The 17th annual Verizon Data Breach Investigations Report (DBIR) once again delivers critical cybersecurity insights and analyses. But with over 100 pages – albeit entertaining with its quippy footnotes – the report can be a bear to dig through. So we’ve pulled out some key highlights for you in this blog.
About Verizon’s 2024 Data Breach Investigations Report
First things first, the report analyzes a total of 30,458 real-world security incidents that took place between November 1, 2022, and October 31, 2023, with the 2023 caseload as the primary analytical focus of the report. From those incidents, Verizon narrowed in on a record-breaking 10,626 confirmed data breaches (compared to just ~5,000 breaches analyzed in last year’s report) that impacted victims in 94 countries.
As a reminder, Verizon defines a breach as, “An incident that results in the confirmed disclosure—not just potential exposure—of data to an unauthorized party. A DDoS attack, for instance, is most often an incident rather than a breach since no data is exfiltrated.”
While data breaches are always the basis of what Verizon measures in their research each year, there are plenty of other fascinating nuggets; the report reveals insights on attack vectors, the impact of human error, and the growing threat of costly ransomware attacks.
Let’s dig in, shall we?
Stolen credentials are still the weakest link
If you’ve been following SpyCloud since we started in 2016, you know we talk a lot about stolen credentials. The ol’ username and password combo is a standard segment of stolen data that bad actors target to gain illegal access, and today, it’s still pretty common for them to do so.
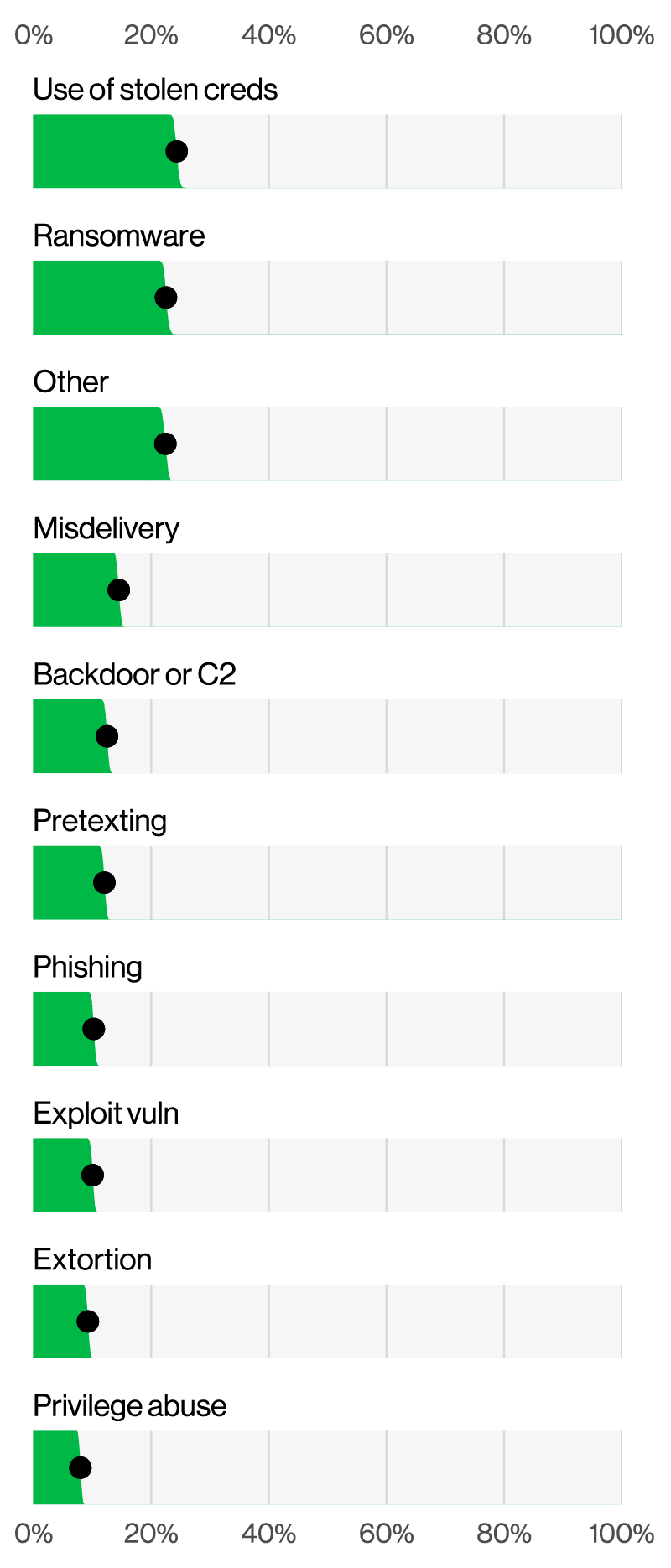
Despite a slight decline year-over-year, credential abuse remains a significant issue, particularly in web application attacks. According to this year’s DBIR report, the use of stolen credentials led the pack as the initial action in 24% of breaches.
With their added finding from an analysis of credential marketplaces that found over 1,000 credentials posted for sale daily, for an average price of $10, it’s clear there is an ongoing demand for stolen credentials driven by criminal profitability.
At SpyCloud, we continue to see stolen credentials circulating the dark web in droves. The more unfortunate news is that we also continue to see users reusing already-compromised passwords across applications, arming criminals with even more opportunities for account takeover. According to our recent Identity Exposure Report, we found that over 74% of passwords found in our recaptured database were reused, meaning a password was already compromised in two or more breaches.
Coming up with unique passwords for the dozens of accounts we have for professional and personal activities can seem daunting, but layered security for an organization comes first at the user level. And there’s clearly continuous room for awareness and training improvements with human-centric errors contributing to 28% of breaches Verizon analyzed for this report.
Businesses that encourage improved password hygiene, and that also prioritize securing credentials through measures like multi-factor authentication (MFA), are in a much better position to defend against cyber threats. It’s clear that helping employees understand the importance of strong, unique passwords while having additional tools in place to monitor for and remediate stolen credentials should continue to be priorities.
A quick note: phishing is an ongoing threat
Before we pivot too far away from the stolen credentials, it’s worth noting that this year’s report found that phishing remains the most common credential-related attack, accounting for 14% of breaches involving credentials. The median time for users to fall for phishing emails is less than 60 seconds – reinforcing the ongoing need for end-user education and training.
Malware: A persistent, non-persistent threat
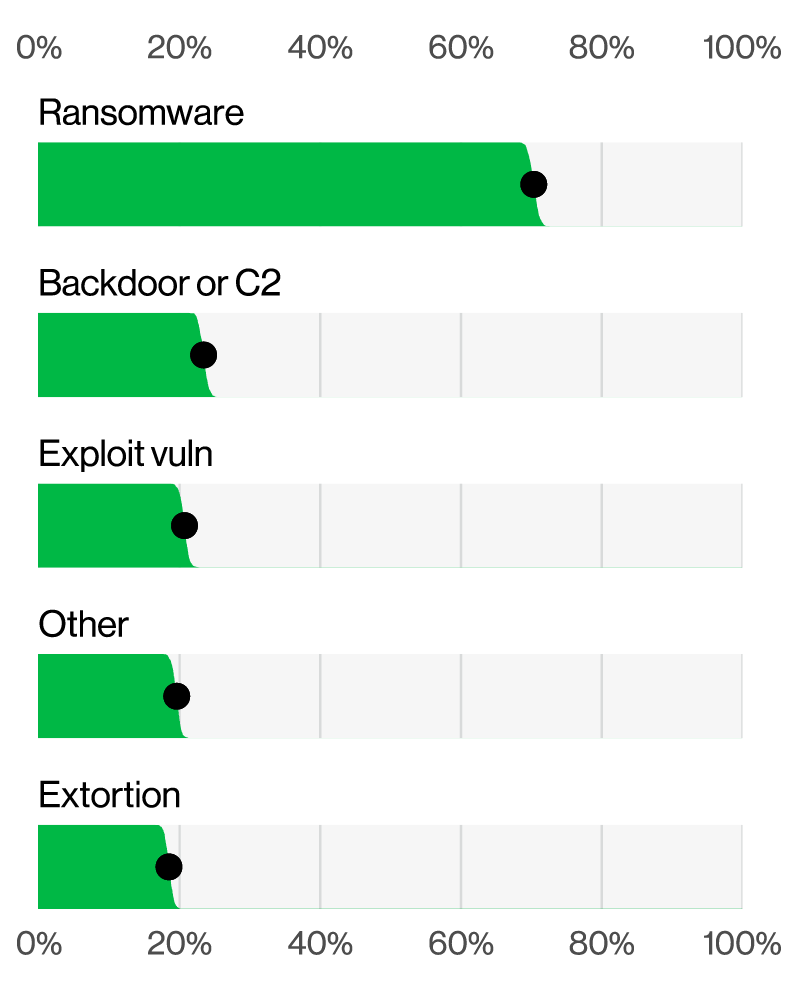
Next up: malware. Malware continues to be a common tool leveraged by criminals in sophisticated system intrusion attacks, often used in conjunction with hacking techniques like phishing. In addition to the deployment of ransomware (70% of incidents), Verizon found the exploitation of vulnerabilities and backdoors to be prevalent components of malware attacks.
Here at SpyCloud, we see overwhelming evidence specifically of:
- Infostealer malware siphoning valuable data that can be used by bad actors for system intrusion, and
- Mobile malware, primarily in the form of banking trojans, that fuels financial fraud opportunities.
Our latest research shows that for the average digital identity exposed on the dark web, there is a 1 in 5 chance of already being the victim of an infostealer malware infection – meaning criminals already have identity data like credentials, personally identifiable information (PII), financial information, and valid session cookies in hand that they can use for follow-on attacks like session hijacking, fraud, and ransomware.
While secure software and device management practices like regularly updating and patching software are significant to reducing the risk of malware exploitation, additional steps are pivotal to proper post-infection remediation to combat additional threats and exposures of a user or organization.
Ransomware: The ever-growing menace
That brings us to the star of the show: ransomware. According to the latest Verizon DBIR, ransomware attacks accounted for 23% of all breaches and affected 92% of industries. And combined, ransomware and extortion techniques were involved in 32% of all breaches, underscoring the persistent and growing threat of these types of attacks. The widespread impact on nearly all industries certainly highlights the need for comprehensive prevention strategies.
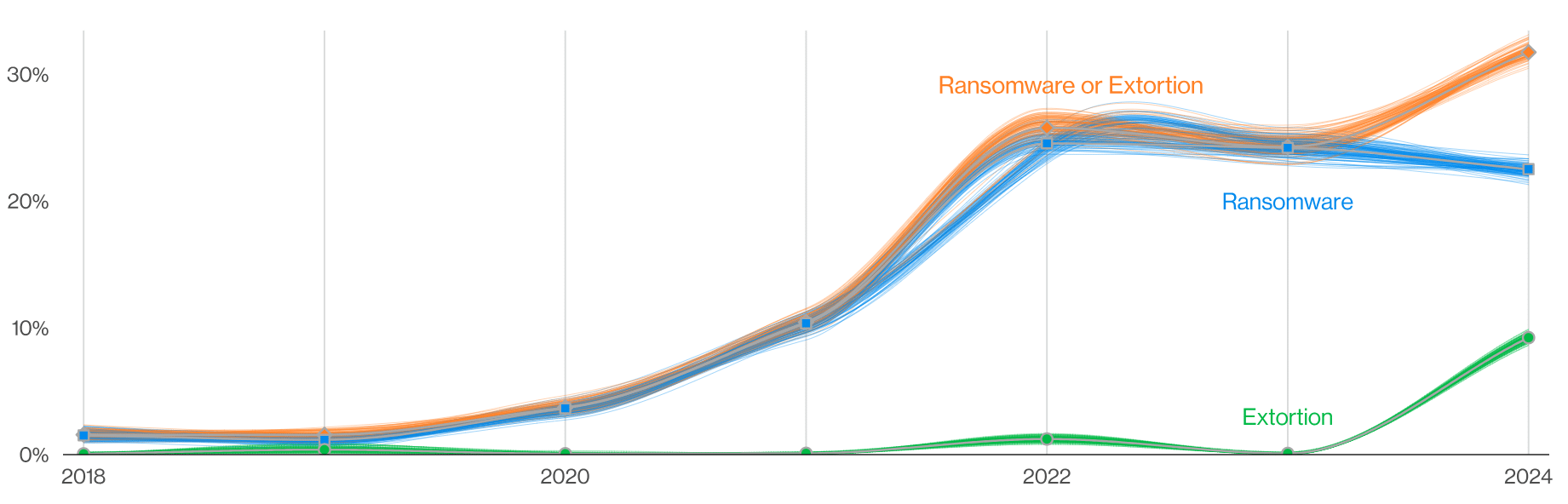
“Ransomware and Extortion breaches over time” sourced from page 7, 2024 Verizon DBIR.
What is also of note is the reported ransom demands and payments. According to the report, the median ransom demand was 1.34% of the victim’s total revenue, with actual payments often reaching significant sums. The median adjusted loss for those who paid ransoms increased to around $46,000, a sharp rise from the previous year’s $26,000.
Those numbers may seem negligible in the scheme of things, but they only account for the ransom itself, not the combined loss to the business for potential downtime, increased resources, customer churn, or overall brand impact.
It’s no secret that financial motivation remains a huge driver for bad actors looking to steal and sell data. According to the report, financially-motivated attacks like ransomware and extortion accounted for nearly two-thirds of breaches over the past three years due to the potential for big payouts.
Industry specific insights: no one is immune
As with ransomware, data breaches and other cyberattacks like account takeover and fraud are rather agnostic when it comes to their targets. It’s a matter of the path of least – or lesser – resistance and the draw toward desired rewards.
Here are a few stats from the Verizon DBIR that we found interesting to industry-specific security:
- Financial and Insurance:
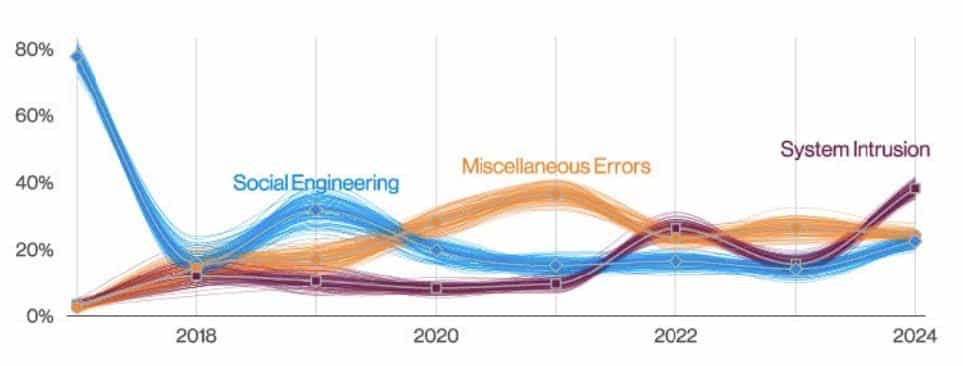
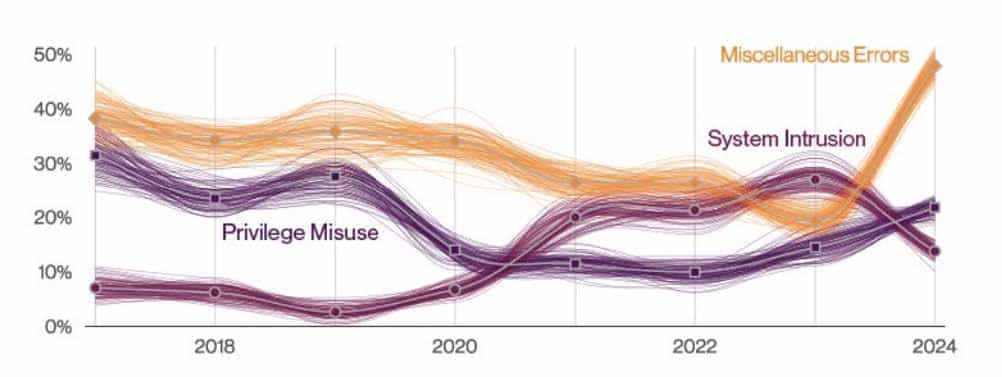
System intrusion accounted for 29% of breaches, with financial data and credentials frequently compromised. The shift towards more complex attacks and the rise in social engineering are notable trends.
Third-party risks: Choose your friends – and partners – wisely
And last but not least, let us not forget the always-looming dangers that come from third-party risk. Verizon found that 15% of breaches involved third-party infrastructures, including partner networks and software supply chain issues. The report states, “This metric ultimately represents a failure of community resilience and recognition of how organizations depend on each other. Every time a choice is made on a partner (or software provider) by your organization and it fails you, this metric goes up” – pointing to the importance of securing your entire ecosystem.
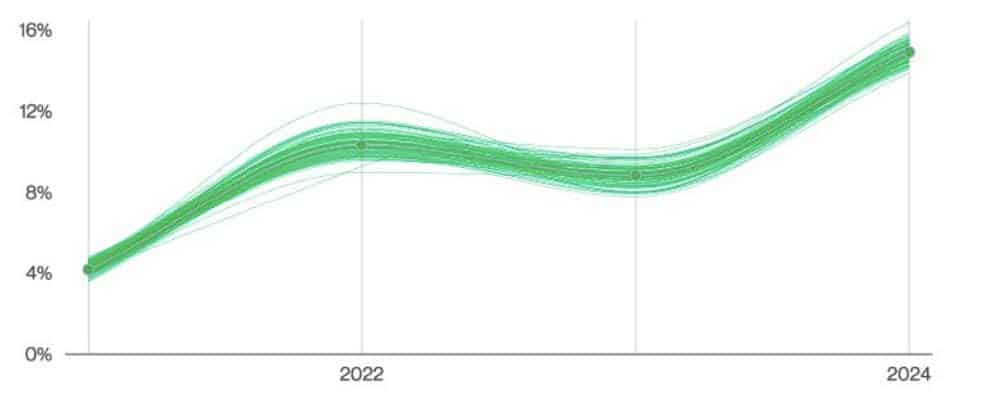
“Supply chain interconnection in breaches over time” sourced from page 13, 2024 Verizon DBIR
Final thoughts on breach trends
The Verizon DBIR never fails to provide critical insights into the current state of cybersecurity threats. At SpyCloud, we emphasize the importance of proactive measures – layered security practices, regular software updates, employee training, and automated monitoring and remediation of compromised data – to mitigate risks and protect against any number of cyber threats and tactics.
By implementing layered security practices, regular software updates, employee training, and the automated monitoring and remediation of compromised data, organizations have a fighting chance to not only reduce their risk of falling victim to these pervasive threats but level the playing field against cybercriminals.
Find out what cybercriminals know about your business. Use SpyCloud’s Check Your Exposure tool to get insights on your corporate darknet exposure, including exposed credentials, malware-infected employees and stolen web session cookies that can be used to launch cyber attacks on your organization
Key takeaways
- The 2024 DBIR analyzed 10,626 confirmed breaches, nearly double from the previous year.
- Stolen credentials were the initial action in 24% of breaches, underscoring the importance of strong password hygiene and MFA.
- Phishing accounted for 14% of breaches involving credentials, with users often falling for phishing emails in less than 60 seconds.
- 70% of malware incidents involved ransomware, while ransomware accounted for 23% of all breaches, affecting 92% of industries.
- Financial, healthcare, manufacturing, retail, educational services, and public administration sectors each face unique cyber threats.
- Human error contributed to 28% of breaches, highlighting the need for continuous employee training
- 15% of breaches involved third-party infrastructures, emphasizing the need for comprehensive ecosystem security.
- Median ransom demand was 1.34% of the victim's total revenue, with a median adjusted loss for those who paid ransoms around $46,000.
- 74% of passwords in SpyCloud’s database were reused, showing a significant risk from compromised credentials.
- Proactive measures like layered security, regular updates, and automated monitoring for & remediation of compromised data are essential to defense against evolving cyber threats.