February may be the shortest month of the year, but it was still jam-packed with cybercrime news. This month brings us some positive news for cyber defenders…and more of the usual from the criminal underground.
In this edition of our monthly cybercrime update, we’ll get into the good, including:
- Arrests and takedowns of the 8Base ransomware group, as well as new insights into the inner workings of the Black Basta ransomware gang after a massive new leak of their Matrix chat records
And on the less-positive side of things, we analyze:
- Another Doxbin leak, more murmurings from B1ack Stash about stolen credit cards, a flurry of media coverage about ALIEN TXTBASE stealer data, and an update to the Darcula phishing kit that makes generating custom phishing campaigns easier than ever before
Without further ado, let’s dig in.
Major Cybercrime Events This Month
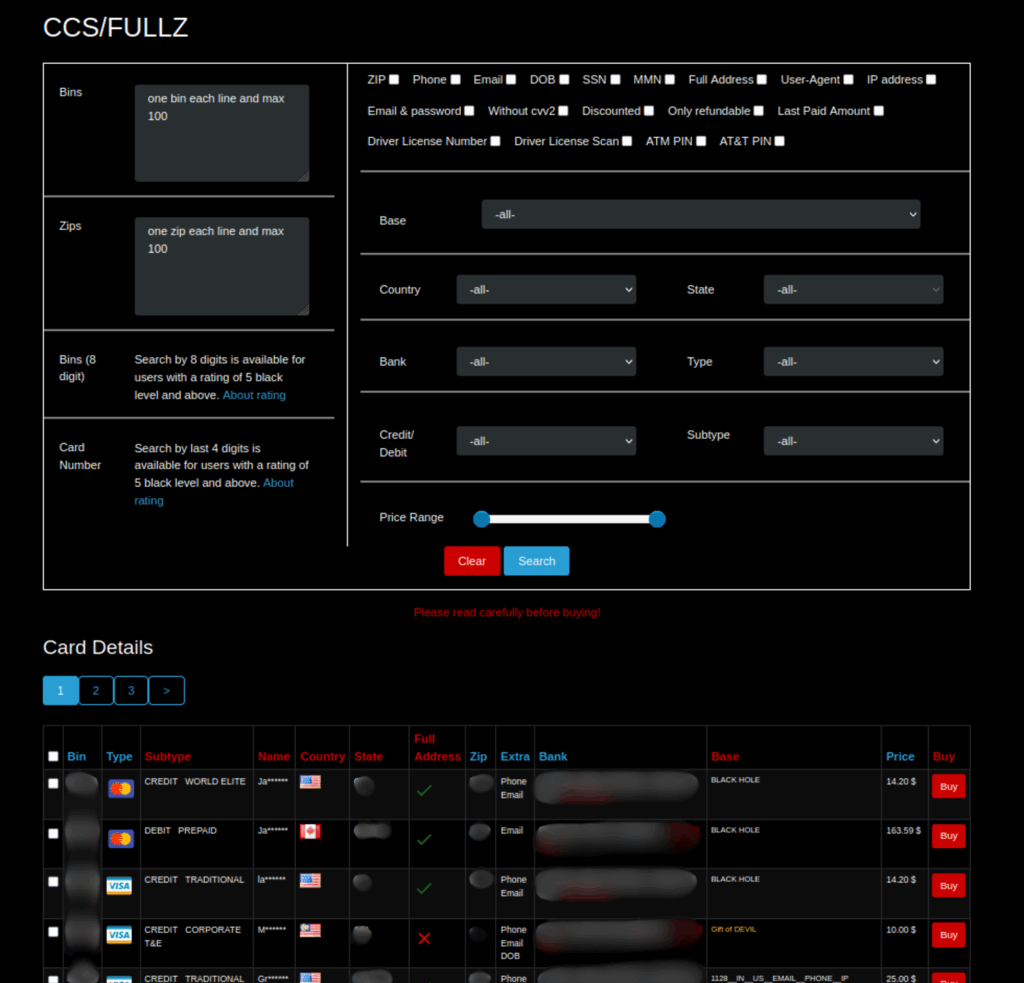
4 Million Free (Stolen) Credit Cards
In April 2024, a new carding marketplace, B1ack’s Stash, launched and attempted to entice users to register on their site by offering 1 million stolen credit cards for free. In February 2025, they ran a similar marketing campaign, this time offering 4 million free cards to anyone who created at least a “Level 1” account on the website.
After downloading this new dataset of 4 million credit cards and de-duplicating the data, SpyCloud Labs analysts concluded that there appear to be only around 10,000 unique cards contained in this dataset. A large portion of these cards appear to belong to cardholders from Southeast Asia.
Across all of the “freebies” posted to the B1ack’s Stash site, there are just over one million unique credit card records, which include the credit card number, and other information like the CVV, expiration date, cardholder name, and other cardholder details. These freebies and datasets of “millions of free cards” all function as marketing campaigns to drive new users to register on the B1ack’s Stash website and purchase premium offerings.
All Your ALIEN TXTBASE Are Belong To Us
In the past week, a dark web data source called ALIEN TXTBASE has been highlighted by cybersecurity researchers and news outlets. ALIEN TXTBASE is a Telegram channel that distributes URL:log:pass (ULP) combolists, large lists of credentials consisting of URLs, email/username logins, and passwords that are usually derived from stealer logs, but are not themselves stealer logs. This Telegram channel currently contains over 700 of these ULP combolists that have been posted by the channel operators over time, containing billions of records in total.
What’s in a stealer log?
A stealer log is a bundle of stolen information taken from a single device that has been infected with infostealer malware. The exact stolen data varies depending on the malware strain, but it almost always includes sensitive information stored in the browser – like passwords, cookies, and saved credit card information – as well as detailed user and device information about the infected device. Additionally, these logs can include a wide variety of additional sensitive data stolen from the infected device, like desktop files, data stored in notes applications, and profiles for desktop applications like Steam and Discord. Stealer logs are often distributed and sold online in darknet forums and marketplaces; the logs are purchased by other threat actors who use the stolen credentials to perpetrate additional intrusions.
The credentials in ULP combolists are usually derived by pulling just the login credential information out of a large collection of stealer logs and aggregating it all together, which strips out most of the context. Often, data is also mixed in from different sources like breaches or even other combolists compiled by separate threat actor groups.
After examining a sample of the ULP data from the ALIEN TXTBASE source, we observed significant overlap (over 60%) with existing stealer log data in SpyCloud’s platform. We also observed even greater overlap (over 80%) with other combolists from other sources, indicating that the data is not particularly unique or fresh, even if a lot of it might have been originally derived from infostealer infections.
Additionally, we see records without associated URLs as well as some evidence of fabricated data, indicating that there may be some amount of data mixed in from breaches or generated using credential-guessing tools like password-similarity models, which fabricate possible alternative credentials based on known existing credentials.
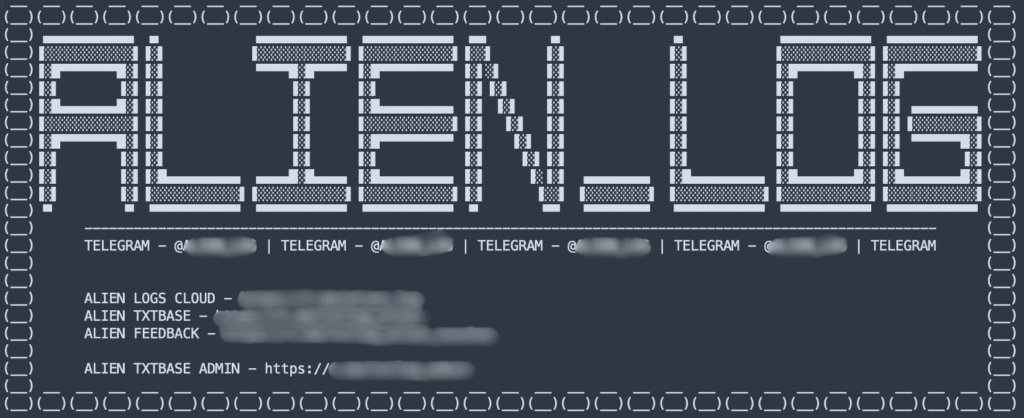
The ALIEN TXTBASE channel itself offers free ULP combolist data to advertise other premium offerings, including an ALIEN LOGS CLOUD channel, which contains full stealer logs. SpyCloud Labs is continuing to monitor this data source, as well as other similar data sources that distribute both ULP combolists and infostealer logs.
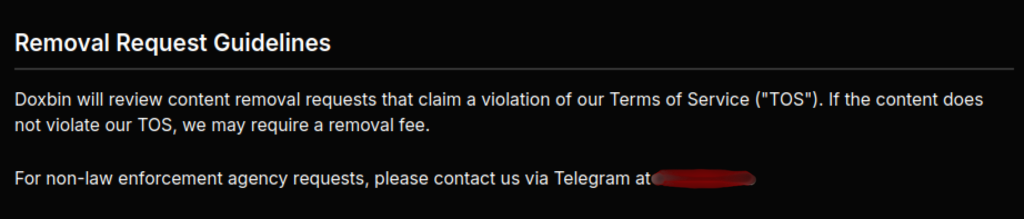
Yet Another Doxbin Leak
On February 11, the TOoDA hacking group took control of the Doxbin website, purged accounts, and leaked site user and administrative data. Doxbin is a pastebin-style website where users are encouraged to dox others (aka posting someone’s personal information online in an attempt to get others to harass them).
There have been multiple Doxbin leaks in the past, including leaked Doxbin user tables containing usernames, emails, and hashed passwords. Additionally, some threat actors also scraped Doxbin and redistributed Doxbin posts as a dataset.
However, what sets this most recent Doxbin leak apart is a spreadsheet of “Blacklist Data,” which appears to be a detailed accounting of Doxbin posts for which the doxxed individuals paid the Doxbin site administrators to have a post containing their personal data taken down. The spreadsheet appears to contain data from some celebrities as well as quite a few cybercriminals. The spreadsheet contains the data from the removed post as well as the email address or Telegram account username used to request the takedown.
Websites like Doxbin highlight how stolen identity data doesn’t just threaten the security of user accounts and enterprise networks, but can also pose a threat to the personal safety and security of individuals. Breached, leaked, and stolen PII can be weaponized to digitally and physically harass individuals on top of being leveraged for cybercrimes like fraud.
Arrests of Phobos and 8Base Ransomware Operators

On February 10, an international group of law enforcement agencies seized 27 servers belonging to the 8Base ransomware group and arrested four individuals associated with the group who are suspected of deploying 8Base ransomware. In Europol’s press release on the takedown, they also highlight previous arrests by the same group of law enforcement agencies of other key figures associated with Phobos ransomware (both affiliates and administrators).
8Base’s ransomware was originally based on Phobos, but the malware has since evolved over time as its operators have made changes to their codebase. This group of law enforcement agencies appears to have closely coordinated their investigations into both Phobos and 8Base. This approach more realistically mirrors the rapid rebranding, splintering, and offshooting that occurs among ransomware groups, often as a purposeful tactic to confuse and evade law enforcement and cybercrime researchers.
TL;DR of new SpyCloud Labs research
Current & Forthcoming Cybercrime Research
Black Basta Integrated Known Stealers with Their Ransomware Operation
On February 11, 2025, a Telegram account called ExploitWhispers leaked a large dump of internal Matrix chat records from the Black Basta ransomware group. The leak appears to include their internal communications from September 2023 through September 2024. Totaling nearly 200k messages, these leaks provide a treasure trove of information, including insights into the group’s organizational structure, infrastructure, tooling, vulnerability exploitation activity, and personal identities.
Our ad-hoc token clustering analysis on the leaked Black Basta chats, integrated with ground truth and a bit of RUMINT, illustrates the potential roles of some key members of the Black Basta operation (image 5). Key tokens are loosely aligned along the kill chain, demonstrating some fuzzy grouping of the members from initial access to actions-on-objectives. More thorough, qualitative analysis on each member was performed by an independent security researcher, bencrypted.
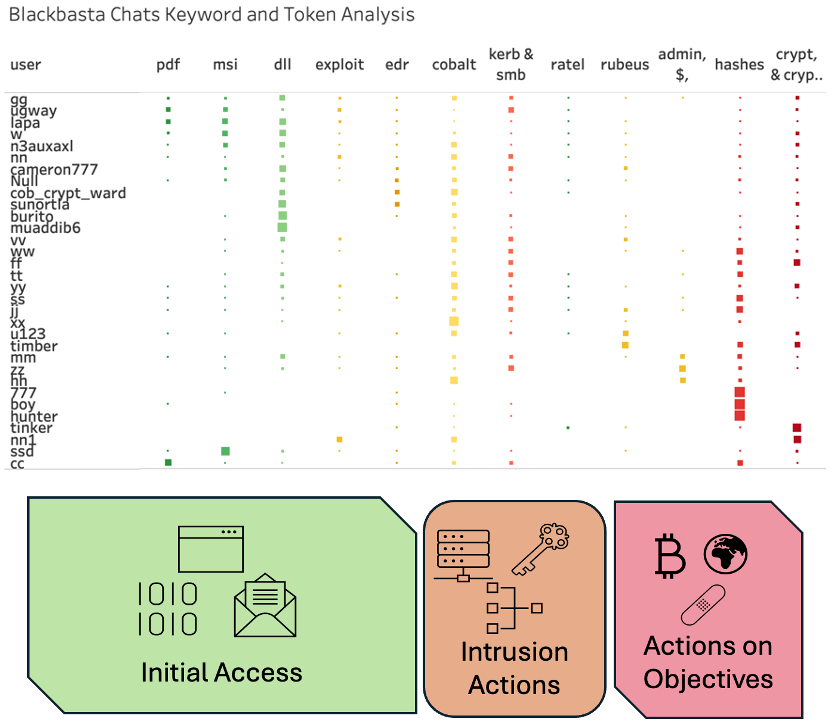
Unlike Conti, another ransomware group whose chat logs were leaked early in 2022, Black Basta kept a tightly closed affiliate model with few active members. Leadership for Black Basta falls largely on gg, who is involved in making judgment calls all along the kill-chain. RUMINT suggests that gg is Tramp, a threat actor best known for his attempted revival at the Emotet botnet. Throughout 2022, Black Basta was a known endgame of Qbot (also known as Qakbot), a popular loader malware that was disrupted by law enforcement in August 2023.

Black Basta has also been observed using other initial access vectors, including Pikabot, vulnerability exploitation, and the use of valid credentials. Valid credentials can facilitate initial access, persistence, and lateral movement.
Best Practices –
Protection from attacks that leverage stolen credentials requires a multi-layered approach:
Protection from attacks that leverage stolen credentials requires a multi-layered approach:
- Reduce risk of infostealer infections. Individuals and organizations should take steps to avoid infostealer infections to minimize the potential for follow-on cyberattacks.
- Specifically, organizations should enhance existing playbooks to include a comprehensive post-infection remediation approach to make sure that – beyond wiping the device clean of the initial stealer – the accounts and credentials tied to the device are remediated and active session cookies closed to ensure any stolen data can not be used for further invasive access to networks and systems.
- Vet online sources to verify legitimacy
- Don’t download free or cracked software
- Verify source when receiving email attachments
- Use password managers. Organizations should offer employees access to a master password tool, and individuals should use a master password keeper instead of storing passwords in the browser. Stealers often steal passwords, credit card information, and other personal data stored in your browser. If you don’t save your passwords using your browser’s built-in password manager, then it’s less likely an infostealer infection will be able to get your passwords.
- Don’t reuse passwords. SpyCloud has found that 70% of users reuse old passwords that have previously been exposed on the dark web. Users can use a password manager to generate a new, unique password for each account and keep them organized. Organizations can look to NIST guidelines to create and enforce good and manageable password hygiene through proper password policies. You can check if any of your passwords are exposed on the dark web with SpyCloud’s free Password Checker.
- Use multi-factor authentication (MFA). MFA renders a stolen password useless without a registered authenticating device or a sophisticated bypass.
Ensure MFA is configured correctly following vendor guidelines. Improperly configured enrollment is easy for threat actors to bypass.
- Monitor for exposed credentials and identity data. There are both consumer-facing and enterprise services to monitor credentials that have been leaked on the darknet due to breaches, malware, or phishing. Users and organizations can get started by using our free Check Your Exposure tool to check your corporate email address to understand if your identity data is circulating in the criminal underground.
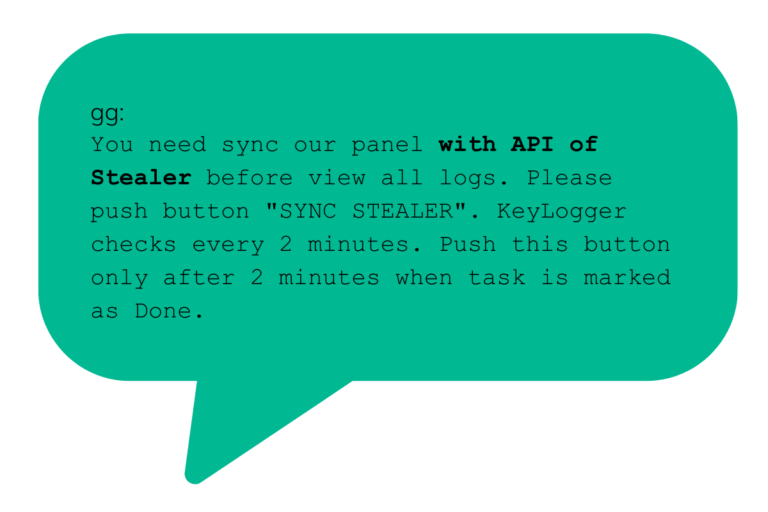
In the Black Basta chat logs, there is strong evidence that the use of valid credentials in Black Basta ransomware intrusions was facilitated by Black Basta’s stealer integration, which allows team members to bring stealer logs directly into attack orchestration.
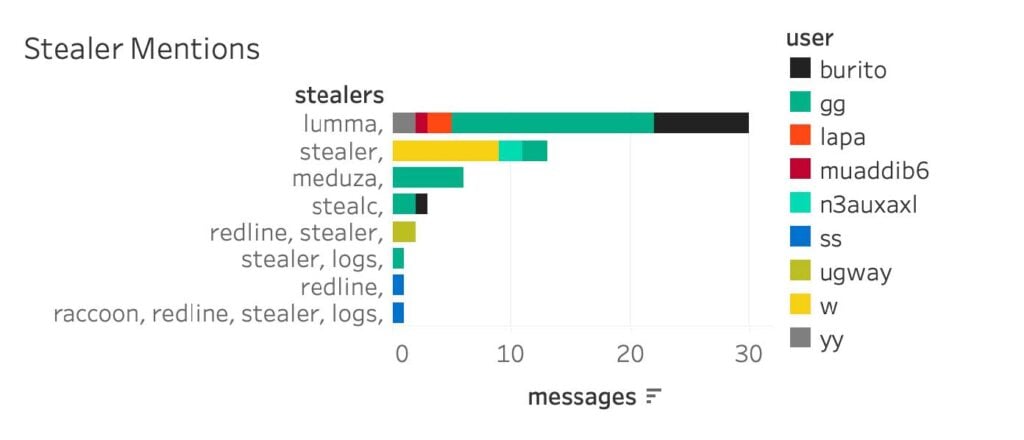
Mentions of infostealer malware, Lumma consisted mostly of .exe and .zip filenames following burito’s suggestion that they wrap the stealer with a crypter (image 6). Stealer logs were also directly shared in the leaked Matrix chats from a handful of stealers with an emphasis on Meduza stealer. Valid credentials have been repeatedly targeted by ransomware groups for initial access, and blue teams often find correlations between accounts found in stealer logs and those leveraged in ransomware incidents. Here, we see an explicit relationship, including specific tooling in the Black Basta panel to support the integration between stealers and active ransomware operations.

Darcula Phishing-as-a-Service
The Phishing-as-a-Service (PhaaS) operators of the Darcula phishing kit have released a “V3” of their kit, making it even easier for non-technical cybercriminals to conduct targeted phishing campaigns.
Darcula is a phishing kit created by Chinese-speaking cybercriminals that allows less technical users to set up sophisticated phishing pages and launch smishing campaigns. Earlier versions of Darcula were known for having pre-built phishing campaign templates for a wide variety of global brands, enabling their customers to easily launch convincing smishing campaigns such as “missing package” campaigns impersonating the postal services for various countries around the world.
The V3 version of Darcula has a particularly novel new feature: phishing kit generation. Essentially, any Darcula user can create their own phishing kit to impersonate any brand simply by inserting the URL of the brand’s legitimate website into the Darcula suite. Then, as researchers at Netcraft reported, the platform appears to use a browser automation tool to export the webpage and associated assets like logos and fonts. Darcula users can then choose a scam template based on the specific types of data they want to phish, make any stylistic changes to make sure the phishing page(s) look legitimate and match the impersonated brand’s website, and finally export the new custom phish kit.
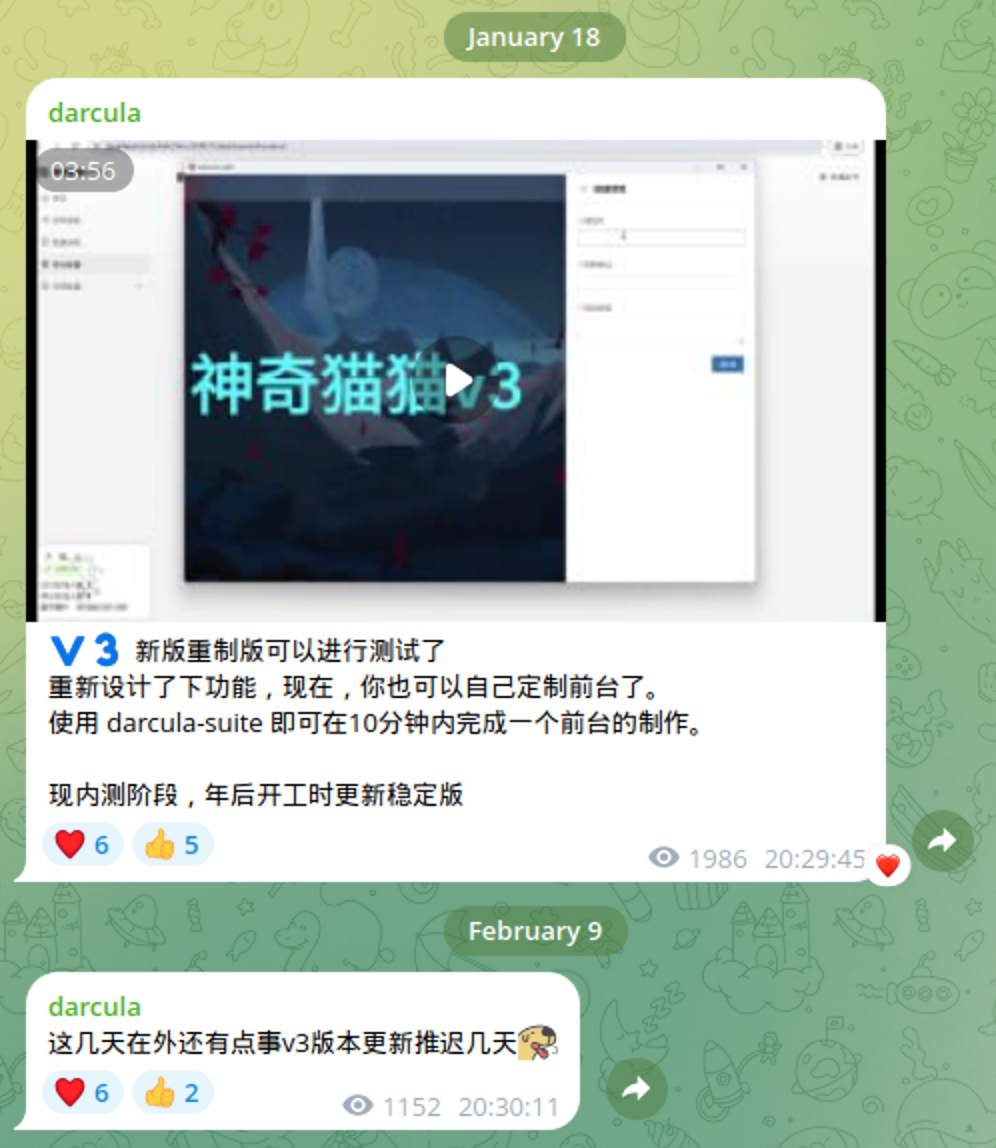
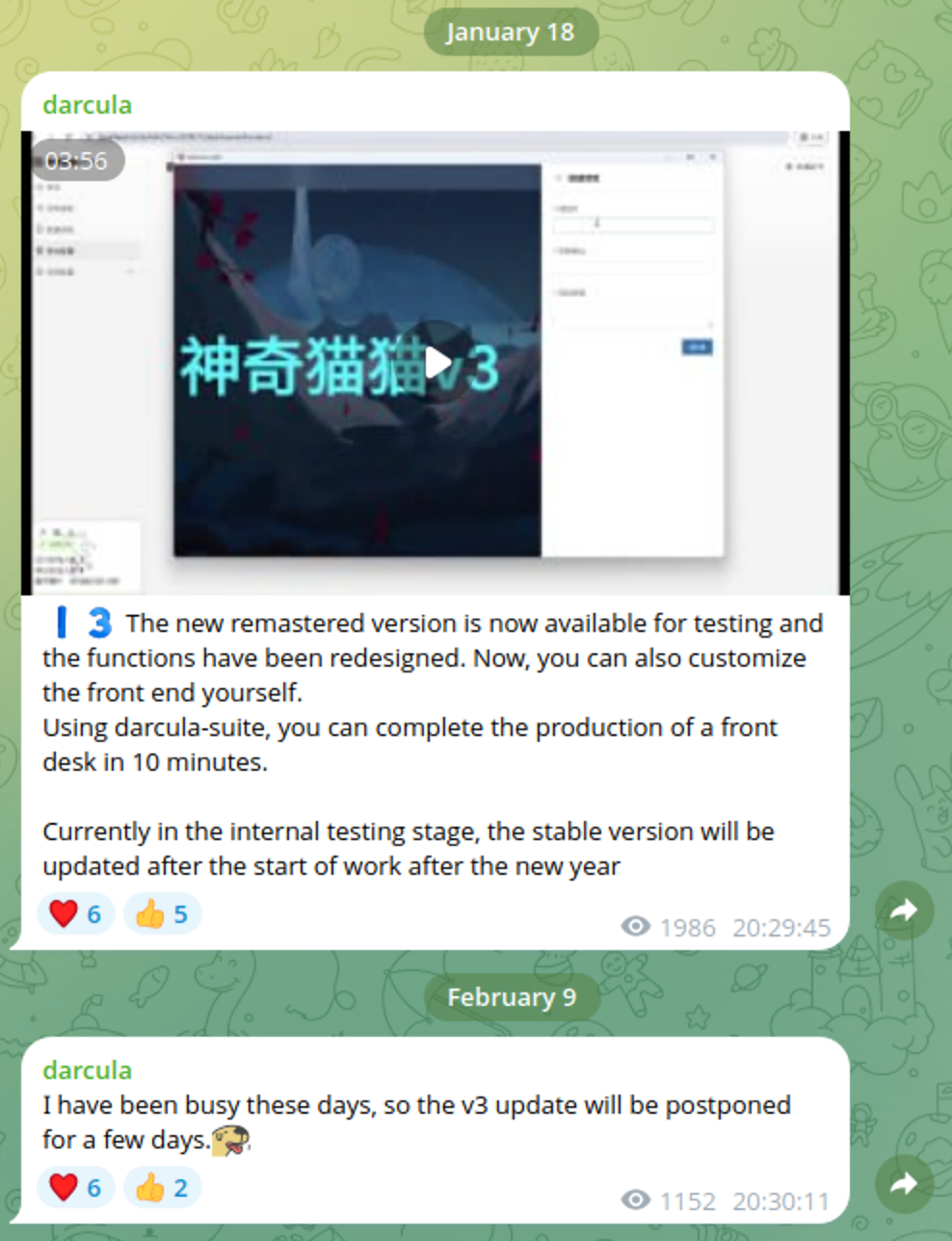
Simple, user-friendly PhaaS tools lower the barrier to entry to conducting cybercrime. At SpyCloud Labs, we refer to the broad ecosystem of tools and services that empower even low-skill threat actors to conduct sophisticated cyber attacks as cybercrime enablement services. Darcula V3 specifically enables cybercrime by allowing anyone to create and deploy a polished, custom phishing campaign that convincingly impersonates any brand of their choice without requiring any specialized web development skills.
SpyCloud Labs will continue to monitor Darcula and other PhaaS activity and provide updates as available.
Coming Soon: The 2025 SpyCloud Annual Identity Exposure Report
Last but not least, the SpyCloud team has been hard at working compiling our annual analysis of identity exposure trends. This year’s report includes:
- A detailed examination of the scale of identity exposure for the average corporate and consumer identity
- In-depth analysis of the stolen data that’s putting businesses most at risk today, including infostealer malware infections, data breaches, and phishing campaigns
- Breakdowns of the data types (hint: PII continues to trend) that are increasingly being targeted by cybercriminals to use in identity-based attacks
- Guidance on how to shift our collective defenses to better address the weaponization of identity sprawl by bad actors through holistic identity threat protection
Subscribe below to be one of the first to get the full report in your inbox and in the meantime, you can look back at last year’s report to get a sense of what to expect.
SpyCloud’s recaptured data collection numbers
February Monthly Total
Total New Recaptured Data Records for February:
2,036,699,103
New Recaptured Third-Party Breach Data this Month
Third-Party Breaches Parsed and Ingested:
355
New Data Records from Third-Party Breaches:
783,869,234
New Recaptured Infostealer Malware Data this Month
Unique Infostealer Infection Logs Parsed:
3,307,807
New Data Records from Infostealer Infections:
25,567,052
New Stolen Cookie Records:
1,227,262,817
New Infostealer Malware Families
PXRECVOWEIWOEI: PXRECVOWEIWOEI, also known as 0bj3ctivityStealer, is an infostealer that targets Windows devices. It steals user system information, passwords, credit card details, autofill data, cookies, application profile information for messaging and gaming applications, and other sensitive data. It can also take screenshots of the desktop and webcam.
PureLogs Stealer: PureLogs is an infostealer developed by a threat actor named PureCoder. PureCoder offers a variety of different types of malware, which can be purchased through subscription services, including PureCrypter, PureMiner, BlueLoader, and PureHVNC.
Braodo Stealer: Braodo is an infostealer that is written in Python. It uses Telegram bots for command-and-control (C2) and data exfiltration.
Unidentified Delphin Stealer: This month, we also started ingesting data from a new stealer log format that we have not yet identified. We are tracking the yet-to-be-identified Windows infostealer that produces these logs as “Unidentified Delphin Stealer.”




