Over the years, we’ve witnessed cybercriminals continue to impact businesses globally as TTPs such as infostealer malware become more and more accessible and effective. And we’ve seen the impacts of cybercriminal tactics even more glaringly in the increased number of ransomware attacks – which remain one of the most common threats facing businesses in all sectors today.
Ransomware affects large enterprises and small organizations alike, with threat actors taking advantage of weaknesses such as compromised passwords and stolen session cookies exfiltrated via malware. With credentials in hand, actors can then gain access to enterprise systems and block access to computer systems and files until a sum of money, or “ransom”, is paid.
Ransomware attacks can be crippling for businesses both operationally and financially. The average downtime for infected organizations in the US ranges between 22-28 days, and during this time, organizations are often locked out of essential systems until they have paid sums averaging $2.73 million – a number that continues to escalate. Even then, there is no guarantee that sensitive information will be returned or recovered.
To avoid dealing with the after effects of a successful ransomware attack, businesses should focus on bolstering their defenses with a comprehensive ransomware prevention strategy.
The importance of taking preventive measures when it comes to ransomware
Cyberattack defense has traditionally been reactive. When businesses finally receive information about breaches or compromised employees, it may be too late. Though you may know better for next time, it’s important to recognize that the best defensive measures require businesses to be proactive in their approach to cybersecurity.
To get ahead, businesses need to fill in key gaps by understanding and shutting down risks associated with compromised employee and third-party credentials.
Some quick background: What is ransomware?
Ransomware is a subset of malware (malicious software) that encrypts a victim’s files, data, or entire computer system, effectively locking the user out. The attackers then demand payment, often in cryptocurrency, in exchange for the decryption key. The encryption used is typically robust, making it almost impossible to access the files without the correct decryption key.
In order to better understand how ransomware risk can affect businesses, let’s take a look at a recent case study for a global biomedical research organization. This organization needed to protect particularly sensitive healthcare research data from cybercriminals, but didn’t have a way to proactively identify exposed employees. To combat this, the organization implemented SpyCloud Enterprise Protection to proactively safeguard over 400 employees from attacks that could open the doors to their business systems and sensitive data.
Taking a page out of this organization’s playbook, other businesses, especially those in a mass-targeted industry such as healthcare, can benefit greatly by taking steps to proactively defend against ransomware attacks. See how SpyCloud’s Enterprise Protection works to prevent ransomware.
Statistics on the impact of ransomware on businesses
- The financial implications of a ransomware attack are incredibly high, with businesses paying an average of $4.91 million per attack in mitigation costs and lost revenue. This number does not include the ransom itself, which in 2024 rose to $2.73 million.
- he number of ransomware attacks increased by 13% in the past 5 years.
- According to SpyCloud’s 2024 Ransomware Defense Report, 92% of businesses said they experienced the consequences of ransomware in the past year.
- Phishing/social engineering, third-party access, and stolen cookies that enabled session hijacking were the three most common entry points that gave bad actors initial access in ransomware attacks in 2024.
- SpyCloud also found that nearly one-third of ransomware attacks are preceded by an infostealer malware infection.
Types of ransomware
- Crypto ransomware: This ransomware encrypts valuable files and demands a ransom, to be paid in cryptocurrency, for the decryption key.
- Locker ransomware: This type locks the victim out of their device, demanding a ransom to unlock it.
- Doxware: This variant threatens to release stolen, sensitive information unless a ransom is paid.
- Scareware: This type of ransomware fakes a threat and tricks the user into paying to remove it.
- Ransomware-as-a-Service (RaaS): RaaS is a malicious software model in which a bad actor manages the entire spectrum of the attack, including ransomware distribution, payment collection, and access restoration, in exchange for a share of the illicit gains.
How ransomware attacks happen
Protecting against ransomware requires both implementing countermeasures and raising security awareness with employees. When threat actors try to infiltrate organizations, they don’t always target specific individuals. Oftentimes, they are casting a wide net to see which employees offhandedly click on a phishing link or don’t have MFA enabled. That’s why it’s important to train anyone who has access to the company system – employees and third-party contractors alike – to recognize common scams and signs of suspicious activity.
Some common vectors that criminals take when targeting accounts or infecting devices are:
- Phishing scams: Imagine you get an email from your IT department saying that your device is compromised and you need to click on a link to reset your password. Or, on your personal device you receive a message from USPS saying that “your package is on the way” and to click on a link to track its delivery status. These are common types of phishing scams, where a threat actor will try to encourage the target to engage with their message – often sent through email, text message, or social media – to gain access to a device on which they can then install malware to exfiltrate data, or lock the user out.
-
Malware: A significant trend with ransomware is the infection of the ransomed device or system with infostealer malware beforehand. In SpyCloud’s 2024 Ransomware Defense report, we found that of a sample of US organizations that were victims of ransomware, 30% had been previously infected with some kind of infostealer. Threat actors often use infostealers as a way to gain access to stolen credentials that can then be used to enter the system and encrypt important files and data, thereby locking the user out.
- In cases like these, post-infection malware remediation is crucial; with SpyCloud’s advanced detection of compromised credentials and other malware-exfiltrated identity data, businesses can shut criminals out before they have a chance to profit off of stolen data.
- Remote Desktop Protocol (RDP): Another strategy that has gained popularity among criminals is exploiting RDPs, especially as hybrid and remote work environments have become the norm. When employees have poor password health, such as reusing passwords that have previously been compromised, it is easy for criminals to enter and seize control of devices to then hold for ransom.
Recent trends in ransomware attacks
After a brief decline in activity in late 2022, ransomware re-emerged with a vengeance over the last 18 months. These trends can be traced back to the mass spread of infostealer malware and subsequent influx of sensitive data available for threat actors to leverage when taking over personal accounts/devices.
Cybercriminals can purchase sensitive information such as account credentials and session cookies that were exposed through infostealer malware to then impersonate employees and gain access to computer systems and files.
SpyCloud’s research showed that ransom payments, recovery costs, and the frequency of ransomware events are all on an upward trend, and particular industries are more likely to be targeted than others in the future. More specifically:
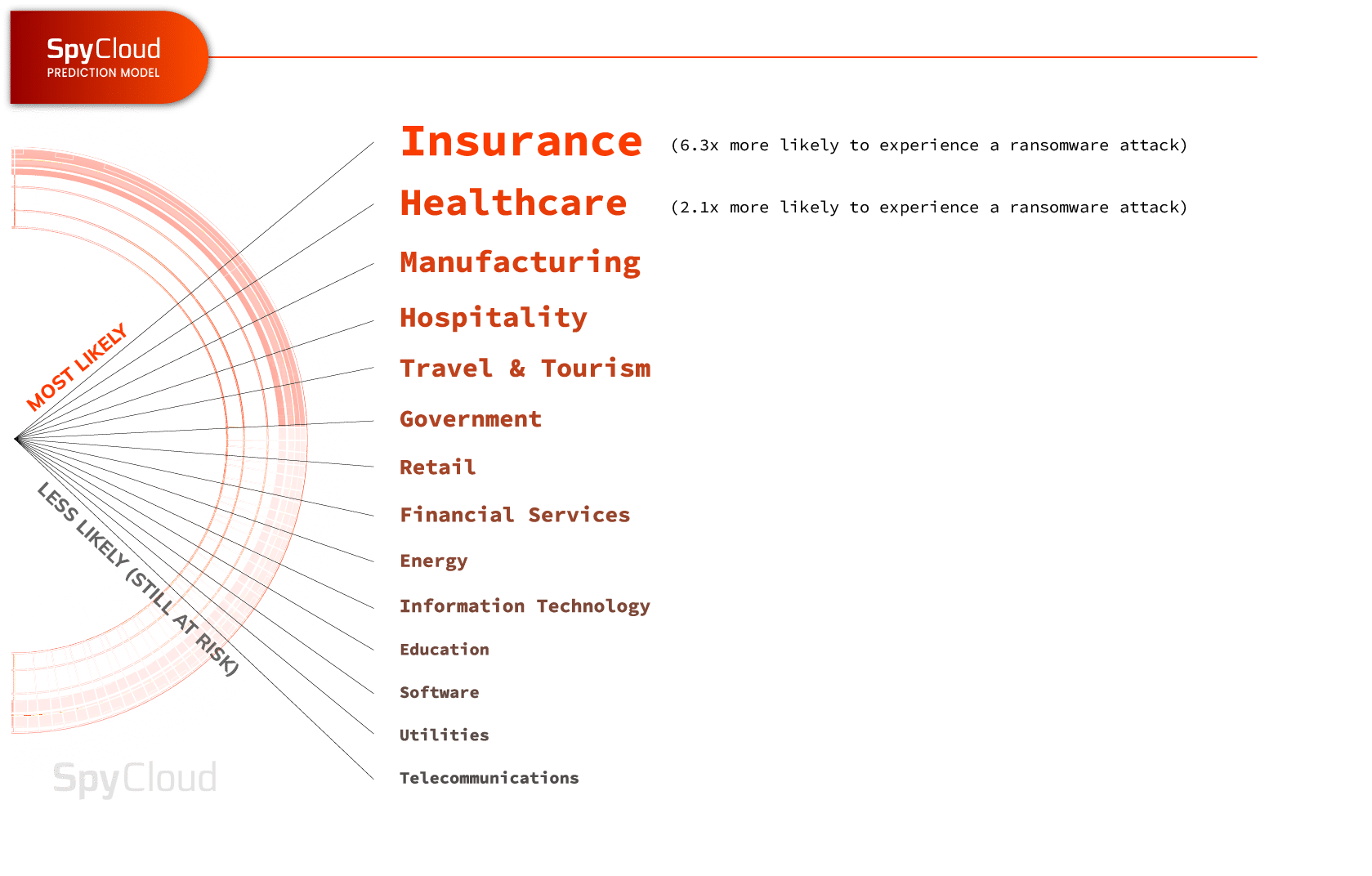
Especially for companies within these industries, it is important to recognize the connection between infostealer malware and ransomware, and take actions to detect and remediate exposed credentials and identities that may leave the organization vulnerable to future attacks.
Criminals are getting smarter, building their own business models that lead to a more complex and tangled marketplace. For example, Ransomware-as-a-Service (RaaS) – a subscription-based software developed by criminal groups to then sell to individual threat actors – makes it easier than ever for criminals, even those with very little knowledge, to launch ransomware attacks against businesses that have not taken the necessary precautions.
Case studies / Examples of ransomware attacks
By professionalizing and standardizing what were once ad-hoc criminal activities, even the most novice cybercriminals can carry out sophisticated attacks. The implications for all of us are huge, and recent high-profile attacks are evidence that the problem is only becoming more significant.
- Medibank ransomware incident: In early October of 2022, Medibank’s SOC discovered that some of their files had been modified to exploit an existing vulnerability. This led Medibank to conduct an investigation and – a few days later – discover that 9.7 million records had been exfiltrated from their database. After further digging, it was found that this breach was initiated through credentials stolen from an outside IT contractor who had saved their Medibank login information to their personal browser on their work laptop. The contractor had then signed into their personal computer, opened the same browser, and became infected with infostealer malware, resulting in the stolen corporate credentials that gave REvil access to a mass amount of data. After trying and failing to extort Medibank, REvil ransomware group then released all 9.7 million records to the dark web.
- LockBit ransomware group: It is important to note that though individual threat actors now have an easier time carrying out attacks than ever, ransomware is still an industry dominated by large groups. One such group, a Russia-based ransomware gang called LockBit, has been rapidly growing the past few years, claiming over 2,000 victims and over $120 million in ransom fees. Groups like these have the resources to execute large-scale attacks against businesses and consumers alike. This is why it is imperative that your security solutions are as proactive as possible, because criminals have already evolved past what legacy defenses can detect.
Essential security measures for ransomware prevention
How can your business adequately protect against ransomware?
SpyCloud has found significant correlation between infostealer malware infections and subsequent ransomware attacks. After a malware infection, your system is vulnerable to targeted account takeover at the hands of criminals who have obtained valuable data, such as usernames, passwords, and session cookies.
The good news is you can block threat actors from capitalizing on stolen data by fully remediating all compromised credentials associated with a given digital identity. Leverage tools that can automate password resets, and view all business applications exposed by infostealer malware so your security teams know which credentials to rest, and obtain this information quickly enough to remain relevant and actionable.
In combination with a malware exposure remediation strategy, companies should also integrate the following measures as an added layer of security:
- Employee training and awareness programs
- Regular updates to software/patch management
- Data backup strategy
- Network segmentation
- Multi-factor authentication (MFA)
- Endpoint/device protection including antivirus software
- Email security (with phishing detection)
- User and entity behavior analytics (UEBA)
- Deception technology (e.g., virtual honeypots)
- A Continuous Zero Trust model
Ransomware prevention takeaways
Preventing ransomware is no small task – it requires a continuous process of detection and remediation plus proper education on how these attacks happen. Especially now, as criminals find more creative ways to infiltrate devices and company systems, keeping your organization’s security measures up-to-date, as well as trusting someone that has comprehensive knowledge of the TTPs cybercriminals use, is crucial to having good security posture. Ransomware attacks aren’t slowing down and will continue to be a threat for the foreseeable future – keeping the pressure on companies across the globe.
Remember, criminals often seek to launch ransomware attacks using credentials that were stolen through malware infections, meaning devices that have been previously compromised are easier to take over if the victim does not take the right preventative measures. These measures include resetting all passwords, deleting inactive accounts, and invalidating session cookies that tie to critical applications. However, for companies and individuals, it is likely too time consuming to enforce these actions for each employee. This is where SpyCloud helps.
Prevent ransomware attacks with SpyCloud
With SpyCloud, your organization’s security team gains full visibility into the breadth of exposed employee identities and recaptured credentials – sourced from the criminal underground before they can be used to harm your business – making taking action faster and more convenient. This information helps your security teams detect and prevent gaps in your security systems before criminals have the chance to take advantage of them.
Regardless of the debate amongst government agencies about whether or not to ban ransomware payments altogether, it’s important for businesses to adequately protect themselves so as to avoid punishment – either through a ransom payment, penalty payment, reputation hit, or lost revenue – from all ends.
Improve your ransomware prevention strategy today
To learn more about ransomware prevention and how to better protect your business, check out Spycloud’s Enterprise Protection.