SpyCloud's Cybercrime Analytics Engine
Making raw data recaptured from breaches, malware, and other underground sources actionable
SpyCloud continuously ingests and intelligently analyzes stolen credentials and personally identifiable information (PII) from the deepest layers of the darknet – totaling more than 25 billion assets every month from data breaches and malware-infected devices. Our proprietary Cybercrime Analytics Engine turns raw, unstructured formats into actionable insights, quickly identifying exact-match exposures of compromised passwords, cookies, and identity data. With these insights, SpyCloud powers prevention solutions for account takeover, ransomware, and online fraud.
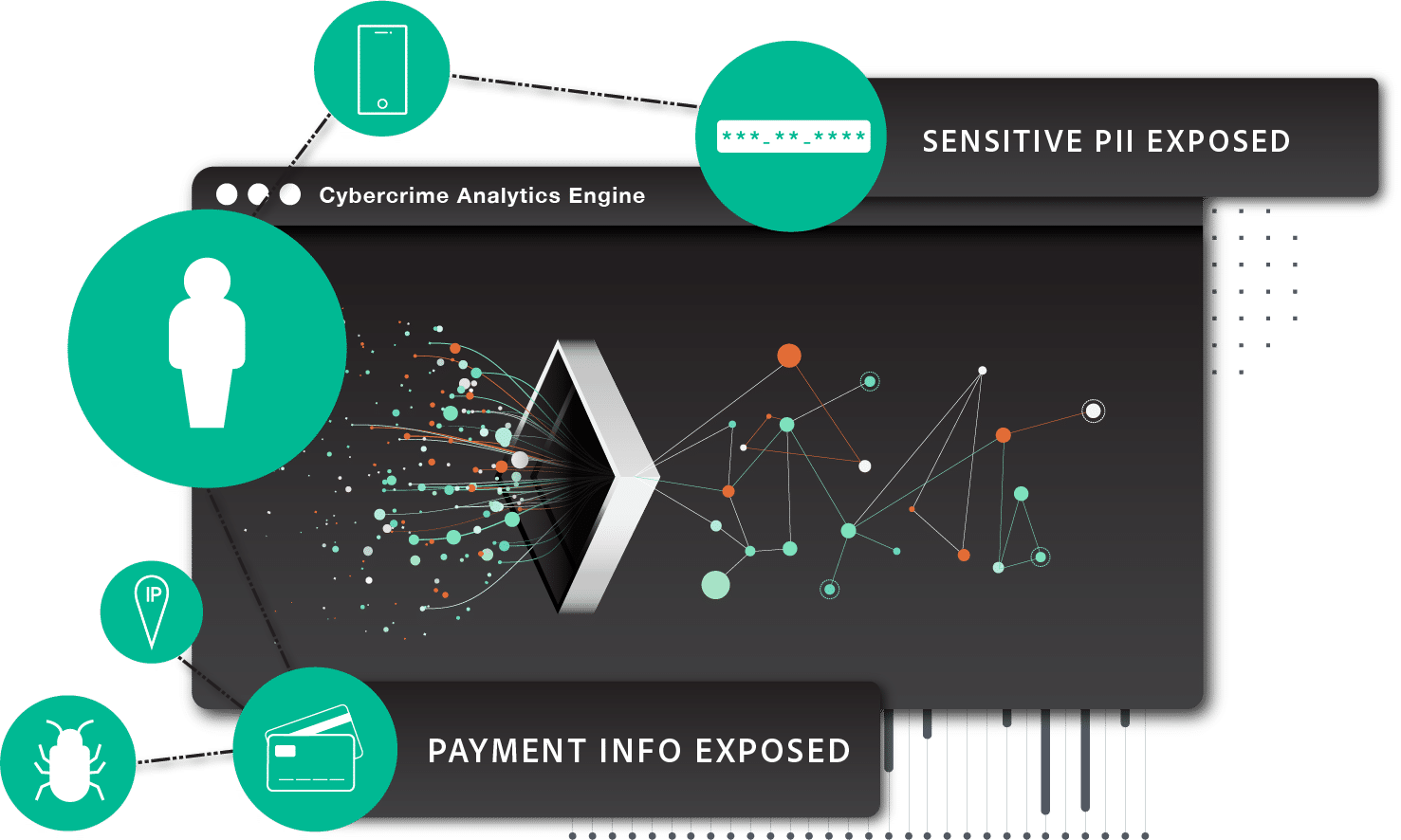
HOW IT WORKS
Cybercrime Analytics Engine
SpyCloud built and maintains the industry’s largest data breach and malware repository of recaptured darknet data that powers ATO, ransomware, and online fraud prevention solutions. But our Cybercrime Analytics Engine goes beyond data collection. After each digital asset is acquired, it is put through a rigorous quality control process to determine its value. We cleanse and parse the datasets, crack passwords and further enrich the data to then correlate it to individual user identities across their multiple online personas to determine their true risk to your enterprise.
The result is actionable insights relevant to your business that you can act on quickly – via integrations into your existing security stack – to shut down cyberattacks.
Collect – The world's largest collection of recaptured data
We rapidly collect stolen and leaked assets from the darknet containing user credentials, cookies, and high-value PII such as first and last names, addresses, phone numbers, dates of birth, SSNs, credit card numbers and much more. This type of data can be used by criminals to easily impersonate users and harm individuals and businesses.
Our collection methods use a combination of security research and automated technology. Our team of researchers have been performing this type of tradecraft for years and are the most capable in this area. Critical information is recaptured by our researchers very early in the attack timeline, often within days of a data breach or malware infection occurring. In many cases, we are the first to inform the affected victim organizations through our responsible disclosure process. These efforts create the world’s largest, continuously updated repository of information gathered from breaches, malware victim logs, and other underground sources.
Curate – Remove noise and extraneous alerts
The Cybercrime Analytics Engine parses and normalizes petabytes of unstructured data, discarding records that do not contain passwords or high-value PII. It compares each record to the billions of assets already in our database. We end up discarding about 60% of the files we collect as duplicates from past breaches that have been repackaged as combo lists. This ensures that our customers are not inundated with extraneous alerts.
Through this process, SpyCloud manages more than 240 distinct attributes collected directly from darknet records that are machine-readable and immediately actionable.
Enrich – Robust context, cracked passwords, more insights
SpyCloud goes further than any other vendor to enrich the recaptured data with supporting contextual information including the source, breach description, and the actual breached password. We have invested heavily in “de-hashing” collected passwords, allowing customers to determine whether exposed credentials exactly match the in-use credentials for their employees and customers. This process lets us provide more than 90% of collected passwords in plaintext, making our data the most actionable in the industry.
In the case of malware-exfiltrated data, SpyCloud provides all relevant context including the machine ID, IP address, infected date and time, and infection path, as well as target URLs, credentials, and cookies for critical workforce applications that have been siphoned and are in criminals’ hands. Acting quickly to invalidate this information with Post-Infection Remediation is crucial for stopping malware infections from becoming full-blown ransomware incidents.
Analyze – Identity–centric risk correlation
Our Cybercrime Analytics Engine draws correlations across billions of records that have been stolen and distributed by criminals, revealing a comprehensive view of your employees’ and consumers’ identities and online behaviors. This allows more confident decisions on whether to enable access, reset passwords, use enhanced authentication, or monitor accounts for suspicious activity. On average, if exposed once, an email address appears 8-10 times in our dataset. By linking these individual appearances across multiple breaches and malware infections, we deliver unique insights about your users’ holistic risk of account takeover, synthetic identity, and fraud tied to malware.
Automate – Drive action to protect digital identities
SpyCloud’s insights are accessible in our Cybercrime Analytics platform, APIs that can be embedded into your workflows and applications, or via integrations to popular directory services and security tools to protect your enterprise from criminals using stolen information to impersonate your users’ identities.
The new way to fight cybercrime
SpyCloud turns the tables by making darknet data work for you. We detect when your employee and customer credentials, cookies, PII and other critical stolen assets are in the hands of cybercriminals and automate remediation to reduce your risk of cyberattacks.
Assets
Breaches
Families
See the data we have on your domain. Discover breach and malware exposures, stolen cookies, password reuse and more.
Interested in integrating SpyCloud data to enhance your solution?
