Underground data – the missing component of your fraud prevention framework
SpyCloud helps enterprises preserve profits and unlock revenue by delivering actionable, predictive fraud risk insights for their consumers based on breach and malware data recovered from the criminal underground.
WHO USES SPYCLOUD?
Stop hard-to-detect fraud with actionable analytics from the deep and dark web
Prevent
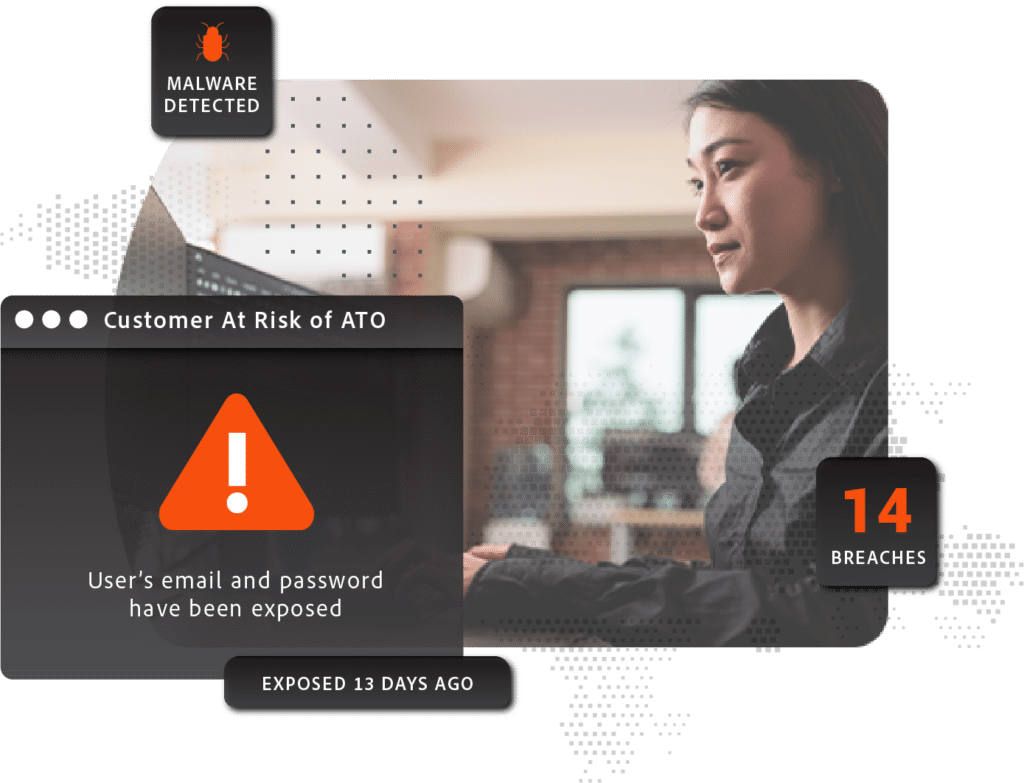
ATO fraud
Prevent fraudulent account creation using previously exposed credentials – with real-time alerts as soon as consumers’ exposed data appears in the criminal underground
Detect
compromised accounts
Leverage recaptured malware data to alert enterprises when consumers’ web sessions are compromised so they can react appropriately to prevent session hijacking
Preserve
customer trust
From account creation to digital transactions – safeguard your consumers’ digital experiences to ensure brand loyalty and trust
Make more informed fraud decisions at scale
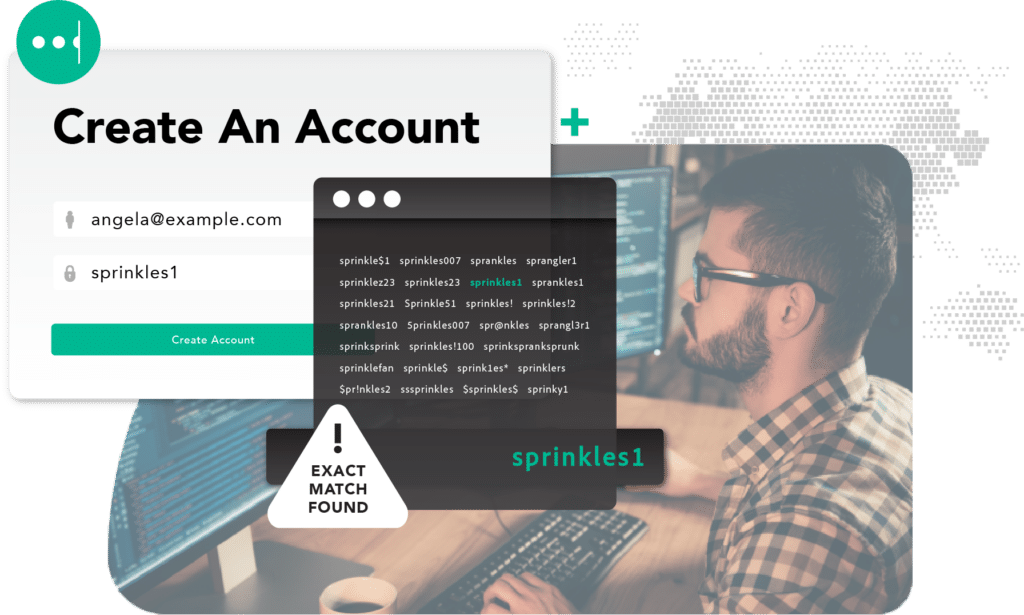
SpyCloud’s data empowers businesses to prevent fraud losses by preemptively identifying exposures within the criminal underground that can be used by criminals to take over accounts.
Preserve profits, optimize resources
SpyCloud’s unique ability to detect malware-infected users strengthens defense mechanisms against emerging ATO techniques. This proactive approach to securing customer accounts not only boosts customer loyalty and reduces attrition, but allows for better allocation of analyst and fraud prevention resources.
Take action with confidence
Enable fraud teams to increase confidence in their fraud prevention frameworks and risk models with a detailed view of a customer’s exposures across the darknet. Insights into no exposures vs recent and high-risk exposures allows fraud teams to enhance the accuracy of their risk assessment and automate the user's journey.
Better data, increased efficiency
SpyCloud delivers high-volume, fresh, actionable breach and malware data via performant APIs for easy integration and automation within your existing applications, workflows, and predictive models to prevent fraud – enabling faster and better fraud decisioning for manual reviews and post-fraud investigations.
Dynamic thresholds, better experiences
Fraud teams can tailor the customer’s journey based on their individual risk, allowing users with little to no exposures to interact friction-free, while implementing the appropriate step-up authentication for compromised accounts – even blocking transactions or logins for highest risk, malware-infected users.
“Since SpyCloud recaptures credentials directly from the criminal underground, we now have a level playing field with fraudsters – with the same data, we can easily identify compromised consumers and be more proactive in protecting them.”
– Ecommerce Marketplace Leader
Explore SpyCloud
Enterprise Protection
Reduce your risk of ransomware and other critical attacks – acting on known points of compromise
Learn more
Consumer Risk Protection
Take a proactive approach to combating account takeover and stop high-risk attacks tied to malware
Learn more
Investigations
Efficiently piece together criminals’ digital breadcrumbs to reveal the identities of specific adversaries engaging in cybercrime
Learn more
Data Partnerships
Access comprehensive breach and malware data to add value to security and fraud detection products and services
Learn more
SecOps
Efficiently secure employee identities and safeguard corporate data and critical IP from cyberattacks.
Learn more
Threat intel teams
Investigate and stop threats with insights well beyond raw data and IOCs
Learn more
Cybercrime Analytics
Learn about the new way to disrupt cybercrime with automated analytics that drive action
Learn more
Test our data
We’re confident you’ll get more matches with SpyCloud – let’s do a match rate test
Learn more
Check your exposure
Uncover threats to your organization like malware-infected employees, stolen session cookies, and recency of breach exposures
See your results
Fight back against fraudsters
Dive into a case study
Learn how a Top 10 Online Travel Booking Site discovers up to 11,000 exposed consumer accounts every hour.
Connect with us
Experience how SpyCloud can help you prevent fraud without impacting the digital experience.
