Everyone’s talking about infostealers…and if you’ve been keeping up with recent headlines about malware and ransomware, you know that infostealer infections can be the starting point in a ransomware attack chain. It’s why so many of our customers are shifting left in their malware detection and response workflows.
To support our customers in this endeavor, we now have a series of Endpoint Detection & Response (EDR) integrations designed to more effectively address the infostealer malware problem and prevent subsequent ATO, session hijacking, and ransomware issues for your security teams.
When paired together, SpyCloud plus your preferred EDR solution can make all the difference in stopping an active attack from spreading and in preventing future malware-related attacks.
Infostealer malware and ransomware are bypassing EDR nets
As we all know, ransomware attacks frequently leverage sensitive data, including corporate IP and employee credentials, which can be captured by infostealer malware. Stealers are often installed alongside other persistent malware so attackers can use that device as a foothold in the network – even infiltrating corporate devices with EDR protection.
According to SpyCloud Lab’s latest analysis of recaptured darknet data in 2025, 66% of malware infections happen on devices with endpoint security solutions installed.
Due to the non-persistent nature of stealers, which allows them to delete themselves within just seconds after extracting data, EDR tools don’t provide foolproof detection capabilities.

How SpyCloud helps optimize malware detection and remediation
- SpyCloud has launched integrations with CrowdStrike Falcon EDR and Microsoft Defender for Endpoint. You can now ingest SpyCloud’s high-fidelity malware alerts directly into your EDR platform to detect any infection that bypasses your security.
- SpyCloud Compass offers extended malware detection into devices outside corporate control and visibility into all exposed applications that could lead to follow-on attacks.
- Our native integrations with leading SIEM and SOAR platforms offer extended enrichment and built-in playbooks to better assess the threat and automate appropriate responses.
- Additionally, SpyCloud Connect offers a hosted automation solution designed to build custom automation workflows for you across your preferred security tools to adhere to your unique malware-infection remediation process.
Since our goal is to help defenders solve the malware challenge, it was natural for us to expand our integration support to include integrations with leading endpoint security software like CrowdStrike Falcon EDR and Microsoft Defender for Endpoint.


In this blog, we’ll focus on the first bullet above – our new EDR integrations. So let’s look at how the new integrations work to enhance your SOC teams’ ability to detect and respond to malware infections that may otherwise go unnoticed.
How SpyCloud and EDR integrations for malware detection work together
SpyCloud’s EDR integrations give your teams high-fidelity malware alerts directly within their EDR environment so you can:
- Gain insights into which corporate devices have been compromised by infostealers
- Leverage actionable intelligence to guide containment, such as automatically quarantining high-risk infected devices and taking fast action to mitigate malware spread
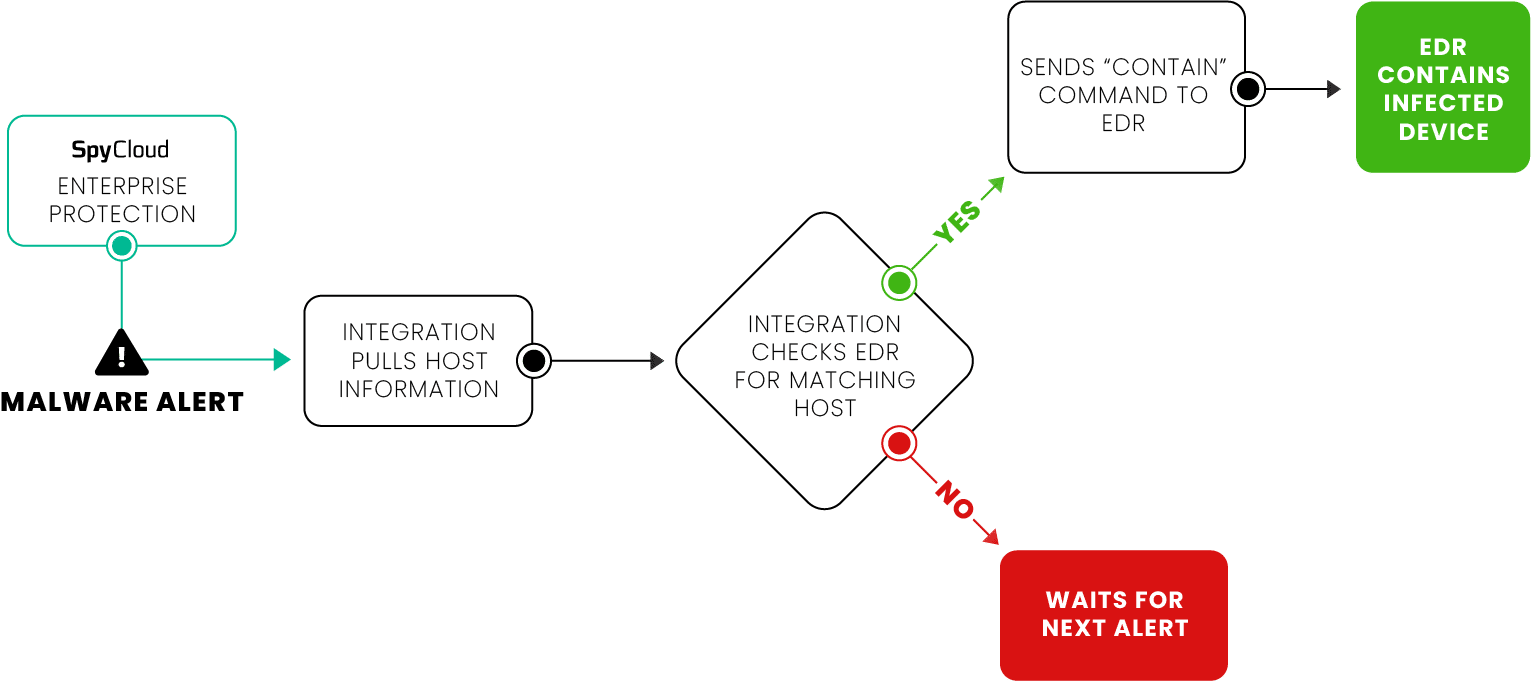
SpyCloud malware alerts integrate with your EDR tool of choice to rapidly respond to malware threats and limit the likelihood of follow-on attacks.
EDR integration implementation with your SpyCloud instance
For SpyCloud Endpoint Threat Protection customers with licenses for Crowdstrike Falcon or Windows Defender, setting up the EDR integration is as easy as:
01
Fill out a secure, simple UI workflow with your API keys for SpyCloud and the EDR of choice
02
Select configuration options for your preferred response actions
03
Start to ingest high-priority malware alerts to get ahead of targeted attacks
SpyCloud does the heavy lifting, analyzing recaptured malware records to determine the hostname. Upon matching, the steps automatically kick-off to alert you directly in your EDR tool.
Looking for help integrating SpyCloud data with your other security tools and processes – wherever and whenever you need it – without burdening your existing resources?
Why SpyCloud is essential for malware detection and remediation
Comprehensive identity data for effective malware remediation
Many security platforms integrate with EDR for identity threat detection and response, but only SpyCloud’s enriched identity data – recaptured from a variety of sources including third-party breaches, successful phishes, and malware infections – provides the depth needed for full post-infection remediation.
SpyCloud gives you definitive evidence of compromised corporate devices, reducing MTTD and MTTR, to prioritize your malware remediation efforts. With SpyCloud’s data from infected hosts integrated into your EDR, you can:
Automatically identify and contain high-risk devices
Gain immediate visibility into corporate devices exposed to malware through SpyCloud’s enriched alerts. By pinpointing infected hosts with precision, you can initiate rapid containment, reducing the risk of malware spreading.
Reduce SOC workload tied to malware detection
Automatically detecting malware infections reduces the manual intervention for security teams, freeing up your resources to instead focus on remediating malware infections to reduce the risk of follow-on attacks.
Shifting left with advanced malware detection and response
With infostealers at play, EDR solutions alone don’t mean you’re fully protected from identity threats. By integrating SpyCloud with your EDR, SOC teams can effectively shift left in their response efforts, preventing attacks earlier in the threat lifecycle.
Our EDR integrations and existing offerings for detecting and remediating malware unify your identity threat protection across your entire security stack, strengthening defenses against advanced threats and reducing the impact of malware infections on corporate networks.
See it in action
SpyCloud’s enriched identity data offers definitive insights to prioritize, remediate, and protect your organization from the escalating landscape of identity threats.