The ransomware problem is snowballing by the day. Ransomware attacks, now deemed a growing national security threat witnessed a breakneck escalation in scale and severity across every industry. In 2020, ransomware attacks soared a staggering 62% worldwide.The trend continued to climb with 304.7 million attempted ransomware attacks recorded in the first six months of 2021, surpassing the 2020 total of 304.6 million. The average cost of ransomware recovery also skyrocketed in 2021, doubling from the past year’s price tag of $760,000 to $1.85 million.
A data-driven view
Considering the escalated severity of the ransomware threat across all sectors and organizations of all sizes, we launched a survey to obtain key insights and understand how security leaders and practitioners feel about the threat and their defenses to guard against it.
The SpyCloud Ransomware Defense Report crystallizes the inputs received from 250 individuals in active IT security roles at US-based organizations with 500 or more employees. The report provides insights in many important areas, such as:
- The top risks related to ransomware and the most significant obstacles to establishing effective defenses;
- Security teams’ priorities for technical countermeasures and other preparedness steps; and,
- Expectations and plans for the next 12 months.
Key findings
The recent surge in ransomware attacks is a systemic problem having all the traits of organic evolution. The threat actors are employing a concert of innovative tactics to carry out successful ransomware incidents. Ransomware-as-a-service business models, double-extortion tactics, and targeted attacks combining automated techniques with human operators are some of the noteworthy trends. And their reported fallouts tally with the key findings of our research.
The Tip of the Iceberg
Our findings align with research data that ranks ransomware as the top incident type in 2020. We are not surprised that 72% of organizations we surveyed were affected by ransomware in the past 12 months. What’s noticeable is that 13% of those organizations were affected by ransomware 6-10 times within that period, with 5% getting hit more than ten times. That’s a crucial indicator of the magnitude of the problem, which is likely to be way more pervasive than many people think. The high-profile attacks making news are a fragment of the full scope of the problem.
Compromised Credentials, A Top Entry Point
Over the past 12 months, many researchers have ranked phishing emails and exposed credentials as top risks. Our survey respondents mirrored that trend by ranking phishing emails with infected attachments or links as the riskiest vector for ransomware attacks, followed narrowly by weak or exposed credentials. Account takeover (ATO), or the use of compromised credentials, is a top attack vector in the early stages of a ransomware attack. In 2020, SpyCloud recaptured 1.5 billion exposed credentials from breaches and botnet logs, underlying the scale of the data criminals have to work with. 29% of the surveyed organizations are planning to add continuous monitoring and remediation of exposed credentials to enable early prevention.
People are the Greatest Barrier to Effective Defenses
Lack of budget is not a significant obstacle in this case. And neither is lack of support from executive management, as high-profile incidents like SolarWinds and Colonial Pipeline helped drive top-level awareness. According to our survey respondents, the top barrier to effective ransomware defense is people. A shortage of skilled security personnel ranked at the top, followed closely by suboptimal security awareness among employees. The pandemic has exacerbated both the talent shortage and the human vulnerability in a remote environment, requiring organizations to find new ways to protect employees from themselves.
Ransomware Isn’t Going Away Any Time Soon
While 13% of respondents believe their organization will be affected by ransomware at least once in the coming year, a remarkable 22% expect to be hit multiple times. In comparison, only 12% do not expect ransomware incidents in their organization in the next year. Bottom line: the majority believe ransomware is here to stay. In terms of preparedness, fewer organizations have more mature solutions like user and entity behavior analytics (UEBA), network and resource segmentation, and compromised credential monitoring — but are planning to add them as defenses in the near future.
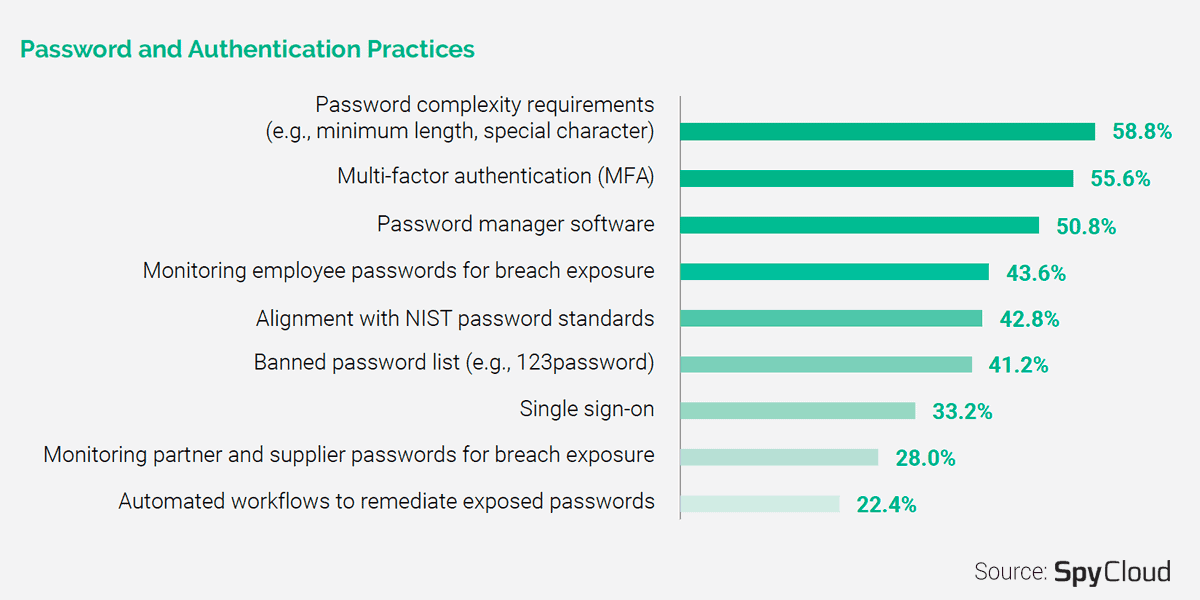
Most Organizations Lack Basic Forms of Prevention
What astounded us from the survey is that 41% of organizations don’t have a password complexity requirement, which is the easiest and least costly form of password security. And only 56% of organizations have implemented multi-factor authentication (MFA). Stolen credentials being a significant enabler of successful attacks, our report highlights ways to prioritize effective defenses to prevent account takeover and other forms of credential compromises.
Learn to protect your organization from ransomware
Ransomware is a complex problem to solve, and the best place to start is by preventing the access itself. In addition to highlighting the survey findings, The SpyCloud Ransomware Defense Report identifies best practices organizations can implement to improve their ransomware defenses. We encourage you to download the full report and use the actionable survey data as you make future decisions about your cybersecurity strategies and investments.
