keys themselves. Physical, a bit of a misnomer there, but the the pass keys or the private key key, whatever you wanna call it, that generates that pass key. They are also not invulnerable. Right? We're talking about data that is stored somewhere. The private key typically is stored locally on the user's device. Well, even if it's encrypted, it's still able to be stolen. Right? And we've we've seen that. It depends on the implementation, but oftentimes it's encrypted using either master password itself or maybe some other password that the user created. It's on the device. It's prone to being stolen by malware. So going back to your point about criminals being ever adapting, if if a criminal can't bypass or steal a recovery method, well, they're gonna have to steal the passkey. And, I in in in the experience that I have in the years that I've spent in this career field, I I I will say that there's one truth that is self evident amongst all others and that is the criminals are ultimately and infinitely adaptable. So if that is what has to happen, I have absolutely zero doubts that the criminals will find a way to do it and, sell it. Make it a commodity. So with all that contextual education on what's happening in this space, I think it's still fair to make sure we address the myths and go over what that reality looks like, when it comes to passwordless. So one of the first myths is MFA is good enough But the reality is is that MFA is still susceptible to bypass. Chip Trevor, expert advice. Yes. Yeah. Yeah. It's still susceptible to bypass. That's absolutely certain. And and I think we we talked a little bit about this already. Is, you know, one of the the primary ways, that I'm aware of, and Trevor can correct me if I'm wrong here is, info stealing malware is still a great way to basically, harness the power of human fallibility and get access to the information that's going to bypass authentication, including trusted device tokens in form of cookie, and, bypass MFA entirely. Is that is that accurate? Yeah. Yeah. I mean, I think the the the obvious, kind of way to take this is to the authentication app side, but I want folks to remember that it's, you know, while while the authentication app certainly are used, email based MFA, SMS based MFA. I mean, these are things that still exists. Right? And we see time and time again, that they fail. You know, an attacker is oftentimes, gonna target an email account first, for various reasons, but chief amongst them is because they know that they can recover past using email. Right? And and oftentimes it's just email. You don't even need an app. Sim swapping, it's still a problem that we deal with in twenty twenty three, all the time. And SIM swapping often is This is exactly why swim swapping happens in many cases, right, is to to bypass, SMS based authentication. So, it's good. It's better than not having any other factored authentication, of course. But it it truly in this role, today is is not good enough. Yep. It drives that good enough because you hear that often, like, it's good enough for what I need until something bad happens or it's good enough for x y z, What can we do to advise people to kind of escape that false sense of security almost in MFA or just overall in in general for security where good enough isn't really just checking the box good enough going to protect you at all times. Yeah. Anytime I hear MFA I leap to cookies because of one thing that I see is still prevalent in a lot of applications is the you're logging into a web based application that requires MFA good on you. You're doing the right thing. But then you have a little checkbox that says remember this device for x number of days. Oops. Right? That's when the cookie gets written. Right? You check that box and you put in the two FA token and then that device has a token that is remembered for that number of times whatever, you know, like it's fifteen days or thirty days, I think, is really common. The criminal has a way to scoop that information up. They're basically bypassing MFA in that way. And I I leap to that because we talked about, you know, convenience. Convenience always trump's security. And so, that that's one of the it's I don't have to do a semi swap. I don't have to do, any of the more difficult technical challenges to get around it. I can just harvest that information because users are doing it. And to your point, like, what what can enterprises do? I mean, I think Chip's point is is incredibly poignant. Right? Like, limit those cookies time to live as much as you possibly can. It's gonna impose some burden on your, your employees, on your users, of course. But I would humbly submit that the slight bit of burden that is imposed is vastly outweighed by the, risk to all the bad stuff at risk aware and all the other things So that's, like, fantastic. Please do that. Some of the other things you can do is, like, be very considerate of, of, you know, MFA, not all MFA is created I I mentioned email and SMS is the boogeyman. Right? But, you know, really evaluate what you're using for MFA. Can you actually tie that MFA itself to a device? A lot of MFA providers are now actually doing that where you can establish a a trusted relationship between that app and the device. So even if somebody were to be able to steal that seed, or be able to emulate that in some way, it's gonna make it even harder, right, for them to to bypass that. But, you know, the other side of that goes back to the recovery method. So don't just look at how you're doing authentication. Look at how you're doing the recovery. So look at what is that little that little, box below the checkbox that Chip talked about and said I forgot my MFA. Right? I don't have this device present. Like, what are your other options and make sure that those themselves are secure? Because That is not always gonna be used by your user. Right? If the criminal sees that, they go, I have other options to get by. Well, so that ties into the next one. So passwordless, same thing as token based MFA common myth. You know, this is put real eloquently. They ain't the same. So could you guys help educate and drive awareness on some of the key differences between passwordless, pass keys, and token based MFA. I'm just gonna step out of the way and let Trevor dance here because I think that he he is, passionate about this and the difference between the two. Oh, man. Yeah. So I've heard this a lot. And honestly, I this is kind of a this is totally an understandable mistake, I think. We're we're we're we are very much in like a semantic era right now. Where we're talking about how we're talking about things. Right? Everything has like six different names. So somebody calls something a private token. Somebody calls it as seed key. I mean, there's there's so many different ways of referring to this stuff. So a lot of it is just just general misunderstanding of of what these things are. So we're we're talking about token based MFA. We're really we're talking about something that creates a one time use token, meaning it can be used one time on a very specific cider service. Right? It's not like blast this out to, you know, everything you can find in a showdown and see what what lies back with the two hundred. That is a very specific interaction between two things. When we're talking about password list, it's similar in that there is a one time password that's created, but it's different in that you can still have MFA with passwordless. Right? Those two are not mutually or they are rather they are mutually exclusive. You can have both at once. Right? So what passwordless is really is this, a per site or a per service, tokenized relationship where you have a you know, a public public and a private key, to create a one time, one time password for that service and perform that authentication. It doesn't replace the multi factor authentication. It really what it replaces is that, like, we were talking several slides ago. When we talk about the layered approach, it's really a first layer. It's that initial authentication. So they aren't the same. Would it be, and and maybe this is a, a one one step too far, but would it be accurate to say that passwordless is really kind of a next generation client, server security. So back when you had two two certificates. Right? You have a trusted device certificate that deploy on a client, authenticate that device against an application. This is kind of making that kind of easier for the masses. Is it not? Yeah. Yeah. It's like advanced PGP. Yeah. It is. So the I mean, the strength and password list really is it comes from the what is stored publicly. Right? So, like, even if we go back to like a traditional traditional authentication. You've got a database on a server somewhere that stores a list of user credentials, right, which you can have like an email or username, whatever, and then a password. Usually, that's hashed and salted, and we feel pretty comfortable about that depending on how it's hashed and and, you know, the randomness of the salt and other factors. But as we've seen time and time again, just because you do a really good job, Hashing and salting your passwords does not mean that somebody can't crack that. Spicloud. We do that. Right? So, what what what password list does is that that bit of information the user credential that saved on that website is is not a cached password. Right? It's not plain text at all. It is a public key. So it's part of a public and private key pair. So and and it's specific to that site. So if you really think about it, like, if somebody steals that database, it's essentially worthless. Right? Like, that database contains data that can authenticate with itself, but that that's it. Right? You don't have the full you don't have the private key. You can't you can't regenerate that, and you would only be able to use those public keys on the server that you already broke into. So that it that's really the strength of it. Right? It it minimizes the risk to, like, traditional data breaches, but it still is a relationship between a public and private key. So If you have both sides of that, then, you know, the security of that relationship is essentially negated. It it doesn't exist. So it's more secure. So passwords are more secure, but then would you also say that it helps alleviate some of the friction points in that user experience? And how they access their digital lives on a daily basis a little more secure, but then also a little less friction for users with password lists. Yeah. I don't I I would even have a hard time saying it's more secure. I mean, it's a different if it it's a different kind of security, really. It I don't think inherently it is more secure. I guess if you look at it as as that trust relationship between a device and a single site, then you could make that argument. But but really it is for ease of use. I think in my opinion, passwordless, you know, that that is a solution, whether it's flawed or not. To the problem of people wanting convenience, and doing things like using the same password on multiple sites. Right? Passwordless enables you to bypass the passwords altogether. And by default, you're gonna create a new password, right, for each site because it's it's baked in. So it's it's it solves the problem of password reuse, really. Yeah. It does. Yeah. It solves the problem of password reuse. It solves the the problem of, you know, data breaches that we see at least mostly. There's still some other parts to that. But but yeah, but but it's still, you know, we're still talking about authentication going back to what I said earlier, it's still access. Right? And there's all this other stuff that's built around that. It is so much easier. It's almost of almost kinda funny when we talk about it, we spend so much time talking about how, oh, adversaries are gonna be able to steal the pass keys and they're, you know, they can regenerate it locally on their all that is kind of a spud's point. Right? I mean, if if an adversary is at that level, like, the everything else has failed. That's not gonna be this that will never be the first thing. That they try because there's so many other ways to get access to an account that are so much easier, than going through all the pain and the heartache of being able to to do that complicated process. Okay. So going into the next one, forcing user password reset recurrently solves for poor hygiene. Another common myth, but the reality is what have y'all been talking about the last ten slides is convenience always wins. Correct? Well, back in back in my day when dinosaurs roamed the earth, and I was, managing users in a in an IT environment. One of the things that we did was we had, you know, the rules in in Microsoft environments, you can set all sorts of really cool rules, including forcing password complexity, and, forcing the the number of iterations of a password that can be identical. So basically, you don't want somebody to continue to use the same password or even like the next two times that they change their password to use that same password. So you can have memory in that. One of the environments that I worked in that list of passwords that you had to have as unique was twelve passwords long. So over the course of, you know, every thirty to sixty days you had change your password. That was a requirement. People actually had lists of passwords that were twelve passwords long that they knew and were variations of the the root password. That they just iterated through, and they would mark off when they had used them, and would go back to that sheet when it was time to change their password. Forecing user password resets on a regular occurring basis does not solve for the poor hygiene process. It makes it, an opportunity for users to be more creative, but it doesn't solve the problem. Well, and sometimes users aren't even creative. Right? Like, one of the way they would what, like, block number one to act retribution is if you see a date in a somebody's password, just iterate a few times. Go up, go down. You'll probably hit another password. Right? Because, I mean, that's what people do. Like, names of the seasons. Right? Like, if your if your enterprise requires a reset every ninety days, well, maybe my password's gonna Trevor summer twenty twenty two. And then the next, it'll be Trevor fall twenty twenty. Right? Like, I mean, this is what again, users love convenience. It makes sense. We are human beings. It ease or ease of memory, but if if it's easy to remember, it's also easy to guess. And that's the part of the puzzle that oftentimes gets overlooked. Right. So for criminals, they don't care about cookies or sessions. Right? But in reality, stolen cookies, as you guys discuss, earlier are highly valuable, and that's what enables the criminals to that access, access to that already authenticated session. So what do you think everyone should know about cookies and sessions and why it's important to also consider that in this passwordless journey. Yeah. Yeah. These are these are so highly sought after. I mean, when when we're sitting in these these threat actor groups online. We're seeing, you know, actors talking about the things that they're looking for and the things that really are valuable to them. Cookies are consistently top three. If not, the number one. I mean, the actors are so aware that this is that this has become a very common TTP that we see. And we see it in in big attacks. We've seen it in ransomware attacks. We've seen it in the, you know, the lapses stuff that was happening a few months ago. They were using cookies to bypass, the login process altogether. Right? So, you know, this is something that is well known in the criminal communities. They're, like I said earlier, there are open source tools that have been built, they usually call themselves, you know, anonymity browsers or anonymous browsers that will allow you to configure a session to look exactly like your victim. So, you know, I know that this person, this is their display resolution. I know they are running Windows ten Pro at this patch number and their user agent string for their Chrome browser is this. And, you know, you can essentially create an identical profile to the person that you're trying to, emulate. And even even things, you know, like the geo filtering that that a lot of MFA has been doing to try to identify anomalous activity. We see the criminals turning to residential proxies. And and now, you know, I can just put in your zip code and select, you know, uh-uh, a residential proxy near you using the same internet service provider that you are, and then, you know, combining that with a valid cookie and device information, I mean, it's it's it's functionally impossible for, any automated system to detect anomalous logins, using that kind of profile because it functionally looks exactly like, the the trusted device. The dirt the other dirty side of this particular problem is the the fact that even if you do know that session cookies have been stolen and they're in criminals hands, there are Not a hundred percent of applications that have a means of invalidating those sessions. It's a very complicated circuitous process to do that in most cases. And that's a struggle, that a lot of our customers have run into is even if they have that cookie information. If you don't have a means already built into that application, to to invalidate those session tokens, and, deal with that problem. It it it all comes to not that's something I think that developers need to start taking a little bit more seriously as well because it is so pervasive and it is so critical to a authentication piece, having a means to do that. That's easy. Is something that should be part of the process. Yeah. And just not to hijack this thread, but the other the other part of this and something we haven't talked about at all is the other means of authentication. So other than passwordless path, you know, we have API tokens in our environments. Right? We have webhooks that we use. And if you think about what those are, a webhook or API token, really, it is access. It is a means of authentication. You know, if I use my you know, personal access token to my GitHub account, I can go and clone that whatever repository I want down using that token. I don't have to log in. So that token in and of itself is authentication. And the other problem that we see with tokens and webhooks is when we talk about time to live, I mean, sometimes those things never even expire. Right? You actually have to go in and revoke them yourself or as an enterprise. You need to roll your tokens Otherwise, those things basically never expire. And we've all heard the the horror stories of people accidentally, you know, leaving an API key in code that's pushed to a production environment or, you know, accidentally pasting it somewhere and it being found. I mean, these are these are things that we know and criminals know as well. So those those tokens are also highly, highly sought after. For the same reason the cookies are, and and, you know, everything else you can bypass an authentication or or perform a legitimate authentication. So for the last one, with passwordless, it was in May when Google announced that pass keys were available for their consumers for self adoption Nothing for self adoption available and for enterprises to fast follow soon. So the other myth is that users are quick to adopt new technologies. And reality is each tool has its use cases that will continue to persist it. What are some examples either in daily lives or in tech where we've seen? This long lengthy process of adoption and understanding for tech. So my favorite my favorite quote here is it's by mechanic quote. I don't know who this is attributed to. Maybe I hallucinated it like chat EBT, but the ninety percent of problems with the car are directly a result of the tool between the driver's seat and the steering wheel. Right? Yep. It's a human being. So the same is true in tech. You know, we we have the same problems. You can build the most fantastic encryption algorithm that is you know, it's gonna take seventeen billion years for Ashcat to to crack it. User, it it enters password one two three four one time. You're method is gone. Right? So, you know, this is this has been the case for a long time. And I there was a SIS report that came out a few months ago if I recall correctly, you're talking about, you know, the the top the top exploited vulnerabilities in twenty twenty three. And I I think something like two or three of the top five were from twenty twelve. You know? And so, people people won't patch their vulnerable systems in over a decade. You know, I I have a really hard time believing we're gonna get to wide industry adoption of something, that is, you know, requires extra user activity quite honestly. Overnight. Chip, did you have any other thoughts on that? Well, yeah. I mean, I I I think that users are incredibly sensitive to any change that could potentially impact their productivity. And that's one of the reasons that they're resistant to change in in technology and means of doing things authentication and and and It's definitely part of that. I I used to get asked this question about password list and, you know, if that was on the horizon, you know, what what does that mean? And a lot of what we've covered today, has definitely been part of the answer that I used to give, but the example that I gave, was that we still have pencils. Right? You think about we have computers, we have pens, we have all these other means of actually recording information, yet there are specific instances in use cases where pencil is perfectly suitable for a job. And the pencil's been around for a very, very long time. It has never been replaced, although it's had, you know, tools or capabilities that are good, good, replacements for it. And that's true for passwords as well as passwords will continue to be pervasive. They're a fundamental. They're a home root for authentication and access, and that's never gonna go away, regardless of how much technology changes. It's so they were still gonna have that that pockets of places where passwords are still used. On a spectrum of, like, fear or comfort, where do you feel something like this sits in or same thing in the context of at GPT, where people will either embrace, get excited, test it out, and that other spectrum of like, really terrified it's gonna steal my job level. Where does something like this passwordless sit within our current space? Or Yeah. I mean, I'm not super concerned. Honestly, I I think, you know, we we exist kind of on this continuum of security versus convenience. And you can kind of think of this as as a a weighted measure of, like, which which side will will win out and and, you know, that's a really simplistic way of saying that. But really, in my opinion, it's always going to fall on convenience, like convenience, especially anytime we're talking about, like, user experience convenience will always win out. And that doesn't mean that security isn't thought of at all. Like, companies develop a security mind all the time. But if it comes down to, is this something that will you know, inhibit our ability to gain new users. The the answer is always going to lend itself to convenience. So I personally am not all that concerned. I do think it's something that we need to think very critically about, and we should be having these discussions. That's why, you know, I really enjoyed participating these kind of discussions now because I think if we if we talk about this early, we can develop, you know, really, really good ways to address this in the future as we do see adoption. But, definitely, not not afraid that, you know, GPT for is going to all of a sudden become the best researcher in the world and all be, without a job. I I I think that that, users are are very focused on, What they need to get their job done, but I think one of the things that changes the landscape a little bit in terms of the security versus convenience equation is all fundamentally founded on people becoming a little bit more aware of privacy implications, and the security tie in there is, you know, if you're working for a company, you may not immediately think about all the security risks for that company, but the second your personal information and your family is at risk or other sorts of things start to kind of become more pervasive changes your mindset. And that change, you know, where you live literally is, definitely something that expands into the enterprise as you become more understanding and aware of the the security risks of of not, not adopting new ways of doing things and focusing on things. And I think that that's something that's interesting. It's certainly been an evolution that we seen accelerating, over the last several years. Do you think advancements in technology take enough into consideration about human behavior and thinking forward like how will they use this? How will it impact them? Will they be in that kind of whole angle? Or there's still room for innovator's technology vendors to bring more of that human element into how they advance certain areas of security. Well, fundamental element of product management or good product manager, and I should say, is to take into account how people are actually using the technology. Because if you don't understand how people are actually going to be doing something. You can't really build in all the catches, that are gonna become critical to doing it the right way. And that requires conversation. It requires watching users, spending time with users and really understanding that fundamental problem. So I I think that it's a little bit on both sides. Right? I think that there's certainly, you know, great new technologies moving fast and and taking us into the brave new world, but they have to take into account the way people are actually going to use them or maybe even more importantly misuse them. K. So on that note, with everything tied around credentials, really evolving into access. You wanted to check your exposure and see what that looks like. We recently launched check your exposure on spy dot dot spy cloud dot com, free tool. All you have to do is provide your business email and see where your company or your personal risk is at. And we wanted to say thank you for hanging out with us and having this discussion around busting myths in our past with us future, and have a great day.
- Video
Webinar: Access Granted: The reality of compromised credentials in a passwordless world
Explore the evolution of authentication and scrutinize common myths around passwordless technology.
Hello. Thank you so much for joining us. My name is Alex Ash, and I am a growth marketing manager here at SpyCloud. Today, we'll be talking about current challenges SOC teams face and how action driven analytics can unlock automated workflows to help your sock team build the foundation for actionable data to optimize your automation potential. I'm happy to introduce our speakers today, Taylor Coppock, senior product marketing manager, and Chip Witt, senior vice president of product management. And with that, I will hand it off to Taylor for further introductions and to go ahead and get us started. Hi there. Taylor Coppock, senior product marketing manager here at SpyCloud. I'm very excited to talk about this subject matter today, explaining a bit more about how we can help you do more with actionable data. And my name is Chip Witt. I'm a senior VP of product management here at SpyCloud, and I'm really excited to join this conversation with Taylor today to add value, add clarity, and insight from some of the conversations that I've had. So today, we're really in a level set. The current state of affairs we see with with SOC teams and some of the the top challenges we know that are really getting in the way of innovation and driving progress and driving towards automation. But But then we wanna show the goal state of why all this matters. It really shows some applicable ways you can drive towards making use of this data to actually unlock automation for your teams. And, of course, we'll have time for some q and a at the end. So we're gonna jump in right into the current state of affairs to kind of understand what the landscape is that people are operating in and why this topic of automation is so important. So first, we need to talk about how did we get here. As cyberattacks grow in sophistication with evolving tactics, techniques, and procedures and targets, security operations teams are basically they're playing a very crucial role in safeguarding organizations by protecting employee identities and access to corporate data, but it's a difficult job. Today, the evolved role of SOC team is to combat threats specifically designed to evade detection. So they have to be right all the time where the bad guy only has to be right once. In this webinar, we're going to take a deeper look at what you're up against so that we can more clearly understand how to tackle modern SOC challenges. The stats that you're actually seeing on the screen here are actually taken from the Tynes twenty twenty three Voice of the SOC report, and they really tell a really good story here in terms of what SOC teams are dealing with. Sixty three percent of practitioners experience some level of burnout, and that's detrimental to the success of the teams because if you're burnt out, you're not doing a very good job at identifying those threats. Fifty percent of respondents say that their SOC team is understaffed, which means that not only are your existing staff burnt out, they don't have enough relief on the bench to solve the big problems that they're having to face. And then finally, more than eighty percent say their workloads have increased in the past year, and this makes sense from the data that we've seen. And, certainly, it no signs of it stopping anytime soon. So security teams, you're not crazy in feeling like your job is tough. It really is. It's a relentless and sometimes thankless work to safeguard employee digital identities and protect corporate data. So now we'll talk about a bit more of the other challenges that are really hindering these teams from driving towards automation. The first off really is people. Some of the things really stand in the way of security teams really driving towards production is just understanding the employees and consumers that we're working with every day. The first line of defense in enterprise network is actually the people behind the computers. And this human behavior often forces these teams to really divert their attention and their focus to try to prevent attacks happening just by what's happening in our daily lives. Even the best data and the best tooling can't really solve everything that humans are doing. A few things we see that are really getting in the way of the frustration for these SOC teams and blocking automation comes down to passwords. In the end, passwords are still one of the primary ways of authentication and login, and teams know their employees still engage in this risky behavior of reusing passwords that might have already been compromised, reusing passwords across devices, across applications. And it's just difficult for SOC teams to really understand what's actually in use and how much threat actually exists there. Also, just some of the knowledge gaps in just the daily lives of employees and and the consumers, inadvertently, people click on malicious links accidentally or they open up phishing emails or other techniques that, again, provide access for criminals to get access to the to the actual enterprise network and open door for other malware infections and data breaches and just stolen credentials. And, of course, humans still like to prioritize convenience. There's many ways throughout the day that just make it more difficult for security teams to really protect what's happening within their organization. People often sync their work and personal profiles. Now the remote world is very blended of what actually is home and work and life, and this causes more just frustration and challenges for security teams. It's often very common for people to install new applications and new tools that work well for them, and this shadow IT and shadow data adds more hidden risk for security teams. So all in all, even with the proper data and the and the information to everything, of what's happening across your enterprise, auto actional data could help to account for some of these human elements, but you can't replace all the impacts out there. But you can hopefully minimize what this causes for security teams. Now what else is really causing burnout and overwork and getting in the way of security teams driving towards automation? A few things that we fairly common we see across the teams are, first off, dealing with the expanded security perimeter. Now with the new bring your right bring your own device policies and relying on third party hosted apps and services, there's just so much more significant vulnerabilities introduced into the security environment that is getting in the way of teams actually driving towards automation. The focus is getting on getting into visibility of what's actually happening, much less having the time or the data to know how to write script and test the automation needed to protect their employees and their customers. This also leads to a growing attack surface. There's just so much out there that teams don't know if it's actually secure because visibility is still a challenge. According to a HackerOne report, over fifty two percent of organizations don't know how much of this growing attack service is actually secured. So there's several paths for these cyber criminals to attempt to steal this confidential data and target your employees and get after your sensitive I IP. So SOC teams don't really have the necessary insights, much less much much less actionable data to even know the full breadth of their attack surface. We're still trying to get this visibility. And, also, the security teams are stuck in the middle of using other tools that might have been purchased by different teams, like your IT team, your networking, your identity team. And security teams are stuck in the middle trying to make sense of all of this to drive towards automation. But with so many different consoles and tools that try to investigate incidents, the time is spent trying to dive into the gaps even know what is out there and how to respond to it. And these tools are only as good as the data being ingested. And a lot of time is spent actually maintaining and piecing these these tools together into a seamless seamless workflow instead of actually trying to drive towards automation. And finally, just all the noise that's out there with false alarms and poor data quality coming in, teams are spent just fighting fires and doing tedious tasks and responding to things every day that is getting in the way of billing out their automation to protect their employees. And all in all, there's one other main challenge we see out there, and it really comes down to the data. So in talking about the data, one of the things that we actually need to recognize is there's a tremendous reliance on traditional threat intelligence platforms to feed processes. And as SOC teams evolve, they're trying to automate using this information. But the problem is the signal to noise is not significant enough to actually drive automation. It requires human effort to separate out the noise from the true signal and then provide a means to automate the recovery of that. And that's an important aspect there too is that information and indication indications of compromise indicators of compromise as they come in, they don't provide deep level context. They require an analyst to spend some time asking, is this relevant to us? If so, what do we do now? Data is never refined enough to the point of being actually actionable. And actionability is the cornerstone of operation being able to to put it to work in the in the organization. If it's not refined or dependable, you can't you can't automate, and that's what we're we're talking about here. The other thing that's also really interesting about threat intel platforms in general and threat intelligence as it comes in, through those platforms is that it doesn't provide definitive evidence of compromise. It it struggles to provide intelligence that highlights what criminals are actually using today to crack into organizations and do the things that they are doing, and that is a cornerstone to being able to take appropriate action in the environment. So if we talk about the goal state, this is why it's so important to figure out how to effectively implement automation and in what context. What does automation mean? Automation offers a path forward for security leaders to scale, use their limited resources more efficiently, and therefore allow SOC teams to speed time on or spend time on other things that are more meaningful and fulfilling tasks. And this is a great quote again from the the Times twenty twenty three voice of the SOC report is automate the present TDM and security teams can anticipate the threats of tomorrow. That's the intelligence of letting your systems automate things and do the things that they can do well and freeing up that human intelligence to do the things that it does well. And that's what we all hope for as we move towards a brighter tomorrow. I used to spend a lot of time talking about information science, and one of the cornerstones of that is the transition of raw data into information. So if you actually look at data, bits of information floating about, if you think about all of that coming in all in one place, it's not very useful. In order for it to become information, you have to organize that data. And then further, to make that information knowledge, you have to add additional context, additional analysis on top of it to then inform action. And actionability is what we're talking about when we actually are are are talking about automation. One of the context that I think is important to bring up, in in this particular vein is that when we talk about automation, we don't always mean automation all the way through to remediation. I was had the honor of of talking to a bunch of security leaders recently, and one of them was talking about SOAR as a a technology used in most SOCs. And, of course, SOURCE stands for security orchestration, automation, and response. And one of the things that he brought to light is that oftentimes, the SO part of that equation is more important than the ANR. And what he meant was that automation is not just about remediating. Sometimes it's about enriching data so that the analyst can make better decisions. And, again, that requires analysis. It requires actually going all the way through this tree to bring forth knowledge that can drive forward better action, whether that's a machine taking that action and automating that remediation or whether it's automating the enrichment process to inform that human, so that they're making better better decisions. Really good example of where you wouldn't want to automate would be you see something, that indicates a compromise on the CFO presenting something to the board. You wouldn't want a machine making the decision to interrupt that and invalidate credentials or in impact that presentation in any way. So you have to have some intelligence built into how, where, and in what capacity you automate. So when we talk about effective automation, ninety three percent of SOCtINE respondents believe that automation would improve their work life balance. And this is important. Right? Effective automation prevents and protects both proactively and reactively. It maximizes the time that the SOC is spending on things that are important and keeping their productivity up. And, also, by virtue of having process driven response, it improves the reliability. It also allows SOC teams to focus on other tasks such as research, development, and integrations, looking around the corner at the threats of tomorrow, finding new opportunities for the organization to grow and become even more secure. And then, of course, the final piece here, effective automation really lends to happier, less burnout SOC teams, which as we started earlier, that is a big cornerstone of the problems in a lot of organizations. And the idea there is is if you have staff that are happier and less burnt out, you're going to retain them for longer and put them to good work to protect the organization in a more proactive way, over a longer period of time. So we have some good news. There is a way forward. We're gonna show you now you how you can actually drive towards in this smart automation using the right data. So we see three main pillars of the steps you can take towards driving towards automation. You might be in a good spot right now. We're gonna provide a checklist after this talk to help you kind of see where you are right now, perhaps some gaps you can fill and where you wanna go next. But it's really important to focus on the data that you have access to, the type of data, and then how to actually layer that into your workflows. So the first pillar we're gonna cover is, again, the source of your data. Where is this coming from? And more importantly, what is the speed at which you're getting it? After that, it comes down to the different attributes of how you define actionable data. How the data is presented to you and all the information you have within each record is very important to really build the the the trust knowing you can actually spend time building automated workflows to protect your employees and your business. After that, it comes down to layering this actionable data into the tools that you're already using across your teams with these seamless integrations. So we'll talk to these three main pillars to show where you are as you drive towards automation. Fundamental question you may be asking yourself is, would you automate workflows based on old data? Probably not because it's only the current relevant data that's in criminals' hands that's actively being used that is truly actionable. And so when we talk about the dark web or the deep and dark net or however you refer to it, a lot of times people think of it in terms of a unidimensional monolith of information that's out there inaccessible to the normal novice and the criminals are, you know, accessing and leveraging openly and trading. And that's not exactly true. It is true, but it's also it's more complex than just a monolith. In fact, we talked about the problem of threat intelligence platforms earlier. Most of those platforms leverage a lot of open forum data that if you look at the the dark and dark web as a a a gumball, multilayered, the top level, the surface layer is where you're gonna find a lot of commodity data that's publicly traded, and pay spin sites and other sorts of places that can be easily scraped. That's the bulk of tip information that is coming to organizations, and it's very noisy. That's a huge problem. You can't automate based on that. Then you have some inner layers that become a little bit more interesting in terms of value. You have less common datasets available in the middle vetted forums, and these are forums that require access, but are a little bit harder to get to in some contexts, but are not necessarily closed off. They're not truly, truly deep and dark, in the context that people like to think they are. The data is valuable enough to sell. It's high volume collections of automated, information that's it's complex information, but it's possible to actually leverage that information and collect it and use it in various ways. Collection requires knowledge of underground markets, but beyond that, it's it's fairly easily accessible. And it fits in also into, a commodity level of information that's being being shared. And get into the lower and core levels of the deep and dark web. You get into high value data, and stuff that's harder to get access to without people that have, trade craft or, have the secret handshake, get invites, to access that information. And this becomes really interesting information from the standpoint of targeted threats, other sorts of things that you are really caring about in terms of protecting, your organization because it's it's data on breaches, information that is, tied to individual relationships, and, the context of that information. Accessing it requires relationships and reputation, to get access to that information. So, databases are often unique and a very high value at at that lower level. And then in the core level, that's the stuff that's super scary. It's dangerous, communities that are sharing extremely sensitive data, and it requires long standing and intimate relationships, and operational security becomes a really big thing there. So, again, trade craft and getting access. And the reason why I I like to surface these areas is that, it's hard to find organizations that provide security solutions and data at those lower two levels. And so when you're looking for, data to automate, you wanna be using the highest fidelity data that's actually part of what criminals are actively buying, trading, selling, and using in criminal enterprise. Because if you don't have that information, again, it's noisy, and it's not very useful. So, hopefully, you're nodding your head. This isn't making sense. But, again, that's just the source of the data. Regardless of where you get it from, data is still data. In order to actually drive these decisions and drive towards automation, you wanna make sure that it's giving you direction and matter and and and focus on more your business and what you need to do. So some of the foundations that we see are key for defining this actionable data that really helps you build this automation comes down to a few things. The first the first one is all about curation. Is this data actually curated to remove all the noise, prevent alerts, and make sure you're you're responding to alerts that matter to your business? Data by itself is just data. You need access to this information that is machine readable to actually be ingested into your tools. Has it been parsed? Has it been normalized? They validate validate all these billion of data points that could mean something valuable for your business or not. A lot of companies take pride in all the data they publish. There's so much happening, so much noise out there that could be that could matter to your your business, but a lot of it could just be noise. What we see often is just these these duplicate datas that most tips are providing because some some of the information being published is just duplicates that's been repackaged to the combo list that it was already exposed in previous breaches. This doesn't really matter for driving towards automation because you would have taken taken action on it the first time. So it's important to make sure that this curation discards information that has already been duplicated in combo lists, but, also, we know that within the records, there are so many attributes that could be of value. You might want to look for information that's already been discarded that does not contain high value PII that that relates to your employees or consumers, but also you might wanna discard records that don't contain passwords that you couldn't actually drive action on. So that's curation. The next one is all about having information that really has been enriched to provide insights on where to take action. Great. So if you've removed the duplicates, you make sure it's including high value PII and passwords. What's next? It really comes down to the enrichment for both breach records and information gleaned from malware records. On the breach side, you wanna make sure that information you actually ingest and start analyzing really includes all the contextual information you need to help drive your decisions for it to automate. You need things like the breach source, the description, and, of course, the password itself. The more you have about the event will help you decide what you should be automating and what decisions need to be made by your team, both in terms of triaging and priority. Now on the malware side, it's very important to, again, to get get as much context as possible. Everything, not just about the device, but anything that helps you understand the severity and the priority and what the actual full exposure might be to bring risks to your business. You need to understand the date and time of the infection, the IP address, the infection path, any of the target URLs that were included with the malware records, but, of course, as much credentials and cookies and passwords that might have been exposed as well. This is very important to know how to stop malware infections from turning to full blown ransomware events. Now for both breach records and for malware logs, passwords are key. But on the enrichment, look for a source that actually has that is providing these plain text passwords. You don't wanna spend the time actually trying to crack the information yourself to understand what to do with it. To really drive action, really be productive, is to have access to the plain text passwords from the get go so that you can actually move forward with some quick scans to actually see the severity of what's actually exposed in the hands of active employees. The final one is all about correlation. You wanna make sure that the data's been correlated to help you understand the full scope of exposures. We see often that if there's been exposed in email once, it probably appeared across multiple breach records in our dataset. You wanna make sure you can look for the full picture of exposed employee identities to know how many credentials are out there across all the different breaches and malware records so that, again, you can prioritize correctly, triage it, and set up the rules in place for automating appropriately to the extent of the risk to your business and your employees. Now those are a few of the foundations. There's a few more that Chip's gonna let you know about. So one of the things that's kind of interesting in in this story is that you also need to have data that adapts to circumstance. What do we mean by this? Criminals change tactics. As defenses become better in one area, criminals will leverage the next lowest hanging fruit to do their bad stuff. So when you start thinking about what criminals are leveraging to to gain access to identities and, corporate data, a lot of it is hinged on credentials. Right? Usernames, passwords, things that are easily stolen by virtue of hacking a site and stealing a database of users associated with that. And knowing that password reuse is so high, executing on that, leveraging that in a meaningful way to to compromise enterprises. But the tactics change as as the landscape for passwords has changed, and the world has changed quite a bit. Even in the last seven years, it's changed significantly. Now we're actually looking at a world where criminals are leveraging things like cookies or API keys, other, you know, more esoteric things that are still tied to identity but are not tied to identity in the same way that we're used to. So you need to have data that adapts to evolving criminal tactics, and this is incredibly important. This deep understanding of the criminal ecosystem means you're able to stay ahead of evolving threats before they become mainstream, knowing what the criminals are actively doing so that you can stand in front of that and block with insights into stolen session cookies or API keys or password vaults or whatever the next thing is. Finally, does your your data prevent exposures across your supply chain and your VIPs, your executives, your key staff developers, and other sorts of of folks? This is important for automation because it gives insight into third parties for automating their own solutions. You can inform policies, for your partners because as we've seen in several major newsworthy cases that are still unraveling, The the supply chain is a significant source for criminals to leverage to gain access to your enterprise because we're trusting these third parties with access to various things. And if their security situation is not, such that they're addressing threats, that then cascades into your risk, and that's incredibly important to be able to shore that up or at least have visibility into it to have the conversation about how you tier access to data and applications by virtue of those risk factors. And I think that that that kind of segues nicely into automated workflows, in terms of, you know, now you have the foundations in place for actionable data. What's next? Exactly. That's right. So you have the right data, the right data source. Now it's about actually layering this into your workflows with some seamless integrations to actually see the the the output of this automation and really drive towards productivity. So a few of the actual workflows that we we can really see help your help your security teams make more, go across a few different tools you're running across your system. On the directory services side, it all comes down to your identity. Regardless of how you're managing your services on prem, hybrid, or in the cloud, having axe access to this fresh, actionable data helps you actually prevent against next gen threats and keep your employees and consumers safe. Now on the actual data side, we mentioned the need for having this enrichment and these these plaintext patterns available published as soon as you get them. Because it's very important for you to start setting up these automated scans to check how many credentials are actively exposed that are that are actually that are being used by your active employees. This isn't possible if you don't have access to plain text passwords. And following this this practice, we'll help you actually align with some of the latest NIST password guidelines where most most vendors that you're running will let you actually integrate this data into to run scans daily to see how much risk exists out there. You wanna make sure you're using your time to understand the priority of where you should focus your team's effort, not spending manually time seeing how much how much how much risk is associated with your with your customers by looking at the passwords. Now with the right data, you can actually scan to see the threat of what's actually exposed that could be in the hands of the criminals that your employees are using perhaps across multiple systems. But not just scanning to see what's out there. You also wanna make sure you're automating the workflows what happens next. We recommend actually setting up some workflows to go ahead and automatically force a password reset if a match was found. The power comes down to you setting the actual remediation path, but having access to the right data helps you know you can make the decision that if you do see your employees are running something that is compromised or potentially matches something else out there, you wanna make sure you can configure the notifications of letting the your employee know they should, reset their password or go ahead and making the change yourself. Those helps you really prevent any potential gaps from criminals having access to your credentials, It all comes down to what's possible with this actionable data that you can ingest in your systems. To add to that, the Simmons source story is a very strong one as well as oftentimes in organizations, you're already managing log entries events from all sorts of disparate systems in a consolidated place for your SOC to manage. Are you bringing in data related to credential theft, cookie hijacks, any of the information that we've been talking about in terms of some of the data, dynamic or otherwise, to help inform decisions around other events that are happening in your organization. That is incredibly important, not only to identify events as incidents themselves, but to provide enrichment on things that you're seeing so that you can kind of draw correlation between multiple disparate events that by themselves may not look like anything, but combined together can help you automatically draw those correlations and lead towards an orchestration or, an actual remediation event, and that's incredibly important. Part of that too is, source play incredible roles we were talking about earlier, automatically creating playbooks, within your source so that you can actually have that workflow either enrich and enhance an analyst's capabilities or drive it all the way through to remediation because it isn't just in the directory services themselves that you might wanna remediate. You might wanna correlate that with other information and drive that action through systems that are looking at a broader context. So bringing it back to the business value here, again, automation offers a path forward for security leaders to scale, use their limited resources more efficiently, and therefore allow their SOC teams to spend time on other more meaningful and fulfilling tasks. That is incredibly important. So take a breath, measure, optimize your automate automation, and keep improving over time. It isn't a one and done situation. It's a continuous process. You know, life's a journey, not a destination. And in security context, that actually truly applies. It isn't about getting to a particular destination. We wanna be more secure for sure, but it really is about the journey and continuing to improve, leveraging the information data that you have at your disposal to make intelligent decisions and make your team more efficient. So we can't, say all of that without saying this. SpyCloud exists to prevent criminals from benefiting off of the information that they steal. And so we do have a checklist that will be published soon that will help you answer some questions around selecting the right vendor, which we, of course, are biased and think is us. We can certainly help you with your automation. Spy Cloud enterprise protection safeguards employees' digital identities, delivering a solution that continuously monitors for compromised credentials, keeps corporate data safe, and reduces overall enterprise risk. With actionable analysis, security teams can extend automated protection across their organization while optimizing response and remediation efforts for proactive coverage against targeted attacks. And that's an incredible important part of rapid response through seamless automation. Right. The q and a portion of today's presentation. We have a couple of questions here. Let me just get to them. Alright. One of our questions. Automation sounds great, but it is probably naive to think that it is the answer for everything. What can you say about the drawbacks or maybe more specifically the aspects of automation that one should look out for as part of this journey? Chip, I'm gonna throw that to you. Yeah. There are there's a lot of meat on that particular bone. One of the I mean, I I think some of the stuff, related to this is stuff that we talked about in this presentation is that, you have to have data that you rely on or can rely on, that is of high fidelity and is coming from the right places that are really identifying criminal activity in the sense that criminals are actively using trading and, leveraging the information. Because if you're not taking action on that information, it's not pretty pretty useful. But beyond that, automation is one of those things that people are always striving for, but one of the the things that we talked about is that the environment changes. Talked about adaptable data. The same is true for your processes around automation. You have to continually look at the processes that are defining what that automation is and make sure they're still relevant in your organization. Because if you're taking automated action and it's no longer relevant to the types of threats your organization is seeing, it's more noise. Right? It's not very useful at that point. So you do have to go back, circle back periodically, and look at what you've automated, how you've automated it, and are you getting the outcomes you expect from that automation? And if you're not doing that, you're a hundred percent right. It's it's naive to think that it's going to be an answer, certainly for anything at that point if you're not actually doing the right things. So I wanna, dig a little bit deeper into your answer there. How do you make sure that you're getting access to data before it's been monetized or used against you even? Well, that's, again, selecting the right vendors that are diving into that dark net data in the way that I described criminals are actively trading and using for the more sophisticated, quieter attacks. I love things like the mother of all breaches that got announced, and everybody got very excited about that. It opens people's eyes to things that they may and everybody got very excited about that. It opens people's eyes to things that they may not be paying attention to. But the honest truth is those types of information leaks, out in the wild are less damaging than the quieter information that you're only going to get by partnering with a company that is looking at the the underground in a very deep analytical way and analyzing what criminals are actively doing and how they're using the information so that that can be fed into analytics that are servicing you and your decisions around automation. So speaking of which, I've heard that session hijacking has led to several recent high profile breaches. How does that relate to credentials and how we should be looking at our automation plans? Well, there's some interesting stuff there. Right? Criminals no longer hack into networks. They log in. That's been true for quite a while now. They're using, you know, user credentials, usernames, passwords, that sort of thing to just you know, that they're coming across through breaches, etcetera, malware infections, info stealing malware, taking credentials, and just logging it and moving laterally once they get in and doing all sorts of damage. This is, again, getting back to the adaptability piece, this has changed a little bit as its access. Right? Access is the identity piece here. It's not just user credentials. Access is provided through a lot of open doors, including cookies, session hijacking, is is preeminent, and also API key usage, when those get exposed. Cookies are really interesting. Right? The there have been several recent breaches that have occurred, that were directly related to cookies. One major SSO provider, had cookies that were exposed and gave stair step access to admin accounts and customer admin accounts that wound up compromising multiple organizations. Scary stuff. Another story related to cookies as well, was a a CICD platform having having cookies exposed by virtue of a browser sharing information. So Chrome and several other browsers have this capability where regardless of where you're logged in, all of the information from your profile gets shared across multiple machines if you choose to do so. And that includes your cookies, credentials, all sorts of other information. And so if you're doing that sort of sharing from an enterprise machine to maybe a personal machine, or a machine that's less protected for whatever reason, and that machine gets popped with info stealing malware, all of those credentials are stolen. And if you're in the enterprise and you're monitoring that enterprise box, you're gonna be none the wiser. And that's what happened to this organization is those cookies got compromised, and that led to follow on attacks. The the last big newsworthy case related to cookies that, I'm aware of, and it's fairly recent as well, really under underlines the fact that the criminals are using networks and sharing information fairly openly. And one of the big underground networks for ten dollars, they were able criminal was able to buy session cookies for Slack and got access to the communications platform and then basically acted as a, a user and made an IT request that then got them deeper access into the organization. So those sorts of things, they happen. And those are the things that, you know, you need to really be aware of is that, it's not just credentials. You need to be looking at all the means of access to your organization, capturing that information, and then automating remediation to prevent that access, from being leveraged. Amazing. Thank you so much. I think that is all we have time for. So let me just move this out of the way. If you want more, you can check out our web page. You can go to spy cloud dot com and our resources page. We have guides, we have reports such as our recently released identity exposure report, and other helpful resources such as an actionable data checklist that we mentioned in this presentation. You can check out our blog and sign up for a monthly newsletter where we'll just round up all of our most important resources for you, and we can send it right to your inbox. And you can also, check to see if your organization has been exposed to any of that dark net data, at spy cloud dot com slash check your exposure. So thank you again for joining us. Thank you to our speakers, Taylor and Chip, and we'll see you next time.
- Video
Webinar: From Zero to Hero: What Your Security Team Can Unlock with Actionable Data
C is for cookie, the missing ingredient in your Zero Trust recipe. Most organizations are somewhere along a Zero Trust journey, either planning, implementing, or reaping measurable benefits from their efforts, whether they actually call the initiative Zero Trust or not. In this webinar, I'll highlight some common gaps in zero trust policy decisions and share how SpyCloud can help. My name is Chip Witt, and I am the senior VP of product management at SpyCloud. SpyCloud transforms recaptured darknet data to protect businesses from cyberattack. Its products operationalize cybercrime analytics and unique data from breaches, malware infected devices, and other underground sources to produce actionable insights that allow enterprises to proactively prevent ransomware and account takeover, safeguard employee and consumer identities, and investigate cybercrime incidents. To begin, let's look at the core elements of Zero Trust. Here we have a standard architecture diagram that should look familiar to anybody that's been researching Zero Trust. Your endpoints and your identities here on the left are working through your policy engine, which which can have a variety of implementations and Zero Trust architectures. That's really controlling and protecting access and a zero trust way to data applications, your infrastructure, and your network as a whole. Regardless of whether you're using secure access access service edge or layered application protections or whether you have the coolest new architecture around data, you're still relying on your policy engine to make those fine grained access decisions. But one of the fundamental problems we see with Zero Trust implementations is they don't have new information with which to make those decisions. You're supposed to be constantly reevaluating and constantly checking how much you really trust this identity and identifying any issues with the endpoint. But you lack valid dynamic information to feed that policy decision. You need inputs from the outside world to tell you when an identity has been compromised and whether an endpoint or device has been compromised. Those additional endpoints help close the loop in your policy engine's decision making. In short, knowledge of your exposures and what's happening in the dark net relevant to your organization are all critical ingredients to making sure your Zero Trust architecture is providing everything you need for the constant and consistent revalidation of your policies that determine what identities and endpoints should be trusted to have access to your enterprise. Zero Trust is all about making decisions based on the inputs given, and threat intel does not give you time sensitive assets that have specific expiration time frames, and they miss key pieces of data that are close to the crime. Threat intel is essentially just too much data and not enough information. SOC teams are drowning and commoditized threat intel, and security data is basically creating a struggle to turn it into actionable insights. SOC teams want to scale their analysis with automated workflows, but the human effort often required to interpret clunky, sometimes unreliable or low quality threat intel data makes it incredibly difficult. Automating critical workflows, including with Zero Trust policy engine decisions with data you can't completely trust brings potential downstream problems with pulse false positives and broken processes. Analysts are needed to take threat intelligence and answer the questions, is this relevant to us? And if so, what do I do now? Data is never refined enough to go to the point of being actionable. If it's not refined or dependable to the point of being actionable, then you can't automate it either. Threat intelligence doesn't provide definitive evidence of compromise. It struggles to provide the intelligence that highlights what criminals are using day to day and doesn't actually give organizations the ability to figure out how they can prevent those actions in their environments. Additionally, immediate reduction for targeted attacks isn't something you can do with threat intel because you can't see the data quickly enough to discern and analyze it appropriately. Threat intelligence is often retrospective and becomes stale really quickly. Manually configuring and training efforts are not only time consuming and tedious, but inefficient and prone to human error. This reactive approach hinders automation initiatives to prevent attacks. There's been a lot of attention on products to block access from other authentication mechanisms, and the policy engines within your framework are using this information to reevaluate access privilege. But what's missing is what's being used by criminals to actually gain access. It's not just usernames and credentials, but it extends to sessions and API keys. The information within session cookies or credentials that are extremely close to the actual crime need to inform and plug into your policy engine so your overall program can respond to any threats rapidly and efficiently. You certainly still need usernames and credentials to protect your enterprise. You also need access to stolen sessions, stolen API keys, which allow you to use your applications in a very similar way to session cookies, are all key ingredients to effective Zero Trust as a whole. Cookie data is so critical because it has the dangerous potential to completely negate all the hard work you've put into authentication improvements with things like single sign on and multi factor authentication. Even if you're implementing passkeys, criminals aren't giving up and seeding defeat. Instead, criminals have recognized they can go to people's devices and steal the authentication or session cookies. They can then distribute them rapidly to other bad actors, and they can use them to get into your applications, VPN, your enterprise. To have a full Zero Trust solution, you need a better set of cybercrime data coming into your policy engine, and it needs to include an understanding of what's going on from the cookie perspective as well. This isn't just hypothetical either. There are a few recent very high profile attacks that all started with someone taking an unexpired session cookie, gaining access to the environment, escalating privilege in that environment, and then taking it from there to a full scale compromise. Actors are using these techniques, tactics, and procedures constantly, but the real issue is that applications don't have any way to detect this, and nobody knows how to find it within their ecosystem. Some of the interesting attacks, there's a leading identity provider breach. Attackers used session tokens. The employee whose credentials were used had synced their personal browser profile and device with their corporate one. Makes sense. Convenient. The threat actor was able to find the credentials of a service account that was saved to an employee's personal profile after they signed into the profile using their work laptop browser. This allowed attackers to access files related to a hundred and thirty four of the identity and access management's provider's customers. The threat actor used the service account, which had permissions to view and update customer cases, to access the customer support system. Among the files the threat actor accessed were HTTP archive files, which are used for logging a web browser's interaction with a website. These contained additional session tokens. The CICD platform breach, data breach was caused by an info stealer on an employee's laptop that stole a valid 2FA backed SSO session. The malware was not detected by the company's endpoint antivirus program, of course, and the malware was able to execute session cookie theft, enabling the threat actor to impersonate the targeted employee in a remote location and then escalate access to a subset of production systems. Because the targeted employee had privileges to generate production access tokens, the attacker had access and was able to steal from a subset of databases and stores. The global video game company breach, is another interesting one because it really showcases the power of the market and the accessibility of this information. Criminals paid ten dollars for stolen cookies on Genesis, a dark web mark marketplace, to access the corporate communications tool, use social engineering to request new multifactor authentication tokens to get access to the network, and then proceeded to move laterally through the enterprise. The threat actors use the authentication cookies to mimic an already logged in an employee's account and access chat channels and then ultimately tricked an IT support staffer into granting them access to the company's internal network. We are seeing criminals go all in on stolen cookies. SpyCloud recaptured more than twenty billion cookies last year, which speaks to their ubiquity in the criminal underground. This amounts to an average of more than two thousand records per infected device. Our findings paint a pretty clear picture that malware exfiltrated session cookies are high value for criminals, and malicious actors will likely continue to pivot in that direction to sidestep multifactor authentication and passwordless authentication. In twenty twenty three, we also recaptured a total of nearly one point three billion passwords, an eighty one point five percent year over year increase from twenty twenty two. And when looking at password reuse rates when within that pool of data, rates remain incredibly high among users exposed in two or more breaches at seventy four percent despite organizations pushing user awareness and training in recent years. Security decisions, even those tied to important initiatives as critical as Zero Trust, don't happen in a vacuum. Arguments for them have to be made beyond just the security rationale and within the context of the overall business priorities for the organization. Increasingly, boardrooms and executive suites are focused on how initiatives and budget requests for solution fit within their chosen risk management framework. Our take on enabling more informed Zero Trust policy decisions lines up well with this focus on risk management frameworks. While this list is not comprehensive, it sheds light on how to position SpyCloud to meet the criteria for protecting digital identities, upholding session integrity, and securing application access for Zero Trust defined within popular frameworks. We call out alignment with specific sections of the Zero Trust architecture and the NIST cybersecurity framework, sections of the NIST special publication on security and privacy controls for information systems and organizations detailing specifically audit and accountability, program management, and risk assessment, the NIST special publication on digital identity guidelines, including the sections helping inform authenticator assurance levels and, of course, CIS top controls. SpikeCloud offers an approach that's more comprehensive and actionable than traditional threat intelligence, powered by analytics that connect compromised entry points to employee identities and giving security teams a seamless integration to automatically remediate the threat. Spike Cloud enterprise protection is powered by our cybercrime analytics. Recaptured data from all layers of the dark net is collected, curated, enriched, and analyzed to drive our products that automate protecting your business and help you take action to protect your business when it matters most. Our solutions include all the insights needed to detect exposure, prevent targeted attacks, and rapidly respond for any remediation efforts to fully protect employees' identities. Why are we different? We have data closer to the crime, and it's unique. And through cybercrime analytics, we produce actionable intelligence. We provide everything you need for the constant and consistent revalidation of your Zero Trust policy decisions. SpyCloud is able to provide real evidence of compromise without unnecessary alerts or false positives. Knowledge of the severity of employee and consumer exposure helps identify previously unknown risks to the business. Stopping criminals requires a new approach, even if you're implementing Zero Trust When getting ahead means taking swift action, distilled answers are essential, and that is the promise of cybercrime analytics. You must prioritize targeted and emerging forms of account takeover and ransomware prevention to dynamically enforce the right policy decisions. But to do so, you need to be able to act on what criminals have in hand before they do. Here we see a screenshot of SpyCloud enterprise protection. Through a malware log SpyCloud collects, we can see compromised assets associated with your company's employees, including infected devices, application credentials, and session cookies, all stolen by a criminal through Infostealing malware. Ongoing monitoring for this sort of information helps shore up Zero Trust policy decision gaps while also providing a clear path to risk mitigation. Our solution helps you respond quickly and effectively to minimize the risk of any exposure, and we help optimize your existing security spend without dramatically increasing the operational overhead on your security team. That's all possible with our automated workflows. Our customers start with SpyCloud to protect their employee identities with our robust integration with Active Directory, and that runs daily scans to prevent employees from choosing weak or exposed passwords. If we do find compromised data, you can automatically reset passwords for active employees and disable high risk accounts. Our exhaustive set of integrations include SIM and SOAR landscape with support for the most major players that your teams are already running like Splunk, Sentinel, Chronicle, and we publish breach and malware records as a high fidelity alert to your SIEM so your teams prioritize and escalate alerts to the appropriate team members. Our data automation gives you the context of identity exposure that goes beyond the simple exact employee email match. Our integrations with source are really interesting and dynamic. They create daily incidents for high priority breach exposure and malware infections and allow you to automate the time consuming piece of investigating raw data and push incidents that need attention, rather than creating noise. We publish all the details of the record that we have available, and each of our playbooks that we include include a starting point for you to not only get the information you need, but to be able to leverage that information for additional remediation for the entire exposed identity. It's not just wiping the device. It's looking beyond and remediating applications and the accounts that are associated with them. Accelerate your Zero Trust initiatives. SpyCloud helps you enable adherence to regulatory and compliance requirements so that you maintain business productivity, helps you free up resources by preventing targeted cyberattacks without adding additional headcount or overburdening existing resources. And SpyCloud also helps you automate protection from employee identity exposures to prevent costly cyberattacks. Why do customers generally choose SpyCloud to protect their employee identities? Well, first, the power of our recaptured data is un unparalleled. We provide context rich data beyond the breadth and depth of threat intel providers. We make sure that the data is highly relevant to your organization, and we capture and publish dark web data faster than competitors to shorten the time period between exposures and threats to so you can act before the criminals can. We take this data and create action driven analytics through alerts that are valuable to your teams for shortening the investigation time, helping them to avoid having to manually correlate or deduplicate data so that they are focused on credentials that truly pose a risk to the organization. Spy SpyCloud scales with the threat landscape through a growing amount of recaptured data we publish daily and through extensive integrations across multiple categories of secured security tools that support existing automated workflows that are already in use in your environment. You're not forced to rip and replace your existing security framework out either. Customers are able to freely layer SpyCloud analytics into existing practices for coordinated response to maximize impact with minimal over organizational overhead. SpyCloud enhances critical aspects of your security defenses to safeguard your sensitive data against the next generation of cyberattacks, but don't just take my word for it. To get a glimpse into the power of cybercrime analytics, start by checking your enterprise exposure. We'll reveal real time insights on exposed employee credentials that are in the hands of criminals, and we'll share those results with you, including any previously unknown exposures that SpyCloud illuminates in a custom report. All you have to do is provide your business email and see the details of your company's risk. This custom exposure report that you'll receive will include an overall security risk score for your business based on SpyCloud data, taking into account malware infections and plaintext passwords, account of malware infected records associated with employee email addresses, which may indicate active infections and exposed active session cookies, insights into third party breach records, exposed executives and VIP credentials, estimated password reuse, and PII exposure for your employees, and finally, specific breach and malware sources with details on when SpyCloud published the data to basically identify customers and compromised data types. I sincerely hope you found this session valuable. Thank you very much for your time.
- Video
Webinar: C is for Cookie: The Missing Ingredient in your Zero Trust Recipe
Learn how to address a common Zero Trust implementation gap that is leaving organizations vulnerable to targeted attacks: users’ stolen session cookies.
Thank you so much for taking the time to join us today. My name is Alex Ash, and I'm the growth marketing manager here at SpyCloud. We here at SpyCloud keep a tight pulse on darknet activity to understand how stolen data exposes organizations and consumers to cybercrimes like account takeover, session hijacking, fraud, and ransomware. So today we'll be talking about key findings from our twenty twenty four Identity Exposure Report. Alright, let's go ahead and get started. Okay. So first, just a quick agenda. We'll be giving a little bit more context on why we do this report and why it matters. Next up, welcome to the showdown. Data stolen by by cybercriminals and traded between bad actors have continued to scale dramatically each year. Case in point, Spy Cloud's total collection of recapture data has grown to more than forty three point seven billion distinct identity records. So here we'll do a deep dive into our most important findings and observations and how NextGen identity attacks are forcing us to reevaluate how we define our digital identity. From there we'll continue our adventure into other important trends. Next on our journey is how to level up the cheat codes, if you will, for how to stay ahead of cybercriminals and other risks. And finally, we'll complete our quest with a few minutes for q and a. And with that, I will hand it off to our presenters. Well, thanks, Alex. Appreciate the introduction. As always, very excited. This is actually one of my favorite reports and webinars to give because it really highlights what we've done, in terms of capturing information and keeping our finger on the pulse of what criminals are actively using. But it also shows kind of the trends, how things are evolving over time, and that's always very interested. I'm the senior VP of product management here. My name is Chip Witt, and I am joined by a cohost. You know, for for those that have oftentimes thought to themselves that, we need help and should, seek the counsel of a good doctor, I know that they had Wallis in mind. Well, Wallis, would you care to introduce yourself and what you do? I I feel like you've done it for me, Chip. Hi, everyone. My name is is Wallis Romzek. I'm our, principal data scientist here at SpyCloud. I'm an applied mathematician. Most of my work for the last decade or so has been in leveraging big data and machine learning to tackle problems in this space. And my work at SpyCloud for the last year and a half or so, has focused on tracking and characterizing cybercrime, and a little bit of the the details we're gonna spell out for you today. Very exciting. Glad to be doing this with you, Alice. This will be fun. Likewise. Let's go. Alright. I think I'm ready. Alright. Good afternoon, everybody. I guess good afternoon for those of you on the East Coast. Thanks for joining us today. As Alex mentioned, the identity exposure report is our opportunity to synthesize what we've seen over the course of one year, relating cyber criminal activity. We create this report to ensure that we keep a close read on the pulse of dark net activity and to ensure that we continue to understand how stolen data exposes organizations and consumers to cybercrime. The number of exposed identities that we see is growing. More and more data relating to more and more people are being compromised. But in recent years, we've also identified a shift in the type of data that malicious actors rely on to compromise those identities. As it says right in front of you on this slide, cyber criminals are stepping up their game. The data under this report are evidence of that, and that's motivated us here at SpyCloud to continue to expand our datasets and be just as dynamic in exploring how emerging and evolving threats put consumers and organizations at risk. Next slide, please, Alex. So let's start with some of the the most important statistics in our report. These data pertain to calendar year twenty twenty three. On average, each breach we published contained one point nine million records, and we published somewhere around fifty five hundred breaches. Those records included well over one billion email addresses and passwords respectively, including at least a hundred thousand master passwords from popular password managers, which is basically like the key to your digital front door. That's troubling. In addition to login credentials, the breach has included thirty two billion pieces of personally identifiable information from social security numbers to birth dates to street addresses to credit card numbers to passport numbers. Lots of different little pieces of us as digital people out there on the dark net. This kind of PII doesn't necessarily allow a threat actor entry into a system or systems the way an email password combination might, but it does enable actors to do a significant amount of damage elsewhere. Open up a line of credit in your name, for example, make a fraudulent purchase, or compromise your identity in some other way. In twenty twenty three, we expanded significantly the types of data that we're collecting to allow us to better understand the criminal market and the realm of the possible. We started adding more credit card information, reclaimed API keys and webhooks, and crypto wallet addresses and session cookies. We also stepped up our malware collection game. And in the course of doing so, we discovered four entirely new to us info stealer malware families. In summary, the theme of this year's report is that the bad guys are evolving. They're using new tactics and techniques, but so are we. We're still keeping our finger on the pulse of both the data that are out there and how they're being used, and that helps us to be equally dynamic in our efforts to disrupt cyber criminals. Next slide, please. So before we get too far into the weeds of the report, let's let's do some level setting and make sure everyone's clear on our definitions and how we're using them at spy cloud. A data breach occurs when information is stolen through unauthorized access to a network or system. Individuals are exposed in those breaches through no fault of their own usually. For better or for worse, actually, that should just be for worse. It seems to be happening more frequently. Most of you have probably gotten a letter from a consumer company or your credit card provider saying that your records have been potentially compromised. We consider a breach record to be the set of data tied to a single user exposed in a breach. If my data were compromised in, say, the twenty three and b breach late last year, all of that information would populate one entry in our database. I feel like most of us know about malware, but better safe than sorry. Malware is software specifically designed to harm or exploit computer systems, networks, or users. Malware can take a number of forms, but we focus mostly on recapturing infostaler malware and Trojan malware infection data. Malware victim data is information that's been exfiltrated from devices infected with malware. Typically, usernames and passwords, sometimes session cookies, anything you've saved to autofill, PII, and device and system details that can be used to impersonate victims and actually, to also unmask criminals, but that's that's a different webinar. Next slide, please, Alex. So getting back to our report. This year we paid particular attention to the concept of a digital identity. A digital identity is the combination of our quote unquote traditional credential data with the PII and other victim data that I described a few slides ago. Malicious actors are moving beyond the traditional, the use of stolen username and password pairs, and broadening their tactics, techniques, and procedures to perpetrate crimes against consumers and organizations alike. So instead of just worrying about protecting their employees or customers emails and passwords, organizations also now have to worry about protecting their digital identities, which can occasionally be stolen outright but more frequently are cobbled together using data from a number of different sources. Given the breadth of data that we're seeing at spy cloud, we can be certain that threat active threat actors have in fact increased the scope of these attacks and are giving organizations and individuals more to worry about. Next slide, please. Okay. The average player. You may be sitting there thinking, I am pretty conscious of OPSEC. I've done this for a while. Digital identity exposure probably isn't an issue for people like me, and you are probably wrong. SpyCloud's data shows that the scale of identity exposure today is massive. In twenty twenty three, we collected forty three point seven billion distinct identity records. The statistics you're seeing on the screen are reflective of a random sample of those identities. And in that sample, the average identity that was exposed and traded in the criminal underground last year is associated with four unique usernames or email addresses. Of those, there's a an exposed password for sixty seven percent. The average identity has been exposed in nine breaches and has data in fifteen distinct breach records. In one in four of those records, the identity's network or physical location was revealed, so a street address or an IP address, for example. And twenty percent of each identity's records showed signs of infostealer malware infection. Those are aggregates. Right? Some identity stats were higher, some were lower, but I think the point here is clear. There's a lot of information out there. And setting aside the potential for personal harm that this information represents, the details it contains often include credentials to one or more of an employer's application systems, which can effectively turn a personal compromise or a third party breach into compromise of an organization. And I think now with that, that we're heading into our malware section. So I think I'll toss the baton over to you, Chip. Outstanding. Really interesting stuff there. Double clicking on malware a bit. In twenty twenty three, spy cloud started tracking more advanced forms of malware as well as collected new forms of exfiltrated data that are fueling identity risks. For this year's report, we doubled down on our efforts to understand the impact of malware following a notable shift in threat actors' tactics and amplified role of the underground marketplaces. The most alarming trend we see today, bar none, is that of malware. Infostealers and other types of malware exfiltrate valid authentication data and login credentials in addition to session cookies and are even beginning to target pass keys. In in the hands of a criminal, this data makes it easy for an attacker to mimic consumers or employees access to networks and applications with a high degree of success. The rapid rise of malware, specifically in infosteelers, is one of the biggest trends that we continue to observe. In twenty twenty three alone, infosteeling malware use tripled by criminals. We saw stealers skyrocket in our recaptured data with as many as one in five people, twenty percent, already the victims of an infostealer infection. The reasons behind infostealers climb to the top of the leaderboard are really clear. They're cheap. They're highly effective in exfiltrating a treasure trove of useful data, and they yield a high return on investment for the criminal. The shift to malware as a service model, is an additional boon for for the criminal, and research suggests that twenty four percent of malware distributed as a service is specifically from info stealing families. Next slide. Of the nearly thirty five hundred breaches we analyzed, over two thousand or about sixty one percent of total breaches were malware related and included over three hundred and forty three million stolen credentials. With valid credentials in hand, cybercriminals have a shortcut into employee and customer accounts that they are more than willing to leverage. Next slide. The records we captured in twenty twenty three were siphoned by fifty two Infosteelian families. Four of these families were new to the scene just last year, Atomic Steeler, Mystic, Exela, Atlantida. Two others, Luma c two and Ryze Pro emerged in the second half of twenty twenty two, but grew exponentially in twenty twenty three. For instance, LUMA c two records in our recapture data skyrocketed by more than two thousand percent in less than six months. Getting a little used there. It was more than LUMA Steeler's rapid growth though that caught our attention. The strain came with new features previously not available in commodity infostealers, such as exfiltration of local password manager vaults and configuration files from remote desktop software. SpyCloud researchers also found evidence of exfiltrated browser based 2FA secrets. This is all on top of the typical capabilities that we've seen in other infostealers, including the the stealing of credentials, session cookies, local files, crypto wallet private keys, and cached browser data like autofills. Our researchers' analysis of data exfiltrated by LummaC2 two showed that a log from a successful infection was three times as large as those from other info stealers, including prominent families like raccoon and redline stealer that people are really already familiar with. More and more complex data likely means more and more sophisticated crimes. There's already measurable indications of a link between info stealers, the data they steal, and ransomware attacks that can follow. And these types of correlations are likely to increase as this data glut from infostealers continues to increase. It's obvious that there's now a universal dependence on smartphones and tablets, which in turn creates a pressing need for better visibility into mobile device threats. This definitely is on the rise. Researchers found a fifty one percent increase in the number of unique mobile malware samples in twenty twenty two, coinciding with a record number of mobile phishing attacks. We recaptured more than ten point five eight million mobile records siphoned by malware between August and December of twenty twenty three. While financial fraud is a major motive behind mobile malware attacks, a successful attack can also lead to sensitive data compromise, disruption of operations, and reputational damage. Yet IT and SOC teams have limited or no visibility into mobile devices and struggle to secure them, leaving a massive gap in exposure. So we'll transfer transition into some other trends. Wallis, what do you have for us? Password reuse continues to be an issue here on this slide. For context, SpyCloud recaptured one point three billion passwords in twenty twenty three. And among the accounts to which those passwords belong, password reuse was seventy four percent, meaning that a digital identity or email credential reuse passwords in seventy four percent of its distinct records. Stop reusing your passwords, please. That statistic is up two percentage points from twenty twenty two, and the all time reuse rate for those same identities is also up, up, over twenty twenty two. This problem is not unique to the private sector. Government employees struggle with this too. Alex, can we go to the next slide, please? In twenty twenty three, we recaptured more breaches containing dot gov emails than ever before. And within those, the password reuse rate was also on the rise, up to sixty seven percent from sixty one percent in twenty twenty two. As a former government adjacent employee myself, this statistic isn't exactly a surprise, but it's certainly worth sharing since digital identity exposure may have even greater implications for the government sector. Given that nation states and other sophisticated actors can and do target critical infrastructure agencies, it's especially important for these organizations and their employees to lock things down. And yet, our data is showing that government identity exposures continues to be an issue. Passwords are also stagnant. It's another one of the trends we observed. This is about public sector employees. They need a little nudge to get creative with their passwords. These three, password, pass one, and one two three four five six were the top three most common passwords associated with dot gov emails in twenty twenty three. I will say that the top three passwords outside of the public sector are not much better. Variations on one, two, three, four, five, six, etcetera made up more of the top twenty passwords than, is acceptable in my personal opinion. And more Taylor Swift references than I'm comfortable with as well. I know. There were there were so many. Other passwords were, like, a little bit more complex, but only slightly. Seasonal trends, current events were the basis for many of the passwords we saw. Fantasy football as a password was observed one point one million times in twenty twenty three. No zeros, no dollar signs for the s. Fantasy football, straight up. We saw some adverts alluding to the Hollywood writer's strike during the five months it was ongoing. We saw references to Lionel Messi as he joined Enter Miami. We saw tons of references to the Barbie movie and Chip, for you, tons of references to Taylor Swift. Awesome. In addition to password reuse, 2023 also saw an increase in stolen session cookies exfiltrated by Infostealer malware. Alex, can we go to the next slide, please? There we go. The victory token. All info stealer siphoned data is immensely valuable to criminals and to at SpyCloud because of its high fidelity. But session cookies and tokens stored in a browser are really just like hitting hitting the jackpot. With a valid cookie in hand, criminals can simply sidestep any authentication mechanism, including multifactor authentication, and hijack a session in an instant. Next slide, please. Oh, that was cute. The risk of, hijacking is high. Last year, SpyCloud recaptured more than twenty billion cookie records. Not all of them session cookies, but twenty billion cookie records with an average of more than two thousand cookies per infected device. Session hijacking effectively turns cyber criminals into employee clones. It gives them unfettered access to sensitive applications and data, but many SOC teams don't yet have the tools to remediate this threat. And consumers are at equal risk. Session hijacking enables bad actors to effectively walk right into websites for commercial organizations or banks and make fraudulent purchases, open new credit lines, or drain loyalty accounts. The sheer number of cookies and devices here indicates that leveraging malware siphoned session cookies for next gen account takeover is already a valuable tactic for threat actors. And as more organizations adopt passwordless authentication, this is this is only going to escalate. Speaking of shared numbers, I think we're segueing into some of our notable breaches. Back and up. For sure. Plenty of high profile data breaches make the news every year, but there are thousands of other large breaches that no one ever hears about. No one, of course, except for a select group of criminals, and, you know, that's not good for for you protecting your organization. Right? So these breaches are first shared by small private criminal channels for fast, high return monetization before they're offered to a broader darknet net audience, and that's where they oftentimes enter into the threat intelligence sort of piece of, of the world. SpyCloud recaptures this data much earlier, and we ingest it into our data as sensitive source until the breached organization reports it publicly. And so now wanna dive in a little bit and share some of the data leaks that caught our attention circulating on the dark net, over the last year. Next slide, please. So the the report obviously outlines a lot of stuff that happened in twenty twenty three, but we we looked at four specific ones that we thought were were relatively interest interesting from the perspective of sharing for this this particular talk. The first one is WhatsApp, at nearly three hundred and sixty five million records leaked. This was data allegedly belonging to messaging platform WhatsApp owned by Meta, and this information was leaked online at an unknown date. The data contained phone numbers and other personal information. This leak was being privately shared on a messaging platform. Twitter, of course, now X, almost two hundred and four million records leaked. In January 2023, scraped user data belonging to social media company Twitter, now X, was leaked on a hacking forum. This data contained email addresses, full names, screen names, and other personal information. Some of the scraped data was made available in the forum for free. The threat actor responsible for collecting the data reportedly manipulated a bug in an exposed Twitter API to scrape the records. This API vulnerability existed between June twenty twenty one and January twenty twenty two, allegedly allowing other intrusions as well. USPII, one of the most creatively named breaches, two hundred and forty eight million records total. This is personally identifying information allegedly belonging to US residents, and it was leaked online in an unknown date. The data contained names, addresses, geolocations, and other personal information. The source of this leak, which was being shared privately in an underground criminal community, was not known. So don't know how this information came into being, but it was out there, and criminals were using it. And the last one, Luxottica, about two hundred and four million records leaked. And this data allegedly belonging to Italian eyewear conglomerate company, Luxottica, was leaked at an unknown date. The leak, which contained names, email addresses, phone numbers, addresses, and other personal information, was being publicly shared in online forums. The company later confirmed that it suffered a data breach in twenty twenty one and blamed it on a third party incident. The breach impacted seventy million customers, so not not small. Next slide, please. And, of course, everybody heard about MOAB, also known as the mother of all breaches. This included twelve terabytes of data. That's a lot of data no matter how you count your data. And this included credentials, from thousands of meticulously compiled and reindexed data leaks, breaches, and privately sold databases over over the years. So, recapitulation of data that had been used. But why do criminals share data? Well, because they found it useful, and they wanna share it with others. It's still an active trade, so it's likely still of use. SpyCloud's analysis found that ninety four percent of the data was already in our repository by the time this MOAB leak became popularly known. But approximately one point six billion records were new, meaning they were previously either released in sample format or had not been released publicly. And so, of course, we did, the the the right thing and pulled that six percent of the unknown data into our database, so it's available as well. Next slide. We wanna round this presentation up with a summary of actionable ways customers and prospects can use this data. Wanna discuss how the key to disrupting criminals' ability to profit off of stolen data is to understand what bad actors know about your their organization and customers and use these insights to identify riskiest users and to act quickly to protect them, giving power back to enterprise and leveling the playing field against the cybercriminal. So where do we go from here? So I think that this is where a talented game developer might do some cool bleep bloop transitional music, but we'll jump quite right into the, the next bit of information here. The key takeaway is really, today, protecting your organization against attacks that stem from exposed identity data means shifting from a device centric focus to an identity centric approach. Not device, identity. It's important. Security teams need quick and accurate evidence when any component of an employee, contractor, vendor, or customer's identity is compromised. You need to ask yourself the question, can you tell when an employee has been exposed? With early access to recaptured dark net data, teams can negate the value of stolen information by quickly identifying the riskiest users and acting quickly to protect them. Next question to maybe ask yourself is are you taking into account next generation emerging threats? Criminals are evolving their tactics, and if your solutions aren't keeping up, that's a big, big problem. As digital identities grow and there are more access points, do your current tools, processes take this into consideration and all these extra ways cybercriminals gain access to credentials. Even if you have things like multifactor authentication, cybercriminals are now finding ways to circumvent your organization need to be and your organization needs to be prepared. Post infection remediation, which this means looking beyond the device in response to a malware event and knowing what user access information and which beyond just credentials can which can include session cookies, two of a secret tokens, and API keys, and for what applications those credentials open up doors. And this is both on prem and in the cloud, and you need to include this as part of your playbook and your protocol for dealing with malware events. And if you're not looking beyond the machine, that's pretty important. And the reason why we stress that is the machine centric approach has been long held to in IT circles. You have a malware event. You focus on the machine, isolate that from the network, and then you burn the hard drive. And that is outdated now because info stealing malware quickly installs itself, steals what it needs to steal, and then uninstalls itself. So the remediation of the device is almost a secondary factor in remediating. In fact, it it's it's it's largely useless at that point because the information the criminals are now using is out in the wild the second that info stealer collects it and exfiltrates it, and that that requires a different approach. So I think that we are ready to transition to Q and A and I think that's my cue to summon Alex back to the call, to see what questions have emerged. Yes. I'm here. I think you can drop your any questions in the chat. Let me know if if that's not the case, but we did have some questions. Okay. So these stats are wonderful, but also terrifying. If I'm not mistaken, it seems as though criminals continue to innovate and find new ways to leverage how a user accesses corporate resources to do bad things. What hope is hidden in this data that illuminates a possible path forward for responding more efficiently or even getting ahead of the problem. Chip, you just spoke to that a little bit, so I'm gonna throw this one to Wallis. Alright. Yes. Definitely. Criminals are just as creative as the rest of us. They're always coming up with something new, and the data in this report confirmed that for us. What heartens me in this report, I think, is the breadth and depth of the data that we accessed in building it. I'm our principal data scientist. My job is to leverage our data to help our customers respond more efficiently to these risks. And what I see here are data that are useful in things like pattern identification, in uncovering, as yet unseen tactics or techniques. Those things that criminals obfuscate as they act, but are maybe visible in the data after the fact. You know, I have, I have a kindergartner, and she's working on deductive reasoning right now when they read stories. They'll read a story about, little Chip who always rides his bicycle to his friend's house after school, and while he does it, he eats a cookie. And And then maybe one day, little Chip doesn't arrive. And so they asked the kids then to figure out what happened to little Chip. If you look outside your house, do you see his bicycle? No. So he didn't make it that far. If you walk the route, he usually takes. Do you see cookie crumbs? No. So he either didn't eat a cookie, but he always eats a cookie, or he didn't ride that way today, and so on and so forth. So they eventually get the kids to the point of, like, where did things go wrong? If I know what usually happens, where do I think things went wrong here? So the same that's kind of a convoluted example, but I think, it's useful here as well. If If you know what usually happens, then that knowledge is a starting point to find out where things went wrong. Modeling cybercrime activity is a complex process, but more data on companies prior to known attacks and more detailed data on those companies at all periods of time help us to identify common attack surfaces, common vulnerabilities, qualities that make companies attractive targets, etcetera, etcetera. So even slight improvements in that understanding help us move our efforts from remediation to preventative. So I guess, Alex, back to your original question. I see the fact that we're observing new and different types of victim data as a positive factor in our efforts to combat those data being compromised in the first place. Amazing. Thank you. I don't know where your daughter goes to kindergarten. It's certainly that's not the curriculum that we had, so love love to hear that. Okay. Confirm Chip does love cookies. So I assumed. Yes. Next question. Great to see mobile malware data coming into view. Are there fundamental differences between mobile and standard PC malware in what criminals are able to access or target? Chip, I'm gonna send that one to you. Yeah. There are are, of course, a lot of similarities in terms of the type of information that's valuable to criminals. And as we all know, people use their phones as a centerpiece to their lives, including increasingly their financial transactions. So to date, our collection of data has been focused primarily on recapturing mobile banking Trojan logs due to their impact on businesses and consumers. Many of these logs include not only a complete credit card detail, but also information on the individual, like birth date, Social Security numbers, mobile device pins, and other really sensitive information. So that's where we're primarily focused right now in terms of what we're collecting for mobile mobile malware. So that's that's the difference between the data is it's a little bit more focused. Gotcha. Thank you. Mhmm. Next question. I read somewhere that criminals are using criminal ecosystems to initiate ransomware attacks. Is there any relationship between what SpyCloud is seeing in info stealing malware and these ransomware attack chains. Wallis, this one is all you. Yes. Definitely. I am very interested in the data we're seeing coming back from info stealers, because of additional work we're doing. The research is still ongoing, but we've, in in trying to move from remediative to predictive of ransomware events, I'm trying to identify some of the relationships that exist, ahead of those events. So the research is still ongoing, but we've identified, for example, some significant, and I mean that in a mathematical sense, relationships between certain types of info steal of course, I do. Certain types of info stealer malware and ransomware events. So we know that we're seeing more evidence of infostealer malware in rec in recaptured records, period. We can never know, the true extent extent of ransomware events, but I feel confident saying that they're not gonna slow down. So this is an area of focus for our data science team, in twenty twenty four. We're exploring the relationships between these types of infostealer malware and ransomware events to determine I've certainly seen it be correlative. I don't yet know if it's predictive. We're exploring that relationship. We're exploring a number of others as well to determine how they matter or don't to a model of the factors that precede ransomware events. We're thinking about compromised SSO credentials. We're thinking about compromised administrative credentials, associated cookies, etcetera. But, yes, thus far, we've observed both strong correlative and statistical relationships between infosteeler malware infection, and follow on ransomware events. And I'll add just one little thing. It does vary by infosteeler family, which I find really interesting and hope to get to the bottom of sometime soon. Awesome. Interesting. Love that. Any not seeing any other questions come through. So if there are, go ahead and drop them in the chat right now. If not, any other closing, thoughts on the report overall, Chip and or Wallis? No. I just think that this is a tremendous opportunity, for us to really kind of take a breath and look at the volume of data and its meaning. And so this is always an eye opener, not only for our customers and partners, but I I I find this tremendously valuable to just, you know, reinvest, dig in into where we're going next. And and, of course, you know, with with Wallis's additions and some of the places that we're going with product, these are in deed interesting days, and, we're in the fight with our customers, with our partners to put this data to good use to prevent criminals from profiting off the data that they steal. That's exciting to me. Yeah. I I don't think I could say it better than that, Chip. I'm excited to work on stuff like this. I'm excited to put it out there in the world. Hopefully, it helps some people. But, Alex, I will ask if I can have my my sorceress, avatar for my own personal use. Yes. I will happily send that to you. Also, our cameras aren't aren't on, but I do have blonde hair. So if you see me using that That's fine. We can share it. Amazing. Well, thank you so much for joining us. To anyone still here, you can always, go to SpyCloud.com to check your exposure. We have an amazing tool for that, and it will help you identify threats to your organization, including malware infected employees, stolen session cookies, recency of breach exposures with the exact sources, dates, and more. You can get far more information, than you would have ever thought possible. It's it is such an amazing tool. You can also sign up for our newsletter, on our website and, check out any other great resources that we have, other guides, other research reports. And that is all we have for you today. So, with that, I will go ahead and close this, and I hope everyone has a great rest of your afternoon. Yep. Thank you for joining us. And, Alex, Wallis, thank you for, for joining me. This has been awesome. Likewise. Thanks, everyone. Thank you.
- Video
Webinar: An Inside Look at Game-Changing Threats in 2024
In this webinar, we cover top trends from the SpyCloud 2024 Identity Exposure Report. Learn about the identity threats putting organizations everywhere at risk.
So thank you for joining us today. I'm Emily at SpyCloud, and today's demo slash webinar hybrid or as some like to call it a demo, we'll we'll be giving you an inside look at SpyCloud's consumer risk protection for financial services, showing how you can better safeguard consumer digital identities and stop high risk attacks tied to malware, helping you more confidently and efficiently answer the ultimate question, is this a legitimate customer trying to do business with me or a criminal using stolen information? So our subject matter expert today is Colette Tomasiak here at SpyCloud. She's our director of product marketing. Colette's going to start out by giving us some background on the massive scale of identity exposure within the financial services industry and then jump into a live demo that exemplifies how SpyCloud's API, can be leveraged within your own applications. So for those of you that were able to join us live today, thank you, and please feel free to chat with us and use that q and a feature in Zoom to ask questions. And we'll try to leave some time at the end to address those, and anything we aren't able to address live, we'll make sure to follow-up with you. So, Colette, we'll hand it over to you. I'm excited to hear from you today, and let's dive in. Perfect. Welcome, everyone. So before we get started, wanna give you some scoop on who SpyCloud is. So our mission is really to help you disrupt cybercrime by enabling you and your teams, whether it be security fraud or even application and product teams, to really act on what cyber criminals know about your business and your consumers. And while we solve for a diverse set of use cases focused on leveraging our darknet telemetry to safeguard digital identities, today, we're really gonna be focusing on SpyCloud's consumer risk protection solution. So criminals are really increasingly motivated to exploit customers' poor cyber hygiene and discover new ways to profit from account takeover, both in the traditional use case of breached credentials to log into customer accounts as well as emerging or more sophisticated techniques like session hijacking. So really businesses today need direct insights into their customers' exposures that include authentication or access details, including credentials and cookies leaked in breaches or exfiltrated from malware infected devices. And with SpyCloud, your customer exposures don't have to affect your business's productivity or even your bottom line. So our consumer risk protection solution allows financial institutions to really derisk consumer compromise. And we do this by enforcing strong passwords at account creation and identifying compromised users at login or at the point of transaction to really uphold and maintain account integrity. We also help enterprises maximize operational efficiency by automating that ATO prevention, and the efforts around it to decrease that need for manual intervention. We also help you uncover undetectable risks by identifying malware infected consumers and really preventing MFA and even pesky bypass to protect your users' web sessions. So now that you have a sneak peek into who SpyCloud is and what our consumer risk protection solution offers, let's get into some of the challenges, that are facing financial institutions today. So a critical factor contributing to the success of account takeovers is the challenge of actually discerning the legitimacy of individuals interacting with your site. And the ATO problem is intensifying with the tax soaring three hundred and fifty three hundred and fifty four percent year over year. So while security teams are really doing what they can with existing solutions to strengthen customer account security, they're faced with challenges that are outside of their control, like a user's poor security hygiene and behavior that puts their own digital identity at risk. And our own analysis reveals that it's still a concerning seventy four percent password reuse rate amongst individuals who were exposed in two or more breaches, which this significantly contributes to the success of automated ATO attacks. And whether it's their own poor password hygiene or data that's been exposed in breaches outside of their own control, meeting customer expectations really involves staying ahead of innovative criminal tactics and implementing more robust measures for account safety. And it's still a substantial seventy three percent of customers really perceive the brand as being accountable for preventing ATO and protecting those consumer credentials, really emphasizing importance of trust for long term customer satisfaction as well as loyalty. So in the face of these evolving criminal tactics and heightened impersonation skills, adopting new solutions really becomes imperative, and the tools and solutions that enterprises use need to provide that visibility necessary to proactively decrease risk, but also enhance overall security. So how can you tell if your customer is an actual consumer or a criminal? Or are you able to even tell if that customer's credentials have been exposed via a malware infection and that they're at high risk of account takeover? So despite a robust lineup of ETO prevention tools and organization might have in their their toolbox, critical insights still remain missing that leave visibility gaps and keep doors open for attacks. And while many tools provide information on data exposed in a breach, there are still really limited solutions that provide definitive evidence that a user has been infected with malware. And this is just one element of it. On the other side, no one's able to innovate as fast as a cyber criminal looking to profit, and it's becoming increasingly difficult for organizations to keep up with the pace at which cyber criminals are evolving their tactics. And this includes MFA bypass, like through a stolen session cookie that was exfiltrated from an info stealer malware infected device. And this grants that criminal access to an already authenticated session, completely sidestepping authentication protocols put in place to really preserve account integrity. And we know that fraud and security teams want to be able to close those visibility caps and really keep up with innovation and new attack methods, but new solutions that are being considered really need to increase account security but without sacrificing team productivity, customer experience, and your organization's bottom line. And we know automation is essential to that, and SpyCloud really supplies you the data you need to proactively protect accounts while also seamlessly integrating our solutions into your already existing workflows. So how exposed are your customers? So we did a little experiment, and we ran the top fifty banks operating in the US according to total assets, based on S and P through SpyCloud's database to show you the volume of malware infected users with exposed credentials, PII, and other data. So you can see that for these top fifty banks collectively, on average, there are over six thousand infected consumers and a total infected customer count of over three hundred and twenty two thousand. And this is all just based on our sample data from the last six months. But there is one caveat to mention around these numbers. The numbers are only a minimum reflection of the actual exposures tied to malware, and that's because our accounts for this data pool only includes the infected consumers where the company URL was included in the malware log. So this doesn't account for active infections that haven't yet captured the consumer's login for the sites they haven't accessed yet. So the point is the number of infected consumers you are doing business with is likely much, much higher. So what data do you need to understand if a consumer is truly a consumer or a criminal taking over the account? And with data, there's always a concern. Data is commoditized. Right? Intel data can get stale really quickly, and it's hard to make informed decisions when the quality of your data is limited, old, or inactionable. So SpyCloud collects data from dark net sources that really other providers simply can't access, where intel is fresh, it's rapidly delivered as we continuously ingest new data. And our intent is to be your go to source for the missing data that you need to really act on what cyber criminals know about your consumers while also seamlessly fitting into your existing workflows to help scale detection, response, and enable you to customize the the action that you need to take to proactively protect consumers' digital identities and prevent that account takeover. So with clear visibility and a more comprehensive view into your consumers' exposures, SpyCloud helps you differentiate between high risk and low risk profiles and really eliminate the guessing game of customer or criminal. And a critical component of essentially winning at this guessing game is realizing that an identity is more than just credentials. And for this, you need data diversity. And our repository has over two hundred plus asset types that we recapture and alert on. So when thinking ATO prevention with credentials, think email plus password, think session cookies, think pass keys. And coupled with our password cracking capabilities, ninety percent of our passwords are available in plain text, which makes it incredibly easy to determine if your user's credentials within your application have also been exposed elsewhere. And this is just one layer. So SpyCloud also gives you insight into sensitive PII, like date of birth, Social Security numbers, driver's licenses, and more. And these are all potential tools for impersonation and identity theft. But, also, we give you financial data such as exposed banking information and credit cards that are often used for fraudulent activities. But the cherry on top of all of this is SpyCloud's ability to detect if your users have been infected with info stealer malware and report on what unique authentication data, like session cookies, have been exposed. So our analytics really correlate billions of data points from diverse sources to uncover exposures across your consumers' digital identities to really give you the confidence to take the right action but at the right time. But what about the consumer journey? A common concern really with security teams and fraud teams is balancing account protection without creating unnecessary friction in the journey. And by knowing what cuss what criminals have in hand to use against your business and your consumers, you your teams can really devalue that and force friction with the customer base where it needs to happen, but not across the board. So for low risk users, they should experience a more seamless journey, and enforcing this should be super easy and really an automated workflow for your teams. For high risk users, on the other hand, like ones infected with malware, this is where you might consider little more friction acceptable. And with SpyCloud's Darknet Telemetry, you can customize the experience based on the insights that you now have into the consumer's exposures. And then the actions you deem appropriate based on their level of risk and apply friction only when necessary. So customizing the journey should be really straightforward and allowing you to neutralize the value of those stolen credentials, so you can enhance a fit efficiency by automating that follow-up authentication and really reduce friction for low risk users and ensure an overall positive and secure experience within your site or application. So next, we're gonna walk through a demo of both low risk and high risk user experiences and what it could look like, based on the data you can leverage with SpyCloud to make those decisions. So just a disclaimer, this is not our product. This is just kind of an example simulation of where you can plug in SpyCloud's API and what that could look like in your potential site. So let's flip over to the demo. Here we have a fictional let's call it a bank, and this bank's called Spy Factor. And we wanna explore two use cases. We're gonna start off with low risk of ATO. So what this looks like is everything on the left hand side over here, you can see it correlated to the API call on the right so so we can follow along. But in this scenario, for a low risk user, we have Elise. Elise wants to log in. She wants to take a look at her bank account, maybe make some transactions, all the good stuff, and she's gonna log in. So we're gonna run that data and take a look. And here we see that there are some breaches tied to Elise. And you can see recency of it, number of exposures, plain text password associated with it. But here you can really click in and get more information on the actual breach. So we're gonna look at Luxottica, for example. So this one is Luxottica. It's an Italian I work conglomerate company. They also manufacture Ray Bans. Maybe Elise was really into Ray Bans like everybody else and then got her information breached through this site. But here you can see additional details like the recapture date, the number of total records, the type of breach it is, and then additional assets exposed in this breach. So with this information, you can determine the type of action that you wanna take for Elise when she logs in to her account. And while some might choose no friction, which means do nothing, for financial institutions, a little friction probably is a little more tolerable, especially as consumers probably will tolerate that when it's their financials at stake. So here, what we see most of our customers doing in terms of the type of action taken is MFA. So we're going to make sure that it is Elise actually logging in and checking her bank information. So Elise is gonna log in. She's going to get an SMS notification with code to verify her identity. She's gonna plug that in, and then she's able to verify her account, log in, and proceed with making any other transactions desired. So let's look at what a high risk situation would look like. So when a user is infected with malware, with exposed credentials, here we're gonna look at Arden. Arden wants to log in to her account using this password. We're gonna run that on our back end, and here we're gonna see that there's malware tied to this specifically. Number of breaches, number of passwords, all of that, but we're gonna double click into the specific malware. Here you can see the details on the info stealer, the type of kind of malware it is, number of records. But here you also get all the additional credentials stolen for this user from this malware infection, and you can even see some password reuse across two sites. So, again, for this one, giving that it is more of a financial scenario in terms of protecting their information and then their funds, password reset is often what other customers choose. Just customers are willing to accept a little bit more of that friction, especially when it comes to protecting their account. So we're gonna have Arden do a password reset. So let's say when she goes to log in, we're gonna run that information, and now we're gonna let her know that we want to to protect her account, and she needs to update her password. So first, we're gonna verify that it actually is Arden. So she's gonna get the SMS code, verify that, and now she gets to go in and change her password. So she has her old password here. And for the new password, she's gonna wanna use Main Street exclamation point. So we're gonna put that in here. And then what SpyCloud then does is we're gonna take just the first five characters of that hash and run it against our database to see if that password has been used before. So if she goes to reset that password, here you can see the hits that we got based on just the first five characters of that hash. To look for an exact match, we're gonna wanna find the hash that's ending in four eight d b. And if we look down here, we can see that this one is the specific password that she wants to use, and there's only seven other exposures and times it showed up in our database. So there's two things you can do here. You can allow her to use this password, or you can also suggest to the customer to choose a more secure password. So it's up to you in terms of how you would want to tailor her experience for this. But let's say, great. This password's accepted. She gets to log in, and she can now make financial transactions, check her statements, transfer funds, whatever she likes to do. And that's kind of the overview in terms of how you can tailor the journey and take different actions based on the risk in terms of what you're willing to tolerate for a risk level and what you feel your customers might be able to tolerate in terms of friction. So here we can go into any q and a. So you can post that, in the Zoom chat, and we can tackle that. But that's it for the overview of SpyCloud and what we offer and how you can customize that journey using dark net data from spy cloud.
- Video
Webinar: Consumer or Criminal? An inside look at SpyCloud’s Consumer Risk Protection for Financial Services
This demo/webinar shows how SpyCloud helps financial organizations safeguard consumer digital identities and stop high-risk attacks tied to malware.
I'm Emily at SpyCloud. And in today's demo webinar hybrid or as I'm eagerly waiting to say, a demo, we'll be giving you an inside look at SpyCloud's consumer risk protection solution for ecommerce, retail, and really any company that has a vested interest in protecting their customers' account integrity and finding an automated way to reduce the risk of account takeover and online fraud. And today, we'll show how SpyCloud can help safeguard consumer digital identities and stop high risk attacks tied to malware. So you can more confidently and efficiently answer the question, is this a legitimate customer trying to do business with me or a criminal using stolen information? This session is meant to be both interactive and informative, so please add questions using the Zoom q and a feature, and we'll leave some time at the end to address those. Our subject matter expert today is Marc Gorelick, our solutions engineering manager here at SpyCloud. And Marc has extensive hands on experience working with organizations that are striving to provide this secure customer experience. So looking forward to hearing some insights from you today, Marc, and let's hand it over to you. Thanks, Emily. So as, as Emily said, if you have questions, please, by all means, interrupt me. This would be a lot more interesting with questions and answers as opposed to me just droning on. Don't really wanna hear myself talk. I'd much rather hear from you folks. So, with that said, let's dive in, shall we? So first, who are we? SpyCloud's mission is to disrupt cybercrime, and you might reasonably ask, well, how do you go about doing that? And the answer is that we have a tremendous amount of information about your customers. In many cases, we have many, we have digital assets about their identity, their usernames, passwords, cookies, and so forth. And our mission is to help you disrupt cybercrime by enabling you and your teams to act on what cybercriminals know about their identities. And we're gonna focus specifically on customer risk protection today. So the list of items or the list of things that we can do are listed across the bottom, and we have a lot of different capabilities that many ecommerce organizations find very valuable. So how are we going to help you fortify account security? So there are really three elements that we wanna emphasize today. The first one is to reduce or derisk, as we're saying here, customer compromises. And the way they're going to do that is we're going to enforce strong passwords at the time that accounts are created. We're going to check to make sure that accounts haven't been exposed, and, that can be done either at login time or transaction time. We're going to improve your operational efficiency by using automated methods to take advantage of this information. It is our objective to make your lives easier and not more difficult, and the way we're going to do that is that by automating these, security checks, we can reduce the need for manual intervention. And then the identification of like, I guess if they were undetectable, we wouldn't be able to detect them either. But what we're really saying here is that we have ways of finding out that or telling you, I should say, that your customers are risky, without in in ways that you wouldn't be able to do without us. So for example, we can identify malware infected consumers. We harvest tremendous numbers of cookies and so forth, and and all of these are ways that you can find out whether your consumers have been exposed. So, the real problem that we're that retailers deal with is, frankly, that their customers have terrible IT security hygiene. And criminals know this and have been taking advantage of it in huge huge quantities. So as we say here, we have seen, a three hundred plus percent increase in account takeover attacks. That's, by the way, in case you don't know what ATO is. It's account takeover, meaning essentially that someone uses stolen credentials to take over an account. And we've seen a tremendous increase in this over the last couple of years. And then also, since we know everybody's password, basically, we've been able to easily do some calculations on password reuse. And not only do seventy four percent of people that in our database reuse passwords, but this number is actually increasing year over year. It was seventy two percent last year. It's up two percent, which, by the way, boggles my mind because it's something that I I think there's increasing awareness of and scrutiny, but it just doesn't seem to be resonating with average users. So people in the IT security space like us know that this is bad. The message is apparently not getting to your consumers. And and that's a problem because as you can see, the overwhelming majority of consumers think that the brand is actually accountable for protecting their accounts. So if someone gets exposed, they don't blame themselves even though they ought to. Instead, they're more likely to blame to blame the operators of the website that, their identity was stolen on or or used on one or the other. We have a tremendous number of assets that we capture, every day. We're publishing new records. And it last year, we recovered over twenty billion stolen cookies. And this year, and it's only May, we've already recovered over fifty million stolen credit card numbers. And we can take advantage of both of those to ensure that your consumers' information hasn't been exposed. Again, if there's questions here, please let me know. So the real question that we're trying to answer is, ultimately, is the person logging in a customer or a criminal? How can you tell? Are you able to tell their whether the customers had their credentials exposed by malware? Are you able to tell whether the password that they're using is the same password that they're using on fourteen other websites? The the thing that we have working against us, we collectively, meaning not only SpyCloud, but the folks on the call today, is that the adversary is essentially better funded and has more time than us. And, you know, no one no one can innovate as fast as cyber criminals, and it's becoming pretty difficult for us to keep pace. However, we do have some ways to make sure that things like, people aren't bypassing, multi factor authentication. We have we can provide a great deal of enhanced visibility by the use of our data. Any So how exposed are your customers? So we did some analysis on the top thousand ecommerce sites, and we came up with some data. And then, you know, the way SpyCloud works is that we're not collecting data for specific domains. We just collect all the data, and it ends up being applicable to various domains. So we have the ability to look at the top thousand ecommerce stores, and we found that on average, there were seven, seven thousand seven hundred exposures per company. So, you know, that's that's a pretty ridiculous number. And, of course, it read you know, if you if you do the math, that means that there's seven point seven million exposed records out there. But this isn't actually all of it either. All this does is the way we calculated jeez. I can't talk. The way we calculated this figure is that we took records where we had seen a particular target URL for one of these ecommerce sites in the malware data. So what this doesn't calculate is all the people that hadn't visited one of these sites yet. So this number is actually gonna be considerably higher. So not only do we have credentials and session cookies and pass keys and so forth, but a lot of this other value the a lot of this other identifiable data is very valuable to people in in the world of ecommerce because we can get not only credentials, but we can also do some attribution for anti fraud purposes. So, in many cases, we captured over, I should say we capture over two hundred different, different data types from various breaches. So in many cases, we'll end up with not only email password, cookies, and so forth, but we'll also end up with people's names, phone numbers. I'm not gonna read you all the things on the slide here, but you get the general idea. We as I mentioned before, we get a ton of credit card data, including all of the stuff that you would need to actually do a transaction. In many cases, we get the home address for people so that they could potentially use a residential proxy to, to mimic a legitimate user coming from a legitimate location. So this wealth of data that we provide is makes it much easier for people in ecommerce to be able to determine not only whether the person is compromised, but who they are and what and what criminals know about them. So the the trick that, ecommerce, ecommerce web operators deal with is that there's always this tension between additional friction for a transaction and security. And so the good news for for ecommerce folks is that SpyCloud is able to determine how risky somebody actually is. For example, if we find somebody who we have only a couple of credentials for, they don't have extensive password reuse, and there's no malware, then they're a comparatively low risk user and, you know, you can apply less friction to a transaction for such a person. On the other hand, if we find that if the user who's logging in has been exposed with malware, potentially has much worse password reuse, is using terrible passwords that have been repeatedly, compromised, then you may wanna impose either additional friction on the transaction or, or potentially, you might want to instead, have the transaction flight for manual review. If there's any if there are any questions, I can dive into the demo aspect. Yeah. Does anybody have any questions? No questions so far, but good reminder to prompt the audience that we can even unmute you if, you have a more detailed question or that q and a box is still open for you. But, yeah, let's go ahead and dive into the demo. Okay. Great. Let's do that. So the demo today is going to show how SpyCloud's APIs can work to improve the security posture of a particular user by determining whether or not user has been exposed and provide that insight to the web to, ecommerce operators. And, so let me drop my share for a moment and share my browser. I trust Emily, is that, share working okay? Yeah. Great. So we're gonna use a, fictitious company here called Spare Factor. And let us imagine for the moment that Spare Factor is the purveyor of amazing audio equipment. And first, we're gonna determine whether or not we wanna see a low risk user or a high risk user. And, of course, we're gonna start with the low risk user. And what we're going to show is the user experience here on the left side of the screen and the API traffic to SpyCloud's data lake on the right side of the screen. So in this case, here's a user logging in, and they've provided their password. And here we have the password. And so what do we know about this user right out of the gate? Well, they've been exposed a couple of times. Once in the Luxottica breach, and for people who don't know, this is the company that operates Ray Ban. This was a real breach that had many millions of of users in it. And in this case, this is a comparatively low severity record, and the reason it's comparatively low severity is because we don't actually have a ClearTax password for this user. And then they've been exposed a second time in the forever twenty one breach, and you notice, by the way, that as I highlight things, the screen over here shows what I'm highlighting. And in SpyCloud one go, a severity twenty record is one where we have a clear text password. And indeed, you can see here, this is the password that we have for this user. So this password has not been reused, by this user. Here's some more detail about the breach that comes from our breach catalog, by the way. In this case, the Luxottica breach provided us with over two hundred million records. And as you can see, there are a number of assets that we gathered of around a hundred million emails, closer to two hundred million full names. I'm not gonna read the rest of it to you. You get the idea. But the breach catalog provides you with all of this information. So for a, a low risk transaction, you probably just don't wanna provide any friction at all. So we're just gonna say no friction here. The person logs in, and then here they are with some transactions, and they're logged in. Okay. Now let's instead talk about someone who's been exposed with malware. Obviously, a much higher risk. In this case, we have a different user who logs in. This is the password they're using. And when we send this email address to our API, responds with all of these records where we've seen exposures, and most worryingly, they've been exposed by a rise pro stealer. And that gives them, in SpyCloud language, a severity of twenty five, which is a critical severity risk. So you can see all the other information that we got back from the API with all these other different breaches. In this case, here we have this person using the same password on a different site. If we look at the details of this particular breach so this is, this was the second one on the list. This is a Philippine airline. And you can see again, you know, millions of records exposed. And in this case, we're gonna do a password reset for this user. So the person logs in. And because we know that they've been exposed by malware, we're going to make them update their password, and we're gonna do that using SMS. So we have a code texted to them. The code is received, then they put the code in, and now they're prompted for a new password. So this is a key aspect of how the SpyCloud password API works. We're gonna look up their intended new password, and we're gonna do this is something called k anonymity. And, essentially, what this means is we're gonna send the hash a fractional hash of the password, to ourselves, and, then we're gonna respond the API will respond with all matching hashes that meet this first five characters, and you'll see this in action in a minute if that doesn't make any sense. So the person types in their password. Again, this is the password they're trying to use. Here's the first five characters. We send the the website sends this five characters. That's actually six. That's five characters to the API, and the API response will spit back everything that matches this first five, and you'll see this in a second here. Okay. And so what happened is this password partial hash was sent to our API, and our API responded with over two thousand partial matches. But the one that really matters is this one that ends in two four eight d b, which is right here. And what this tells you is that this password has only been exposed in SpyCloud's data seven times, which is a very small number. Bearing in mind that we have over twenty five billion clear text passwords, the likelihood of finding one that we haven't seen before is fairly low, unless it's something completely random from a, let's say, a password manager. But in this case, this password has only been exposed seven times. So this represents a bit of a tuning knob for the for the website operator. It might be difficult to come up with a password that's been exposed zero times, so maybe seven isn't that bad. But if it was seven thousand, you probably would wanna have the user pick a different password. This is definitely a your mileage may vary type of situation. But, anyway, that's how this works. And, then after the password is reset, the user is allowed in. So maybe in your environment, you don't wanna force the password reset. Maybe you just maybe just MFA is good enough for you, and you do manual review afterwards. We give you all the options, and it's essentially up to you how you do it. And we have customers that do this many, many different ways. And then this just explains how k anonymity works. Again, first five characters, API responds with all the matches, and then you decide whether that's good enough for you. And, at this point, I'll take questions if there are any. And if not, I'll wish you a farewell. Yeah. No questions have come in yet. I kinda had one, though, that popped up, Marc, while you were showing the k anonymity. Is that designed just to enhance the security and privacy of the customer so that we're not actually looking at their real passwords? Right. Exactly. So the idea is that we never want a customer to send us, and it's not sent in clear text, of course. It's done in over HTTPS, SHA two fifty six, etcetera. So the the data that is coming our way is encrypted as well, but there's really no good reason for even encrypted, for anybody to send us a clear text password. It's there's always the possibility of some kind of man in the middle. I think the frequency of that actually happening is hugely overblown, but, nevertheless, it's not impossible for that to happen. And so there's no good reason for us to send any clear text data out of your environment. Nice. Yeah. That makes sense. Have you had any customers that you work with, you know, concerned about that data privacy element for their customers? And, I guess, how would you approach that? So we definitely have customers that are on a spectrum of I'm gonna use the word paranoia, but I'm also cognizant of the phrase just because you're paranoid doesn't mean they're not out to get you. So, let's say that this our customers are on a spectrum of worry, if you like. And the very worried customers will be pleased to know that we can solve and hash this data as well as making it shot two fifty six. So So that'll make it yet another layer, and, and and we have customers that do that. So, for those that don't think the k anonymity even is up to their standards, we have ways to to enhance it even further. But, yes, the whole reason for this is to not send clear text data out of the customer environment. Excellent. Well, that's good to know. Alright. We did have a a question come in. So, Marc, with the password hash compare k anonymity, is that going against just have I been pwned, or is this against SpyCloud's entire proprietary dataset? Can you maybe explain a little bit more about the data? Yeah. That's that's a great that's that's a good question. So, of course, we're very aware of how they've been pwned, and and I I personally admire the heck out of out of Troy Hunt. I think he does an amazing job for basically being one guy. SlightCloud's big differentiator is that we've essentially industrialized what have I been pwned does, and we have over two hundred people that have been working on this for eight years, and we have a great many more breaches than than Troy has. Last estimate, I think he had around seven hundred and fifty, and we were over fifty thousand. So the the password check goes against our data. I feel like we have everything Troy has. And then the other thing that, that's worthy of mention is that, have I been pwned? And, again, nothing but respect for that or for for Troy and and what he's done. But we give you clear text passwords, and he doesn't have them. And part of the reason we have clear text passwords is because we aggressively crack them. So, there's a a a Slack channel internally that tells us about new breaches and new data that's posted. And just about every week, there's at least a hundred thousand new passwords that we've cracked. So So this is a big part of what we do, and we feel pretty strongly that if you don't know what the actual clear text password is, how are you gonna compare it to what's in your environment? Right? So, we think that that's pretty important. Hopefully, that answered your question. Yeah. I think so. And then kind of the malware data as well. Right? Yeah. Troy access to all those malware logs, so that's another And those passwords are almost always in clear text because they're stolen right out of the user's browser. So not only does each successive malware infection, give us more passwords, but it gives us more clear text passwords as well. And in fact, actually, it's quite useful for our password cracking efforts too because we can then take the new hashes and compare them to the hashes that we're trying to crack, and sometimes we uncover new ones. So that's like the lazy way of, of cracking passwords is to take an already cracked password, hash it, and see if it matches one that we already have. There you go. And you had mentioned all the other data that's siphoned from a info stealer malware infection. Like, it could be a passkey, API keys, the credit card so really anything on that machine. Of course, that's why the the malware, kind of flow that we showed here is super high risk compared to an old breach without any password reuse just from the sheer gravity of all the information that they've stolen from that stealer infection. Right? Yes. Yes. Absolutely. So, you know, the the reason that the person got infected in the first place is because the bad guys wanna steal stuff from them. And among the things that they steal are credentials of all different types, and you've outlined almost all of them a moment ago, so I won't bother repeating them. But you're all of those were definitely things that get stolen. And then I would also add stuff like crypto wallets, you know, all manner of other things. Actually, what we what we actually receive are called bot logs. This is this is a zip file. And and when you unpack the zip file, it contains a directory with passwords in it, a directory with cookies in it, a directory with pass keys, and other authentication stuff in it. And then somewhat amusingly, generally speaking, it'll also have a screenshot of the desktop when the person clicked the thing they shouldn't have clicked on. So you can see how people are getting infected. And, and what we see over and over are people getting infected on home computers, when somebody tries to run some sort of a cheap or a video game or something. We see a lot of corporate credentials get exposed this way too because, you know, maybe, you know, mom's been working on on the computer all day for work. And then in the evening, kid will come over and load it cheap for Call of Duty, and all of mom's employers credentials are now a matter of I won't say public record, but the bad guys have them, and we get them very soon thereafter. A very common scenario. So the data we're collecting could be relevant, you know, both for your enterprise, your employees, but your consumers as well, like what we demonstrated here. Right. Absolutely. Yeah. We you know, the there there's sort of, three main use cases that SpyCloud customers take advantage of our services for. Employee protection is definitely one. Obviously, the focus today is on consumers, and then we also have some very powerful investigative capabilities that I briefly outlined talking about some of the other data types, things like Social Security numbers, credit card numbers, and that kind of stuff. Excellent. Well, thanks for helping out with those questions, Marc. And for anyone on the call, if you have any additional questions or wanna double click on anything that Marc showed, our team will be reaching out to you or, yeah, please feel free to connect with your, SpyCloud point of contact that you've been working with recently. So, yeah, thanks again, Marc. Thanks to you all for joining live, and, we'll hope to hear from you soon. Thanks, boss.
- Video
Webinar: Consumer or Criminal? An inside look at SpyCloud’s Consumer Risk Protection
This demo/webinar shows how SpyCloud helps eCommerce organizations safeguard consumer digital identities and stop high-risk attacks tied to malware.
Hi, everyone. Welcome to our webinar on preserving account integrity and reducing risk with SpyCloud's consumer risk protection. In this webinar, we'll give you more info on who SpyCloud is, the challenges that teams are facing in solving for protecting both their customers and their brand and what business outcomes you can expect with SpyCloud. So SpyCloud's mission is to help you disrupt cybercrime by enabling you and your teams, whether it be security, fraud, or even application and product teams, to act on what cybercriminals know about your business and your consumers. And while we solve for a diverse set of use cases focused on leveraging our darknet telemetry to safeguard digital identities, Today, we'll be focusing on SpyCloud's consumer risk protection solution. And criminals are increasingly motivated to exploit customers' poor cyber hygiene and to discover new ways to profit from account takeovers. Both the traditional use of breach credentials to log into customer accounts, but also emerging sophisticated techniques like session hijacking. So businesses need direct insights into their customers' exposures that include authentication or access details, including credentials and cookies leaked in breaches or exfiltrated from malware infected devices. And with SpyCloud, your customers' exposures don't have to affect your business's productivity or your bottom line. So let's get into some of the challenges. So account security is paramount today more than ever and with customers relying on brands to safeguard their sensitive information. But it's human behavior that plays that significant role in driving account risk as individuals often unwittingly expose themselves to cyber threats through their actions. And this necessitates proactive measures to address vulnerabilities and protect against various forms of attacks. So So how do you balance then customer expectations versus how they behave online? So customers expect brands to keep their accounts safe, but their actions contribute to that risk. And individuals often use weak passwords or reuse them across multiple sites for convenience inadvertently increasing that vulnerability. The next one is credential stuffing attacks. Cybercriminals leverage compromised credentials and automated attacks, gaining unauthorized access to accounts across various platforms. So security teams must implement checks during account creation to identify previously exposed credentials and mitigate the risk of automated attacks. When it comes to the rise of sophisticated malware campaigns, malicious actors are enhancing malware campaigns, leading to an increase in phishing schemes and malicious downloads. And these attacks compromise devices, and they facilitate the theft of sensitive information, including authentication data. So you really have to shift that focus to prevention strategies, and security teams need to detect malware infected users and stolen cookies to prevent those emerging forms of account takeover, like session hijacking, and to safeguard their user accounts. So too much data, not enough context is another challenge. But in this ever evolving landscape of cybersecurity, the challenge lies not only in the sheer volume of data, but also in that contextual relevance. Without sufficient insight into the circulation of sensitive data on that dark net, including stolen authentication data like passwords and session cookies, organizations remain vulnerable to account breaches and fraudulent activities. So you need that visibility and that contextual understanding. Lack of visibility into credential identity and financial data on the dark net allows attackers to exploit vulnerabilities without triggering existing security measures. And traditional monitoring tools often provide outdated information from the surface layer of the dark web, rendering it ineffective in preventing timely responses to those threats. And that timeliness is key. So intelligence on data breaches become stale quickly, increasing the likelihood of attackers having already exploited it, and taking advantage of that compromised information. So the recency and the severity of the breaches determine the urgency for criminals to monetize that stolen data, necessitating real time monitoring and response capabilities. So when it comes to the mitigation strategies, you need a comprehensive overview of exposed data and its severity, and it's essential for mitigating the impact of prior exposures, but also in preventing future breaches. And real time alerts, high fidelity alerts enable proactive measures to prevent account takeover and fraud as those criminal tactics evolve. So when it comes to challenges of data overload, security teams are inundated with excessive data, and more isn't always better. And it hinders their ability to effectively analyze and respond to threats. So operationalizing risk insights requires advanced analytics and next gen threat intelligence that can be integrated seamlessly into existing workflows but without adding an extra burden on your resources. So when it comes to the emerging threats, there's often a full sense of security. Often relying solely on reacting to known threats isn't sufficient. And with emerging and constantly evolving threats, organizations must proactively anticipate and adapt to stay ahead of cyber criminals. And this is especially crucial in addressing the threat posed by malware, which is rendering traditional security measures ineffective. So you have to be continuously vigilant and adapt your techniques and resources. And that dynamic nature of cyber threats requires organizations to constantly monitor the widening gaps in their tech stacks and exposure vulnerabilities across their entire customer base. So strategies must be adaptable and stay ahead of adversaries and really anticipate potential attack vectors. And malware has a huge impact on security solutions. Infostealer malware deployments are undermining the effectiveness of conventional account security solutions. And previously reliable measures like MFA are circumvented by malware exfiltrated session cookies, facilitating advanced account takeover attacks like session hijacking. So those sophisticated ATO techniques, it happens when a stolen session cookie is used in an anti detect browser to execute a session hijack, an advanced account takeover technique. But this bypasses traditional security measures such such as passwords, MFA, even passkeys, highlighting the need for advanced threat mitigation strategies. But all of this, you also have to consider the customer experience and how do you minimize that friction in that customer's digital experience? And balancing stringent security measures with user user experience, it's a formidable task faced by most teams, and this kind of equilibrium is crucial for fostering brand loyalty or customer trust and optimizing your business's productivity. However, achieving this balance means navigating the fine line between fraud prevention and customer satisfaction as any disruption can lead to lost opportunities. So it's imperative for security teams to make informed decisions swiftly, but without introducing unnecessary friction into customer interactions or operational workflows. So you wanna focus on that balance between security and user experience. And striking that right balance between robust security measures and user friendly experiences is vital for brand loyalty, but also for business growth. And interruptions and friction in the digital journey can result in lost conversions, highlighting the importance of a seamless user experience. So you have to also make those decisions in real time without friction. Security teams really have to be capable of making rapid decisions in real time without impeding customer interactions or even operational processes. So you have to take action with confidence and ensure a smooth experience for customers while maintaining efficient risk evaluation and mitigation processes. But you also wanna make sure that there's differentiation for tailored experiences. Adopting tools that can differentiate between low and high risk users enables businesses to tailor each customer experience appropriately. And by maintaining low transaction review rates and minimizing the risk of chargebacks and fraud, organizations can drive business forward while also preserving customer loyalty and trust. So as criminals exploit stolen data from malicious activities from fraudulent transactions to identity theft, The security of customers' accounts and their personal information is a top concern for security teams. This surge in stolen personal and authentication data traded on the criminal underground, coupled with sophisticated criminal tactics, presents security practitioners with an ever growing challenge. How do you distinguish between a legitimate customer and a criminal using stolen information? So how we protect our customers and our business has to evolve just as rapidly as the tactics that bad actors are using to infiltrate and steal data. And it's often a collaborative effort across multiple teams from application security, information security, fraud, identity, governance, risk and compliance and security operations. And it's on those teams to build programs that reduce risk while also maximizing business productivity and maintaining low friction for customers. And with SpyCloud, our goal is to ensure you can keep your customers' data safe, maintain your brand reputation, but also prevent fraudulent activity. And how we do that is by giving enterprises actionable intel fast. With the largest repository of recaptured data of digital identity intelligence in the world, SpyCloud gives you actionable insights on breached credentials, malware exfiltrated authentication data, and exposed PII powered by cybercrime analytics. SpyCloud cybercrime analytics engine delivers high volume recaptured data from the deepest layers of the dark net, curating, analyzing, and enriching it with actionable insights to deliver really only the most relevant and high quality information to security teams. Then businesses can in turn increase operational efficiency by reducing noise and streamlining otherwise manual processes. And we have over two hundred and twenty supported data types tied to a user's digital identity, including sensitive data beyond just username and passwords, and this includes physical addresses, date date of birth, government IDs, IP addresses, credit card numbers, expiration dates, and more. And unlike many other solutions available, we deliver about ninety percent of our passwords in plain text. So how does SpyCloud help you with your goals? The first one is you want to get insights that drive those confident decisions. SpyCloud provides a comprehensive view of your customer's risk by analyzing billions of data points exposed in data breaches and malware infections and correlates them directly to your user, eliminating the guesswork so you can act on what criminals know to protect your consumers' digital identities. The data is fresh and actionable, having been recaptured within days of the breach or infection, which is a stark contrast to existing solutions that often lag behind by eight to twelve months post breach. Additionally, SpyCloud offers what no other solution on the market can, the ability to identify the highest risk customers whose devices are infected with malware and the unique authentication data like valid stolen cookies that are in criminals' hands. Identifying and invalidating compromised cookies is a critical component of modern ATO prevention. The next one is you wanna automate ATO prevention with a frictionless digital experience for your customers. And while SpyCloud maintains the world's largest database of recaptured data, we believe in efficiency, not overload. Our data is curated, stripping away the noise, adding valuable context, cracking passwords, and directly correlating to risk. So the result is you get actionable insights that you can integrate into your decision making workflows. Teams can leverage SpyCloud's API to implement automated actions like enhanced authentication or password changes or session logouts to invalidate stolen session cookies, denying risky transactions or accelerating low risk users through their digital journey. SpyCloud really promotes a friction only when necessary approach to ATO prevention without the constant need for manual intervention. The next one is that we talked about earlier is tailoring the customer journey based on known exposures. Exceptional customer experiences are key to retaining loyalty in a market saturated with options. And SpyCloud's underground risk analytics make it easier to tailor the customer journey, balancing a friction free experience for low risk users while high risk users are flagged for scrutiny or subjected to enhanced authentication or approvals. So SpyCloud's data gives your team essential insights facilitating process continuity, vigilant interaction monitoring, and proactive fraud decisions for secure and seamless customer interaction. You also wanna build trust by notifying customers of exposures and show them the added value that your solution delivers and protecting and safeguarding their digital identity. So as a security team, one of your primary responsibilities is to protect consumer accounts, but it's equally important for consumers to play their part by adopting better security hygiene. And that often requires empowering users through education when their data is exposed. So notifying customers of third party breaches, exposed or weak passwords, and malware infections is becoming more common, and it really helps businesses build and foster trust with their consumers when done the right way. ICloud also offers best practice guides along with sample messaging that your teams can use to notify your customers at potential risk and offer the best guidance on remediation of those exposures. So SpyCloud ensures that enterprises have the right data at the right time to protect their consumers and their business and leveraging darknet data to prevent account takeover, forecasted targeted attacks, and predict fraud tied to malware. If you want to learn more about SpyCloud, the solutions that we offer, or to see a demo, visit SpyCloud.com, and thanks for joining our short webinar today.
- Video
Webinar: Preserving Account Integrity and Reducing ATO Risk
Hello. Welcome. Thank you so much for taking the time to join us today. My name is Ashley, and I am the growth marketing manager here at SpyCloud. So buckle up. Today, we are taking a journey to the underground to explore what is fueling ransomware in twenty twenty four. We'll dive into the most important findings from the twenty twenty four SpyCloud Malware and Ransomware Defense Report and actionable takeaways for your organization to help defend against future ransomware attacks. Alright. So here's our quick agenda for the day. First, let the journey begin. We'll start by sharing the reports origin story and some context about why we do it and what we are hoping to learn this year. Then moving on, we'll explore the landscape and the ransomware resurgence, which includes top results from our research, such as the most common industries likely to be affected by ransomware, entry points, and the current cybercrime ecosystem. Then we'll go a little deeper into what continues to drive risk. And finally, we'll wrap up by going back into the light and setting everyone on the path to a hero's journey about what your organization can focus on for prevention. Then we should definitely have a couple of minutes for q and a. So without further ado, let me introduce our journey leaders for today. First up is Trevor Hilligoss, the vice president of SpyCloud Labs. Trevor served nine years in the US army and has an extensive background in federal law enforcement tracking threat actors for both the DOD and FBI, specializing in advanced malware investigations. He is a member of the joint ransomware task force and serves in an advisory capacity for multiple cybersecurity focused nonprofits. Next up, we have Taylor Coppock, our senior product marketing manager here, bringing over a decade's worth of experience building SaaS software to transform data into action across diverse sectors. He is currently working closely with SpyCloud customers to better address cybersecurity challenges for enterprise protection. And with that, I will hand it off to Taylor. Thank you. Hi, everybody. I'm Taylor. I'm glad you joined to hear a bit more about our discussion on the journey to ransomware. But before I dive in with Trevor, we wanted to briefly introduce BiCloud. So who are we? We as a company, we exist to disrupt cybercrime. So as you can imagine, it's very important to understand latest trends and impacts of one of the biggest threats out there, ransomware. Here at SpyCloud, we collect and enrich and publish all the stolen identity data that criminals have about you and your organization so you can act on what they know about your employees. We help protect your enterprise from cyberattacks and provide a variety of use cases, but today's focus is all about understanding and preventing ransomware. So let's dive right in. Let's let's start the journey into understanding ransomware. And to understand the story today, I wanna share a bit more insight into why we do this survey itself. This is now our fourth consecutive year of creating this malware and ransomware defense report, and we surveyed more people than ever this year. To really disrupt cybercrime and know the latest trends in ransomware, we wanna make sure we're balancing our own research with what the actual organizations across the world are facing. So this year, we surveyed over five hundred cybersecurity professionals across the US and UK. These respondents range everywhere from executives and CISOs and IT security executives, all the way down to analysts and engineers and operators, and also the identity team for the first time in our report. As you can see, majority of these respondents work at very large organizations, so we wanna make sure we're actually listening and understanding what they're telling us. So what we wanna know this year in particular about ransomware itself is, again, some of the concerns these organizations face both about malware and ransomware as well as how they're currently trying to defend against these cyberattacks. We also are leaning into something new this year. We wanna know what were most common entry points from organizations who were hit with the ransom to know how criminals are trying to steal this initial access. Then, of course, you wanna know the actual impact, the monetary, the time impact of these ransom attacks on organizations while understanding what they're trying to do to prevent attacks and where their future security priorities lie. So on that note, I'm gonna pass to Trevor to cover a bit more about the whole cybercrime landscape at large. Thank you, Taylor and Ashley, for starting us off. We start our journey with two major trends that have converged over the past eighteen months and which are playing a large role in shaping the landscape we find ourselves in today. First off, ransomware, unfortunately, saw resurgence as a frequent and damaging attack method increasing in prevalence in twenty twenty four. Ransomware remains the leading cybersecurity threat across every industry we examined. The number of organizations who said that they were affected by ransomware at least once rose from eighty one percent to ninety two percent, and those affected more than once grew even more significantly from sixty one percent last year to seventy five percent this year. The average cost is almost five million dollars. And, unfortunately, our data shows that year over year significantly more organizations paid a ransom, sixty two percent this year versus forty eight percent in last year's report. Even more troubling, only about a third of those organizations fully recovered their data, which is a stark reminder that giving into cybercriminals' demands is a gamble, and the odds are not always in your favor. In some cases, cumulative costs can extend to general disruption, loss of business and opportunities, productivity decreases, reputational damages, and more. For instance, we found in an average successful ransomware attack, forty nine percent of an organization's computers are impacted in some way, which can obviously impact business functions. Third party exposure is fueling exponential risk across the board. We'll dig a little deeper into these risks in a bit. The presence of an Infostealer infection leads to future ransomware attacks. We found that nearly one third of companies that experienced a ransomware event last year had at least one Infostealer infection in the sixteen weeks prior to the attack being made public. We'll definitely talk about that in a few slides. The second trend we saw is that more commonly, cybercriminals shifted to next generation tactics, using data exfiltrated by infostealers to gain initial access for follow on attacks like ransomware, which we'll also cover in short order. Now the cybercrime ecosystem is vast, and we don't have time in this webinar to explore all of its parts. Nonetheless, let's quickly discuss some of the more significant components. Mower as a Service describes the commodification of malware, Much like legitimate software as a service enables professionals to access tools and services that they couldn't code themselves, malware as a service enables less technical criminals to gain access to sophisticated malware and the capabilities necessary to launch it in an alarming scale. Install brokers work hand in hand with criminals, enabling their malware to spread far and wide. These brokers have a vast network of compromised websites and ads that can deliver malicious executables disguised as messaging applications, game sheets, free software, and more. Next up, the initial access brokers often take the proceeds of successful infostealer infections and resell that access, sometimes with guarantees, to other criminals, especially ransomware operators. Now These brokers aren't limited to using data exfiltrated by infostealers. However, data stolen by infostealers remains a critical component to the access broker. Lastly, ransomware as a service enables large affiliate networks of criminals who often operate independently while still being able to benefit from established malware, command and control networks, and leak blogs. Taken as the whole, the cybercrime ecosystem poses a significant threat to our connected world. Let's talk infostealers. Our research highlights how infostealers have become a critical part of the ransomware supply chain. To further investigate this, we conducted an analysis of publicly announced ransomware events over the past year and correlated those events with infostealer infections that preceded them. What we found was alarming. In nearly one third of the events we analyzed, we found at least one infostealer infection of an enterprise account, often including SSO or some other centralized authentication service, prior to the ransomware event. When we look at which malware families had the strongest correlation with a subsequent ransomware event, a few stood out. Lumacy two topped the list and is one of the most sophisticated info stealers on the market today. It also benefits from constant development and wide market adoption. Redline remains a juggernaut. However, it is notably less feature rich than LumaC two. Nonetheless, as one of the older stealers on the list, it enjoys wide use in criminal communities and benefits from name recognition. Steel c is a relatively recent addition, but one that has been quick to adopt cutting edge methods for theft and detection evasion. I'll also give an honorable mention here to Atomic, which is noteworthy for being the first macOS targeted infosteeler to see widespread success in stealing data from Apple devices. And all of these infosteeler families, regardless of their individual characteristics, are important because they massively lower the barrier to entry for cybercriminals. This off the shelf model for a variety of malware, and especially infostealers, enables even low skilled or no skilled cybercriminals to steal fresh and accurate identity data in bulk, including login credentials, session cookies, files saved on a device, and that device's details. Basically, everything needed to impersonate an identity. So let's dive in a little deeper to these findings. What's driving risk? Alright. Deeper we go into some of the the risk we see. So this year, we we asked those organizations who had been affected by ransom. Again, not just the impact of time and money, but we wanna know what happened before the ransom attacks. So we actually had information with organizations of what were the entry points used by attackers to gain this initial access. So the top three that stood out among all of the data points, really number one, the continued reliance on phishing and social engineering tactics. Followed up by number two and three, all about third party access and stolen session cookies that enable session hijacking. So in terms of general perception, no real surprise that phishing, social engineering still top of the list since it still comes down to people at the end. However, like, the focus only on remediating and handling that entry point is is not the only way forward since to fully combat the scope of ransomware attacks, we need to know a bit more about the other entry points that have really shown up in the data. And the second one being all about the risk of unauthorized third party access. We've seen a lot of SpyCloud, so I'm I'm not shocked to see this mark so highly from our survey respondents. But as criminals look for all the ways to gain the upper hand in in the malware landscape and launching ransom attacks, another opportunity is all about these malware infected third party devices and unmanaged devices. Of course, the respondents, the identity teams are really the most concerned of the risk this brings. From the survey, almost one hundred percent of those surveyed really worry about the risks from third party path third party third party accounts that come from these malware compromised devices. Primarily, these devices that are really outside of corporate control just make it so much harder to detect what's happening, much less remediate because they're outside of IT control and visibility with limited security practices for these devices. Now, when you have access to these third party applications along with the ones you manage yourself on these unmanaged and third party devices, there's so much information that criminal can use to gain access, advance privilege, then eventually deploy rank and attack. However, we still had teams really rank this capability and priority to really detect when there are infected third party devices quite low compared to other tactics. Here at SpyCloud alone, and Trevor has more information on this, of course. Last year, we were captured of four point seven million popular third party application credentials from malware infections. So whether they belong to an employer or third party contractor, criminals using this access to really follow-up with targeted attack. We also thought that on average, a single malware infection exposed access anywhere between ten and twenty five business critical DApp applications. Scary stuff. So next generation account takeover, which uses session hijacking instead of relying on traditional credentials, allows threat actors to sidestep all types of authentication. It can bypass the process entirely. This includes MFA and passkeys or a passwordless login. By hijacking user sessions that have already been authenticated, cybercriminals, including ransomware operators, become a clone of an illegitimate employee without setting off typical intrusion alarm bells. This greatly increases their rate of success in gaining access to an organization's network and systems to launch an attack. In our most important countermeasures to combat ransomware, data backup and endpoint or device protection have maintained their position on the list of the most important countermeasures from last year, while MFA moved up six spots to number two on our list. This suggests that MFA adoption is now more mainstream, but it's also a cautionary tale. Cybercriminals are adapting to current trends, and as we've seen in this past year, they're targeting MFA. With Infostealer siphon session cookies, they can simply hijack the session and bypass even the most robust MFA setup. Some critical session cookies can remain valid for weeks, months, even longer. A big target are session cookies for email providers, for example. Since many of these organizations don't yet monitor for cookies stolen by infostealer malware, let alone invalidate those sessions, a single infection could leave an organization exposed for a relatively long period of time. When leveraged by ransomware perpetrators, this access can come with immense consequences. Unfortunately, we expect to see session hijacking continue to gather momentum. And the more organizations are aware and prepared, the better off they'll be. Now based on recaptured data and malware logs tied to the industries we surveyed, as well as previously self reported ransomware attacks, Spy Cal out has constructed a model using machine learning to identify the industries with the greatest risk of future ransomware events. Now probably saw a poll pop up on your screen. Go ahead and answer that before we continue. We're very interested to hear your opinions on which industry or industries is the most likely to be targeted by a future ransomware attack. What are we – Actually, I can't see the respondents, so just let me know when, we have quorum. Let's see. What are they saying? What are they choosing? Yeah. It's looking like so far on health care is the, front runner with seventy three percent of the votes. And, actually, other is next, with eighteen percent followed by insurance with only nine percent. So with that, we will end the call and then, go and see what the actual results are. Yeah. Interesting. Well, I would like to hear if if you're if you're willing. If you answered other, go ahead and drop maybe a question or or in the chat. I'm not sure how Zoom functions there, but I'd I'd be interested to hear what your what your, specific industry for other is. Based on our data, we, we did find health care was, up there, certainly, but not number one. And even more surprisingly, seventeen percent of health care respondents reported not being affected at all by ransomware last year. However, based on our prediction modeling, as I mentioned, health care is one of the industries with the greatest risk of future ransomware events in twenty twenty four leading into twenty twenty five. In fact, it's about two times more likely to experience a ransomware attack. Now the sector we found to be most at risk, and you guys highlighted this in the poll, is insurance. Insurance is more than six times as likely to experience a ransomware attack in the remainder of the year. Only three sectors Manufacturing, Retail, and Technology rated improved man ransomware prevention capabilities among their two main priorities in the next twelve to eighteen months. Okay. So now the positive part. As we now continue the journey into the light, we're gonna talk a bit more about some of the optimism we saw from our own research and from the respondents and how we can help really prevent these ransomware attacks. The first tip to share, honestly, is reflecting internally. We saw quite a perception mismatch among the survey respondents with their overall confidence of their organization's ability to really prevent a a full blown ransomware attack. So majority of the security executives felt very, very confident, over ninety percent of their ability to prevent this full blown attack. And these executives were also much more confident in their whole company's ability to both respond to malware infections and ransomware attacks. But we saw the data was quite different across the other teams. Identity teams are also a bit more confident. They've all been a bit more aware of some of the risk from third party exposure, malware infection in general. But we saw some disconnect with the actual operators, incident responders, and analysts being a little less confident. So, again, we just wanna really promote that you really align internally and self reflect on your own capabilities to detect malware infections, respond to that, to prevent ransomware attacks, especially as we look into planning for priorities and tactics and projects for next year. And on the disconnect piece, a bit more about the malware capabilities we've seen. Yeah. Thanks, Taylor. So security researchers found that as many of ninety percent of security compromises originate from unmanaged or undermanaged devices. I don't think that's any surprise. Outside of IT control and visibility and with limited security, these devices hold an undeniable appeal for threat actors. Unfortunately, detecting third party or unmanaged devices infected by malware is the capability organizations lack most today. Without visibility into these exposures, it's difficult for an organization to fully understand its risk and properly defend itself. Now even if you don't have a bring your own device policy, which I hope you don't, be aware that modern browser sync capabilities are often the culprit in allowing enterprise logins to be copied out of your monitored environment and onto a personal device. This device can then be infected by malware, and those enterprise credentials can be siphoned out. Unauthorized third party access is high on Teams' radar, rated as the second most risky entry point for ransomware in this year's survey. By improving visibility into malware exfiltrated data, including unmanaged and third party devices outside of the traditional corporate oversight, you'll have more complete coverage and faster discovery of exposed applications and therefore drastically reduce your time to remediation. And you might even reduce the likelihood of being a victim of ransomware in the first place. Overwhelmingly, our respondents agree that having better visibility of malware exfiltrated data, such as exposed credentials and session cookies or tokens, and automating remediation workflows would significantly improve their organization's resistance to ransomware attacks and their overall security posture. Back to you, Taylor. Hey. Another tip also speaks to the data but we also talking about device device device all morning. And speaking of this data and this recapture stolen data, we believe there's a paradigm shift needed to shift away just from thinking about device focus but more towards this identity centric approach. It's really important to have visibility into all the stolen data out there to connect what makes up this holistic digital identity for your workforce and your supply chain. We've seen it quite often that criminals are now moving beyond traditional use of stolen username and password pairs alone for their attacks. Criminals now have this expanded dataset to use to really increase the scope and veracity of their attack patterns based upon all the stolen identity records that come from a variety of sources of breaches and malware infections that criminals are now linking together to really help create synthetic identities and personate accounts. We have the information to really target this access that Trevor spoke to. Using everything from, of course, credentials and usernames, but PII, social handles, backup emails, street addresses, Social Security numbers. There's so much information that criminals are now targeting because as you saw a few months ago, the massive NPD breach. This is all over our radar. We know the extent of one of the largest breaches in history where if I thought alone ingested over two point seven billion identity records, it says that is the it's something with this breach. So I know my exposure. I know what information is now in the criminal's hands of my own past and blending my digital identity. But it's up to now that the security teams really move towards this identity focused approach to have this timely definitive evidence of exposed identity data to really go beyond the the device to know that when there is an infection or exposure, you know all the pieces and all the assets that criminals are using to gain access to really prevent them in their attacks. And our final tip, as you can imagine, comes back to malware. We believe strongly that ransomware itself is a malware problem at its core. And there are some good trends, some good news within all the data and our own research. More teams, as Trevor showed, strongly agree they need its visibility into malware exfiltrated data. They have the right steps to get this data, and they're slowly moving towards adopting full remediation steps. But we still saw a lot of respondents say that the primary action is just a brute force reset and wipe situation. Well, that doesn't work when you're trying to address the larger identity access that criminals have, much less the the risk of unauthorized third party access and devices you don't manage. Trevor showed the risk of session hijacking. Now we saw that identity teams really are more in tune with these identity attacks and more on the frontline of detecting and preventing this. But we want to make sure you have this malware post infection remediation playbook ready. That comes down to two things. It comes down to really understanding and identifying all the exposed business applications that your organization runs, even those that you don't manage, but all the fast third party apps because that exposed access unlocks a lot for the criminals. But also comes down to these active stolen session cookies and compromised web sessions. I've missed information to know, again, what access is out there, but making a plan to know how and when to remediate and the impact of resetting those sessions, what it has on your employees, your customers, and organization. So So it comes down to detecting these compromised credentials and these compromised session cookies. Majority of the teams we saw are reviewing the logs of what's been exposed and terminated open sessions, but it's both having the data and the remediation path in play. Just resetting and wiping and quarantining is a step. We wanna want to broaden the whole malware post infection and know how you can actually detect stolen access and make the proper plan for your organization. So, in closing, we see some great trends in the next twelve to eighteen months to improve malware detection, remediation capabilities, all about visibility and this compromised access for criminals. Now before we shift to q and a, I do want to highlight in the chat, we've shared a a fun infographic that kind of highlights the latest trends and insights from this year's report. But I also encourage you to download the full by cloud malware and ransomware defense report. There's so much information that myself and Trevor could not get to today. I want you to read this really help with your own priorities for next year and just feel confident about your ability to prevent these attacks. So let's more of a chat. Let's see what questions you have, and ready to help us, really close the journey out together. Let me move on, and let's wait a second to see what is top of mind for this audience. Awesome. Thank you. That was so great. I know it's a lot of information to digest. But feel free to drop any additional q and a in the question box there. To start, Trevor, I'm gonna throw this one your way. Can you give some general best practices for how to avoid session hijacking? Sure. So the biggest point that I will make there is most sessions, most cookies are gonna have, time to live. Right? They're gonna have an expiration date on them. Now, sometimes that's not user configurable, but oftentimes it is, especially in the case of more popular SSO providers. You can actually configure, how long that cookie will live before it, is expired. I would encourage everyone, and I understand this is kind of a, trade off between user experience and security as are a lot of things in life. I would encourage everyone, if you have the ability, make that time to live as short as possible, especially for things like SSO. Email is also a huge target for criminals that are deploying, Infostealers. If you think about if somebody gets into your email inbox, you know, think about the ability to reset passwords or even just enumerate all the services that you use, in kind of a similar way that that SSO can be used in that way. So, definitely decrease those those TTLs as much as you possibly can for all of the the cookies that you have the ability to do so. Awesome. Thank you. Okay. Next question. Trevor, I'm gonna throw this one your way as well. We use independent contractors all the time. How can we get ahead of making sure they don't pose a risk to our business? Yeah. That's a good question. So this this is hard. Right? We we have a pretty good way we we do pretty well at securing, you know, the devices that we manage, the full time employees that report directly to our companies. We can install endpoint, monitoring. We can, you know, monitor their, you know, their their device activity. Gets a lot harder when you have people that don't necessarily work for you as a company or maybe they're not using, you know, devices that you manage. So I would say the the big thing right there is really of of, awareness. Right? Be be be cognizant of the employee, of the contractors that you're using. Obviously, limit their scope as much as you possibly can, but have some way of monitoring if and when they become exposed. And realize that that might not actually include any of your domain information, you know, on its face. We might not see a, you know, spycloud dot com email address if this is a contractor, but that doesn't mean that that info stealer or whatever malware hit that endpoint, didn't pull some proprietary information that it might have been downloaded and saved. So definitely monitor, definitely limit their scope as much as you possibly can. Those are some pretty good, good policies there. Great. Thank you. So to add on to that, a follow-up question was, do organizations overlook dark web monitoring? It's kinda hard to answer conclusively. Obviously, we're a bit biased in that, that question too. I mean, I think it's easy to overlook. You know, when we say dark web, it's really a kind of a misnomer. Right? We're talking about, obviously, yes, the dark web, Tor, you know, ITP, whatever other, networks exist. But we're also talking about clear web websites. Right? Breach Data gets shared on Twitter. We're talking about malware app, I'm sorry, messaging applications. Right? Telegram or or Discord, for example. So, you know, it's a huge it's a huge area, to cover. And so being able to do that on your own is is very difficult. Of course, that's why companies like SpyCloud exist, and we'd be more than happy to to help you with that. But, I do think it's it's it's heartening to me to see that more people tend to be talking about this over the past couple years than than historically. So there's more focus on this, and and hopefully that will, lead to more awareness, that that there are risks out there and and how to remediate those risks. Awesome. Thank you. Taylor, I'm gonna throw one your way. Of the key takeaways, if you had to pick one place to start slash implement, which would you choose? Okay. Well, ever since the NPD breach, identity has been top of mind for me, both as a human, just knowing what's been exposed. I think it really comes down to this shift of thinking of identity access and all the information that criminals could use to really take over access of of my life and my my corporate access. So I think it really comes down to the data and understanding the connections criminals could make to broaden the scope into a digital identity. So, again, if there was an infection on any kind of device or any kind of contractor or an employee, just knowing what what's really stolen, what's available that's beyond just, again, my username, my password, to really think more about identity at large and understand how that can be used to gain unauthorized access to then think, well, how would I detect this? How would I know all the assets that make up an identity to actually then, again, monitor and detect and get ahead of that? So, really, all about identity, that's been just top of mind for me. Awesome. Thank you. Trevor, if any stolen company data is detected on the dark web, could it be removed from there? Short answer, no. The Internet is forever, for better or worse. Now that's not to say that, you know, things things fall off all the time. Things are posted on very niche corners of the Internet and and, you know, maybe those get taken down or they're never archived. But, really, in my experience, once data is exposed, whether it's exposed in a Telegram channel or Russian cyber criminal forum or, you know, Twitter, It's, you know, it spreads from there. Right? The, the the the the the Internet is highly transitive and, especially when we're talking about threat actor communities. You know, there's this whole I could I could talk for hours about this. There's this this whole, you know, ecosystem that that thrives off of, you know, criminals basically sharing information with each other. Sometimes it's for monetary gain, oftentimes it's for clout. But, you know, one one one data breach gets posted, we see it, you know, on, XSS, for example, Russian language, cyber criminal forum. And then we can we can track that at that one breach over the course of the next several months. I will see it pop up on a Telegram channel one week and a Discord server the next week, and maybe it shows it up on another forum the week after that. It it it kinda gets a mind of its own. So that that's why we're really big proponents of the, awareness part of this because, you know, obviously, there are certain things. If your Social Security number gets exposed, that's hard to change. But, you know, if it's password, if it's a cookie, if it's an API key, you know, typically, we we have a a reset path. Right? There's some way, either your, you know, IT administrator or maybe your you yourself can go and change that password, invalidate that cookie, reissue that token. And obviously, it doesn't change the fact that that information was out there, still is. But the next time it gets shared, the next criminal that tries to use it, they're gonna be a lot less successful. So, when we talk about remediation, really, we're talking about awareness, identifying the exposure, and then doing whatever you can to make that exposure less valuable to the criminals. Awesome. Thank you. Okay. One more question, Trevor. If we experience a security incident slash ransomware attempt, can SpyCloud be used to investigate the root cause? Hopefully. You know, I can't can't speak to every single incident ever. SpyCloud my my organization, SpyCloud Labs, we're the we're the research part of SpyCloud, and we collect a massive amount of data every single day, malware, breach records, phish data, etcetera. So, you know, oftentimes, we have had great success working with our clients to, you know, identify where that initial exposure came from. If it's malware, you know, we can give you that information and and let you know what else was stolen at the same time, which can be super valuable, of course. In the case of ransomware, you know, root cause analysis tends to, you know, look for patient zero, what was the entry point. Like we covered kind of in the remainder of this webinar, a lot of times that's info stealers or some other malware, by way of maybe an access broker. So those are things that we can call out, definitely. And, I mean, bottom line, look, we're we're in this fight together. I think everybody has to kinda be part of the same team for us to succeed. So, we'll help however we can, even if that's just kind of looking at all the information and recommending some next steps. Awesome. Thank you. Okay. So, yes, we will be, sharing the slides or the the video, I'm sorry, of this. We will get that out to you as soon as it is available. And then, Taylor, if you could move on to the next slide. We have one more action item for you if you wanna speak to that, Trevor. Sure. So, this is a a service we launched a while ago. Highly recommend everybody take a look at it. So if you're not aware, you know, Spikelet enhances critical aspects of your security defenses to safeguard your sensitive data against next generation cyberattacks. That's what we've been talking about this whole time. If you wanna get a glimpse into the power of cybercrime analytics, you can start by checking your enterprise exposure. If you use this tool, we'll reveal real time insights on exposed employee credentials that are in the hands of criminals and share the results, including any previously unknown exposures that SpyCloud illuminates. So in that question that we had about, can SpyCloud help me with RCA, definitely encourage you check out, check your exposure and, see what it see what shows up there. That's a good good place to start. So once you do this, you'll receive a custom exposure report that'll include an overall security risk score for your business based on SpyCloud's data. That also takes into account malware infections and plain text passwords. We'll give you account of malware infected records associated with employee email addresses, which may indicate active infections and exposed active session cookies. We'll also share share insights into third party breach records, exposed executive and VIP credentials, estimated password reuse, and PII exposure for your employees. And we'll share specific breach and malware sources with details on when SpyCloud published the data to customers and the compromised data types. So if you have questions, you can absolutely find us during the networking session, or you can reach out to us by email. Okay. We have one quick question. I'm hoping you you can answer, Trevor. Is this GDPR compliant? Yes. It is. Okay. Awesome. Okay. Well, thank you so much to everyone joining us today. Please go check your exposure. And then if you have any other questions, please feel free to reach out. And I hope you all have a wonderful rest of your day. Thank you. Thank you. Keep coming, folks. Thank you. Have a great day.
- Video
Webinar: Journey to the Underground: Insights Into What’s Fueling Ransomware in 2024
This webinar breaks down the most important findings from The SpyCloud 2024 Malware and Ransomware Defense Report and what your organization can do to get ahead of emerging cyber threats.
- Video
Ransomware Reality Check: The New Landscape
This webinar breaks down the most important findings from SpyCloud’s 2023 Ransomware Defense Report, and what your organization can do to get ahead of emerging cyber threats.
- Video
Don’t Play Footsie with Cybercriminals
On-Demand Webinar: Unveil the top darknet exposure trends for London’s FTSE 100 companies, including insights on password reuse, stolen session cookies and cloud app exposures
Your organization's security is only as good as the security of your supply chain. A single exposure can be devastating. The entry points are ever expanding, and they can be your people, they can be your contractors, they can be your devices. Our new product gives you visibility into the one attack surface that others cannot see continuously, and that is the attacks that are facing their supply chain. Here at SpyCloud, we are constantly monitoring the darknet, looking for those key elements that have been stolen from organizations that are used to attack the identities of any other organization. SpyCloud is constantly recapturing identity data that's been exposed via malware or phishing attempts or resold in combolist. And this data is making it all the time in to our supply chain product as signals. What differentiates the supply chain threat protection product is that it focuses on identity threats. It gathers its data continuously from the darknet so that we have a deep understanding of the real threat. So you understand when they're making progress, when they're starting to fall short, so that you can have conversations quarter over quarter, year over year, at procurement time. It's a tool that you can use throughout the life cycle of your partnership with this third party. The Identity Threat Index gives a better picture because it's focused on data that no one else is focused on. Bringing a third-party vendor into your supply chain is a major decision. And it's one that involves mutual trust. And not having visibility into quite literally how they are exposed at any given point in time, it harms your ability to know if you can trust that third party. And so with our tool, you are now suddenly capable of having that level of visibility to really understand, can you trust this vendor to make sure that they're protecting themselves and therefore you?
- Video
SpyCloud Supply Chain Threat Protection
I think that the most dangerous threat to organizations today is the ever increasing complexity and sophistication that's being used by the people who are trying to do bad things on the Internet. All of us have digital baggage from our past that we're bringing into our current workplace or in doing business with digital businesses online. It doesn't matter who you are, it doesn't matter where you work, your identity has been compromised. We're a cyber security company based in Austin, Texas, but with a global presence. We help organizations combat cyber threats, like account takeover, ransomware, session hijacking, based off of the data that's being stolen and traded on the criminal underground. I think what's really quite unique about SpyCloud is the fact that we're not only a cybersecurity company, but a big data company kinda merged into one. We are very customer centric and driven, and that really drives home to our engineers. But, yeah, you're not just a a bricklayer. You are actually a missionary coming here to solve cybercrime. It is not only the quality of the information that we provide, but it is the true level, detail and magnitude of the analytics that are on top of it. As soon as something happens in the an asset is available for a particular identity, we go out there and try to protect that identity or protect that customer. I gave a demo today of, you know, our investigations platform and then obviously showed this person how it speeds up the investigation by running it through AI insights. And this person's response was amazing. They actually said that this is the best application of AI that they've seen ever of any product that claimed to have AI as a component of their product. Identity is the most important component of any security infrastructure. You need to know who you're working with and what you're trying to do with them. Our holistic identity gives us the ability to see both who you are in the corporate environment, but all the other yous that you've created across all the different systems for their identity. We've gone to great lengths to build an engineering team so that we can curate it and enrich it and make it actionable and human readable. And we wanna help businesses stay steps ahead of every possible threat that they could face. Everybody that works here not only deeply cares about the mission, but they deeply care about doing a good job and doing a good job together. The truth is it's people's belief in the mission. And because of that, it leads into great collaboration, great support, everybody willing to jump in and help, and always with the customer at the forefront. To me, it's not like coming into work. It's coming into work with your best friends and all your family members and trying to make a difference. An environment that prioritizes not only the work that we have to do and the impact it has, but also our own personal lives and the balance that's needed to have a full life, appropriate prioritization, and the teamwork support that we provide one another, both inside and outside of the workplace. So we are looking for people who are curious and, you know, have high agency and and, and, have the grit to not, you know, it's okay to fail, but get up and let's do it. We've got an amazing group of people that are super talented, very collaborative, the best people you've ever worked with. Honestly, Everybody is here growing in the same direction, and I think our future is unlimited. What am I most proud of at SpyCloud? Proud of the fact that we've been in business for nine years. Our growth has been stellar every year along the way. The team of people that we pull together is amazing. We've overcome a thousand different obstacles along the way, and now we're being used by companies all over the world protecting over four billion accounts on a daily basis. It's something to be proud of.
- Video
About SpyCloud Video
From recovering stolen identity data on the criminal underground to leveraging AI‑driven investigations, our mission is clear: protect people, protect businesses, and stop cybercrime before it strikes. Hear our story.
Hi, I'm Trevor Hilligoss I am the Senior Vice President of SpyCloud Labs. I am Damon Fleury. I am the Chief Product Officer at SpyCloud. So do we just want to do a segment here where we just kind of throw around, this confidence gap problem? Where 86% of leaders express confidence in their ability, but 85% also experience at least some level of ransomware incident. Whether they experience it themselves or they experienced that through a partner, or some, some something about ransomware impacted them. 85% of them reported that. So like, what gives here? How is this even possible? TREVOR: Yeah. It's it's interesting. I, I mean, I think there's like, I don't know, maybe even a philosophical question to this. I mean, we, we definitely see the same threats, that we've seen year over year. And I think at the end of the day, really it doesn't, I would say that it doesn't matter quite as much what the actual means of access, or the way that access was obtained. It's the fact that access was obtained. Right. So one of the other things that we noted pretty significantly is that phishing is still a huge problem. In fact, it's even a bigger problem today than it was last year, just based on the numbers. And we're seeing the same kind of thing with, with phishing that we saw with malware, where more and more threat actors are turning to commodity level kits that are created and polished and, you know, available for sale. And, I think what that means, going back to the the kind of the point of this of access is that the barrier to entry is much lower, and it doesn't really require the level of sophistication that it once did in order to get access to, you know, networks or systems. And then, you know, you add in the financial motivations of ransomware. I don't I don't think it should be much of a surprise that we see a lot of, you know, ransomware arising from phishing. And, you know, squaring the circle of that confidence gap, is, is, I think, challenging? I probably don't have the credentials to, to, you know, speak to the psychology potentially at play there. But, you know, it is it is concerning that we we seem to overestimate our preparedness. DAMON: I think it's interesting about this report overall is that, you know, there's there's a lot of conflicting data within this report in itself. And that, you know, there's so many data points that show that, we as an industry think we've got a good handle on security. And then and even in the survey results that we point out that we are still constantly falling prey to what are the most sophisticated of attacks. And then how do you, you know, how do you reconcile this? And then if you look at the SpyCloud data, what we bring into the report, you find at the same time that it's true we are falling prey to all of these attacks, right? There is rampant malware, rampant phishing. And so I think one of the data points in the attack and sorry, the report, is that 45% of CIOs and CISOs report feeling very confident that their ransomware defense capabilities, but only 28% of security directors and their teams and their team leads say the same thing. So, you know, then, of course, our data shows that, you know, the vast majority of, these organizations are seeing constant malware, constant phishing, constant, identity threats as well. I mean, I look at this and think, do we have leaders that are just kind of, you know, inflating the capabilities of their organizations? Or maybe we have leaders that are that are trying to show that that they have confidence that even though they cannot stop the attack, right, that they're they have the right team in place, they have the right tools in place that they'll be able to to weather the attack. Like, I know most organizations now. Now what, 20 years into ransomware ish, they can handle a ransomware attack. Like they get hit by ransomware. They are not likely to shut down the business anymore. Most, you know, I say some bigger than small enterprise. You know, so they have that they have the backups in place, they have the team in place. They'll they'll figure out a way to get through it. It will be costly, but they will live. So maybe that's what they're trying to say. That's what they're trying to convey that we're not we're not at zero here with our capabilities. I don't know what you think? TREVOR: Yeah, I think, proximity probably plays a role here as well. I mean, you know, I once upon a time, I was probably closer to that security director role in terms of, you know, being a little bit more pessimistic about, the reality and the threats that that we face. I think there's another way to say that is as being perhaps a little bit more realistic. Because I do think, you know, you said you said something in your, in your preamble there, which was that, you know, the sophistication of attacks. And I what I have kind of come to you over the past couple of years, and I think that this continues to be proven right, I would say, is that, you know, sophistication is not really the way, the right way to think about this. Because, you know, time and time again, we see sophistication of adversaries kind of being immaterial to their rate of success. I mean, as we're recording this, you know, obviously the whole Salesloft slash drift thing just just happened and hit the news a couple of weeks ago. And by all, you know, accounts right now, that seems to basically be, due to some, you know, tokens that were left in a, in a GitHub repository. And obviously, I don't want to speculate on how that access that GitHub repository was, was made. But, you know, at the end of the day, we're not talking about some kind of highly sophisticated zero day or even an end day. We're talking about secrets that were left in a place that they shouldn't have been left, right? So I think that is also very transitive to the conversations about, you know, like we were just talking about phishing kits becoming a commodity, malware having been a commodity for a very long time now. And that just becoming more and more of a, you know, factor of cybersecurity is that criminals can just buy access, instead of having to kind of go through this, a longer, more thought out and more sophisticated, you know, attack plans or developing their own tooling. So, I don't know, I, I do think there's some proximity at play to why we do see this imbalance between, you know, CISOs thinking that they're much more prepared than people that are a little bit more close to, say, instant response or, more of a, you know, workaday, defensive, practices. But I also think that the, the environment has changed such that the sophistication of threat actors is a lot less of a, you know, factor, influencing success than it used to be. DAMON: And so I think that plays well into another topic, that, the, the report wants to want to talk to through a little bit and that's specifically like AI, you know, how is AI impacting what you just described, that sophistication of that actor. The report talks to 90% of organizations, sorry, 92% of organizations agree that AI-powered cybercrime has intensified risk, and that they're seeing cybercriminals use it, at the same time. we’re a little slower as an industry to adopt AI and to use it to defend ourselves with only 47% of organizations saying that they leverage AI tools in some way. And I've certainly seen that and all the conversations that we have with customers that, you know, while actors do not care at all about the compliance issues of AI and about what data is used for training and how they are more than happy to use Curser to write their malware, or more than happy to use ChatGPT to help them do translation. And there's no questions at all about what they can and can't do. So they're fast, right? They're happy to take it. And that's going to make everything we think slightly more effective. And the businesses are, you know, we're looking at our ability to respond to this, and we want to think about it before we are ready to adopt it for good reason. Right? There's an impact to the business. What do you think there? I mean, it's an interesting dichotomy. It's an interesting problem. TREVOR: Yeah. No, it reminded me. So every time I hear this it reminds me of a Defcon talk that I attended years and probably ten years ago now, it was a and I, I wish I could credit the actual speakers, but that that nugget of memory has long since left my brain. But I remember they were a Singaporean, research group that is meaningful to anyone listening. But, they did they did an analysis on, phishing emails. So if you craft a really, you know, well done phishing email, you take, you know, you go on their LinkedIn and you find, their title or maybe where they live. And then so you, you know, you integrate some of that almost like a social engineering level of, of, you know, very targeted phish versus the, you know, Nigerian prince with misspellings and all, you know, all the all the crazy stuff we see in most phishing emails. They actually found that there was no, from what I recall, at least hopefully I'm remembering this right, They actually found that there was no significant difference in the success rate between the two. And I believe their kind of conclusion there is that if you're if you're the type of person that's likely to click on a phish, you're probably not really evaluating the context of that message all that much. Right? You're kind of skipping ahead. So the reason that makes every time I kind of talk about AI that I think about that is I think AI is really impactful on the margins. Less so, kind of at, at the, the mean. Right? So I think, I think AI becomes very interesting in cybercrime when you talk about, what AI can do to either a very, you know, low tech, a very, you know, unsophisticated cybercriminal and, or a very sophisticated, you know, somebody on the other end of that spectrum. So for like the very low tech, you know, think about maybe a member of the com or somebody that's just kind of getting into this cybercrime world. Give him AI maybe they're going to be able to, you know, do some vibe coding and make something that is resembles malware. Or maybe they can start with something that's available in a public GitHub repository and then using AI that can, you know, adapt that into something that does maybe more malicious things. And then on the other end of the spectrum, you have those, I'll use the term sophisticated actors that maybe with AI they can scale up a little bit. Right? They can do more than they would have been able to do where they doing things manually or, you know, that phishing example maybe, maybe, maybe scale was the problem there. And that that research, you know, ten years ago it didn't AI can do a better job of making those targeted phishers. And then if we look at that on the margins, maybe, maybe most people are going to click on it regardless. But those few that won't be fooled by the Nigerian prince scam, would be fooled by, you know, what ChatGPT comes up with. Or, you know, I would imagine ChatGPT would probably say no to this request, but dark GPT comes up with. Right? And so to me, that's I think that's the really interesting part there. And, you know, it's kind of kind of plays well with that, that earlier conversation that we had about lowering the barrier to entry. You know, AI is it allows people to do things that they probably couldn't do without AI. You know, anybody who's waded through the, the, the Stack Overflow, you know, question responses, it's not always super clear. So AI kind of makes that a lot more consumable. And, you know, Cursor it'll do the changes for you. So, yeah, I think that's kind of where my, my, my brain goes that it's less of, you know, does this really shift the needle, dramatically for everything and more so, you know, what does this do on the margins? DAMON: Yeah, I think those are great points. And I think that when it comes to the industry, right, the industry adopting tools, if you really look at the bulk of capabilities that are out there now, the AI that's really being baked into most offerings is really like kind of taking the concept of generative AI or natural language conversation with the AI, and using that to enhance the ability of the person in your SoC or your CTI analyst. Right? It's making research faster. And I you know, I think it's, you know, it's basically taking their tedious tasks and speeding them up. So it's making them a little bit more powerful and their capabilities, that in itself is not going to dramatically actually fix a cybercrime problem. Specifically, I think we're at the very beginning of the industry, using the LLMs to do really powerful things. Right. And I think we've kind of moved to a place where finally, security companies, are starting to bake LLMs into their offering to figure out how can we do analysis that goes way beyond what what we were able to do without our LLMs? Right? How can we better detect crime? How can we predict what the next crime is going to be? And certainly that's what we're doing with this SpyCloud products. I think as an industry, those are things that are new, right? Those are things that we don't know how to understand, how effective they are, how well they work, how to deploy them, how to do these things at scale. Those are all things that are new. So, I think the the CISOs, the survey, I mean, it kind of shows that they're looking at AI with a little bit of skepticism like, well, how is it really going to move the needle? And I think we're only at the beginning of starting to understand that. Let's see. So Trevor, let's talk about Let’s talk about malware. TREVOR: Ooh, my favorite. DAMON: I know. So malware. This report talks to a little bit about the changes in the malware environment. I know that, you know, we've we've you and I have talked to the, you know, the industry. We've talked a lot about what happened with Red line diminishing in the world and Lumma jumping up in the world. What's the latest what's going on as far malware goes? TREVOR: Yeah. So just to kind of position this obviously we're talking about a very specific kind of malware generally called infostealers. I would include keyloggers in that although we don't see as many keyloggers as we used to, but, these are what I would refer to as commodity malware. A lot of them are sold as malware-as-a-service, which is basically just a model of selling something where you have the, you know, the, the actual software itself as well as support for that software, as well as all of the tools that you would need to actually make use of that software. So just like, you know, everybody knows, I think at this point with SaaS is there's a there's a, you know, an equivalent in mass that is has, you know, not this is not a new thing. This has been happening for years, but certainly, gaining prominence. Even more so. As far as, you know, where we are, you mentioned RedLine back in 2024. We saw some fantastic work by U.S. and international law enforcement, to take down RedLine, that also impacted meta, which is was at the time basically a fork of RedLine. That is effectively gotten rid of those, which is objectively a win. And I think we should all celebrate that. However, and not to put a damper on the enthusiasm here, it really it has not solved the problem. Right? This, this type of infostealing malware, you know, continues to be a huge threat, in, in, in, in volume in targeted attacks, you know, you name it. I would say, you know, the king of the hill at this point is LummaC2 that is, it targets Windows exclusively. It's relatively cheap. It's relatively full-featured. It's very well-supported, perceives regular updates has a, you know, vibrant community of, of users, that, share tips and tricks on how to, you know, infect the most victims and earn the most money. We see a lot of, you know, the that kind of the proceeds then go certainly towards ransomware and more enterprise focused attacks, but also, you know, much lower skill, lower effort, things like crypto draining and, you know, financial fraud, that kind of stuff. So that that's kind of the king of the hill. We see some other. Right, is is still there. We see, still see occasionally certainly LummaC2 has it for, for Windows. And then on the MacOS side, you know, we do see Atomic also called AMOS, online. Is, is still, you know, in the on the order of a few thousand a month at least. Infections. We have another stealer, another MacOS targeted stealer that we haven't been able to figure out what the actual name is. Yeah. Per month of of unique infections of, of Mac products, of MacOS running, products. And that's also kind of an interesting subtext too because as we see businesses, you know, turning more towards, using Mac devices, I, I've heard from several, you know, people that are kind of going through these processes. One of the one of the reasons that they cite often is security. They're not they're not infallible. Our families that target MacOS, they do a pretty good job of of pulling things like keychain and, you know, secrets from, from those devices. So, I would say, you know, the TLDR of that is, they're still happening. We've seen some success. Law enforcement has done some great work on taking down some of these families. But, you know, unfortunately, this is an engine that just keeps on running. And, I really don't see an end in sight. DAMON: Let's talk about phishing for a moment. Survey respondents talked about how, phishing was seen by them as the entry point for ransomware and 35% of attacks, up from up 10% from last year. And so, you know, we definitely see phishing is the problem. That just will not go away I feel like it's been here since the creation of the computer. It feels like almost, but probably not quite that long. And we certainly are starting to see it be, industrialized by the criminals. Right? Where there the phishing-as-a-service platforms are only scaling up their capabilities. What are you seeing as far as phishing and growth in the phishing ecosystem? goes? TREVOR: Yeah. This is so funny because I yeah, I think actually I'm pretty sure somebody is going to there's going to be a Wikipedia that's going to prove me wrong when I say this, but I'm pretty sure the first phish was like in the late 90s or something like that. I, I remember being on AOL Instant Messenger on the early 2000s and getting like, obvious phishing messages. Right? I think, so yeah, phishing is not new, which is this. It's so funny that this continues to be such a huge problem. But it absolutely does. And honestly, I mean, phishing has gone the way of malware, and turned into a commodity. We, you know, as of the recording, we track 18 distinct kits. Named kits that are being sold, and used. A lot of them are, well, I don't know. They range in, in, in, you know, how, how good they are or how well-written they are, but a lot of them are quite good. And we do see a lot of, you know, very large, enterprises, unfortunately, showing up in the, in the phish data. So, they're making an impact. There's definitely a path between phish, you know, phish data and and ransomware, especially for some of the more sophisticated kits, that can, for example, you know, be a man in the middle for cookies. That's. Yeah. MFA bypass effectively is is what the goal there is. We also see, you know, phishes targeting things like non-human identities, like API tokens. We see them targeting things like, you know, crypto seed phrases. So there's just a range of threats that, that, that these phish kits pose. And I think the, the availability of them and kind of how cheaply they are to obtain, makes them pretty dangerous. And I do I do think we will see more phish kits, more commodity kits, and better commodity kits, in the years to come. Unfortunately. DAMON: Yeah. I think it's been interesting for me and talking to enterprises and CISOs that, everybody understands the phish threat exists. Everybody fights it with security awareness training or some move into human resource management. But I still think most, most, most enterprises don't quite realize the scale of what's happening with phish. And the reason that it continues to be a business for the criminals is that continues to work, and they just get more and more sophisticated. And how these systems do the work for the other actors. Right? And the providing of that service. And it's so easy to phish and you just need a few clicks. You get one admin credential. and man, you just made a ton of money on what is a really low cost service that's being provided. And so it's, it's a very interesting part of the darknet. And it's so effective, even if the numbers of victims are low, but they're not they're very high up and so effective. It is not going away. This is only going to continue to scale, just like we continue to see malware scale until we figure out a way to, really make those credentials that they're stealing and those assets that they're stealing completely ineffective. Right? And, and that's really the big step we need to take as a, as a group. Yeah, thanks for joining our conversation. And for more information about all of the details we've talked about and those stats, please check out our new Identity Threat Report available at SpyCloud.com
- Video
2025 Identity Threat Report: A Discussion of Key Findings
Tune in with Trevor Hilligoss, SVP of SpyCloud Labs, and Damon Fleury, Chief Product Officer, to learn about the top threats shaking up the cyber world this year – and what you it means for identity threat protection.
SpyCloud Investigations powered by AI is really a paradigm shift because now investigators can do investigations at scale with AI driving the analytics. It lowers the sophistication and threshold that an investigator needs to have. It takes away the mundane portion of the investigation and speeds that part up. SpyCloud Investigations is meant for analysts and investigators, both public and private, all skill levels, to look for attribution of actors, and also understand communities of actors and their infrastructure. SpyCloud augments every single analyst within a SOC with an AI expert, turning what could take hours into seconds in a report that they can share out with their team. SpyCloud data can be used to uncover malicious, so witting insider threat, as well as unwitting or innocent victim, insider threat examples. SpyCloud gives visibility into fraud campaign infrastructure and insider threat in a way that no other tool does. Ready to expedite your investigations? Go to spycloud.com.
- Video
Close Investigative Gaps Faster: SpyCloud Investigations with AI Insights
Thanks for joining us today. My name is Damon Fleury. I'm the Chief Product Officer here at SpyCloud, and I'm joined here by my colleague, Trevor. Introduce yourself. And I am Trevor Hilligoss. I'm the Senior Vice President of SpyCloud Labs at SpyCloud. So today, we want to talk about our newest release of the Identity Exposure Report for for the data that we collected through 2024. This report talks a lot about the different types of data that we've been able to see on the darknet that we've collected from the criminal underground and how that data can impact you as you are trying to protect your enterprise from the things that criminals can do with this data. And one of the key findings in this report is that we've seen an interesting shift, a shift from user-centric attacks where the criminals are focused on the email addresses that might be attached to your enterprise and all the information they can see connected to that email address, to going way beyond that, to studying the individual that's connected that email address and looking at that holistic identity that can be connected to that individual. That broader information provides them a much larger view into the total attack surface that they can use, other passwords, other aspects of that individual, they can use to attack your enterprise using the email address or the login that's specific to your enterprise. So this has been a really interesting and important finding that we've shared in this report, but all of this comes from the data that we're able to see on the dark net that criminals are using. So Trevor, could you share a little bit of it with us about what is that data and where does it come from? I'd love to, Damon. So when we're talking about sourcing this data, really, we're talking about information that comes from third-party breaches. So that's a company or a service that you or your employee might might use that gets compromised, and then the data is stolen and leaked on the dark web. We're also talking about malware infections and the data that those expose as well as phishing kits. So summarizing all of that together, by the end of 2024, SpyCloud has recaptured over 53 billion total identity records. Now that's a 22% increase year-over-year. So we're seeing an increase in the amount of data that's available to these criminals that can be used to craft these sophisticated attacks. Now part of that 50 billion records are obviously individual assets, and the number of assets vary pretty dramatically depending on what we're talking about, whether it's a malware infection or a breach record or a phish. In all, SpyCloud has collected 750 billion stolen identity assets. The important thing to recognize there is the more assets that are available about you or your employee, the more data can be used to craft that holistic identity attack against either you or your employee. Cybercriminals are not just stealing individual credentials anymore. They're now gathering a vast amount of data from multiple sources, which is in turn making their attacks much more effective. So by enhancing the view of identity exposure using holistic identity matching, SpyCloud sees more than 12 times the exposed data for an individual employee on average. So this illuminates a larger, more accurate picture of true identity exposure. Now, Damon, would you mind kind of describing what is that average identity exposure? What does that look like for an individual? Yeah. That's a great question. And so we saw this year that an individual such as myself saw on average eleven stolen records that were based on their corporate email address. And so that means that eleven different times in third party breaches or maybe even a malware infection or a phish event, data showed up, through some type of dark net communication. If you looked at the holistic identity of that individual, on average, we saw a 146 records. So that spread across their personal email addresses, that spread across older work email addresses or some other organization they were once a part of. That could mean as many as 13 different unique email addresses versus one if I looked at it from a single user account standpoint. Or a 141 credential pairs that have target URLs attached to them, which means that that's the actual website that they logged into with that username and that password. There were IP addresses, so you could figure out where the individual was coming from 50% of the time. And on average, that information came from eight different sources, which could be different malware infections or could be different third-party breaches. And then if you look at this from the perspective of a consumer, then we can see that there's an even larger number of records where you might see as many as 229 records if I'm looking at this from a consumer email address and not just a corporate email address. And so you can see that as criminals are pulling this information together and they're connecting it all, then it is really giving them a really broad view into the picture of that holistic individual. And so this is really, unfortunately, empowered and given our attackers more tools to use that we have to be ready to protect against. So, Trevor, how are the attackers using this type of information, and how is this presenting a threat to our businesses? Yeah. So just like SpyCloud can aggregate this data, and provide it to our, customers so that they can protect themselves, criminals are doing the exact same thing for much more nefarious purposes. So we see a lot of these, criminal communities online that serve to aggregate this data, that serve to create these holistic identities so that they can target both the consumer approach, which is largely financial, or the enterprise, which is where we look at initial access brokers leading into things like ransomware. So, really, a holistic identity approach is a necessary evolution for understanding and remediating the full scope of user exposures that affect the organizations with which they work and do business these days. I think a good next question is what can you do to help protect your own enterprise from attacks that leverage the holistic identity? The first step is to gain access to this type of information to make sure that you're using the world's best data source that is tracking what the criminals are doing and tracking the information they're using and can be aggregated in a way that you can understand it. There are also tools available that can automate the remediation of this information within your own infrastructure. So gaining access to those types of tools and services are a really powerful deterrent and can protect your organization from holistic identities being used against you. For more information about this, we highly encourage you to download our our Identity Exposure Report for this year. You can get it at www.spycloud.com. It's right there on our landing page. Please do review it, and feel free to reach out to us with questions. We'd love to discuss this more.
- Video
2025 SpyCloud Report: Holistic Identity Exposure Trends
Cybercriminals aren’t just stealing credentials anymore. Learn about the shift from user-centric attacks to the sophisticated identity-based attacks that take advantage of a broad & growing range of darknet exposures.
Backed by the world's largest recaptured darknet data repository and powered by advanced analytics, SpyCloud gives you visibility into the holistic identity of your users and gives analysts the ability to uncover and link hidden identity assets. With SpyCloud, build comprehensive cybercrime investigations and protect your enterprise from identity based attacks stemming from your employees, customers, and suppliers' dark net exposures.
- Video
The Power of SpyCloud Investigations
See how you can leverage SpyCloud Investigations to build comprehensive cybercrime investigations and protect your enterprise from identity-based attacks stemming from your employees, customers, and suppliers’ darknet exposures.
The majority of Zero Trust implementations are missing a key input. Here's how SpyCloud is closing the gap. Traditional Zero Trust policy engines only test the validity of users and devices when they first access the network. This approach doesn't take into account the vast amount of identity, device, and access information criminals already have in hand. Beating bad actors is a relentless cycle made more challenging by digital Zero Trust implementation should mirror that reality. Continuous Zero Trust means your identity protection never sleeps, constantly verifying user identities and endpoints for exposures. Truly mitigating risk hinges on the ability to make informed decisions around the clock. Spy Cloud feeds your Zero Trust engine with actionable breach and malware data, keeping your policies always informed and one step ahead. Harnessing cybercrime telemetry, SpyCloud integrates with your existing identity and security tools and gives you the power to make informed decisions about whether a user account should be allowed access based on real evidence of compromise. Cybercrime doesn't take a break, and neither do we. Protect your organization against next -gen identity threats with Continuous Zero Trust powered by SpyCloud.
- Video
Continuous Zero Trust with SpyCloud
Traditional Zero Trust policy engines only test the validity of users and devices when they first access the network, missing the vast amount of identity, device, and access information that criminals already have.
Hello. My name is Joe Roosen, and welcome to another technical chat with SpyCloud Labs about some of our recent research and reverse engineering work. Today, I'm joined again by James, staff security researcher at SpyCloud Labs, and the topic of discussion is the notorious Atomic MacOS Stealer. First off, James, can you tell us a little bit about Atomic Stealer? What is it, and why did we decide to reverse engineer it? So Atomic Stealer is a one of the few macOS based infostealers, that operates as a as a malware as a service model, which means that the malware authors actually release a panel, that, that clients can, like, pay to then access. And that panel provides, malware builds, and access to the logs that the the malware steals. And so this means that the malware authors, while they might run Atomic Stealer, they are not the only people running Atomic Stealer. There's actually quite a few people who are running Atomic Stealer. And, the people who run Atomic Stealer have to pay a fairly hefty monthly fee ranging from around five hundred dollars to one thousand per month, for access to the Atomic Stealer panel, which is pretty pretty sizable, compared to a lot of other Stealers that we see. So we when we were looking at Atomic Stealer, for the reasons for why we want to look at this Atomic Stealer, we wanted to learn more about it for a couple reasons. So first, it's it's one of the few active macOS infostealer malware families with full fledged stealing capabilities. It's designed to capture things like admin and key chain password, sensitive system information, and credentials and browser information from Chrome, Firefox, and other applications on a on a on a computer's machine, or on a victim's computer. And then we were also really curious about it because of the popular ways that we've that we're seeing it get distributed by bad actors, most notably through pay through pay per install services like SpaxMedia and and Install Bank, which we've reported on in other research. And in fact, the sample that we looked at in our most recent analysis came from, pay per install services like SpaxMedia and and Install Bank. Gotcha. Okay. So let's talk about what you found when you dug in. Can you expand on what types of data Atomic can steal and from where? Yeah. So Atomic Stealer exfiltrates data from lots source sources. Like, for example, common browsers, so, like, Chrome, Safari, Firefox. It also has a lot of, uncommon browsers, many, many Chromium browsers like Vivaldi, Brave, etcetera. It also has a variety of crypto wallets, like Exodus. It has it steals from a ton of extension browser extensions as well. Most of these browser extensions, most to possibly all. I didn't go through every single list or every single extension in this list, but most of these browser extensions are crypto wallet browser extensions. So it's still just targeting crypto wallets. But, additionally, if Atomic Stealer detects that a victim has specifically the Ledger Live crypto wallet installed, Atomic Steeler will then, attempt to install a backdoor version of Ledger Live, and we can expand on this piece a little bit more shortly. And then, also, we can grab info from from software that's stored on the system, so like Telegram, Apple Notes, and a variety of other applications. Yikes. That's definitely something to be concerned about and have on our radar, of course, for the security community. What do we know about how it's installed and how it runs? So when Atomic Stealer installs, it creates an installed and data exfiltration, folder at a randomly generated numerical based directory in the victims slash users slash username folder, in which it stores all of the data that it steals. This data is is zipped up and then sent to the command and controls, server before being deleted from the system. So when defenders are looking at a system, if they see that up here, that indicates an Atomic Stealer infection. Additionally, Atomic Stealer leverages, AppleScript or OSAScript, which are macOS shell scripts, which are launched with the OSA script utility. These shell normally allow the user to automate all times all kinds of tasks on macOS, not unlike Bash on Linux. But in this case, allow Atomic Stealer to just steal passwords and files as well as carry out the vast majority of its core functionality. Defenders should be on the lookout for unexpected OSA script usage as Atomic Stealer's file grabber grabber is entirely OSA script based and sends the commands line line by line. So you'll see quite a few, quite a lot of OSA script usage. Okay. So let's circle back to some of Atomic's core capabilities. When you did, the reverse engineering work, what did you find that you expected to see, and what was unexpected? Well, so the things are pretty standard for, infostealer malware, but they're still important for the admin or for defenders to know about are things like admin password theft, keychain theft, stealing, system info, the file grabber, and then, like, credential and background and browser pass and browser theft. But then this is kinda where it gets really interesting. I mentioned earlier the Ledger Live backdoor, and, this is this is something that was unexpected to me personally. So in newer versions of Atomic Stealer, when Atomic Stealer is doing the system info, detection, it it gets a list of all installed software. It then scans through that list of installed software and looks for the Ledger Live application. If it sees the Ledger Live application in your list of installed software, meaning that you have, the Ledger Live crypto wallet installed. It'll then attempt to pull down, using Curl, a backdoor Ledger Live application. And it'll install this ledge backdoor Ledger Live application using your own installed Ledger Live application. And then, like, it'll overwrite your installed Ledger Live application. We were not able to actually pull this, sample, but we're looking online from companies that were able to pull it. We were able to see that, it this application like, this backdoor application's sole purpose was to just steal crypto seed seed phrases, which is super interesting. I I'm I don't know much about how Ledger Live functions, so I'm unsure why they would need to backdoor it entirely to steal it. But it's just super interesting that they would backdoor an application like that. But, as far as and so as far as what surprised me, in addition to that, I was surprised that Atomic appears to have gone backwards in this development as well. It's a bit louder compared to previous versions. In previous versions for exfiltrating, data, instead of dropping the data to the, to the device in, like, an exfiltration folder, it would actually assemble the ZIP in in memory, and then send that ZIP to its command and control infrastructure all done in memory. And in recent versions, that functionality has been completely removed, and that might have been changed to avoid certain detections from the Apple themselves. We're unsure on that, but it it could be that they were writing signatures based on applications assembling zips and memory. Wow. That's really interesting about the zip and memory. I would think that'd be a lot more secure, but it like you say, Apple probably caught on to it. So very interesting stuff. So if you had to leave listeners with some key takeaways, what would those be? So it's important to note that Atomic Stealer log log files indicate that the malware affects both x86 and ARM architecture. So all versions of Mac are affected by Atomic Stealer. And defenders should definitely keep an eye out for that OSA script usage. Additionally, users should be aware that their personal and work identities are so for example, if you are working at a financial, institution, in your personal life, you then begin to assume some of the risks of the financial institution. Note, namely, that you, in your personal life, could be targeted by actors that are looking to target said financial institutions. So it's just something to be aware of, when practicing safe Internet safety practices outside of your work outside of your work life, because a lot of infections that happen in work environments initially occur from personal, device compromises. And then the final the final point is that remember that, like like most infostealers, Atomic doesn't have persistence and can slip by antivirus software unnoticed. We recommend that security teams integrate post infection malware remediation steps into your playbooks for confirmed exposures to minimize risk and prevent follow on attacks. Wow. That's some great stuff, James. Yeah. Good point on the personal and work identities being intertwined. Well, I can't wait till I hear what you come up with next. Hopefully, we'll get to talk to you again soon. Thank you. Yeah. No problem.
- Video
Reverse Engineering Atomic macOS Stealer
Hello. I'm Damon Flurry. I'm the Chief Product Officer here at SpyCloud. And I'm joined here by Trevor Hilligoss, who's our Vice President of SpyCloud Labs. You may have seen on our blog that we have been posting a lot of information about the mother of all breaches (MOAB) that several weeks ago, from the time that we're recording, came out and created quite a stir within the security community. We at SpyCloud have done a lot of work. By we, I mean, SpyCloud Labs, Trevor's team have done a lot of work and understanding what what MOAB is and how it impacts the larger community, and we'd like to talk about it for just a few moments. So thanks for joining us, Trevor. We'll save a look. Thank you. Alright. So let's get into it. Trevor, can you tell us about Moab? What is this data leak? Why is it a big deal? Yeah. So Moab, mid January 2024, a bunch of cyber security focus, news, organization started covering this as a, unitary breach. It is, in fact, not a unitary breach. What we're talking about is basically aggregation of a little north of forty one hundred individual breaches, collected over a pretty large period of time, potentially ranging from the early twenty tens, to about 2023 or so. So that's about 26 billion records within the Moab, it's important to note too that that number is preprocessed. So we'll kinda get into this in a few questions, not to do a little bit of foreshadowing, but There's a lot of duplication within this data. So 26 billion, a a pretty, a pretty big number. It's it's likely much less than that. But to put that in perspective, so we we did analyze the data against, SpyCloud's holdings, and we found that approximately 14% by record count was already in SpyCloud's holdings. It represents about 94% of the Moab data those records that we talked about. And that that equates to about ten percent of the total number of breaches that spike has ingested. So this is a a massive amount of data, certainly. But when you kind of compare it to what has been historically publicly available, and certainly what we've already collected and normalized becomes, a much more digestible number. So can you tell us a little bit more about how this data ended up getting out there? What's the story behind? Yeah. So, December time frame of last year's of 2023. There was a an elastic search cluster that was left exposed, unsecured on an IPV six address and it was available to be acquired. We have no idea how long that elastic cluster had been exposed. No idea who else had obtained that data previously. There has been a an organization has come out publicly and claimed, authorship of that of that database. We have no information to authenticate those client claims at this point. But over the ensuing about a month towards the middle of January, SpyCloud Labs began digging into the data and finally kinda getting our our hands around it. Because it was quite a large amount of data even though it was relatively normalized, you know, at at at the beginning. Excellent. And are there any, like, specific, artifacts within this? Can you tell us anything about the breaches that were within Moab that are interesting? Yes. A lot of highs and lows. So we did we did find some interesting things in there. They're worth talking about. One of the kinda highlights, and we mentioned our blog as well, is a previously undisclosed QQ breach, at about north of seven hundred million unique QQ logins, users, rather, so it'd be like q q, the email address, the q q username, and a phone. But for every fantastic, new net new, breach. There was several that were, well, less so. So a couple of those that that stand out to me. There was a claimed breach of triple a. So that's the pure in the United States. That's the company that will bring you a a can of gas if you were like me and, like to play a dangerous game of chicken with your, your gas tank in your car. However, once we take took a look at it, it was pretty clear that it was in fact not a breach of the American automobile administration, but in fact, Ohio voter registration data, from a much earlier and public breach. There was also another one that was claimed to be an eharmony breach that turned out to be a whole bunch of random passwords and hashes. No idea where that came from. And then, obviously, many, many others that we ended up having to throw away because they were either mislabeled, almost entirely duplicative or just unable to be understood. Excellent. So when spy when SpyCloud digests all this information, when we figure out what each of these breaches are, what do we do with it? Do we notify people that were impacted by this and their data was stolen long ago? Yeah. Yeah. So, parallel, in parallel with our kind of parsing and ingestion process. We, our responsible disclosure, organization within SpyCloud Labs was very, very busy. So we have been going through this data extensively identifying anything that was new, especially because, you know, these breaches that get a lot of public, notice, obviously people that have their names, companies that have their names in these, breaches that don't have the ability to see the data. There's a lot of uncertainty there. So we have accomplished dozens of responsible disclosures over the past couple weeks through this data, which is just us responsibly handing off the data to the company. That was impacted or allegedly impacted. Some of those, we've gotten some feedback that says, cool. Thanks, but, this is not us, and it's junk. Which is fantastic. Obviously, that's the response we want to receive. Others have been very grateful, that we were able to give this data to them. So That's also a good feeling, when we can when we can do that. And the process is not over. So we sit here in February of twenty twenty four, anticipate There will be many of these, obviously tapering off, but into the next few weeks and or months as we, finish sorting through this data. Excellent. So we collected it by cloud all this data. We went through it. If I was already a by cloud customer, What is the difference for me that SpyCloud now has Moab? Was this already if these were older breaches, was I already covered? Yeah. Yeah. Pretty pretty pretty minimal. So, you know, I don't wanna I don't wanna minimize that we we pulled in when this is all said and done, probably about 1.6 billion net new records, which, you know, A huge number sounds like a scary number. But if you kind of compare that to the 92ish billion records that we already had, puts it a little bit into context. So we at spike cloud labs have analyzed the data and we believe that there's right about ninety four or ninety five percent overlap, with the Moab data that was with spike lab data that was already within our our holdings prior to Moab. So, basically, what this means is we're just closing that six percent gap from Moab, which, really, if you put that in perspective of the data that SpyCloud already has, is, you know, one percent, if not less. Excellent. Alright. Thanks, Trevor, for sharing your thoughts about this. If folks would like to know more about, more about our with Moab, please come to the SpyCloud Labs website, and also Check Your Exposure. So if you'd like to know if your data was within any of these breaches, you can get a view of that at spycloud.com. Click on the check your exposure link, and you can learn more about where your data shows up and whether it was in these breaches.
- Video
The Mother of All Breaches Data Leak
In this video, our team at SpyCloud Labs discusses the monumental “Mother of All Breaches” (MOAB) Data Leak that shook the security community. Watch to learn about the 26 billion record data leak, the extensive analysis by SpyCloud Labs, and highlights covering the intriguing findings.
[MUSIC PLAYING] - We've recently had a client reach out eight weeks after SpyCloud had published data saying, hey, we got an alert from another dark web monitoring platform as part of another service that said that our information was on the dark web associated to this specific breach. 360 Privacy's been around for four years. Started a group of former special forces individuals that were focused on signals intelligence and the intelligence cycle overseas, wanted to create a company that could better support and delete the digital footprint of individuals because of the right to privacy within the United States. The clientele at 360 Privacy ultra high net worth individuals were focused on antifraud, were focused on reputational harm, were focused on account takeovers, specifically using SpyCloud data to better protect their social media accounts, their email addresses. - It's obviously like we are a privacy company, so our clients are inherently hiring us to manage their privacy. There's a lot of trust and responsibility that goes along with that and we don't take it lightly. Because of that, by working with a group like SpyCloud, we're so connected now through technology that our lives live on our phones in our pocket. If you can get on my device, if you can get in my email, you can get in my iCloud account or whatever, you can literally do a complete digital life takeover. - But if you truly don't understand your dark web digital footprint, you don't understand that even if you had a service that deletes you from the open web, you still have vulnerabilities and SpyCloud helps us identify those vulnerabilities for our clients. - By working with teams like SpyCloud, we're able to proactively find and then remediate this information. Oftentimes the information that we get through SpyCloud comes weeks in advance compared to some of the other platforms out there or the other competitors. - Intelligence becomes stale quickly. More doesn't mean better, what we found with SpyCloud as far as looking at the legitimate data is as I looked at the input to output ratio, we were actually able to get rid of a platform that we had at the time that was costing the company a lot of money because the value of SpyCloud to the program and to our client was just exceptionally higher. Really it just makes it a cleaner experience for the analysts, it's less noise. Because as an analyst, if you're going through data day in and day out, you get fatigue and the way that the interface works for SpyCloud is that you don't get that fatigue because the data is so clean, it's easy on an analyst to really parse through. Once we onboarded SpyCloud, we were able to keep the same amount of bodies but increase efficiency to the point where we don't need to pay for more bodies because that's losing money for the company simply because of SpyCloud. And I think what I really want to tell people is that SpyCloud is more than just credential data. They have so many different data sets that cover everything from your personally identifiable information to maybe publicly available information that because of other dark web exposures could actually expose you and your family. When we've put SpyCloud through the wringer, so to say, they've come out on top. And so us being able to pivot away from other, what I would consider maybe substandard vendors in the area and work with a group like SpyCloud, it's a win for everybody. So what SpyCloud gives our client is honestly a peace of mind because they're able to have that understanding of what truly happened, what's out there, what's their exposure, and then what we're going to do to mitigate future issues. [MUSIC PLAYING] PLAYING]
- Video
360 Privacy | SpyCloud Customer Success Story
Hear how 360 Privacy leverages SpyCloud’s suite of holistic identity protection solutions to protect more than 1,800 individuals and their digital footprints – reducing risk from dark web exposures and protecting against targeted attacks.
Blog
Case Studies
Tools
- Tools
Darknet Exposure Check
Identify threats to your organization including third-party breach exposures, malware-infected employees and consumers, password reuse, and more.
- Tools
Password Exposure Check
Test any password to see how many times it has appeared on the darknet, meaning it’s unsafe to use.
Guides
Research Reports
Whitepapers & Ebooks
On-Demand Webinars
Webinar Videos
Okay. Great. We see a lot of participants. So, let's go ahead and get started. Thanks for joining today. Today, we have a live event all about minding the malware gap, about identity threat protection beyond the endpoint. Our hosts today are Damon Fleury, the chief product officer at SpyCloud, and Joe Russin, director of security research. Joe is over twenty years in various IT roles, but is now focused on cybersecurity and leads our whole security research arm. He's all about collecting all the breach and malware and fish data that we'll talk about today, and he's actively collecting data as we speak. So, a little Zoom etiquette today. Please post your question in q and a in Zoom. We'll have time at the end to address it, or we'll have live q and a depending on on how the conversation goes. But please add it to q and a. We'll make sure we answer your question on this call or afterwards. So today is all about malware. We're gonna give a brief overview of the malware landscape and what's changed the past few years. Joe will talk a bit more about what SpyCloud Labs has learned from, looking at trends malware and analyzing some of the top stealer families out there. Dane will talk a bit more about the malware kill chain and the attack life cycle we're seeing from, bad actors, but then we'll go beyond the the endpoint with spy cloud, show a bit more about how our solutions could help you, including a live demo. And then Joe will give some tips for how you can protect your workforce identities today. Thanks, Taylor. So before we get into the conversation around exactly what is going on with malware, Just wanted to give a brief overview of the kinds of data that spy cloud does collect. And so spy cloud really focuses on information that is flowing through the dark net. Like in this image, you know, we have all these data points flowing through the dark net that is on its way to actors, With those actors, you're using this information and this identity related information in order to attack your enterprise at the end of the day for account takeover, for online fraud, for ransomware, for a variety of other types of attacks. And when we are looking for data, when SpyCloud is looking for data that becomes the basis of our products, we're really looking for three forms of data. What we're known the most for is this box in the middle here for breached data that we've been collecting since the beginning of the company, and we have more than forty thousand distinct third party breaches. We're adjusting hundreds of new breaches that we find throughout the globe every single week. So we have a lot of data that comes from third party breaches. We also have data that comes from successful fishes. So when you when one of your employees or an individual clicks on that link and just just falls prey to that trick once again, and they actually give up their data, I mean, the the actors are using that information for their own for their own agenda. We are collecting that data, and we'll have some webinars on how that works coming up. But what we wanna talk most about today is another core element of what we collect, and that's malware victim logs. So when individuals do accidentally install malware or somehow malware does get installed on that system, then those bad actors are collecting as much as they can from that system as quickly as possible, funneling that into the dark net, and that's where SpyCloud picks up that data. So just wanted to set the stage for these are the different types of data. So when you're a SpyCloud customer, you gain access to all of these. But we know a lot of lot of customers and a lot of folks are interested in what's going on with respect to malware data specifically, and how that can be used to help protect your enterprise, the data that we find. So with that, I wanna turn this over to Joe to talk much more about the malware landscape. Thanks, Damon. Good morning, everybody. Two thousand twenty four was a great year for collections in Spy Cloud Labs. We have, nearly eight billion third party records ingested, and those are the breaches that Damon was talking about or the breach data assets. And we also have, five hundred and forty eight million malware records that were ingested. This is actually what we're talking about today, and that's across sixty four malware families. We also had a good one point five million, Telegram messages collected, and those might include things like combo lists or phishing data or even sometimes the third party records that we were talking about earlier and even some malware records for, stinger logs. So these things are actually something that we're looking to leverage more in the future and hopefully be able to have quite a bit more data as we increase our assets. But we also had, speaking of assets, a good, fifty four billion or so, new assets ingested. So that's quite the number. We're we also have a pretty decent, report, if I must say so. The two thousand twenty five spike cloud identity report, you should check it out if you haven't already online. I thought it was extremely well written, and there's a lot of good little tidbits of information. We have basically a couple things here that we want to go over that's related to this particular, scenario today, which is, ninety one percent of orgs reported some sort of identity threat in the last year. And then stolen credentials were actually part of eighty percent of the breaches, that we basically saw that were related to malware, in malware or combo list. And, honestly, with combo list and what we call, URL login and password or U LPs, those basically all kind of our source from combo or excuse me, from malware. The stealers that are actually involved, basically, are usually parsed out by the threat actors, and they make up these specific type lists where we can basically then, where they target certain organizations or certain vertical sectors. The other thing that we wanted to mention here is that the Infostealer malware, basically had been involved in fifty percent of corporate user infections. So as you see here in in this slide, we had quite a bit of red line in two thousand twenty four, and you also will see Rizepro and, Steel Seed, Meta, and LUMA kinda at the bottom. But here's the big thing that changed, basically, in this, near New Year. Basically, as of two thousand twenty five, even in the first quarter so far, we have seen Luma really take off. Base if if you could see here, the increase is huge compared to what we had in the past. You're looking at a twelve thousand, eight hundred or excuse me, twelve thousand eighty three percent, or twelve hundred eighty three percent, excuse me, year over year luma increase. And as you could see also, the other Steelers kind of all kind of, fell by the wayside. We think that this particular issue or what we see here is because of red line's takedown with Operation Magnus in October twenty, excuse me, October twenty ninth two thousand twenty four. This basically led to LUMA kind of taking over the underground and being the stealer of choice or the commodity malware of choice. So, going back to the heyday of monolithic botnets and kinda going back to two thousand seventeen or even earlier, in the past, what we saw was a single owner, that were a group of owners that had a modular code base. We're talking about botnets like Quackbot, Emotet, Trickbot, these types of things. The way that the malware kind of, worked at that time, it was pretty centralized, and it actually had trite infection vectors. You probably have all seen it in the past where you get an email, it's a phishing email, and it tries to get you to execute some sort of macro code on your machine. The technology basically is now or excuse me, has was at that time more centralized and and susceptible to LE action. And law enforcement agencies actually executed takedowns of Emotet in two thousand twenty one, and also in two thousand twenty two, and then Quietbot in two thousand twenty three. And then we saw, operation endgame, which took down Iced ID, Bumblebee, Peekabot in two thousand twenty four. All of these things kinda had a very heavy weight on the, underground infrastructure for criminals. They, were no longer able to utilize these things for the initial access brokerage. So, essentially, the attack chain also was expensive to, maintain. They had to do every angle or every part of the whole attack chain themselves or somehow package it within their c two infrastructure. Social engineering also was the main thing that was getting them, access or their lures in Microsoft, as we mentioned earlier, had basically macros, that we're allowing by automatic or default, executions on local machines. It was pretty easy for users to click one box and infect themselves. That changed in July two thousand twenty two, and we basically had the new infection vectors, that they tried to use afterwards. Not so effective. Things like l n k's or ISOs or JavaScript where they were fifteen some different steps you had to do, and it was unlikely that users were basically going to do the whole chain of events in order to infect themselves. So what we have today is, as a result of that law enforcement action in bad actors having to adapt, They started to look towards things like commoditized malware and taking things off the shelf. Things like info stealers were already on the rise. They were basically coming up and becoming more sophisticated, but this actually really accelerated that. What really mattered to the endpoint actors, in order for them to be able to install some sort of ransomware or to extract things is just the access. That's all they care about. They need to basically get those different victims listed so they can actually attack them. So one of the ways that the teams or the people that do the actual initial access, brokerage for them was they started to use malvertising. And this is where you have common apps that you might have on the Internet where people look and try to find some sort of a download for maybe Zoom or Slack. And these types of things were leveraged by threat actors to create fake ads, and the ads always show up at the top of the list when you do a search. And since end users are accustomed to searching for things, they just pick the first thing. And that way, the actors can set up a fake website, essentially, that is a mirror of a real download website for Slack or Zoom, and then they have their malware that's actually injected as part of the process. The technology was essentially no longer as centralized as it was, with the old take downs of the past. So for the most part, they were more resilient to being able to be taken down, although we still seen some action to it. They also, are leveraging a mature ecosystem of criminal services. There's best of recode. There's a whole criminal infrastructure that essentially is, partners or a web of partnerships where people trade services. So this leverages that. Speaking of those services, some of the independent services that were out there, like Ghostox, have had some very, burgeoning partnerships with modules for the info stealers. So the impact is basically we have, an expanded and diversified malware economy. It broadens the threat actors, community access with common tooling, which is very important because then people can move from team to team in order and have the actual exact same tools that they're accustomed to using. In the users, actually, as we mentioned, infect themselves because they're searching for apps to install. And when they go to install the app, actually, it does, in a lot of cases, install it, but it is also putting some malware in there for along the ride. So here we have basically an example of the one of the partnerships. Ghostox has been working with Luma, and we had created a blog on this that we'll send out to you afterwards. But, the main idea here is that LUMA has a second punch now where most of the cases in the past, Infostealers would run once, and they'd be done after ex exfiltrating all the data from your system. In this particular instance, the threat actor can, from the c two panel, actually decide to install Ghostox on a particular victim, and then that victim has a persistent backdoor on their machine. What will happen then is that the threat actor can essentially run commands and browse through that, SOX proxy. That SOX proxy, could be used to do spam or fraud, or they will sell that access to somebody else. And then that basically is just another issue for your environment. Here's an example of basically some of the law enforcement take downs and how it's leveraged, essentially by large ransomware type groups. Bypass, you probably heard about, had a issue recently where they their chats were released, and, we took some time to announce do some analysis on the the chats. We found that, basically, when operation Duck Hunt took down Quackbot, which was in August two thousand twenty nine, of two thousand twenty three excuse me. Basically, we had, essentially, the threat actors have a, oh, crap moment because they didn't have any of those initial access vectors coming in anymore. They had to find something other than quackbot in order to get their foot in the door. So as you could tell with the listing of the different chat topics here, this is a map of what the chat topics were over a period of time in with September first being after the takedown. As you could see with the Steelers, it actually starts to increase over time. Eventually, Black Vesta decided to move more towards brute forcing, but this is from another blog that's gonna be coming up soon. So look out for that, which gives you a more in-depth, sort of overview. But Black Vesta did have in their panel a Steeler module. So what's in a Steeler log? Why are these such an issue? Well, you can kinda see, what we have here in this page is at the bottom, we have a a, atomic stealer. Basically, the log that shows you the key chain access, and the key chain access for your macOS is essentially where you save all your passwords. Also, you could see there's autofills in there. There's some brute force ideas. Sometimes there's more than zero bytes in there. That one just happens to be empty. But, you can also see cookies. You could see things like desktop files inside of this or browsing history or even desktop screen captures of what you were doing when you installed the malware. The, really critical thing too is from a financial perspective, it also will pull out credit cards from the browsers or it'll pull out cryptocurrency wallets from different apps. It will also, basically look at different common application installs to see what may be saved for credentials. So the really important thing and something to think about how you could pivot or very easily get into a corporate system if if a user at home installs essentially, a malware that is an info stealer that pulls data from their remote desktop application, whether that's VNC or something else. They can then basically get the access to that remote system. So if they use that in order to remote into their workplace or their enterprise, you could see how that would be a big problem. Some of the common apps you can see on the right, there is AnyDesk, Telegram, TypeVNC that are listed at the top there. That actually is a Luma c two, log that's shown. So let's meet the, top malware, Essentially, inside of our, our top list, I guess you could say, on the Windows side, you see Lumacy two. By far, it's the most common sealer infection we've seen in two thousand twenty five. We expect this to continue. LumaC two has seen some constant, development. There's been a lot of, things where different browser, creators will try to lock down things like cookies or stuff like that with encryption, but then matter of days, this developer from Lumacy two comes back and has a workaround for it and still has access to it. The it's essentially a cat and mouse game with detection. We have we we have quite a few different pieces of the ecosystem where the actors are able to take their malware, send it to a particular encryptor or a loader service. And from that point, it has a whole new attack vector and is able to get in quite easily. The as we already mentioned, we pull unique configs on the configuration with Luma c two, and we also have that GOSOX partnership we already talked about. So if we have, essentially, Max, are we okay? Well, not so much. If you take a look at what we also have in the ecosystem, we have Atomic Steeler. And what we've noticed so far is that this is growing and is increasing in size in the amount of, atomic steeler logs that we're able to collect in the dark net. And this is probably one of the fastest growing even though Luma is growing so fast from what I see. The same type of malvertising is used for, basically, these third party, apps vectors, where if you're trying to install, for instance, a particular Mac OS application, they will be out there mirroring those download sites and doing malvertising to get you to choose them first, and then they come along for the ride. One thing to that's really important to note with the malvertising is, just to touch on it again, we see basically some of these packages that they put together installs this info stealer, but it also installs the real app. So the end user doesn't realize something has actually happened. Logs are also including the keychain info, as I mentioned earlier, which is pretty critical. And now I'm gonna send it over to Damon. Thanks, Joe. And I see there's a question, in the q and a that actually segues perfectly into the next part of our conversation. And that question is how good are EDRs at preventing malvertising from being successful, and can they bypass EDRs? And I think the unfortunate reality is even though EDRs are fantastic and critical parts of your protective mechanism, you absolutely we do absolutely have issues where some of these different technologies and malware are bypassing the EDR. And, you know, this number on the screen is specifically talking to that. In the first quarter of this year, we discovered we pulled in from our dark net sources ten point seven million infections of systems, and sixty six percent of those had an endpoint security product of some kind, an AV or an EDR, deployed on that device at the time of infection. And so the unfortunate reality is that there isn't a silver bullet in stopping malware. There isn't there isn't something that could stop every single case. And we'll talk a little bit more about what some of those what some of the reasons might be for this. But our reality as as individuals that wanna protect enterprises is that we, you know, we have EDR. We have to have it. It's a critical piece of that solution, but we have to realize that some things will get passed. And are there ways for us to understand, and what can we do in those scenarios? And so I wanna talk for a little bit about this kind of larger ecosystem of of malware. You know, I think Joe just gave us a great, bit of insight into what we're seeing, particularly in the info stealer part of malware. But I think it's easy to get kinda lost in. Well, we talked about all these different variants. I think we'd last year, we had sixty four variants of of Infosys we are tracking. We're up to seventy five different variants already this year. How does all that fit into when an actor is trying to target an enterprise or trying to to gain access and find a way to make money off of one of our companies. Like, what's going on, and where does LUMA c two or any of these infrastillers fit into that? And how can SpyCloud get this data, and what can you do about it when that happens? And so, so all, you know, all endpoints, endpoint security solutions, and really all kind of malware detection solutions are trying to find any place in the attack cycle that an actor is trying to take advantage of a weakness, and you wanna detect that and you wanna stop it. And so when you think about the attack life cycle, many forms of malware may play a role, and the things Joe just talked about are just one of those bits of malware. So if you think about somebody trying to attack an organization, it always starts with the entry to that organization. You see in this first column on the left, they could get in through a phish. They could get in just with stolen identity and credentials, which is something that we we see quite a bit from spy cloud's perspective or social engineering. There's a variety of ways to get entry to a system, and that typically happens very quickly. And once they gain entry to a system, they immediately move into what I like to think of as the recon phase. They're trying to establish some level of control so they can run more malware or some level of connectivity. It's often automated. There's there's sometimes not, you know, any additional steps. And then they're trying to figure out where are they? What have they gained access to? Running an info stealer has become the primary way of getting an inventory about that computer and about the rest of the system. They wanna know things like, are they on a domain? What kinds of applications are installed? What do these users have access to? Do these look like administrators? Like, where have they landed? Right? And they at at the beginning, they don't know. And an infostealer is a really well established set of infrastructure that allows an actor to run this tool really quickly. It goes up to a command and control or to a panel, and then they can gain access to that data right away. They'll also run other tools to do network mapping or to to run domain enumeration. So they're trying to figure out where have they landed, and that infostillers a key piece of it in most of these attack scenarios. Then they move to the entrenchment phase. Right? And so they know a little about where they are, and they now wanna move laterally within that organization or they wanna disable security apps. They wanna figure out, can they get to privilege escalation? They form a back door back to their command and control. You know, I'm not gonna read all of the boxes, but there's a lot of steps that they'll take to entrench themselves within that organization and to make sure that they can then move to the next step. A lot of times, once they've entrenched themselves, that's the point that they might sell access to another actor. That's a point at which they might, you know, go to an initial access broker, sell it, and then a ransomware gang might purchase that access, or there's a variety of ways that access can then be distributed. And then they move to the the disruption or the monetization phase, right, where they've got access to that organization. They wanna steal something they can sell through IP theft, or they want to, lock you out or, you know, domain lockout, admin lockout, data theft, data encryption. All of these core components are what often make up a ransomware attack right at the end of the day, usually with many forms of malware. And so we're talking about how do we understand this entire life cycle. And what Joe was talking about is, you know, we've been able to, with our interaction with the actors, gain a lot of access to this info stealer part. And if we can detect and see that info stealer event, it can help us to know that the controls haven't stopped them from getting this far. And can we then take the take steps to get ahead of the entrenchment and the disruption phase? And the sooner in this life cycle that we can stop the threat, the the cheaper it is for us to fix it. And so endpoint security is an absolutely critical part of this. Right? You know, regardless of of whether spy cloud sees that info stealer, you need this endpoint security solution to help you try to detect the entry, detect the reconnaissance phase, detect the entrenchment phase, and then stop a ransomware. I know we have a lot of endpoint security products and EDR products now. They have tools to stop the actual encryption activities. All those things are critical. And like I said earlier, the sooner that you can detect it, if you can detect it at entry and stop that phish from being successful, well, you're stopping the rest of this life cycle. You're protecting your business from that damage. So all of that is really important. But, nonetheless, no security solution is foolproof. Right? There are mechanisms. It's a as as Joe said, it's a cat mouse game. The actors are always working against us. They are always they themselves are installing the popular EDRs. They are finding ways to get around them or to suspend them. I know when I spent a lot of time in incident response, the first thing we would see with these these, these attacks would be that they would go after immediately whatever the EDR was and take steps to disable those processes or to find that registry configuration that would make it so that, signatures got turned off or they would take whatever steps they could to somehow limit that that that technology, and that game is only escalating. It's not it's not getting simpler. And so what can we do with the kinds of things we've been talking about today? Where can we apply knowledge of an info stealer event? And so in that recon phase, you know, as you see on your picture here, so we have the attack entry. In that recon phase, if a successful info stealer, successful from the actor standpoint, does run and gather that data, that data gets sent to the criminal underground. And then often within minutes, Spy Cloud can gather that information and feed it to our product that we call Compass, which provides malware protection. As soon as we get that data, often within five minutes, we could deliver that to, to our customers through our integrations. And then we have integrations with popular endpoint detection or response platforms such as CrowdStrike, such as Defender. We can immediately take that information, either make your SOC aware, or if configured, we can quarantine that device. And the goal is to take the knowledge that an info stealer did run, run it through the spy cloud compass product, get it to your EDR, give you the ability to take steps before it can reach the entrenchment phase or before it can reach the disruption phase. And the sooner we can figure that out, the more we can protect you from that that eventual disruption. And so why why is this happening? Right? This is a pretty common question of, you know, I I've invested in a very strong EDR solution. I know it's blocking things. I'm getting the alerts. You know, how is this still happening? And the reality is this is happening to all EDR vendors. Like, we we have the data. We can see what's installed on those systems because the logs tell us that no vendor is immune to, you know, to these types of events that that do slip through at times. Why could it happen? We certainly see issues in systems management such as an out of date endpoint software, failure to install security updates, systems sporadically online, or sometimes policy management issues. This is way more common than you might think where something is being interfered with by the endpoint security solution or at least you think it is, and an administrator might turn it off for a little while and then just never get a chance to go back and to reconcile that particular issue, leaving that system vulnerable. That's a very common scenario. I know when I did a lot of IR, that was way too often what was actually happening. But then there's also just the reality that, those actors are always working against the endpoint security solutions. Zero day exploits, do exist. Unpatched vulnerabilities are out there. There are there are always innovations in malware such as memory only malware or specifically EDR targeting malware or polymorphic malware. And I think Joe talked to some of the things. Luma c two has made a business, to finding ways to get around these detection mechanisms. And so all of that fits into a a spy cloud architecture that includes Compass. So the Compass feature set allow us to gain access to these the malware logs that can be connected directly to your domain, and it that information about the infected user along the top can then be used directly to respond to your employee systems or to, other people that have access to your network. That could be directly integrated into your active directory guardian where, sorry, to your Active Directory system through our product called Active Directory Guardian that can automatically take action to reset passwords that are found that that are found through these malware logs that could be used against your enterprise. It can also be integrated with your SIM and your SOAR so that you could take automated actions that are unique to your enterprise. And then on the bottom of the screen, we have this integration with the endpoint detection response system, which we're gonna talk a little more about of how this information can be fed directly into the EDR so that you can then take immediate action in order to protect your enterprise. And so using the Compass product, you can detect unseen infections. We provide you conclusive evidence that there was a malware infection. And it's important to realize that, these infections occur on on enterprise system or enterprise controlled or managed devices that are managed by EDR. But we also often discover infections that occur on unmanaged devices. Maybe an employee went home and had to log in from home due to some critical issue. Well and they didn't realize that their kid's computer was also used to install mods for Minecraft or Fortnite, which provided that opportunity that Joe mentioned for someone to accidentally to you know, not accidentally at all. For Mowers to maliciously put, some type of insert into that package. This is way too common of a case that we see. Your favorite skins on Fortnite are, you know, the thing that cost you your corporate credentials. And then you have things like, you know, password sharing that can make passwords move between people's computers when you log in from multiple places. So all of those things lead to information that ends up getting shared, and those come through unmanaged devices. We cannot resolve those with the EDR because you don't most companies don't have policies that re that require the installation of that EDR on their home computers. But you can at least detect those, and you have conclusive evidence of whether it's an unmanaged device or whether it's a managed device. When it is a managed device, you can also take advantage of automating your response to make sure that that corporate device is protected. And then your goal in all of this is to block that entrenchment phase as early as possible and hopefully to stop ever reaching the disruption phase. And so let me show you what that looks like, when it comes to, our you know, how you can see it in the spy cloud interfaces. And so what I'm showing you here is the spy cloud enterprise protection portal, and, you know, there's a wide variety of features that we could walk through. But today, we're just gonna focus on the Compass set of features where we have this little section here, the Compass compromised device list. And what you'll see when you look at your set of compromised devices is each of these represents an infected computer, that, that gives us information about an infection that happened and all the information that was stolen by whatever that infection is. And let me also say at the get go here that what I'm showing you is sample data. This is data that we create for the purposes of showing how the product works. We're not showing you any sensitive data. If you wanted to specifically see how this could impact your organization, we would love to set up a demo for you. Feel free to reach out. But as we're looking at this sample data, wanna walk through just a quick example of here's a place where we see a computer that was infected that has a name that looks like something I might see in my enterprise. So if I click on that specific one, I can see the types of data that was stolen by this. And let me just just continue to reiterate here. We have no access at all to this computer desktop eighteen ninety six. What we have is access to the information that the bad actors stole about this computer. So we know the system name. We have a little bit of data about the system owner. We can tell it looks like it could be a work computer because it's a Windows ten device. I can then say, well, what's the likelihood that this was actually, you know, fits within my world? And I could see when it was infected, and I could see additional details about the country that it's likely to be in. And down below, I can see the list of applications that that login details were stolen from when they stole the data off of this specific computer. So if I go back to that just to show you another way to view this same type of information, you can also look at this in a graphical form, and this just gives you another way to view that we have a computer that was infected, and we have access to, the list of applications that were accessed by that computer. And you can see often there's there's things that are interesting. The fact that the one login credentials were were, stolen. This hopefully, multifactor authentication was deployed for this enterprise. But even if it was, you just went down to one factor, and, you know, you're depending on that MFA step, to protect you. So you would love to reset those password credentials, which you could do in an automated fashion. And then, you know, you could see the other list of applications. You could see that this user also had a GitHub account. Gives you an opportunity to make sure that all of your applications are in fact managed by your SSO and that you don't have, you know, some credentials slipping out for some type of shadow IT or or access that you may not be aware of. And so this is just a view into we have a computer. It's desktop eighteen ninety six. It does, in fact, appear to be infected or experience an infection moment. And so then you can also see how that would integrate into your endpoint detection. So we offer, as I mentioned before, very straightforward integrations today with CrowdStrike and Defender with more to come. And what you're looking at is the configuration page for our integration with a CrowdStrike deployment that is managing this sample data, the sample environment we call spare factor dot com. And here you can see beyond just basic configuration, the types of things that we can do is that when you have this this configuration enabled, we are always running. We are responding to the detection of new malware events. When we see those, we have the ability to send a daily report to to folks that need to see it. We can also, configure to send notifications at the moment of detection so that what you're really getting is a check between I see a spy cloud event. Does it match to a CrowdStrike managed device? If so, send an email or open a ticket. You can see we support sending tickets into Jira or ServiceNow with more to come. We'd love your feedback on what else we need to add. And then if we see that match, we know there was an infection of that that that could impact or did impact a managed device. We also support automatically isolating those devices when they appear. This is an option that some of our customers are interested in. Many are not quite ready to do that isolation depending on the impact that it has, but that is an option should you need it. And, of course, if you want that, you have to you make you go through a few steps to make sure that we do understand you. You understand the implications of automatically quarantining devices, and most of you have EDRs. You're familiar with this, you know, this conversation. And just to show you what this data could look like, moving to the part where we can show you what is matching between what the spy cloud data looks like and what the CrowdStrike access has. In this part of our configuration, we show you these are the latest compass matches, the data coming from spy cloud. And then down here in this table, we'll show you which ones do map directly to crouch to endpoints that are managed by CrowdStrike. We can see here that desktop eighteen ninety six we were just looking at with a specific username was in fact matched as a managed device. And then I can, you know, I can understand that. A notification would have already been sent. But if I wanted to, I could come in here. I could click that option, and I could say confirm. Please do quarantine that device, and I've now taken a manual step. Of course, you could have done that through CrowdStrike as well if that was your if that was your preference, but we wanted to give you one place to understand it and to respond as quickly as possible. And so at the end of the day, it's a straightforward connection between the data that we have and the ability to respond to it within your own EDR. So I'll stop sharing, turn it back to Joe. Thanks, Damon. Yeah. That's really cool how that works. I'm really impressed with the integration between that and, you know, CrowdStrike. Awesome. Yeah. I wanted to do a little slide here just to kinda go over some things to basically help you with, these threats even if you don't buy our products. This is something we wanted to do just to help everybody. So enterprise tips basically that I have for you are, an advertising threat is quite the the vector here. And it seems like, you know, we had this happen in the past where you had, essentially, maybe in two thousand, you know, eight or so, there was malvertising injected from, you know, ads in ad brokers. But now we've kind of evolved where the actors are stealing, like, AdWords accounts for Google or Bing advertisement accounts, and they are very often putting it in those search bar, essentially searches where they're the top thing for the install of a particular app. And from that standpoint, you definitely want to try to use some sort of ad blocker, and that seems to be like the primary thing that I found in in environments in the last decade or so that really help on this. Also, you definitely want to have your users know where to go to install their applications. They should be basically going to their corporate app store, especially on their corporate machine. They shouldn't be allowed to install random things, just from things that they download from the Internet. Endpoint management solutions can obviously help with this, but, having that known place where where to go or be able to push apps to or official approved apps is very critical because that cuts this off from being an issue. Obviously, as well, if they don't have that particular app in the App Store, they might go and find a pirated version of it. That is also very bad. That's like the number one vector, basically, for these things to get installed for an Infostealers to come along for the ride. And, again, with Infostealers, they just upload that data to a c two. And a lot of times, they don't leave anything behind, and you won't really know that you're infected, especially if they have been ingenious with their deployment where it actually installs something at that same time. It looks like it worked to the end user. The other thing is the holistic identity lens. Basically, if you can have, visibility or as much visibility as possible into their an end user's past, present work, or personal data, this actually helps you. We have a product called, investigations that gives you a deeper dive access into a particular person and what they might use for passwords and things like that. That often is something I found even in my years of do being a sysadmin that comes back to haunt them where they use the same type of password. It's always their dog's name or whatever, and that actually could be used to attack the enterprise. Password hygiene, speaking of which, ensure passwords are not reused and similar with across the enterprise. This is something I keep seeing where, uniqueness is not necessarily enforced at a level where people are having to make a really unique password, and they could just depend different characters onto it. So make sure you do those password policies. And then, of course, MFA. MFA is basically the biggest issue. Security is an onion. You need these layers. Not no single layer is going to solve the issue, but having that extra layer there, I can't tell you how many times I've seen it save people. And then we wanna talk about some of the end user devices and personal devices. Again, pirating is really bad. This is something that I would definitely give education to your users that installing pirated software is almost always going to give you some sort of thing along for the ride. Otherwise, what's the incentive for actors to basically put this stuff together and send it out there? It's basically the number one thing. And, again, installing the ads or through ads is a bad idea. Please try to train users or remember, to understand that in if you search for something in the search bar, because everybody goes and types something, I wanna I want Zoom. Right? Go to the search bar and I type that in. Boom. You get an ad for Zoom install. Well, why not go to the real Zoom site or just type Zoom dot com in? Because that actually is the right way to usually define things. And then, again, as Damon was already talking about, like, skins for different software or rather games or cheats for games. I've seen in YouTube where different actors have actually put very intricate sort of, sort of, I guess, you could say promotional videos for their malware, where you have the ability to get a cool skin or essentially a cheat for a game, and then they go have you download from, what they call their deployment site or their install site. And, essentially, it's just, again, another malware thing. And then also separating personal and work, don't mix passwords. Once again, I think it's a good hygiene thing for everybody to get kind of in the habit of. Password managers are also pretty good. That's basically something that I usually recommend for everybody from a Hoho user. And, again, ad blockers are very good. Going back and keep driving on that one, I think that even though you do get blocked when you go to certain sites, remember, when people come back and say, oh, I I don't use that because I can't read my news articles. Well, you can make exceptions for that news article site, so don't forget that part of it. And then finally, MFA forever ever. If you can do MFA, do it. It's that extra layer that usually saves you. Wonderful. Okay. But we have some time for some live q and a. A few questions came in. There were some issues we're seeing in the demo on the Zoom video. So we'll make sure to send out a recording of the sessions so I can see the spy cloud demo in action with Compass and the endpoint protection integration. So go ahead and please ask your q and a. We have time with Joe and Damon, but there's two that came in. And the first one be for you, Joe. More about the evolution of info stealers and this cat and mouse paradigm. So how would that impact future prevention strategies if the technology is always evolving? So the Infosteeler, community or the these particular types of criminal ecosystems are usually trading secrets amongst themselves in order to get around any endpoints like Damon was referencing. So you really need a layered solution, and you need basically an idea that you will catch certain things at certain times, but you want to also be able to monitor and actually do your own recon instead of them doing recon on you. And, essentially, that's where we try to position ourselves to layer in there to be that check to prevent, those unique things that they basically come up with in the back end or trade amongst themselves from actually making it successful into your environment. This way, if they do get in, now we can actually tell you about it, and and you'd probably be able to go back and figure out why and then plug the hole. A few more live questions are coming in for Damon and Joe. More about infostealers. Any more tips for enhancing prevention and early detection? And then, some information about how to actually triage when you get an alert from your EDR that an infostealer is present. So as far as tips for best practices, I'm interested in your thoughts too, Joe. I mean, I think the reality is enabling your EDR to be as draconian and strict as possible, the less likely you will be to install malware. I mean, we all live in a in a company, and we all, you know, face the restrictions where the companies won't let us install software packages or run macros and those types of things. The more you can, you know, constrain what they're allowed to install, the better. And, you know, sir well, the better from that perspective. I can't, you know, I can't comment on the complaints you're going to get from, you know, from your users because we all face that too. You're also you know, the more that you can, kinda make sure that you're keeping up with the the updates and that you're responding very critically to any alerts from your centralized control that a system has been taken out of band. Right? I mean, I've I've I know from my experiences, I mentioned I've done a little IR. There was usually an alert that system x y z stopped responding to heartbeats from the centralized control of the EDR, and there wasn't necessarily a playbook to to deal with that, right, or to understand how to manage that. So things like that, really give you an opportunity to know that something something is amiss. It also means you're responding to a lot of things, like they went to a weird hotel and the Internet CO service sucked. And so, you know, there's a little bit of downside with with those as well. Any other thoughts there, Jim? Yeah. I I think, actually, you're definitely on the right track with everything there because the more you monitor the situation, you kinda get a pulse for things, and you want to use the, basically, the filtering in in your seam or sore in order to essentially get an idea of what really matters and what doesn't. Everything is gonna require tuning, but that's where the expertise comes in, and that's where the humans come in to be able to help with the automation to find the unique things, things that are novel, things that are out of the ordinary, because there's always gonna be what I call confirmation errors. Absolutely. And then to the the second part of that question, what are the best steps to triage and if a stealer threat that's been alerted by, by the EDR? I think we recommend you quarantine immediately. And then I think that usually, the next steps we would recommend are the same next steps that your EDR vendor is going to give you. Quarantine that device, scan for additional malware, look for the things, the indicators. Often, we see an Infos dealer will run and then delete itself, and leave no trace that it was ever there. But, yeah, that's hard to tell the difference between that and a very good maliciously hidden, piece. And so what you'll have to piece of malware. So what you'll have to do is, you know, you'll get to the point where you've run all the tools and you've made sure that there's nothing there. We always we always recommend that you, of course, you have cleaned the system. If you can go to a full fully clean system, that is recommended as well. But then you do need to take the next next steps, which are understanding the things that were stolen by that by that info stealer, making sure you've reset all the related passwords, make sure that if they stole things like Coinbase seed phrases or any other tokens that, yeah, that are that are in there, that you've reset those and that you've also reset session cookies, that could be used to access all of your enterprise accounts as well. So all of those are great steps. There's automation that could be added for many of those, for many of those issues, to help you do that in an auto to do that quickly. Yeah. I I also want to add in. You can also leverage things, like network access control. If you actually have them on your campus, you can follow the OSI model. And what I always do is start at the physical level. If I can, I'll just shut the port off. And that way, I know they're not gonna be talking anymore. But I would also do other things too. Like, if they're outside the network, then I would revoke all their cookies, and all their logins would change and immediately be locked. So there's things like that that you can do, and you can kinda go up the the level depending on what kind of controls you have available. We have a few more questions. Damon, you mentioned cookies, and, this might ask, what are you seeing in terms of the amount of stolen cookies and stolen passwords and how they're being used by bad actors? Yeah. Excellent question. You know, if you just looked at the proportion of the stolen cookies stolen, versus passwords, it's easily ten x the number of cookies are stolen on a on a given device. And I don't have that specific number, but it's way more than ten x. We're getting on a single device, thousands of cookies are stolen that give a lot of information about that user's behavior as well as, often cookies that can be used to bypass multifactor and to bypass all these these great improvements we made in, passwordless technologies. And so, but I still think so I don't have specific numbers for you, so I'll give you an anecdotal, you know, my view of it. And, Joe, you should offer your opinion as well. Right now, we still see passwords are still the number one vector. Right? They still work way too well. And then social engineering to get through MFA if it's in the way, but there's still so many places where MFA is not implemented, not implemented correctly or fully. Passwords are still the key vector. We'd love to say it's not the case, but, I mean, it's very much the case. Now for things like accessing financial systems and for, you know, very high value targets, we do see the the movement of actors to start using cookies. And so we have one customer that, you know, they reset thirty thousand cookies a month, just alone on the on the knowledge that they have active they found active cookies within their, in that case, consumer facing application, but you could do the same for many enterprise applications. And so we see this as a growing vector. We don't have numbers, good numbers to say whether, you know, what the proportion is of cookie usage and session hijacking is versus, versus credential usage. Joe, did you have more thoughts? Yep. I think, the other thing too is if you have control of how the cookies are issued for your internal enterprise apps, set time to live on them. Make sure that you basically make them expire or become invalid quicker. It may be inconvenient for users in some instances, but it also may save you because sometimes it takes time for the actor to actually figure out what they really have and then actually to bang on it. So if you have it expire before it's actually valid, that still is something that's going to save you in the end. And that's also why the passwords are more effective because peep people basically are looking at the password still as the first thing because it doesn't have that time based sort of thing where it has a time to live. Yeah. And the next couple of questions, Joe, are about, recommended ad blockers. I don't have specific recommendations here. I haven't looked at enough. I just had the one that I use. Do you have specific recommendations? Yep. MuBlock, light origins, is what I tend to use in a lot of cases. And what I do is I turn it up, to the max amount that they have for the support or add other, different lists to it. But pretty much the list that come with the default are pretty good. The only thing that's bad about the the light version of it is that it comes at a lower sort of level. So you there's like a slider where you can turn it up as you click on the icon as you for your extension. And that slider, if you turn it up to the top, it does a really good job, but it starts at, like, the second rung, and that's kinda, and so I I think that, there's a lot of, back and forth with the different, advertisers out there where they're trying to push back on, you know, not being, able to have these sort of things. So, again, you can always click on it, make an exception for that website, and get past it from that. But, definitely, MEW block origins lite is where I bet. Alright. Okay. Wonderful. Well, thanks for joining, Damon and Joe. We appreciate all the knowledge about malware and endpoint protection. We'll send out a recording of the session if you wanna see a bit more about the topics or watch the demo again. But, again, please reach out if you have any more questions about everything we covered today, or you wanna schedule a personalized spy cloud demo that talks more about your organization's data and your own domains. But, otherwise, we're running a a offer for the next few months. So anybody who wants to go ahead and purchase our enterprise protection solution that includes the Compass product that Damon demoed, we're eligible for discount before the end of June. So please reach out with more questions, and thank you both for joining. Thanks, everyone. Appreciate the Thank you. Appreciate your time.
- Video
Minding the Malware Gap – Identity Threat Protection Beyond The Endpoint
This webinar explores the latest malware trends uncovered by our SpyCloud Labs team, and how these insights help security teams enable proactive measures to secure corporate access.
- Video
Accelerate Cybercrime and Identity Threats Investigations
This demo/webinar shows how SpyCloud Investigations revolutionizes your analyst and investigators impact.
Hi! Thanks for joining us! My name is Alex Ash and I’m the Growth Marketing Manager here at SpyCloud. Today we’ll be joined by SpyCloud Labs researchers, Ashley Allocca and Kyla Cardona to discuss The Illicit Chinese "Pantsless Data" Trade, Uncovering Chinese-language actor TTPs for data access, acquisition, and exfiltration. As a refresher, SpyCloud Labs is a focused research group dedicated to uncovering and analyzing the most intricate cybercrime patterns from the criminal underground. They nerd out on all things breach, malware, and threat actor-related – and are hellbent on making the internet a safer place for all. If you want to learn more about SpyCloud Labs, you can visit our website on our resources page - I will post the exact link at the end of our presentation. Okay - a little bit of background on our amazing speakers: Ashley has a background in cyber threat intelligence and holds an M.S. in Cybersecurity from Fordham University. Here at SpyCloud, her research is focused on emerging threats within cybercriminal and illicit communities, Kyla is a U.S. military veteran from the Air Force, Marines, and Army, and holds a BS in Computer Information Systems and multiple cybersecurity certifications. Kyla is a Staff Security Researcher at SpyCloud, with a focus on cyber threats in China and other cybercrimes occurring within deep/dark web illicit communities. Alright, today we will be covering Chinese cybercrime slang terms and keywords, data leaks perspective: western actors vs. Chinese threat actors, Chinese cybercriminals and their TTPs, Chinese data leaks and finally, everyone’s favorite part - the takeaways. And with that, I will hand it off. Thanks, Alex. My name is Ashley Allocca like Alex mentioned, I’m a Security Staff Researcher here at SpyCloud. And we just wanted to start off by quickly defining a few acronyms that will pop up throughout the presentation. The first is TTPs, which stands for tactic, techniques, and procedures, and we will use this phrase to refer to methods we observed by Chinese cybercriminals. APT refers to advanced persistent threat groups, which encompasses state sponsored groups. This presentation will look at Chinese-language cybercriminals who do not have any obvious ties to state-sponsored groups but we just wanted to define that up front. SDK refers to software development kits, and is a tool in the data exfiltration arsenal of these cybercriminals. DPI refers to deep packet inspection, and is both a holistic and invasive tool used to categorize network traffic between end users and telecom companies. Like SDK, DPI is used in data exfiltration efforts. MD5 is a hash function used to encrypt data. In this presentation it will refer to decryption services offered by Chinese-language cybercriminals. SGK which refers to Social Work Libraries, which are functionally data repositories. And we have a couple of slides that will dive into that later on in this presentation. There are words used to describe different elements of the illicit data trade and are specific to public discussions of and advertisements for data in Chinese Telegram channels. We’ll start here with pantsless data. The phrase “pantsless data'' is commonly used in Chinese cybercriminal communities to refer to hacked databases. The origin of this phrase comes from the Chinese homophone for “library dragging”, which is the term used for hacking sites and exfiltrating their data. Library dragging is pronounced tuwow dong kwoo, and it’s homophone tuhwow duwow koozie, translates to “trouser removal” or “to take off one’s pants.” Trouser removal will often refer to the total compromise of an individual’s data or hacking of an entity. There are other iterations of this phrase that include using the Chinese word for “pants,” which sometimes refers to leaked personal information, or using the word “naked” to identify a hacked entity. Other keywords and phrases that are commonly used in the illicit data trade ecosystem include: “Spinach”, which refers to data originating from online gambling, casinos, and to the “chess” industry. Chess is often used to also refer to the lottery and gambling data sets. It is possible that Chinese actors need to use code words or euphemisms, like spinach, when referring to lottery games or online casinos as gambling is illegal in China. The next phrase is “Angels and Demons” which refer to China’s Public Security Bureau, which is their law enforcement entity, or bank employees or individuals affiliated with banks. This phrase highlights the dichotomy of the public opinion of those affiliated with the police and banks, based on their standing in Chinese society. Individual cybercriminals will use this term to refer to either data belonging to the police or financial entities, sort of based on their experience or where they are from. Next is “Red Hat Hackers” and this refers to hackers and cybercriminals who are loyal to the People’s Republic of China. The use of this phrase does not specifically imply an affiliation with state-sponsored actors. Next is “selling dog meat by hanging a sheep’s head” - it's a colloquialism used to refer to data brokers, referring to their deceptive nature. This term may also be used to describe “second hand” or low-quality data, as it may be being passed off as higher value data. And finally we just wanted to point out the use of the English-language phrase “CVV and POS” which is commonly used to advertise or refer to financial data and financial data theft services. So now we’ll take a look at Chinese actors versus their western counterparts. Comparing data leaks between Chinese cybercriminal communities and their western counterparts can help establish an understanding of the inner workings of this illicit data trade ecosystem. Both Chinese-language and western cybercriminals utilize Telegram to illicitly sell, buy, and trade data. However, Chinese cybercriminals are much less likely to repost a specific file when advertising their offerings. This is due to the high value that’s placed upon “real time” data, which is supported by an actor's ability to maintain persistent access to compromised entities. In some channels, actors will leak data samples daily, and they’ll even name the file with that day’s date to highlight the freshness of that data. More information regarding these methods to exfiltrate this data will be explored on subsequent slides. Conversely, in Western channels, databases are generally shared multiple times between channels and actors, with actors incorrectly claiming that a data set originated from them. There is definitely less of an emphasis on first hand, fresh data compared to Chinese channels. Like I had previously mentioned, Chinese channels put a great deal of importance on “real time” data. Depending on the data type and where it originated from, actors can consistently acquire requested data between one and three days from the day their customer placed an order with them. There does not appear to be a similar market within western cybercriminal communities. Finally, like their Western counterparts, Chinese cybercriminals maintain public and searchable data repositories made up of data from publicized breaches. In Chinese communities, these are generally referred to as social work libraries - often abbreviated as SGK. In the West, sites like Search[.]0t[.]rocks offer similar services by aggregating mostly publicly available leaks, and allowing individuals to search for records by various data types. We’ll explore SGKs further in subsequent slides. I will hand it off now to Kyla. Thanks Ashley. I’m Kyla and let’s dive in to talk all about Chinese threat actors! These actors are primarily Chinese-speaking because they use slang terms to refer to data and data exfiltration methods, as well as use Chinese-language emojis in group chats and engagements. They are also deeply concerned about the recent Chinese New Year holiday, as there was a significant decline in data publishing during this time. Some actors also posted “away” messages claiming that they will take a break and start again in the New Year. These Chinese Actors are found on mostly Telegram channels & X, however they also operate on clearnet forums and underground websites, such as vastdata, datahive, free market, royal city and more. Their X accounts are mainly used to advertise their data theft services, with common keywords and hashtags such as SDK, DPI, SMS Hijacking, penetration services, take pants off data, pants removal data, overseas data, and infiltration. These specific methods of exfiltration will be explained later by Ashley. They may also use marketing and telemarketing to refer to their services to obfuscate their true business motive, which is data theft in the illegal data trading industry. Later, we will show you examples of their X accounts, in which they showcase both SDK/DPI data in spreadsheets with redacted information and tend to refer to their Telegram accounts and channels to find more. Chinese Actors have claimed that they use Telegram for privacy purposes as they believe the “Internet police” as they call it, for domestic Chinese platforms, are heavily monitored and controlled. On Telegram, Chinese Actors use similar keywords in their channel descriptions and group chats as those found in Twitter. Some of the Chinese Actors who publish data refer to themselves as black hat hackers, red hat hackers (which means they are loyal to the People’s Republic of China as Ashley mentioned earlier), and dark web hackers (as these are commonly found in their names and channel descriptions). However, not all Chinese cybercriminals self-identify or claim to be hackers. Some people refer to themselves as salesmen, data brokers, or even reptiles (because they use crawler methods to exfiltrate data) and do not claim to provide the penetration services that hackers do. Chinese Actors operate in many ways: they may work individually, have their own teams, or be a part of a data company. The individual operators may engage in data trade with other hackers and also sell data for their own profits. Those that operate in a team have a “sales” team that take orders, usually through Bill of Lading forms, from customers interested in purchasing stolen PII and credentials. Usually, they have a Bill of Lading template for their orders and also have a minimum order, for example of 5,000-10,000 records. The “tech team” are allegedly the people that manage the data access and are experts on technological tools used for data exfiltration and collection. Some Chinese Actors work for quote unquote “companies” that specialize in data exfiltration, collection, packaging and publishing. Analysts at SpyCloud have used social engineering methods to engage with Chinese-speaking threat actors as well as have done extensive research in finding that these Actors are claiming to have insider access to “first-hand” or “real-time” data as Ashley mentioned earlier. Some Telegram channels publish a library list of apps they claim to have access to. This so-called “insider access” could be in the form of backend permissions to apps or websites or have contacts that have direct access to the data. However, if a customer specifies a target that is not on their library list, some Actors are willing to provide penetration services for the target app or website for upwards of $12K per target. Lastly, the Gray/Black Product Industry is a slang term and another name for the illegal data trading industry or data theft industry, which encompasses the entire Chinese cybercriminal ecosystem of data exfiltration, data collection, data sales, and data trading. Let’s take a look at their Telegram channels. On the left is a screenshot of a Telegram channel ran by a Chinese Actor that publishes and sells infiltration data (also known as penetration data), dpi data, and sdk data in the following industries: spinach, lottery, financing, loans, social security, marriage, students, parents, car owners, medical care, air tickets, and domestic and overseas data. On the right is a screenshot of a Telegram channel ran by a Chinese Actor that publishes and sells “real first-hand” operator sdk/dpi/sms data, this means that they are claiming to have insider access to various types of “fresh” data in the following industries: sports, spinach, games, students, medical care, and online shopping. The keyword of “real first hand” operator data reinforces the importance of the “real-time data” to Chinese cybercriminals that Ashley has mentioned earlier. Chinese actors categorize and organize their data differently from Western Actors. Industry-based data is another way to say data that is organized by sector. Usually, this data contains domestic PII. This term is also used interchangeably with “first-hand,” “fresh,” and “real-time” data because of the short time between data extraction and delivery. Actors organize these “data files” by sector to obfuscate the targeted companies and websites, essentially to make it harder for law enforcement officials to track them down so they can maintain access to the victim entity. Ashley will go more in-depth on industry-based data in subsequent slides. Second/Third hand Data refers to data collection from other methods, such as penetration services or hacking tools. CVV/POS Data is a slang term used to refer to foreign financial or credit card data as mentioned earlier. The targets in the Chinese cybercriminal Telegram channels are usually global users. SGK is another term for social work library, or social engineering database. This so-called “library” or “database” is a collection of leaked databases that a hacker or hacker groups have compiled and made searchable for users. Lastly, combolists are also used by Chinese actors. They usually contain email addresses and passwords. With extensive research and testing, analysts at SpyCloud have found that the combolists released from these channels are mostly derived from Collections #1-5. Collections #1-5 is a Megabreach from January 2019, with billions of email addresses and passwords. It was also known as the “breach of breaches” as it was a collection of credentials from numerous websites. Chinese actors tend to repurpose, repackage, and rename these combolists and sort them by country when they publish them. So let’s take a look at some more screenshots. The first screenshot here is a Chinese actor on X offering “operator” SDK and DPI data quote unquote “directly from the source” which often means they will provide first-hand or real-time data and they have “insider access.” The second screenshot is a Chinese Actor on X masking their data theft services by using the phrase “telemarketing data.” However, they continue to use other similar phrases to Chinese Actors, such as “first-hand accurate data” and also offer SDK, DPI, MD5, and SMS hijacking services. Ashley will take a closer look at these services in the next slide. The third screenshot you see here is a Chinese channel on Telegram who refers to themselves as an “overseas data professional penetration master team” claiming to have “many years of penetration experience.” They also claim to focus on overseas markets, global investors, currency circles, overseas Chinese data, gambling, shopping and all other data resources. The fourth screenshot is a Chinese actor on X offering SDK, DPI, SMS Hijacking, penetration data extraction and various types of “pants removal” which again means for a hacker to invade a target website or app and steal all users’ information and the database. I will now hand it off to Ashley. Thanks Kyla. So we touched on some of these methods of exfiltration already, so now we’ll get a bit more into the weeds. The first method we’re going to take a look at are SMS-focused attacks. SMS-focused attacks can include SMS hijacking, smishing, SMS reply attacks, and SMS sniffing attacks. These attacks are sometimes coupled with various social engineering techniques in order to trick victims into disclosing sensitive information. For example, in SMS sniffing attacks, actors may use pseudo base stations, which are akin to mini cellular towers, but leveraged for malicious purposes, in order to intercept data. These pseudo base stations can also be used to disseminate smishing messages with malicious links that also lead to further data collection. DPI - the next method, like we had mentioned in the beginning of the presentation stands for Deep Packet Inspection, and it’s a legitimately used tool by telecom companies to manage network traffic. DPI is holistic and invasive, like we mentioned, so it can accurately look at network traffic in order to best identify and categorize it. Threat actors who claim to have direct access, sometimes through signed contracts with telecom providers, perform data collection when users access a website/app on the network of a Chinese telecom provider. Details of these alleged signed contracts have not been observed publicly at this time, or have not been made public at this time, so the inner workings of these partnerships are unclear. Leaked DPI databases tend to include sensitive information like phone numbers, location information, IP addresses, and URLs. The third method of data exfiltration we’ll take a look at includes the use of Software Development Kits. Software development kits (SDKs) are legitimate packages of software tools bundled together to be used by app developers. SDKs are often built separately from the applications themselves, leaving room for malicious actors to produce their own SDKs to shop around to developers. These Chinese cybercriminals have been observed advertising their SDK data with “t+1” and “t+2” attributes. These attributes likely indicate the amount of time in days after the initial leak date (t) that the buyer will receive their order of the exfiltrated data via SDK exfiltration methods. SDK is considered one of the least accurate and least timely exfiltration methods. This could in part be due to various reasons like the fact that end users may not opt to share PII with an app at all, or they may knowingly input false information to protect their identity. This will obviously impact the fidelity of the exfiltrated information, which data brokers understand. SDK data also most likely passes through several hands before getting to the end customer, which further dilutes the timeliness and accuracy of this data. Additionally, actors may be poisoning and repackaging open source SDKs with vulnerabile or malicious components, which would allow them to maintain access to the SDK but it could also lead to supply chain attacks, as dev tools do persist as an attack vector with supply chain attacks. SDK data may include phone numbers, genders, ages, and location information, and a lot of SDK data tends to be domestic PII of Chinese citizens. The fourth method of exfiltration is referred to as MD5. Although actors claim to provide already desensitized and unhashed data, they can also provide decryption services if a customer has procured hashed data, ostensibly most likely from another source. This is another way that they can make data available through their de-hashing services. They may also advertise their MD5 services as an add-on to their data exfiltration. And finally: penetration services. Penetration services refer to data that is procured using third-party hacking methods. Actors will target vulnerabilities in applications or websites they do not otherwise have access to. Kyla will cover more on these services later on in this presentation. So here we have two examples of what this exfiltrated data looks like, and these files have all been publicly shared in Chinese-language Telegram channels. So the first screenshot is a file called “Malaysia Loan,” and includes sensitive data like applicant names, email addresses, and gross incomes. This database also includes browser information and IP addresses. Based on the information collected, it is possible that this information was exfiltrated using DPI methods, however this has not been confirmed by the original poster. You can see here under the bank name column that it includes the names of several Malaysian banks so it’s possible that this data was collected while individuals were attempting to connect to the websites of these banks. The second screenshot is from a sample file entitled, “China Bank.” This data includes names, unspecified certificate numbers (which have been obfuscated), genders, birth dates, location information, phone numbers, and card numbers. The original poster of this data did not publicly confirm the exfiltration method, though it appears it could have been collected using SDK methods. This top screen shot is called, “South Korea PII,” so while it appears this is called “South Korea PII,” it appears that the location information is actually based in Singapore, which may indicate that this is data of Singapore-based users, possibly of a South Korean app or website. Like we’ve been mentioning, these files are often named something ambiguous in order for these actors to maintain access to the files. And the final screenshot at the bottom exemplifies what a sample file looks like posted on Telegram. This sample is allegedly of data from China’s Provident Fund. The poster of this sample alleges that they can obtain provident fund data from different regions in China. This data was likely collected using some sort of first-hand exfiltration method. Like Kyla mentioned, actors will target certain industries or entities in order to extract specific data types. While some actors specifically target overseas data, much of the observable targeting results in the exfiltration of domestic Chinese data. So the first screenshot to the left shows a file ambiguously called “advanced units - sample” and contains valuable data types, including full names, phone numbers, national ID numbers, ages, and physical addresses. The second screenshot is a sample file called, “Chinese Orders.” Order and product information are also commonly targeted, as they can include sensitive information like shipping addresses, phone numbers, and shipping numbers. Data brokers and their customers will additionally seek out PII like email addresses, usernames, passwords, messaging app accounts, job titles, salary and company information, device information and location information. Some of the data types may have less value on their own, but become increasingly more valuable combined with other data types. First-hand data is regarded as the most accurate data type among Chinese-language threat actors. First-hand data tends to be broken down by industry and is collected generally via SMS, SDK and DPI methods. Chinese cybercriminals tend to name their samples and breach files by sector, and will also use the phrase “industry data” or “industry base data” when referring to these types of offerings on Telegram These offerings can include: online shopping data, online loan information, insurance information, including medical insurance information from the Chinese Social Security System, education information, including details on students,their parents, teachers, and even exams. Data from China Provident Fund and housing fund, like we saw on the last slide about the China Provident Fund and finally, this can include financial data from banking apps or internal bank employees. This data, as previously mentioned, is often referred to as “angel/demon” data. On the slide is a screenshot of a sample file shared on Telegram. The file is called “vietnam bank loan numbers”, and is representative of how similar data sets are advertised. It might include a location, a sector - it’s pretty vague nonetheless. And I will kick it back over to Kyla. Thanks Ashley. So Chinese actors use the term “penetration services” or “infiltration services,” to describe the data they have exfiltrated using hacking methods. But they also offer it as a service for apps or websites requested by customers that they already don’t have access to. A few penetration tools that these actors claim to use are crawlers, fraudulent (trojanized) applications, scripting tools, SQL injection, and phishing kits. They usually use these terms to describe their method of exfiltration for overseas or foreign data files. After careful observation by analysts at SpyCloud, there are times when the overseas or foreign data is unique to the Chinese Actor’s platform or channel, but there are other times when they are originating from a Western Actors’ platform. This means that they do repost data files from Western actors' platforms, so when this happens, the Chinese actors can repost the file or repost, and reduce them in size, to sell the full file for profit. After extensive research and engagements with Chinese Actors, it is important to note that these Actors find the least amount of confidence in this type of data collection method as they believe the data can be forged and altered, and it is usually not extracted in near real time (such as when compared to their other data collection methods that Ashley mentioned earlier). Additionally, second-hand/third-hand data also refers to data that has been pre-parsed and organized by Chinese actors, as this type of data is not usually found in its raw format. Let’s take a look at the screenshots here a little closer. On the top is a screenshot of a channel run by a Chinese Actor on Telegram, claiming themselves to be a “hacker data vendor” for overseas and domestic data. They are offering data in the following industries: recruitment and job hunting, car owners, high-tech careers, banks, currency circles, corporate companies, overseas Chinese, dating, and other data resources. On the bottom is a screenshot of a channel ran by Chinese Actor on Telegram advertising their various services - domestic data, bank-wide resources, and penetration data in the following industries: finance, medical care, online loans, financial management, credit cards, SMS hijacking and interception, provident fund, state-owned enterprises, teachers, students, online shopping, and SDK/DPI penetration. As you can see, there is a pattern to what these actors are claiming to provide as their service and what data files they all tend to leak. As previously mentioned by Ashley, CVV/POS is a slang term used to refer to foreign financial or credit card data. The targets in these channels are usually unfortunately global users. Most advertisements from these channels highlight the availability of US and Japan credit cards. Threat Actors also have sources for checking if the credit cards are “LIVE.” However, credit cards that have been validated (meaning they have had a small pre-authorization charge run against it) will cost more than the cards that have not been validated. Credit card data is leaked in various ways by Chinese actors; some with just the financial details, while others publish FULLZ information. Fullz data is a slang term for full information, and is used to describe stolen identities and credit card information. This can include full names, full physical addresses, phone numbers, credit card information, expiration code, and the cvv. Now let’s talk about global targets. Domestic financial material is not popular in this data collection method, as Chinese actors claim that this financial data can usually be exfiltrated through the exfiltration methods of SMS/SDK/DPI that Ashley has mentioned earlier. Additionally, they claim that domestic credit cards generally require more information such as payment passwords and SMS verification codes and even banking information for larger purchases. All in all, they’re just saying that it’s harder to use it for domestic citizens. However, Chinese actors claim that for foreign or overseas credit cards, there is no multi-step verification of passwords or sms verification to make a successful purchase or transaction. They believe that in foreign countries, (in most cases) a card number, name, expiration date, cvv, and zip code is enough to make a purchase (but this usually depends on the payment gateway). Their methods of attack for this type of data collection are credit card sniffing and phishing kits. These phishing kits are shared in private platforms. However, they also have public clearnet websites that they use for phishing TTPs such as cvvboy and haocvv. Let’s look at telegram channels next. CVV/POS data can be posted in Telegram as both downloadable files or in the body of messages in the group chat or channel. If we look at the screenshots here, the top two screenshots shows the data found in the body of the messages posted inside the CVV/POS channels, which include: Credit Card Number, CVV, Expiration Date, Full Name, Zip Code, Phone numbers, Email addresses, Card Type (Credit, Debit), IP address, Phone & Browser Information. The third screenshot shows a downloadable file posted in a Chinese Telegram channel. The fourth screenshot shows the same, but the last screenshot shows the credit card data found inside the file titled 2024.2.6 - the file shows credit card numbers, expiration dates, cvv codes, card type, country, and if the card is live (or active), SGK is a Chinese term for social work library, or social engineering database, as mentioned earlier. Chinese actors create their own centralized repositories of leaked PII, therefore, these repositories consist of data they have sold in the past, or data they have found or exchanged with other hackers. An SGK can be owned by one hacker, and other times it is owned by a group of hackers. Another motivation for hackers to publish data for free is for this purpose - to exchange databases and build these platforms. These libraries require users to register with an email address or username and password. Registered users can search through the dataset for various records, as it contains detailed personal information. The searchable fields include: QQIDs, mobile phone number, ID number, email address, Weibo ID, household registration, and more. Most SGKs offer a tiered access system: free users (meaning users who have registered but have not deposited any funds or bitcoin into their account), are able to run search queries but only receive a limited amount of results or obfuscated results. If the user wants more results, they must be willing to pay. It is important to note that SGK platforms are not only another money-making scheme for Chinese actors, but they also enable other Chinese actors to collect relational data to perpetuate other types of fraud and cybercrime, such as doxing, support phishing campaigns, social engineering, malicious marketing, identity theft and financial theft. These SGK libraries can be found on clearnet websites, underground websites, Telegram channels, and Telegram bots. For Telegram, there are two types of channels: the first is an SGK telegram bot where a person run search queries, the second is a channel that contains forwarded search queries from SGK bots, and these channels posts PII in the body of the Telegram messages. Let’s take a closer look at the screenshots of the various SGK platforms. The screenshot on the far left is a SGK telegram channel message that was forwarded from a SGK Telegram bot, The fields in the example post are the following: name, ID number, telephone, mobile phone location and service provider, date of birth, nationality, gender, landline number. As you can see that is very detailed information on individuals. The screenshot with multiple links on the far right is a clearnet SGK platform that leads to various websites for different search queries, such as household registration, delivery information, WeChat and Weibo information The screenshot with the text ‘Privacy is Dead - get over it’ is a clearnet SGK platform with searchable fields such as QQ ID, phone number, ID number, email address, and Weibo IDs. The screenshot on the very bottom is a clearnet SGK platform where you can search using the following fields: QQ ID, mobile phone, password, email address, mobile phone number, ID card, name, Weibo UID, and also specify if it is a comprehensive query or a group relations one. As you can see The Chinese Cybercrime Ecosystem is unique and different from that of the Western ecosystem: Western platforms are missing a substantial amount of data leaks from Chinese platforms, for both domestic Chinese data and overseas/foreign data that Chinese actors have targeted themselves. Chinese Threat Actors use generic names for their data leaks and organize them based on industries. Their purposes for this tactic is 1) to obfuscate the target entities, 2) to make it harder for law enforcement officials to find the data and then track them, and 3) to enable them to maintain access to the data. As Ashley mentioned earlier, Chinese cybercrime actors prefer fresh, first-hand, real-time data extracted from the source, or as close to the source as they can get. This type of data is of higher value and accuracy to Chinese actors, rather than data extracted from penetration services and hacking tools, which they find of low confidence, value, and accuracy. Chinese Actors publish files of all sizes, as “real-time data” can have a small or big range in the number of records, depending on the time of extraction. Some actors purposely reduce the file size and publish sample files as their “proof” or “vouch” that their data theft services are credible, with the ultimate goal of selling the full size data file, Other Chinese actors post full-sized files for data exchange and other malicious purposes. The data that analysts at SpyCloud are recapturing from these public and private Chinese cybercriminal platforms are tangible and actionable. They contain sensitive personal and financial information, not just from individuals residing in China, but also from around the globe. Going to hand it off to Ashley. Thanks Kyla. Before we wrap things up, we wanted to leave you with what we think are a few important takeaways. The first is the threat posed by Chinese illicit data trade, the Chinese cybercriminals access to data and exfiltration of this data extends beyond China. Anybody with a Chinese SIM-card that connects to a telecom provider is vulnerable, so this could extend to tourists in the country who get a Chinese SIM-card to put into their phone to have better connectivity throughout their travels. Additionally anybody that has downloaded an app with a malicious SDK is vulnerable, and the use of second-data and penetration services also extends this threat beyond China. The second point that we’d like to drive home is that illicit data trade occurs beyond Telegram, so while our research for this specific presentation honed in on Telegram and X-based cybercriminals, and their breaches, the Chinese illicit data trade extends to both clearnet and tour-based forums and markets. The third point we’d like to leave you with is whether these Chinese cybercriminals are connected to known APT groups. When people hear about Chinese cybercrime the assumption generally tends to be that a state-sponsored group is involved, however, the long and short of it is that we are not entirely sure whether there is a connection between these Chinese cybercriminals that we’ve discussed in this presentation and APT groups, although there is really no overt indication that these groups are affiliated or connected in any way. Additionally the primary motivation of these Telegram actors appears to be financial, whereas APT groups are primarily motivated by espionage. And finally, is the strong emphasis on real-time data. What is perhaps one of the most material differences between the Chinese illicit data trade and the Western data leak market is the emphasis on real-time data. It exhibits that these cybercriminals have consistent access, seemingly vast amounts of sensitive data, and they prioritize timeliness and accuracy of this data. No such prioritization of this data is as obviously apparent in Western cybercriminal communities so it’s very interesting that there is such a heavy emphasis on this real-time data. And on that note, we’ll conclude our presentation. Awesome, thank you so so much! That was so informative. Thank you for all your hard work and research and thank you for joining us. If you would like to hear more from SpyCloud and SpyCloud Labs, you can email us if you have any questions. You can visit our webpage - as promised, there is the SpyCloud Labs specific webpage. You can sign up for our newsletter - we send it out once a month and it will always include updates and any new SpyCloud Labs research. You can connect with us on X, aka Twitter @spycloudlabs and finally, if you’re curious about what cybercriminals might know about your organization, you can use our free darknet exposure tool at Check Your Exposure, which recently had some updates, so make sure to check that out. And once again, thank you so much for joining us and hopefully we’ll talk soon.
- Video
The Illicit Chinese “Pantsless Data” Trade
Hear from SpyCloud Labs researchers how Chinese cybercriminals are accessing, exfiltrating, and trading vast amounts of PII, with international impact.
Hi, everyone. Welcome to our webinar access granted, the reality of compromised credentials in a passwordless world. Let's get started. Okay. So on this call, we're gonna have Chip Witt, who's our VP of product management, Trevor Hiligloss, our director of security research, and I'm Collette Pameshek, director of product marketing. Today, we're gonna go over what we'll cover. We'll give you some context on who spy cloud is and what our overall mission is focused on. Covering some trends in the password problem, the added layers of authentication, and overall what that path to password list looks like. And then we're gonna go over myth versus reality and go into detail on what you need to know about that landscape, the evolution of passwords, to help you for cyberattacks and essentially fortify your enterprise. So at SpyCloud, we're really focused on solving a big problem. And what it is is that criminals profit from stolen data about your organization, about your customers, and it's a huge problem on a scale that's really hard for teams to digest and manage on a daily basis. Our mission at Spy Cloud is to stop that from happening to really ensure that we equip you and your teams with the information context insights you need to protect your business from malware infections or ransomware attempts and just data breaches by taking our recapture data and turning it around on the criminals. So this enables your teams to act quickly whenever enterprise or customer data is compromised, and you can get ahead of these cyber attacks. And what that looks like, it's really more than just threat intel. With Spy Cloud, what we're looking to do is introduce cybercrime analytics, where all of our products are built around our cyber analytics engine. And it's really there to address the problem set that you encounter when you're trying to use lower or core darkenet data It's not just to learn or gain context, but to really take action and protect your business when it actually matters the most. So our engine here on the left side is where all of that recapture data from all of those layers of the dark matte is collected. It's then curated. It's enriched and analyzed. To drive our products that automate protecting your business so you can take action on that data. And one of the reasons that other vendors don't work with some of that lower or core layer because of its raw data formats. It's overwhelming and it's not even unstructured data. It just comes in a variety of broken databases or broken data structure and often in binary or mixed formats at massive scales. So our engine specializes in figuring out when that raw data is. And how it can be used to protect you, parsing, curating, so then can be ingested into our core data set. So our engine also invests heavily in cracking and analyzing passwords and other PII assets and that results in almost ninety percent of passwords being provided in plain text in our products and access to these data elements allows us to perform analysis and create relational links between those different elements we have producing actionable insights to protect your business. And then if you look on that right side of the slide, This is essentially the output of our engine, the use cases that we enable for enterprises, and our engine is leveraged by our products and the APIs in automated protection use cases. And this includes everything from ransomware protection, account takeover protection, online fraud, and we also support cybercrime investigations with access to our dataset. So overall, Spy Cloud is really focused on leveraging this analytics engine that's built to provide you with the industry's deepest and broadest data set that is collected extremely early in that cycle of crime and that is automated to actively protect your business. So let's dive into the core premise of the webinar. We're gonna kick it off with the past program, which I'm gonna pass over to Chip. Yeah. So the password problem, I I think one of the things that's really interesting about the password problem is it probably more than anything provides really interesting insight into the human condition. One of the things that you see, in terms of this because there's a human portion of it. That's very, very important. There's also the criminal ingenuity focuses on those human weaknesses. Do we talk about when we talk about human weaknesses? Well, first of all, users tend to prioritize ease of use and convenience over security. And so they choose passwords that aren't necessarily the smartest passwords. They're usually linked to things that they know and can remember easily. Even if they have, a recurrent password reset, hoisted upon them as part of, enterprise policy. They tend to pick passwords, and lists of passwords that they can continue to reuse over and over. That's where password reuse comes in is it's not just in the enterprise environment that people tend to reuse those passwords. They have over two hundred online services if they're average people. That they're logging into an authenticating most often, most frequently by way of password. And so remembering passwords, if you change them and make them unique for every distinct site, becomes a problem the headspace can't deal with. Humans aren't don't have that kind of capacity. So you see a seventy two percent password reuse rate is what we saw in breaches over the last year. And that's just because humans typically will reuse passwords across all the sites. My favorite, kinda throwback to remember is the LinkedIn breach. Everybody and their brother got within the LinkedIn breach. They all got the word from LinkedIn to change their passwords, changed their passwords, But what they didn't do is change it on the Facebook, the Twitter, the Instagrams, and all the other services on which they were using that exact same password. Criminals knew this and leveraged it by virtue of just sort of adapting to that particular problem. People also tend to use things that are socially relevant, and that's actually one of the really interesting things. We do a password exposure report every year, and it shows that people use real life events to make commentary on their particular stance on those issues or their favorite sports or entertainers, as part of their password. That's interesting considering that nobody else should know your password. So why would you use that as commentary? But nonetheless, we see this habitually, in human behavior. So very, very important to recognize that password fatigue is inescapable. Because of the pervasiveness of the need for passwords, but for criminals, this this human element is of tremendously high value, and they leverage it at every turn to pull out the low hanging fruit and make good use of that profiting off of that that that particular problem with with people's habits. Okay, guys. So what about password managers? So after hearing that ship, I think that the natural next step is, okay, we'll we'll use a password manager. And just to kinda level set before I can get into this slide, That's fantastic. Password managers are great. Right? With Spike Cloud, big fans, anything that's gonna make it harder for the adversary, impose kind of risk in this case. We'll talk about the consequences later, but that's that's good. Right? Those are good things to start doing. The important thing to note there is it's not foolproof. Right? These these, these things that we come up with to protect our enterprises, to protect ourselves, They're fantastic when used properly, but our research has shown that, a, they're not always used properly. And, b, even when they are used properly. There still are vulnerabilities that exist and need to be managed. So this, you know, up here on the screen, the hundred and eighteen thousand master passwords that we found, couple of things to note. We only looked for eight password managers. There's a lot more than eight password managers out there. So if we had expanded our scope, I expect we would have seen more master passwords. The other thing that this really suggests going back to kind of the human element of this. So you're familiar with how browsers work, right, you you kind of have your in browser password manager, say, you know, you use Google Chrome, use the Google Chrome password manager, or you know, some other application, in its own password manager. And then the the the password managers that we're talking about are the ones that are kinda layered on top of that. So these are these are different companies that reduce, you know, a secured vault, enable you to log in with one password and create randomized passwords for all your different services. The fact that we're seeing those master passwords indicates that there's crossover. Right? So even though people are using these external password managers, that are are themselves quite secure. Recent news might say otherwise, in, in, at least in some cases, but they are secure in in what they do. They do it very well. But once you start overlapping, it almost is like password reuse, right, going back to that last slide. You're using the same master password for, your password manager, but you're also saving that password inside of your browser, or you're using it in your auto or even worse, that master password is something that's used as a regular password for various sites. So the problem that that that that arises is now you're giving the criminals access to that vault. So even if you're doing things like, you know, making randomized passwords, you're using, the the password generation function that's often built into those to generate a different password for each of the logins. If you have that master password as a criminal, that gives me access into that vault, which means it's now even worse. Right? Because even though you're not sharing those passwords across all of those services, they are different. The vault itself is a shared password. Right? By dint of that master password. So by gaining access to that vault, that criminal then has access to basically your entire, you know, online infrastructure. Be that a corporate environment or a or a or a commercial, residential environment. So just because you use password managers, You still have to control for user behavior. And, some of the kind of recommendations there are making sure that that master password is used only as that master password. Right? That shouldn't be anywhere else. The way that I like thinking about this is choose something unique, but complicated. Choose like a sentence or something. Add some special characters in there. So it's a little bit more random, but make it memorable. Then you don't have to write it down. It doesn't have to be something that's used on multiple services. And the other thing is pick one password manager and stick with Right? If you're gonna use a an external password manager, use that. Don't use that and then save your password manager in the browser's built in. Manager. Right? We're crossing different applications. We're widening our risk, vector in doing that. So on that, it feels like password is an issue. Password manager still isn't full proof. So then all those additional added layers that we're looking to either authenticate that identity. Do you guys wanna talk about what that landscape looks like and where it's heading towards passwordless? Yeah. So this is super interesting. And you know, we get questions on this all the time. The the security field is constantly adapting Right. We're we've seen massive changes just over the past five to ten years. And it seems like it it maybe it's even, you know, speeding up in terms of the kinds of that we're coming out with to keep ourselves safe, which is just fantastic. This has kind of caused me to reevaluate the way that I think about this. So now, you know, used to think about credentials as being like a username and a password, right, or maybe your your email address and a password. Authentication now is kind of much more broad, right, authentication, maybe it's like a a time based one time password, right? Everybody's had those sites where you don't really have a password, you just put in your email and it sends you a code and you you log in with that code or, you know, redirects you to a link that's that's time based There's pass there's physical tokens out there. Right? So things that you physically plug into your device and that stores the cryptographic material on that physical token that is used to authenticate. The new thing that has come out recently, and we'll talk about it a little bit in future slides, is fully passwordless. So this uses, like, some combination. So usually, like, biometric fingerprint or a, you know, face ID or something like that, in place of your password. But the the the thing to remember here is it's all on authentication. Right? Regardless of how that session is authenticated. The point from the criminal perspective is that there was a section that has been authenticated. And we'll talk we'll get into kinda why that's really significant now. But, you know, whatever kind of part of of the web that you're looking at on screen here you fall into, just remember that we're talking about authentication, and the and that that access is what's really important here. Okay. So on that note of kind of focusing on the access. That is almost in and of itself a layered experience. Right? So you think about like Let's say I I have a multi factor authentication on my GitHub. Right? So I enter my my username, my password, it prompts me with a multi factor code once I enter all of that, I get a authenticated session. Right? There is a cookie that's created on my device that uniquely identifies that device as having logged into that application, successfully, and that's time bound, and there's importance is there. But you can kind of split that up into multi layers. Right? There's like the the the login attempt itself with that traditional username and password. There's the multi factor attempt. Right, using that, you know, password, multi factor authenticator app or, you know, maybe it's like a a physical token or whatever. And then the last one there is kind of the assignment of that session cookie. Right? And that kinda has the longest life in terms of the actual user activity, even though it's not something you really see, constantly in the background, your browser, every time you you click on a different, you know, link on that website, your browser is constantly communicating with that server. To to verify that it is still authenticated. Otherwise, it's gonna kick you back out to the the login prompt. Right? So the point of that is you know, whether we were talking about the first stage of that, the actual login attempt itself, you know, the the multi factor, whether that can be bypassed or not, the cookie Really, all of this is access, you know, from from from the perspective of the criminal, and and how they talk about this online, you know, they're they're talking about that as a means of So I have access into company x, or I have access into x number of accounts on this service. They don't really care quite honestly what that access is. It might be, an RDP access into a device. Right? It might be an established session that has a very long cookie, a long lived cookie that's going to be active for maybe hours, days, weeks. The point is that that access exists and that it can be used for malicious purposes. And that's really what the criminals are after because that leads to the next phased, whether that next phase is, you know, something malicious, just in and of itself or much more commonly monetization, right, fraud committing, either theft or some other form of, fraud to to gain the criminal money. So if access is how they make profit, what are the odds that with Paskis being another form of access for a user? Criminners are like, wow, that is really complicated. No thanks. I'm good. I have an revenue. What does that look like? Well, yeah, from the beginning of time, that whole access problem, the fundamentals of it haven't changed all that much. What has changed is the mechanics or the technical aspects of it. And so right now, from a a bypass of authentication, there are entire ecosystems that are dedicated to stealing, cookie data. Specific to bypass authentication to, you know, leverage, MFA, trusted device to took and said bypass MFA entirely. That is still a big part of what people are doing all in terms of this, this mechanism. So as we move towards pass key and passwordless, that pro problem doesn't change. There's still going to be cookies that are looking to bypass authentication. So if criminals get access to that, they can Get array rid of the problem entirely and not have to worry about having the the the the token or you having a password or any of that. There's also the the the very real, criminal activity of stealing recovery passwords and, Trevor already spoke a little bit about this is that, a a lot of services home run back to a password to reset that device. So if you lose a device, or you change devices or, something happens that fundamentally breaks or has to be upgraded, you still have a password. Password managers still have a central password. And so that data is still of high value if criminals can find a way to get it. So a lot of those human elements that we were talking about earlier, those bad habits around security hygiene are still leveraged by criminals to get access to probably what could be considered even more sensitive passwords because they unlike to the entire entire castle. And, the third piece here is that, and more in line with what I think Collette was asking just a few ago is as the technology evolves so too do the criminal capabilities, innovation around that, criminals are very smart. They look for low hanging fruit, but as technology changes, that fruit changes. And so they're looking for different things on devices, and we've actually seen evidence of this already, the criminals are beginning to explore ways that they can leverage tokens off of devices and take that information. So actually, rather than me talking about details and high hand wavy motions on this slide, let's go on to the next slide and Trevor, can you give us a little bit more insight into what criminals are actually doing? Yeah. Yeah. And I I think that that last call out is fantastic. Right? In the in the research community, we we we talk a lot about sophistication. That's like a buzzword. Right? The actor sophistication, but it's really I as and I'm guilty of as much as the next guy about talking about sophistication just just to be clear. But but really that's it's kind of a a bit of a logical fallacy. Right? Because while things, you know, we we we on the blue side, we we, build tools, we make it harder for the actors. And you might think kind of just sort of having a have a logical exercise there that it being harder means that only those really sophisticated actors are gonna be able to do But the that's actually wrong because what's gonna happen is the sophisticated actors are going to build tooling that the low sophistication actors are gonna use without having to to to under fully understand it. Right? Just like, you know, we think about cookie bypass. Well, you know, if if I if you were to say like, hey, There's no tools. You need to figure out how to do cookie bypass yourself. I mean, that might be a difficult problem, but that's not the problem. Right? There are, dozens, if not hundreds of open source tools, browser frameworks, you know, that allow you to do that. And it's already built for you you you basically have to have no coding experience whatsoever, just the ability to click a mouse and control v, control c a couple times, control c control v. That's all that it takes. Right? So so reframing this into it's not so much actor sophistication. You know, there is certainly a a a timeline there that maybe that is a bit of lag, but very, very quickly, you know, those actors are going to adopt. What we have, conquer it, and then build tooling for others, to do the same. So I just I just really wanted to touch on that real quick because I think that's an excellent point. The other thing too is it's also an economy. Right? That's that's a fundamental word that I see on this slide. It's not, you know, actors doing things as singletons. They've built an entire economy dedicated to this problem. Totally. Totally. Yeah. Yeah. I mean, the the the cybercrime ecosystem deserves a a a webinar of its own, but know, you you only need to look as far as, like, look at all the mowers of service that we've seen pop over over the past, you know, ten years or so, maybe even closer to nine. But, you know, malware developers that are very good at what they do. Pulling out malware, they're not deploying it. I mean, some of them might be, here and there, but, but really, the the the scheme is that they're some person somewhere is going to build malware and then sell that to other people who are gonna use it. Right? Look at the ransomware affiliate. I mean, there there's so many examples of this It really is the commodification of cybercrime in it. And and it's it is, kind of the, you know, bring it to the masses as as you alluded to. Right? And the same is true really for for the, for this, right, for for kind of going to past scheme limitation. One of my biggest concerns, and again, you just want to stay It's great. Right? It's good that we're doing this. We we need to be introducing these things. This does make it harder for the adversaries. We're not saying don't use pass keys. Right. We're not diminishing the great work that's been done on password list. But it does have some significant issues. And the recovery is one of those significant issues in my opinion. So currently, as it stands today, you know, June of twenty twenty three, this might be different tomorrow. But all of the current implementations still require some use of a password. Right? So whether that's like setting up the account itself, or as the case in what we're talking about here, recovering that passkey. There was a few months ago I listed a podcast where they had the one of the co founders of Ubiqui on. And, the he was asked, I forget his name, but he was asked something along the lines of, you know, So my enterprise has just moved Yubiquis. We've we've bought Yubiquis for all of our employees. What should we do next? Right? And his answer was buy a second Yuboon key. And, you know, obviously, like, there's some bias there clearly. Marketing one zero one. Right. Right. Exactly. Well, the point he was trying to make was, you know, What happens when somebody loses a Yubiquee? I mean, Yubiquee's are fantastic. That's great. But you have to have some means of recovering that authentication. We can't just throw our hands up and say, well, I guess that employee doesn't here anymore. Right? Sorry, Bob. You lost your Yubikey. I hope you have a good luck finding your next job. We still have to find some way to get that person access to their accounts. So what that turns to in a lot of cases is either somebody, some human being, an IT worker that can manually reset, a pass key or maybe they can grant access, using, like, a temporary code or something, or some traditional method of reset. Right? Like, get a code to your email and then respond to an MFA prompt or use your password that you created when you created that account, along with some other function, and then, you know, we'll we'll give you access. We'll we'll renew those tokens. So that itself is a large vulnerability. And again, it goes back to the whole convenience factor. Right? We can't just say, well, Sorry, Bob. Right? We gotta make some way for Bob to get access to his stuff again, and and therein lies the security risk. Is is that kind of fungibility of the security, by by in in in pursuit of convenience. So, the last one here, you know, we've talked about bypassing the authentication altogether. I think we've we've beaten that one to death. Talked about stealing recovery, passwords or, you know, making malicious use of that recovery process altogether. But the physical path keys themselves. Physical, a bit of a misnomer there, but the the pass keys or the private key key, whatever you wanna call it, that generates that pass key. They are also not invulnerable. Right? We're talking about data that is stored somewhere. The private key typically is stored locally on the user's device. Well, even if it's encrypted, it's still able to be stolen. Right? And we've we've seen that. It depends on the implementation, but oftentimes it's encrypted using either master password itself or maybe some other password that the user created. It's on the device. It's prone to being stolen by malware. So going back to your point about criminals being ever adapting, if if a criminal can't bypass or steal a recovery method, well, they're gonna have to steal the passkey. And, I in in in the experience that I have in the years that I've spent in this career field, I I I will say that there's one truth that is self evident amongst all others and that is the criminals are ultimately and infinitely adaptable. So if that is what has to happen, I have absolutely zero doubts that the criminals will find a way to do it and, sell it. Make it a commodity. So with all that contextual education on what's happening in this space, I think it's still fair to make sure we address the myths and go over what that reality looks like, when it comes to passwordless. So one of the first myths is MFA is good enough But the reality is is that MFA is still susceptible to bypass. Chip Trevor, expert advice. Yes. Yeah. Yeah. It's still susceptible to bypass. That's absolutely certain. And and I think we we talked a little bit about this already. Is, you know, one of the the primary ways, that I'm aware of, and Trevor can correct me if I'm wrong here is, info stealing malware is still a great way to basically, harness the power of human fallibility and get access to the information that's going to bypass authentication, including trusted device tokens in form of cookie, and, bypass MFA entirely. Is that is that accurate? Yeah. Yeah. I mean, I think the the the obvious, kind of way to take this is to the authentication app side, but I want folks to remember that it's, you know, while while the authentication app certainly are used, email based MFA, SMS based MFA. I mean, these are things that still exists. Right? And we see time and time again, that they fail. You know, an attacker is oftentimes, gonna target an email account first, for various reasons, but chief amongst them is because they know that they can recover past using email. Right? And and oftentimes it's just email. You don't even need an app. Sim swapping, it's still a problem that we deal with in twenty twenty three, all the time. And SIM swapping often is This is exactly why swim swapping happens in many cases, right, is to to bypass, SMS based authentication. So, it's good. It's better than not having any other factored authentication, of course. But it it truly in this role, today is is not good enough. Yep. It drives that good enough because you hear that often, like, it's good enough for what I need until something bad happens or it's good enough for x y z, What can we do to advise people to kind of escape that false sense of security almost in MFA or just overall in in general for security where good enough isn't really just checking the box good enough going to protect you at all times. Yeah. Anytime I hear MFA I leap to cookies because of one thing that I see is still prevalent in a lot of applications is the you're logging into a web based application that requires MFA good on you. You're doing the right thing. But then you have a little checkbox that says remember this device for x number of days. Oops. Right? That's when the cookie gets written. Right? You check that box and you put in the two FA token and then that device has a token that is remembered for that number of times whatever, you know, like it's fifteen days or thirty days, I think, is really common. The criminal has a way to scoop that information up. They're basically bypassing MFA in that way. And I I leap to that because we talked about, you know, convenience. Convenience always trump's security. And so, that that's one of the it's I don't have to do a semi swap. I don't have to do, any of the more difficult technical challenges to get around it. I can just harvest that information because users are doing it. And to your point, like, what what can enterprises do? I mean, I think Chip's point is is incredibly poignant. Right? Like, limit those cookies time to live as much as you possibly can. It's gonna impose some burden on your, your employees, on your users, of course. But I would humbly submit that the slight bit of burden that is imposed is vastly outweighed by the, risk to all the bad stuff at risk aware and all the other things So that's, like, fantastic. Please do that. Some of the other things you can do is, like, be very considerate of, of, you know, MFA, not all MFA is created I I mentioned email and SMS is the boogeyman. Right? But, you know, really evaluate what you're using for MFA. Can you actually tie that MFA itself to a device? A lot of MFA providers are now actually doing that where you can establish a a trusted relationship between that app and the device. So even if somebody were to be able to steal that seed, or be able to emulate that in some way, it's gonna make it even harder, right, for them to to bypass that. But, you know, the other side of that goes back to the recovery method. So don't just look at how you're doing authentication. Look at how you're doing the recovery. So look at what is that little that little, box below the checkbox that Chip talked about and said I forgot my MFA. Right? I don't have this device present. Like, what are your other options and make sure that those themselves are secure? Because That is not always gonna be used by your user. Right? If the criminal sees that, they go, I have other options to get by. Well, so that ties into the next one. So passwordless, same thing as token based MFA common myth. You know, this is put real eloquently. They ain't the same. So could you guys help educate and drive awareness on some of the key differences between passwordless, pass keys, and token based MFA. I'm just gonna step out of the way and let Trevor dance here because I think that he he is, passionate about this and the difference between the two. Oh, man. Yeah. So I've heard this a lot. And honestly, I this is kind of a this is totally an understandable mistake, I think. We're we're we're we are very much in like a semantic era right now. Where we're talking about how we're talking about things. Right? Everything has like six different names. So somebody calls something a private token. Somebody calls it as seed key. I mean, there's there's so many different ways of referring to this stuff. So a lot of it is just just general misunderstanding of of what these things are. So we're we're talking about token based MFA. We're really we're talking about something that creates a one time use token, meaning it can be used one time on a very specific cider service. Right? It's not like blast this out to, you know, everything you can find in a showdown and see what what lies back with the two hundred. That is a very specific interaction between two things. When we're talking about password list, it's similar in that there is a one time password that's created, but it's different in that you can still have MFA with passwordless. Right? Those two are not mutually or they are rather they are mutually exclusive. You can have both at once. Right? So what passwordless is really is this, a per site or a per service, tokenized relationship where you have a you know, a public public and a private key, to create a one time, one time password for that service and perform that authentication. It doesn't replace the multi factor authentication. It really what it replaces is that, like, we were talking several slides ago. When we talk about the layered approach, it's really a first layer. It's that initial authentication. So they aren't the same. Would it be, and and maybe this is a, a one one step too far, but would it be accurate to say that passwordless is really kind of a next generation client, server security. So back when you had two two certificates. Right? You have a trusted device certificate that deploy on a client, authenticate that device against an application. This is kind of making that kind of easier for the masses. Is it not? Yeah. Yeah. It's like advanced PGP. Yeah. It is. So the I mean, the strength and password list really is it comes from the what is stored publicly. Right? So, like, even if we go back to like a traditional traditional authentication. You've got a database on a server somewhere that stores a list of user credentials, right, which you can have like an email or username, whatever, and then a password. Usually, that's hashed and salted, and we feel pretty comfortable about that depending on how it's hashed and and, you know, the randomness of the salt and other factors. But as we've seen time and time again, just because you do a really good job, Hashing and salting your passwords does not mean that somebody can't crack that. Spicloud. We do that. Right? So, what what what password list does is that that bit of information the user credential that saved on that website is is not a cached password. Right? It's not plain text at all. It is a public key. So it's part of a public and private key pair. So and and it's specific to that site. So if you really think about it, like, if somebody steals that database, it's essentially worthless. Right? Like, that database contains data that can authenticate with itself, but that that's it. Right? You don't have the full you don't have the private key. You can't you can't regenerate that, and you would only be able to use those public keys on the server that you already broke into. So that it that's really the strength of it. Right? It it minimizes the risk to, like, traditional data breaches, but it still is a relationship between a public and private key. So If you have both sides of that, then, you know, the security of that relationship is essentially negated. It it doesn't exist. So it's more secure. So passwords are more secure, but then would you also say that it helps alleviate some of the friction points in that user experience? And how they access their digital lives on a daily basis a little more secure, but then also a little less friction for users with password lists. Yeah. I don't I I would even have a hard time saying it's more secure. I mean, it's a different if it it's a different kind of security, really. It I don't think inherently it is more secure. I guess if you look at it as as that trust relationship between a device and a single site, then you could make that argument. But but really it is for ease of use. I think in my opinion, passwordless, you know, that that is a solution, whether it's flawed or not. To the problem of people wanting convenience, and doing things like using the same password on multiple sites. Right? Passwordless enables you to bypass the passwords altogether. And by default, you're gonna create a new password, right, for each site because it's it's baked in. So it's it's it solves the problem of password reuse, really. Yeah. It does. Yeah. It solves the problem of password reuse. It solves the the problem of, you know, data breaches that we see at least mostly. There's still some other parts to that. But but yeah, but but it's still, you know, we're still talking about authentication going back to what I said earlier, it's still access. Right? And there's all this other stuff that's built around that. It is so much easier. It's almost of almost kinda funny when we talk about it, we spend so much time talking about how, oh, adversaries are gonna be able to steal the pass keys and they're, you know, they can regenerate it locally on their all that is kind of a spud's point. Right? I mean, if if an adversary is at that level, like, the everything else has failed. That's not gonna be this that will never be the first thing. That they try because there's so many other ways to get access to an account that are so much easier, than going through all the pain and the heartache of being able to to do that complicated process. Okay. So going into the next one, forcing user password reset recurrently solves for poor hygiene. Another common myth, but the reality is what have y'all been talking about the last ten slides is convenience always wins. Correct? Well, back in back in my day when dinosaurs roamed the earth, and I was, managing users in a in an IT environment. One of the things that we did was we had, you know, the rules in in Microsoft environments, you can set all sorts of really cool rules, including forcing password complexity, and, forcing the the number of iterations of a password that can be identical. So basically, you don't want somebody to continue to use the same password or even like the next two times that they change their password to use that same password. So you can have memory in that. One of the environments that I worked in that list of passwords that you had to have as unique was twelve passwords long. So over the course of, you know, every thirty to sixty days you had change your password. That was a requirement. People actually had lists of passwords that were twelve passwords long that they knew and were variations of the the root password. That they just iterated through, and they would mark off when they had used them, and would go back to that sheet when it was time to change their password. Forecing user password resets on a regular occurring basis does not solve for the poor hygiene process. It makes it, an opportunity for users to be more creative, but it doesn't solve the problem. Well, and sometimes users aren't even creative. Right? Like, one of the way they would what, like, block number one to act retribution is if you see a date in a somebody's password, just iterate a few times. Go up, go down. You'll probably hit another password. Right? Because, I mean, that's what people do. Like, names of the seasons. Right? Like, if your if your enterprise requires a reset every ninety days, well, maybe my password's gonna Trevor summer twenty twenty two. And then the next, it'll be Trevor fall twenty twenty. Right? Like, I mean, this is what again, users love convenience. It makes sense. We are human beings. It ease or ease of memory, but if if it's easy to remember, it's also easy to guess. And that's the part of the puzzle that oftentimes gets overlooked. Right. So for criminals, they don't care about cookies or sessions. Right? But in reality, stolen cookies, as you guys discuss, earlier are highly valuable, and that's what enables the criminals to that access, access to that already authenticated session. So what do you think everyone should know about cookies and sessions and why it's important to also consider that in this passwordless journey. Yeah. Yeah. These are these are so highly sought after. I mean, when when we're sitting in these these threat actor groups online. We're seeing, you know, actors talking about the things that they're looking for and the things that really are valuable to them. Cookies are consistently top three. If not, the number one. I mean, the actors are so aware that this is that this has become a very common TTP that we see. And we see it in in big attacks. We've seen it in ransomware attacks. We've seen it in the, you know, the lapses stuff that was happening a few months ago. They were using cookies to bypass, the login process altogether. Right? So, you know, this is something that is well known in the criminal communities. They're, like I said earlier, there are open source tools that have been built, they usually call themselves, you know, anonymity browsers or anonymous browsers that will allow you to configure a session to look exactly like your victim. So, you know, I know that this person, this is their display resolution. I know they are running Windows ten Pro at this patch number and their user agent string for their Chrome browser is this. And, you know, you can essentially create an identical profile to the person that you're trying to, emulate. And even even things, you know, like the geo filtering that that a lot of MFA has been doing to try to identify anomalous activity. We see the criminals turning to residential proxies. And and now, you know, I can just put in your zip code and select, you know, uh-uh, a residential proxy near you using the same internet service provider that you are, and then, you know, combining that with a valid cookie and device information, I mean, it's it's it's functionally impossible for, any automated system to detect anomalous logins, using that kind of profile because it functionally looks exactly like, the the trusted device. The dirt the other dirty side of this particular problem is the the fact that even if you do know that session cookies have been stolen and they're in criminals hands, there are Not a hundred percent of applications that have a means of invalidating those sessions. It's a very complicated circuitous process to do that in most cases. And that's a struggle, that a lot of our customers have run into is even if they have that cookie information. If you don't have a means already built into that application, to to invalidate those session tokens, and, deal with that problem. It it it all comes to not that's something I think that developers need to start taking a little bit more seriously as well because it is so pervasive and it is so critical to a authentication piece, having a means to do that. That's easy. Is something that should be part of the process. Yeah. And just not to hijack this thread, but the other the other part of this and something we haven't talked about at all is the other means of authentication. So other than passwordless path, you know, we have API tokens in our environments. Right? We have webhooks that we use. And if you think about what those are, a webhook or API token, really, it is access. It is a means of authentication. You know, if I use my you know, personal access token to my GitHub account, I can go and clone that whatever repository I want down using that token. I don't have to log in. So that token in and of itself is authentication. And the other problem that we see with tokens and webhooks is when we talk about time to live, I mean, sometimes those things never even expire. Right? You actually have to go in and revoke them yourself or as an enterprise. You need to roll your tokens Otherwise, those things basically never expire. And we've all heard the the horror stories of people accidentally, you know, leaving an API key in code that's pushed to a production environment or, you know, accidentally pasting it somewhere and it being found. I mean, these are these are things that we know and criminals know as well. So those those tokens are also highly, highly sought after. For the same reason the cookies are, and and, you know, everything else you can bypass an authentication or or perform a legitimate authentication. So for the last one, with passwordless, it was in May when Google announced that pass keys were available for their consumers for self adoption Nothing for self adoption available and for enterprises to fast follow soon. So the other myth is that users are quick to adopt new technologies. And reality is each tool has its use cases that will continue to persist it. What are some examples either in daily lives or in tech where we've seen? This long lengthy process of adoption and understanding for tech. So my favorite my favorite quote here is it's by mechanic quote. I don't know who this is attributed to. Maybe I hallucinated it like chat EBT, but the ninety percent of problems with the car are directly a result of the tool between the driver's seat and the steering wheel. Right? Yep. It's a human being. So the same is true in tech. You know, we we have the same problems. You can build the most fantastic encryption algorithm that is you know, it's gonna take seventeen billion years for Ashcat to to crack it. User, it it enters password one two three four one time. You're method is gone. Right? So, you know, this is this has been the case for a long time. And I there was a SIS report that came out a few months ago if I recall correctly, you're talking about, you know, the the top the top exploited vulnerabilities in twenty twenty three. And I I think something like two or three of the top five were from twenty twelve. You know? And so, people people won't patch their vulnerable systems in over a decade. You know, I I have a really hard time believing we're gonna get to wide industry adoption of something, that is, you know, requires extra user activity quite honestly. Overnight. Chip, did you have any other thoughts on that? Well, yeah. I mean, I I I think that users are incredibly sensitive to any change that could potentially impact their productivity. And that's one of the reasons that they're resistant to change in in technology and means of doing things authentication and and and It's definitely part of that. I I used to get asked this question about password list and, you know, if that was on the horizon, you know, what what does that mean? And a lot of what we've covered today, has definitely been part of the answer that I used to give, but the example that I gave, was that we still have pencils. Right? You think about we have computers, we have pens, we have all these other means of actually recording information, yet there are specific instances in use cases where pencil is perfectly suitable for a job. And the pencil's been around for a very, very long time. It has never been replaced, although it's had, you know, tools or capabilities that are good, good, replacements for it. And that's true for passwords as well as passwords will continue to be pervasive. They're a fundamental. They're a home root for authentication and access, and that's never gonna go away, regardless of how much technology changes. It's so they were still gonna have that that pockets of places where passwords are still used. On a spectrum of, like, fear or comfort, where do you feel something like this sits in or same thing in the context of at GPT, where people will either embrace, get excited, test it out, and that other spectrum of like, really terrified it's gonna steal my job level. Where does something like this passwordless sit within our current space? Or Yeah. I mean, I'm not super concerned. Honestly, I I think, you know, we we exist kind of on this continuum of security versus convenience. And you can kind of think of this as as a a weighted measure of, like, which which side will will win out and and, you know, that's a really simplistic way of saying that. But really, in my opinion, it's always going to fall on convenience, like convenience, especially anytime we're talking about, like, user experience convenience will always win out. And that doesn't mean that security isn't thought of at all. Like, companies develop a security mind all the time. But if it comes down to, is this something that will you know, inhibit our ability to gain new users. The the answer is always going to lend itself to convenience. So I personally am not all that concerned. I do think it's something that we need to think very critically about, and we should be having these discussions. That's why, you know, I really enjoyed participating these kind of discussions now because I think if we if we talk about this early, we can develop, you know, really, really good ways to address this in the future as we do see adoption. But, definitely, not not afraid that, you know, GPT for is going to all of a sudden become the best researcher in the world and all be, without a job. I I I think that that, users are are very focused on, What they need to get their job done, but I think one of the things that changes the landscape a little bit in terms of the security versus convenience equation is all fundamentally founded on people becoming a little bit more aware of privacy implications, and the security tie in there is, you know, if you're working for a company, you may not immediately think about all the security risks for that company, but the second your personal information and your family is at risk or other sorts of things start to kind of become more pervasive changes your mindset. And that change, you know, where you live literally is, definitely something that expands into the enterprise as you become more understanding and aware of the the security risks of of not, not adopting new ways of doing things and focusing on things. And I think that that's something that's interesting. It's certainly been an evolution that we seen accelerating, over the last several years. Do you think advancements in technology take enough into consideration about human behavior and thinking forward like how will they use this? How will it impact them? Will they be in that kind of whole angle? Or there's still room for innovator's technology vendors to bring more of that human element into how they advance certain areas of security. Well, fundamental element of product management or good product manager, and I should say, is to take into account how people are actually using the technology. Because if you don't understand how people are actually going to be doing something. You can't really build in all the catches, that are gonna become critical to doing it the right way. And that requires conversation. It requires watching users, spending time with users and really understanding that fundamental problem. So I I think that it's a little bit on both sides. Right? I think that there's certainly, you know, great new technologies moving fast and and taking us into the brave new world, but they have to take into account the way people are actually going to use them or maybe even more importantly misuse them. K. So on that note, with everything tied around credentials, really evolving into access. You wanted to check your exposure and see what that looks like. We recently launched check your exposure on spy dot dot spy cloud dot com, free tool. All you have to do is provide your business email and see where your company or your personal risk is at. And we wanted to say thank you for hanging out with us and having this discussion around busting myths in our past with us future, and have a great day.
- Video
Webinar: Access Granted: The reality of compromised credentials in a passwordless world
Explore the evolution of authentication and scrutinize common myths around passwordless technology.
Hello. Thank you so much for joining us. My name is Alex Ash, and I am a growth marketing manager here at SpyCloud. Today, we'll be talking about current challenges SOC teams face and how action driven analytics can unlock automated workflows to help your sock team build the foundation for actionable data to optimize your automation potential. I'm happy to introduce our speakers today, Taylor Coppock, senior product marketing manager, and Chip Witt, senior vice president of product management. And with that, I will hand it off to Taylor for further introductions and to go ahead and get us started. Hi there. Taylor Coppock, senior product marketing manager here at SpyCloud. I'm very excited to talk about this subject matter today, explaining a bit more about how we can help you do more with actionable data. And my name is Chip Witt. I'm a senior VP of product management here at SpyCloud, and I'm really excited to join this conversation with Taylor today to add value, add clarity, and insight from some of the conversations that I've had. So today, we're really in a level set. The current state of affairs we see with with SOC teams and some of the the top challenges we know that are really getting in the way of innovation and driving progress and driving towards automation. But But then we wanna show the goal state of why all this matters. It really shows some applicable ways you can drive towards making use of this data to actually unlock automation for your teams. And, of course, we'll have time for some q and a at the end. So we're gonna jump in right into the current state of affairs to kind of understand what the landscape is that people are operating in and why this topic of automation is so important. So first, we need to talk about how did we get here. As cyberattacks grow in sophistication with evolving tactics, techniques, and procedures and targets, security operations teams are basically they're playing a very crucial role in safeguarding organizations by protecting employee identities and access to corporate data, but it's a difficult job. Today, the evolved role of SOC team is to combat threats specifically designed to evade detection. So they have to be right all the time where the bad guy only has to be right once. In this webinar, we're going to take a deeper look at what you're up against so that we can more clearly understand how to tackle modern SOC challenges. The stats that you're actually seeing on the screen here are actually taken from the Tynes twenty twenty three Voice of the SOC report, and they really tell a really good story here in terms of what SOC teams are dealing with. Sixty three percent of practitioners experience some level of burnout, and that's detrimental to the success of the teams because if you're burnt out, you're not doing a very good job at identifying those threats. Fifty percent of respondents say that their SOC team is understaffed, which means that not only are your existing staff burnt out, they don't have enough relief on the bench to solve the big problems that they're having to face. And then finally, more than eighty percent say their workloads have increased in the past year, and this makes sense from the data that we've seen. And, certainly, it no signs of it stopping anytime soon. So security teams, you're not crazy in feeling like your job is tough. It really is. It's a relentless and sometimes thankless work to safeguard employee digital identities and protect corporate data. So now we'll talk about a bit more of the other challenges that are really hindering these teams from driving towards automation. The first off really is people. Some of the things really stand in the way of security teams really driving towards production is just understanding the employees and consumers that we're working with every day. The first line of defense in enterprise network is actually the people behind the computers. And this human behavior often forces these teams to really divert their attention and their focus to try to prevent attacks happening just by what's happening in our daily lives. Even the best data and the best tooling can't really solve everything that humans are doing. A few things we see that are really getting in the way of the frustration for these SOC teams and blocking automation comes down to passwords. In the end, passwords are still one of the primary ways of authentication and login, and teams know their employees still engage in this risky behavior of reusing passwords that might have already been compromised, reusing passwords across devices, across applications. And it's just difficult for SOC teams to really understand what's actually in use and how much threat actually exists there. Also, just some of the knowledge gaps in just the daily lives of employees and and the consumers, inadvertently, people click on malicious links accidentally or they open up phishing emails or other techniques that, again, provide access for criminals to get access to the to the actual enterprise network and open door for other malware infections and data breaches and just stolen credentials. And, of course, humans still like to prioritize convenience. There's many ways throughout the day that just make it more difficult for security teams to really protect what's happening within their organization. People often sync their work and personal profiles. Now the remote world is very blended of what actually is home and work and life, and this causes more just frustration and challenges for security teams. It's often very common for people to install new applications and new tools that work well for them, and this shadow IT and shadow data adds more hidden risk for security teams. So all in all, even with the proper data and the and the information to everything, of what's happening across your enterprise, auto actional data could help to account for some of these human elements, but you can't replace all the impacts out there. But you can hopefully minimize what this causes for security teams. Now what else is really causing burnout and overwork and getting in the way of security teams driving towards automation? A few things that we fairly common we see across the teams are, first off, dealing with the expanded security perimeter. Now with the new bring your right bring your own device policies and relying on third party hosted apps and services, there's just so much more significant vulnerabilities introduced into the security environment that is getting in the way of teams actually driving towards automation. The focus is getting on getting into visibility of what's actually happening, much less having the time or the data to know how to write script and test the automation needed to protect their employees and their customers. This also leads to a growing attack surface. There's just so much out there that teams don't know if it's actually secure because visibility is still a challenge. According to a HackerOne report, over fifty two percent of organizations don't know how much of this growing attack service is actually secured. So there's several paths for these cyber criminals to attempt to steal this confidential data and target your employees and get after your sensitive I IP. So SOC teams don't really have the necessary insights, much less much much less actionable data to even know the full breadth of their attack surface. We're still trying to get this visibility. And, also, the security teams are stuck in the middle of using other tools that might have been purchased by different teams, like your IT team, your networking, your identity team. And security teams are stuck in the middle trying to make sense of all of this to drive towards automation. But with so many different consoles and tools that try to investigate incidents, the time is spent trying to dive into the gaps even know what is out there and how to respond to it. And these tools are only as good as the data being ingested. And a lot of time is spent actually maintaining and piecing these these tools together into a seamless seamless workflow instead of actually trying to drive towards automation. And finally, just all the noise that's out there with false alarms and poor data quality coming in, teams are spent just fighting fires and doing tedious tasks and responding to things every day that is getting in the way of billing out their automation to protect their employees. And all in all, there's one other main challenge we see out there, and it really comes down to the data. So in talking about the data, one of the things that we actually need to recognize is there's a tremendous reliance on traditional threat intelligence platforms to feed processes. And as SOC teams evolve, they're trying to automate using this information. But the problem is the signal to noise is not significant enough to actually drive automation. It requires human effort to separate out the noise from the true signal and then provide a means to automate the recovery of that. And that's an important aspect there too is that information and indication indications of compromise indicators of compromise as they come in, they don't provide deep level context. They require an analyst to spend some time asking, is this relevant to us? If so, what do we do now? Data is never refined enough to the point of being actually actionable. And actionability is the cornerstone of operation being able to to put it to work in the in the organization. If it's not refined or dependable, you can't you can't automate, and that's what we're we're talking about here. The other thing that's also really interesting about threat intel platforms in general and threat intelligence as it comes in, through those platforms is that it doesn't provide definitive evidence of compromise. It it struggles to provide intelligence that highlights what criminals are actually using today to crack into organizations and do the things that they are doing, and that is a cornerstone to being able to take appropriate action in the environment. So if we talk about the goal state, this is why it's so important to figure out how to effectively implement automation and in what context. What does automation mean? Automation offers a path forward for security leaders to scale, use their limited resources more efficiently, and therefore allow SOC teams to speed time on or spend time on other things that are more meaningful and fulfilling tasks. And this is a great quote again from the the Times twenty twenty three voice of the SOC report is automate the present TDM and security teams can anticipate the threats of tomorrow. That's the intelligence of letting your systems automate things and do the things that they can do well and freeing up that human intelligence to do the things that it does well. And that's what we all hope for as we move towards a brighter tomorrow. I used to spend a lot of time talking about information science, and one of the cornerstones of that is the transition of raw data into information. So if you actually look at data, bits of information floating about, if you think about all of that coming in all in one place, it's not very useful. In order for it to become information, you have to organize that data. And then further, to make that information knowledge, you have to add additional context, additional analysis on top of it to then inform action. And actionability is what we're talking about when we actually are are are talking about automation. One of the context that I think is important to bring up, in in this particular vein is that when we talk about automation, we don't always mean automation all the way through to remediation. I was had the honor of of talking to a bunch of security leaders recently, and one of them was talking about SOAR as a a technology used in most SOCs. And, of course, SOURCE stands for security orchestration, automation, and response. And one of the things that he brought to light is that oftentimes, the SO part of that equation is more important than the ANR. And what he meant was that automation is not just about remediating. Sometimes it's about enriching data so that the analyst can make better decisions. And, again, that requires analysis. It requires actually going all the way through this tree to bring forth knowledge that can drive forward better action, whether that's a machine taking that action and automating that remediation or whether it's automating the enrichment process to inform that human, so that they're making better better decisions. Really good example of where you wouldn't want to automate would be you see something, that indicates a compromise on the CFO presenting something to the board. You wouldn't want a machine making the decision to interrupt that and invalidate credentials or in impact that presentation in any way. So you have to have some intelligence built into how, where, and in what capacity you automate. So when we talk about effective automation, ninety three percent of SOCtINE respondents believe that automation would improve their work life balance. And this is important. Right? Effective automation prevents and protects both proactively and reactively. It maximizes the time that the SOC is spending on things that are important and keeping their productivity up. And, also, by virtue of having process driven response, it improves the reliability. It also allows SOC teams to focus on other tasks such as research, development, and integrations, looking around the corner at the threats of tomorrow, finding new opportunities for the organization to grow and become even more secure. And then, of course, the final piece here, effective automation really lends to happier, less burnout SOC teams, which as we started earlier, that is a big cornerstone of the problems in a lot of organizations. And the idea there is is if you have staff that are happier and less burnt out, you're going to retain them for longer and put them to good work to protect the organization in a more proactive way, over a longer period of time. So we have some good news. There is a way forward. We're gonna show you now you how you can actually drive towards in this smart automation using the right data. So we see three main pillars of the steps you can take towards driving towards automation. You might be in a good spot right now. We're gonna provide a checklist after this talk to help you kind of see where you are right now, perhaps some gaps you can fill and where you wanna go next. But it's really important to focus on the data that you have access to, the type of data, and then how to actually layer that into your workflows. So the first pillar we're gonna cover is, again, the source of your data. Where is this coming from? And more importantly, what is the speed at which you're getting it? After that, it comes down to the different attributes of how you define actionable data. How the data is presented to you and all the information you have within each record is very important to really build the the the trust knowing you can actually spend time building automated workflows to protect your employees and your business. After that, it comes down to layering this actionable data into the tools that you're already using across your teams with these seamless integrations. So we'll talk to these three main pillars to show where you are as you drive towards automation. Fundamental question you may be asking yourself is, would you automate workflows based on old data? Probably not because it's only the current relevant data that's in criminals' hands that's actively being used that is truly actionable. And so when we talk about the dark web or the deep and dark net or however you refer to it, a lot of times people think of it in terms of a unidimensional monolith of information that's out there inaccessible to the normal novice and the criminals are, you know, accessing and leveraging openly and trading. And that's not exactly true. It is true, but it's also it's more complex than just a monolith. In fact, we talked about the problem of threat intelligence platforms earlier. Most of those platforms leverage a lot of open forum data that if you look at the the dark and dark web as a a a gumball, multilayered, the top level, the surface layer is where you're gonna find a lot of commodity data that's publicly traded, and pay spin sites and other sorts of places that can be easily scraped. That's the bulk of tip information that is coming to organizations, and it's very noisy. That's a huge problem. You can't automate based on that. Then you have some inner layers that become a little bit more interesting in terms of value. You have less common datasets available in the middle vetted forums, and these are forums that require access, but are a little bit harder to get to in some contexts, but are not necessarily closed off. They're not truly, truly deep and dark, in the context that people like to think they are. The data is valuable enough to sell. It's high volume collections of automated, information that's it's complex information, but it's possible to actually leverage that information and collect it and use it in various ways. Collection requires knowledge of underground markets, but beyond that, it's it's fairly easily accessible. And it fits in also into, a commodity level of information that's being being shared. And get into the lower and core levels of the deep and dark web. You get into high value data, and stuff that's harder to get access to without people that have, trade craft or, have the secret handshake, get invites, to access that information. And this becomes really interesting information from the standpoint of targeted threats, other sorts of things that you are really caring about in terms of protecting, your organization because it's it's data on breaches, information that is, tied to individual relationships, and, the context of that information. Accessing it requires relationships and reputation, to get access to that information. So, databases are often unique and a very high value at at that lower level. And then in the core level, that's the stuff that's super scary. It's dangerous, communities that are sharing extremely sensitive data, and it requires long standing and intimate relationships, and operational security becomes a really big thing there. So, again, trade craft and getting access. And the reason why I I like to surface these areas is that, it's hard to find organizations that provide security solutions and data at those lower two levels. And so when you're looking for, data to automate, you wanna be using the highest fidelity data that's actually part of what criminals are actively buying, trading, selling, and using in criminal enterprise. Because if you don't have that information, again, it's noisy, and it's not very useful. So, hopefully, you're nodding your head. This isn't making sense. But, again, that's just the source of the data. Regardless of where you get it from, data is still data. In order to actually drive these decisions and drive towards automation, you wanna make sure that it's giving you direction and matter and and and focus on more your business and what you need to do. So some of the foundations that we see are key for defining this actionable data that really helps you build this automation comes down to a few things. The first the first one is all about curation. Is this data actually curated to remove all the noise, prevent alerts, and make sure you're you're responding to alerts that matter to your business? Data by itself is just data. You need access to this information that is machine readable to actually be ingested into your tools. Has it been parsed? Has it been normalized? They validate validate all these billion of data points that could mean something valuable for your business or not. A lot of companies take pride in all the data they publish. There's so much happening, so much noise out there that could be that could matter to your your business, but a lot of it could just be noise. What we see often is just these these duplicate datas that most tips are providing because some some of the information being published is just duplicates that's been repackaged to the combo list that it was already exposed in previous breaches. This doesn't really matter for driving towards automation because you would have taken taken action on it the first time. So it's important to make sure that this curation discards information that has already been duplicated in combo lists, but, also, we know that within the records, there are so many attributes that could be of value. You might want to look for information that's already been discarded that does not contain high value PII that that relates to your employees or consumers, but also you might wanna discard records that don't contain passwords that you couldn't actually drive action on. So that's curation. The next one is all about having information that really has been enriched to provide insights on where to take action. Great. So if you've removed the duplicates, you make sure it's including high value PII and passwords. What's next? It really comes down to the enrichment for both breach records and information gleaned from malware records. On the breach side, you wanna make sure that information you actually ingest and start analyzing really includes all the contextual information you need to help drive your decisions for it to automate. You need things like the breach source, the description, and, of course, the password itself. The more you have about the event will help you decide what you should be automating and what decisions need to be made by your team, both in terms of triaging and priority. Now on the malware side, it's very important to, again, to get get as much context as possible. Everything, not just about the device, but anything that helps you understand the severity and the priority and what the actual full exposure might be to bring risks to your business. You need to understand the date and time of the infection, the IP address, the infection path, any of the target URLs that were included with the malware records, but, of course, as much credentials and cookies and passwords that might have been exposed as well. This is very important to know how to stop malware infections from turning to full blown ransomware events. Now for both breach records and for malware logs, passwords are key. But on the enrichment, look for a source that actually has that is providing these plain text passwords. You don't wanna spend the time actually trying to crack the information yourself to understand what to do with it. To really drive action, really be productive, is to have access to the plain text passwords from the get go so that you can actually move forward with some quick scans to actually see the severity of what's actually exposed in the hands of active employees. The final one is all about correlation. You wanna make sure that the data's been correlated to help you understand the full scope of exposures. We see often that if there's been exposed in email once, it probably appeared across multiple breach records in our dataset. You wanna make sure you can look for the full picture of exposed employee identities to know how many credentials are out there across all the different breaches and malware records so that, again, you can prioritize correctly, triage it, and set up the rules in place for automating appropriately to the extent of the risk to your business and your employees. Now those are a few of the foundations. There's a few more that Chip's gonna let you know about. So one of the things that's kind of interesting in in this story is that you also need to have data that adapts to circumstance. What do we mean by this? Criminals change tactics. As defenses become better in one area, criminals will leverage the next lowest hanging fruit to do their bad stuff. So when you start thinking about what criminals are leveraging to to gain access to identities and, corporate data, a lot of it is hinged on credentials. Right? Usernames, passwords, things that are easily stolen by virtue of hacking a site and stealing a database of users associated with that. And knowing that password reuse is so high, executing on that, leveraging that in a meaningful way to to compromise enterprises. But the tactics change as as the landscape for passwords has changed, and the world has changed quite a bit. Even in the last seven years, it's changed significantly. Now we're actually looking at a world where criminals are leveraging things like cookies or API keys, other, you know, more esoteric things that are still tied to identity but are not tied to identity in the same way that we're used to. So you need to have data that adapts to evolving criminal tactics, and this is incredibly important. This deep understanding of the criminal ecosystem means you're able to stay ahead of evolving threats before they become mainstream, knowing what the criminals are actively doing so that you can stand in front of that and block with insights into stolen session cookies or API keys or password vaults or whatever the next thing is. Finally, does your your data prevent exposures across your supply chain and your VIPs, your executives, your key staff developers, and other sorts of of folks? This is important for automation because it gives insight into third parties for automating their own solutions. You can inform policies, for your partners because as we've seen in several major newsworthy cases that are still unraveling, The the supply chain is a significant source for criminals to leverage to gain access to your enterprise because we're trusting these third parties with access to various things. And if their security situation is not, such that they're addressing threats, that then cascades into your risk, and that's incredibly important to be able to shore that up or at least have visibility into it to have the conversation about how you tier access to data and applications by virtue of those risk factors. And I think that that that kind of segues nicely into automated workflows, in terms of, you know, now you have the foundations in place for actionable data. What's next? Exactly. That's right. So you have the right data, the right data source. Now it's about actually layering this into your workflows with some seamless integrations to actually see the the the output of this automation and really drive towards productivity. So a few of the actual workflows that we we can really see help your help your security teams make more, go across a few different tools you're running across your system. On the directory services side, it all comes down to your identity. Regardless of how you're managing your services on prem, hybrid, or in the cloud, having axe access to this fresh, actionable data helps you actually prevent against next gen threats and keep your employees and consumers safe. Now on the actual data side, we mentioned the need for having this enrichment and these these plaintext patterns available published as soon as you get them. Because it's very important for you to start setting up these automated scans to check how many credentials are actively exposed that are that are actually that are being used by your active employees. This isn't possible if you don't have access to plain text passwords. And following this this practice, we'll help you actually align with some of the latest NIST password guidelines where most most vendors that you're running will let you actually integrate this data into to run scans daily to see how much risk exists out there. You wanna make sure you're using your time to understand the priority of where you should focus your team's effort, not spending manually time seeing how much how much how much risk is associated with your with your customers by looking at the passwords. Now with the right data, you can actually scan to see the threat of what's actually exposed that could be in the hands of the criminals that your employees are using perhaps across multiple systems. But not just scanning to see what's out there. You also wanna make sure you're automating the workflows what happens next. We recommend actually setting up some workflows to go ahead and automatically force a password reset if a match was found. The power comes down to you setting the actual remediation path, but having access to the right data helps you know you can make the decision that if you do see your employees are running something that is compromised or potentially matches something else out there, you wanna make sure you can configure the notifications of letting the your employee know they should, reset their password or go ahead and making the change yourself. Those helps you really prevent any potential gaps from criminals having access to your credentials, It all comes down to what's possible with this actionable data that you can ingest in your systems. To add to that, the Simmons source story is a very strong one as well as oftentimes in organizations, you're already managing log entries events from all sorts of disparate systems in a consolidated place for your SOC to manage. Are you bringing in data related to credential theft, cookie hijacks, any of the information that we've been talking about in terms of some of the data, dynamic or otherwise, to help inform decisions around other events that are happening in your organization. That is incredibly important, not only to identify events as incidents themselves, but to provide enrichment on things that you're seeing so that you can kind of draw correlation between multiple disparate events that by themselves may not look like anything, but combined together can help you automatically draw those correlations and lead towards an orchestration or, an actual remediation event, and that's incredibly important. Part of that too is, source play incredible roles we were talking about earlier, automatically creating playbooks, within your source so that you can actually have that workflow either enrich and enhance an analyst's capabilities or drive it all the way through to remediation because it isn't just in the directory services themselves that you might wanna remediate. You might wanna correlate that with other information and drive that action through systems that are looking at a broader context. So bringing it back to the business value here, again, automation offers a path forward for security leaders to scale, use their limited resources more efficiently, and therefore allow their SOC teams to spend time on other more meaningful and fulfilling tasks. That is incredibly important. So take a breath, measure, optimize your automate automation, and keep improving over time. It isn't a one and done situation. It's a continuous process. You know, life's a journey, not a destination. And in security context, that actually truly applies. It isn't about getting to a particular destination. We wanna be more secure for sure, but it really is about the journey and continuing to improve, leveraging the information data that you have at your disposal to make intelligent decisions and make your team more efficient. So we can't, say all of that without saying this. SpyCloud exists to prevent criminals from benefiting off of the information that they steal. And so we do have a checklist that will be published soon that will help you answer some questions around selecting the right vendor, which we, of course, are biased and think is us. We can certainly help you with your automation. Spy Cloud enterprise protection safeguards employees' digital identities, delivering a solution that continuously monitors for compromised credentials, keeps corporate data safe, and reduces overall enterprise risk. With actionable analysis, security teams can extend automated protection across their organization while optimizing response and remediation efforts for proactive coverage against targeted attacks. And that's an incredible important part of rapid response through seamless automation. Right. The q and a portion of today's presentation. We have a couple of questions here. Let me just get to them. Alright. One of our questions. Automation sounds great, but it is probably naive to think that it is the answer for everything. What can you say about the drawbacks or maybe more specifically the aspects of automation that one should look out for as part of this journey? Chip, I'm gonna throw that to you. Yeah. There are there's a lot of meat on that particular bone. One of the I mean, I I think some of the stuff, related to this is stuff that we talked about in this presentation is that, you have to have data that you rely on or can rely on, that is of high fidelity and is coming from the right places that are really identifying criminal activity in the sense that criminals are actively using trading and, leveraging the information. Because if you're not taking action on that information, it's not pretty pretty useful. But beyond that, automation is one of those things that people are always striving for, but one of the the things that we talked about is that the environment changes. Talked about adaptable data. The same is true for your processes around automation. You have to continually look at the processes that are defining what that automation is and make sure they're still relevant in your organization. Because if you're taking automated action and it's no longer relevant to the types of threats your organization is seeing, it's more noise. Right? It's not very useful at that point. So you do have to go back, circle back periodically, and look at what you've automated, how you've automated it, and are you getting the outcomes you expect from that automation? And if you're not doing that, you're a hundred percent right. It's it's naive to think that it's going to be an answer, certainly for anything at that point if you're not actually doing the right things. So I wanna, dig a little bit deeper into your answer there. How do you make sure that you're getting access to data before it's been monetized or used against you even? Well, that's, again, selecting the right vendors that are diving into that dark net data in the way that I described criminals are actively trading and using for the more sophisticated, quieter attacks. I love things like the mother of all breaches that got announced, and everybody got very excited about that. It opens people's eyes to things that they may and everybody got very excited about that. It opens people's eyes to things that they may not be paying attention to. But the honest truth is those types of information leaks, out in the wild are less damaging than the quieter information that you're only going to get by partnering with a company that is looking at the the underground in a very deep analytical way and analyzing what criminals are actively doing and how they're using the information so that that can be fed into analytics that are servicing you and your decisions around automation. So speaking of which, I've heard that session hijacking has led to several recent high profile breaches. How does that relate to credentials and how we should be looking at our automation plans? Well, there's some interesting stuff there. Right? Criminals no longer hack into networks. They log in. That's been true for quite a while now. They're using, you know, user credentials, usernames, passwords, that sort of thing to just you know, that they're coming across through breaches, etcetera, malware infections, info stealing malware, taking credentials, and just logging it and moving laterally once they get in and doing all sorts of damage. This is, again, getting back to the adaptability piece, this has changed a little bit as its access. Right? Access is the identity piece here. It's not just user credentials. Access is provided through a lot of open doors, including cookies, session hijacking, is is preeminent, and also API key usage, when those get exposed. Cookies are really interesting. Right? The there have been several recent breaches that have occurred, that were directly related to cookies. One major SSO provider, had cookies that were exposed and gave stair step access to admin accounts and customer admin accounts that wound up compromising multiple organizations. Scary stuff. Another story related to cookies as well, was a a CICD platform having having cookies exposed by virtue of a browser sharing information. So Chrome and several other browsers have this capability where regardless of where you're logged in, all of the information from your profile gets shared across multiple machines if you choose to do so. And that includes your cookies, credentials, all sorts of other information. And so if you're doing that sort of sharing from an enterprise machine to maybe a personal machine, or a machine that's less protected for whatever reason, and that machine gets popped with info stealing malware, all of those credentials are stolen. And if you're in the enterprise and you're monitoring that enterprise box, you're gonna be none the wiser. And that's what happened to this organization is those cookies got compromised, and that led to follow on attacks. The the last big newsworthy case related to cookies that, I'm aware of, and it's fairly recent as well, really under underlines the fact that the criminals are using networks and sharing information fairly openly. And one of the big underground networks for ten dollars, they were able criminal was able to buy session cookies for Slack and got access to the communications platform and then basically acted as a, a user and made an IT request that then got them deeper access into the organization. So those sorts of things, they happen. And those are the things that, you know, you need to really be aware of is that, it's not just credentials. You need to be looking at all the means of access to your organization, capturing that information, and then automating remediation to prevent that access, from being leveraged. Amazing. Thank you so much. I think that is all we have time for. So let me just move this out of the way. If you want more, you can check out our web page. You can go to spy cloud dot com and our resources page. We have guides, we have reports such as our recently released identity exposure report, and other helpful resources such as an actionable data checklist that we mentioned in this presentation. You can check out our blog and sign up for a monthly newsletter where we'll just round up all of our most important resources for you, and we can send it right to your inbox. And you can also, check to see if your organization has been exposed to any of that dark net data, at spy cloud dot com slash check your exposure. So thank you again for joining us. Thank you to our speakers, Taylor and Chip, and we'll see you next time.
- Video
Webinar: From Zero to Hero: What Your Security Team Can Unlock with Actionable Data
C is for cookie, the missing ingredient in your Zero Trust recipe. Most organizations are somewhere along a Zero Trust journey, either planning, implementing, or reaping measurable benefits from their efforts, whether they actually call the initiative Zero Trust or not. In this webinar, I'll highlight some common gaps in zero trust policy decisions and share how SpyCloud can help. My name is Chip Witt, and I am the senior VP of product management at SpyCloud. SpyCloud transforms recaptured darknet data to protect businesses from cyberattack. Its products operationalize cybercrime analytics and unique data from breaches, malware infected devices, and other underground sources to produce actionable insights that allow enterprises to proactively prevent ransomware and account takeover, safeguard employee and consumer identities, and investigate cybercrime incidents. To begin, let's look at the core elements of Zero Trust. Here we have a standard architecture diagram that should look familiar to anybody that's been researching Zero Trust. Your endpoints and your identities here on the left are working through your policy engine, which which can have a variety of implementations and Zero Trust architectures. That's really controlling and protecting access and a zero trust way to data applications, your infrastructure, and your network as a whole. Regardless of whether you're using secure access access service edge or layered application protections or whether you have the coolest new architecture around data, you're still relying on your policy engine to make those fine grained access decisions. But one of the fundamental problems we see with Zero Trust implementations is they don't have new information with which to make those decisions. You're supposed to be constantly reevaluating and constantly checking how much you really trust this identity and identifying any issues with the endpoint. But you lack valid dynamic information to feed that policy decision. You need inputs from the outside world to tell you when an identity has been compromised and whether an endpoint or device has been compromised. Those additional endpoints help close the loop in your policy engine's decision making. In short, knowledge of your exposures and what's happening in the dark net relevant to your organization are all critical ingredients to making sure your Zero Trust architecture is providing everything you need for the constant and consistent revalidation of your policies that determine what identities and endpoints should be trusted to have access to your enterprise. Zero Trust is all about making decisions based on the inputs given, and threat intel does not give you time sensitive assets that have specific expiration time frames, and they miss key pieces of data that are close to the crime. Threat intel is essentially just too much data and not enough information. SOC teams are drowning and commoditized threat intel, and security data is basically creating a struggle to turn it into actionable insights. SOC teams want to scale their analysis with automated workflows, but the human effort often required to interpret clunky, sometimes unreliable or low quality threat intel data makes it incredibly difficult. Automating critical workflows, including with Zero Trust policy engine decisions with data you can't completely trust brings potential downstream problems with pulse false positives and broken processes. Analysts are needed to take threat intelligence and answer the questions, is this relevant to us? And if so, what do I do now? Data is never refined enough to go to the point of being actionable. If it's not refined or dependable to the point of being actionable, then you can't automate it either. Threat intelligence doesn't provide definitive evidence of compromise. It struggles to provide the intelligence that highlights what criminals are using day to day and doesn't actually give organizations the ability to figure out how they can prevent those actions in their environments. Additionally, immediate reduction for targeted attacks isn't something you can do with threat intel because you can't see the data quickly enough to discern and analyze it appropriately. Threat intelligence is often retrospective and becomes stale really quickly. Manually configuring and training efforts are not only time consuming and tedious, but inefficient and prone to human error. This reactive approach hinders automation initiatives to prevent attacks. There's been a lot of attention on products to block access from other authentication mechanisms, and the policy engines within your framework are using this information to reevaluate access privilege. But what's missing is what's being used by criminals to actually gain access. It's not just usernames and credentials, but it extends to sessions and API keys. The information within session cookies or credentials that are extremely close to the actual crime need to inform and plug into your policy engine so your overall program can respond to any threats rapidly and efficiently. You certainly still need usernames and credentials to protect your enterprise. You also need access to stolen sessions, stolen API keys, which allow you to use your applications in a very similar way to session cookies, are all key ingredients to effective Zero Trust as a whole. Cookie data is so critical because it has the dangerous potential to completely negate all the hard work you've put into authentication improvements with things like single sign on and multi factor authentication. Even if you're implementing passkeys, criminals aren't giving up and seeding defeat. Instead, criminals have recognized they can go to people's devices and steal the authentication or session cookies. They can then distribute them rapidly to other bad actors, and they can use them to get into your applications, VPN, your enterprise. To have a full Zero Trust solution, you need a better set of cybercrime data coming into your policy engine, and it needs to include an understanding of what's going on from the cookie perspective as well. This isn't just hypothetical either. There are a few recent very high profile attacks that all started with someone taking an unexpired session cookie, gaining access to the environment, escalating privilege in that environment, and then taking it from there to a full scale compromise. Actors are using these techniques, tactics, and procedures constantly, but the real issue is that applications don't have any way to detect this, and nobody knows how to find it within their ecosystem. Some of the interesting attacks, there's a leading identity provider breach. Attackers used session tokens. The employee whose credentials were used had synced their personal browser profile and device with their corporate one. Makes sense. Convenient. The threat actor was able to find the credentials of a service account that was saved to an employee's personal profile after they signed into the profile using their work laptop browser. This allowed attackers to access files related to a hundred and thirty four of the identity and access management's provider's customers. The threat actor used the service account, which had permissions to view and update customer cases, to access the customer support system. Among the files the threat actor accessed were HTTP archive files, which are used for logging a web browser's interaction with a website. These contained additional session tokens. The CICD platform breach, data breach was caused by an info stealer on an employee's laptop that stole a valid 2FA backed SSO session. The malware was not detected by the company's endpoint antivirus program, of course, and the malware was able to execute session cookie theft, enabling the threat actor to impersonate the targeted employee in a remote location and then escalate access to a subset of production systems. Because the targeted employee had privileges to generate production access tokens, the attacker had access and was able to steal from a subset of databases and stores. The global video game company breach, is another interesting one because it really showcases the power of the market and the accessibility of this information. Criminals paid ten dollars for stolen cookies on Genesis, a dark web mark marketplace, to access the corporate communications tool, use social engineering to request new multifactor authentication tokens to get access to the network, and then proceeded to move laterally through the enterprise. The threat actors use the authentication cookies to mimic an already logged in an employee's account and access chat channels and then ultimately tricked an IT support staffer into granting them access to the company's internal network. We are seeing criminals go all in on stolen cookies. SpyCloud recaptured more than twenty billion cookies last year, which speaks to their ubiquity in the criminal underground. This amounts to an average of more than two thousand records per infected device. Our findings paint a pretty clear picture that malware exfiltrated session cookies are high value for criminals, and malicious actors will likely continue to pivot in that direction to sidestep multifactor authentication and passwordless authentication. In twenty twenty three, we also recaptured a total of nearly one point three billion passwords, an eighty one point five percent year over year increase from twenty twenty two. And when looking at password reuse rates when within that pool of data, rates remain incredibly high among users exposed in two or more breaches at seventy four percent despite organizations pushing user awareness and training in recent years. Security decisions, even those tied to important initiatives as critical as Zero Trust, don't happen in a vacuum. Arguments for them have to be made beyond just the security rationale and within the context of the overall business priorities for the organization. Increasingly, boardrooms and executive suites are focused on how initiatives and budget requests for solution fit within their chosen risk management framework. Our take on enabling more informed Zero Trust policy decisions lines up well with this focus on risk management frameworks. While this list is not comprehensive, it sheds light on how to position SpyCloud to meet the criteria for protecting digital identities, upholding session integrity, and securing application access for Zero Trust defined within popular frameworks. We call out alignment with specific sections of the Zero Trust architecture and the NIST cybersecurity framework, sections of the NIST special publication on security and privacy controls for information systems and organizations detailing specifically audit and accountability, program management, and risk assessment, the NIST special publication on digital identity guidelines, including the sections helping inform authenticator assurance levels and, of course, CIS top controls. SpikeCloud offers an approach that's more comprehensive and actionable than traditional threat intelligence, powered by analytics that connect compromised entry points to employee identities and giving security teams a seamless integration to automatically remediate the threat. Spike Cloud enterprise protection is powered by our cybercrime analytics. Recaptured data from all layers of the dark net is collected, curated, enriched, and analyzed to drive our products that automate protecting your business and help you take action to protect your business when it matters most. Our solutions include all the insights needed to detect exposure, prevent targeted attacks, and rapidly respond for any remediation efforts to fully protect employees' identities. Why are we different? We have data closer to the crime, and it's unique. And through cybercrime analytics, we produce actionable intelligence. We provide everything you need for the constant and consistent revalidation of your Zero Trust policy decisions. SpyCloud is able to provide real evidence of compromise without unnecessary alerts or false positives. Knowledge of the severity of employee and consumer exposure helps identify previously unknown risks to the business. Stopping criminals requires a new approach, even if you're implementing Zero Trust When getting ahead means taking swift action, distilled answers are essential, and that is the promise of cybercrime analytics. You must prioritize targeted and emerging forms of account takeover and ransomware prevention to dynamically enforce the right policy decisions. But to do so, you need to be able to act on what criminals have in hand before they do. Here we see a screenshot of SpyCloud enterprise protection. Through a malware log SpyCloud collects, we can see compromised assets associated with your company's employees, including infected devices, application credentials, and session cookies, all stolen by a criminal through Infostealing malware. Ongoing monitoring for this sort of information helps shore up Zero Trust policy decision gaps while also providing a clear path to risk mitigation. Our solution helps you respond quickly and effectively to minimize the risk of any exposure, and we help optimize your existing security spend without dramatically increasing the operational overhead on your security team. That's all possible with our automated workflows. Our customers start with SpyCloud to protect their employee identities with our robust integration with Active Directory, and that runs daily scans to prevent employees from choosing weak or exposed passwords. If we do find compromised data, you can automatically reset passwords for active employees and disable high risk accounts. Our exhaustive set of integrations include SIM and SOAR landscape with support for the most major players that your teams are already running like Splunk, Sentinel, Chronicle, and we publish breach and malware records as a high fidelity alert to your SIEM so your teams prioritize and escalate alerts to the appropriate team members. Our data automation gives you the context of identity exposure that goes beyond the simple exact employee email match. Our integrations with source are really interesting and dynamic. They create daily incidents for high priority breach exposure and malware infections and allow you to automate the time consuming piece of investigating raw data and push incidents that need attention, rather than creating noise. We publish all the details of the record that we have available, and each of our playbooks that we include include a starting point for you to not only get the information you need, but to be able to leverage that information for additional remediation for the entire exposed identity. It's not just wiping the device. It's looking beyond and remediating applications and the accounts that are associated with them. Accelerate your Zero Trust initiatives. SpyCloud helps you enable adherence to regulatory and compliance requirements so that you maintain business productivity, helps you free up resources by preventing targeted cyberattacks without adding additional headcount or overburdening existing resources. And SpyCloud also helps you automate protection from employee identity exposures to prevent costly cyberattacks. Why do customers generally choose SpyCloud to protect their employee identities? Well, first, the power of our recaptured data is un unparalleled. We provide context rich data beyond the breadth and depth of threat intel providers. We make sure that the data is highly relevant to your organization, and we capture and publish dark web data faster than competitors to shorten the time period between exposures and threats to so you can act before the criminals can. We take this data and create action driven analytics through alerts that are valuable to your teams for shortening the investigation time, helping them to avoid having to manually correlate or deduplicate data so that they are focused on credentials that truly pose a risk to the organization. Spy SpyCloud scales with the threat landscape through a growing amount of recaptured data we publish daily and through extensive integrations across multiple categories of secured security tools that support existing automated workflows that are already in use in your environment. You're not forced to rip and replace your existing security framework out either. Customers are able to freely layer SpyCloud analytics into existing practices for coordinated response to maximize impact with minimal over organizational overhead. SpyCloud enhances critical aspects of your security defenses to safeguard your sensitive data against the next generation of cyberattacks, but don't just take my word for it. To get a glimpse into the power of cybercrime analytics, start by checking your enterprise exposure. We'll reveal real time insights on exposed employee credentials that are in the hands of criminals, and we'll share those results with you, including any previously unknown exposures that SpyCloud illuminates in a custom report. All you have to do is provide your business email and see the details of your company's risk. This custom exposure report that you'll receive will include an overall security risk score for your business based on SpyCloud data, taking into account malware infections and plaintext passwords, account of malware infected records associated with employee email addresses, which may indicate active infections and exposed active session cookies, insights into third party breach records, exposed executives and VIP credentials, estimated password reuse, and PII exposure for your employees, and finally, specific breach and malware sources with details on when SpyCloud published the data to basically identify customers and compromised data types. I sincerely hope you found this session valuable. Thank you very much for your time.
- Video
Webinar: C is for Cookie: The Missing Ingredient in your Zero Trust Recipe
Learn how to address a common Zero Trust implementation gap that is leaving organizations vulnerable to targeted attacks: users’ stolen session cookies.
Thank you so much for taking the time to join us today. My name is Alex Ash, and I'm the growth marketing manager here at SpyCloud. We here at SpyCloud keep a tight pulse on darknet activity to understand how stolen data exposes organizations and consumers to cybercrimes like account takeover, session hijacking, fraud, and ransomware. So today we'll be talking about key findings from our twenty twenty four Identity Exposure Report. Alright, let's go ahead and get started. Okay. So first, just a quick agenda. We'll be giving a little bit more context on why we do this report and why it matters. Next up, welcome to the showdown. Data stolen by by cybercriminals and traded between bad actors have continued to scale dramatically each year. Case in point, Spy Cloud's total collection of recapture data has grown to more than forty three point seven billion distinct identity records. So here we'll do a deep dive into our most important findings and observations and how NextGen identity attacks are forcing us to reevaluate how we define our digital identity. From there we'll continue our adventure into other important trends. Next on our journey is how to level up the cheat codes, if you will, for how to stay ahead of cybercriminals and other risks. And finally, we'll complete our quest with a few minutes for q and a. And with that, I will hand it off to our presenters. Well, thanks, Alex. Appreciate the introduction. As always, very excited. This is actually one of my favorite reports and webinars to give because it really highlights what we've done, in terms of capturing information and keeping our finger on the pulse of what criminals are actively using. But it also shows kind of the trends, how things are evolving over time, and that's always very interested. I'm the senior VP of product management here. My name is Chip Witt, and I am joined by a cohost. You know, for for those that have oftentimes thought to themselves that, we need help and should, seek the counsel of a good doctor, I know that they had Wallis in mind. Well, Wallis, would you care to introduce yourself and what you do? I I feel like you've done it for me, Chip. Hi, everyone. My name is is Wallis Romzek. I'm our, principal data scientist here at SpyCloud. I'm an applied mathematician. Most of my work for the last decade or so has been in leveraging big data and machine learning to tackle problems in this space. And my work at SpyCloud for the last year and a half or so, has focused on tracking and characterizing cybercrime, and a little bit of the the details we're gonna spell out for you today. Very exciting. Glad to be doing this with you, Alice. This will be fun. Likewise. Let's go. Alright. I think I'm ready. Alright. Good afternoon, everybody. I guess good afternoon for those of you on the East Coast. Thanks for joining us today. As Alex mentioned, the identity exposure report is our opportunity to synthesize what we've seen over the course of one year, relating cyber criminal activity. We create this report to ensure that we keep a close read on the pulse of dark net activity and to ensure that we continue to understand how stolen data exposes organizations and consumers to cybercrime. The number of exposed identities that we see is growing. More and more data relating to more and more people are being compromised. But in recent years, we've also identified a shift in the type of data that malicious actors rely on to compromise those identities. As it says right in front of you on this slide, cyber criminals are stepping up their game. The data under this report are evidence of that, and that's motivated us here at SpyCloud to continue to expand our datasets and be just as dynamic in exploring how emerging and evolving threats put consumers and organizations at risk. Next slide, please, Alex. So let's start with some of the the most important statistics in our report. These data pertain to calendar year twenty twenty three. On average, each breach we published contained one point nine million records, and we published somewhere around fifty five hundred breaches. Those records included well over one billion email addresses and passwords respectively, including at least a hundred thousand master passwords from popular password managers, which is basically like the key to your digital front door. That's troubling. In addition to login credentials, the breach has included thirty two billion pieces of personally identifiable information from social security numbers to birth dates to street addresses to credit card numbers to passport numbers. Lots of different little pieces of us as digital people out there on the dark net. This kind of PII doesn't necessarily allow a threat actor entry into a system or systems the way an email password combination might, but it does enable actors to do a significant amount of damage elsewhere. Open up a line of credit in your name, for example, make a fraudulent purchase, or compromise your identity in some other way. In twenty twenty three, we expanded significantly the types of data that we're collecting to allow us to better understand the criminal market and the realm of the possible. We started adding more credit card information, reclaimed API keys and webhooks, and crypto wallet addresses and session cookies. We also stepped up our malware collection game. And in the course of doing so, we discovered four entirely new to us info stealer malware families. In summary, the theme of this year's report is that the bad guys are evolving. They're using new tactics and techniques, but so are we. We're still keeping our finger on the pulse of both the data that are out there and how they're being used, and that helps us to be equally dynamic in our efforts to disrupt cyber criminals. Next slide, please. So before we get too far into the weeds of the report, let's let's do some level setting and make sure everyone's clear on our definitions and how we're using them at spy cloud. A data breach occurs when information is stolen through unauthorized access to a network or system. Individuals are exposed in those breaches through no fault of their own usually. For better or for worse, actually, that should just be for worse. It seems to be happening more frequently. Most of you have probably gotten a letter from a consumer company or your credit card provider saying that your records have been potentially compromised. We consider a breach record to be the set of data tied to a single user exposed in a breach. If my data were compromised in, say, the twenty three and b breach late last year, all of that information would populate one entry in our database. I feel like most of us know about malware, but better safe than sorry. Malware is software specifically designed to harm or exploit computer systems, networks, or users. Malware can take a number of forms, but we focus mostly on recapturing infostaler malware and Trojan malware infection data. Malware victim data is information that's been exfiltrated from devices infected with malware. Typically, usernames and passwords, sometimes session cookies, anything you've saved to autofill, PII, and device and system details that can be used to impersonate victims and actually, to also unmask criminals, but that's that's a different webinar. Next slide, please, Alex. So getting back to our report. This year we paid particular attention to the concept of a digital identity. A digital identity is the combination of our quote unquote traditional credential data with the PII and other victim data that I described a few slides ago. Malicious actors are moving beyond the traditional, the use of stolen username and password pairs, and broadening their tactics, techniques, and procedures to perpetrate crimes against consumers and organizations alike. So instead of just worrying about protecting their employees or customers emails and passwords, organizations also now have to worry about protecting their digital identities, which can occasionally be stolen outright but more frequently are cobbled together using data from a number of different sources. Given the breadth of data that we're seeing at spy cloud, we can be certain that threat active threat actors have in fact increased the scope of these attacks and are giving organizations and individuals more to worry about. Next slide, please. Okay. The average player. You may be sitting there thinking, I am pretty conscious of OPSEC. I've done this for a while. Digital identity exposure probably isn't an issue for people like me, and you are probably wrong. SpyCloud's data shows that the scale of identity exposure today is massive. In twenty twenty three, we collected forty three point seven billion distinct identity records. The statistics you're seeing on the screen are reflective of a random sample of those identities. And in that sample, the average identity that was exposed and traded in the criminal underground last year is associated with four unique usernames or email addresses. Of those, there's a an exposed password for sixty seven percent. The average identity has been exposed in nine breaches and has data in fifteen distinct breach records. In one in four of those records, the identity's network or physical location was revealed, so a street address or an IP address, for example. And twenty percent of each identity's records showed signs of infostealer malware infection. Those are aggregates. Right? Some identity stats were higher, some were lower, but I think the point here is clear. There's a lot of information out there. And setting aside the potential for personal harm that this information represents, the details it contains often include credentials to one or more of an employer's application systems, which can effectively turn a personal compromise or a third party breach into compromise of an organization. And I think now with that, that we're heading into our malware section. So I think I'll toss the baton over to you, Chip. Outstanding. Really interesting stuff there. Double clicking on malware a bit. In twenty twenty three, spy cloud started tracking more advanced forms of malware as well as collected new forms of exfiltrated data that are fueling identity risks. For this year's report, we doubled down on our efforts to understand the impact of malware following a notable shift in threat actors' tactics and amplified role of the underground marketplaces. The most alarming trend we see today, bar none, is that of malware. Infostealers and other types of malware exfiltrate valid authentication data and login credentials in addition to session cookies and are even beginning to target pass keys. In in the hands of a criminal, this data makes it easy for an attacker to mimic consumers or employees access to networks and applications with a high degree of success. The rapid rise of malware, specifically in infosteelers, is one of the biggest trends that we continue to observe. In twenty twenty three alone, infosteeling malware use tripled by criminals. We saw stealers skyrocket in our recaptured data with as many as one in five people, twenty percent, already the victims of an infostealer infection. The reasons behind infostealers climb to the top of the leaderboard are really clear. They're cheap. They're highly effective in exfiltrating a treasure trove of useful data, and they yield a high return on investment for the criminal. The shift to malware as a service model, is an additional boon for for the criminal, and research suggests that twenty four percent of malware distributed as a service is specifically from info stealing families. Next slide. Of the nearly thirty five hundred breaches we analyzed, over two thousand or about sixty one percent of total breaches were malware related and included over three hundred and forty three million stolen credentials. With valid credentials in hand, cybercriminals have a shortcut into employee and customer accounts that they are more than willing to leverage. Next slide. The records we captured in twenty twenty three were siphoned by fifty two Infosteelian families. Four of these families were new to the scene just last year, Atomic Steeler, Mystic, Exela, Atlantida. Two others, Luma c two and Ryze Pro emerged in the second half of twenty twenty two, but grew exponentially in twenty twenty three. For instance, LUMA c two records in our recapture data skyrocketed by more than two thousand percent in less than six months. Getting a little used there. It was more than LUMA Steeler's rapid growth though that caught our attention. The strain came with new features previously not available in commodity infostealers, such as exfiltration of local password manager vaults and configuration files from remote desktop software. SpyCloud researchers also found evidence of exfiltrated browser based 2FA secrets. This is all on top of the typical capabilities that we've seen in other infostealers, including the the stealing of credentials, session cookies, local files, crypto wallet private keys, and cached browser data like autofills. Our researchers' analysis of data exfiltrated by LummaC2 two showed that a log from a successful infection was three times as large as those from other info stealers, including prominent families like raccoon and redline stealer that people are really already familiar with. More and more complex data likely means more and more sophisticated crimes. There's already measurable indications of a link between info stealers, the data they steal, and ransomware attacks that can follow. And these types of correlations are likely to increase as this data glut from infostealers continues to increase. It's obvious that there's now a universal dependence on smartphones and tablets, which in turn creates a pressing need for better visibility into mobile device threats. This definitely is on the rise. Researchers found a fifty one percent increase in the number of unique mobile malware samples in twenty twenty two, coinciding with a record number of mobile phishing attacks. We recaptured more than ten point five eight million mobile records siphoned by malware between August and December of twenty twenty three. While financial fraud is a major motive behind mobile malware attacks, a successful attack can also lead to sensitive data compromise, disruption of operations, and reputational damage. Yet IT and SOC teams have limited or no visibility into mobile devices and struggle to secure them, leaving a massive gap in exposure. So we'll transfer transition into some other trends. Wallis, what do you have for us? Password reuse continues to be an issue here on this slide. For context, SpyCloud recaptured one point three billion passwords in twenty twenty three. And among the accounts to which those passwords belong, password reuse was seventy four percent, meaning that a digital identity or email credential reuse passwords in seventy four percent of its distinct records. Stop reusing your passwords, please. That statistic is up two percentage points from twenty twenty two, and the all time reuse rate for those same identities is also up, up, over twenty twenty two. This problem is not unique to the private sector. Government employees struggle with this too. Alex, can we go to the next slide, please? In twenty twenty three, we recaptured more breaches containing dot gov emails than ever before. And within those, the password reuse rate was also on the rise, up to sixty seven percent from sixty one percent in twenty twenty two. As a former government adjacent employee myself, this statistic isn't exactly a surprise, but it's certainly worth sharing since digital identity exposure may have even greater implications for the government sector. Given that nation states and other sophisticated actors can and do target critical infrastructure agencies, it's especially important for these organizations and their employees to lock things down. And yet, our data is showing that government identity exposures continues to be an issue. Passwords are also stagnant. It's another one of the trends we observed. This is about public sector employees. They need a little nudge to get creative with their passwords. These three, password, pass one, and one two three four five six were the top three most common passwords associated with dot gov emails in twenty twenty three. I will say that the top three passwords outside of the public sector are not much better. Variations on one, two, three, four, five, six, etcetera made up more of the top twenty passwords than, is acceptable in my personal opinion. And more Taylor Swift references than I'm comfortable with as well. I know. There were there were so many. Other passwords were, like, a little bit more complex, but only slightly. Seasonal trends, current events were the basis for many of the passwords we saw. Fantasy football as a password was observed one point one million times in twenty twenty three. No zeros, no dollar signs for the s. Fantasy football, straight up. We saw some adverts alluding to the Hollywood writer's strike during the five months it was ongoing. We saw references to Lionel Messi as he joined Enter Miami. We saw tons of references to the Barbie movie and Chip, for you, tons of references to Taylor Swift. Awesome. In addition to password reuse, 2023 also saw an increase in stolen session cookies exfiltrated by Infostealer malware. Alex, can we go to the next slide, please? There we go. The victory token. All info stealer siphoned data is immensely valuable to criminals and to at SpyCloud because of its high fidelity. But session cookies and tokens stored in a browser are really just like hitting hitting the jackpot. With a valid cookie in hand, criminals can simply sidestep any authentication mechanism, including multifactor authentication, and hijack a session in an instant. Next slide, please. Oh, that was cute. The risk of, hijacking is high. Last year, SpyCloud recaptured more than twenty billion cookie records. Not all of them session cookies, but twenty billion cookie records with an average of more than two thousand cookies per infected device. Session hijacking effectively turns cyber criminals into employee clones. It gives them unfettered access to sensitive applications and data, but many SOC teams don't yet have the tools to remediate this threat. And consumers are at equal risk. Session hijacking enables bad actors to effectively walk right into websites for commercial organizations or banks and make fraudulent purchases, open new credit lines, or drain loyalty accounts. The sheer number of cookies and devices here indicates that leveraging malware siphoned session cookies for next gen account takeover is already a valuable tactic for threat actors. And as more organizations adopt passwordless authentication, this is this is only going to escalate. Speaking of shared numbers, I think we're segueing into some of our notable breaches. Back and up. For sure. Plenty of high profile data breaches make the news every year, but there are thousands of other large breaches that no one ever hears about. No one, of course, except for a select group of criminals, and, you know, that's not good for for you protecting your organization. Right? So these breaches are first shared by small private criminal channels for fast, high return monetization before they're offered to a broader darknet net audience, and that's where they oftentimes enter into the threat intelligence sort of piece of, of the world. SpyCloud recaptures this data much earlier, and we ingest it into our data as sensitive source until the breached organization reports it publicly. And so now wanna dive in a little bit and share some of the data leaks that caught our attention circulating on the dark net, over the last year. Next slide, please. So the the report obviously outlines a lot of stuff that happened in twenty twenty three, but we we looked at four specific ones that we thought were were relatively interest interesting from the perspective of sharing for this this particular talk. The first one is WhatsApp, at nearly three hundred and sixty five million records leaked. This was data allegedly belonging to messaging platform WhatsApp owned by Meta, and this information was leaked online at an unknown date. The data contained phone numbers and other personal information. This leak was being privately shared on a messaging platform. Twitter, of course, now X, almost two hundred and four million records leaked. In January 2023, scraped user data belonging to social media company Twitter, now X, was leaked on a hacking forum. This data contained email addresses, full names, screen names, and other personal information. Some of the scraped data was made available in the forum for free. The threat actor responsible for collecting the data reportedly manipulated a bug in an exposed Twitter API to scrape the records. This API vulnerability existed between June twenty twenty one and January twenty twenty two, allegedly allowing other intrusions as well. USPII, one of the most creatively named breaches, two hundred and forty eight million records total. This is personally identifying information allegedly belonging to US residents, and it was leaked online in an unknown date. The data contained names, addresses, geolocations, and other personal information. The source of this leak, which was being shared privately in an underground criminal community, was not known. So don't know how this information came into being, but it was out there, and criminals were using it. And the last one, Luxottica, about two hundred and four million records leaked. And this data allegedly belonging to Italian eyewear conglomerate company, Luxottica, was leaked at an unknown date. The leak, which contained names, email addresses, phone numbers, addresses, and other personal information, was being publicly shared in online forums. The company later confirmed that it suffered a data breach in twenty twenty one and blamed it on a third party incident. The breach impacted seventy million customers, so not not small. Next slide, please. And, of course, everybody heard about MOAB, also known as the mother of all breaches. This included twelve terabytes of data. That's a lot of data no matter how you count your data. And this included credentials, from thousands of meticulously compiled and reindexed data leaks, breaches, and privately sold databases over over the years. So, recapitulation of data that had been used. But why do criminals share data? Well, because they found it useful, and they wanna share it with others. It's still an active trade, so it's likely still of use. SpyCloud's analysis found that ninety four percent of the data was already in our repository by the time this MOAB leak became popularly known. But approximately one point six billion records were new, meaning they were previously either released in sample format or had not been released publicly. And so, of course, we did, the the the right thing and pulled that six percent of the unknown data into our database, so it's available as well. Next slide. We wanna round this presentation up with a summary of actionable ways customers and prospects can use this data. Wanna discuss how the key to disrupting criminals' ability to profit off of stolen data is to understand what bad actors know about your their organization and customers and use these insights to identify riskiest users and to act quickly to protect them, giving power back to enterprise and leveling the playing field against the cybercriminal. So where do we go from here? So I think that this is where a talented game developer might do some cool bleep bloop transitional music, but we'll jump quite right into the, the next bit of information here. The key takeaway is really, today, protecting your organization against attacks that stem from exposed identity data means shifting from a device centric focus to an identity centric approach. Not device, identity. It's important. Security teams need quick and accurate evidence when any component of an employee, contractor, vendor, or customer's identity is compromised. You need to ask yourself the question, can you tell when an employee has been exposed? With early access to recaptured dark net data, teams can negate the value of stolen information by quickly identifying the riskiest users and acting quickly to protect them. Next question to maybe ask yourself is are you taking into account next generation emerging threats? Criminals are evolving their tactics, and if your solutions aren't keeping up, that's a big, big problem. As digital identities grow and there are more access points, do your current tools, processes take this into consideration and all these extra ways cybercriminals gain access to credentials. Even if you have things like multifactor authentication, cybercriminals are now finding ways to circumvent your organization need to be and your organization needs to be prepared. Post infection remediation, which this means looking beyond the device in response to a malware event and knowing what user access information and which beyond just credentials can which can include session cookies, two of a secret tokens, and API keys, and for what applications those credentials open up doors. And this is both on prem and in the cloud, and you need to include this as part of your playbook and your protocol for dealing with malware events. And if you're not looking beyond the machine, that's pretty important. And the reason why we stress that is the machine centric approach has been long held to in IT circles. You have a malware event. You focus on the machine, isolate that from the network, and then you burn the hard drive. And that is outdated now because info stealing malware quickly installs itself, steals what it needs to steal, and then uninstalls itself. So the remediation of the device is almost a secondary factor in remediating. In fact, it it's it's it's largely useless at that point because the information the criminals are now using is out in the wild the second that info stealer collects it and exfiltrates it, and that that requires a different approach. So I think that we are ready to transition to Q and A and I think that's my cue to summon Alex back to the call, to see what questions have emerged. Yes. I'm here. I think you can drop your any questions in the chat. Let me know if if that's not the case, but we did have some questions. Okay. So these stats are wonderful, but also terrifying. If I'm not mistaken, it seems as though criminals continue to innovate and find new ways to leverage how a user accesses corporate resources to do bad things. What hope is hidden in this data that illuminates a possible path forward for responding more efficiently or even getting ahead of the problem. Chip, you just spoke to that a little bit, so I'm gonna throw this one to Wallis. Alright. Yes. Definitely. Criminals are just as creative as the rest of us. They're always coming up with something new, and the data in this report confirmed that for us. What heartens me in this report, I think, is the breadth and depth of the data that we accessed in building it. I'm our principal data scientist. My job is to leverage our data to help our customers respond more efficiently to these risks. And what I see here are data that are useful in things like pattern identification, in uncovering, as yet unseen tactics or techniques. Those things that criminals obfuscate as they act, but are maybe visible in the data after the fact. You know, I have, I have a kindergartner, and she's working on deductive reasoning right now when they read stories. They'll read a story about, little Chip who always rides his bicycle to his friend's house after school, and while he does it, he eats a cookie. And And then maybe one day, little Chip doesn't arrive. And so they asked the kids then to figure out what happened to little Chip. If you look outside your house, do you see his bicycle? No. So he didn't make it that far. If you walk the route, he usually takes. Do you see cookie crumbs? No. So he either didn't eat a cookie, but he always eats a cookie, or he didn't ride that way today, and so on and so forth. So they eventually get the kids to the point of, like, where did things go wrong? If I know what usually happens, where do I think things went wrong here? So the same that's kind of a convoluted example, but I think, it's useful here as well. If If you know what usually happens, then that knowledge is a starting point to find out where things went wrong. Modeling cybercrime activity is a complex process, but more data on companies prior to known attacks and more detailed data on those companies at all periods of time help us to identify common attack surfaces, common vulnerabilities, qualities that make companies attractive targets, etcetera, etcetera. So even slight improvements in that understanding help us move our efforts from remediation to preventative. So I guess, Alex, back to your original question. I see the fact that we're observing new and different types of victim data as a positive factor in our efforts to combat those data being compromised in the first place. Amazing. Thank you. I don't know where your daughter goes to kindergarten. It's certainly that's not the curriculum that we had, so love love to hear that. Okay. Confirm Chip does love cookies. So I assumed. Yes. Next question. Great to see mobile malware data coming into view. Are there fundamental differences between mobile and standard PC malware in what criminals are able to access or target? Chip, I'm gonna send that one to you. Yeah. There are are, of course, a lot of similarities in terms of the type of information that's valuable to criminals. And as we all know, people use their phones as a centerpiece to their lives, including increasingly their financial transactions. So to date, our collection of data has been focused primarily on recapturing mobile banking Trojan logs due to their impact on businesses and consumers. Many of these logs include not only a complete credit card detail, but also information on the individual, like birth date, Social Security numbers, mobile device pins, and other really sensitive information. So that's where we're primarily focused right now in terms of what we're collecting for mobile mobile malware. So that's that's the difference between the data is it's a little bit more focused. Gotcha. Thank you. Mhmm. Next question. I read somewhere that criminals are using criminal ecosystems to initiate ransomware attacks. Is there any relationship between what SpyCloud is seeing in info stealing malware and these ransomware attack chains. Wallis, this one is all you. Yes. Definitely. I am very interested in the data we're seeing coming back from info stealers, because of additional work we're doing. The research is still ongoing, but we've, in in trying to move from remediative to predictive of ransomware events, I'm trying to identify some of the relationships that exist, ahead of those events. So the research is still ongoing, but we've identified, for example, some significant, and I mean that in a mathematical sense, relationships between certain types of info steal of course, I do. Certain types of info stealer malware and ransomware events. So we know that we're seeing more evidence of infostealer malware in rec in recaptured records, period. We can never know, the true extent extent of ransomware events, but I feel confident saying that they're not gonna slow down. So this is an area of focus for our data science team, in twenty twenty four. We're exploring the relationships between these types of infostealer malware and ransomware events to determine I've certainly seen it be correlative. I don't yet know if it's predictive. We're exploring that relationship. We're exploring a number of others as well to determine how they matter or don't to a model of the factors that precede ransomware events. We're thinking about compromised SSO credentials. We're thinking about compromised administrative credentials, associated cookies, etcetera. But, yes, thus far, we've observed both strong correlative and statistical relationships between infosteeler malware infection, and follow on ransomware events. And I'll add just one little thing. It does vary by infosteeler family, which I find really interesting and hope to get to the bottom of sometime soon. Awesome. Interesting. Love that. Any not seeing any other questions come through. So if there are, go ahead and drop them in the chat right now. If not, any other closing, thoughts on the report overall, Chip and or Wallis? No. I just think that this is a tremendous opportunity, for us to really kind of take a breath and look at the volume of data and its meaning. And so this is always an eye opener, not only for our customers and partners, but I I I find this tremendously valuable to just, you know, reinvest, dig in into where we're going next. And and, of course, you know, with with Wallis's additions and some of the places that we're going with product, these are in deed interesting days, and, we're in the fight with our customers, with our partners to put this data to good use to prevent criminals from profiting off the data that they steal. That's exciting to me. Yeah. I I don't think I could say it better than that, Chip. I'm excited to work on stuff like this. I'm excited to put it out there in the world. Hopefully, it helps some people. But, Alex, I will ask if I can have my my sorceress, avatar for my own personal use. Yes. I will happily send that to you. Also, our cameras aren't aren't on, but I do have blonde hair. So if you see me using that That's fine. We can share it. Amazing. Well, thank you so much for joining us. To anyone still here, you can always, go to SpyCloud.com to check your exposure. We have an amazing tool for that, and it will help you identify threats to your organization, including malware infected employees, stolen session cookies, recency of breach exposures with the exact sources, dates, and more. You can get far more information, than you would have ever thought possible. It's it is such an amazing tool. You can also sign up for our newsletter, on our website and, check out any other great resources that we have, other guides, other research reports. And that is all we have for you today. So, with that, I will go ahead and close this, and I hope everyone has a great rest of your afternoon. Yep. Thank you for joining us. And, Alex, Wallis, thank you for, for joining me. This has been awesome. Likewise. Thanks, everyone. Thank you.
- Video
Webinar: An Inside Look at Game-Changing Threats in 2024
In this webinar, we cover top trends from the SpyCloud 2024 Identity Exposure Report. Learn about the identity threats putting organizations everywhere at risk.
So thank you for joining us today. I'm Emily at SpyCloud, and today's demo slash webinar hybrid or as some like to call it a demo, we'll we'll be giving you an inside look at SpyCloud's consumer risk protection for financial services, showing how you can better safeguard consumer digital identities and stop high risk attacks tied to malware, helping you more confidently and efficiently answer the ultimate question, is this a legitimate customer trying to do business with me or a criminal using stolen information? So our subject matter expert today is Colette Tomasiak here at SpyCloud. She's our director of product marketing. Colette's going to start out by giving us some background on the massive scale of identity exposure within the financial services industry and then jump into a live demo that exemplifies how SpyCloud's API, can be leveraged within your own applications. So for those of you that were able to join us live today, thank you, and please feel free to chat with us and use that q and a feature in Zoom to ask questions. And we'll try to leave some time at the end to address those, and anything we aren't able to address live, we'll make sure to follow-up with you. So, Colette, we'll hand it over to you. I'm excited to hear from you today, and let's dive in. Perfect. Welcome, everyone. So before we get started, wanna give you some scoop on who SpyCloud is. So our mission is really to help you disrupt cybercrime by enabling you and your teams, whether it be security fraud or even application and product teams, to really act on what cyber criminals know about your business and your consumers. And while we solve for a diverse set of use cases focused on leveraging our darknet telemetry to safeguard digital identities, today, we're really gonna be focusing on SpyCloud's consumer risk protection solution. So criminals are really increasingly motivated to exploit customers' poor cyber hygiene and discover new ways to profit from account takeover, both in the traditional use case of breached credentials to log into customer accounts as well as emerging or more sophisticated techniques like session hijacking. So really businesses today need direct insights into their customers' exposures that include authentication or access details, including credentials and cookies leaked in breaches or exfiltrated from malware infected devices. And with SpyCloud, your customer exposures don't have to affect your business's productivity or even your bottom line. So our consumer risk protection solution allows financial institutions to really derisk consumer compromise. And we do this by enforcing strong passwords at account creation and identifying compromised users at login or at the point of transaction to really uphold and maintain account integrity. We also help enterprises maximize operational efficiency by automating that ATO prevention, and the efforts around it to decrease that need for manual intervention. We also help you uncover undetectable risks by identifying malware infected consumers and really preventing MFA and even pesky bypass to protect your users' web sessions. So now that you have a sneak peek into who SpyCloud is and what our consumer risk protection solution offers, let's get into some of the challenges, that are facing financial institutions today. So a critical factor contributing to the success of account takeovers is the challenge of actually discerning the legitimacy of individuals interacting with your site. And the ATO problem is intensifying with the tax soaring three hundred and fifty three hundred and fifty four percent year over year. So while security teams are really doing what they can with existing solutions to strengthen customer account security, they're faced with challenges that are outside of their control, like a user's poor security hygiene and behavior that puts their own digital identity at risk. And our own analysis reveals that it's still a concerning seventy four percent password reuse rate amongst individuals who were exposed in two or more breaches, which this significantly contributes to the success of automated ATO attacks. And whether it's their own poor password hygiene or data that's been exposed in breaches outside of their own control, meeting customer expectations really involves staying ahead of innovative criminal tactics and implementing more robust measures for account safety. And it's still a substantial seventy three percent of customers really perceive the brand as being accountable for preventing ATO and protecting those consumer credentials, really emphasizing importance of trust for long term customer satisfaction as well as loyalty. So in the face of these evolving criminal tactics and heightened impersonation skills, adopting new solutions really becomes imperative, and the tools and solutions that enterprises use need to provide that visibility necessary to proactively decrease risk, but also enhance overall security. So how can you tell if your customer is an actual consumer or a criminal? Or are you able to even tell if that customer's credentials have been exposed via a malware infection and that they're at high risk of account takeover? So despite a robust lineup of ETO prevention tools and organization might have in their their toolbox, critical insights still remain missing that leave visibility gaps and keep doors open for attacks. And while many tools provide information on data exposed in a breach, there are still really limited solutions that provide definitive evidence that a user has been infected with malware. And this is just one element of it. On the other side, no one's able to innovate as fast as a cyber criminal looking to profit, and it's becoming increasingly difficult for organizations to keep up with the pace at which cyber criminals are evolving their tactics. And this includes MFA bypass, like through a stolen session cookie that was exfiltrated from an info stealer malware infected device. And this grants that criminal access to an already authenticated session, completely sidestepping authentication protocols put in place to really preserve account integrity. And we know that fraud and security teams want to be able to close those visibility caps and really keep up with innovation and new attack methods, but new solutions that are being considered really need to increase account security but without sacrificing team productivity, customer experience, and your organization's bottom line. And we know automation is essential to that, and SpyCloud really supplies you the data you need to proactively protect accounts while also seamlessly integrating our solutions into your already existing workflows. So how exposed are your customers? So we did a little experiment, and we ran the top fifty banks operating in the US according to total assets, based on S and P through SpyCloud's database to show you the volume of malware infected users with exposed credentials, PII, and other data. So you can see that for these top fifty banks collectively, on average, there are over six thousand infected consumers and a total infected customer count of over three hundred and twenty two thousand. And this is all just based on our sample data from the last six months. But there is one caveat to mention around these numbers. The numbers are only a minimum reflection of the actual exposures tied to malware, and that's because our accounts for this data pool only includes the infected consumers where the company URL was included in the malware log. So this doesn't account for active infections that haven't yet captured the consumer's login for the sites they haven't accessed yet. So the point is the number of infected consumers you are doing business with is likely much, much higher. So what data do you need to understand if a consumer is truly a consumer or a criminal taking over the account? And with data, there's always a concern. Data is commoditized. Right? Intel data can get stale really quickly, and it's hard to make informed decisions when the quality of your data is limited, old, or inactionable. So SpyCloud collects data from dark net sources that really other providers simply can't access, where intel is fresh, it's rapidly delivered as we continuously ingest new data. And our intent is to be your go to source for the missing data that you need to really act on what cyber criminals know about your consumers while also seamlessly fitting into your existing workflows to help scale detection, response, and enable you to customize the the action that you need to take to proactively protect consumers' digital identities and prevent that account takeover. So with clear visibility and a more comprehensive view into your consumers' exposures, SpyCloud helps you differentiate between high risk and low risk profiles and really eliminate the guessing game of customer or criminal. And a critical component of essentially winning at this guessing game is realizing that an identity is more than just credentials. And for this, you need data diversity. And our repository has over two hundred plus asset types that we recapture and alert on. So when thinking ATO prevention with credentials, think email plus password, think session cookies, think pass keys. And coupled with our password cracking capabilities, ninety percent of our passwords are available in plain text, which makes it incredibly easy to determine if your user's credentials within your application have also been exposed elsewhere. And this is just one layer. So SpyCloud also gives you insight into sensitive PII, like date of birth, Social Security numbers, driver's licenses, and more. And these are all potential tools for impersonation and identity theft. But, also, we give you financial data such as exposed banking information and credit cards that are often used for fraudulent activities. But the cherry on top of all of this is SpyCloud's ability to detect if your users have been infected with info stealer malware and report on what unique authentication data, like session cookies, have been exposed. So our analytics really correlate billions of data points from diverse sources to uncover exposures across your consumers' digital identities to really give you the confidence to take the right action but at the right time. But what about the consumer journey? A common concern really with security teams and fraud teams is balancing account protection without creating unnecessary friction in the journey. And by knowing what cuss what criminals have in hand to use against your business and your consumers, you your teams can really devalue that and force friction with the customer base where it needs to happen, but not across the board. So for low risk users, they should experience a more seamless journey, and enforcing this should be super easy and really an automated workflow for your teams. For high risk users, on the other hand, like ones infected with malware, this is where you might consider little more friction acceptable. And with SpyCloud's Darknet Telemetry, you can customize the experience based on the insights that you now have into the consumer's exposures. And then the actions you deem appropriate based on their level of risk and apply friction only when necessary. So customizing the journey should be really straightforward and allowing you to neutralize the value of those stolen credentials, so you can enhance a fit efficiency by automating that follow-up authentication and really reduce friction for low risk users and ensure an overall positive and secure experience within your site or application. So next, we're gonna walk through a demo of both low risk and high risk user experiences and what it could look like, based on the data you can leverage with SpyCloud to make those decisions. So just a disclaimer, this is not our product. This is just kind of an example simulation of where you can plug in SpyCloud's API and what that could look like in your potential site. So let's flip over to the demo. Here we have a fictional let's call it a bank, and this bank's called Spy Factor. And we wanna explore two use cases. We're gonna start off with low risk of ATO. So what this looks like is everything on the left hand side over here, you can see it correlated to the API call on the right so so we can follow along. But in this scenario, for a low risk user, we have Elise. Elise wants to log in. She wants to take a look at her bank account, maybe make some transactions, all the good stuff, and she's gonna log in. So we're gonna run that data and take a look. And here we see that there are some breaches tied to Elise. And you can see recency of it, number of exposures, plain text password associated with it. But here you can really click in and get more information on the actual breach. So we're gonna look at Luxottica, for example. So this one is Luxottica. It's an Italian I work conglomerate company. They also manufacture Ray Bans. Maybe Elise was really into Ray Bans like everybody else and then got her information breached through this site. But here you can see additional details like the recapture date, the number of total records, the type of breach it is, and then additional assets exposed in this breach. So with this information, you can determine the type of action that you wanna take for Elise when she logs in to her account. And while some might choose no friction, which means do nothing, for financial institutions, a little friction probably is a little more tolerable, especially as consumers probably will tolerate that when it's their financials at stake. So here, what we see most of our customers doing in terms of the type of action taken is MFA. So we're going to make sure that it is Elise actually logging in and checking her bank information. So Elise is gonna log in. She's going to get an SMS notification with code to verify her identity. She's gonna plug that in, and then she's able to verify her account, log in, and proceed with making any other transactions desired. So let's look at what a high risk situation would look like. So when a user is infected with malware, with exposed credentials, here we're gonna look at Arden. Arden wants to log in to her account using this password. We're gonna run that on our back end, and here we're gonna see that there's malware tied to this specifically. Number of breaches, number of passwords, all of that, but we're gonna double click into the specific malware. Here you can see the details on the info stealer, the type of kind of malware it is, number of records. But here you also get all the additional credentials stolen for this user from this malware infection, and you can even see some password reuse across two sites. So, again, for this one, giving that it is more of a financial scenario in terms of protecting their information and then their funds, password reset is often what other customers choose. Just customers are willing to accept a little bit more of that friction, especially when it comes to protecting their account. So we're gonna have Arden do a password reset. So let's say when she goes to log in, we're gonna run that information, and now we're gonna let her know that we want to to protect her account, and she needs to update her password. So first, we're gonna verify that it actually is Arden. So she's gonna get the SMS code, verify that, and now she gets to go in and change her password. So she has her old password here. And for the new password, she's gonna wanna use Main Street exclamation point. So we're gonna put that in here. And then what SpyCloud then does is we're gonna take just the first five characters of that hash and run it against our database to see if that password has been used before. So if she goes to reset that password, here you can see the hits that we got based on just the first five characters of that hash. To look for an exact match, we're gonna wanna find the hash that's ending in four eight d b. And if we look down here, we can see that this one is the specific password that she wants to use, and there's only seven other exposures and times it showed up in our database. So there's two things you can do here. You can allow her to use this password, or you can also suggest to the customer to choose a more secure password. So it's up to you in terms of how you would want to tailor her experience for this. But let's say, great. This password's accepted. She gets to log in, and she can now make financial transactions, check her statements, transfer funds, whatever she likes to do. And that's kind of the overview in terms of how you can tailor the journey and take different actions based on the risk in terms of what you're willing to tolerate for a risk level and what you feel your customers might be able to tolerate in terms of friction. So here we can go into any q and a. So you can post that, in the Zoom chat, and we can tackle that. But that's it for the overview of SpyCloud and what we offer and how you can customize that journey using dark net data from spy cloud.
- Video
Webinar: Consumer or Criminal? An inside look at SpyCloud’s Consumer Risk Protection for Financial Services
This demo/webinar shows how SpyCloud helps financial organizations safeguard consumer digital identities and stop high-risk attacks tied to malware.
I'm Emily at SpyCloud. And in today's demo webinar hybrid or as I'm eagerly waiting to say, a demo, we'll be giving you an inside look at SpyCloud's consumer risk protection solution for ecommerce, retail, and really any company that has a vested interest in protecting their customers' account integrity and finding an automated way to reduce the risk of account takeover and online fraud. And today, we'll show how SpyCloud can help safeguard consumer digital identities and stop high risk attacks tied to malware. So you can more confidently and efficiently answer the question, is this a legitimate customer trying to do business with me or a criminal using stolen information? This session is meant to be both interactive and informative, so please add questions using the Zoom q and a feature, and we'll leave some time at the end to address those. Our subject matter expert today is Marc Gorelick, our solutions engineering manager here at SpyCloud. And Marc has extensive hands on experience working with organizations that are striving to provide this secure customer experience. So looking forward to hearing some insights from you today, Marc, and let's hand it over to you. Thanks, Emily. So as, as Emily said, if you have questions, please, by all means, interrupt me. This would be a lot more interesting with questions and answers as opposed to me just droning on. Don't really wanna hear myself talk. I'd much rather hear from you folks. So, with that said, let's dive in, shall we? So first, who are we? SpyCloud's mission is to disrupt cybercrime, and you might reasonably ask, well, how do you go about doing that? And the answer is that we have a tremendous amount of information about your customers. In many cases, we have many, we have digital assets about their identity, their usernames, passwords, cookies, and so forth. And our mission is to help you disrupt cybercrime by enabling you and your teams to act on what cybercriminals know about their identities. And we're gonna focus specifically on customer risk protection today. So the list of items or the list of things that we can do are listed across the bottom, and we have a lot of different capabilities that many ecommerce organizations find very valuable. So how are we going to help you fortify account security? So there are really three elements that we wanna emphasize today. The first one is to reduce or derisk, as we're saying here, customer compromises. And the way they're going to do that is we're going to enforce strong passwords at the time that accounts are created. We're going to check to make sure that accounts haven't been exposed, and, that can be done either at login time or transaction time. We're going to improve your operational efficiency by using automated methods to take advantage of this information. It is our objective to make your lives easier and not more difficult, and the way we're going to do that is that by automating these, security checks, we can reduce the need for manual intervention. And then the identification of like, I guess if they were undetectable, we wouldn't be able to detect them either. But what we're really saying here is that we have ways of finding out that or telling you, I should say, that your customers are risky, without in in ways that you wouldn't be able to do without us. So for example, we can identify malware infected consumers. We harvest tremendous numbers of cookies and so forth, and and all of these are ways that you can find out whether your consumers have been exposed. So, the real problem that we're that retailers deal with is, frankly, that their customers have terrible IT security hygiene. And criminals know this and have been taking advantage of it in huge huge quantities. So as we say here, we have seen, a three hundred plus percent increase in account takeover attacks. That's, by the way, in case you don't know what ATO is. It's account takeover, meaning essentially that someone uses stolen credentials to take over an account. And we've seen a tremendous increase in this over the last couple of years. And then also, since we know everybody's password, basically, we've been able to easily do some calculations on password reuse. And not only do seventy four percent of people that in our database reuse passwords, but this number is actually increasing year over year. It was seventy two percent last year. It's up two percent, which, by the way, boggles my mind because it's something that I I think there's increasing awareness of and scrutiny, but it just doesn't seem to be resonating with average users. So people in the IT security space like us know that this is bad. The message is apparently not getting to your consumers. And and that's a problem because as you can see, the overwhelming majority of consumers think that the brand is actually accountable for protecting their accounts. So if someone gets exposed, they don't blame themselves even though they ought to. Instead, they're more likely to blame to blame the operators of the website that, their identity was stolen on or or used on one or the other. We have a tremendous number of assets that we capture, every day. We're publishing new records. And it last year, we recovered over twenty billion stolen cookies. And this year, and it's only May, we've already recovered over fifty million stolen credit card numbers. And we can take advantage of both of those to ensure that your consumers' information hasn't been exposed. Again, if there's questions here, please let me know. So the real question that we're trying to answer is, ultimately, is the person logging in a customer or a criminal? How can you tell? Are you able to tell their whether the customers had their credentials exposed by malware? Are you able to tell whether the password that they're using is the same password that they're using on fourteen other websites? The the thing that we have working against us, we collectively, meaning not only SpyCloud, but the folks on the call today, is that the adversary is essentially better funded and has more time than us. And, you know, no one no one can innovate as fast as cyber criminals, and it's becoming pretty difficult for us to keep pace. However, we do have some ways to make sure that things like, people aren't bypassing, multi factor authentication. We have we can provide a great deal of enhanced visibility by the use of our data. Any So how exposed are your customers? So we did some analysis on the top thousand ecommerce sites, and we came up with some data. And then, you know, the way SpyCloud works is that we're not collecting data for specific domains. We just collect all the data, and it ends up being applicable to various domains. So we have the ability to look at the top thousand ecommerce stores, and we found that on average, there were seven, seven thousand seven hundred exposures per company. So, you know, that's that's a pretty ridiculous number. And, of course, it read you know, if you if you do the math, that means that there's seven point seven million exposed records out there. But this isn't actually all of it either. All this does is the way we calculated jeez. I can't talk. The way we calculated this figure is that we took records where we had seen a particular target URL for one of these ecommerce sites in the malware data. So what this doesn't calculate is all the people that hadn't visited one of these sites yet. So this number is actually gonna be considerably higher. So not only do we have credentials and session cookies and pass keys and so forth, but a lot of this other value the a lot of this other identifiable data is very valuable to people in in the world of ecommerce because we can get not only credentials, but we can also do some attribution for anti fraud purposes. So, in many cases, we captured over, I should say we capture over two hundred different, different data types from various breaches. So in many cases, we'll end up with not only email password, cookies, and so forth, but we'll also end up with people's names, phone numbers. I'm not gonna read you all the things on the slide here, but you get the general idea. We as I mentioned before, we get a ton of credit card data, including all of the stuff that you would need to actually do a transaction. In many cases, we get the home address for people so that they could potentially use a residential proxy to, to mimic a legitimate user coming from a legitimate location. So this wealth of data that we provide is makes it much easier for people in ecommerce to be able to determine not only whether the person is compromised, but who they are and what and what criminals know about them. So the the trick that, ecommerce, ecommerce web operators deal with is that there's always this tension between additional friction for a transaction and security. And so the good news for for ecommerce folks is that SpyCloud is able to determine how risky somebody actually is. For example, if we find somebody who we have only a couple of credentials for, they don't have extensive password reuse, and there's no malware, then they're a comparatively low risk user and, you know, you can apply less friction to a transaction for such a person. On the other hand, if we find that if the user who's logging in has been exposed with malware, potentially has much worse password reuse, is using terrible passwords that have been repeatedly, compromised, then you may wanna impose either additional friction on the transaction or, or potentially, you might want to instead, have the transaction flight for manual review. If there's any if there are any questions, I can dive into the demo aspect. Yeah. Does anybody have any questions? No questions so far, but good reminder to prompt the audience that we can even unmute you if, you have a more detailed question or that q and a box is still open for you. But, yeah, let's go ahead and dive into the demo. Okay. Great. Let's do that. So the demo today is going to show how SpyCloud's APIs can work to improve the security posture of a particular user by determining whether or not user has been exposed and provide that insight to the web to, ecommerce operators. And, so let me drop my share for a moment and share my browser. I trust Emily, is that, share working okay? Yeah. Great. So we're gonna use a, fictitious company here called Spare Factor. And let us imagine for the moment that Spare Factor is the purveyor of amazing audio equipment. And first, we're gonna determine whether or not we wanna see a low risk user or a high risk user. And, of course, we're gonna start with the low risk user. And what we're going to show is the user experience here on the left side of the screen and the API traffic to SpyCloud's data lake on the right side of the screen. So in this case, here's a user logging in, and they've provided their password. And here we have the password. And so what do we know about this user right out of the gate? Well, they've been exposed a couple of times. Once in the Luxottica breach, and for people who don't know, this is the company that operates Ray Ban. This was a real breach that had many millions of of users in it. And in this case, this is a comparatively low severity record, and the reason it's comparatively low severity is because we don't actually have a ClearTax password for this user. And then they've been exposed a second time in the forever twenty one breach, and you notice, by the way, that as I highlight things, the screen over here shows what I'm highlighting. And in SpyCloud one go, a severity twenty record is one where we have a clear text password. And indeed, you can see here, this is the password that we have for this user. So this password has not been reused, by this user. Here's some more detail about the breach that comes from our breach catalog, by the way. In this case, the Luxottica breach provided us with over two hundred million records. And as you can see, there are a number of assets that we gathered of around a hundred million emails, closer to two hundred million full names. I'm not gonna read the rest of it to you. You get the idea. But the breach catalog provides you with all of this information. So for a, a low risk transaction, you probably just don't wanna provide any friction at all. So we're just gonna say no friction here. The person logs in, and then here they are with some transactions, and they're logged in. Okay. Now let's instead talk about someone who's been exposed with malware. Obviously, a much higher risk. In this case, we have a different user who logs in. This is the password they're using. And when we send this email address to our API, responds with all of these records where we've seen exposures, and most worryingly, they've been exposed by a rise pro stealer. And that gives them, in SpyCloud language, a severity of twenty five, which is a critical severity risk. So you can see all the other information that we got back from the API with all these other different breaches. In this case, here we have this person using the same password on a different site. If we look at the details of this particular breach so this is, this was the second one on the list. This is a Philippine airline. And you can see again, you know, millions of records exposed. And in this case, we're gonna do a password reset for this user. So the person logs in. And because we know that they've been exposed by malware, we're going to make them update their password, and we're gonna do that using SMS. So we have a code texted to them. The code is received, then they put the code in, and now they're prompted for a new password. So this is a key aspect of how the SpyCloud password API works. We're gonna look up their intended new password, and we're gonna do this is something called k anonymity. And, essentially, what this means is we're gonna send the hash a fractional hash of the password, to ourselves, and, then we're gonna respond the API will respond with all matching hashes that meet this first five characters, and you'll see this in action in a minute if that doesn't make any sense. So the person types in their password. Again, this is the password they're trying to use. Here's the first five characters. We send the the website sends this five characters. That's actually six. That's five characters to the API, and the API response will spit back everything that matches this first five, and you'll see this in a second here. Okay. And so what happened is this password partial hash was sent to our API, and our API responded with over two thousand partial matches. But the one that really matters is this one that ends in two four eight d b, which is right here. And what this tells you is that this password has only been exposed in SpyCloud's data seven times, which is a very small number. Bearing in mind that we have over twenty five billion clear text passwords, the likelihood of finding one that we haven't seen before is fairly low, unless it's something completely random from a, let's say, a password manager. But in this case, this password has only been exposed seven times. So this represents a bit of a tuning knob for the for the website operator. It might be difficult to come up with a password that's been exposed zero times, so maybe seven isn't that bad. But if it was seven thousand, you probably would wanna have the user pick a different password. This is definitely a your mileage may vary type of situation. But, anyway, that's how this works. And, then after the password is reset, the user is allowed in. So maybe in your environment, you don't wanna force the password reset. Maybe you just maybe just MFA is good enough for you, and you do manual review afterwards. We give you all the options, and it's essentially up to you how you do it. And we have customers that do this many, many different ways. And then this just explains how k anonymity works. Again, first five characters, API responds with all the matches, and then you decide whether that's good enough for you. And, at this point, I'll take questions if there are any. And if not, I'll wish you a farewell. Yeah. No questions have come in yet. I kinda had one, though, that popped up, Marc, while you were showing the k anonymity. Is that designed just to enhance the security and privacy of the customer so that we're not actually looking at their real passwords? Right. Exactly. So the idea is that we never want a customer to send us, and it's not sent in clear text, of course. It's done in over HTTPS, SHA two fifty six, etcetera. So the the data that is coming our way is encrypted as well, but there's really no good reason for even encrypted, for anybody to send us a clear text password. It's there's always the possibility of some kind of man in the middle. I think the frequency of that actually happening is hugely overblown, but, nevertheless, it's not impossible for that to happen. And so there's no good reason for us to send any clear text data out of your environment. Nice. Yeah. That makes sense. Have you had any customers that you work with, you know, concerned about that data privacy element for their customers? And, I guess, how would you approach that? So we definitely have customers that are on a spectrum of I'm gonna use the word paranoia, but I'm also cognizant of the phrase just because you're paranoid doesn't mean they're not out to get you. So, let's say that this our customers are on a spectrum of worry, if you like. And the very worried customers will be pleased to know that we can solve and hash this data as well as making it shot two fifty six. So So that'll make it yet another layer, and, and and we have customers that do that. So, for those that don't think the k anonymity even is up to their standards, we have ways to to enhance it even further. But, yes, the whole reason for this is to not send clear text data out of the customer environment. Excellent. Well, that's good to know. Alright. We did have a a question come in. So, Marc, with the password hash compare k anonymity, is that going against just have I been pwned, or is this against SpyCloud's entire proprietary dataset? Can you maybe explain a little bit more about the data? Yeah. That's that's a great that's that's a good question. So, of course, we're very aware of how they've been pwned, and and I I personally admire the heck out of out of Troy Hunt. I think he does an amazing job for basically being one guy. SlightCloud's big differentiator is that we've essentially industrialized what have I been pwned does, and we have over two hundred people that have been working on this for eight years, and we have a great many more breaches than than Troy has. Last estimate, I think he had around seven hundred and fifty, and we were over fifty thousand. So the the password check goes against our data. I feel like we have everything Troy has. And then the other thing that, that's worthy of mention is that, have I been pwned? And, again, nothing but respect for that or for for Troy and and what he's done. But we give you clear text passwords, and he doesn't have them. And part of the reason we have clear text passwords is because we aggressively crack them. So, there's a a a Slack channel internally that tells us about new breaches and new data that's posted. And just about every week, there's at least a hundred thousand new passwords that we've cracked. So So this is a big part of what we do, and we feel pretty strongly that if you don't know what the actual clear text password is, how are you gonna compare it to what's in your environment? Right? So, we think that that's pretty important. Hopefully, that answered your question. Yeah. I think so. And then kind of the malware data as well. Right? Yeah. Troy access to all those malware logs, so that's another And those passwords are almost always in clear text because they're stolen right out of the user's browser. So not only does each successive malware infection, give us more passwords, but it gives us more clear text passwords as well. And in fact, actually, it's quite useful for our password cracking efforts too because we can then take the new hashes and compare them to the hashes that we're trying to crack, and sometimes we uncover new ones. So that's like the lazy way of, of cracking passwords is to take an already cracked password, hash it, and see if it matches one that we already have. There you go. And you had mentioned all the other data that's siphoned from a info stealer malware infection. Like, it could be a passkey, API keys, the credit card so really anything on that machine. Of course, that's why the the malware, kind of flow that we showed here is super high risk compared to an old breach without any password reuse just from the sheer gravity of all the information that they've stolen from that stealer infection. Right? Yes. Yes. Absolutely. So, you know, the the reason that the person got infected in the first place is because the bad guys wanna steal stuff from them. And among the things that they steal are credentials of all different types, and you've outlined almost all of them a moment ago, so I won't bother repeating them. But you're all of those were definitely things that get stolen. And then I would also add stuff like crypto wallets, you know, all manner of other things. Actually, what we what we actually receive are called bot logs. This is this is a zip file. And and when you unpack the zip file, it contains a directory with passwords in it, a directory with cookies in it, a directory with pass keys, and other authentication stuff in it. And then somewhat amusingly, generally speaking, it'll also have a screenshot of the desktop when the person clicked the thing they shouldn't have clicked on. So you can see how people are getting infected. And, and what we see over and over are people getting infected on home computers, when somebody tries to run some sort of a cheap or a video game or something. We see a lot of corporate credentials get exposed this way too because, you know, maybe, you know, mom's been working on on the computer all day for work. And then in the evening, kid will come over and load it cheap for Call of Duty, and all of mom's employers credentials are now a matter of I won't say public record, but the bad guys have them, and we get them very soon thereafter. A very common scenario. So the data we're collecting could be relevant, you know, both for your enterprise, your employees, but your consumers as well, like what we demonstrated here. Right. Absolutely. Yeah. We you know, the there there's sort of, three main use cases that SpyCloud customers take advantage of our services for. Employee protection is definitely one. Obviously, the focus today is on consumers, and then we also have some very powerful investigative capabilities that I briefly outlined talking about some of the other data types, things like Social Security numbers, credit card numbers, and that kind of stuff. Excellent. Well, thanks for helping out with those questions, Marc. And for anyone on the call, if you have any additional questions or wanna double click on anything that Marc showed, our team will be reaching out to you or, yeah, please feel free to connect with your, SpyCloud point of contact that you've been working with recently. So, yeah, thanks again, Marc. Thanks to you all for joining live, and, we'll hope to hear from you soon. Thanks, boss.
- Video
Webinar: Consumer or Criminal? An inside look at SpyCloud’s Consumer Risk Protection
This demo/webinar shows how SpyCloud helps eCommerce organizations safeguard consumer digital identities and stop high-risk attacks tied to malware.
Hi, everyone. Welcome to our webinar on preserving account integrity and reducing risk with SpyCloud's consumer risk protection. In this webinar, we'll give you more info on who SpyCloud is, the challenges that teams are facing in solving for protecting both their customers and their brand and what business outcomes you can expect with SpyCloud. So SpyCloud's mission is to help you disrupt cybercrime by enabling you and your teams, whether it be security, fraud, or even application and product teams, to act on what cybercriminals know about your business and your consumers. And while we solve for a diverse set of use cases focused on leveraging our darknet telemetry to safeguard digital identities, Today, we'll be focusing on SpyCloud's consumer risk protection solution. And criminals are increasingly motivated to exploit customers' poor cyber hygiene and to discover new ways to profit from account takeovers. Both the traditional use of breach credentials to log into customer accounts, but also emerging sophisticated techniques like session hijacking. So businesses need direct insights into their customers' exposures that include authentication or access details, including credentials and cookies leaked in breaches or exfiltrated from malware infected devices. And with SpyCloud, your customers' exposures don't have to affect your business's productivity or your bottom line. So let's get into some of the challenges. So account security is paramount today more than ever and with customers relying on brands to safeguard their sensitive information. But it's human behavior that plays that significant role in driving account risk as individuals often unwittingly expose themselves to cyber threats through their actions. And this necessitates proactive measures to address vulnerabilities and protect against various forms of attacks. So So how do you balance then customer expectations versus how they behave online? So customers expect brands to keep their accounts safe, but their actions contribute to that risk. And individuals often use weak passwords or reuse them across multiple sites for convenience inadvertently increasing that vulnerability. The next one is credential stuffing attacks. Cybercriminals leverage compromised credentials and automated attacks, gaining unauthorized access to accounts across various platforms. So security teams must implement checks during account creation to identify previously exposed credentials and mitigate the risk of automated attacks. When it comes to the rise of sophisticated malware campaigns, malicious actors are enhancing malware campaigns, leading to an increase in phishing schemes and malicious downloads. And these attacks compromise devices, and they facilitate the theft of sensitive information, including authentication data. So you really have to shift that focus to prevention strategies, and security teams need to detect malware infected users and stolen cookies to prevent those emerging forms of account takeover, like session hijacking, and to safeguard their user accounts. So too much data, not enough context is another challenge. But in this ever evolving landscape of cybersecurity, the challenge lies not only in the sheer volume of data, but also in that contextual relevance. Without sufficient insight into the circulation of sensitive data on that dark net, including stolen authentication data like passwords and session cookies, organizations remain vulnerable to account breaches and fraudulent activities. So you need that visibility and that contextual understanding. Lack of visibility into credential identity and financial data on the dark net allows attackers to exploit vulnerabilities without triggering existing security measures. And traditional monitoring tools often provide outdated information from the surface layer of the dark web, rendering it ineffective in preventing timely responses to those threats. And that timeliness is key. So intelligence on data breaches become stale quickly, increasing the likelihood of attackers having already exploited it, and taking advantage of that compromised information. So the recency and the severity of the breaches determine the urgency for criminals to monetize that stolen data, necessitating real time monitoring and response capabilities. So when it comes to the mitigation strategies, you need a comprehensive overview of exposed data and its severity, and it's essential for mitigating the impact of prior exposures, but also in preventing future breaches. And real time alerts, high fidelity alerts enable proactive measures to prevent account takeover and fraud as those criminal tactics evolve. So when it comes to challenges of data overload, security teams are inundated with excessive data, and more isn't always better. And it hinders their ability to effectively analyze and respond to threats. So operationalizing risk insights requires advanced analytics and next gen threat intelligence that can be integrated seamlessly into existing workflows but without adding an extra burden on your resources. So when it comes to the emerging threats, there's often a full sense of security. Often relying solely on reacting to known threats isn't sufficient. And with emerging and constantly evolving threats, organizations must proactively anticipate and adapt to stay ahead of cyber criminals. And this is especially crucial in addressing the threat posed by malware, which is rendering traditional security measures ineffective. So you have to be continuously vigilant and adapt your techniques and resources. And that dynamic nature of cyber threats requires organizations to constantly monitor the widening gaps in their tech stacks and exposure vulnerabilities across their entire customer base. So strategies must be adaptable and stay ahead of adversaries and really anticipate potential attack vectors. And malware has a huge impact on security solutions. Infostealer malware deployments are undermining the effectiveness of conventional account security solutions. And previously reliable measures like MFA are circumvented by malware exfiltrated session cookies, facilitating advanced account takeover attacks like session hijacking. So those sophisticated ATO techniques, it happens when a stolen session cookie is used in an anti detect browser to execute a session hijack, an advanced account takeover technique. But this bypasses traditional security measures such such as passwords, MFA, even passkeys, highlighting the need for advanced threat mitigation strategies. But all of this, you also have to consider the customer experience and how do you minimize that friction in that customer's digital experience? And balancing stringent security measures with user user experience, it's a formidable task faced by most teams, and this kind of equilibrium is crucial for fostering brand loyalty or customer trust and optimizing your business's productivity. However, achieving this balance means navigating the fine line between fraud prevention and customer satisfaction as any disruption can lead to lost opportunities. So it's imperative for security teams to make informed decisions swiftly, but without introducing unnecessary friction into customer interactions or operational workflows. So you wanna focus on that balance between security and user experience. And striking that right balance between robust security measures and user friendly experiences is vital for brand loyalty, but also for business growth. And interruptions and friction in the digital journey can result in lost conversions, highlighting the importance of a seamless user experience. So you have to also make those decisions in real time without friction. Security teams really have to be capable of making rapid decisions in real time without impeding customer interactions or even operational processes. So you have to take action with confidence and ensure a smooth experience for customers while maintaining efficient risk evaluation and mitigation processes. But you also wanna make sure that there's differentiation for tailored experiences. Adopting tools that can differentiate between low and high risk users enables businesses to tailor each customer experience appropriately. And by maintaining low transaction review rates and minimizing the risk of chargebacks and fraud, organizations can drive business forward while also preserving customer loyalty and trust. So as criminals exploit stolen data from malicious activities from fraudulent transactions to identity theft, The security of customers' accounts and their personal information is a top concern for security teams. This surge in stolen personal and authentication data traded on the criminal underground, coupled with sophisticated criminal tactics, presents security practitioners with an ever growing challenge. How do you distinguish between a legitimate customer and a criminal using stolen information? So how we protect our customers and our business has to evolve just as rapidly as the tactics that bad actors are using to infiltrate and steal data. And it's often a collaborative effort across multiple teams from application security, information security, fraud, identity, governance, risk and compliance and security operations. And it's on those teams to build programs that reduce risk while also maximizing business productivity and maintaining low friction for customers. And with SpyCloud, our goal is to ensure you can keep your customers' data safe, maintain your brand reputation, but also prevent fraudulent activity. And how we do that is by giving enterprises actionable intel fast. With the largest repository of recaptured data of digital identity intelligence in the world, SpyCloud gives you actionable insights on breached credentials, malware exfiltrated authentication data, and exposed PII powered by cybercrime analytics. SpyCloud cybercrime analytics engine delivers high volume recaptured data from the deepest layers of the dark net, curating, analyzing, and enriching it with actionable insights to deliver really only the most relevant and high quality information to security teams. Then businesses can in turn increase operational efficiency by reducing noise and streamlining otherwise manual processes. And we have over two hundred and twenty supported data types tied to a user's digital identity, including sensitive data beyond just username and passwords, and this includes physical addresses, date date of birth, government IDs, IP addresses, credit card numbers, expiration dates, and more. And unlike many other solutions available, we deliver about ninety percent of our passwords in plain text. So how does SpyCloud help you with your goals? The first one is you want to get insights that drive those confident decisions. SpyCloud provides a comprehensive view of your customer's risk by analyzing billions of data points exposed in data breaches and malware infections and correlates them directly to your user, eliminating the guesswork so you can act on what criminals know to protect your consumers' digital identities. The data is fresh and actionable, having been recaptured within days of the breach or infection, which is a stark contrast to existing solutions that often lag behind by eight to twelve months post breach. Additionally, SpyCloud offers what no other solution on the market can, the ability to identify the highest risk customers whose devices are infected with malware and the unique authentication data like valid stolen cookies that are in criminals' hands. Identifying and invalidating compromised cookies is a critical component of modern ATO prevention. The next one is you wanna automate ATO prevention with a frictionless digital experience for your customers. And while SpyCloud maintains the world's largest database of recaptured data, we believe in efficiency, not overload. Our data is curated, stripping away the noise, adding valuable context, cracking passwords, and directly correlating to risk. So the result is you get actionable insights that you can integrate into your decision making workflows. Teams can leverage SpyCloud's API to implement automated actions like enhanced authentication or password changes or session logouts to invalidate stolen session cookies, denying risky transactions or accelerating low risk users through their digital journey. SpyCloud really promotes a friction only when necessary approach to ATO prevention without the constant need for manual intervention. The next one is that we talked about earlier is tailoring the customer journey based on known exposures. Exceptional customer experiences are key to retaining loyalty in a market saturated with options. And SpyCloud's underground risk analytics make it easier to tailor the customer journey, balancing a friction free experience for low risk users while high risk users are flagged for scrutiny or subjected to enhanced authentication or approvals. So SpyCloud's data gives your team essential insights facilitating process continuity, vigilant interaction monitoring, and proactive fraud decisions for secure and seamless customer interaction. You also wanna build trust by notifying customers of exposures and show them the added value that your solution delivers and protecting and safeguarding their digital identity. So as a security team, one of your primary responsibilities is to protect consumer accounts, but it's equally important for consumers to play their part by adopting better security hygiene. And that often requires empowering users through education when their data is exposed. So notifying customers of third party breaches, exposed or weak passwords, and malware infections is becoming more common, and it really helps businesses build and foster trust with their consumers when done the right way. ICloud also offers best practice guides along with sample messaging that your teams can use to notify your customers at potential risk and offer the best guidance on remediation of those exposures. So SpyCloud ensures that enterprises have the right data at the right time to protect their consumers and their business and leveraging darknet data to prevent account takeover, forecasted targeted attacks, and predict fraud tied to malware. If you want to learn more about SpyCloud, the solutions that we offer, or to see a demo, visit SpyCloud.com, and thanks for joining our short webinar today.
- Video
Webinar: Preserving Account Integrity and Reducing ATO Risk
Hello. Welcome. Thank you so much for taking the time to join us today. My name is Ashley, and I am the growth marketing manager here at SpyCloud. So buckle up. Today, we are taking a journey to the underground to explore what is fueling ransomware in twenty twenty four. We'll dive into the most important findings from the twenty twenty four SpyCloud Malware and Ransomware Defense Report and actionable takeaways for your organization to help defend against future ransomware attacks. Alright. So here's our quick agenda for the day. First, let the journey begin. We'll start by sharing the reports origin story and some context about why we do it and what we are hoping to learn this year. Then moving on, we'll explore the landscape and the ransomware resurgence, which includes top results from our research, such as the most common industries likely to be affected by ransomware, entry points, and the current cybercrime ecosystem. Then we'll go a little deeper into what continues to drive risk. And finally, we'll wrap up by going back into the light and setting everyone on the path to a hero's journey about what your organization can focus on for prevention. Then we should definitely have a couple of minutes for q and a. So without further ado, let me introduce our journey leaders for today. First up is Trevor Hilligoss, the vice president of SpyCloud Labs. Trevor served nine years in the US army and has an extensive background in federal law enforcement tracking threat actors for both the DOD and FBI, specializing in advanced malware investigations. He is a member of the joint ransomware task force and serves in an advisory capacity for multiple cybersecurity focused nonprofits. Next up, we have Taylor Coppock, our senior product marketing manager here, bringing over a decade's worth of experience building SaaS software to transform data into action across diverse sectors. He is currently working closely with SpyCloud customers to better address cybersecurity challenges for enterprise protection. And with that, I will hand it off to Taylor. Thank you. Hi, everybody. I'm Taylor. I'm glad you joined to hear a bit more about our discussion on the journey to ransomware. But before I dive in with Trevor, we wanted to briefly introduce BiCloud. So who are we? We as a company, we exist to disrupt cybercrime. So as you can imagine, it's very important to understand latest trends and impacts of one of the biggest threats out there, ransomware. Here at SpyCloud, we collect and enrich and publish all the stolen identity data that criminals have about you and your organization so you can act on what they know about your employees. We help protect your enterprise from cyberattacks and provide a variety of use cases, but today's focus is all about understanding and preventing ransomware. So let's dive right in. Let's let's start the journey into understanding ransomware. And to understand the story today, I wanna share a bit more insight into why we do this survey itself. This is now our fourth consecutive year of creating this malware and ransomware defense report, and we surveyed more people than ever this year. To really disrupt cybercrime and know the latest trends in ransomware, we wanna make sure we're balancing our own research with what the actual organizations across the world are facing. So this year, we surveyed over five hundred cybersecurity professionals across the US and UK. These respondents range everywhere from executives and CISOs and IT security executives, all the way down to analysts and engineers and operators, and also the identity team for the first time in our report. As you can see, majority of these respondents work at very large organizations, so we wanna make sure we're actually listening and understanding what they're telling us. So what we wanna know this year in particular about ransomware itself is, again, some of the concerns these organizations face both about malware and ransomware as well as how they're currently trying to defend against these cyberattacks. We also are leaning into something new this year. We wanna know what were most common entry points from organizations who were hit with the ransom to know how criminals are trying to steal this initial access. Then, of course, you wanna know the actual impact, the monetary, the time impact of these ransom attacks on organizations while understanding what they're trying to do to prevent attacks and where their future security priorities lie. So on that note, I'm gonna pass to Trevor to cover a bit more about the whole cybercrime landscape at large. Thank you, Taylor and Ashley, for starting us off. We start our journey with two major trends that have converged over the past eighteen months and which are playing a large role in shaping the landscape we find ourselves in today. First off, ransomware, unfortunately, saw resurgence as a frequent and damaging attack method increasing in prevalence in twenty twenty four. Ransomware remains the leading cybersecurity threat across every industry we examined. The number of organizations who said that they were affected by ransomware at least once rose from eighty one percent to ninety two percent, and those affected more than once grew even more significantly from sixty one percent last year to seventy five percent this year. The average cost is almost five million dollars. And, unfortunately, our data shows that year over year significantly more organizations paid a ransom, sixty two percent this year versus forty eight percent in last year's report. Even more troubling, only about a third of those organizations fully recovered their data, which is a stark reminder that giving into cybercriminals' demands is a gamble, and the odds are not always in your favor. In some cases, cumulative costs can extend to general disruption, loss of business and opportunities, productivity decreases, reputational damages, and more. For instance, we found in an average successful ransomware attack, forty nine percent of an organization's computers are impacted in some way, which can obviously impact business functions. Third party exposure is fueling exponential risk across the board. We'll dig a little deeper into these risks in a bit. The presence of an Infostealer infection leads to future ransomware attacks. We found that nearly one third of companies that experienced a ransomware event last year had at least one Infostealer infection in the sixteen weeks prior to the attack being made public. We'll definitely talk about that in a few slides. The second trend we saw is that more commonly, cybercriminals shifted to next generation tactics, using data exfiltrated by infostealers to gain initial access for follow on attacks like ransomware, which we'll also cover in short order. Now the cybercrime ecosystem is vast, and we don't have time in this webinar to explore all of its parts. Nonetheless, let's quickly discuss some of the more significant components. Mower as a Service describes the commodification of malware, Much like legitimate software as a service enables professionals to access tools and services that they couldn't code themselves, malware as a service enables less technical criminals to gain access to sophisticated malware and the capabilities necessary to launch it in an alarming scale. Install brokers work hand in hand with criminals, enabling their malware to spread far and wide. These brokers have a vast network of compromised websites and ads that can deliver malicious executables disguised as messaging applications, game sheets, free software, and more. Next up, the initial access brokers often take the proceeds of successful infostealer infections and resell that access, sometimes with guarantees, to other criminals, especially ransomware operators. Now These brokers aren't limited to using data exfiltrated by infostealers. However, data stolen by infostealers remains a critical component to the access broker. Lastly, ransomware as a service enables large affiliate networks of criminals who often operate independently while still being able to benefit from established malware, command and control networks, and leak blogs. Taken as the whole, the cybercrime ecosystem poses a significant threat to our connected world. Let's talk infostealers. Our research highlights how infostealers have become a critical part of the ransomware supply chain. To further investigate this, we conducted an analysis of publicly announced ransomware events over the past year and correlated those events with infostealer infections that preceded them. What we found was alarming. In nearly one third of the events we analyzed, we found at least one infostealer infection of an enterprise account, often including SSO or some other centralized authentication service, prior to the ransomware event. When we look at which malware families had the strongest correlation with a subsequent ransomware event, a few stood out. Lumacy two topped the list and is one of the most sophisticated info stealers on the market today. It also benefits from constant development and wide market adoption. Redline remains a juggernaut. However, it is notably less feature rich than LumaC two. Nonetheless, as one of the older stealers on the list, it enjoys wide use in criminal communities and benefits from name recognition. Steel c is a relatively recent addition, but one that has been quick to adopt cutting edge methods for theft and detection evasion. I'll also give an honorable mention here to Atomic, which is noteworthy for being the first macOS targeted infosteeler to see widespread success in stealing data from Apple devices. And all of these infosteeler families, regardless of their individual characteristics, are important because they massively lower the barrier to entry for cybercriminals. This off the shelf model for a variety of malware, and especially infostealers, enables even low skilled or no skilled cybercriminals to steal fresh and accurate identity data in bulk, including login credentials, session cookies, files saved on a device, and that device's details. Basically, everything needed to impersonate an identity. So let's dive in a little deeper to these findings. What's driving risk? Alright. Deeper we go into some of the the risk we see. So this year, we we asked those organizations who had been affected by ransom. Again, not just the impact of time and money, but we wanna know what happened before the ransom attacks. So we actually had information with organizations of what were the entry points used by attackers to gain this initial access. So the top three that stood out among all of the data points, really number one, the continued reliance on phishing and social engineering tactics. Followed up by number two and three, all about third party access and stolen session cookies that enable session hijacking. So in terms of general perception, no real surprise that phishing, social engineering still top of the list since it still comes down to people at the end. However, like, the focus only on remediating and handling that entry point is is not the only way forward since to fully combat the scope of ransomware attacks, we need to know a bit more about the other entry points that have really shown up in the data. And the second one being all about the risk of unauthorized third party access. We've seen a lot of SpyCloud, so I'm I'm not shocked to see this mark so highly from our survey respondents. But as criminals look for all the ways to gain the upper hand in in the malware landscape and launching ransom attacks, another opportunity is all about these malware infected third party devices and unmanaged devices. Of course, the respondents, the identity teams are really the most concerned of the risk this brings. From the survey, almost one hundred percent of those surveyed really worry about the risks from third party path third party third party accounts that come from these malware compromised devices. Primarily, these devices that are really outside of corporate control just make it so much harder to detect what's happening, much less remediate because they're outside of IT control and visibility with limited security practices for these devices. Now, when you have access to these third party applications along with the ones you manage yourself on these unmanaged and third party devices, there's so much information that criminal can use to gain access, advance privilege, then eventually deploy rank and attack. However, we still had teams really rank this capability and priority to really detect when there are infected third party devices quite low compared to other tactics. Here at SpyCloud alone, and Trevor has more information on this, of course. Last year, we were captured of four point seven million popular third party application credentials from malware infections. So whether they belong to an employer or third party contractor, criminals using this access to really follow-up with targeted attack. We also thought that on average, a single malware infection exposed access anywhere between ten and twenty five business critical DApp applications. Scary stuff. So next generation account takeover, which uses session hijacking instead of relying on traditional credentials, allows threat actors to sidestep all types of authentication. It can bypass the process entirely. This includes MFA and passkeys or a passwordless login. By hijacking user sessions that have already been authenticated, cybercriminals, including ransomware operators, become a clone of an illegitimate employee without setting off typical intrusion alarm bells. This greatly increases their rate of success in gaining access to an organization's network and systems to launch an attack. In our most important countermeasures to combat ransomware, data backup and endpoint or device protection have maintained their position on the list of the most important countermeasures from last year, while MFA moved up six spots to number two on our list. This suggests that MFA adoption is now more mainstream, but it's also a cautionary tale. Cybercriminals are adapting to current trends, and as we've seen in this past year, they're targeting MFA. With Infostealer siphon session cookies, they can simply hijack the session and bypass even the most robust MFA setup. Some critical session cookies can remain valid for weeks, months, even longer. A big target are session cookies for email providers, for example. Since many of these organizations don't yet monitor for cookies stolen by infostealer malware, let alone invalidate those sessions, a single infection could leave an organization exposed for a relatively long period of time. When leveraged by ransomware perpetrators, this access can come with immense consequences. Unfortunately, we expect to see session hijacking continue to gather momentum. And the more organizations are aware and prepared, the better off they'll be. Now based on recaptured data and malware logs tied to the industries we surveyed, as well as previously self reported ransomware attacks, Spy Cal out has constructed a model using machine learning to identify the industries with the greatest risk of future ransomware events. Now probably saw a poll pop up on your screen. Go ahead and answer that before we continue. We're very interested to hear your opinions on which industry or industries is the most likely to be targeted by a future ransomware attack. What are we – Actually, I can't see the respondents, so just let me know when, we have quorum. Let's see. What are they saying? What are they choosing? Yeah. It's looking like so far on health care is the, front runner with seventy three percent of the votes. And, actually, other is next, with eighteen percent followed by insurance with only nine percent. So with that, we will end the call and then, go and see what the actual results are. Yeah. Interesting. Well, I would like to hear if if you're if you're willing. If you answered other, go ahead and drop maybe a question or or in the chat. I'm not sure how Zoom functions there, but I'd I'd be interested to hear what your what your, specific industry for other is. Based on our data, we, we did find health care was, up there, certainly, but not number one. And even more surprisingly, seventeen percent of health care respondents reported not being affected at all by ransomware last year. However, based on our prediction modeling, as I mentioned, health care is one of the industries with the greatest risk of future ransomware events in twenty twenty four leading into twenty twenty five. In fact, it's about two times more likely to experience a ransomware attack. Now the sector we found to be most at risk, and you guys highlighted this in the poll, is insurance. Insurance is more than six times as likely to experience a ransomware attack in the remainder of the year. Only three sectors Manufacturing, Retail, and Technology rated improved man ransomware prevention capabilities among their two main priorities in the next twelve to eighteen months. Okay. So now the positive part. As we now continue the journey into the light, we're gonna talk a bit more about some of the optimism we saw from our own research and from the respondents and how we can help really prevent these ransomware attacks. The first tip to share, honestly, is reflecting internally. We saw quite a perception mismatch among the survey respondents with their overall confidence of their organization's ability to really prevent a a full blown ransomware attack. So majority of the security executives felt very, very confident, over ninety percent of their ability to prevent this full blown attack. And these executives were also much more confident in their whole company's ability to both respond to malware infections and ransomware attacks. But we saw the data was quite different across the other teams. Identity teams are also a bit more confident. They've all been a bit more aware of some of the risk from third party exposure, malware infection in general. But we saw some disconnect with the actual operators, incident responders, and analysts being a little less confident. So, again, we just wanna really promote that you really align internally and self reflect on your own capabilities to detect malware infections, respond to that, to prevent ransomware attacks, especially as we look into planning for priorities and tactics and projects for next year. And on the disconnect piece, a bit more about the malware capabilities we've seen. Yeah. Thanks, Taylor. So security researchers found that as many of ninety percent of security compromises originate from unmanaged or undermanaged devices. I don't think that's any surprise. Outside of IT control and visibility and with limited security, these devices hold an undeniable appeal for threat actors. Unfortunately, detecting third party or unmanaged devices infected by malware is the capability organizations lack most today. Without visibility into these exposures, it's difficult for an organization to fully understand its risk and properly defend itself. Now even if you don't have a bring your own device policy, which I hope you don't, be aware that modern browser sync capabilities are often the culprit in allowing enterprise logins to be copied out of your monitored environment and onto a personal device. This device can then be infected by malware, and those enterprise credentials can be siphoned out. Unauthorized third party access is high on Teams' radar, rated as the second most risky entry point for ransomware in this year's survey. By improving visibility into malware exfiltrated data, including unmanaged and third party devices outside of the traditional corporate oversight, you'll have more complete coverage and faster discovery of exposed applications and therefore drastically reduce your time to remediation. And you might even reduce the likelihood of being a victim of ransomware in the first place. Overwhelmingly, our respondents agree that having better visibility of malware exfiltrated data, such as exposed credentials and session cookies or tokens, and automating remediation workflows would significantly improve their organization's resistance to ransomware attacks and their overall security posture. Back to you, Taylor. Hey. Another tip also speaks to the data but we also talking about device device device all morning. And speaking of this data and this recapture stolen data, we believe there's a paradigm shift needed to shift away just from thinking about device focus but more towards this identity centric approach. It's really important to have visibility into all the stolen data out there to connect what makes up this holistic digital identity for your workforce and your supply chain. We've seen it quite often that criminals are now moving beyond traditional use of stolen username and password pairs alone for their attacks. Criminals now have this expanded dataset to use to really increase the scope and veracity of their attack patterns based upon all the stolen identity records that come from a variety of sources of breaches and malware infections that criminals are now linking together to really help create synthetic identities and personate accounts. We have the information to really target this access that Trevor spoke to. Using everything from, of course, credentials and usernames, but PII, social handles, backup emails, street addresses, Social Security numbers. There's so much information that criminals are now targeting because as you saw a few months ago, the massive NPD breach. This is all over our radar. We know the extent of one of the largest breaches in history where if I thought alone ingested over two point seven billion identity records, it says that is the it's something with this breach. So I know my exposure. I know what information is now in the criminal's hands of my own past and blending my digital identity. But it's up to now that the security teams really move towards this identity focused approach to have this timely definitive evidence of exposed identity data to really go beyond the the device to know that when there is an infection or exposure, you know all the pieces and all the assets that criminals are using to gain access to really prevent them in their attacks. And our final tip, as you can imagine, comes back to malware. We believe strongly that ransomware itself is a malware problem at its core. And there are some good trends, some good news within all the data and our own research. More teams, as Trevor showed, strongly agree they need its visibility into malware exfiltrated data. They have the right steps to get this data, and they're slowly moving towards adopting full remediation steps. But we still saw a lot of respondents say that the primary action is just a brute force reset and wipe situation. Well, that doesn't work when you're trying to address the larger identity access that criminals have, much less the the risk of unauthorized third party access and devices you don't manage. Trevor showed the risk of session hijacking. Now we saw that identity teams really are more in tune with these identity attacks and more on the frontline of detecting and preventing this. But we want to make sure you have this malware post infection remediation playbook ready. That comes down to two things. It comes down to really understanding and identifying all the exposed business applications that your organization runs, even those that you don't manage, but all the fast third party apps because that exposed access unlocks a lot for the criminals. But also comes down to these active stolen session cookies and compromised web sessions. I've missed information to know, again, what access is out there, but making a plan to know how and when to remediate and the impact of resetting those sessions, what it has on your employees, your customers, and organization. So So it comes down to detecting these compromised credentials and these compromised session cookies. Majority of the teams we saw are reviewing the logs of what's been exposed and terminated open sessions, but it's both having the data and the remediation path in play. Just resetting and wiping and quarantining is a step. We wanna want to broaden the whole malware post infection and know how you can actually detect stolen access and make the proper plan for your organization. So, in closing, we see some great trends in the next twelve to eighteen months to improve malware detection, remediation capabilities, all about visibility and this compromised access for criminals. Now before we shift to q and a, I do want to highlight in the chat, we've shared a a fun infographic that kind of highlights the latest trends and insights from this year's report. But I also encourage you to download the full by cloud malware and ransomware defense report. There's so much information that myself and Trevor could not get to today. I want you to read this really help with your own priorities for next year and just feel confident about your ability to prevent these attacks. So let's more of a chat. Let's see what questions you have, and ready to help us, really close the journey out together. Let me move on, and let's wait a second to see what is top of mind for this audience. Awesome. Thank you. That was so great. I know it's a lot of information to digest. But feel free to drop any additional q and a in the question box there. To start, Trevor, I'm gonna throw this one your way. Can you give some general best practices for how to avoid session hijacking? Sure. So the biggest point that I will make there is most sessions, most cookies are gonna have, time to live. Right? They're gonna have an expiration date on them. Now, sometimes that's not user configurable, but oftentimes it is, especially in the case of more popular SSO providers. You can actually configure, how long that cookie will live before it, is expired. I would encourage everyone, and I understand this is kind of a, trade off between user experience and security as are a lot of things in life. I would encourage everyone, if you have the ability, make that time to live as short as possible, especially for things like SSO. Email is also a huge target for criminals that are deploying, Infostealers. If you think about if somebody gets into your email inbox, you know, think about the ability to reset passwords or even just enumerate all the services that you use, in kind of a similar way that that SSO can be used in that way. So, definitely decrease those those TTLs as much as you possibly can for all of the the cookies that you have the ability to do so. Awesome. Thank you. Okay. Next question. Trevor, I'm gonna throw this one your way as well. We use independent contractors all the time. How can we get ahead of making sure they don't pose a risk to our business? Yeah. That's a good question. So this this is hard. Right? We we have a pretty good way we we do pretty well at securing, you know, the devices that we manage, the full time employees that report directly to our companies. We can install endpoint, monitoring. We can, you know, monitor their, you know, their their device activity. Gets a lot harder when you have people that don't necessarily work for you as a company or maybe they're not using, you know, devices that you manage. So I would say the the big thing right there is really of of, awareness. Right? Be be be cognizant of the employee, of the contractors that you're using. Obviously, limit their scope as much as you possibly can, but have some way of monitoring if and when they become exposed. And realize that that might not actually include any of your domain information, you know, on its face. We might not see a, you know, spycloud dot com email address if this is a contractor, but that doesn't mean that that info stealer or whatever malware hit that endpoint, didn't pull some proprietary information that it might have been downloaded and saved. So definitely monitor, definitely limit their scope as much as you possibly can. Those are some pretty good, good policies there. Great. Thank you. So to add on to that, a follow-up question was, do organizations overlook dark web monitoring? It's kinda hard to answer conclusively. Obviously, we're a bit biased in that, that question too. I mean, I think it's easy to overlook. You know, when we say dark web, it's really a kind of a misnomer. Right? We're talking about, obviously, yes, the dark web, Tor, you know, ITP, whatever other, networks exist. But we're also talking about clear web websites. Right? Breach Data gets shared on Twitter. We're talking about malware app, I'm sorry, messaging applications. Right? Telegram or or Discord, for example. So, you know, it's a huge it's a huge area, to cover. And so being able to do that on your own is is very difficult. Of course, that's why companies like SpyCloud exist, and we'd be more than happy to to help you with that. But, I do think it's it's it's heartening to me to see that more people tend to be talking about this over the past couple years than than historically. So there's more focus on this, and and hopefully that will, lead to more awareness, that that there are risks out there and and how to remediate those risks. Awesome. Thank you. Taylor, I'm gonna throw one your way. Of the key takeaways, if you had to pick one place to start slash implement, which would you choose? Okay. Well, ever since the NPD breach, identity has been top of mind for me, both as a human, just knowing what's been exposed. I think it really comes down to this shift of thinking of identity access and all the information that criminals could use to really take over access of of my life and my my corporate access. So I think it really comes down to the data and understanding the connections criminals could make to broaden the scope into a digital identity. So, again, if there was an infection on any kind of device or any kind of contractor or an employee, just knowing what what's really stolen, what's available that's beyond just, again, my username, my password, to really think more about identity at large and understand how that can be used to gain unauthorized access to then think, well, how would I detect this? How would I know all the assets that make up an identity to actually then, again, monitor and detect and get ahead of that? So, really, all about identity, that's been just top of mind for me. Awesome. Thank you. Trevor, if any stolen company data is detected on the dark web, could it be removed from there? Short answer, no. The Internet is forever, for better or worse. Now that's not to say that, you know, things things fall off all the time. Things are posted on very niche corners of the Internet and and, you know, maybe those get taken down or they're never archived. But, really, in my experience, once data is exposed, whether it's exposed in a Telegram channel or Russian cyber criminal forum or, you know, Twitter, It's, you know, it spreads from there. Right? The, the the the the the Internet is highly transitive and, especially when we're talking about threat actor communities. You know, there's this whole I could I could talk for hours about this. There's this this whole, you know, ecosystem that that thrives off of, you know, criminals basically sharing information with each other. Sometimes it's for monetary gain, oftentimes it's for clout. But, you know, one one one data breach gets posted, we see it, you know, on, XSS, for example, Russian language, cyber criminal forum. And then we can we can track that at that one breach over the course of the next several months. I will see it pop up on a Telegram channel one week and a Discord server the next week, and maybe it shows it up on another forum the week after that. It it it kinda gets a mind of its own. So that that's why we're really big proponents of the, awareness part of this because, you know, obviously, there are certain things. If your Social Security number gets exposed, that's hard to change. But, you know, if it's password, if it's a cookie, if it's an API key, you know, typically, we we have a a reset path. Right? There's some way, either your, you know, IT administrator or maybe your you yourself can go and change that password, invalidate that cookie, reissue that token. And obviously, it doesn't change the fact that that information was out there, still is. But the next time it gets shared, the next criminal that tries to use it, they're gonna be a lot less successful. So, when we talk about remediation, really, we're talking about awareness, identifying the exposure, and then doing whatever you can to make that exposure less valuable to the criminals. Awesome. Thank you. Okay. One more question, Trevor. If we experience a security incident slash ransomware attempt, can SpyCloud be used to investigate the root cause? Hopefully. You know, I can't can't speak to every single incident ever. SpyCloud my my organization, SpyCloud Labs, we're the we're the research part of SpyCloud, and we collect a massive amount of data every single day, malware, breach records, phish data, etcetera. So, you know, oftentimes, we have had great success working with our clients to, you know, identify where that initial exposure came from. If it's malware, you know, we can give you that information and and let you know what else was stolen at the same time, which can be super valuable, of course. In the case of ransomware, you know, root cause analysis tends to, you know, look for patient zero, what was the entry point. Like we covered kind of in the remainder of this webinar, a lot of times that's info stealers or some other malware, by way of maybe an access broker. So those are things that we can call out, definitely. And, I mean, bottom line, look, we're we're in this fight together. I think everybody has to kinda be part of the same team for us to succeed. So, we'll help however we can, even if that's just kind of looking at all the information and recommending some next steps. Awesome. Thank you. Okay. So, yes, we will be, sharing the slides or the the video, I'm sorry, of this. We will get that out to you as soon as it is available. And then, Taylor, if you could move on to the next slide. We have one more action item for you if you wanna speak to that, Trevor. Sure. So, this is a a service we launched a while ago. Highly recommend everybody take a look at it. So if you're not aware, you know, Spikelet enhances critical aspects of your security defenses to safeguard your sensitive data against next generation cyberattacks. That's what we've been talking about this whole time. If you wanna get a glimpse into the power of cybercrime analytics, you can start by checking your enterprise exposure. If you use this tool, we'll reveal real time insights on exposed employee credentials that are in the hands of criminals and share the results, including any previously unknown exposures that SpyCloud illuminates. So in that question that we had about, can SpyCloud help me with RCA, definitely encourage you check out, check your exposure and, see what it see what shows up there. That's a good good place to start. So once you do this, you'll receive a custom exposure report that'll include an overall security risk score for your business based on SpyCloud's data. That also takes into account malware infections and plain text passwords. We'll give you account of malware infected records associated with employee email addresses, which may indicate active infections and exposed active session cookies. We'll also share share insights into third party breach records, exposed executive and VIP credentials, estimated password reuse, and PII exposure for your employees. And we'll share specific breach and malware sources with details on when SpyCloud published the data to customers and the compromised data types. So if you have questions, you can absolutely find us during the networking session, or you can reach out to us by email. Okay. We have one quick question. I'm hoping you you can answer, Trevor. Is this GDPR compliant? Yes. It is. Okay. Awesome. Okay. Well, thank you so much to everyone joining us today. Please go check your exposure. And then if you have any other questions, please feel free to reach out. And I hope you all have a wonderful rest of your day. Thank you. Thank you. Keep coming, folks. Thank you. Have a great day.
- Video
Webinar: Journey to the Underground: Insights Into What’s Fueling Ransomware in 2024
This webinar breaks down the most important findings from The SpyCloud 2024 Malware and Ransomware Defense Report and what your organization can do to get ahead of emerging cyber threats.
- Video
Ransomware Reality Check: The New Landscape
This webinar breaks down the most important findings from SpyCloud’s 2023 Ransomware Defense Report, and what your organization can do to get ahead of emerging cyber threats.
- Video
Don’t Play Footsie with Cybercriminals
On-Demand Webinar: Unveil the top darknet exposure trends for London’s FTSE 100 companies, including insights on password reuse, stolen session cookies and cloud app exposures
Infographics
Videos
- Video
SpyCloud Supply Chain Threat Protection
- Video
About SpyCloud Video
- Video
2025 Identity Threat Report: A Discussion of Key Findings
- Video
Close Investigative Gaps Faster: SpyCloud Investigations with AI Insights
- Video
2025 SpyCloud Report: Holistic Identity Exposure Trends
- Video
The Power of SpyCloud Investigations
See how you can leverage SpyCloud Investigations to build comprehensive cybercrime investigations and protect your enterprise from identity-based attacks stemming from your employees, customers, and suppliers’ darknet exposures.
- Video
Continuous Zero Trust with SpyCloud
Traditional Zero Trust policy engines only test the validity of users and devices when they first access the network, missing the vast amount of identity, device, and access information that criminals already have.
- Video
Reverse Engineering Atomic macOS Stealer
- Video
The Mother of All Breaches Data Leak
In this video, our team at SpyCloud Labs discusses the monumental “Mother of All Breaches” (MOAB) Data Leak that shook the security community. Watch to learn about the 26 billion record data leak, the extensive analysis by SpyCloud Labs, and highlights covering the intriguing findings.
- Video
360 Privacy | SpyCloud Customer Success Story
Hear how 360 Privacy leverages SpyCloud’s suite of holistic identity protection solutions to protect more than 1,800 individuals and their digital footprints – reducing risk from dark web exposures and protecting against targeted attacks.
- Video
Webinar: Access Granted: The reality of compromised credentials in a passwordless world
Explore the evolution of authentication and scrutinize common myths around passwordless technology.
- Video
Webinar: From Zero to Hero: What Your Security Team Can Unlock with Actionable Data
- Video
Webinar: C is for Cookie: The Missing Ingredient in your Zero Trust Recipe
Learn how to address a common Zero Trust implementation gap that is leaving organizations vulnerable to targeted attacks: users’ stolen session cookies.
- Video
Webinar: An Inside Look at Game-Changing Threats in 2024
In this webinar, we cover top trends from the SpyCloud 2024 Identity Exposure Report. Learn about the identity threats putting organizations everywhere at risk.
- Video
Webinar: Consumer or Criminal? An inside look at SpyCloud’s Consumer Risk Protection for Financial Services
This demo/webinar shows how SpyCloud helps financial organizations safeguard consumer digital identities and stop high-risk attacks tied to malware.
- Video
Webinar: Consumer or Criminal? An inside look at SpyCloud’s Consumer Risk Protection
This demo/webinar shows how SpyCloud helps eCommerce organizations safeguard consumer digital identities and stop high-risk attacks tied to malware.
- Video
Webinar: Preserving Account Integrity and Reducing ATO Risk
- Video