There’s a problem with the way cybercrime and identity threat investigations have been conducted to date. And it’s not analysts’ fault.
With the rise in volume and types of data at their disposal, analysts navigating the complex OSINT environment face the challenge of weaving together a variety of sources and tools, ideally paired with a data science degree and scripting expertise to get the most accurate insights.
We know this pain well – our team of seasoned investigators with decades of experience actively working to disrupt the cybercrime economy have spent their fair shares of hours compiling and adding domain knowledge to various tools and workflows. They’re experts at pulling on any and every thread to get a good outcome. They know exactly what questions to ask, using every available tool and dataset to get the answers. They’ll do whatever it takes to identify cybercriminals’ patterns of life and real world identities, insider risks, VIP and supply chain exposures, and platform abuse, alongside our customers.
But it’s 2024. It shouldn’t have to be this hard.
We knew we could do better for our own investigators and for all the other CTI, SOC, and fraud analysts and investigators putting in the blood, sweat, and tears to combat cybercrime.
So we did. Today we’re proud to share the new and improved SpyCloud Investigations solution with our proprietary IDLink advanced analytics built right in. The result is unparalleled access to previously unknown information and massive time savings.
Introducing the new SpyCloud Investigations Portal with IDLink advanced analytics
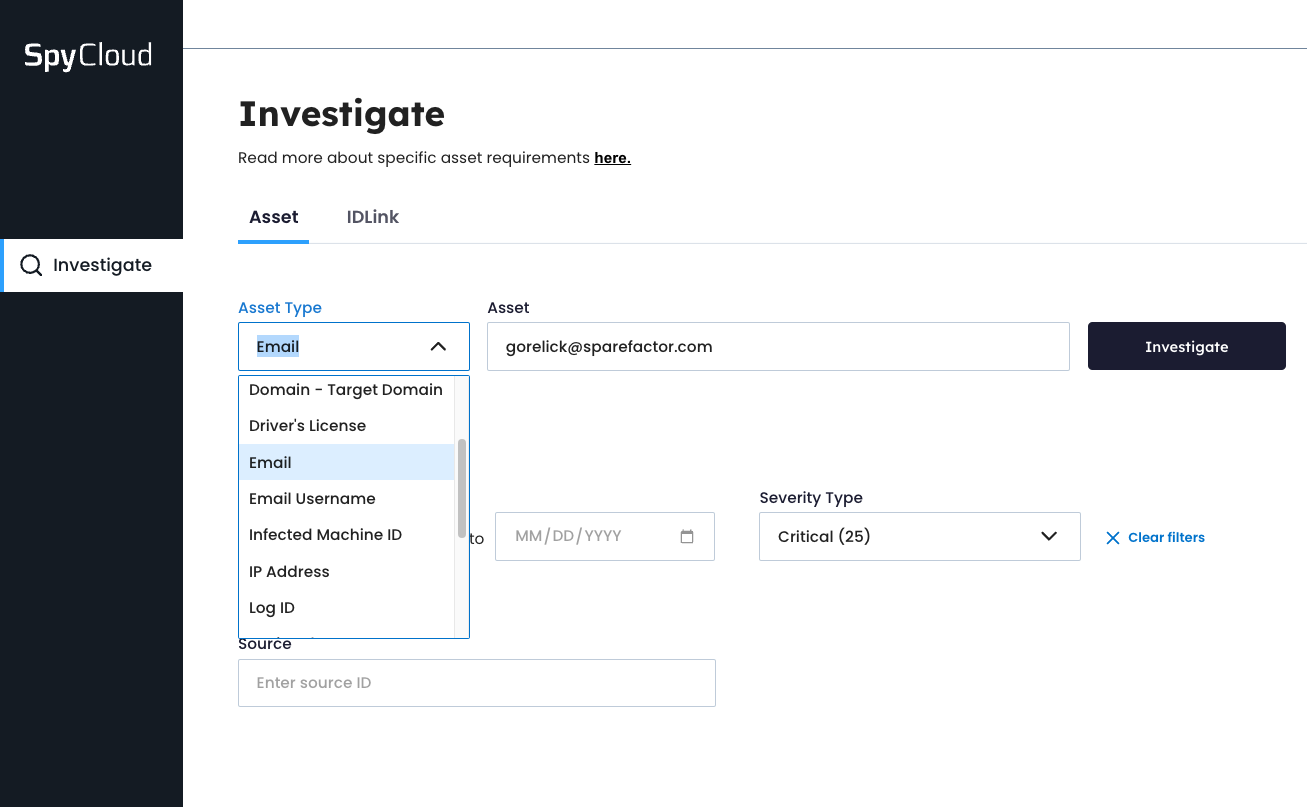
Investigate on these asset types, and more:
- Domain
- Email address
- Password (Hashed)
- Phone number
- Infected machine ID
- Social media handle
- Username
- SSN
- Drivers license number
SpyCloud Investigations is the first-of-its-kind, ultimate force multiplier for analysts, providing a wealth of quality identity analytics to deeply understand organizational risk from exposed users and infrastructure, open new angles to investigate, and illuminate connections that make it faster and more efficient to get the answers you seek.
The Investigations solution is a SaaS portal, powered by our unique IDLink advanced analytics, which automatically builds holistic digital identity profiles that give you the speed and resources you need to drive better analysis to attribution. In a sense, SpyCloud Investigations with IDLink offers an ‘analyst in a box’ experience to rapidly increase discovery and speed up resolution for more definitive and confident analysis of identity threats and cybercrime.
Here’s how it works:
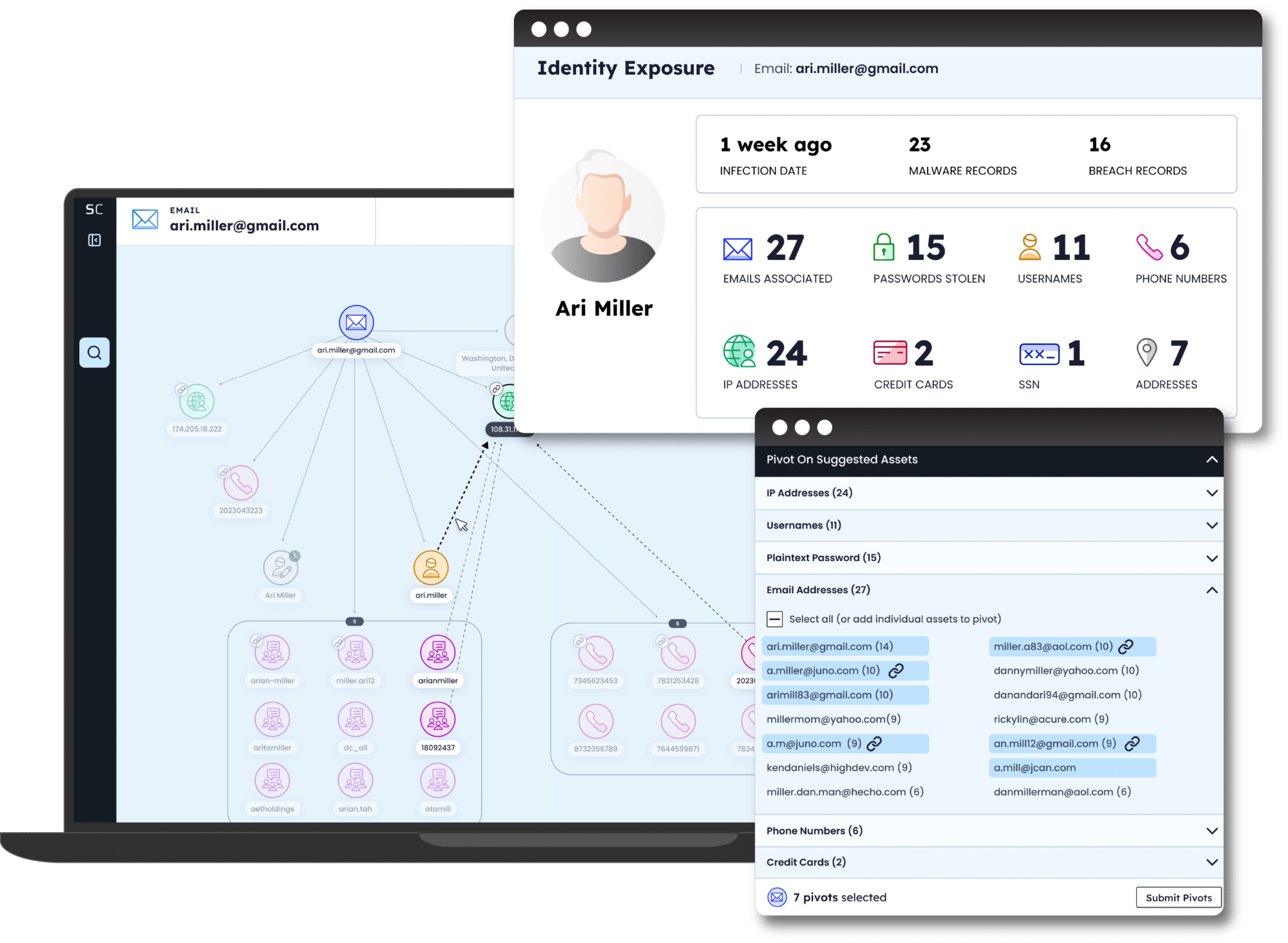
- After searching on an email, username, or phone number, IDLink automatically runs pivots in the background, looking for connections on everything that makes up a digital identity – from matching emails and backup emails, to shared and exposed PII, usernames, passwords, and over a dozen other asset types.
- SpyCloud Investigations with IDLink only returns new, highly-relevant results, removing any out-of-scope identity asset that slows down analysis.
- SpyCloud Investigations enhances raw data with additional context to give you a broader view of exposed identities and threats.
- After searching on an email, username, or phone number, IDLink automatically runs pivots in the background, looking for connections on everything that makes up a digital identity – from matching emails and backup emails, to shared and exposed PII, usernames, passwords, and over a dozen other asset types.
- SpyCloud Investigations with IDLink only returns new, highly-relevant results, removing any out-of-scope identity asset that slows down analysis.
- SpyCloud Investigations enhances raw data with additional context to give you a broader view of exposed identities and threats.
Leveraging the power of IDLink analytics
SpyCloud Investigations visualizes the digital identity of your subject, using IDLink analytics to uncover connections across hidden assets.
SOC
EFFICIENCY
“SpyCloud Investigations with IDLink has drastically reduced our investigation time, turning 2 hours of SOC work into just a few minutes.“
CTI TIME
SAVINGS
UP-LEVEL ANALYST PRODUCTIVITY
CTI Lead, Leading global IT professional services company
Examples of what you can do with SpyCloud Investigations
SpyCloud Investigations helps your teams investigate criminal, employee, and supply chain identities to analyze risk, attribute threats, correlate previously hidden data points, and get to the answer faster.
Let’s explore two common scenarios that relate to your CTI, SOC, and Fraud/Risk teams to see what using SpyCloud Investigations with IDLink analytics can look like.
Using SpyCloud Investigations for Malware Infected Host Identification
THE SITUATION:
An organization’s SOC team is alerted to an unusual employee login from an unfamiliar geolocation, different from the employee’s typical location.
INITIAL ACTION:
The team’s analyst goes to SpyCloud Investigations to examine the source and cause of the login, scoping out the risk.
QUESTION TO BE ANSWERED:
Is the corporate infrastructure exposed from an employee’s malware-infected device? Does the infected machine contain victim data?
INVESTIGATIVE WORKFLOW WITH SPYCLOUD
- The analyst queries the employee’s login credentials in SpyCloud’s recaptured database to search for any compromised credentials.
- SpyCloud results show malware-exfiltrated records containing application credentials, passwords, and other linked asset types.
- The analyst needs to dig deeper to determine the root cause, so they expand their analysis by using IDLink to query the employee’s email address, uncovering hidden assets and clues.
- The analyst reviews the more detailed results, which include exposed records from target domains and subdomains, confirming criminals had attempted to log in and take over the employee’s account.
HOW IDLINK HELPS IN THIS SITUATION:
IDLink returns hundreds of highly-correlated identity assets (like backup emails, social handles, and usernames), including proof of the exposed subdomain, all without having to spend time running manual pivots.
OUTCOME:
SpyCloud helps the analyst prevent employee account takeover by exposing risks tied to the employee’s digital identity. With IDLink, the analyst can continue with malware post-infection remediation steps, including resetting malware-compromised application credentials, to prevent criminals from using the stolen identity data in an ATO attack.
Using SpyCloud Investigations for Financial Crime Analysis
THE SITUATION:
An airline customer reports strange behavior in their account, and the airline’s support team escalates the issue to their fraud & risk team.
INITIAL ACTION:
A fraud analyst uses SpyCloud Investigations to query the customer’s username (a unique loyalty number), looking for patterns of financial crime.
QUESTION TO BE ANSWERED:
Are there indicators of fraud or criminal activity in our domain’s dataset? And is the criminal potentially targeting other similar organizations or services?
INVESTIGATIVE WORKFLOW WITH SPYCLOUD
- The fraud analyst knows they are going to have to expand their investigation given the uniqueness of the starting selector – a highly unique airline loyalty number – so they start their search in SpyCloud Investigations with IDLink.
- The results from IDLink return hundreds of records correlated to an infected machine. The results indicate a criminal’s use of the legitimate customer’s information retrieved from breach data traded or purchased from a dark web marketplace.
- After viewing the curated set of broader results, the analyst notices a consistent IP address showing up repeatedly across dozens of domains and URLs, along with exposed VPN credentials indicating the criminal was behind a proxy.
- The analyst continues to dig into the results and discovers that the company’s target URL confirms indicators of fraud, including criminal patterns and behavioral clues, unique usernames, and even evidence of movement of money, helping uncover more TTPs associated with fraud.
HOW IDLINK HELPS IN THIS SITUATION:
IDLink overcomes the challenge of starting an investigation with a single unique selector, uncovering malware-exfiltrated records and indicators of fraud by digging deeply and connecting common assets across the dataset.
OUTCOME:
SpyCloud helps the analyst uncover a coordinated fraud operation targeting multiple airlines, giving the fraud & risk team a deep view into the attacker’s behavior. This also allows the incident response team to remediate the malware infection, and the support team can complete the customer inquiry to uphold customer satisfaction.
Get started with SpyCloud Investigations today
SpyCloud Investigations takes into account our team’s deep tradecraft and expertise in the cybercrime economy and combines it with SpyCloud proprietary pivoting and identity analytics. It gives SOC, CTI, and Fraud/Risk teams a competitive advantage in the race to complete cyber investigations – so if you’re in need of a better way to get fast and reliable resolutions, get started with SpyCloud by requesting pricing or watching a demo today.
Fill out this short form to watch an on-demand demo of SpyCloud Investigations.